Most organizations treat access controls as a security checkbox rather than an operational foundation. This creates a fundamental gap between policy documentation and actual enforcement—a gap that becomes apparent when auditors demand evidence of who accessed what, when incidents occur, or when regulatory scrutiny intensifies. In 2026, regulators expect provable control over access, not policy statements about intent.
The shift from perimeter-based security to identity-driven access management reflects a basic reality: enterprise environments now operate across distributed cloud infrastructure, SaaS applications, remote workforces, and third-party integrations. Traditional perimeter defenses no longer contain the attack surface. Access controls now determine whether unauthorized users can reach sensitive data, whether compromised credentials can escalate to administrative privileges, and whether security incidents remain contained or cascade across systems.
What Access Controls Mean in a Modern Enterprise Context
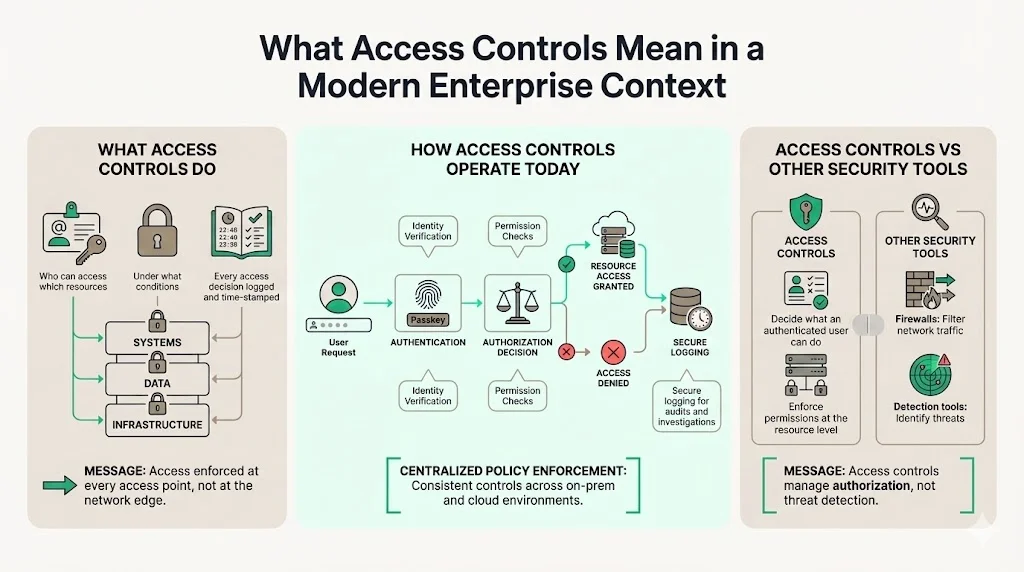
Access controls are rules that govern who can access what resources and under which conditions—every access request and decision must be logged, time-stamped, and stored securely for incident investigations, compliance reporting, and auditing. These controls operate across systems, data, and infrastructure, enforcing authorization decisions at every access point rather than relying on network boundaries.
Access controls differ from broader security tooling in their fundamental purpose: they manage identity verification and permission enforcement, not threat detection or incident response. A firewall blocks network traffic based on IP addresses and ports. Access controls determine whether an authenticated user with valid credentials can read a database record, modify a configuration file, or access a cloud storage bucket.
Key Components That Make Access Controls Work
Authentication verifies identity before granting access. This includes password verification, multi-factor authentication, biometric validation, or certificate-based authentication tied to identity management systems.
Authorization determines what an authenticated user can do. After verifying identity, the system evaluates permissions against defined policies—whether a user can view, edit, delete, or execute specific resources.
Privilege levels establish graduated access rights across user populations. Standard users access resources required for their job function. Privileged users hold administrative rights that allow system configuration changes, security setting modifications, or access to sensitive data repositories.
Identity management systems tie these components together, maintaining centralized records of user identities, assigned roles, permission mappings, and access histories across disparate systems.
Access Controls as a Compliance Requirement, Not Just a Security Feature
How Regulations Treat Access Controls
Access control requirements appear explicitly in SOC 2, ISO 27001, HIPAA, GDPR, and PCI DSS—frameworks that define specific expectations around managing user access and permissions. Regulators require organizations to enforce least privilege principles, restricting user access to only what's necessary for their defined role. SOC 2 security controls must cover role-based access, least privilege enforcement, and regular access reviews.
ISO 27001:2022 requires documented access control policies tied to risk assessments, with evidence demonstrating how access rights align with business needs and security requirements. HIPAA updates require multi-factor authentication enforcement, encryption on systems handling protected health information, and asset inventories documenting where sensitive data resides and who can access it. GDPR mandates technical measures ensuring only authorized personnel can access personal data, with documented justification for access rights and data processing activities.
The distinction between proof-based compliance and policy-based compliance matters. Writing an access control policy satisfies documentation requirements. Demonstrating that the policy is enforced through technical controls, access logs, and regular reviews satisfies audit requirements.
Audit Readiness and Access Transparency
Auditors examine access management evidence to verify that documented policies translate into operational controls. This includes reviewing user provisioning and deprovisioning processes, access request approvals, permission assignments, and audit logs showing who accessed sensitive systems during the observation period.
Access controls reduce audit scope by demonstrating containment boundaries. When auditors can verify that only authorized users with documented business justification can access cardholder data environments, protected health information repositories, or financial reporting systems, they can limit testing to those defined populations rather than examining the entire user base.
Detailed audit logs tracking successful and failed access attempts, user actions, and changes to permissions form the evidentiary foundation that auditors require. Organizations without comprehensive access logs face expanded audit scope, additional testing requirements, and potential findings related to insufficient monitoring and accountability.
Access Control Models Used in Enterprise Environments
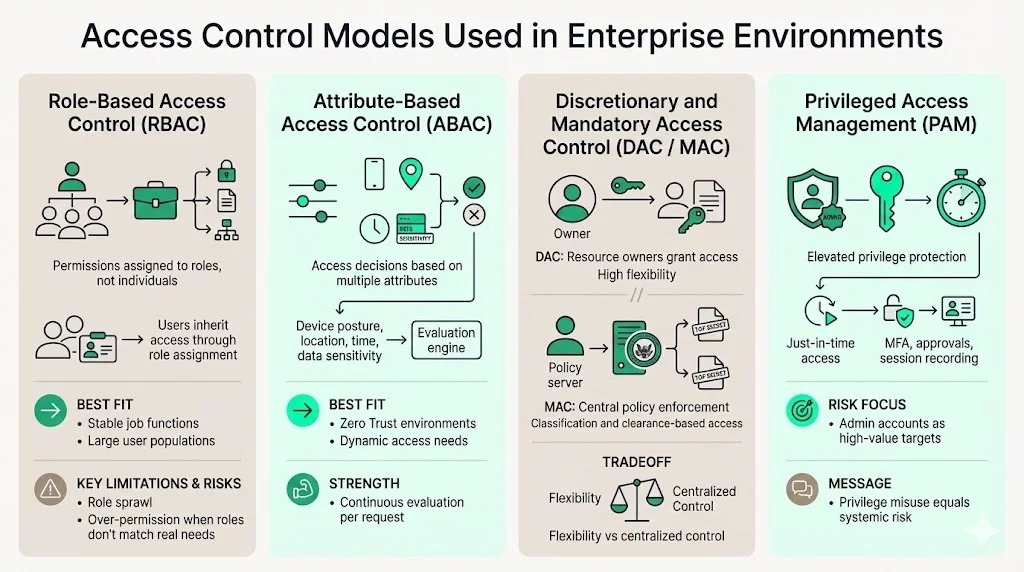
1) Role-Based Access Control (RBAC)
RBAC assigns permissions to predefined roles rather than individual users. A financial analyst role receives access to reporting tools, revenue data, and forecasting systems. When a new analyst joins, administrators assign the analyst role rather than configuring individual permissions across dozens of applications.
RBAC works well at scale in organizations with stable job functions and clearly defined responsibilities. Role definitions remain consistent across user populations, reducing administrative overhead and ensuring permission consistency.
Limitations emerge in dynamic environments where job responsibilities shift frequently, projects require temporary cross-functional access, or users need permissions that don't align with predefined roles. RBAC can lead to role proliferation—hundreds of granular roles created to accommodate edge cases—or over-permissioned users assigned multiple roles to cover their actual access needs.
2) Attribute-Based Access Control (ABAC)
ABAC makes access decisions based on multiple attributes: user identity, device security posture, network location, time of day, data classification, and environmental context. A user accessing sensitive data from a managed device on the corporate network during business hours receives different permissions than the same user connecting from an unmanaged device on public Wi-Fi at midnight.
ABAC supports Zero Trust Architecture strategies, operating on the principle of continuous verification and assuming no user or device is inherently trustworthy. Each access request triggers a new evaluation against current attributes rather than relying on previously granted permissions.
3) Discretionary and Mandatory Access Control
Discretionary Access Control (DAC) allows resource owners to grant or revoke access at their discretion. A document owner decides which users can read, edit, or share the document. DAC provides flexibility but introduces governance challenges when access decisions are decentralized across thousands of resource owners.
Mandatory Access Control (MAC) enforces centrally defined policies based on security classifications and user clearance levels. Users cannot grant access regardless of resource ownership—the system enforces access decisions based on classification labels. MAC appears primarily in government and defense environments where data classification schemes drive access policies.
4) Privileged Access Management (PAM)
PAM addresses the elevated risk associated with administrative privileges. Privileged access requires enforced multi-factor authentication and conditional access policies based on device posture and user behavior. PAM solutions implement just-in-time access provisioning, session recording, credential rotation, and approval workflows before granting administrative rights.
Administrative credentials represent high-value targets. Compromising a standard user account provides limited access to systems and data. Compromising an administrative account provides the ability to disable security controls, exfiltrate sensitive data, create backdoor accounts, and move laterally across the environment.
How Access Controls Reduce Breach Risk
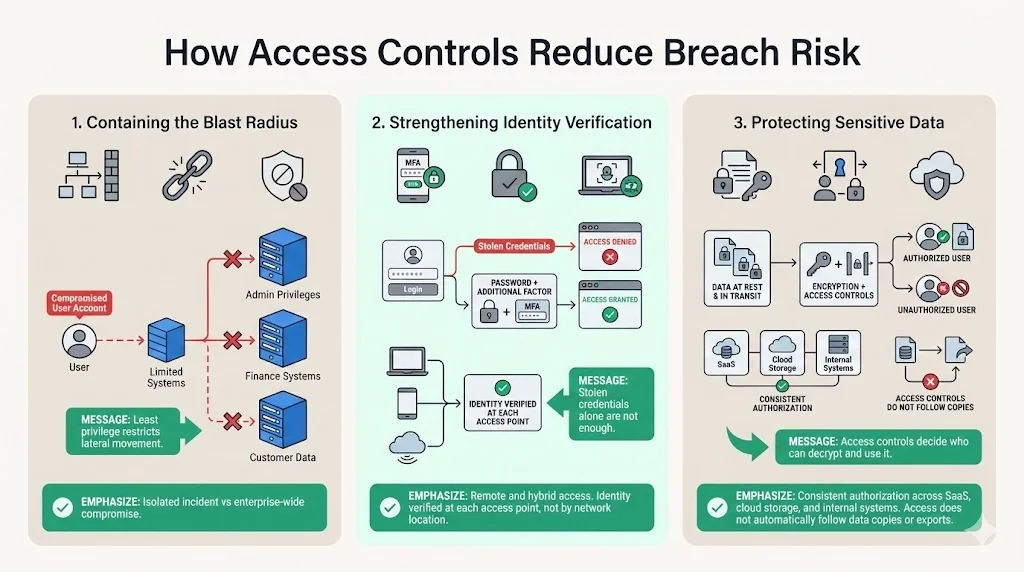
1) Containing the Blast Radius
Access controls limit lateral movement after initial compromise. When an attacker gains access to a standard user account through phishing or credential theft, least privilege restrictions prevent that account from accessing systems and data outside its authorized scope. The attacker cannot escalate to administrative privileges, cannot access financial systems from a compromised marketing account, and cannot exfiltrate customer data from a compromised help desk credential.
Containing the blast radius transforms a potential enterprise-wide breach into an isolated incident affecting a limited scope of systems and data.
2) Strengthening Identity Verification
Multi-factor authentication prevents credential-based attacks from succeeding. Stolen passwords alone cannot grant access when the system requires additional verification factors. Even when attackers obtain usernames and passwords through phishing campaigns, database breaches, or credential stuffing attacks, MFA blocks unauthorized access attempts.
Remote and hybrid workforces accessing corporate resources from diverse locations and devices require stronger identity verification than perimeter-based security provides. Access controls verify identity at every access point rather than assuming that users inside the network perimeter are authorized.
3) Protecting Sensitive Data
Access controls work alongside encryption and data protection mechanisms to enforce authorization boundaries. Encrypted data remains protected during storage and transmission. Access controls determine which users can decrypt and access that data, ensuring technical measures align with authorization policies.
Preventing unauthorized access to cloud storage, SaaS applications, and internal systems requires access controls that span heterogeneous environments. A user authorized to access human resources data in the corporate HRIS should not automatically receive access to that same data when it's exported to cloud storage or replicated to a business intelligence platform.
Access Controls in Distributed and Cloud-First Enterprises
Managing access across multiple cloud providers, dozens of SaaS applications, and legacy on-premises systems introduces identity sprawl and permission creep. Each system maintains its own user database, permission model, and access control implementation. Users accumulate permissions as they move between roles, projects, and responsibilities without corresponding deprovisioning of previous access rights.
Identity sprawl occurs when user identities proliferate across disconnected systems—separate accounts in AWS, Azure, Google Cloud, Salesforce, Workday, GitHub, and internal applications. Permission creep happens when users retain access rights after changing roles or completing projects, accumulating more permissions over time rather than maintaining least privilege.
Access management becomes exponentially harder as environments scale. Organizations operating 50 SaaS applications face fundamentally different access governance challenges than those operating 5 applications. Each additional system introduces new permission models, authentication requirements, and audit logging implementations that must be centrally managed and continuously monitored.
Operationalizing Access Controls at Enterprise Scale
Policy Design and Enforcement
Translating security policies into enforceable controls requires mapping business requirements to technical implementations. A policy stating "only authorized personnel can access customer financial data" must define who qualifies as authorized personnel, what constitutes customer financial data, which systems contain that data, how access requests are approved, and how frequently access rights are reviewed.
Access policies must align with business needs. Overly restrictive policies that block legitimate business activities create workarounds—users share credentials, maintain shadow IT systems, or escalate every access request to emergency exceptions. Insufficiently restrictive policies leave sensitive data exposed to unauthorized access.
Monitoring and Continuous Review
Static access reviews conducted quarterly or annually fail to keep pace with organizational change. Users join, change roles, and leave. Applications are deployed, reconfigured, and decommissioned. Permissions granted for temporary projects become permanent when no one remembers to revoke them.
Continuous validation using audit logs and usage patterns enables teams to monitor access patterns, detect suspicious behavior, and meet regulatory obligations through dashboards and reporting tools. Automated analysis identifies dormant accounts that haven't been authenticated in 90 days, privileged accounts used outside normal business hours, or users accessing systems unrelated to their job function.
Integration With Existing Security Stack
Access controls integrate with identity providers, Security Information and Event Management (SIEM) platforms, and governance tools to create centralized visibility and policy enforcement. Identity providers maintain authoritative user directories and authenticate access attempts. SIEMs aggregate access logs across systems for security monitoring and incident investigation. Governance platforms orchestrate access request workflows, approval processes, and compliance reporting.
Making access controls actionable requires collaboration across IT operations, security teams, and business stakeholders. IT teams provision user accounts and assign permissions. Security teams define policies and monitor for violations. Business managers approve access requests and certify that their team members hold appropriate access rights.
Common Mistakes That Weaken Access Control Programs
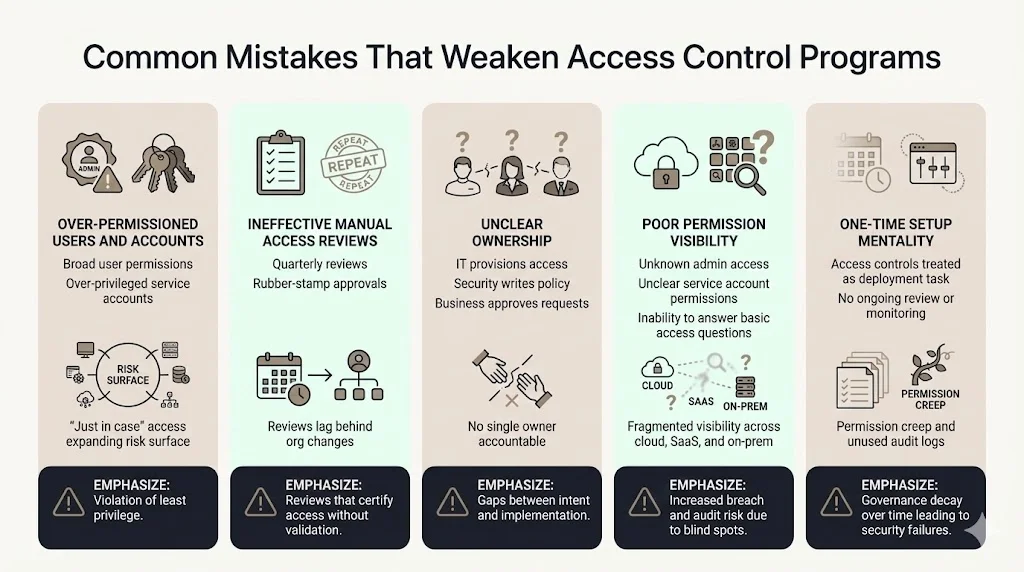
Over-permissioned users and service accounts undermine least privilege principles. Granting users administrative rights "just in case they need it later" or assigning broad permissions to service accounts "because it's easier than determining specific requirements" creates unnecessary risk exposure.
Manual access reviews fail to keep pace with organizational change. Quarterly reviews that require managers to certify hundreds of user access rights result in rubber-stamp approvals rather than meaningful validation. By the time the review completes, organizational changes have already rendered the findings obsolete.
Lack of ownership between IT, security, and business teams creates accountability gaps. IT teams provision access based on manager requests without understanding business context. Security teams define policies without understanding operational requirements. Business managers approve access requests without understanding security implications.
Poor visibility into effective permissions across cloud environments, SaaS applications, and on-premises systems means organizations cannot answer basic questions: Who can access customer data? Which users hold administrative privileges? What permissions does this service account actually have?
Treating access controls as a one-time setup during initial system deployment rather than continuous operational discipline guarantees that access governance degrades over time. Permissions accumulate, policies drift from implementation, and audit logs go unreviewed until an incident occurs or an auditor requests evidence.
Business Value for Vendors Selling to Enterprise Clients
Enterprise buyers evaluate vendor access controls as a trust signal extending beyond security teams. Procurement teams, legal counsel, and compliance officers examine vendor security practices before approving contracts—particularly for vendors handling sensitive customer data, integrating with internal systems, or operating in regulated industries.
Strong access controls reduce compliance costs and accelerate audit timelines. Vendors demonstrating mature access governance provide audit documentation faster, require fewer follow-up inquiries, and pass security assessments without remediation delays. This operational efficiency translates to faster deal cycles and reduced friction in customer relationships.
Many enterprise customers now require SOC 2 compliance from vendors before signing contracts, especially in SaaS and cloud service sectors. Vendors without documented access controls face elongated sales cycles, additional due diligence requirements, or disqualification from procurement consideration.
Access controls support long-term enterprise growth by establishing the security foundation required to handle increasingly sensitive data, expand into regulated industries, and integrate with customer environments. Vendors building access governance into their operational model from the beginning avoid the disruptive remediation projects that inevitably occur when security practices cannot support business growth.
Why Access Controls Support Both Compliance and Resilience
Access controls serve dual purposes: satisfying regulatory requirements while reducing operational risk. Compliance frameworks require access controls because those controls address fundamental security objectives—protecting confidentiality, ensuring accountability, and limiting exposure to unauthorized access.
The long-term cost of weak access governance includes regulatory penalties, customer contract violations, incident response expenses, and reputational damage. Organizations discovering widespread access control failures during audit preparation face remediation projects spanning months, delayed certifications, and findings that must be disclosed to customers and business partners.
Treating access management as a continuous operational discipline—not a compliance project with defined completion dates—requires sustained investment in policy enforcement, user training, technical controls, and monitoring capabilities. Organizations that maintain rigorous access governance avoid the crisis-driven remediation cycles that characterize reactive security programs.
Frequently Asked Questions
1) What are access controls?
Access controls are enforced rules governing who can access specific systems, data, and resources based on verified identity and assigned permissions. They combine authentication to verify user identity, authorization to determine permitted actions, and audit logging to maintain accountability. Access controls operate across cloud infrastructure, SaaS applications, databases, and internal systems, enforcing least privilege principles and preventing unauthorized access.
2) Why are access controls critical for compliance?
Regulations including SOC 2, ISO 27001, HIPAA, and GDPR explicitly require organizations to implement access controls, managing user permissions and protecting sensitive information. Auditors require documented evidence demonstrating that access policies are technically enforced, not merely documented in policy statements. Access controls provide the audit logs, access reviews, and permission records that satisfy regulatory requirements around least privilege, segregation of duties, and accountability.
3) What types of access control models exist?
Role-Based Access Control (RBAC) assigns permissions based on job roles. Attribute-Based Access Control (ABAC) makes dynamic decisions based on user, device, location, and context attributes. Discretionary Access Control (DAC) allows resource owners to grant access at their discretion. Mandatory Access Control (MAC) enforces centralized policies based on security classifications. Privileged Access Management (PAM) implements additional controls around administrative accounts with elevated permissions.
4) How do access controls reduce breach risk?
Access controls limit lateral movement after initial compromise by restricting what compromised credentials can access. Least privilege principles prevent standard user accounts from escalating to administrative privileges or accessing systems outside their authorized scope. Multi-factor authentication blocks credential-based attacks even when passwords are stolen. Access controls contain breach impact to the initially compromised account rather than allowing enterprise-wide compromise.
5) What mistakes weaken access control programs?
Over-permissioned users and service accounts violate least privilege principles. Manual access reviews that occur quarterly or annually cannot keep pace with organizational change. Lack of clear ownership between IT, security, and business teams creates accountability gaps. Poor visibility into effective permissions across cloud and SaaS environments means organizations cannot determine who can access sensitive data. Treating access controls as one-time configuration rather than continuous operational discipline guarantees that governance degrades over time.



.svg)
.svg)
.svg)