Most organisations treating PCI compliance as an annual checkbox exercise discover a fundamental flaw when external threats materialize: their internet-facing systems harbor vulnerabilities that auditors never examined between validation cycles. PCI DSS Requirement 11.3.2 requires evidence of passing external scans, performed by an ASV, at least once every three months—a mandate designed to detect security weaknesses before attackers exploit them.
An Approved Scanning Vendor (ASV) provides external vulnerability scanning services specifically certified by the PCI Security Standards Council (PCI SSC) to validate compliance with payment security standards. These scans systematically probe internet-facing systems—web servers, firewalls, routers, gateways, APIs—to identify exploitable vulnerabilities that could compromise cardholder data environments (CDEs).
This definition explains how ASV PCI compliance supports data protection standards in 2026 and beyond, examining the mechanics of external vulnerability scanning, its role in risk management, implementation requirements, and how it integrates with broader security infrastructure including firewall configuration, network segmentation, encryption, and continuous monitoring.
Understanding the basics — What is ASV PCI compliance?
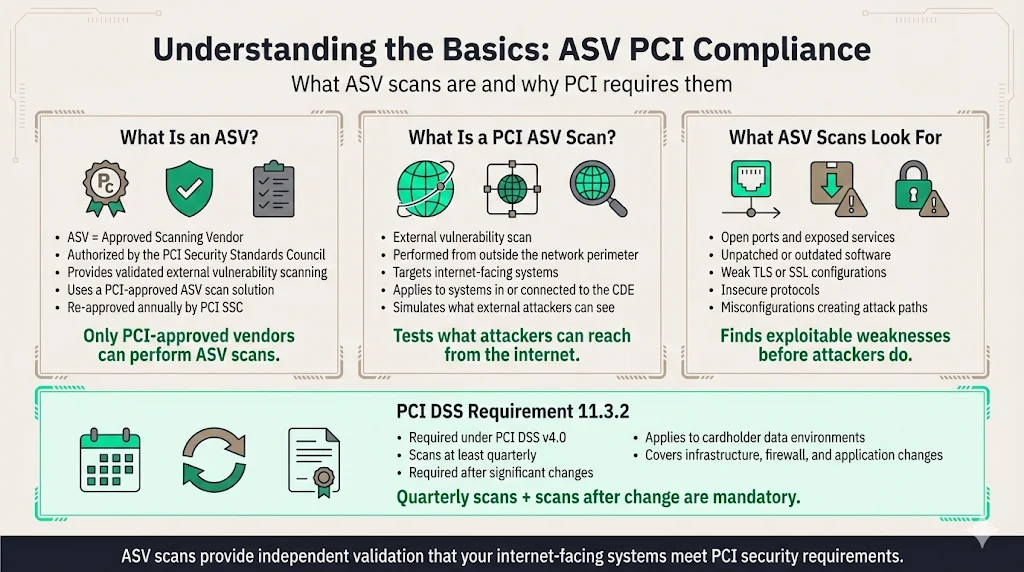
What is an ASV?
An ASV is an organization with a set of security services and tools ("ASV scan solution") to conduct external vulnerability scanning services to validate adherence with the external scanning requirements of PCI DSS Requirement 11.3.2. These vendors undergo rigorous certification by the PCI Security Standards Council before being authorized to perform compliance-mandated scans.
The scanning vendor's ASV scan solution is tested and approved by PCI SSC before an ASV is added to PCI SSC's List of Approved Scanning Vendors. This qualification process ensures that ASV solutions can accurately detect vulnerabilities according to baseline requirements established by the Council. The PCI Security Standards Council maintains a structured process for security solution providers to become Approved Scanning Vendors (ASVs), as well as to be re-approved each year, ensuring ongoing capability and compliance with evolving standards.
What is an ASV scan / PCI ASV scan?
External vulnerability scanning examines internet-facing systems from outside the network perimeter to detect security weaknesses exploitable by external threat actors. An external vulnerability scan is performed from beyond the logical network perimeter on any Internet-facing hosts that are either located within or connected to an organisation's cardholder data environment (CDE).
Requirement 11.3.2 of PCI DSS v4.0 requires organizations that meet certain criteria to have external vulnerability scans performed by a PCI SSC Approved Scanning Vendor (ASV) at least once every three months and after significant changes to their environment. These scans detect open ports, unpatched software, weak TLS configurations, insecure protocols, misconfigurations, and other vulnerabilities that could provide attack vectors into systems processing or storing credit card data.
The scanning mandate applies to entities handling cardholder data under the PCI Data Security Standard. PCI DSS Requirement 11.3.2.1 emphasises the importance of performing external vulnerability scans following any significant modifications made to your system—ensuring that infrastructure changes, firewall reconfigurations, or new application deployments don't inadvertently introduce exploitable weaknesses.
Why ASV PCI compliance matters for data protection and payment security
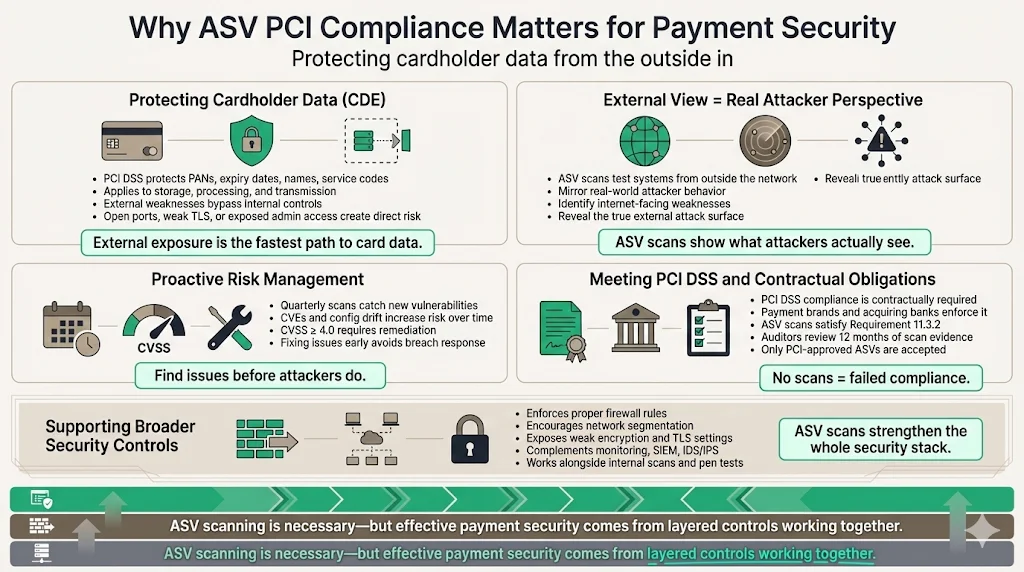
Protecting credit card data & safeguarding the cardholder data environment (CDE)
PCI DSS governs how cardholder data—Primary Account Numbers (PANs), expiry dates, cardholder names, service codes—must be stored, processed, and transmitted. The standard establishes comprehensive requirements covering encryption, access control, network segmentation, and vulnerability management designed to protect payment card information throughout its lifecycle.
Scans reveal weaknesses in your system's setup, programs, and equipment that cyber attackers could use to infiltrate your network without permission and possibly steal sensitive cardholder information. External vulnerabilities represent high-risk exposure points: an unpatched web server, misconfigured TLS endpoint, or open administrative port can provide direct pathways for attackers to access CDEs, bypassing internal security controls entirely.
The scans are designed to test for vulnerabilities from the outside in, looking for any potential and well-known weaknesses a bad actor can exploit to gain access to the company's cardholder data environment (CDE). This external perspective mirrors actual attack vectors used by threat actors scanning internet address ranges for vulnerable targets—making ASV scans essential for understanding your organization's external attack surface from an adversarial viewpoint.Risk management & proactive vulnerability detection
Quarterly scanning ensures new vulnerabilities get identified before exploitation. Software vendors continuously discover and patch security flaws; threat researchers publish Common Vulnerabilities and Exposures (CVEs) documenting newly identified weaknesses; configuration changes during system maintenance can inadvertently expose services or weaken security postures. Without regular external scanning, these vulnerabilities accumulate undetected.
After completing a scan, it is important to take action (remediate) on the identified vulnerabilities that have a CVSS score of 4.0 or higher. The Common Vulnerability Scoring System (CVSS) provides standardized risk ratings, allowing organizations to prioritize remediation based on severity. Vulnerabilities scoring 4.0 or higher represent medium-to-critical risks requiring immediate attention to prevent exploitation.
This proactive detection reduces organizational risk from external threats, preventing data breaches that result in fraud, regulatory penalties, contractual violations with acquiring banks, reputational damage, and customer trust erosion. Organizations discovering vulnerabilities through ASV scans rather than through breach incidents maintain operational control over remediation timelines and avoid the cascading consequences of compromised cardholder data.
Meeting security standards & regulatory obligations
PCI DSS compliance represents more than best practice—it's contractually mandated for entities accepting card payments. Payment brands (Visa, Mastercard, American Express, Discover, JCB) and acquiring banks impose compliance requirements as conditions for processing payment card transactions. Non-compliance can result in increased transaction fees, fines, loss of processing privileges, or contractual termination.
For PCI DSS 4.0, ASV scans validate adherence to the external scanning requirements in Requirement 11.3.2 and are a crucial element in maintaining a secure environment and ensuring compliance with PCI DSS. External vulnerability scanning forms a core component of Requirement 11, which mandates that organizations regularly test security systems and processes to ensure vulnerabilities are identified, prioritized, and addressed.
For those organizations using the defined approach, Requirement 11 testing procedures include examining ASV scan reports from the last 12 months to verify that external vulnerability scans occurred at least once every three months, examining reports to verify that vulnerabilities are resolved and ASV Program Guide requirements for passing scans are met, and verifying that scans were completed by a PCI SSC Approved Scanning Vendor. These documentation requirements provide auditable evidence of continuous security hygiene.
Supporting complementary security practices
While ASV scans focus specifically on external vulnerabilities, they encourage and validate broader security disciplines. Passing ASV scans requires proper firewall configuration—ensuring that only necessary ports remain open, that administrative interfaces aren't exposed to the internet, and that firewall rules appropriately restrict inbound traffic to internet-facing services.
Effective network segmentation limits the scope of ASV scanning by isolating cardholder data environments from general corporate networks and ensuring that internet-facing systems have controlled, monitored pathways to CDEs rather than direct access. Organizations implementing robust segmentation reduce both their compliance scope and their actual risk exposure by containing potential breaches.
Encryption requirements for data in transit become evident during ASV scans, which detect weak TLS configurations, support for deprecated SSL protocols, insufficient cipher suites, or certificate validation issues. Organizations must maintain current encryption standards—disabling TLS 1.0, TLS 1.1, and all SSL versions while implementing TLS 1.2 or TLS 1.3 with strong cipher suites.
Continuous network monitoring and logging complement ASV scanning by providing real-time detection of suspicious activities, unauthorized access attempts, and anomalous traffic patterns that static quarterly scans might miss. Organizations combining external vulnerability scanning with Security Information and Event Management (SIEM) systems, intrusion detection/prevention systems (IDS/IPS), and log analysis create layered defenses that address both known vulnerabilities and novel attack patterns.
ASV scanning alone represents necessary but insufficient security. Comprehensive payment security requires internal vulnerability scanning (distinct from external ASV scans), penetration testing to validate that identified vulnerabilities are actually exploitable, application security testing, secure configuration management, patch management, access controls, encryption, monitoring, and incident response capabilities working in concert.
How the process works — implementing ASV PCI compliance in your company
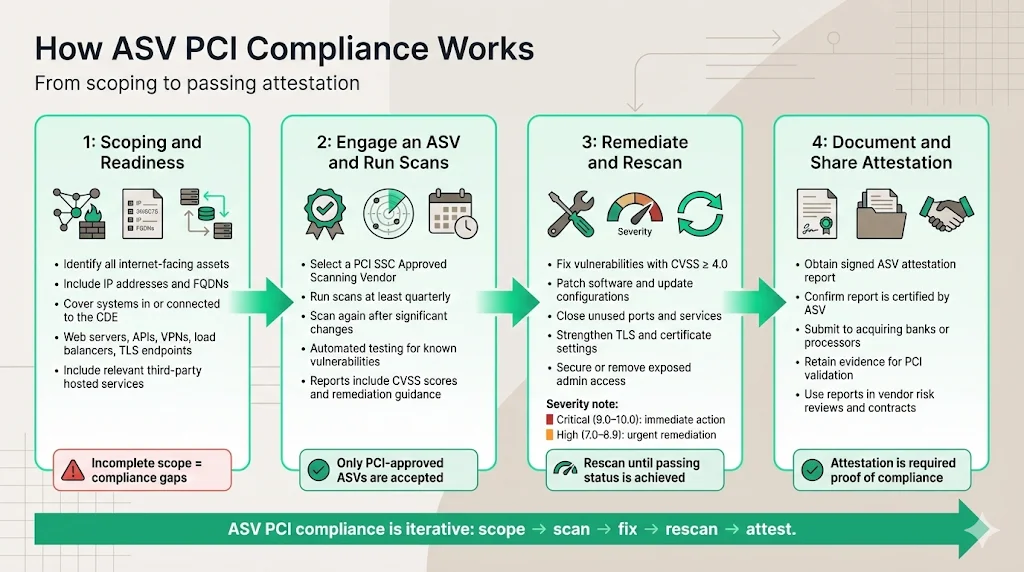
Scoping and readiness: identifying what needs to be scanned
Organizations must accurately define the scope of their internet-facing assets before engaging an ASV. This requirement specifies that all internet-facing components you own or utilise as part of your cardholder data environment (CDE), as well as any externally facing system components that may provide access to the CDE, must be scanned via IP addresses and any relevant Fully Qualified Domain Names (FQDN).
Typical scope includes web servers hosting e-commerce applications or payment pages, public-facing APIs processing payment data, firewalls and routers with external interfaces, VPN endpoints and remote-access gateways, load balancers, TLS/SSL termination points, and any third-party hosted services that connect to internal cardholder data environments. Organizations must provide complete inventories of IP addresses and FQDNs to their ASV, ensuring that scanning coverage encompasses all potential external attack vectors.
Scoping errors—failing to include internet-facing assets that connect to CDEs or accidentally including out-of-scope systems—create compliance gaps or unnecessary scanning overhead. Accurate scoping requires collaboration among network administrators, security teams, compliance personnel, and application owners who understand data flows and system interconnections.
Engaging an ASV and performing external vulnerability scans
Organizations select an ASV from the official list maintained by the PCI Security Standards Council. The scanning vendor's ASV scan solution is tested and approved by PCI SSC before an ASV is added to PCI SSC's List of Approved Scanning Vendors. While all listed ASVs meet baseline qualification requirements, vendors differ in pricing models, reporting quality, remediation guidance, customer support responsiveness, and additional services offered.
Scans must occur at minimum quarterly—every 90 days—with additional scans required after significant changes including infrastructure modifications, firewall rule changes, new internet-facing applications, system upgrades affecting external services, or network architecture changes. Organizations implementing continuous deployment models or frequent infrastructure changes may conduct monthly scanning to maintain ongoing visibility.
ASV scan solutions use automated tools to probe target systems, testing for thousands of known vulnerabilities, configuration weaknesses, compliance with encryption standards, exposure of sensitive information, and deviation from security best practices. The ASV generates detailed reports documenting identified vulnerabilities, CVSS scores, affected systems, technical descriptions, and recommended remediation steps.
Remediation and rescanning until passing status
It is necessary to conduct rescans as needed to verify that the vulnerabilities have been resolved. Based on ASV reports, organizations must systematically address identified issues: applying software patches, updating operating systems and applications, tightening firewall rules to close unnecessary ports, reconfiguring TLS/SSL implementations to disable weak protocols and ciphers, implementing proper certificate validation, securing or removing exposed administrative interfaces, correcting DNS misconfigurations, and strengthening authentication mechanisms.
After completing a scan, it is important to take action (remediate) on the identified vulnerabilities that have a CVSS score of 4.0 or higher. Organizations prioritize remediation based on vulnerability severity, exploitability, and potential impact on cardholder data security. Critical vulnerabilities scoring 9.0-10.0 on the CVSS scale require immediate remediation; high-severity vulnerabilities (7.0-8.9) demand prompt attention within defined remediation windows.
Rescanning continues iteratively until all reportable vulnerabilities are resolved and the ASV issues a passing attestation. The report will only be deemed "certified" once the ASV confirms its validity. False positives—scan results flagging issues that don't actually represent vulnerabilities in the specific context—require documentation and ASV review to exclude from passing criteria without leaving actual vulnerabilities unaddressed.
Documenting compliance and sharing attestation
Collaborate with your selected ASV to guarantee that they furnish a signed attestation report together with the scan findings. The final ASV attestation report documents that the organization passed external vulnerability scanning requirements, providing evidence required during PCI DSS validation processes.
Organizations submit ASV attestation reports to acquiring banks, payment processors, or payment brands as part of their compliance validation. Merchant level and service provider classification determine whether organizations complete Self-Assessment Questionnaires (SAQs) or undergo Qualified Security Assessor (QSA) audits—but external ASV scan attestations remain mandatory across most validation approaches.
These reports serve as documented proof when negotiating contracts with enterprise clients conducting vendor risk assessments, responding to customer security questionnaires, and demonstrating operational security discipline to business partners, regulators, and auditors.
How ASV PCI compliance supports enterprise-grade data protection standards
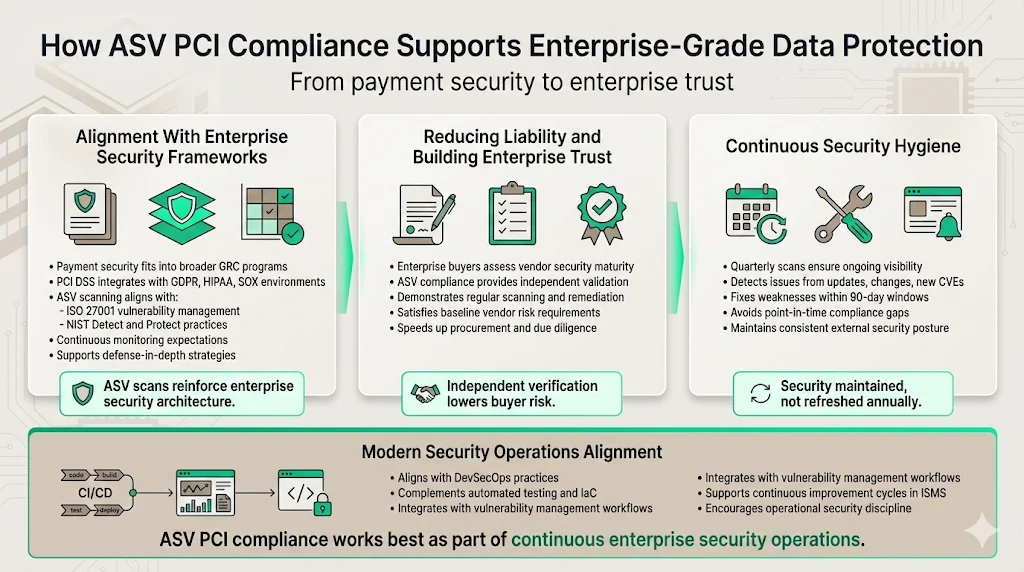
Alignment with global data protection and security principles
For enterprises, payment security represents one component of broader governance, risk, and compliance (GRC) frameworks encompassing information security policies, data protection strategies, regulatory compliance programs, and operational risk management. Organizations managing payment data alongside other sensitive information—personal data under GDPR, protected health information under HIPAA, financial records under SOX—integrate PCI DSS requirements into comprehensive security architectures.
ASV scanning provides regular external threat assessment comparable to vulnerability management requirements in ISO 27001 (control A.12.6.1 addressing technical vulnerability management), NIST Cybersecurity Framework practices (Detect and Protect functions), and security frameworks mandating continuous monitoring and risk assessment. When combined with encryption protecting data at rest and in transit, network segmentation isolating sensitive systems, robust access controls implementing least privilege principles, and security monitoring detecting anomalous activities, ASV compliance contributes to defense-in-depth strategies protecting multiple data types across enterprise environments.
Organizations implementing Information Security Management Systems (ISMS) incorporate ASV scanning into documented vulnerability management procedures, risk treatment plans, and continuous improvement cycles—demonstrating systematic approaches to security rather than isolated compliance activities.
Reducing liability and building trust with enterprise clients
For companies selling to enterprise customers, ASV PCI compliance signals operational maturity in payment security and risk management. Enterprise procurement processes routinely include vendor security assessments examining compliance certifications, security controls, vulnerability management practices, and incident history before approving vendors for contracts involving payment processing or access to customer payment data.
Being ASV PCI compliant provides documented evidence during vendor due diligence, demonstrating that the organization maintains current external vulnerability scanning, remediates identified weaknesses systematically, and undergoes independent verification by PCI SSC-approved vendors. This reduces perceived risk for enterprise customers and accelerates procurement timelines by satisfying baseline security requirements.
Documented ASV compliance minimizes organizational liability from data breaches compromising cardholder data. While no security measure guarantees absolute protection, organizations demonstrating regular vulnerability scanning, systematic remediation, and adherence to industry standards establish reasonable security practices that reduce legal exposure, regulatory penalties, and reputational damage if incidents occur despite implemented controls.
Continuous security hygiene through regular scans and remediation
Quarterly scanning cadence ensures continuous security hygiene rather than annual compliance theater. This frequency matches enterprise expectations for ongoing risk management, monitoring, and compliance maintenance over time rather than point-in-time certifications providing false assurance between validation cycles.
Regular scanning allows early detection and remediation of vulnerabilities introduced through software updates, configuration changes, infrastructure additions, or newly disclosed CVEs affecting deployed technologies. Organizations discover and address vulnerabilities within 90-day windows rather than allowing exposure to persist for extended periods while awaiting annual assessments.
This continuous approach aligns with modern DevSecOps practices integrating security into operational workflows, continuous integration/continuous deployment (CI/CD) pipelines incorporating automated security testing, and infrastructure-as-code implementations embedding security requirements in deployment configurations. Organizations treating security as continuous operational discipline rather than periodic compliance activity achieve sustainably stronger security postures.
Limitations & best practices — what ASV PCI compliance alone does not guarantee
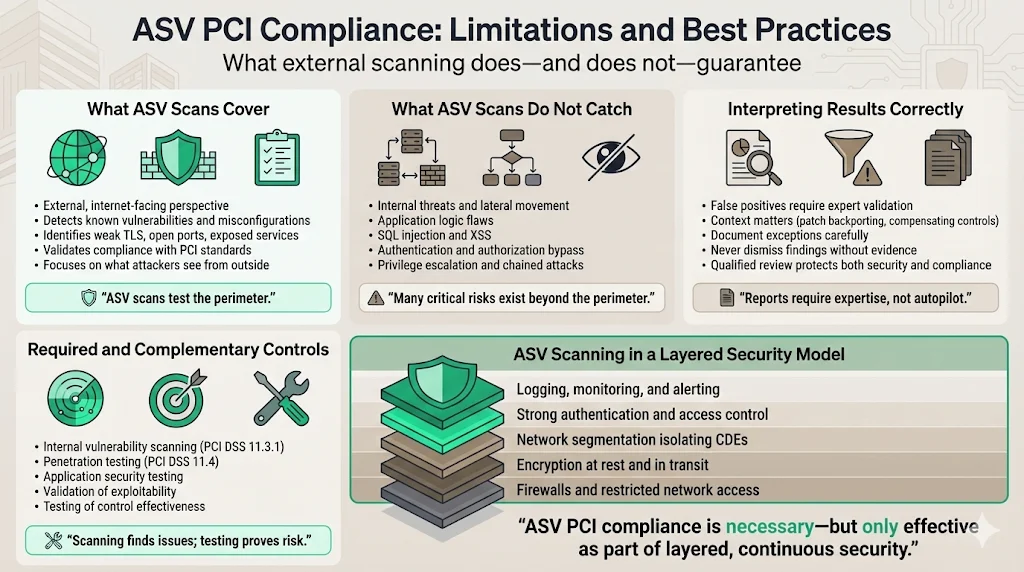
External ASV scans detect known vulnerabilities, common misconfigurations, and standards violations visible from outside the network perimeter—but they don't identify internal threats, application logic flaws, SQL injection vulnerabilities, cross-site scripting weaknesses, authentication bypass vulnerabilities, privilege escalation paths, or complex attack chains exploiting multiple systems. That's where internal network scanning, application security testing, and penetration testing become essential.
Internal vulnerability scanning examines systems from inside the network perimeter, detecting vulnerabilities in internal servers, databases, workstations, and infrastructure components not directly accessible from the internet. PCI DSS Requirement 11.3.1 mandates internal scanning separate from external ASV requirements, recognizing that comprehensive vulnerability management requires both internal and external perspectives.
Penetration testing goes beyond vulnerability identification to actively attempt exploitation, validating whether detected vulnerabilities are actually exploitable in the specific environment, testing security control effectiveness, identifying attack paths through multiple systems, and discovering logic flaws or configuration combinations that vulnerability scanners miss. PCI DSS Requirement 11.4 mandates penetration testing at least annually and after significant infrastructure or application changes.
False positives occur when scanning tools flag issues that don't represent actual vulnerabilities in the specific context—for example, detecting a service banner suggesting an outdated version when patches were backported, or identifying theoretical vulnerabilities mitigated by compensating controls. ASV reports require careful review by qualified personnel who understand the technical context, can validate findings, and document legitimate exceptions without dismissing genuine security issues.
ASV scanning remains reactive—detecting existing known vulnerabilities rather than preventing unknown zero-day threats or sophisticated targeted attacks. Well-rounded security programs must include proactive measures: encryption protecting data even if systems are compromised, network segmentation limiting breach impact, security monitoring detecting anomalous activities indicating novel attacks, access controls preventing unauthorized actions even on compromised systems, and incident response capabilities enabling rapid containment and recovery when prevention fails.
Organizations must treat ASV compliance as one component of layered security architecture rather than a sufficient endpoint. Comprehensive payment security requires firewall configuration restricting unnecessary network access, data encryption protecting cardholder data at rest and in transit, network segmentation isolating CDEs, strong authentication and access control limiting system access to authorized personnel, logging and monitoring detecting suspicious activities, regular internal scans identifying internal vulnerabilities, penetration testing validating control effectiveness, secure application development preventing code-level vulnerabilities, and documented security policies establishing organizational security standards.
How enterprises should integrate ASV PCI compliance into their broader data protection / security strategy
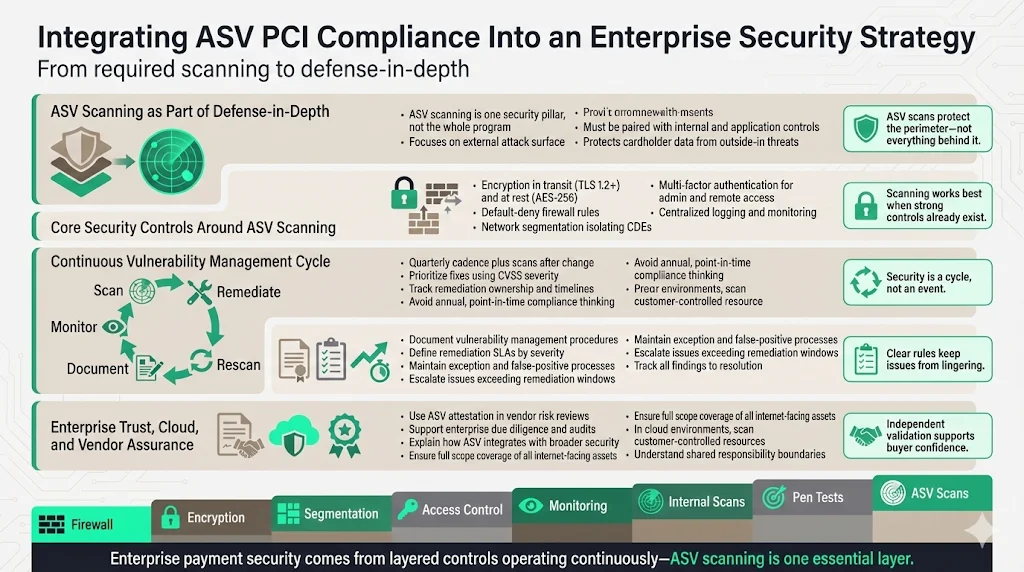
Treat ASV scanning as one essential pillar of defense-in-depth architecture. Organizations should implement layered security combining multiple independent controls protecting cardholder data: encryption of cardholder data in transit using TLS 1.2 or higher and at rest using AES-256 or equivalent strong encryption, strict firewall configuration implementing default-deny rules and allowing only necessary network access, network segmentation isolating cardholder data environments from general networks and internet-facing systems, strong authentication requiring multi-factor authentication for administrative access and remote access to CDEs, comprehensive logging and monitoring capturing security events and enabling rapid detection of suspicious activities, regular internal vulnerability scans detecting weaknesses in internal systems, annual penetration testing validating control effectiveness and identifying exploitable vulnerabilities, and secure software development lifecycle practices preventing vulnerabilities in custom payment applications.
Maintain continuous cycles of scanning, remediation, rescanning, documentation, and monitoring rather than treating compliance as an annual checkpoint. This operational rhythm supports ongoing risk management and adapts to evolving threats, infrastructure changes, and scaling requirements as organizations grow or launch new services and products.
Organizations should establish documented vulnerability management procedures defining responsibilities, remediation timelines based on CVSS severity scores, exception processes for documented false positives or accepted risks, escalation paths for vulnerabilities exceeding remediation windows, and tracking mechanisms ensuring all identified issues receive appropriate disposition.
Use ASV certification and attestation reports as components of vendor security assurance when working with enterprise clients. These documents provide independent verification of external security hygiene, supporting customer due diligence processes and risk assessments. Organizations should be prepared to discuss their vulnerability management practices, typical remediation timelines, and how external scanning integrates with broader security programs during vendor assessments.
For merchants and service providers processing card payments, ensure ASV scanning scope covers all internet-facing components plus any systems providing connectivity to cardholder data environments. This includes e-commerce web servers and applications, payment gateway interfaces, public APIs processing or transmitting payment data, external firewall and router interfaces, VPN endpoints enabling remote access, load balancers distributing traffic to payment systems, third-party integrations with access to CDEs, and any cloud-hosted services storing, processing, or transmitting cardholder data.
Organizations implementing cloud infrastructure must understand shared responsibility models: cloud providers typically secure underlying infrastructure, but customers remain responsible for securing their applications, data, and configurations. ASV scanning must cover customer-controlled internet-facing resources even when deployed in cloud environments, and organizations must verify that cloud configurations don't inadvertently expose resources to the internet.
Conclusion
ASV PCI compliance plays a critical role in protecting cardholder data and meeting mandatory payment security standards under PCI DSS. PCI DSS Requirement 11.3.2 requires evidence of passing external scans, performed by an ASV, at least once every three months—detecting external vulnerabilities before attackers exploit them, managing risk proactively, and providing documented evidence of security hygiene.
For companies selling to enterprise clients, ASV compliance demonstrates commitment to operational security, regulatory discipline, and systematic risk management—building trust and reducing perceived vendor risk during procurement processes. Organizations maintaining current ASV attestations accelerate enterprise sales cycles by satisfying baseline security requirements that enterprise procurement and security teams verify during vendor assessments.
ASV scanning represents necessary but insufficient security. Comprehensive protection requires integration with encryption protecting cardholder data throughout its lifecycle, network segmentation limiting breach impact and compliance scope, internal vulnerability scanning addressing internal threats, penetration testing validating exploitability, continuous security monitoring detecting anomalous activities, robust access controls limiting system access, and documented security policies establishing organizational standards.
Organizations treating ASV compliance as one component of defense-in-depth architecture—rather than an isolated checkbox—build genuinely secure payment processing environments that protect customer data, prevent breaches, maintain regulatory compliance, and support sustainable business growth.
FAQ
1) What is ASV in PCI compliance?
An ASV is an organization with a set of security services and tools ("ASV scan solution") to conduct external vulnerability scanning services to validate adherence with the external scanning requirements of PCI DSS Requirement 11.3.2. ASV stands for Approved Scanning Vendor—third-party organizations certified by the PCI Security Standards Council to perform external vulnerability scans required under PCI DSS. These vendors undergo qualification testing to verify their scanning solutions can accurately detect vulnerabilities according to PCI SSC baseline requirements.
2) How do you become a PCI ASV?
Organizations become Approved Scanning Vendors by completing the PCI SSC qualification process. The PCI Security Standards Council maintains a structured process for security solution providers to become Approved Scanning Vendors (ASVs), as well as to be re-approved each year. The qualification process requires vendors to register with PCI SSC, submit administrative documentation and attestation of compliance with ASV Qualification Requirements, undergo remote testing against PCI SSC's test infrastructure containing simulated vulnerabilities to prove the scanning solution accurately detects security flaws, and demonstrate adherence to reporting and operational requirements. Upon passing qualification testing, the vendor is listed on the official ASV list maintained by PCI SSC. Annual recertification ensures ASVs maintain current capabilities as standards evolve.
3) What are the 4 levels of PCI compliance?
PCI DSS classifies merchants and service providers into four levels based on annual transaction volume, determining validation and reporting requirements. For merchants: Level 1 processes over 6 million Visa transactions annually (or any merchant experiencing a data breach) and typically requires onsite assessment by a Qualified Security Assessor (QSA) plus quarterly ASV scans. Level 2 processes 1-6 million Visa transactions annually and typically requires annual Self-Assessment Questionnaire (SAQ) completion plus quarterly ASV scans. Level 3 processes 20,000-1 million e-commerce Visa transactions annually and typically requires annual SAQ plus quarterly ASV scans. Level 4 processes fewer than 20,000 e-commerce transactions or up to 1 million total Visa transactions annually and typically requires annual SAQ completion; ASV scan requirements depend on the specific SAQ type applicable to the merchant's processing method. Service provider levels follow similar volume-based classification with different thresholds, determining whether onsite QSA assessments or SAQ completion is required. Specific requirements vary by payment brand (Visa, Mastercard, American Express, Discover, JCB) and acquiring bank.
4) How much does a PCI ASV scan cost?
ASV scan costs vary significantly based on provider, number of internet-facing assets (IP addresses and FQDNs in scope), scan frequency, level of remediation support provided, and whether the service includes consultative guidance beyond basic scanning. Costs typically range from several hundred dollars annually for small merchants with minimal internet-facing infrastructure to several thousand dollars for larger organizations with extensive external attack surfaces. Some ASVs charge per-IP or per-domain pricing models; others offer subscription-based pricing for unlimited quarterly scans. Organizations with existing relationships with vulnerability management vendors, managed security service providers, or PCI compliance consultancies may obtain ASV scanning as part of broader service agreements, potentially reducing standalone costs. For comparison, penetration testing—which provides deeper security validation than automated scanning—typically costs $15,000-$70,000 depending on scope, engagement duration, and testing methodology. Organizations should evaluate ASV providers based on reporting quality, remediation guidance, customer support responsiveness, and integration with existing security workflows rather than cost alone.



.svg)
.svg)
.svg)