Most organizations allocate substantial resources to risk management without understanding the difference between risk-based decision making and risk theater. This gap becomes apparent when security incidents expose fundamental weaknesses that passed audit scrutiny—vulnerabilities that existed not because controls were absent, but because risk was never properly assessed in the first place.
NIST Special Publication 800-30 provides guidance for conducting risk assessments of federal information systems and organizations, establishing a structured methodology that connects threat identification, vulnerability analysis, and impact determination to actual control selection and implementation. For enterprise vendors and their clients, SP 800-30 offers more than compliance documentation—it provides the analytical framework needed to align security investments with business risk, demonstrate mature risk management processes to stakeholders, and structure security offerings around clearly scoped threats rather than generic checklists.
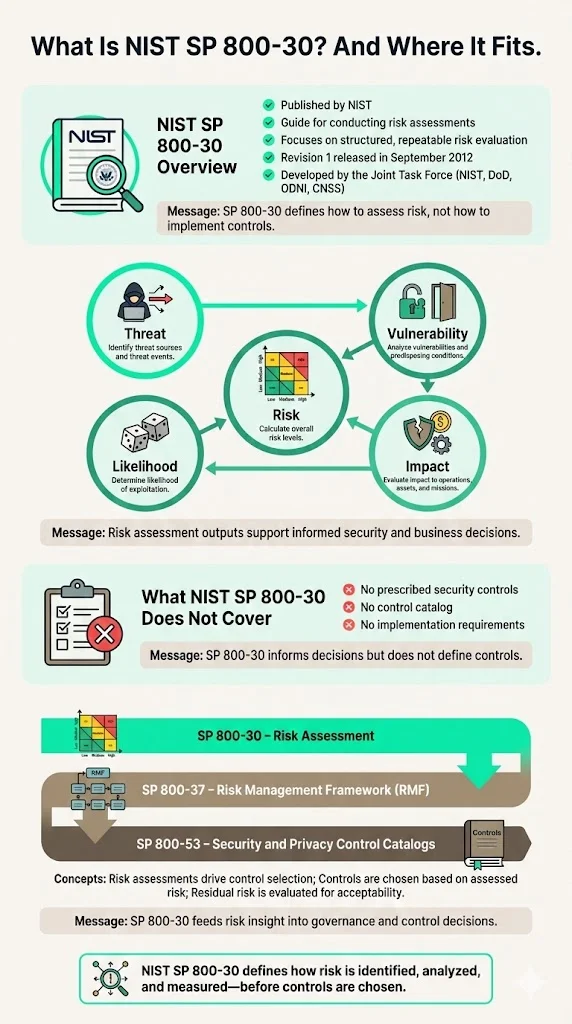
What is NIST SP 800-30? (and where it fits)
The National Institute of Standards and Technology (NIST) published Special Publication 800-30, Revision 1, Guide for Conducting Risk Assessments as the authoritative methodology for systematic risk evaluation. The original SP 800-30 was released in July 2002 as broader risk management guidance. The update to Special Publication 800-30 focuses exclusively on risk assessments, one of the four steps in the risk management process, with Revision 1 published in September 2012 after eighteen months of development by the Joint Task Force—a partnership among NIST, the Department of Defense, the Office of the Director of National Intelligence, and the Committee on National Security Systems.
What SP 800-30 covers vs what it doesn't
SP 800-30 addresses the risk assessment component of risk management: identifying threat sources and events, analyzing vulnerabilities and predisposing conditions, determining likelihood of exploitation, evaluating potential impact to operations and assets, and calculating risk levels to inform control selection. The purpose of the risk assessment component is to identify threats to organizations, vulnerabilities internal and external to organizations, impact to organizations that may occur given the potential for threats exploiting vulnerabilities, and likelihood that harm will occur.
The guide does not prescribe specific security controls or define control catalogs. Instead, risk assessment outputs drive decisions about which controls are necessary, how controls should be prioritized, and whether residual risk after control implementation remains acceptable. SP 800-30 functions within a broader ecosystem of NIST publications—risk assessments per SP 800-30 feed into the Risk Management Framework defined in SP 800-37, which then references control catalogs like SP 800-53 for actual control selection and implementation specifications.
Why enterprise-focused vendors/clients should care
For vendors selling to enterprise clients and organizations managing complex security relationships, SP 800-30 provides three distinct advantages. First, it establishes a standard, widely recognized methodology that satisfies audit and compliance requirements across industries—particularly valuable when clients demand documented risk management processes as part of vendor due diligence. Second, it enables vendors to demonstrate mature risk-based security practices rather than reactive control implementation, positioning security discussions in business terms that resonate with executive stakeholders. Third, by structuring security offerings around assessed risks rather than generic frameworks, vendors can tailor control implementations to actual threat landscapes, improving both cost-effectiveness and security outcomes.
Core Concepts — Risk Assessment, Threats, Vulnerabilities, Impact, Residual Risk
Understanding SP 800-30 requires precision about how the methodology defines and operationalizes fundamental risk concepts.
1) Risk Assessment & Risk Management Process
Risk assessment is the systematic process of identifying and evaluating risks to information systems, organizational operations, and assets. Risk assessments, carried out at all three tiers in the risk management hierarchy, are part of an overall risk management process—providing senior leaders/executives with the information needed to determine appropriate courses of action in response to identified risks. Risk assessment produces the intelligence required for informed decision making about control selection, risk acceptance, risk mitigation strategies, or risk transfer mechanisms—but assessment itself is one component within the larger risk management lifecycle that includes risk framing, risk response, and continuous risk monitoring.
2) Threat Identification & Hazard Identification
Threat identification enumerates potential threat sources (adversarial, accidental, structural, environmental) and specific threat events that could adversely affect systems or operations. In SP 800-30 terminology, threats directed through organizations, insider threats, advanced persistent threats, supply chain compromises, and natural hazards all constitute threat sources requiring identification. The methodology requires assessing both the capability and intent of adversarial threat sources, alongside the likelihood of non-adversarial events—creating a comprehensive threat landscape against which vulnerabilities and controls can be evaluated.
3) Vulnerability Analysis (Vulnerability Identification)
Vulnerability analysis identifies weaknesses in system design, configuration, implementation, or operation that could be exploited by threat sources. This extends beyond technical vulnerabilities cataloged in CVE databases to encompass procedural weaknesses, architectural deficiencies, gaps in administrative controls, and predisposing conditions that increase susceptibility to threats. SP 800-30 treats vulnerability identification as context-dependent—the same system characteristic may constitute a vulnerability relative to one threat but not another, requiring analysis of vulnerability-threat pairings rather than abstract vulnerability lists.
4) Impact Analysis (and Likelihood Determination)
Impact analysis estimates potential adverse consequences if a threat successfully exploits a vulnerability. Consequences are evaluated across multiple dimensions: impact to mission-critical operations, compromise of confidentiality/integrity/availability, financial loss, reputational damage, legal/regulatory violations, and harm to individuals or other organizations. SP 800-30 expresses risk as a function combining likelihood and impact—requiring both dimensions for meaningful risk determination.
Likelihood determination assesses the probability that a threat event will occur and successfully exploit identified vulnerabilities under existing conditions. For adversarial threats, likelihood considers threat capability, intent, and targeting combined with vulnerability severity and the presence (or absence) of existing controls. For non-adversarial threats, likelihood depends on historical frequency, environmental factors, and predisposing conditions.
5) Residual Risk & Security Posture
Residual risk represents the risk remaining after security controls are implemented—the risk level an organization must accept, further mitigate, or transfer. Calculating residual risk requires evaluating control effectiveness: how much does a given control reduce likelihood, mitigate impact, or both? SP 800-30 emphasizes that risk determination is iterative—initial risk assessment identifies inherent risk absent controls, subsequent analysis determines residual risk with planned or existing controls, and ongoing assessment tracks whether residual risk remains within organizational risk tolerance as threats, vulnerabilities, and environments evolve.
Security posture reflects an organization's overall readiness and resilience considering implemented controls, residual risk levels, continuous monitoring capabilities, and incident response preparedness. A mature security posture results from systematic risk assessment informing control selection, not from control proliferation disconnected from assessed threats.
The SP 800-30 Risk Assessment Methodology — Step-by-Step
This document provides guidance for carrying out each of the three steps in the risk assessment process (prepare for the assessment, conduct the assessment, and maintain the assessment), establishing a repeatable methodology applicable across organizational contexts.
The Four-Phase Risk Assessment Lifecycle
SP 800-30 structures risk assessment as an ongoing process rather than a one-time project:
1) Prepare for Assessment — Establish context, purpose, scope, assumptions, constraints, risk model, and analytical approach. Identify information sources, assessment team composition, and communications strategy.
2) Conduct Assessment — Execute the systematic analysis of threats, vulnerabilities, likelihood, impact, and risk determination. Evaluate existing and planned controls. Calculate residual risk.
3) Communicate Results — Document findings, risk levels, and recommendations. Tailor communications for different stakeholder audiences—executives require business-context risk information while technical teams need detailed vulnerability and control specifications.
4) Maintain Assessment — Monitor for changes in threat landscape, system configurations, organizational context, or mission/business processes that invalidate prior risk determinations. Conduct periodic reassessments and continuous monitoring.
Detailed Steps: From System Characterization to Risk Determination
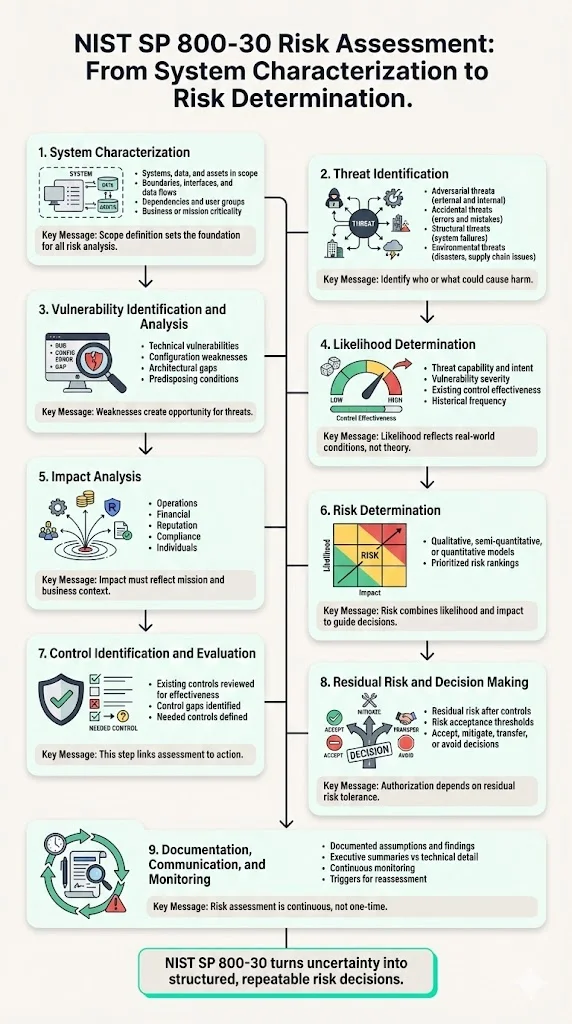
- System Characterization — Define and document what systems, data, assets, processes, and organizational functions fall within assessment scope. Document system boundaries, interfaces, data flows, dependencies, users, and criticality to mission/business operations. System characterization establishes the context for all subsequent threat, vulnerability, and impact analysis.
- Threat Identification — Enumerate potential threat sources relevant to the system: adversarial (nation-states, organized crime, hacktivists, malicious insiders), accidental (user errors, administrator mistakes), structural (hardware failures, software defects), and environmental (natural disasters, infrastructure failures, supply chain disruptions). Document specific threat events that each source might initiate.
- Vulnerability Identification / Analysis — Identify weaknesses that could be exploited by identified threats. Sources include vulnerability scanning, penetration testing, code review, configuration assessments, security control audits, architecture reviews, and threat modeling. Document predisposing conditions—organizational factors that increase susceptibility to exploitation.
- Likelihood Determination — Estimate probability of threat exploitation of vulnerabilities under current conditions. For adversarial threats, assess threat capability (resources, expertise, access), intent (motivation, targeting), and vulnerability severity. For non-adversarial threats, evaluate historical frequency and contributing factors. Existing security controls reduce likelihood—require assessment of control effectiveness.
- Impact (Consequence) Analysis — Assess potential consequences if exploitation occurs. Evaluate impact across relevant dimensions: operational impact (disruption to mission-critical functions), financial impact (direct costs, lost revenue, regulatory penalties), reputational impact (loss of stakeholder trust), compliance impact (regulatory violations, contractual breaches), and impact to individuals (privacy breaches, safety risks). Impact determination should be context-specific and mission-focused.
- Risk Determination / Risk Model Application — Combine likelihood and impact assessments to characterize risk levels. SP 800-30 supports qualitative (high/medium/low), semi-quantitative (numerical scales), or quantitative (probabilistic) risk models depending on organizational needs and available data. Risk determination produces prioritized risk rankings to inform decision making.
- Identify & Analyze Controls (Security Control Evaluation) — Identify potential security controls to mitigate risks. Evaluate existing controls for effectiveness—are they implemented correctly, operating as intended, producing desired outcomes? Conduct gap analysis between current controls and controls needed to reduce risk to acceptable levels. This step bridges risk assessment to risk response planning.
- Residual Risk & Decision Making — Determine residual risk after planned or existing controls are applied. Compare residual risk to organizational risk tolerance thresholds. Decide whether to accept residual risk, implement additional controls, transfer risk (insurance, contractual terms), or avoid risk (discontinue risky activities). Authorization decisions—whether to operate a system—depend on residual risk acceptability.
- Documentation & Communication — Document all assessment inputs, methods, findings, assumptions, and recommendations. Tailor communications for different audiences: executives require business-context risk summaries, technical teams need detailed vulnerability and remediation guidance, auditors require evidence of systematic methodology. Documentation supports traceability, accountability, and future reassessments.
- Ongoing Monitoring & Periodic Review — Risk assessment is not static. Implement continuous monitoring to detect changes that invalidate prior assessments: new vulnerabilities, emerging threats, system modifications, changes to mission/business processes. Establish triggers for reassessment and schedules for periodic comprehensive reviews.
Tiered Assessments: From Enterprise to System Level
NIST Special Publication 800-39 provides guidance on the three tiers in the risk management hierarchy including Tier 1 (organization), Tier 2 (mission/business process), and Tier 3 (information system). Risk assessments can be conducted at any tier depending on purpose and scope. Tier 1 assessments address enterprise-wide strategic risks affecting organizational governance, reputation, and mission success. Tier 2 assessments evaluate risks to specific business processes or operational functions. Tier 3 assessments focus on technical risks to specific information systems or system components.
For enterprise vendors, tiered assessment enables alignment between technical system-level risks (Tier 3) that engineers understand and business-level risks (Tier 1) that executives and clients prioritize. Effective risk communication requires translating technical findings into business impact—demonstrating how a SQL injection vulnerability (Tier 3 technical risk) creates risk of customer data breach (Tier 2 process risk) that threatens regulatory compliance and market reputation (Tier 1 organizational risk).
Role in Compliance, Governance, and Security Posture
Compliance and Audit Readiness
SP 800-30 provides a structured, documented methodology that demonstrates mature risk management practices to auditors, regulators, and enterprise clients conducting security due diligence. Because the framework is publicly available, vendor-neutral, and widely adopted across industries and international markets, implementing risk assessments per SP 800-30 establishes credible evidence of systematic security practices. For organizations in regulated sectors—healthcare, financial services, critical infrastructure—documented risk assessments are increasingly required to demonstrate compliance with regulations mandating risk-based security programs.
Audit readiness extends beyond documenting that risk assessments occurred. Auditors evaluate whether assessments used appropriate scope, identified relevant threats, analyzed vulnerabilities systematically, determined likelihood and impact with reasonable rigor, and produced risk determinations that logically justified control selection and residual risk acceptance decisions. SP 800-30's detailed methodology provides the structure needed to withstand audit scrutiny.
Informing Control Selection & Security Controls Evaluation
Random control implementation creates two problems: over-investment in controls that don't address actual risks, and under-investment in controls that mitigate significant threats. Risk assessment outputs from SP 800-30 enable rational control selection—implementing controls where they reduce likelihood or impact of assessed risks, avoiding control proliferation where risk is inherently low.
This approach improves both security effectiveness and cost-efficiency. Vendors can tailor security offerings to client-specific threat landscapes rather than selling generic control packages. Clients can evaluate vendor security controls against their own risk assessments, verifying that vendor controls address threats that matter to their operations rather than accepting vendor-defined security theater.
Aligning Security Posture with Business Context
Through impact analysis tied to specific mission functions and business operations, SP 800-30 enables risk prioritization based on what matters to organizational success. Not all risks warrant equal investment—risk to systems supporting revenue-generating operations may justify more aggressive control implementation than risk to non-critical internal systems, even if technical vulnerability severity is identical.
The methodology provides a common language for risk communication across organizational boundaries. Likelihood and impact expressed in business terms—probability of operational disruption, magnitude of financial loss, regulatory violation likelihood—enable productive conversations between technical security teams, business executives, legal/compliance departments, and external stakeholders. For vendors, this common language transforms security discussions with enterprise clients from technical debates about control implementation to business conversations about risk tolerance and acceptable residual risk.
Supporting Incident Response Planning and Risk Management Strategy
By identifying threats, vulnerabilities, and potential impacts before incidents occur, risk assessments enable proactive incident response planning. Organizations know which incident scenarios to prepare for, which response capabilities to develop, which external resources (forensics, legal counsel, public relations) to pre-position. Risk assessment outputs inform business continuity planning, disaster recovery priorities, and cyber insurance requirements.
Risk assessments also drive strategic decisions about risk acceptance, mitigation, transfer, or avoidance. Some risks warrant control investment to reduce likelihood or impact. Other risks may be accepted if residual risk falls within tolerance and control costs exceed potential losses. Still other risks may be transferred through insurance, contractual indemnification, or outsourcing to specialized providers. These strategic choices require the analytical foundation that SP 800-30 provides.
Where SP 800-30 Fits in the Larger NIST Ecosystem
Relationship with NIST SP 800-37 and the Risk Management Framework (RMF)
SP 800-37 defines the Risk Management Framework—a structured process for integrating security and risk management into system development lifecycles, authorization decisions, and continuous monitoring. The RMF encompasses six steps: categorization (determining system criticality), control selection (choosing appropriate controls), control implementation (deploying controls), control assessment (verifying effectiveness), system authorization (accepting risk and authorizing operation), and continuous monitoring (ongoing security oversight).
Risk assessment per SP 800-30 feeds multiple RMF steps. Initial categorization relies on preliminary risk assessment to determine system criticality. Control selection requires risk assessment outputs to identify which threats require mitigation. Control assessment evaluates whether implemented controls reduce risk as intended. Authorization decisions depend on residual risk determination. Continuous monitoring detects changes requiring reassessment. Using SP 800-30 within the RMF ensures risk assessments drive authorization decisions rather than existing as disconnected compliance artifacts.
Complementarity with Security Controls Catalog (e.g. NIST SP 800-53)
SP 800-53 provides a comprehensive catalog of security and privacy controls spanning access control, incident response, system monitoring, configuration management, supply chain risk management, and more. Once risk assessment identifies threats requiring mitigation, organizations select applicable controls from catalogs like SP 800-53 rather than designing custom controls from scratch.
This separation between risk assessment (SP 800-30) and control specification (SP 800-53) creates analytical discipline. Risk assessment determines what risks exist and what risk reduction is needed. Control selection matches standardized controls to assess risks. Control effectiveness evaluation verifies whether selected controls achieve intended risk reduction. This sequence prevents the common dysfunction of implementing controls because frameworks require them without understanding what risks those controls mitigate.
Flexibility — Use by Different Types of Organizations (Not just US Federal)
The risk assessment guidance has been designed to have maximum flexibility so the process can meet the needs of many types of organizations and communities of interest, large and small, including financial institutions, healthcare providers, software developers, manufacturing organizations, and law enforcement. Though developed for US federal agencies, SP 800-30 is vendor-neutral, technology-agnostic, and adaptable to diverse organizational contexts and regulatory requirements.
For enterprises operating globally, SP 800-30 offers a credible baseline that satisfies risk assessment requirements across multiple compliance frameworks. Organizations can conduct risk assessments per SP 800-30 and map results to ISO 27001 risk treatment requirements, GDPR data protection impact assessments, HIPAA security risk analysis mandates, or industry-specific regulations—reducing assessment duplication while maintaining rigorous methodology.
Practical Considerations & Challenges for Implementation
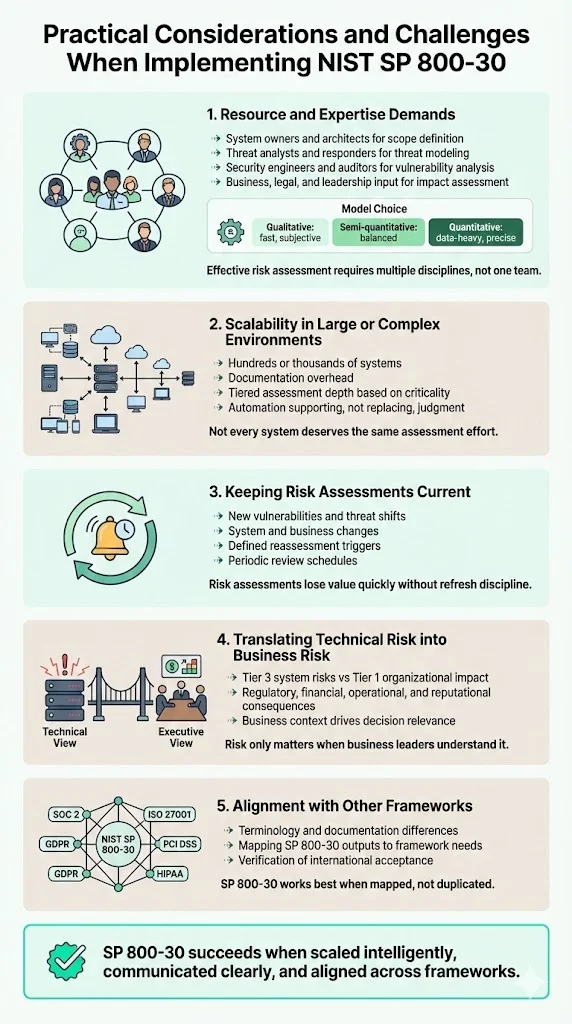
1) Resource & Expertise Requirements
Effective risk assessment requires multidisciplinary expertise. System characterization needs input from system owners, architects, and operations teams who understand system functionality, data flows, and dependencies. Threat identification benefits from threat intelligence analysts, security researchers, and incident response teams familiar with current attack techniques and adversary capabilities. Vulnerability analysis requires security engineers, penetration testers, and auditors who can identify technical and procedural weaknesses. Impact analysis demands engagement with business process owners, legal/compliance staff, and executives who understand operational criticality and business consequences.
Organizations choosing between qualitative and quantitative risk models face trade-offs. Qualitative assessments (high/medium/low risk ratings) require less data and specialized expertise but produce subjective results vulnerable to inconsistency across assessors. Quantitative assessments (probabilistic loss calculations) demand historical incident data, actuarial expertise, and significant analytical resources but generate objective, comparable risk metrics. Semi-quantitative approaches using numerical rating scales offer middle ground—more rigor than purely qualitative methods without full quantitative data requirements.
2) Scalability Risks for Large / Complex Enterprise Environments
Large organizations managing hundreds or thousands of information systems face significant scalability challenges. Conducting comprehensive SP 800-30 assessments for every system consumes substantial time and specialized resources. Risk assessment documentation, if approached bureaucratically, can generate massive artifacts requiring ongoing maintenance as systems and threats evolve.
Successful enterprise implementation requires strategic scoping. Not every system warrants the same assessment depth—high-criticality systems supporting mission-essential functions or processing sensitive data justify more rigorous assessment than low-impact administrative systems. Organizations can tier assessment rigor based on system categorization, conducting detailed assessments for high-impact systems while using streamlined approaches for lower-risk systems. Automation tools supporting vulnerability scanning, threat intelligence integration, and risk calculation workflows reduce manual effort, though they cannot replace human judgment about likelihood, impact, and control effectiveness.
Maintaining assessment currency presents ongoing challenges. As threat landscapes shift, new vulnerabilities emerge, systems are modified, and business processes change, prior risk assessments become obsolete. Organizations need defined triggers for reassessment—major system changes, significant security incidents, regulatory changes, periodic review schedules—balanced against resource constraints preventing continuous comprehensive reassessment.
3) Translating Technical Risk into Business Risk — Bridging the Tier Gap
Technical security teams naturally focus on Tier 3 system-level risks: specific vulnerabilities, attack techniques, technical control deficiencies. Business executives and enterprise clients care about Tier 1 organizational risks: regulatory violations, operational disruptions, financial losses, reputational damage. Effective risk communication requires translating technical findings into business consequences.
This translation demands understanding business context—which operations depend on which systems, what data sensitivity means for regulatory compliance, how operational disruptions cascade into financial impact, what reputational consequences follow from different types of breaches. For vendors, this means engaging with client business stakeholders to understand their priorities rather than assuming technical security metrics speak for themselves.
4) Integration with Other Frameworks and Standards
Organizations rarely implement SP 800-30 in isolation. Most enterprises must satisfy multiple compliance frameworks simultaneously: SOC 2 trust services criteria, ISO 27001 risk assessment requirements, PCI DSS risk analysis mandates, GDPR data protection impact assessments, HIPAA security risk analysis obligations. Each framework has specific risk assessment requirements, terminology, and documentation expectations.
Mapping SP 800-30 methodology to other frameworks requires careful alignment. ISO 27001 defines risk assessment, risk treatment, and risk acceptance processes that align conceptually with SP 800-30 but use different terminology and documentation structures. SOC 2 requires evidence of risk assessment processes informing control selection but doesn't mandate specific methodology. HIPAA requires security risk analysis addressing specific regulatory requirements—physical safeguards, technical safeguards, administrative safeguards—that must be mapped to general-purpose SP 800-30 threat and vulnerability categories.
For global enterprises and vendors serving international clients, the question becomes whether NIST-based risk assessments satisfy non-US regulatory requirements. Most regulators accept SP 800-30 methodology if assessments address framework-specific risks and documentation meets regulatory expectations—but organizations should verify regulatory acceptance rather than assuming US federal guidance automatically satisfies international requirements.
What "Role in Compliance and Security" Means for Enterprise Vendors
For vendors selling to enterprise clients—particularly in healthcare, finance, government, and other regulated sectors—implementing risk assessments per SP 800-30 creates several strategic advantages. First, it demonstrates security maturity to clients conducting vendor security due diligence. Enterprise procurement teams increasingly require evidence of structured risk management processes, not just compliance certifications. Documented risk assessments show systematic security practices that align with how sophisticated clients evaluate their own risks.
Second, risk-based security enables vendors to tailor offerings to client-specific threats rather than selling generic control packages. When vendors can articulate "we assessed these threat scenarios relevant to your industry, identified these vulnerabilities in our architecture, implemented these controls to reduce likelihood and impact, and residual risk levels are X"—that conversation is far more credible than "we comply with SOC 2" or "we implement industry best practices." Clients understand what risks the vendor has addressed and what residual risks they're accepting.
Third, structured risk assessment supports audit readiness and compliance validation. When enterprise clients audit vendor security, documented risk assessments provide the analytical foundation demonstrating why specific controls were selected, how effectiveness is evaluated, and how residual risk is monitored. This transforms vendor audits from checkbox exercises into substantive security dialogues.
Fourth, ongoing risk assessment enables continuous security improvement rather than point-in-time compliance. Vendors can demonstrate to clients that security isn't static—new threats are monitored, vulnerability assessments are repeated, risk determinations are updated, controls are adapted as environments change. This positions the vendor-client relationship as an ongoing security partnership rather than a one-time certification event.
Finally, common risk language facilitates vendor-client security discussions. When both parties use consistent terminology—threat sources, likelihood, impact, residual risk—conversations become more productive. Disagreements about security requirements can be resolved through shared risk assessment rather than positional debates. Clients can articulate risk tolerance thresholds, vendors can demonstrate how their controls meet those thresholds, and both parties can make informed decisions about acceptable risk levels.
Conclusion
SP 800-30 provides the analytical foundation for risk-based security—moving organizations beyond compliance theater toward security practices grounded in actual threat landscapes, vulnerabilities, and business consequences. For companies targeting enterprise clients, adopting or aligning with SP 800-30 methodology elevates security posture from reactive control implementation to strategic risk management.
The methodology's value lies not in generating assessment documentation but in producing actionable intelligence that drives control selection, informs authorization decisions, supports incident response planning, and enables continuous security improvement. Organizations that treat risk assessment as an ongoing analytical process embedded in system lifecycles and vendor relationships—rather than periodic compliance exercises—develop the security resilience that matters when threats materialize.
For enterprise vendors, this means structured risk assessment becomes a competitive differentiator. Vendors demonstrating mature risk management processes build trust with sophisticated clients, enable more substantive security discussions, support efficient audit processes, and position long-term relationships around continuous security partnership rather than transactional compliance.
FAQs
1) What is the difference between NIST 800-30 and 800-37?
SP 800-30 provides detailed methodology for conducting risk assessments—identifying threats, analyzing vulnerabilities, determining likelihood and impact, calculating risk levels, and evaluating residual risk after controls. SP 800-37 defines the broader Risk Management Framework (RMF)—a lifecycle process encompassing system categorization, control selection, control implementation, control assessment, system authorization, and continuous monitoring. Risk assessment per SP 800-30 feeds into RMF steps, particularly control selection and authorization decisions. SP 800-30 addresses the "assess risk" component; SP 800-37 addresses the entire risk management lifecycle.
2) What are the steps in the NIST SP 800-30 risk management (risk assessment) process?
The SP 800-30 risk assessment process encompasses three major phases: Prepare for assessment—establish scope, context, risk model, analytical approach, team composition, and information sources. Conduct assessment—execute system characterization, threat identification, vulnerability identification and analysis, likelihood determination, impact analysis, risk determination, control identification and evaluation, and residual risk calculation. Communicate results—document findings and risk levels, tailor communications for different stakeholder audiences, provide recommendations for risk response. Maintain assessment—implement ongoing monitoring to detect changes invalidating prior assessments, conduct periodic reassessments, update risk determinations as threats, vulnerabilities, systems, or missions evolve.
3) What is the NIST SP 800 framework?
"NIST SP 800" refers to the Special Publication 800-series—a collection of guidance documents published by NIST covering information security, risk management, privacy, and cybersecurity. The series includes dozens of publications addressing different aspects of security and risk management. SP 800-30 specifically addresses risk assessment methodology. SP 800-37 defines the Risk Management Framework. SP 800-53 provides a comprehensive security and privacy controls catalog. SP 800-39 addresses enterprise risk management. Other publications cover incident handling, contingency planning, cryptography, access control, and specialized security topics. The series functions as an integrated ecosystem—publications reference and complement each other to support comprehensive security programs.
4) What are the 4 types of risk assessments?
While SP 800-30 doesn't rigidly define "4 types," risk assessments are commonly characterized along two dimensions. By organizational tier: Tier 1 (enterprise/organizational level) assesses strategic risks to mission, reputation, and governance; Tier 2 (mission/business process level) evaluates risks to specific operational functions or business processes; Tier 3 (information system level) examines technical risks to specific systems or applications. By analytical approach: qualitative assessments use descriptive categories (high/medium/low risk); semi-quantitative assessments apply numerical rating scales; quantitative assessments calculate probabilistic risk metrics using historical data and loss models; hybrid approaches combine qualitative and quantitative methods depending on available data and assessment objectives. Assessment type selection depends on organizational needs, resource availability, data quality, and decision-making requirements.



.svg)
.svg)
.svg)