Healthcare organizations handle protected health information (PHI) across every patient interaction—from scheduling appointments to transmitting lab results to processing insurance claims. This information exists in multiple formats: paper charts, verbal communications, and increasingly, electronic systems. The digital transformation of healthcare has introduced efficiency gains while simultaneously expanding the attack surface for data breaches and unauthorized access.
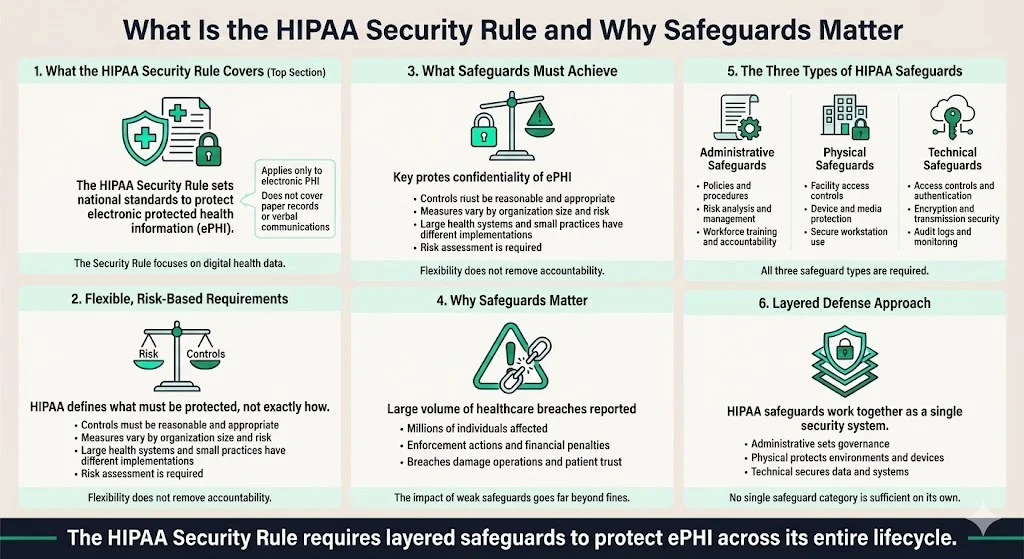
The Health Insurance Portability and Accountability Act (HIPAA) Security Rule establishes national standards requiring covered entities and business associates to implement administrative, physical, and technical safeguards to secure individuals' electronic protected health information (ePHI). These three safeguard categories form the foundation of regulatory compliance for protecting patient data in electronic form.
This article defines each safeguard type, explains their implementation requirements, and addresses the practical considerations healthcare organizations face when building compliant security infrastructure. Understanding how these safeguards complement each other enables organizations to move beyond checklist compliance toward genuine data protection.
What is the HIPAA Security Rule & Why Safeguards Matter
The Security Rule establishes a national set of security standards to protect certain health information that is maintained or transmitted in electronic form. Unlike general PHI—which encompasses paper records, verbal communications, and electronic data—the Security Rule applies specifically to electronic protected health information (ePHI).
HIPAA legislation doesn't specify exact controls or tools that need to be in place for compliance, focusing more on what healthcare organizations should do to protect patient data rather than the specifics of how it needs to be accomplished. Organizations must determine what measures are "reasonable and appropriate" based on their size, infrastructure, risk environment, and resources. A national hospital system implements different security measures than a three-physician practice—but both must demonstrate systematic risk assessment and appropriate safeguards.
Safeguards must ensure the integrity and confidentiality of information while protecting against reasonably anticipated threats or hazards to security and unauthorized uses or disclosures. The consequences of inadequate safeguards extend beyond regulatory penalties. In the first three quarters of 2025, 546 healthcare data breaches of unsecured PHI were reported to the Office for Civil Rights, affecting an estimated 42 million individuals. With 19 settlements and over $8 million in fines issued in 2025 to date, the year has already broken the record for the highest number of resolution agreements.
Organizations failing to implement adequate safeguards face direct financial exposure, operational disruption, reputational damage, and erosion of patient trust—outcomes that far exceed the cost of proper security implementation.
3 Types of HIPAA Safeguards
The Security Rule requires implementation of three types of safeguards: administrative, physical, and technical. These categories address different dimensions of data protection: organizational policies and processes, physical infrastructure and access controls, and technology-based security measures.
The safeguards function as a layered defense system. Administrative safeguards establish the governance framework and workforce accountability mechanisms. Physical safeguards protect the premises, devices, and media where ePHI resides. Technical safeguards secure data through access controls, encryption, and system monitoring. Organizations cannot achieve comprehensive security by implementing only one or two categories—all three must work in concert to protect ePHI throughout its lifecycle.
Administrative Safeguards — Building the Policy & Process Foundation
What are Administrative Safeguards
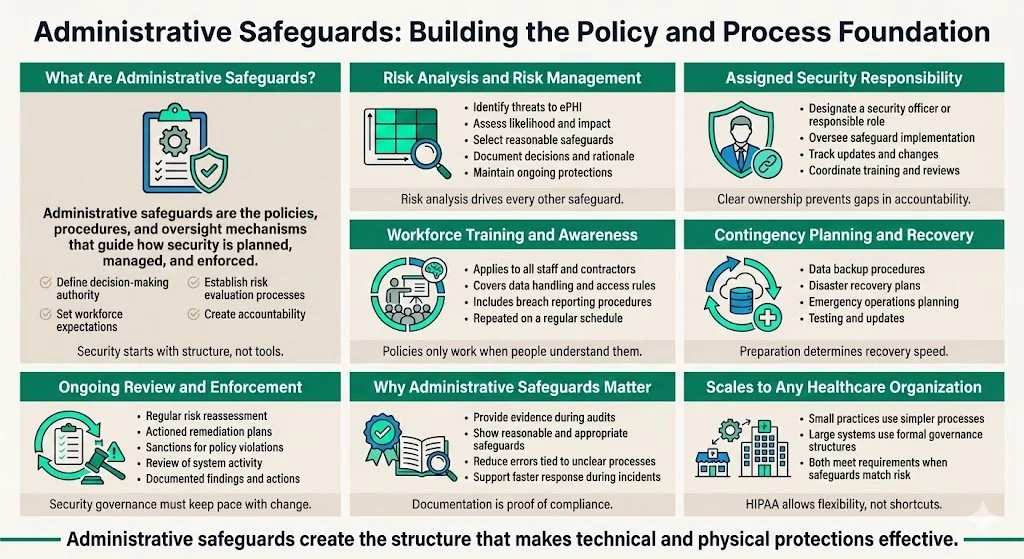
Administrative safeguards involve administrative actions, policies, and procedures to manage the selection, development, implementation, and maintenance of security measures. These safeguards form the compliance foundation—establishing who makes security decisions, how risks are evaluated, what policies govern data handling, and how the workforce is trained and held accountable.
Administrative safeguards are often considered the core of security compliance because they determine whether an organization has structured, documented processes or operates through ad hoc reactions to security concerns.
Key Components / Requirements
The Security Rule administrative safeguard provisions require covered entities and business associates to perform a risk analysis, which helps determine what security measures are reasonable and appropriate through evaluating the likelihood and impact of potential risks to ePHI, implementing appropriate security measures, documenting chosen measures and rationale, and maintaining continuous protections.
Organizations must designate a security officer or responsible party to oversee compliance, monitor implementation, manage updates, and coordinate training. This individual or team serves as the accountable authority for security posture across the organization.
Workforce training and awareness programs ensure all personnel understand security protocols, data handling requirements, and breach response procedures. Training extends beyond clinical staff with direct ePHI access—administrative personnel, facilities staff, and contractors must understand their role in maintaining security.
Contingency planning and data backup/recovery procedures address emergencies, system failures, natural disasters, and cyberattacks. These plans ensure ePHI remains available and secure during disruptions while enabling rapid restoration of systems and data.
Periodic review and updates address the reality that risk evolves continuously. New technologies introduce vulnerabilities, threat actors develop more sophisticated attack methods, and organizational changes alter the risk landscape. The security management process must consist of at least a risk analysis, an actioned remediation plan, a sanctions policy, and procedures to regularly review information system activity, with all analyses, remediation plans, sanctions, and reviews documented.
Why It Matters for Healthcare Companies
Administrative safeguards provide the structured, documented compliance framework that demonstrates regulatory adherence during audits and investigations. Organizations without documented policies, risk assessments, and training records cannot prove they've implemented "reasonable and appropriate" safeguards—regardless of their actual security posture.
These safeguards reduce human error and careless data handling by establishing clear expectations and consequences. Security breaches frequently result from workforce members who lack training on proper protocols or organizations that fail to enforce policies consistently.
Contingency planning prepares organizations for incident response and recovery. When ransomware attacks encrypt EHR systems or natural disasters damage data centers, organizations with tested contingency plans restore operations within hours or days rather than weeks or months.
The flexibility of administrative safeguards allows them to scale across different organizational sizes and types. Small clinics document simpler processes with fewer personnel, while large hospital systems implement more complex governance structures—but both can demonstrate compliance appropriate to their circumstances.
Physical Safeguards — Protecting the Physical Environment & Devices
What are Physical Safeguards
Physical safeguards encompass physical measures, policies, and procedures to protect a covered entity's electronic information systems and related buildings and equipment from natural and environmental hazards and unauthorized intrusion. These safeguards address both premises (offices, server rooms, storage facilities) and devices or media that store or transmit ePHI (computers, servers, hard drives, backup tapes, mobile devices).
Physical security creates the foundation that enables other safeguards to function effectively. Without proper facility access controls and device protections, even sophisticated technical measures may fail when unauthorized individuals gain physical access to systems.
Main Areas / Implementation Specifications
Facility access controls include locks, alarm systems, badge readers, biometric scanners, visitor sign-in procedures, restricted areas, and access validation mechanisms. Organizations implement multiple layers of physical barriers—perimeter security, building entry controls, department-level access restrictions, and secured areas for particularly sensitive systems like servers or backup storage.
Workstation use and security policies ensure computers and terminals are positioned in secure locations away from public view. Privacy screens prevent unauthorized viewing, automatic screen locks activate after brief inactivity periods, and workstation positioning considers visibility from hallways, waiting areas, or windows. Organizations establish clear rules about workstation access, screen clearing when stepping away, and prohibition of unattended logged-in sessions.
Physical safeguards protect the physical points of access to PHI, setting the stage for how employees should manage their workstation and mobile devices to keep sensitive information secure through limits to facility access via surveillance cameras or ID badges and outlining proper and improper use of technology.
Device and media controls govern how hardware and storage media containing ePHI are moved, stored, reused, and disposed of. Organizations track devices throughout their lifecycle, implement secure transportation procedures when moving equipment between locations, and ensure ePHI is securely wiped or destroyed before disposal or reuse. These controls address hard drives, backup tapes, external storage devices, decommissioned servers, and mobile devices.
Environmental protections safeguard against natural hazards including fire, flood, temperature extremes, power failures, and physical damage. Implementation includes surveillance systems, structural security measures, secure cabinets or safes for backup media, redundant power supplies, climate controls, and fire suppression systems.
Importance for Healthcare Organizations
Physical safeguards prevent unauthorized physical access to patient data—from external intruders attempting to steal devices or breach facilities, and from internal personnel who lack authorization to access specific systems or areas. A receptionist should not have physical access to the server room; visitors should not move through facilities unescorted.
These protections secure hardware and media throughout their lifecycle. Devices containing ePHI that are lost, stolen, or improperly disposed of create data breach obligations and patient notification requirements. Organizations that implement proper device tracking, secure disposal, and environmental protections avoid these exposures.
Physical safeguards work as a foundational layer of defense. If someone steals a server from an unsecured room, encryption and access controls become irrelevant—the attacker possesses the hardware and can attempt to bypass technical protections without detection. Physical security prevents such scenarios from occurring.
The increasing prevalence of mobile devices, remote work arrangements, and distributed systems makes physical safeguards more complex but equally vital. Organizations must extend facility-based protections to home offices, mobile clinics, satellite locations, and portable devices that travel between sites.
Technical Safeguards — Securing the Data and Digital Systems
What are Technical Safeguards
Technical safeguards include measures—such as firewalls, encryption, and data backup—to be implemented to keep ePHI secure, including technical policies and procedures that allow only authorized persons to access ePHI. These safeguards protect ePHI in both storage (data at rest) and transmission (data in transit) through technology-based security controls.
Technical safeguards address the digital dimension of security—the systems, networks, databases, and applications where ePHI resides and moves throughout healthcare operations.
Key Technical Safeguards (Implementation Specifications)
Access controls implement technical policies and procedures that allow only authorized persons to access ePHI. Organizations assign unique user identifiers, implement role-based access permissions that limit users to only the data necessary for their functions, and enforce the principle of least privilege. Access control systems prevent unauthorized users from viewing, modifying, or extracting ePHI.
Audit controls implement hardware, software, and procedural mechanisms to record and examine access in information systems that contain or use ePHI. These logging mechanisms capture who accessed what data, when access occurred, what actions were performed, and from which systems. Organizations review audit logs to identify suspicious activity, investigate potential breaches, and maintain accountability.
Integrity controls implement policies and procedures to ensure that ePHI has not been, and will not be, improperly altered or destroyed. Checksums, version controls, digital signatures, and validation mechanisms detect unauthorized modifications to patient records or system data.
Authentication and authorization mechanisms verify user identity before granting system access. Multi-factor authentication (MFA) combines something the user knows (password), something they possess (security token or smartphone), and potentially something they are (biometric identifier) to prevent unauthorized access even when credentials are compromised.
Transmission security implements technical security measures that guard against unauthorized access to ePHI that is transmitted over an electronic network. Organizations encrypt ePHI when transmitted across networks—particularly open or unsecured networks including the internet—and implement secure communication channels, VPNs, and secure protocols.
Automatic log-off and session management prevent unauthorized access when users leave workstations without manually logging out. Systems terminate sessions after defined inactivity periods, requiring reauthentication before resuming access.
Why Technical Safeguards Are Critical
Technical safeguards protect ePHI in digital format—which constitutes the vast majority of healthcare data today. Electronic health records, billing systems, lab information systems, radiology archives, telehealth platforms, and patient portals all require technical protections.
These safeguards defend against cyber threats including unauthorized access attempts, data exfiltration, ransomware attacks, data tampering, and interception during transmission. In January 2025, HHS proposed major updates to the HIPAA Security Rule—the first substantive overhaul in over a decade—to address growing cybersecurity threats targeting healthcare, driven by a sharp rise in cyberattacks and data breaches exposing gaps in outdated systems and inconsistent security practices.
Audit trails provide essential compliance documentation, enabling organizations to demonstrate who accessed ePHI, detect suspicious patterns, investigate potential breaches, and maintain workforce accountability. During regulatory investigations, comprehensive audit logs distinguish organizations that maintained proper oversight from those operating without visibility into system access.
The Security Rule doesn't specify the exact kind of technology organizations must use to stay compliant—instead, measures must meet the challenges of security as they exist at the time of implementation. This flexibility allows organizations to select tools and technologies appropriate for their size, budget, and risk tolerance while meeting the "reasonable and appropriate" standard.
How the Three Safeguards Work Together — Creating a Layered Defense
No single safeguard category provides sufficient protection when implemented in isolation. Administrative safeguards establish policies and governance but cannot prevent physical theft or digital attacks. Physical safeguards secure facilities and devices but cannot protect data transmitted across networks. Technical safeguards implement encryption and access controls but fail without workforce training and policy enforcement.
Consider a hospital implementing layered defenses: Administrative safeguards establish data access policies, designate a security officer, conduct risk assessments, train staff on security protocols, and define breach response procedures. Physical safeguards restrict server room access through badge readers, position workstations away from public view, implement surveillance systems, and securely dispose of decommissioned hardware. Technical safeguards encrypt the EHR database, require multi-factor authentication for system access, log all data access for audit review, and encrypt transmissions to business associates.
Together, these safeguards minimize risk from insider threats (workforce members exceeding authorization), external attackers (attempting network intrusion or physical theft), accidental exposures (lost devices or misdirected communications), and environmental hazards (disasters affecting data availability).
Organizations must tailor safeguard implementation to their specific circumstances—size, resources, risk profile, data volume, workflow complexity, and technical infrastructure. A solo practitioner implements different measures than a regional health system, but both must demonstrate systematic risk assessment and deployment of reasonable and appropriate controls across all three safeguard categories.
HIPAA compliance functions as an ongoing process rather than a one-time project. Risk assessments identify new vulnerabilities as systems change. Audits verify controls remain effective. Updates address emerging threats. Training reinforces proper protocols as workforce composition evolves. Organizations treating safeguards as static checklists rather than continuous operational disciplines inevitably face compliance gaps.
Practical Tips for Healthcare Companies Implementing HIPAA Safeguards
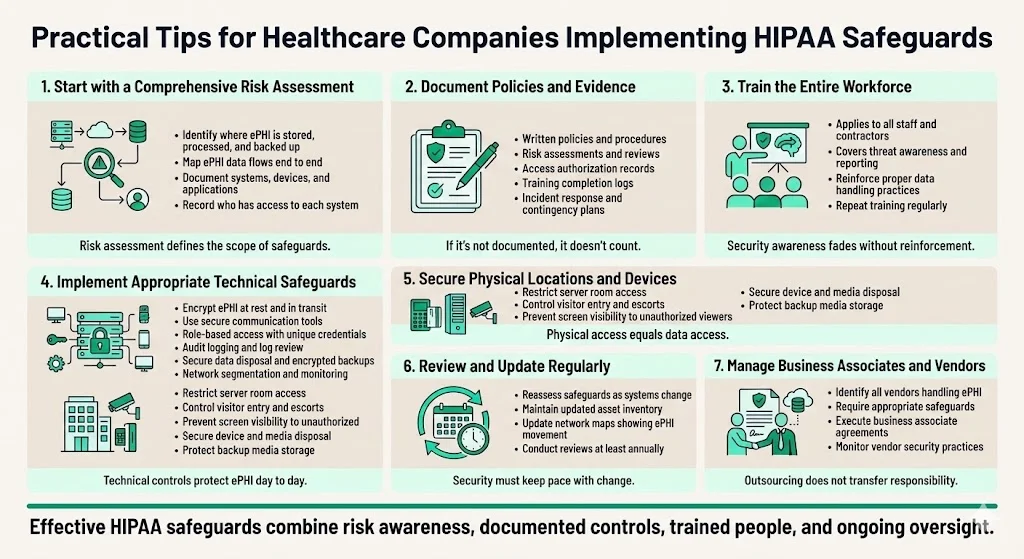
Begin with a comprehensive risk assessment. Document where ePHI resides across systems, applications, databases, devices, and backup media. Map how ePHI flows through your organization—from creation or receipt, through use and storage, to eventual disposal. Identify who has access to each system and data repository. This assessment defines the scope of required safeguards and reveals existing vulnerabilities requiring remediation.
Document everything. Policies, procedures, access authorization lists, risk assessments, audit reviews, training completion records, contingency plans, and incident response documentation all provide evidence of compliance during regulatory audits. Organizations unable to produce documentation demonstrating their security management process face significant compliance risk regardless of actual security posture.
Train the workforce regularly. All personnel—clinical staff, administrative employees, facilities teams, IT departments, contractors, and temporary workers—must understand their data protection responsibilities, recognize security threats, follow proper protocols, and know how to report suspected breaches. Security awareness degrades over time without reinforcement through periodic training.
Select appropriate technical solutions. Implement encryption for data at rest and in transit. Deploy secure communication platforms for ePHI exchange. Assign unique credentials with role-based access controls. Enable comprehensive audit logging and review logs for suspicious activity. Secure data disposal processes that render ePHI unrecoverable. Maintain encrypted backups stored in geographically separate locations. Implement network segmentation, firewalls, and intrusion detection systems appropriate to your risk profile.
Secure physical premises. Restrict server room and data center access to authorized personnel only. Control visitor entry through sign-in procedures and escort requirements. Position workstations to prevent unauthorized viewing. Manage hardware disposal carefully through certified destruction vendors. Implement surveillance appropriate to facility risk. Store backup media in secured, climate-controlled environments.
Review and update periodically. As systems change, staff rotate, technology evolves, threats emerge, and regulations update, reassess your safeguards. The proposed HIPAA Security Rule updates require development and revision of a technology asset inventory and network map illustrating the movement of ePHI throughout the regulated entity's electronic information systems on an ongoing basis, but at least every 12 months. Organizations conducting annual risk assessments identify and address vulnerabilities before they result in breaches.
Address business associates and third-party vendors. Any entity that handles ePHI on your behalf must implement equivalent safeguards and provide satisfactory assurances through business associate agreements. Vendor security failures create covered entity liability—organizations remain accountable for proper safeguards even when ePHI is processed by contractors, cloud service providers, billing companies, or other business associates.
Conclusion
HIPAA's Security Rule sets forth administrative, physical, and technical safeguards that covered entities and business associates must put in place to secure individuals' electronic protected health information. These three safeguard categories form the regulatory framework for protecting patient data in healthcare organizations of all sizes and types.
Implementing all three safeguard types—tailored to your organization's specific risk environment, resources, and operational needs—meets legal requirements while reducing exposure to data breaches, unauthorized access, and regulatory penalties. Organizations approaching safeguards as compliance theater rather than genuine security infrastructure create the appearance of protection without substance. This approach satisfies cursory reviews while leaving systems fundamentally vulnerable.
Treat safeguard implementation as an ongoing operational discipline rather than a one-time checklist exercise. Risk evolves continuously. Technologies change. Threats become more sophisticated. Workforce composition shifts. Organizations maintaining continuous assessment, monitoring, training, and improvement cycles build resilient security postures that protect patient data and organizational interests simultaneously.
FAQs
1) What are the three types of safeguards for HIPAA?
The three types of safeguards required by the HIPAA Security Rule are administrative safeguards, physical safeguards, and technical safeguards. Administrative safeguards establish policies, procedures, and workforce management processes. Physical safeguards protect facilities, devices, and media. Technical safeguards secure data through access controls, encryption, and system monitoring.
2) What are the three major safeguards?
The three major safeguards under the HIPAA Security Rule are administrative, physical, and technical safeguards. These categories represent the primary security controls healthcare organizations must implement to protect electronic protected health information throughout its lifecycle.
3) What is the "standard 3" of HIPAA?
The "standard 3" typically refers to the three required safeguard categories under the HIPAA Security Rule: administrative safeguards, physical safeguards, and technical safeguards. These standards form the foundation of compliance requirements for protecting electronic protected health information.
4) What are the three safeguards to data privacy?
Under HIPAA regulations governing electronic protected health information, the three safeguards to data privacy are administrative safeguards (policies and procedures), physical safeguards (facility and device protections), and technical safeguards (technology-based security controls). These safeguards work together to ensure the confidentiality, integrity, and availability of patient data.



.svg)
.svg)
.svg)