The Cybersecurity Maturity Model Certification (CMMC) Program verifies contractors have implemented required security measures necessary to safeguard Federal Contract Information (FCI) and Controlled Unclassified Information (CUI). Within this ecosystem, the CMMC Assessor and Instructor Certification Organization (CAICO) serves a critical credentialing function: training, testing, authorizing, certifying, and recertifying CMMC assessors, instructors, and related professionals.
Most organizations treat CMMC as a procurement hurdle rather than a security imperative. This creates a fundamental gap between certification status and actual security posture—a gap that becomes apparent when assessors lack standardized qualifications or when organizations discover their third-party assessor cannot deliver the rigor required. Understanding CAICO's role clarifies how the CMMC ecosystem maintains assessment quality, why assessor credentials matter, and what organizations must expect when preparing for certification in 2026 and beyond.
This definition covers CAICO's statutory responsibilities, the CMMC framework structure, assessor certification paths, and practical implications for Defense Industrial Base (DIB) contractors and enterprise organizations pursuing security maturity.
What is CAICO: Role and Responsibilities
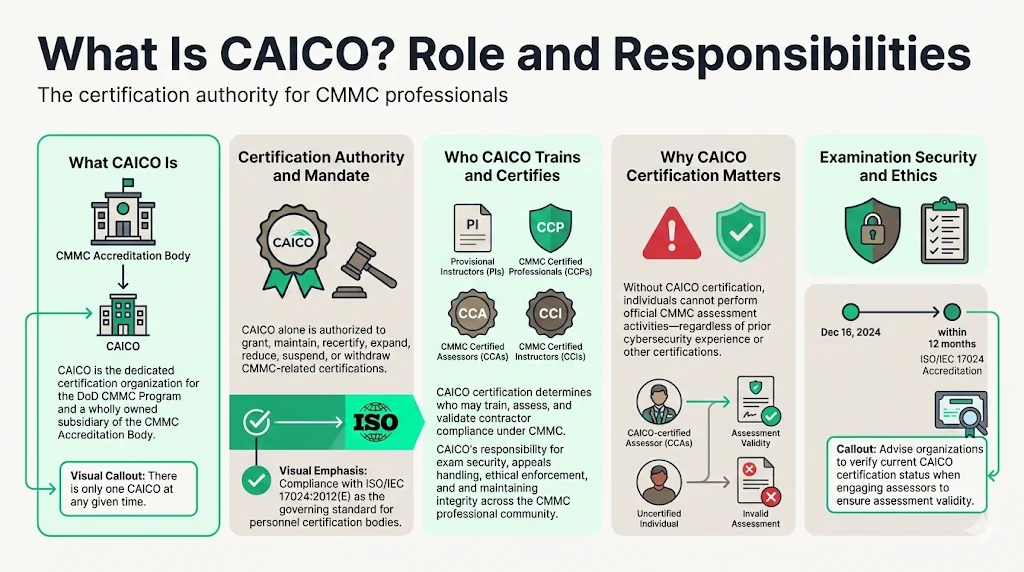
CAICO is responsible for training, testing, authorizing, certifying, and recertifying CMMC assessors, instructors, and related professionals. The CAICO is a wholly owned subsidiary of the CMMC Accreditation Body, operating as the dedicated certification organization for CMMC personnel. At any given point in time, there will be only one CAICO for the DoD CMMC Program.
CAICO's regulatory mandate extends beyond basic training coordination. Only the CAICO may make decisions relating to examination certifications, including the granting, maintaining, recertifying, expanding, and reducing the scope of certification, and suspending or withdrawing certification in accordance with current ISO/IEC 17024:2012(E). This compliance requirement ensures CAICO maintains international standards for personnel certification bodies—a critical foundation for assessment credibility.
CAICO trains, tests, designates Provisional Instructors (PIs), and certifies CMMC Certified Professionals (CCPs), CMMC Certified Assessors (CCAs), CMMC Certified Instructors (CCIs). These credentials establish who can participate in assessments, deliver training, and validate contractor compliance within the CMMC ecosystem. Without CAICO certification, individuals cannot perform official CMMC assessment activities—regardless of their cybersecurity experience or other industry certifications.
CAICO maintains examination security, administers appeals processes, and enforces ethical standards across the CMMC professional community. The CAICO must achieve and maintain ISO/IEC 17024(E) accreditation within 12 months of December 16, 2024—establishing a defined timeline for full operational maturity. Organizations engaging with CMMC assessors should verify current CAICO certification status, as credentials directly impact assessment validity.
What is CMMC: Overview and Purpose
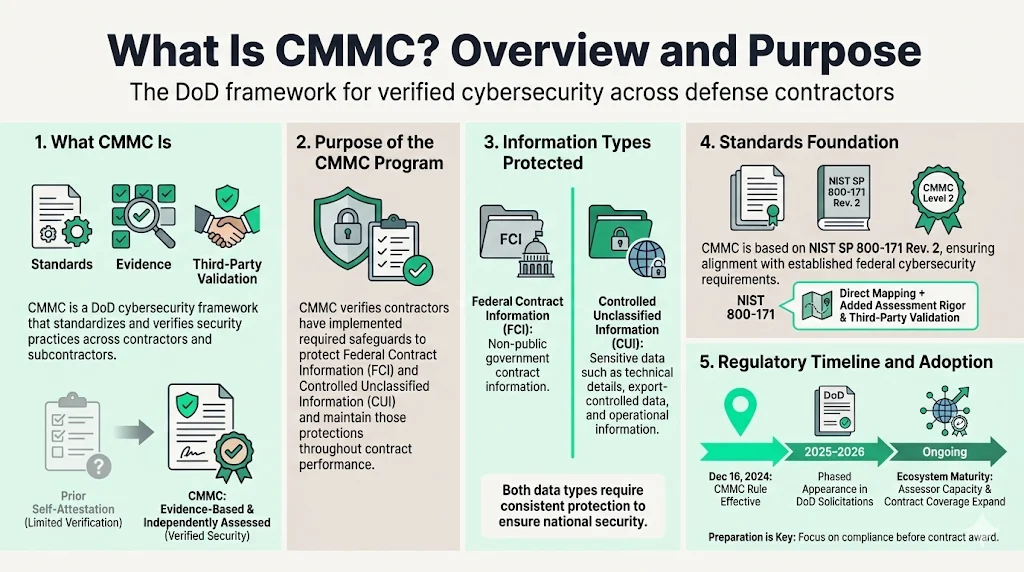
CMMC is a cybersecurity framework developed by the U.S. Department of Defense to standardize and verify security practices across defense contractors and their supply chains. Unlike previous self-attestation models, CMMC requires documented evidence of control implementation and—for most contractors handling sensitive information—independent third-party assessment.
The CMMC Program verifies contractors have implemented required security measures necessary to safeguard Federal Contract Information (FCI) and Controlled Unclassified Information (CUI), allowing the Department to confirm a defense contractor or subcontractor has implemented the security requirements for a specified CMMC level and is maintaining that status across the contract period of performance.
Federal Contract Information includes information provided by or generated for the government under contract that is not intended for public release. Controlled Unclassified Information encompasses a broader category of sensitive government information requiring safeguarding under federal law, regulation, or policy—including technical data, export-controlled information, and operational details that adversaries could exploit.
CMMC is based on National Institute Standards and Technology (NIST) 800-171r2, Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations. This alignment ensures CMMC requirements reflect established federal cybersecurity standards rather than creating parallel or conflicting control frameworks. Organizations already implementing NIST 800-171 controls will find direct mapping to CMMC Level 2 requirements, though CMMC adds assessment rigor and third-party validation not present in pure NIST compliance.
The CMMC rule is effective December 16, 2024, establishing the regulatory foundation for phased implementation across DoD contracts. Contractors should anticipate CMMC requirements appearing in solicitations throughout 2025 and 2026, with full ecosystem maturity expected as assessor capacity scales and contract requirements expand.
CMMC Levels: Structure and What They Mean for Contractors
CMMC employs a tiered approach reflecting different data sensitivity levels and corresponding security maturity requirements. The current framework defines three levels—Foundational, Advanced, and Expert—each aligned to specific information types and threat profiles.
Level 1 (Foundational) addresses basic cyber hygiene practices suitable for protecting Federal Contract Information. This level emphasizes fundamental security measures: access controls, physical security, system maintenance, and incident response basics. Level 1 generally permits annual self-assessment, allowing contractors to affirm compliance without third-party validation. Organizations handling only FCI—typically lower-tier subcontractors or those providing commercial off-the-shelf products—will likely fall into this category.
Level 2 (Advanced) encompasses the 110 security requirements derived from NIST 800-171, designed specifically for protecting Controlled Unclassified Information. This level represents the most common CMMC requirement for DIB contractors handling technical data, procurement-sensitive information, or operational details. Level 2 requires triennial third-party assessment conducted by CAICO-certified assessors working through Certified Third-Party Assessor Organizations (C3PAOs). The assessment observation period, evidence requirements, and control implementation documentation significantly exceed Level 1 expectations.
Level 3 (Expert) combines CMMC Level 2 practices with additional enhanced controls addressing advanced persistent threats and sophisticated adversaries. These supplementary requirements—drawn from NIST 800-172—focus on threat hunting, advanced malware detection, insider threat programs, and supply chain risk management. Level 3 applies to contractors handling the most sensitive CUI, particularly those supporting critical defense programs or advanced weapons systems. Government assessors typically conduct Level 3 certifications rather than commercial C3PAOs.
Contractors must determine their required CMMC level based on contract clauses specifying information types handled and assessment requirements. Prime contractors frequently flow down CMMC requirements to subcontractors, creating cascading compliance obligations throughout the supply chain. Organizations should identify their highest CMMC requirement across all contracts and subcontracts, as maintaining multiple certification levels proves operationally complex and economically inefficient.
CAICO's Role within the CMMC Ecosystem: Certification and Assessments
CAICO establishes the professional standards that ensure assessment consistency and technical competence across the CMMC ecosystem. The certification pathway involves structured training, examinations, background checks, and ongoing professional development requirements.
CMMC Certified Professional (CCP) represents the entry-level credential within the CMMC professional community. The CCP examination verifies a candidate's knowledge of the Department of Defense (DoD) CMMC framework and the roles and responsibilities of various positions within it. CCPs can support Level 1 self-assessments and participate in higher-level assessment teams but cannot serve as lead assessors or make final compliance determinations. The CCP credential demonstrates foundational CMMC knowledge—valuable for consultants, internal compliance staff, and organizations preparing for certification.
Certified CMMC Assessor (CCA) represents the professional certification required to conduct Level 2 assessments. A Certified CMMC Assessor (CCA) who successfully completes all certification program requirements as outlined by the CAICO will be authorized to work in an assessor capacity on Level 2 Assessments on behalf of a Certified Third-Party Assessor Organization (C3PAO). CCA certification requires CCP prerequisite completion, minimum of two years of full-time professional work experience in IT or cybersecurity as a minimum requirement to become a CMMC Certified Assessor, plus successful completion of advanced training and examination.
CMMC Certified Instructor (CCI) credentials authorize individuals to deliver official CAICO-approved training to aspiring assessors and professionals. CCIs must complete provisional instructor training, demonstrate teaching competency, and maintain subject matter expertise across CMMC domains. The instructor cadre directly impacts assessor quality—weak training produces assessors unable to evaluate complex security implementations or distinguish genuine controls from performative compliance.
CAICO manages ongoing professional requirements including recertification, continuing education, and ethics compliance. CMMC Ecosystem members must report to the CAICO within 30 days of convictions, guilty pleas, or no contest pleas to crimes of fraud, larceny, embezzlement, misappropriation of funds, misrepresentation, perjury, false swearing, conspiracy to conceal, or a similar offense—establishing accountability standards that protect assessment integrity.
Organizations selecting assessors or consultants should verify current CAICO certification through official channels. Expired credentials, lapsed certifications, or individuals claiming CMMC expertise without formal CAICO certification signal potential quality issues that could compromise assessment validity or contract eligibility.
Why This Matters for Companies Selling to Enterprise Clients: Compliance, Risk Management, Security Assurance

CMMC compliance extends beyond DoD contracting requirements into broader enterprise security expectations. Organizations demonstrating CMMC certification—or implementing equivalent controls—signal mature cybersecurity practices valuable to risk-conscious enterprise clients across industries.
Enterprise buyers increasingly evaluate supplier security posture before awarding contracts, particularly when suppliers access sensitive data, integrate with corporate networks, or support critical operations. CMMC provides a standardized assessment framework that reduces buyer evaluation burden while establishing verifiable security baselines. Companies certified at CMMC Level 2 demonstrate implementation of 110 security controls addressing access management, incident response, vulnerability management, configuration control, and data protection—capabilities directly relevant to supply chain risk management.
CAICO's role in standardizing assessor qualifications ensures CMMC certifications represent consistent evaluation rigor. This standardization benefits buyers who can trust that CMMC-certified suppliers underwent comparable assessment processes regardless of which C3PAO conducted the evaluation. Without CAICO's credentialing function, CMMC assessments would vary widely in quality, depth, and technical competence—undermining the framework's reliability as a security indicator.
Organizations pursuing CMMC compliance must recognize that certification represents continuous security operations rather than point-in-time achievement. CMMC Level 2 requires triennial reassessment, but the underlying NIST 800-171 controls demand ongoing maintenance: patch management, access reviews, security awareness training, incident response procedures, and vulnerability remediation. Companies treating CMMC as a periodic compliance project rather than sustained security discipline inevitably face rushed preparations, control degradation between assessments, and potential certification loss.
The investment required for CMMC compliance—estimated at 550-600 hours annually for organizations managing certification internally—reflects the comprehensive nature of required controls. Organizations can significantly reduce this burden through managed security services that implement controls, maintain evidence, and sustain audit readiness year-round. The choice between self-managed and supported compliance approaches affects both resource allocation and certification success probability.
Challenges and Considerations for Non-U.S. or Non-Defense Suppliers
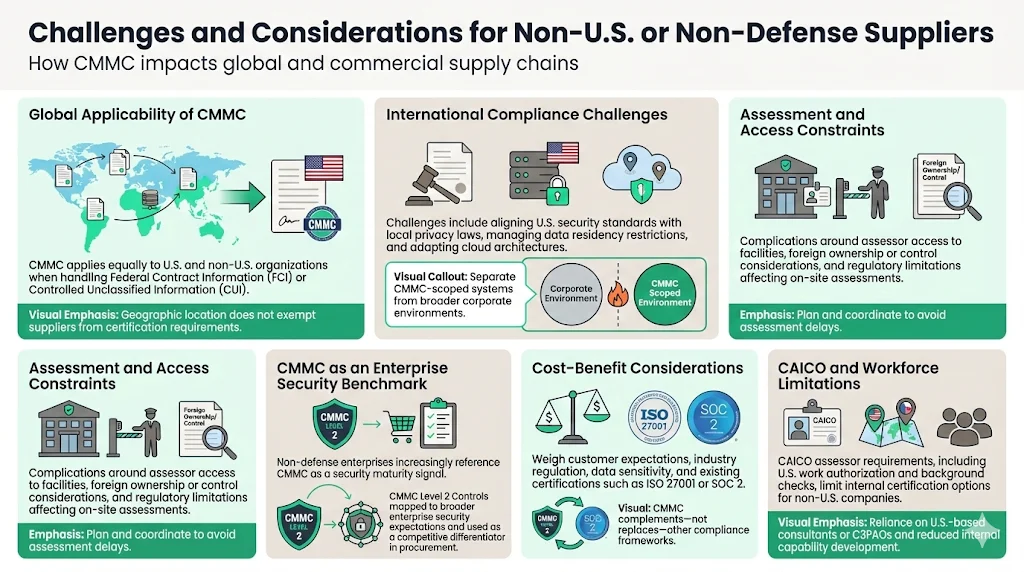
CMMC originates from the U.S. Department of Defense requirements, but its implications extend to international suppliers, commercial enterprises, and organizations outside traditional defense contracting. Companies headquartered abroad but participating in U.S. defense supply chains face identical CMMC requirements as domestic contractors—geography does not exempt organizations from certification when handling FCI or CUI.
International suppliers encounter specific challenges: aligning U.S.-origin security standards with local data protection regulations, navigating cloud service requirements when geographic data residency restrictions apply, and ensuring assessor access to facilities potentially subject to foreign ownership or control limitations. These complexities require careful planning, legal review, and potentially architectural adjustments to separate CMMC-scope systems from broader corporate infrastructure.
Non-defense enterprise clients increasingly reference CMMC as a security benchmark even when DoD contracts are not involved. Organizations seeking to demonstrate robust cybersecurity practices can map their controls to CMMC Level 2 requirements, undergo assessment by CAICO-certified professionals, and market their certification status to security-conscious buyers. This approach positions CMMC as a differentiator in competitive procurement environments where buyers lack standardized methods to evaluate supplier security maturity.
Companies outside the defense sector should evaluate whether CMMC certification provides competitive advantage sufficient to justify implementation costs. Factors include: customer security expectations, industry regulatory environment, data sensitivity handled, and existing compliance framework investments (ISO 27001, SOC 2, etc.). CMMC may complement rather than replace existing certifications, particularly when customers require multiple attestations or when control frameworks address different security domains.
The CAICO assessor prerequisite—requiring U.S. work authorization and background checks—creates barriers for international organizations seeking to develop internal CMMC expertise. Non-U.S. companies typically engage U.S.-based consultants or C3PAOs rather than certifying staff directly, increasing dependence on external resources and limiting internal capability development.
Practical Steps for a Company to Prepare for CAICO/CMMC Compliance
Organizations pursuing CMMC certification should approach preparation systematically, treating compliance as a security infrastructure project rather than documentation exercise.
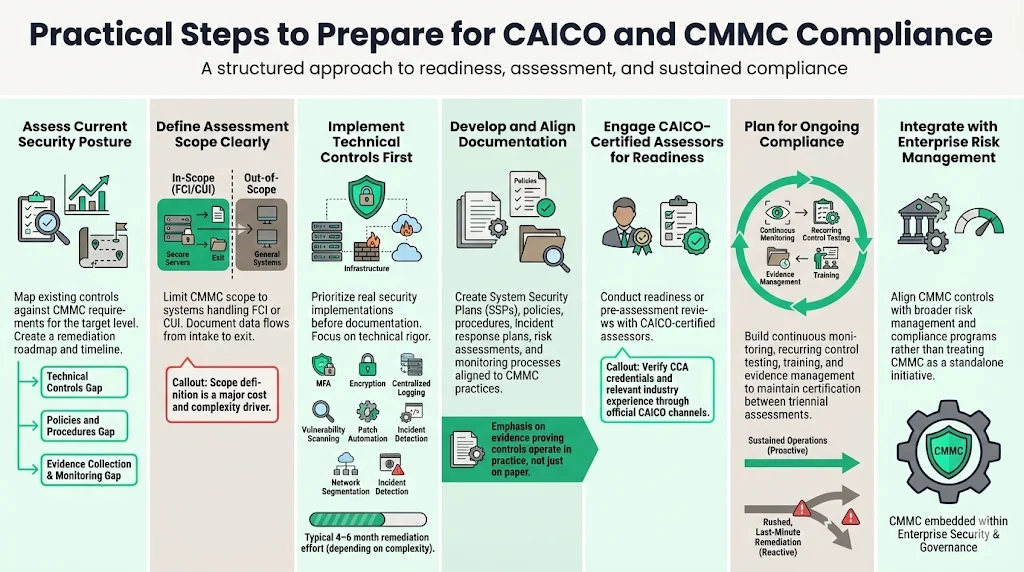
Conduct comprehensive security posture assessment. Map current controls against CMMC requirements for your target level. Identify gaps in technical implementation (missing encryption, inadequate access controls, absent logging), process documentation (policies, procedures, plans), and evidence collection systems. This assessment establishes the remediation roadmap and implementation timeline.
Define CMMC assessment scope boundaries. Contractors need not apply CMMC controls across the entire corporate infrastructure—only to systems processing, storing, or transmitting FCI or CUI. Clearly delineate in-scope systems, networks, and facilities. Document data flows showing where sensitive information enters, processes, stores, and exits your environment. Scope definition directly impacts implementation cost and operational complexity.
Address technical control gaps before documentation. CMMC assessors evaluate actual security implementations, not just written policies. Deploy missing technical controls: multi-factor authentication, encryption at rest and in transit, centralized logging, vulnerability scanning, patch management automation, network segmentation, and incident detection capabilities. Technical remediation typically requires 4-6 months depending on infrastructure complexity and resource availability.
Develop comprehensive documentation aligned to CMMC practice requirements. Document security policies, system security plans, configuration management processes, incident response procedures, risk assessment methodologies, and continuous monitoring activities. CMMC assessments require evidence demonstrating that documented procedures are actually followed—implement evidence collection systems that capture control execution without creating unsustainable manual processes.
Engage CAICO-certified assessors for readiness evaluation. Pre-assessment reviews identify gaps assessors will flag during official certification, allowing remediation before formal evaluation. Verify assessor credentials through official CAICO channels. Confirm the C3PAO or consulting firm employs CCAs with relevant experience in your industry and technology environment.
Plan for sustained compliance rather than point-in-time certification. Establish continuous monitoring, periodic control testing, ongoing security awareness training, and evidence management processes that maintain certification between triennial assessments. Organizations that sustain security operations year-round experience significantly smoother recertification compared to those implementing rushed pre-assessment remediation cycles.
Align CMMC implementation with broader risk management strategy. CMMC controls address specific federal requirements, but security investments should support comprehensive risk reduction across threat vectors, data types, and business operations. Integrate CMMC into existing governance, risk management, and compliance frameworks rather than treating it as an isolated initiative.
Conclusion
CAICO serves as the quality assurance mechanism within the CMMC ecosystem, ensuring that assessors possess standardized qualifications and that certifications reflect consistent evaluation rigor. CAICO's responsibility for training, testing, authorizing, certifying, and recertifying CMMC assessors, instructors, and related professionals, combined with its status as the singular credentialing organization, establishes accountability for assessment quality across the Defense Industrial Base.
Organizations serving enterprise clients—particularly those handling sensitive data or operating in regulated industries—should recognize CMMC as more than DoD-specific compliance requirement. The framework represents a standardized approach to cybersecurity maturity valuable for demonstrating security capabilities to risk-conscious buyers. Companies that implement CMMC controls as genuine security infrastructure rather than performative compliance achieve both certification objectives and actual risk reduction.
The phased CMMC implementation beginning in 2025-2026 creates urgency for defense contractors while providing a proven framework that commercial enterprises can adopt voluntarily. Organizations that treat CMMC compliance as an integrated component of comprehensive security strategy—rather than isolated regulatory obligation—position themselves advantageously in procurement environments where cybersecurity posture increasingly determines contract eligibility.
Frequently Asked Questions
1) What is a CAICO?
The Cybersecurity Assessor and Instructor Certification Organization (CAICO) is the nonprofit organization responsible for training, testing, and certifying professionals within the CMMC ecosystem. CAICO operates as a wholly owned subsidiary of the CMMC Accreditation Body, serving as the exclusive credentialing organization for CMMC assessors, instructors, and professionals. CAICO ensures assessment quality and standardization across the Defense Industrial Base by maintaining professional certification standards aligned to ISO/IEC 17024 requirements.
2) What is a CMMC CCP (Certified CMMC Professional)?
The CCP examination verifies a candidate's knowledge of the Department of Defense (DoD) CMMC framework and the roles and responsibilities of various positions within it. CCP represents the entry-level credential for CMMC professionals. CCPs can support Level 1 self-assessments and participate in assessment teams but cannot serve as lead assessors or make final compliance determinations. The CCP credential serves as a prerequisite for advancing to Certified CMMC Assessor (CCA) certification.
3) What is a CMMC CCA (Certified CMMC Assessor)?
A Certified CMMC Assessor (CCA) who successfully completes all certification program requirements as outlined by the CAICO will be authorized to work in an assessor capacity on Level 2 Assessments on behalf of a Certified Third-Party Assessor Organization (C3PAO). CCA certification requires CCP prerequisite completion, minimum two years of professional IT or cybersecurity experience, advanced CAICO training, and successful examination. CCAs conduct the third-party assessments that determine contractor CMMC compliance for most DIB organizations.
4) What are CMMC and CUI?
CMMC (Cybersecurity Maturity Model Certification) is a DoD framework verifying that defense contractors implement required cybersecurity controls to protect sensitive information. Controlled Unclassified Information (CUI) is government-created or government-owned information requiring safeguarding under federal law, regulation, or policy. CUI includes technical data, export-controlled information, procurement-sensitive details, and operational information that adversaries could exploit. CMMC Level 2 specifically addresses CUI protection through 110 security requirements derived from NIST 800-171, requiring triennial third-party assessment by CAICO-certified assessors.
5) What is the difference between CCA and CCP in CMMC?
CMMC Certified Professional (CCP) represents entry-level certification demonstrating foundational CMMC knowledge, while Certified CMMC Assessor (CCA) represents advanced certification authorizing individuals to conduct official Level 2 assessments. CCPs can support assessments and verify Level 1 practices but cannot make final compliance determinations or lead assessments. CCAs possess assessment authority, can serve as lead assessors for C3PAOs, and conduct the evaluations determining contractor certification status. CCP certification serves as a mandatory prerequisite for pursuing CCA credentials.



.svg)
.svg)
.svg)