Most organizations attempting to secure defense contracts approach CMMC compliance as an isolated certification event. This creates a fundamental gap between audit performance and operational cybersecurity maturity—a gap that becomes immediately apparent when assessors review actual control implementation rather than documentation alone. CMMC Level 2 certification is now required for contractors handling Controlled Unclassified Information (CUI) for the Department of Defense, with most contracts involving CUI requiring full Level 2 certification from a Certified Third Party Assessment Organization (C3PAO) starting in late 2025. At the center of this assessment process stands the Certified CMMC Assessor (CCA)—the credentialed professional authorized to evaluate whether organizations meet stringent federal security requirements.
What is the CMMC Framework?
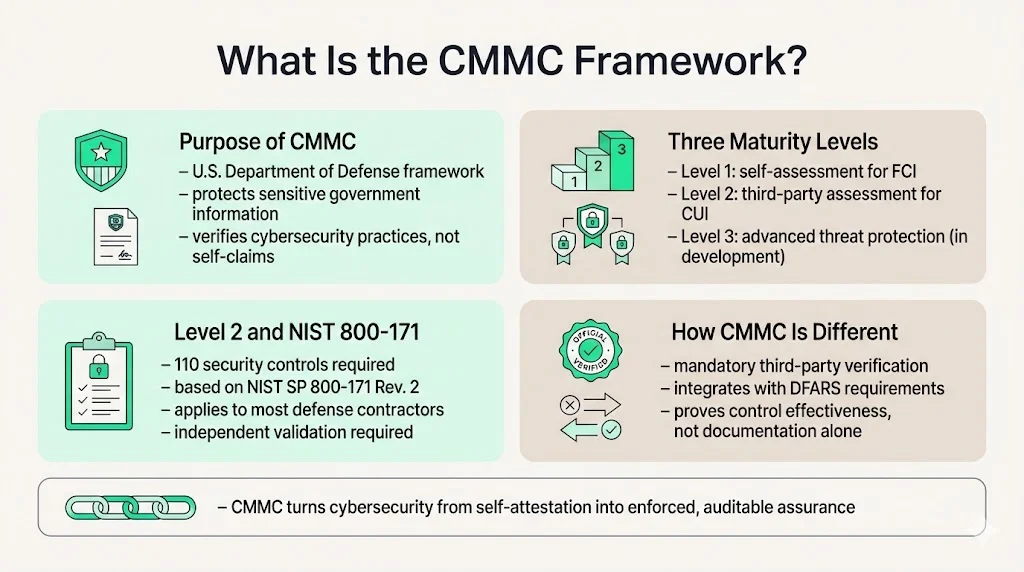
The Cybersecurity Maturity Model Certification (CMMC) is the Department of Defense's standardized approach to verifying that defense contractors implement adequate cybersecurity protections for sensitive government information. CMMC Level 2 requires organizations to prove they meet all 110 controls in NIST SP 800-171 Revision 2, moving beyond self-attestation to independent third-party verification.
CMMC establishes three levels of cybersecurity maturity. Level 1 permits self-assessment for contractors handling Federal Contract Information (FCI). Level 2—where most defense contractors operate—requires third-party assessment against NIST SP 800-171 security requirements for organizations processing, storing, or transmitting CUI. Level 3, still under development, will address Advanced Persistent Threat protection for the most sensitive programs.
This framework integrates with existing regulatory requirements including DFARS 252.204-7012 and NIST standards, but adds mandatory verification through independent assessment. The distinction matters: documentation claiming compliance differs fundamentally from demonstrated control effectiveness validated by trained assessors.
Who is a Certified CMMC Assessor (CCA)?
A Certified CMMC Assessor (CCA) is a certified individual authorized to perform formal CMMC Level 2 assessments within the Department of Defense's cybersecurity ecosystem, equipped with advanced skills to evaluate evidence, validate security controls, conduct interviews, and determine whether organizations handling CUI meet CMMC Level 2 requirements.
The CCA designation represents the official credential—not "auditor," which remains informal industry terminology. CCAs may only conduct assessments as part of a C3PAO's official assessment team and must comply with strict security, conduct, and confidentiality obligations. This distinction matters operationally: CCAs cannot conduct independent assessments outside the C3PAO structure.
CCAs differ fundamentally from CMMC Certified Professionals (CCPs). A CCP can participate on CMMC Level 2 Certification Assessments with CCA oversight, however CCAs are responsible for making final assessment determinations. The CCP credential serves as a prerequisite to CCA certification, qualifying individuals to provide consulting and advisory services but not to lead formal assessments or render certification determinations.
Why CCAs Matter for Enterprise & Defense Contractors
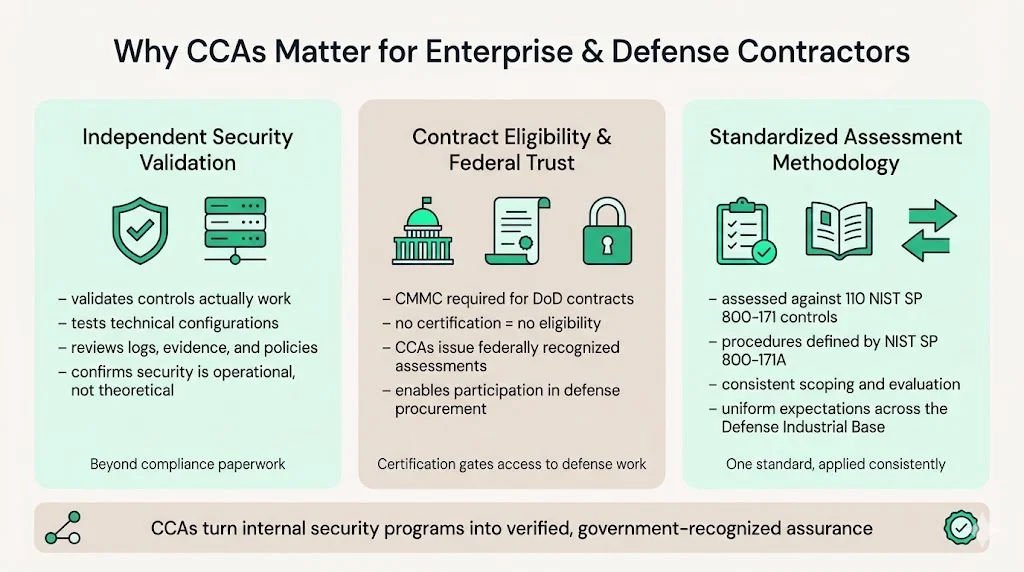
CCAs play a central role in national security, ensuring defense contractors properly protect Controlled Unclassified Information (CUI). Beyond compliance theater, CCAs validate that implemented controls actually function as documented—testing technical configurations, reviewing evidence trails, and verifying that security policies translate into operational practice.
CMMC certification increasingly determines contract eligibility. Organizations without valid certification face exclusion from procurement opportunities, regardless of technical capabilities or past performance. CCAs provide the independent verification that transforms internal security programs into federally recognized certifications, enabling contractors to compete for and maintain defense work.
CCAs assess defense contractors against the 110 security requirements from NIST SP 800-171, using assessment procedures defined in NIST SP 800-171A, in alignment with assessment processes and scoping requirements. This methodology ensures consistent evaluation across the Defense Industrial Base, creating standardized security expectations rather than variable interpretations of compliance obligations.
What a CCA Does During a CMMC Assessment
CMMC assessments follow structured methodology combining documentation review, technical validation, and organizational interviews. CCAs examine evidence artifacts demonstrating control implementation—configuration files, access logs, policy documents, training records, incident response procedures, and system inventories.
Technical control testing verifies that documented policies actually constrain system behavior. CCAs validate access controls by testing authentication mechanisms, review encryption implementation across data stores and transmission channels, examine vulnerability management processes through scan results and remediation tracking, and verify that logging captures security-relevant events.
Policy and procedure evaluation confirms that documented processes align with NIST requirements while remaining operationally realistic for the organization's environment. CCAs interview personnel at multiple organizational levels—system administrators, security leads, executives, and end users—to verify that documented procedures reflect actual practice rather than aspirational documentation.
Assessment outcomes include compliance scoring against required controls, identification of gaps requiring remediation, and formal recommendations regarding certification. Organizations scoring 88 or higher with only certain items remaining open may receive Conditional Certification, requiring closure of these items within 180 days, with certification lasting 3 years and yearly affirmations required.
CCAs maintain strict objectivity during formal assessments. They evaluate control implementation without providing remediation guidance—a separation ensuring assessment independence and preventing conflicts of interest that would compromise certification validity.
How to Become a Certified CMMC Assessor
To earn the CCA credential, candidates must hold a CMMC Certified Professional (CCP) Certification, as the CCP credential is a prerequisite. This foundational requirement ensures CCAs understand CMMC framework fundamentals, regulatory context, and assessment terminology before conducting formal evaluations.
CCAs must have at least 3 years of cybersecurity experience and at least 1 year of audit or assessment experience. This experience requirement ensures assessors understand both security control implementation and evaluation methodologies—theoretical knowledge alone proves insufficient for validating complex technical environments.
Candidates must hold at least one certification aligned to the Intermediate or Advanced Proficiency Level of DoD Cyber Workforce Framework's Work Role 612: Security Control Assessor. Acceptable certifications include CISSP, CISA, or equivalent credentials demonstrating assessment competency aligned with federal workforce standards.
Candidates must complete a CCA training course from an Approved Training Provider (ATP) and pass the CMMC Certified Assessor (CCA) exam. Training covers four domains: evaluating organizations against CMMC Level 2 requirements, assessment scoping methodology, the CMMC Assessment Process, and assessing CMMC Level 2 practices.
CCAs must complete a Tier 3 background investigation or equivalent, ensuring assessors accessing sensitive contractor environments meet federal security clearance standards. This requirement reflects the sensitive nature of information CCAs encounter during assessments—including proprietary technical architectures, security configurations, and vulnerability data.
Certification maintenance requires ongoing professional development, adherence to ethical standards established by the CMMC Accreditation Body, and periodic recertification to maintain currency with evolving requirements.
CCAs Within the CMMC Ecosystem
The CCA course is a requirement for becoming an assessor for CMMC Third Party Assessment Organizations (C3PAOs). C3PAOs represent accredited organizations authorized to conduct official CMMC assessments, while CCAs represent individual professionals certified to perform assessment activities within those organizations.
Each assessment must include, at minimum, a Lead CMMC Certified Assessor (Lead CCA) and a CMMC Certified Assessor (CCA), with an additional CCA fulfilling a quality assurance role. This team structure ensures adequate expertise, prevents individual assessor bias, and provides quality control throughout the evaluation process.
Lead CCAs carry additional responsibilities and qualification requirements beyond standard CCA credentials, including extended experience thresholds and demonstrated leadership capabilities. Organizations seeking certification engage C3PAOs—not individual CCAs—for assessment services, with the C3PAO then deploying credentialed assessment teams including CCAs and Lead CCAs.
This organizational structure maintains assessment quality through institutional oversight, standardized methodologies, and accountability mechanisms that wouldn't exist with independent assessor models. C3PAOs undergo their own accreditation processes, ensuring organizational capabilities match individual assessor credentials.
Choosing the Right Assessor & Assessment Partner
Selecting a C3PAO requires evaluating organizational experience beyond individual assessor credentials. Organizations with extensive Defense Industrial Base assessment history understand contractor operational realities, industry-specific technical environments, and common implementation challenges that generic assessors miss.
Technical expertise depth matters significantly. C3PAOs employ assessors with hands-on implementation experience—not merely audit backgrounds—better understand realistic control implementation within resource-constrained environments. Assessors who have configured access controls, implemented encryption, and managed vulnerability remediation bring operational perspective that purely compliance-focused evaluators lack.
Communication style and scheduling flexibility impact assessment efficiency substantially. Most companies take 6 to 12 months and spend about 150 thousand to 450 thousand dollars to get ready for CMMC certification. C3PAOs offering pre-assessment consultations, readiness reviews, and gap analysis services help organizations invest remediation resources efficiently rather than discovering critical deficiencies during formal assessment.
Pre-assessment evaluations—whether mock assessments or readiness reviews—identify gaps before formal certification attempts, reducing failure risk and avoiding costly re-assessments. Organizations treating pre-assessment as an unnecessary cost frequently encounter unexpected deficiencies during formal evaluation, extending timelines and increasing total certification expenditure.
Preparing Your Business for a CCA-Led Assessment
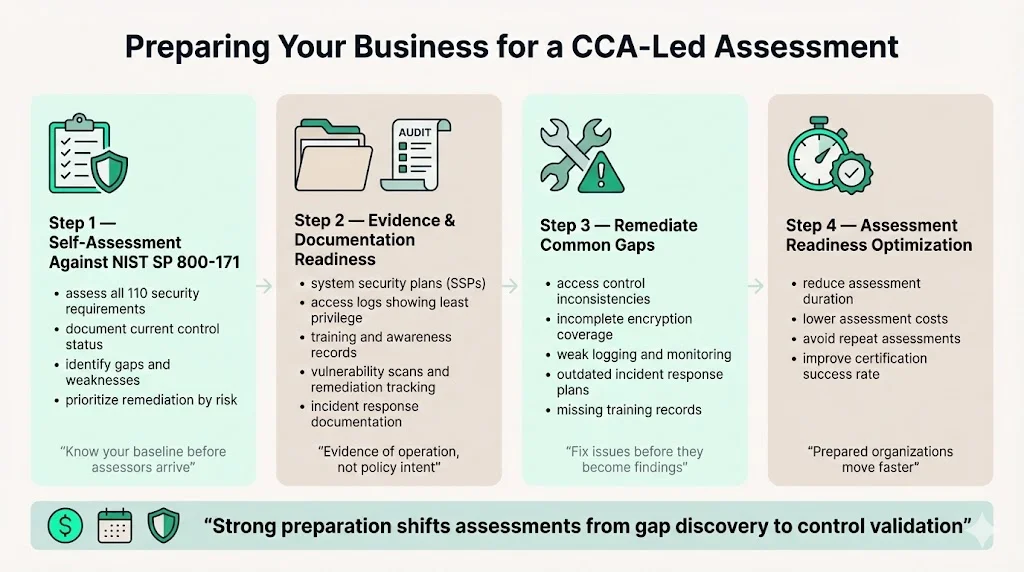
Internal preparation begins with systematic self-assessment against NIST SP 800-171 control requirements. Organizations should evaluate current implementation against each of the 110 security requirements, documenting control status, identifying gaps, and prioritizing remediation based on risk and implementation complexity.
Documentation organization proves critical during assessment. CCAs require evidence demonstrating control effectiveness over time—not merely policy documents claiming compliance. Organizations should compile configuration documentation, access logs demonstrating least privilege enforcement, training records proving security awareness, vulnerability scan results with remediation tracking, incident response documentation, and system security plans detailing technical architecture.
Addressing gaps in security controls and policies before formal assessment reduces assessment duration and improves certification likelihood. Common deficiencies include incomplete access control implementation, inadequate encryption coverage, insufficient logging and monitoring, incomplete security awareness training documentation, and missing or outdated incident response procedures.
Readiness preparation reduces assessment costs by minimizing assessor time spent identifying obvious deficiencies. Organizations entering formal assessment with documented control implementation and organized evidence allow assessors to focus on validation rather than gap identification, accelerating the assessment timeline and reducing associated costs.
The Business Value of CMMC Certification in 2026
CMMC certification creates competitive differentiation within defense contracting markets. As certification requirements expand across DoD contracts, certified organizations gain preferential positioning for contract awards while uncertified competitors face systematic exclusion from procurement opportunities.
Certification demonstrates cybersecurity posture to enterprise clients beyond DoD. Organizations requiring vendor risk assessments increasingly recognize CMMC certification as validated security maturity rather than accepting self-reported compliance claims. Third-party certification reduces due diligence burdens for enterprise buyers while providing standardized security benchmarking.
According to DoD projections, 76,598 organizations will require CMMC Level 2 Certification assessment every three years, equating to roughly 25,532 C3PAO-led certification assessments per year during the seven-year rollout period. This assessment volume represents the scale of compliance obligation facing the Defense Industrial Base, creating both market pressure for certification and demand for qualified assessment services.
CMMC certification improves organizational audit resilience and risk management maturity. The control implementation, documentation discipline, and evidence collection practices required for CMMC certification strengthen overall security operations—reducing incident likelihood, improving detection capabilities, and accelerating response effectiveness when security events occur.
Conclusion
Certified CMMC Assessors represent the independent validation mechanism ensuring defense contractors implement genuine security controls rather than performative compliance documentation. CCAs combine technical expertise, assessment methodology, and regulatory knowledge to evaluate whether organizations handling sensitive government information meet federal security standards.
Organizations pursuing CMMC certification engage C3PAOs employing credentialed CCAs to conduct formal assessments—understanding this credential as evidence of assessor qualification and regulatory authorization. The CCA role extends beyond documentation review to technical validation, ensuring that security controls actually function as documented and that organizational security maturity matches certification claims.
As CMMC requirements expand across defense contracts, understanding the CCA role, assessment methodology, and preparation requirements becomes essential for contractors maintaining DoD eligibility and enterprise competitiveness.
FAQs
1) What is a Certified CMMC Assessor?
A Certified CMMC Assessor (CCA) is a credentialed cybersecurity professional authorized to conduct formal CMMC Level 2 assessments as part of C3PAO assessment teams, evaluating whether defense contractors properly implement NIST SP 800-171 security controls and meet federal requirements for handling Controlled Unclassified Information.
2) Do all contractors need a CCA?
Contractors requiring CMMC Level 2 certification must engage C3PAOs employing CCAs for third-party assessment. Level 1 permits self-assessment without CCA involvement. Most defense contractors handling CUI require Level 2 certification, making CCA-led assessment mandatory for contract eligibility.
3) What does a CCA do during an assessment?
CCAs evaluate control implementation through evidence review, technical control testing, policy and procedure examination, and personnel interviews. They validate that documented security controls actually function as claimed, identify gaps requiring remediation, and determine whether organizations meet certification requirements based on objective assessment criteria.
4) How is a CCA different from a C3PAO?
A CCA represents an individual professional credential authorizing participation in CMMC assessments. A C3PAO represents an accredited organization authorized to conduct official CMMC assessments. CCAs work as employees or contractors of C3PAOs—organizations seeking certification engage C3PAOs, which deploy credentialed CCA teams to perform assessment activities.
5) How long does it take to become a CCA?
The timeline varies based on the candidate 's background. Prerequisites include active CCP certification, 3 years cybersecurity experience, 1 year audit experience, DoD-aligned baseline certification, ATP-provided training, exam passage, and Tier 3 background investigation completion. Candidates meeting experience requirements typically complete training and examination within 3-6 months, with background investigation adding several additional months.



.svg)
.svg)
.svg)