Enterprise buyers in healthcare procurement often request a Business Associate Agreement before evaluating product functionality, pricing, or integration capabilities. A Business Associate Agreement (BAA) is a legally required HIPAA contract that governs how third-party vendors handle protected health information on behalf of covered entities. This agreement serves as a foundational trust mechanism, establishes clear risk allocation, and directly influences sales cycle length in regulated industries. Without a signed BAA, healthcare organizations cannot legally share protected health information with vendors—making the agreement a non-negotiable prerequisite for market entry, not a formality to address later in the procurement process.
What Is a Business Associate Agreement?
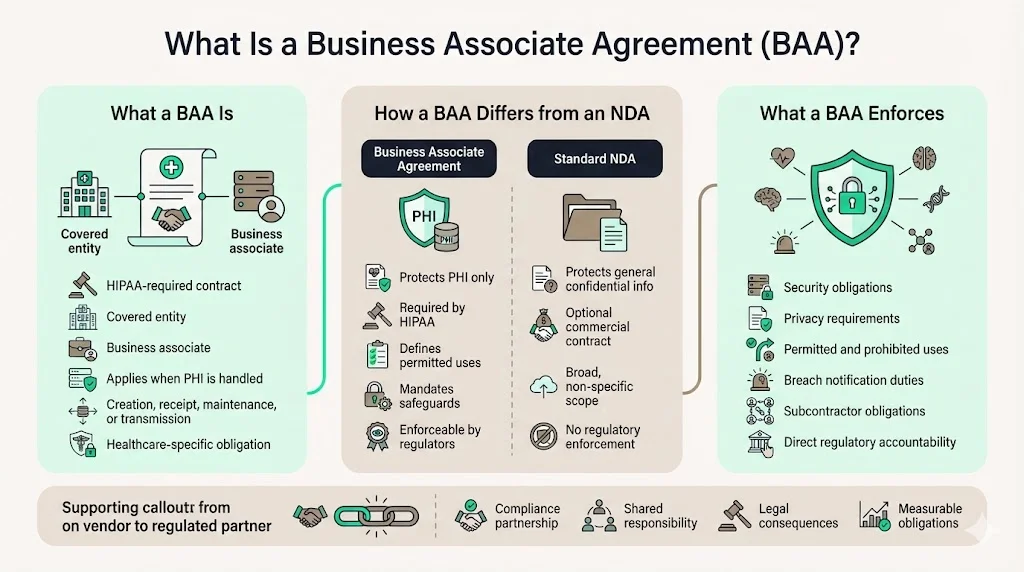
A Business Associate Agreement is a contract between a HIPAA covered entity and a business or individual that performs certain functions or activities on behalf of, or provides a service to, the covered entity when the function, activity, or service involves the creation, receipt, maintenance, or transmission of Protected Health Information (PHI). Unlike a standard non-disclosure agreement that protects general business confidential information, a BAA is a very specific, legally-mandated contract under HIPAA designed to protect one thing: Protected Health Information (PHI). This contractual mechanism establishes enforceable security obligations, defines permitted and prohibited uses of health data, and creates direct regulatory accountability—transforming vendor relationships from transactional arrangements into compliance partnerships with measurable legal consequences.
Why Business Associate Agreements Exist
The Health Insurance Portability and Accountability Act established comprehensive federal protections for protected health information through the Privacy Rule and Security Rule. When covered entities—hospitals, health plans, and healthcare clearinghouses—engage third-party vendors to perform functions requiring PHI access, regulatory risk extends beyond organizational boundaries. As the cyber threat landscape evolves and data privacy and security concerns escalate, healthcare organizations are increasingly relying on third parties to manage vast amounts of PHI. As a result, comprehensive business associate agreements have become crucial to compliance, security, and privacy.
BAAs exist because HIPAA compliance obligations do not stop at the covered entity's legal perimeter. While HIPAA mandates that Covered Entities must safeguard PHI, compliance does not stop with them. Every third-party partner that touches PHI must also follow the same standards—this is where the BAA becomes essential. The agreement formalizes accountability, creates enforceable safeguard requirements, and establishes breach notification protocols—addressing the fundamental compliance gap created when protected health information moves outside direct organizational control.
Who Is Considered a Business Associate?
HHS defines a business associate as "a person or entity that performs certain functions or activities that involve the use or disclosure of protected health information on behalf of, or provides services to, a covered entity." This definition encompasses a broad range of enterprise vendors whose services require PHI access or transmission.
Common business associates relevant to enterprise technology vendors include:
- SaaS Providers: Cloud-based healthcare applications that store, process, or transmit electronic protected health information as part of core functionality.
- Cloud Hosting Companies: Infrastructure and platform providers like AWS, Microsoft Azure, and Google Cloud Platform when hosting covered entity workloads containing PHI.
- Analytics and Business Intelligence Vendors: Organizations providing data analysis, reporting, or predictive modeling services using patient-level healthcare data.
- IT Support and Managed Service Providers: Technology vendors performing system administration, security monitoring, or technical support functions with access to systems containing PHI.
- Billing and Payment Processing: Third-party administrators handling claims processing, payment operations, or revenue cycle management.
A company selling software becomes a business associate the moment its product architecture requires creating, receiving, maintaining, or transmitting protected health information on behalf of a covered entity customer. This determination depends on data flow and system design—not vendor intent or product marketing positioning. Members of your workforce aren't business associates. Neither are other covered entities when they're providing treatment. And if a vendor only has incidental access to PHI—like a janitorial service that might glimpse a document while cleaning—they typically don't qualify as business associates either.
When a Business Associate Agreement Is Required
A Business Associate Agreement (BAA) is required whenever a Covered Entity grants a third-party vendor access to Protected Health Information (PHI) in the course of providing services. This applies whether the PHI is being created, received, stored, transmitted, or simply maintained on behalf of the Covered Entity. The triggering event is not the nature of the service provided but whether the service delivery model necessitates PHI exposure.
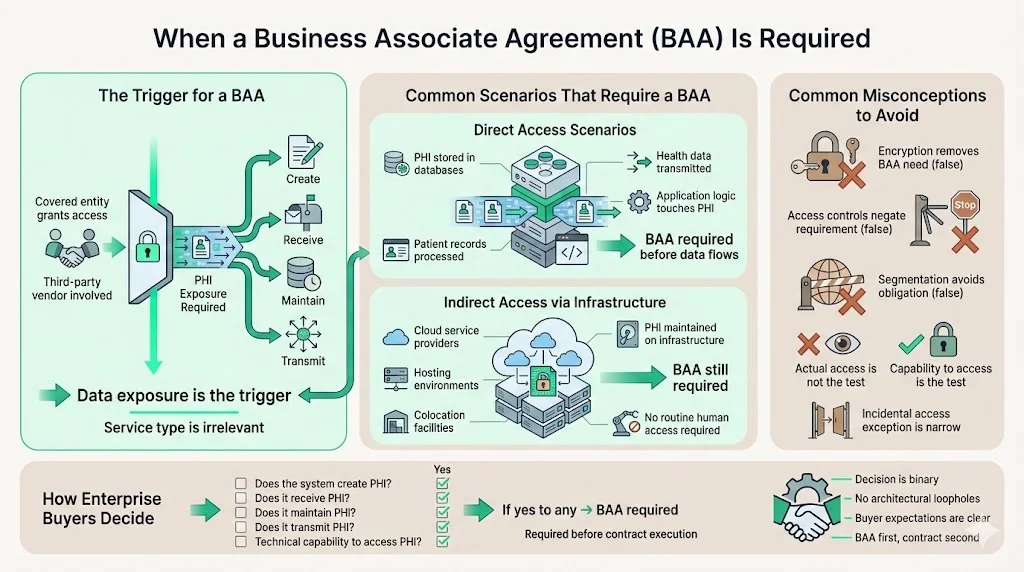
Direct Access Scenarios: Vendors whose systems store PHI in databases, process patient records through application logic, or transmit health information between parties require BAAs before any data flows.
Indirect Access Through Infrastructure: Cloud service providers, colocation facilities, and hosting vendors require BAAs when they maintain infrastructure storing covered entity PHI—even when vendor personnel do not routinely access patient-level data.
Common Misconceptions Among Enterprise Vendors: Many SaaS companies mistakenly believe encryption, access controls, or architectural segmentation eliminate BAA requirements. HIPAA regulations require BAAs based on potential access capability, not actual access patterns. A business associate contract is not required with persons or organizations whose functions, activities, or services do not involve the use or disclosure of protected health information, and where any access to protected health information by such persons would be incidental, if at all.
Enterprise buyers apply a straightforward checklist: Will the vendor's system create, receive, maintain, or transmit PHI? Does the vendor possess technical capability to access PHI regardless of contractual access restrictions? If either answer is yes, the vendor is a business associate and a BAA is required before contract execution.
What a Business Associate Agreement Covers
Core Provisions
A written contract between a covered entity and a business associate must: (1) establish the permitted and required uses and disclosures of protected health information by the business associate; (2) provide that the business associate will not use or further disclose the information other than as permitted or required by the contract or as required by law; (3) require the business associate to implement appropriate safeguards to prevent unauthorized use or disclosure of the information, including implementing requirements of the HIPAA Security Rule.
Permitted and Prohibited Uses of PHI: BAAs define precisely how business associates may use protected health information—typically limited to providing contracted services, performing required legal functions, and supporting the covered entity's treatment, payment, or healthcare operations activities.
Safeguards for Data Security: Business associates must implement administrative, physical, and technical safeguards meeting HIPAA Security Rule standards. This includes access controls, encryption requirements, audit logging, and incident response capabilities documented through risk assessments and security policies.
Breach Reporting Timelines: Entering into a BAA holds business associates accountable for complying with HIPAA or risk facing penalties associated with noncompliance. Agreements specify discovery-to-notification timeframes—typically requiring business associates to report breaches of unsecured PHI to covered entities within 60 days of discovery.
Subcontractor Responsibilities: A BA can also use a subcontractor (BAS) to perform some of its services. A BAA is required between the BA and the BAS if a BAS accesses PHI. Business associates must obtain equivalent written assurances from downstream subcontractors through separate BAAs—creating flow-down compliance obligations throughout the vendor supply chain.
Compliance and Enforcement
BAA provisions align directly with HIPAA Privacy Rule requirements governing use and disclosure limitations, individual rights, and minimum necessary standards. Security Rule alignment mandates documented risk analysis, security management processes, and technical safeguard implementation. It outlines how PHI can be used, disclosed, or accessed, providing traceability in the event of an audit or breach.
Covered entities retain audit rights to verify business associate compliance through documentation reviews, security assessments, and control testing. Most enterprise BAAs require business associates to maintain evidence of HIPAA compliance for six years following agreement termination—matching regulatory record retention requirements under 45 CFR 164.530(j).
Business Associate Agreement vs Other Legal Agreements
BAA vs Data Processing Agreement: Data Processing Agreements govern GDPR and broader data privacy obligations across all personal data categories. BAAs address exclusively HIPAA-regulated protected health information. Healthcare organizations operating internationally often require both agreements—DPAs covering European patient data and BAAs addressing US-based PHI.
BAA vs NDA: Business associate agreements serve a distinct legal purpose from non-disclosure agreements, protecting PHI under federal HIPAA regulations rather than general confidential information, and carrying significantly steeper penalties including potential criminal charges.
Enterprise procurement teams treat BAAs as non-negotiable baseline requirements rather than negotiable contract terms. Healthcare legal departments typically refuse to modify core BAA provisions addressing permitted uses, safeguard requirements, breach notification, or subcontractor obligations—provisions directly mandated by HIPAA regulations. Vendors proposing substantive BAA modifications signal either inexperience with healthcare compliance or unwillingness to accept standard market risk allocation, immediately slowing procurement cycles.
BAAs integrate into larger vendor risk management frameworks alongside security questionnaires, SOC 2 attestations, penetration test results, and business continuity documentation. Covered entities cannot legally share PHI without executing BAAs regardless of other security assurances—making BAA execution a hard gate in enterprise sales processes, not a parallel workstream.
Risks of Not Having a Business Associate Agreement
Operating without executed BAAs creates direct regulatory violations for both covered entities and business associates. The HHS website states that business associates are directly liable for the following HIPAA violations: Failure to provide the Secretary with records and compliance reports; cooperate with complaint investigations and compliance reviews. Covered entities sharing PHI with vendors lacking BAAs violate HIPAA's minimum necessary and administrative safeguard requirements—creating organizational liability regardless of actual data breaches.
Financial penalties for HIPAA violations without BAAs range from $100 to $50,000 per violation with annual maximums reaching $1.5 million per violation category. In September 2020, CHSPSC agreed to pay $2.3 million in penalties as part of the most recent enforcement action against a business associate by the Office for Civil Rights (OCR). The enforcement action stemmed from a 2014 data breach that impacted more than 6 million patients and 237 covered entities.
For enterprise-focused vendors, missing BAAs eliminate market access to healthcare customers. Procurement departments cannot approve vendor contracts lacking BAAs regardless of product differentiation, competitive pricing, or executive relationships. Sales cycles stop permanently—not temporarily—absent executed agreements. The reputational damage extends beyond individual deals: vendors unable to provide standard BAAs signal operational immaturity to healthcare buyers, creating persistent credibility deficits across the market segment.
How Enterprise Buyers Evaluate BAAs
Enterprise legal and compliance teams evaluate BAAs against HHS sample agreements published at 45 CFR 164.504(e), organizational risk tolerance, and standard healthcare contracting practices. Buyers scrutinize whether agreements address all mandatory provisions: permitted uses, prohibition on unauthorized disclosure, safeguard implementation, breach notification, individual access rights, PHI return or destruction, and subcontractor requirements.
Standard Clauses Buyers Rarely Change: Core HIPAA-mandated provisions including breach notification timelines, safeguard requirements, and audit rights typically remain non-negotiable. Healthcare organizations refuse to dilute regulatory obligations through contract modifications—maintaining standard language across all business associate relationships.
Red Flags That Slow Contract Approval: Vendors proposing liability caps below breach remediation costs, limiting indemnification for regulatory violations, restricting covered entity audit rights, or excluding subcontractor flow-down obligations trigger extended legal review. BAAs containing outdated regulatory citations, missing Security Rule references, or generic privacy language signal template neglect—requiring complete redrafting before approval.
Clean, current BAAs incorporating HHS model language and addressing common healthcare buyer concerns accelerate contract execution significantly. Standard vendor agreements typically require 80% legal involvement and take an average of 45 days to execute. Vendors presenting pre-negotiated BAAs aligned with standard market terms reduce legal review cycles from weeks to days—directly improving sales velocity and quarter-end pipeline conversion.
Best Practices for Vendors Handling BAAs
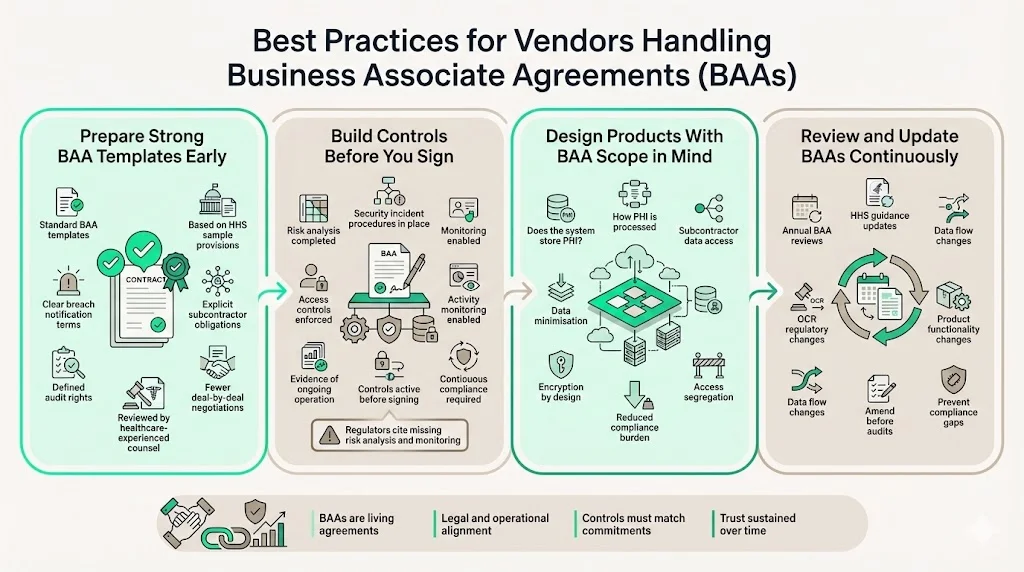
Enterprise-focused vendors should prepare standard BAA templates before engaging healthcare prospects. Templates should incorporate HHS sample provisions, address subcontractor obligations explicitly, define breach notification procedures clearly, and establish audit rights meeting enterprise buyer expectations. Having counsel experienced in healthcare transactions review templates before market deployment prevents recurring negotiation cycles across multiple deals.
Internal controls supporting BAA commitments require documented evidence: The OCR's audit revealed "longstanding, systemic noncompliance with the HIPAA Security Rule including failure to conduct a risk analysis, and failures to implement information system activity review, security incident procedures, and access controls." Vendors must implement risk analysis processes, security incident procedures, access controls, and activity monitoring before signing BAAs—not after customer requests. These controls require ongoing operation throughout customer relationships, not one-time implementation at contract signing.
Product design decisions directly impact BAA obligations. Architectural choices determining whether systems store PHI, how applications process health data, and what subcontractors require PHI access shape compliance complexity and operational risk. Engineering teams should evaluate data minimization opportunities, encryption implementation, and access segregation capabilities during product development—reducing downstream compliance burden.
When the scope of services changes, or when regulations update, your BAAs should be reviewed and amended accordingly. Review BAAs annually against current HHS guidance, following regulatory updates from the Office for Civil Rights, and whenever product functionality or data processing practices change materially. This proactive review cycle identifies compliance gaps before customer audits or regulatory investigations.
Conclusion
A Business Associate Agreement is a legally required HIPAA contract governing how third-party vendors handle protected health information on behalf of covered entities—establishing enforceable security obligations, defining permitted uses, and creating direct regulatory accountability. Understanding BAAs is essential for enterprise-focused companies because healthcare customers cannot legally share PHI without executed agreements, making BAAs non-negotiable prerequisites for market entry rather than negotiable contract terms. Organizations that prepare compliant BAA templates, implement supporting security controls, and maintain current agreements throughout customer relationships demonstrate operational maturity—accelerating deal velocity, reducing legal friction, and building long-term credibility with healthcare buyers who evaluate vendor compliance posture as carefully as product functionality.
Frequently Asked Questions (FAQs)
1. When is a BAA required?
A BAA is required whenever a vendor's services involve creating, receiving, maintaining, or transmitting protected health information on behalf of a covered entity. The triggering factor is PHI exposure capability—not actual access frequency, data volume, or vendor intent. Covered entities must execute BAAs before sharing any PHI with business associates, making agreement execution a prerequisite for service commencement rather than a parallel contracting workstream.
2. Who signs a business associate agreement?
Covered entities and business associates sign BAAs through authorized signers possessing contractual authority. For covered entities, authorized signers typically include compliance officers, legal counsel, or procurement executives with delegation authority. Business associates require officer-level or designated signatory authorization. Both parties must maintain executed originals for regulatory record retention—currently six years following relationship termination under HIPAA requirements.
3. What happens if a BAA is missing?
Missing BAAs create direct HIPAA violations for covered entities sharing PHI and business associates receiving PHI without contractual safeguards. Without it, Covered Entities may face regulatory fines, legal liability, and reputational harm if their vendors mishandle PHI. The Office for Civil Rights can impose financial penalties ranging from $100 to $50,000 per violation with annual maximums of $1.5 million per violation category. Beyond regulatory consequences, missing BAAs eliminate healthcare market access—procurement departments cannot approve vendor relationships lacking executed agreements regardless of other contract terms.
4. Does a BAA cover subcontractors?
BAAs establish flow-down obligations requiring business associates to obtain equivalent written assurances from subcontractors accessing PHI. Ensure your business associates maintain BAAs with their own subcontractors who handle PHI, as the subcontractor chain requirement is a commonly overlooked compliance gap that creates direct liability for the covered entity. Business associates remain directly liable to covered entities for subcontractor HIPAA violations—making subcontractor BAA management a critical vendor responsibility rather than a covered entity obligation.
5. How often should BAAs be reviewed?
Review BAAs annually as standard practice, following Office for Civil Rights regulatory updates, and whenever vendor service scope or data processing practices change materially. Regulatory changes requiring BAA amendments include new breach notification requirements, updated Security Rule technical specifications, or revised individual access rights. Product changes triggering BAA review include new subcontractor relationships involving PHI access, expanded data processing activities, or architectural modifications affecting where PHI is stored or transmitted. Proactive review cycles identify compliance gaps before customer audits expose them.



.svg)
.svg)
.svg)