Most organizations pursuing federal contracts or enterprise deals discover FIPS 140-2 requirements buried in procurement specifications—often after significant product development investment. This creates a fundamental compliance gap that surfaces during contract negotiations, security assessments, or customer onboarding processes when enterprise buyers demand documented cryptographic validation.
FIPS 140-2 is a U.S. government computer security standard used to approve cryptographic modules under the title "Security Requirements for Cryptographic Modules." Understanding this standard matters because the standard is an information technology security approval program for cryptographic modules produced by private sector vendors who seek to have their products certified for use in government departments and regulated industries (such as financial and health-care institutions) that collect, store, transfer, share and disseminate sensitive but unclassified (SBU) information.
The distinction between possessing FIPS validation and merely implementing approved algorithms determines whether your product appears on procurement approved vendor lists or faces immediate disqualification.
What is FIPS 140-2?
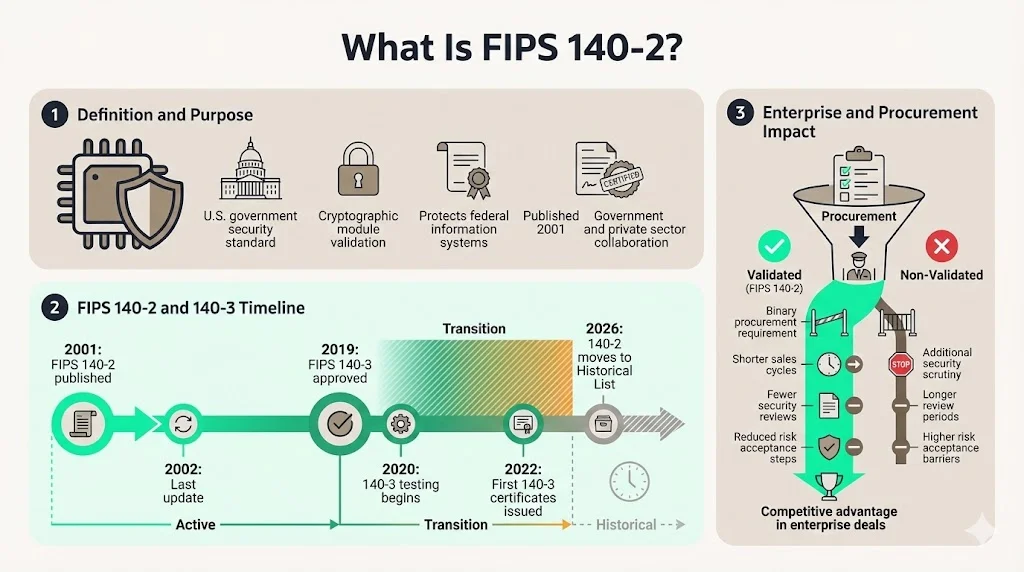
Federal Information Processing Standard Publication 140-2 is a U.S. government computer security standard used to approve cryptographic modules, initially published on May 25, 2001, and last updated December 3, 2002. The standard emerged from collaboration between government agencies and private sector vendors recognizing the need for validated cryptographic implementations protecting federal information systems.
FIPS 140-3 was approved on March 22, 2019, and became effective on September 22, 2019, with testing beginning on September 22, 2020, and the first FIPS 140-3 validation certificates issued in December 2022. Despite this succession, all FIPS 140-2 validations will be moved to the Historical List on September 21, 2026, though modules validated as conforming to FIPS 140-2 can continue to be accepted by Federal agencies for the protection of controlled unclassified information through that date.
Enterprise technology evaluations routinely include FIPS 140-2 validation as a binary procurement criterion. Companies lacking current validation certificates face extended sales cycles requiring security architecture reviews, compliance attestations, and risk acceptance procedures that competitors with validated modules bypass entirely.
Why FIPS 140-2 Matters for Companies
Federal procurement mandates represent the most direct driver of FIPS validation requirements. Non-validated cryptography is viewed as providing no protection to the information or data—in effect the data would be considered unprotected plaintext. If the agency specifies that the information or data be cryptographically protected, then FIPS 140-2 or FIPS 140-3 is applicable. In essence, if cryptography is required, then it must be validated.
Beyond direct federal sales, FIPS validation cascades into regulated industries through compliance frameworks. FIPS 140-2 has proliferated into other verticals, like healthcare (HIPAA) and the financial industry. Enterprise security teams evaluating vendor cryptographic implementations reference FIPS validation as objective third-party verification of security engineering competence—distinguishing vendors who implement cryptographic best practices from those offering encryption features without validated assurance.
Advertising FIPS 140-2 compliance signals operational maturity that resonates with technical decision-makers navigating procurement processes. Organizations demonstrating validated cryptographic modules position themselves as vendors capable of meeting federal security baselines, regulatory requirements, and enterprise risk management standards without requiring customer-funded security audits or architectural remediation.
FIPS 140-2 Requirements: What They Cover
Overview of FIPS 140-2 Requirements
Security requirements cover 11 areas related to the design and implementation of a cryptographic module. Within most areas, a cryptographic module receives a security level rating (1–4, from lowest to highest), depending on what requirements are met. These requirement areas encompass cryptographic module specification, ports and interfaces, roles and services authentication, finite state model, physical security, operational environment, cryptographic key management, electromagnetic interference/electromagnetic compatibility, self-tests, design assurance, and mitigation of other attacks.
The standard establishes specific criteria for how cryptographic modules protect sensitive information through technical controls, documentation requirements, and operational procedures. An overall rating indicates the minimum of the independent ratings received in the areas with levels and fulfillment of all requirements in other areas. On a vendor's validation certificate, individual ratings are listed, as well as the overall rating.
Security Levels Explained
The standard provides four increasing qualitative levels of security intended to cover a wide range of potential applications and environments. Understanding these distinctions enables organizations to align validation investments with customer requirements and operational threat models.
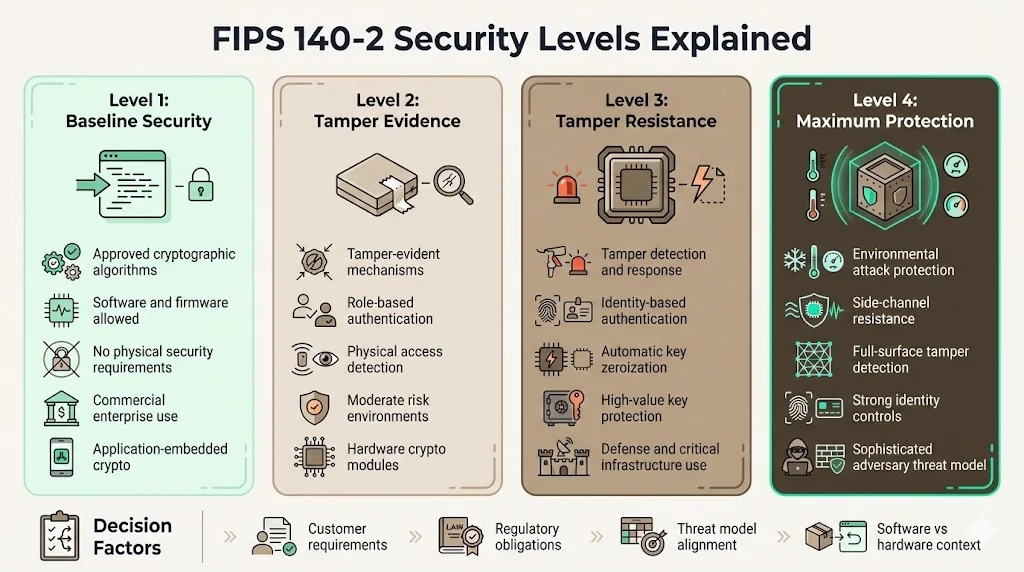
Level 1 establishes baseline security requiring use of approved cryptographic algorithms and security functions. This level permits software and firmware implementations without specific physical security requirements beyond production-grade components. Organizations targeting commercial enterprise customers typically pursue Level 1 validation for software cryptographic modules embedded in broader application platforms.
Level 2 adds tamper-evidence requirements through physical security mechanisms like tamper-evident seals or coatings and implements role-based authentication requiring operators to authenticate before performing cryptographic operations. Hardware cryptographic modules at Level 2 demonstrate physical evidence if enclosures have been opened or modified, addressing scenarios where equipment faces moderate physical access risks.
Level 3 strengthens tamper resistance with identity-based authentication mechanisms and physical security designed to detect and respond to tampering attempts—including tamper response mechanisms that zeroize critical security parameters when intrusion occurs. Organizations serving defense, intelligence, or critical infrastructure sectors frequently require Level 3 validation for hardware security modules protecting high-value cryptographic keys.
Level 4 provides the highest protection against sophisticated physical attacks including environmental manipulation and side-channel analysis. This level requires environmental failure protection and testing, tamper detection and response covering all module surfaces, and strong identity-based authentication. Level 4 validations address scenarios involving determined adversaries with substantial technical capabilities and physical access.
Companies determine appropriate security levels by evaluating customer procurement specifications, regulatory requirements, and threat models. Most commercial enterprise software vendors pursue Level 1 validation, while hardware security module manufacturers targeting federal agencies typically validate at Level 2 or Level 3.
Cryptographic Modules: Core to FIPS 140-2
A commercial cryptographic module is commonly referred to as a hardware security module (HSM). Cryptographic modules encompass hardware, software, firmware, or combinations thereof implementing cryptographic functions including encryption, decryption, digital signatures, key generation, and key management. The module boundary defines precisely which components, interfaces, and cryptographic operations fall within validation scope.
Companies typically implement validated cryptographic modules through dedicated hardware security appliances protecting root cryptographic keys, software libraries embedded in applications providing encryption capabilities, or firmware components within networking equipment securing communications. Examples include OpenSSL-based cryptographic libraries validated for specific operating system and compiler combinations, dedicated HSM appliances like those securing payment processing systems, or cryptographic implementations within secure communications devices.
Validating these modules represents the core compliance mechanism. All of the tests under the CMVP are handled by third-party laboratories that are accredited as Cryptographic Module Testing laboratories by the National Voluntary Laboratory Accreditation Program (NVLAP). Vendors interested in validation testing may select any of the accredited labs. NVLAP accredited Cryptographic Modules Testing laboratories perform validation testing of cryptographic modules. This third-party validation process establishes independent verification that cryptographic implementations meet documented security requirements.
FIPS 140-2 and Encryption Compliance
FIPS validation establishes direct linkage to broader encryption compliance frameworks mandating validated cryptography. Federal Risk and Authorization Management Program baselines, Department of Defense security technical implementation guides, and intelligence community directives reference FIPS 140 validation as mandatory cryptographic protection mechanisms for information systems.
Enterprise procurement specifications frequently mandate FIPS 140-2 certification as non-negotiable requirements—vendors lacking current validation certificates face immediate disqualification regardless of encryption algorithm strength or security architecture sophistication. Procurement teams distinguish between "FIPS-compliant" products using approved algorithms and "FIPS-validated" products possessing official CMVP certificates. Only validated modules satisfy federal acquisition regulations and most enterprise security standards.
Approved algorithms and key management best practices form the foundation of FIPS requirements. Modules must implement cryptographic algorithms from NIST-approved lists including Advanced Encryption Standard for symmetric encryption, RSA and Elliptic Curve Cryptography for asymmetric operations, and Secure Hash Algorithm variants for cryptographic hashing. Key management requirements address cryptographic key generation using approved random number generators, key establishment through validated protocols, key storage with appropriate access controls, and key destruction ensuring cryptographic material cannot be recovered after zeroization.
FIPS 140-2 Testing and Validation
The Cryptographic Module Validation Program (CMVP), a joint effort of the U.S. National Institute of Standards and Technology (NIST) and the Canadian Centre for Cyber Security (CCCS), validates cryptographic modules to the Security Requirements for Cryptographic Modules standard (FIPS 140-2) and related FIPS cryptography standards. This bilateral program establishes mutual recognition between United States and Canadian federal agencies.
Validation entails comprehensive conformance testing performed by NVLAP-accredited laboratories evaluating cryptographic implementations against detailed derived test requirements. Testing laboratories examine module documentation, conduct algorithm validation testing, verify physical security mechanisms, assess key management implementations, and validate operational procedures. Third-party testers identify non-conformances requiring vendor remediation before validation certificates are issued.
Certification timelines vary substantially based on module complexity, laboratory workload, and vendor preparedness. Organizations should anticipate 6-12 months from initial laboratory engagement to certificate issuance for straightforward software modules, with hardware modules or complex implementations potentially requiring 12-18 months. Common hurdles include incomplete documentation packages, algorithm implementation errors requiring code changes, insufficient physical security mechanisms necessitating hardware modifications, and evolving implementation guidance requiring test approach adjustments. Vendors frequently underestimate documentation rigor required for security policies, cryptographic module specifications, and operational procedures.
Transition to FIPS 140-3
FIPS 140-3 was approved on March 22, 2019, and became effective on September 22, 2019. FIPS 140-3 testing began on September 22, 2020, and the first FIPS 140-3 validation certificates were issued in December 2022. The newer standard aligns NIST guidance with international cryptographic module security standards ISO/IEC 19790:2012 and ISO/IEC 24759:2017, facilitating international recognition and reducing duplicative testing burdens.
All FIPS 140-2 validations will be moved to the Historical List on September 21, 2026, though modules validated as conforming to FIPS 140-2 can continue to be accepted by Federal agencies through that date. After that time CMVP will place the FIPS 140-2 validated modules on the Historical list, allowing agencies to continue using these modules for existing systems only. Enterprises should recognize that FIPS 140-2 certificates remain legally valid for federal procurement through September 2026, providing continued value for existing validations while new submissions must pursue FIPS 140-3 certification.
Organizations maintaining product portfolios with FIPS 140-2 validations face strategic decisions regarding transition timing. Starting immediate FIPS 140-3 validation efforts positions products for post-2026 procurement cycles and signals commitment to current standards. However, Agencies should continue to make use of FIPS 140-2 modules until replacement FIPS 140-3 modules become available. This guidance acknowledges that FIPS 140-3 validated module availability remains limited compared to the extensive FIPS 140-2 validated module ecosystem developed over two decades.
Comparing FIPS 140-2 to Other Standards
FIPS 140-2 vs. FIPS 140-3
FIPS 140-3 represents an evolutionary update rather than fundamental reconceptualization. The successor standard maintains the same four security levels and eleven requirement areas while incorporating updated cryptographic algorithm requirements, enhanced software security provisions, and alignment with international standards. Key differences include more rigorous documentation requirements, updated approved algorithm lists reflecting current cryptographic best practices, and modified physical security testing procedures.
Organizations holding FIPS 140-2 validations cannot simply "upgrade" to FIPS 140-3 status—new validations require complete retesting under updated standards. Companies planning product roadmaps should evaluate whether pursuing FIPS 140-3 validation for new modules while maintaining existing FIPS 140-2 certificates for current products provides optimal risk-adjusted investment.
FIPS 140-2 vs. Common Criteria
FIPS 140-2 and Common Criteria address fundamentally different security evaluation scopes. FIPS validation focuses exclusively on cryptographic module security requirements—examining how cryptographic algorithms, key management, physical security, and operational procedures protect sensitive information. Common Criteria provides a broader IT product security evaluation methodology assessing security functionality claims across entire product architectures including access control, audit, identification and authentication, and security management.
Federal procurement specifications frequently require both certifications for security-critical products. Defense information systems might mandate Common Criteria Evaluation Assurance Level 4 for operating system security functionality validation combined with FIPS 140-2 Level 3 for embedded cryptographic modules. Enterprise customers typically prioritize FIPS validation for products where cryptographic protection represents primary security functionality while Common Criteria evaluations address products requiring comprehensive security architecture assessment.
Validation costs, timelines, and maintenance burdens differ substantially between standards. FIPS validation typically requires 6-18 months with costs ranging from $100,000-$500,000 depending on module complexity and security level. Common Criteria evaluations span 12-24 months with costs frequently exceeding $500,000 for higher evaluation assurance levels. Organizations should align certification investments with customer requirements and competitive differentiation opportunities rather than pursuing validation comprehensively.
Practical Guide: How Companies Achieve FIPS 140-2 Compliance
Organizations pursuing FIPS validation should establish clear module boundaries defining cryptographic functionality scope before engaging testing laboratories. Early boundary definition decisions—whether validating entire applications, specific cryptographic libraries, or dedicated hardware components—fundamentally impact documentation requirements, testing scope, and operational constraints.
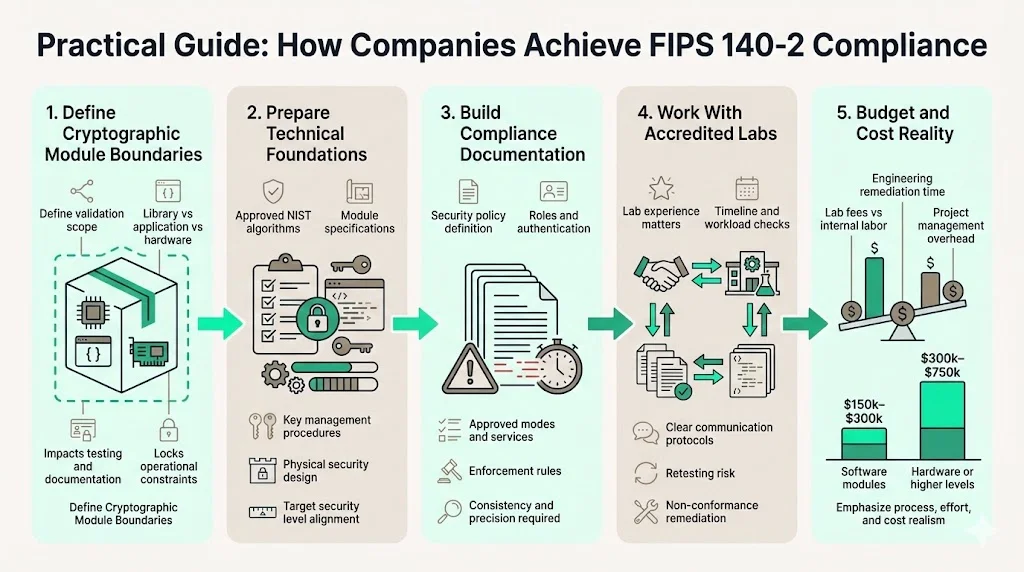
Preparation steps include developing comprehensive security policy documentation specifying security rules governing module operation, creating cryptographic module specification documents detailing module components and interfaces, implementing approved cryptographic algorithms from NIST-validated algorithm lists, establishing cryptographic key management procedures addressing key lifecycle operations, and designing physical security mechanisms appropriate for target security levels.
Documentation requirements represent the most commonly underestimated validation component. Security policies must precisely specify approved modes of operation, cryptographic officer and user roles, authentication mechanisms, approved services, and security rules enforcement. Organizations lacking technical writing resources dedicated to compliance documentation frequently experience validation delays when testing laboratories identify incomplete or inconsistent documentation packages.
Working with accredited laboratories begins with vendor selection evaluating laboratory experience with similar module types, current workload affecting timeline projections, communication practices during testing phases, and cost structures including initial testing fees and potential re-testing charges. Vendors should establish clear communication protocols, provide complete documentation packages before formal testing begins, maintain technical resources available for laboratory questions, and budget contingency time for addressing non-conformance findings.
Cost management requires understanding that quoted laboratory fees represent testing services only—vendor engineering time for remediation, documentation development, and project management typically equals or exceeds direct laboratory costs. Organizations should budget $150,000-$300,000 for straightforward software module validation including laboratory fees and internal labor, with hardware modules or higher security levels potentially requiring $300,000-$750,000 total investment.
Conclusion
FIPS 140-2 validation remains operationally relevant through September 2026 for organizations selling to federal agencies, regulated industries, and security-conscious enterprises requiring documented cryptographic assurance. Understanding the distinction between implementing approved encryption algorithms and possessing validated cryptographic modules directly impacts procurement qualification, competitive positioning, and sales cycle duration.
Organizations should approach FIPS validation as a strategic investment requiring 6-18 month timelines, $100,000-$500,000+ budgets, and sustained engineering commitment rather than compliance checkbox activities. The transition to FIPS 140-3 creates planning considerations for companies maintaining validated product portfolios—balancing continued FIPS 140-2 certificate value against positioning for post-2026 procurement requirements.
Companies serious about federal and enterprise markets implement validated cryptographic modules within product architectures from initial design rather than retrofitting validation onto existing implementations. This approach reduces validation timeline risks, minimizes architectural constraints from boundary definition limitations, and demonstrates security engineering maturity that technical evaluators recognize during procurement assessments.
FAQs
1) What does FIPS 140-2 compliant mean?
A product is FIPS 140-2 compliant when its cryptographic modules meet the standard's security requirements and have been validated through the official CMVP program administered by NIST and the Canadian Centre for Cyber Security. Compliance requires possession of validation certificates listing specific module names, version numbers, and operational environments rather than simply implementing approved cryptographic algorithms.
2) Is FIPS 140-2 obsolete?
FIPS 140-2 is being phased out in favor of FIPS 140-3 but remains relevant until September 21, 2026 for historical validations. Federal agencies can continue accepting FIPS 140-2 validated modules through that date, and existing systems may continue using these modules afterward. Organizations should evaluate FIPS 140-3 validation for new modules while existing FIPS 140-2 certificates retain procurement value through the transition period.
3) What is the difference between FIPS 140-2 and 140-3?
FIPS 140-3 is the newer version with updated criteria and structure aligning with international standards ISO/IEC 19790:2012 and ISO/IEC 24759:2017, though both cover cryptographic module security across the same four security levels and eleven requirement areas. The updated standard includes revised algorithm requirements, enhanced software security provisions, and modified physical security testing procedures requiring complete revalidation rather than certificate updates.
4) What is the difference between FIPS 140-2 and Common Criteria?
FIPS 140-2 focuses specifically on cryptographic modules examining algorithm implementations, key management, physical security, and operational procedures, whereas Common Criteria covers broader IT product evaluation assessing security functionality claims across entire product architectures including access control, audit, and security management. Federal procurement frequently requires both certifications—FIPS validation for cryptographic components and Common Criteria evaluation for comprehensive security architecture assessment.
5) What is FIPS 140-2?
FIPS 140-2 is a federal standard defining security requirements for cryptographic modules used to protect sensitive but unclassified information in government systems and regulated industries. The standard specifies four security levels addressing cryptographic algorithms, key management, physical security, and operational procedures validated through independent third-party laboratories accredited by NVLAP.
6) Who needs FIPS 140-2 compliance?
Government agencies and any vendor selling to those agencies or regulated industries that mandate the standard require FIPS 140-2 compliance. This includes federal contractors, defense industry suppliers, healthcare organizations handling protected health information, financial institutions managing sensitive financial data, and enterprise technology vendors targeting security-conscious customers with cryptographic protection requirements.
7) Is FIPS 140-2 still relevant in 2026?
Yes. Validations remain listed as active through September 21, 2026, when FIPS 140-2 certificates transition to the historical list permitting continued use in existing systems but prohibiting inclusion in new federal system deployments. Enterprise clients recognize FIPS validation value beyond regulatory compliance timelines as objective verification of cryptographic implementation competence, maintaining commercial relevance even as FIPS 140-3 becomes the standard for new validations.



.svg)
.svg)
.svg)