Most organizations pursuing Department of Defense contracts treat cybersecurity compliance as a procurement obstacle rather than a strategic capability. This creates a fundamental vulnerability—security posture that satisfies contracting officers on paper while leaving systems exposed to increasingly sophisticated threats targeting the Defense Industrial Base.
Understanding the Cybersecurity Maturity Model Certification ecosystem requires navigating a complex network of roles, assessments, and certification authorities. Among these, the Certified CMMC Professional (CCP) serves as a foundational credential for organizations building internal compliance capabilities and individuals positioning themselves within the defense cybersecurity landscape.
This article examines what a CCP is, how the role functions within the CMMC ecosystem, and why organizations selling to enterprise or defense clients should consider CCP certification as part of their broader security and compliance strategy through 2026 and beyond.
What is Cybersecurity Maturity Model Certification (CMMC)
The Department of Defense introduced CMMC 2.0, reducing the framework to three levels, aligned with existing NIST standards, and introducing the possibility of self-assessment for Level 1 and some Level 2 contracts. The program addresses a persistent reality: conventional contractual cybersecurity requirements lacked verification mechanisms, allowing contractors to attest compliance without demonstrating actual security controls.
CMMC applies to defense contractors and subcontractors handling Federal Contract Information (FCI) or Controlled Unclassified Information (CUI). An amendment to the DFARS went into effect November 10, 2025, officially mandating that all Defense Department solicitations and contracts include requirements for Cybersecurity Maturity Model Certification 2.0. Phase 2 will begin one year after the start of Phase 1 (November 10, 2026), at which point most organizations handling CUI will require third-party certification assessments.
The CMMC structure establishes three certification levels:
- Level 1 requires implementation of 17 basic cybersecurity practices derived from FAR 52.204-21, protecting Federal Contract Information through foundational safeguards. Organizations self-assess annually with senior leadership affirmation.
- Level 2 mandates implementation of all 110 controls in NIST SP 800-171 Revision 2 for organizations handling Controlled Unclassified Information. Level 2 requires a third-party assessment from a CMMC 3rd Party Assessment Organization (C3PAO), where a Cyber AB authorized assessor will evaluate cybersecurity practices to ensure they meet the necessary security requirements.
- Level 3 applies to organizations supporting the most critical national security programs, requiring implementation of NIST SP 800-172 controls and government-led assessments. Contractors seeking Level 3 certification will need to achieve a CMMC Level 2 Certificate of Status first to demonstrate their eligibility.
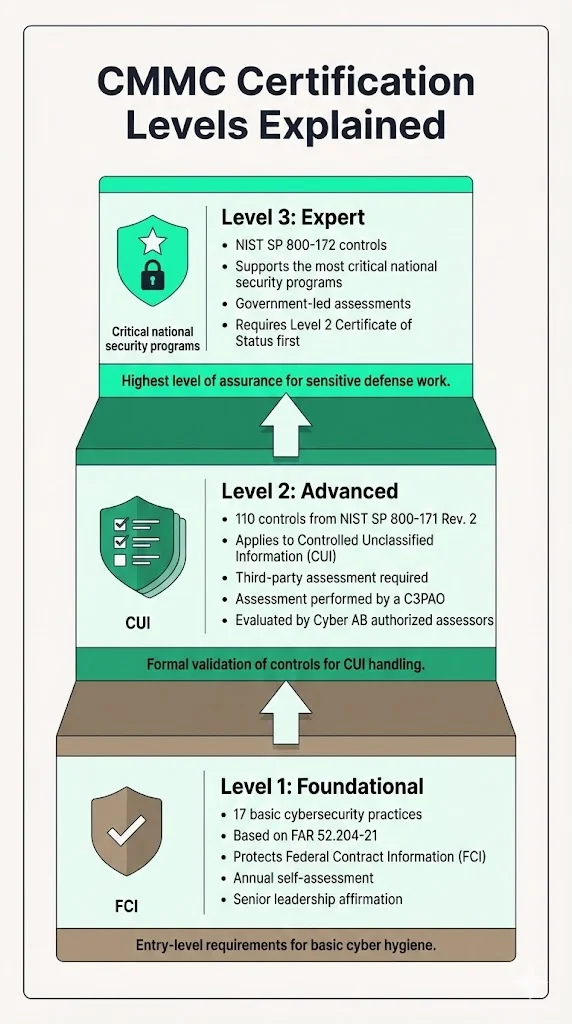
The certification structure reflects a fundamental principle: compliance requirements should scale proportionally to the sensitivity of information handled and the criticality of defense programs supported.
Who is a Certified CMMC Professional (CCP) and what does the role involve
A Certified CMMC Professional represents the entry-level certification within the CMMC ecosystem—individuals who have completed formal training on the CMMC framework, assessment methodology, and implementation requirements. CCPs possess documented knowledge of CMMC architecture, control requirements, scoping principles, and assessment processes, verified through examination and credentialing by the Cyber Accreditation Body (Cyber AB).
The CCP credential serves two primary constituencies: organizations building internal CMMC readiness capabilities and individuals establishing careers in defense cybersecurity compliance. Unlike Certified CMMC Assessors (CCA), CCPs cannot conduct official CMMC assessments or issue certifications. The distinction matters considerably—CCPs function as knowledgeable practitioners and preparation specialists, not authorized auditors.
Within the CMMC ecosystem, several distinct roles operate:
- Certified CMMC Assessors (CCA) conduct official CMMC assessments under C3PAO authorization, evaluating organizations against CMMC requirements and contributing to certification decisions. CCAs undergo more extensive training, demonstrate practical assessment experience, and meet higher qualification standards than CCPs.
- Certified CMMC Professionals (CCP) support organizations preparing for CMMC assessments through gap analysis, remediation planning, documentation development, and internal readiness activities. CCPs may participate in assessment teams for specific activities but cannot make certification determinations.
- Registered Practitioners (RP) and Registered Practitioner Organizations (RPO) assist organizations with CMMC preparation through consulting, implementation support, and advisory services. The RP credential demonstrates CMMC knowledge without assessment authorization.
CCP responsibilities typically include:
Conducting internal readiness assessments to identify gaps between current security posture and CMMC requirements across relevant control domains. This involves examining existing security controls, documentation, policies, and technical implementations against the 110 NIST SP 800-171 requirements for Level 2 or the 17 practices for Level 1.
Developing System Security Plans, Policies and Procedures, and Plans of Action and Milestones documentation required for CMMC assessment. Evidence collection and documentation often consume 200-400 hours for organizations lacking mature security programs—CCP knowledge helps structure this effort efficiently.
Guiding scoping activities to properly classify information systems, data flows, and security boundaries. Proper scoping directly impacts assessment cost, timeline, and ongoing maintenance burden. Organizations frequently over-scope environments, subjecting unnecessary systems to CMMC requirements and increasing compliance costs by 30-50%.
Supporting remediation planning by mapping identified gaps to specific technical, administrative, and physical controls, then establishing implementation roadmaps with realistic timelines and resource requirements.
Training internal teams on CMMC requirements, control objectives, evidence requirements, and maintenance obligations. Sustainable compliance requires broad organizational understanding, not isolated security team knowledge.
Why CCP matters for companies selling to enterprise / defense-oriented clients
Organizations pursuing defense contracts face a fundamental credibility gap: asserting cybersecurity maturity without demonstrated expertise or formal credentials. Enterprise clients—particularly those managing defense programs or handling sensitive government data—increasingly scrutinize subcontractor and vendor security postures before contract award.
Having CCP-credentialed staff demonstrates institutional commitment to CMMC compliance beyond contractual obligation. It signals that an organization has invested in formal knowledge transfer, understands assessment expectations, and maintains internal capabilities for ongoing compliance management. This distinction matters when enterprise clients evaluate vendor risk and compliance readiness.
CCP expertise enables proactive compliance preparation rather than reactive remediation. Most companies take 6 to 12 months and spend about 150 thousand to 450 thousand dollars to get ready for CMMC Level 2 certification. Organizations approaching CMMC without internal expertise consistently underestimate scope complexity, documentation requirements, and technical control gaps—leading to failed assessments, extended timelines, and budget overruns.
CCPs help organizations avoid common pitfalls that delay certification:
1) Improper scoping that includes out-of-scope systems or fails to adequately protect CUI processing environments. Assessors identify scoping errors in approximately 40% of initial assessment attempts, requiring re-scoping and additional preparation time.
2) Incomplete documentation that lacks required detail, fails to map controls to actual implementations, or contains inconsistencies between policies and operational reality. System Security Plans averaging 150-200 pages must accurately reflect technical architecture, data flows, and control implementations.
3) Control implementation gaps where organizations believe they've satisfied requirements but lack evidence demonstrating effectiveness over time. CMMC requires documented proof of controls operating consistently, not aspirational policies.
4) Inadequate evidence collection systems that cannot efficiently produce artifacts demonstrating control effectiveness during assessment. Organizations struggle to retroactively compile evidence—CCPs establish evidence collection processes before assessment preparation begins.
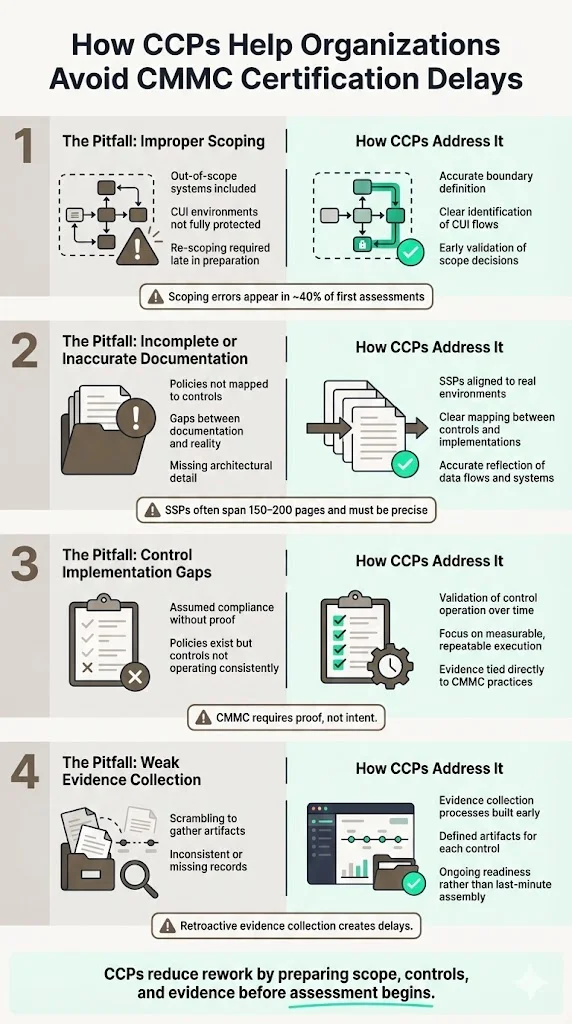
For vendors and subcontractors handling CUI within defense supply chains, CCP-trained personnel reduce dependence on external consultants for routine compliance activities. While organizations typically engage C3PAOs for official assessments and may utilize RPOs for major remediation projects, internal CCP expertise handles ongoing compliance management, internal audits, and maintenance activities consuming 75-150 hours annually.
How to become a CCP — requirements, process, and effort involved
Obtaining CCP certification requires completing a structured training program through a Cyber AB-authorized Licensed Training Provider (LTP) or Authorized Training Provider (ATP), passing the CCP examination, and completing the credential application process including background verification.
Prerequisites for CCP candidacy include foundational familiarity with cybersecurity principles, though formal IT security certifications are not mandatory. Ideal candidates possess experience with information security concepts, risk management frameworks, compliance documentation, or technical security controls. Organizations frequently send IT managers, security engineers, compliance officers, or operations personnel for CCP training.
The certification process follows these stages:
Training enrollment: Candidates register for a CCP training course through an authorized provider. Training typically spans 5 days in instructor-led format or equivalent hours in virtual delivery. Course content covers CMMC ecosystem structure, assessment methodology, control requirements, scoping principles, and documentation standards.
Examination: Upon completing training, candidates take the CCP examination administered by Cyber AB. The exam tests knowledge across multiple domains including CMMC architecture, assessment processes, code of professional conduct, governance structures, and control evaluation methodology. Passing requires demonstrating comprehensive understanding of CMMC framework components and assessment principles.
Application and background verification: Successful examinees submit formal applications to Cyber AB including required documentation and background check authorization. The background investigation typically involves a Tier 3 personnel security review, examining criminal history, employment verification, and other factors establishing trustworthiness for handling sensitive assessment information.
Credential issuance: Upon satisfactory completion of all requirements, Cyber AB issues the CCP credential, authorizing the individual to represent themselves as a Certified CMMC Professional.
The complete process—from training enrollment through credential issuance—typically requires 2-6 months depending on background check processing times and application review cycles. The training itself represents approximately 40 hours of intensive instruction, with additional study time for examination preparation.
CCP certification requires periodic renewal to maintain active status. Renewal typically involves demonstrating continued professional engagement with CMMC through activities such as continuing education, participation in CMMC community events, or ongoing professional practice. Annual renewal fees apply, though specific amounts vary based on Cyber AB fee schedules.
Organizations should anticipate total costs including training fees (typically $2,500-$4,000 per person), examination fees, initial application costs, and annual renewal fees. While not insignificant, CCP investment compares favorably to external consultant rates of $150-$300 per hour for comparable CMMC preparation services.
What CCP training and exam cover — scope of knowledge & competencies
CCP training encompasses comprehensive coverage of CMMC framework components, assessment methodology, and practical application skills required to support organizations pursuing certification. The curriculum addresses both conceptual understanding and operational competencies.
Training domains typically include:
- CMMC Ecosystem and Governance: Understanding the organizational structure governing CMMC implementation, including the roles of DoD, Cyber AB, C3PAOs, assessors, and practitioners within the certification ecosystem. This includes comprehending how the CMMC program integrates with existing defense acquisition regulations and contractual requirements.
- Code of Professional Conduct and Ethics: Examining ethical obligations governing CMMC professionals, including confidentiality requirements, objectivity standards, conflict of interest management, and proper handling of assessment materials and organizational information. Professional conduct violations can result in credential revocation.
- CMMC Model Architecture: Detailed examination of the three CMMC levels, their associated control requirements, maturity expectations, and relationships to underlying NIST standards. This includes understanding how NIST SP 800-171 practices map to Level 2 requirements and how assessment objectives test control effectiveness.
- Source Documents and Information Protection: Analyzing the regulatory foundations for CMMC including DFARS clauses, FAR requirements, and CUI/FCI classification standards. Understanding what constitutes Federal Contract Information versus Controlled Unclassified Information determines appropriate certification level requirements.
- CMMC Assessment Process (CAP): Comprehensive coverage of assessment methodology including preparation phases, scoping activities, documentation review, artifact examination, technical testing, interview protocols, and results determination. The assessment process follows structured procedures that CCPs must understand to effectively prepare organizations.
- Scoping Principles and Boundaries: Establishing proper assessment boundaries represents one of the most complex CMMC activities. Training addresses how to identify CUI processing systems, establish security boundaries, evaluate external service providers, and properly document scope definitions that withstand assessor scrutiny.
- Control Evaluation and Evidence Assessment: Developing skills to evaluate whether implemented controls satisfy CMMC objectives, what evidence demonstrates effectiveness, and how to identify gaps requiring remediation. This includes understanding assessment procedures from NIST SP 800-171A that define testing methodology.
- Documentation Development: Practical guidance on creating System Security Plans, Policies and Procedures documentation, Plans of Action and Milestones, and other artifacts required for assessment. Documentation must accurately reflect actual implementations while satisfying assessor requirements for detail and comprehensiveness.
Beyond theoretical knowledge, CCP training emphasizes practical competencies: interpreting CMMC requirements for specific organizational contexts, conducting gap analyses, planning remediation activities, preparing evidence packages, and managing stakeholder communications throughout the compliance process.
Limitations of CCP — what it does not allow you to do (without further certification)
Understanding CCP limitations proves as important as recognizing its capabilities. The credential authorizes specific activities while explicitly prohibiting others reserved for more advanced certifications.
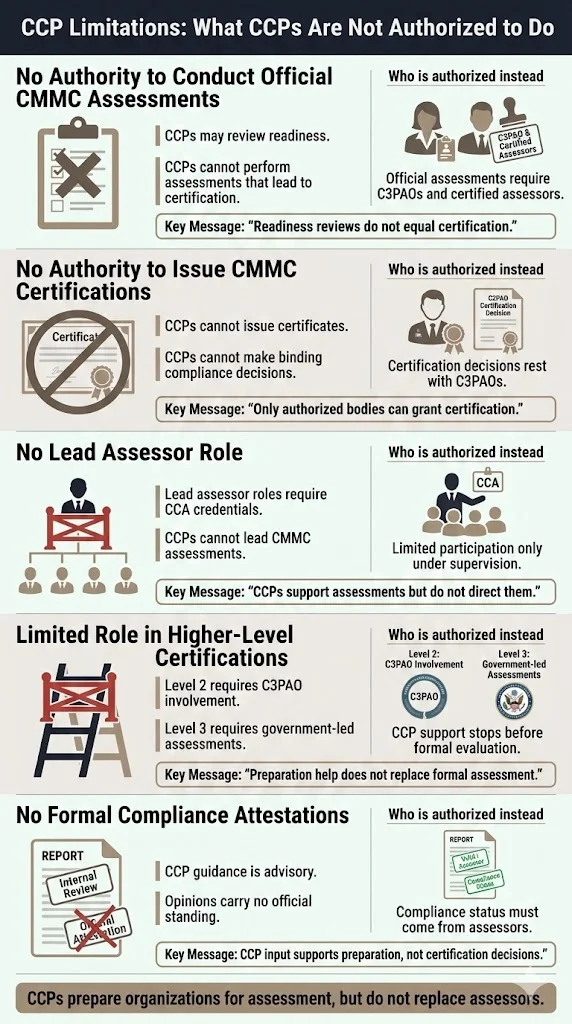
CCPs cannot conduct official CMMC assessments that result in certification decisions. Official assessments require Certified CMMC Assessor credentials and must be performed through authorized C3PAOs. Organizations cannot achieve CMMC certification through CCP-conducted evaluations, regardless of how thorough or professionally executed.
CCPs cannot issue CMMC certifications or make formal compliance determinations. Certification authority resides exclusively with C3PAOs based on assessor findings and established criteria. While CCPs can provide informed opinions on readiness, these carry no official standing in the certification process.
CCPs cannot serve as lead assessors for CMMC assessments. Lead assessor roles require CCA credentials combined with additional qualifications and experience requirements. CCPs may participate in assessment teams for limited activities—particularly verification of Level 1 practices during Level 2 assessments—but only under CCA supervision.
For organizations seeking higher CMMC levels, CCP expertise provides valuable preparation support but cannot substitute for formal assessment. Level 2 certification requires C3PAO engagement. Level 3 assessments involve government-led evaluations with even more stringent requirements. CCP knowledge helps organizations prepare effectively, reducing assessment duration and improving first-time passage rates, but cannot replace the official assessment process.
CCPs also face limitations in certain advisory contexts. While CCPs can provide general CMMC guidance and preparation support, specific attestations about organizational compliance status or certification eligibility properly belong to qualified assessors conducting formal evaluations. Organizations should understand that CCP opinions, while informed, represent internal assessments rather than official determinations.
Benefits for companies and individuals — why investing in CCP pays off
CCP certification delivers tangible value for both organizations pursuing defense contracts and individuals building cybersecurity compliance careers.
For organizations:
CCP-credentialed staff enable self-directed compliance preparation, reducing dependence on external consultants for routine activities while reserving paid advisory services for complex technical implementations or specialized expertise. Organizations with internal CCP capabilities report 40-60% reductions in external consulting costs during CMMC preparation.
Internal CCP expertise supports ongoing compliance maintenance after initial certification. CMMC imposes continuous compliance obligations including annual affirmations, System Security Plan updates, control effectiveness monitoring, and evidence collection. Organizations lacking internal expertise face recurring consulting costs of $25,000-$75,000 annually for these maintenance activities.
Having CCP-trained personnel demonstrates to enterprise clients and prime contractors that your organization takes CMMC seriously beyond minimum contractual compliance. When prime contractors evaluate subcontractor security posture, formal credentials provide objective evidence of capability that generic security claims cannot match.
CCP knowledge enables more effective C3PAO engagement. Organizations understanding assessment procedures, evidence requirements, and scoping principles communicate more efficiently with assessors, respond to information requests more completely, and avoid common misunderstandings that extend assessment timelines by weeks.
Internal gap analysis and remediation planning guided by CCP expertise identifies problems early when fixes cost less. Discovering control gaps during official assessment requires expensive re-work and assessment rescheduling. CCP-led readiness reviews surface issues during preparation when remediation integrates naturally into implementation planning.
For individuals:
CCP certification validates expertise in an increasingly critical compliance domain. As of the October CyberAB Town Hall, only 431 organizations had achieved a final CMMC Level 2 certification—representing just 0.5% of the roughly 80,000 companies the DoD estimates will require Level 2. This massive readiness gap creates sustained demand for professionals with documented CMMC knowledge.
The credential opens roles in compliance management, security engineering, risk management, internal audit, and consulting. Organizations across the defense industrial base need personnel capable of managing CMMC preparation, maintaining certified status, and supporting ongoing compliance operations. These roles typically command salaries 15-25% higher than equivalent positions without specialized compliance credentials.
CCP serves as a stepping stone toward more advanced certifications including CCA. Assessor roles offer higher compensation and consulting opportunities, but require CCP certification as a prerequisite. Individuals building long-term careers in cybersecurity compliance benefit from establishing the CCP foundation early.
Professional credibility extends beyond formal role requirements. In cross-functional teams implementing security controls, CCP credentials establish technical authority when discussing requirements, debating implementation approaches, or resolving conflicting interpretations of control objectives.
How CCP fits within broader cybersecurity certification and compliance landscape
CMMC represents one component of an interconnected compliance landscape spanning multiple frameworks, standards, and regulatory requirements. Organizations pursuing defense contracts typically navigate several concurrent compliance obligations.
CCP knowledge complements expertise in related frameworks:
- ISO 27001 establishes an Information Security Management System (ISMS) requiring documented risk assessments, statement of applicability, and continuous improvement cycles. Organizations certified to ISO 27001 find significant control overlap with CMMC Level 2—both frameworks address access control, cryptography, operations security, and incident management. CCP-trained personnel understand how to map ISO 27001 controls to NIST SP 800-171 requirements, avoiding duplicative implementations.
- SOC 2 attestations examine controls relevant to Trust Services Criteria including security, availability, confidentiality, processing integrity, and privacy. SOC 2 Type II requires documented evidence of control effectiveness over a minimum 6-month observation period—similar to CMMC's emphasis on sustained compliance. Organizations pursuing both CMMC and SOC 2 benefit from unified control implementation and evidence collection processes that CCP expertise helps coordinate.
- FedRAMP governs cloud service providers serving federal agencies, requiring implementation of NIST SP 800-53 controls and continuous monitoring. Defense contractors utilizing FedRAMP-authorized cloud services simplify CMMC compliance by inheriting certain controls from cloud providers—CCP training addresses how to properly document inherited controls in System Security Plans.
- NIST Cybersecurity Framework provides voluntary guidance for managing cybersecurity risk through identification, protection, detection, response, and recovery functions. Many organizations use CSF for overall security program structure while implementing specific CMMC requirements for defense contracts. CCP knowledge helps integrate prescriptive CMMC controls within broader CSF-based security strategies.
The compliance landscape increasingly demands professionals who understand relationships between frameworks, can identify control overlaps, and efficiently implement unified security programs satisfying multiple requirements simultaneously. CCP certification provides foundational knowledge in one critical framework while building transferable skills applicable across compliance domains.
Organizations strengthening their security posture benefit from viewing CMMC not as an isolated compliance theater but as one instantiation of fundamental security principles reflected across multiple frameworks. CCP-trained personnel recognize these connections, enabling more efficient compliance strategies that protect actual security rather than generating assessment artifacts.
Practical steps for companies looking to adopt CCP-driven compliance
Organizations pursuing CMMC readiness through internal CCP expertise should approach implementation systematically:
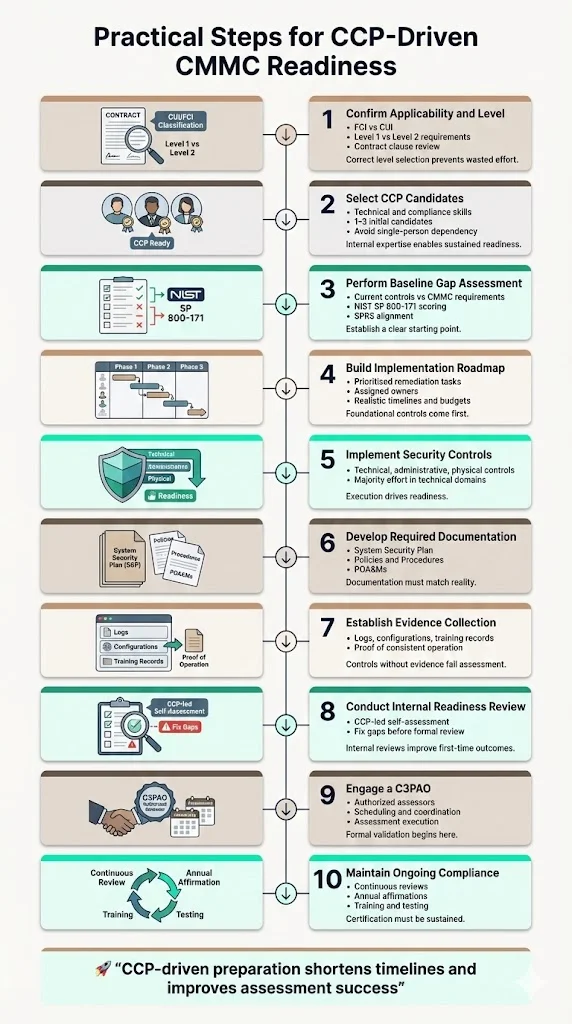
1) Assess applicability and level requirements: Determine whether your contracts involve Federal Contract Information requiring Level 1 self-assessment or Controlled Unclassified Information requiring Level 2 third-party certification. Review contract clauses, communicate with contracting officers, and evaluate CUI markings in contract documents and deliverables. Organizations frequently misidentify their required level, pursuing insufficient certification or over-investing in unnecessary requirements.
2) Identify CCP training candidates: Select personnel with appropriate backgrounds for CCP training. Ideal candidates combine technical understanding of IT systems with compliance orientation and stakeholder communication skills. Organizations typically train 1-3 individuals initially—sufficient for preparation activities while avoiding single-person dependency risks. For organizations exceeding 500 employees or managing particularly complex environments, additional CCP-credentialed personnel provide capacity for parallel work streams.
3) Conduct baseline gap assessment: Before extensive remediation investment, perform structured gap analysis comparing current security controls against CMMC requirements. This establishes your starting point, identifies major deficiencies requiring attention, and supports realistic timeline and budget planning. Document findings using the NIST SP 800-171 scoring methodology—the same approach used for Supplier Performance Risk System (SPRS) score calculations.
4) Develop implementation roadmap: Translate gap analysis findings into specific remediation activities with assigned owners, realistic timelines, and resource requirements. Prioritize foundational controls that enable subsequent implementations—organizations cannot effectively implement access logging without first establishing proper access control, for example. Budget 6-12 months for comprehensive Level 2 remediation depending on starting maturity and resource availability.
5) Execute technical and administrative controls: Implement required security controls across technical domains (access control, encryption, network security, system integrity), administrative areas (policies, procedures, training, incident response), and physical security. Technical implementations typically consume 60-70% of remediation effort while administrative controls require 20-30% and physical security 10-15%.
6) Develop required documentation: Create or update System Security Plans documenting your security architecture, control implementations, data flows, and security boundaries. Develop comprehensive Policies and Procedures addressing each NIST SP 800-171 requirement family. Establish Plans of Action and Milestones for any controls not yet fully implemented. Documentation accuracy matters critically—assessors identify documentation-implementation mismatches as the most common assessment finding.
7) Establish evidence collection processes: Implement systematic evidence collection supporting control effectiveness demonstrations. This includes configuration exports, log samples, training records, access reviews, vulnerability scan results, and incident response documentation. Organizations discover during assessment that controls they believed operational lack evidence proving consistent effectiveness.
8) Conduct internal readiness review: Perform comprehensive self-assessment using CCP expertise several months before scheduling official C3PAO assessment. Identify remaining gaps, documentation deficiencies, or evidence collection issues requiring correction. Organizations conducting thorough internal reviews achieve 80-90% first-time passage rates compared to 40-50% for organizations proceeding directly to official assessment.
9) Engage C3PAO for official assessment: Select an authorized C3PAO based on experience with organizations similar to yours, assessor availability, and cost structures. Coordinate assessment scheduling, provide requested documentation, facilitate assessor access to systems and personnel, and respond to findings professionally. The assessment typically requires 3-5 days onsite depending on scope complexity.
10) Maintain ongoing compliance: Establish processes supporting continuous compliance including quarterly control reviews, annual System Security Plan updates, security awareness training delivery, incident response exercises, and vulnerability management. Submit required annual affirmations on schedule—missed affirmations can invalidate certifications and jeopardize contract eligibility.
Conclusion
The Certified CMMC Professional credential represents a foundational building block for organizations pursuing cybersecurity maturity within the defense industrial base. While CCP certification alone does not grant assessment authority or substitute for official C3PAO evaluation, it equips organizations with knowledge, processes, and internal capabilities required to prepare effectively for CMMC certification and maintain compliance over time.
Independent research found that only 1% of DIB organizations felt fully prepared for upcoming CMMC assessments, with fewer than 50% having completed foundational documentation like an SSP or POA&M or implemented all NIST 800-171 requirements. This readiness gap creates both risk and opportunity—organizations building CCP-driven compliance capabilities position themselves competitively while those delaying preparation face contract disqualification.
Organizations targeting enterprise clients, pursuing defense sector work, or operating within supply chains handling sensitive information should evaluate CCP certification as part of their compliance and security roadmap. The investment in formal training, credential acquisition, and internal capability development pays returns through reduced external consulting dependence, more efficient compliance preparation, and demonstrated commitment to cybersecurity maturity that contract requirements increasingly demand.
Frequently Asked Questions
1) What is a certified CMMC professional?
A Certified CMMC Professional (CCP) is an individual who has completed formal training on the Cybersecurity Maturity Model Certification framework, passed the CCP examination administered by the Cyber Accreditation Body (Cyber AB), and obtained official credential authorization following background verification. CCPs possess documented knowledge of CMMC architecture, assessment processes, control requirements, and scoping principles. They support organizations preparing for CMMC certification through gap analysis, remediation planning, documentation development, and readiness activities. However, CCPs cannot conduct official CMMC assessments or issue certifications—these activities require Certified CMMC Assessor (CCA) credentials and authorized C3PAO engagement.
2) How do I get CMMC certified?
Organizations cannot "get CMMC certified" through self-directed activity—CMMC certification requires official assessment by authorized entities. For Level 1, organizations perform annual self-assessments with senior leadership affirmation. For Level 2, organizations must engage a CMMC Third Party Assessment Organization (C3PAO) to conduct formal evaluation of all 110 NIST SP 800-171 controls and issue certification based on demonstrated compliance. The process involves implementing required security controls, developing documentation including System Security Plans, collecting evidence demonstrating control effectiveness, conducting internal readiness reviews, then scheduling official assessment. Level 2 preparation typically requires 6-12 months and $150,000-$450,000 investment depending on starting security maturity and organizational complexity.
3) Is CMMC certification hard?
CMMC Level 2 certification presents significant complexity requiring comprehensive implementation of 110 security controls across 14 control families, extensive documentation development, evidence collection demonstrating sustained effectiveness, and successful third-party assessment. Organizations with mature security programs aligned to NIST standards find CMMC moderately challenging, primarily involving documentation formalization and evidence systematization. Organizations lacking structured security programs face substantial technical implementations, policy development, and cultural changes requiring 6-12 months of focused effort. The difficulty stems less from any single requirement and more from the breadth of controls, documentation precision required, and need to demonstrate actual effectiveness rather than aspirational policies. Structured training through CCP certification or engagement with experienced Registered Practitioner Organizations significantly reduces complexity through proper planning and execution.
4) How much does it cost to get CMMC certified?
CMMC certification costs vary substantially based on organizational size, current security maturity, and required level. Level 1 self-assessment involves minimal direct costs beyond internal staff time for documentation and annual affirmation. Level 2 certification typically costs $150,000-$450,000 including gap assessment ($15,000-$25,000), technical control implementation ($75,000-$250,000), documentation development ($25,000-$50,000), and C3PAO assessment fees ($20,000-$75,000 depending on scope complexity). Organizations with mature security programs may spend toward the lower range while those requiring extensive remediation approach the upper range. Ongoing maintenance adds $25,000-$75,000 annually for continuous monitoring, annual affirmations, documentation updates, and evidence management. Internal CCP-trained personnel reduce recurring consulting costs by 40-60% compared to full external management.
5) How long does it take to become a Certified CMMC Professional?
The CCP certification process typically requires 2-6 months from training enrollment through credential issuance. Training itself spans approximately 5 days (40 hours) of intensive instruction through an authorized training provider, delivered in classroom, virtual, or hybrid formats. Following training, candidates take the CCP examination testing knowledge across CMMC domains including framework architecture, assessment methodology, and professional conduct. Upon passing the exam, candidates submit formal applications including background check authorization. The Tier 3 background investigation typically requires 4-12 weeks depending on investigation complexity and processing queues. Once background clearance completes and Cyber AB approves the application, the CCP credential is issued. Candidates should plan for approximately 3 months as a realistic timeline, though expedited processing sometimes occurs.
6) What are the requirements for becoming a Certified CMMC Professional?
CCP certification requires: completion of a CCP training course through a Cyber AB-authorized Licensed Training Provider (LTP) or Authorized Training Provider (ATP) covering CMMC framework components, assessment methodology, control requirements, and professional conduct; successful passage of the CCP examination demonstrating comprehensive knowledge of CMMC architecture, assessment processes, scoping principles, and code of ethics; submission of a formal application to Cyber AB including required documentation and fees; completion of a favorable Tier 3 background investigation examining criminal history, employment verification, and other trustworthiness factors; and acceptance of professional conduct obligations and ethical standards governing CCP practice. While formal prerequisites are minimal, candidates benefit from foundational familiarity with cybersecurity concepts, information security frameworks, compliance documentation, or technical security controls.
7) What are the benefits of becoming a Certified CMMC Professional?
For individuals, CCP certification validates expertise in defense cybersecurity compliance, opening roles in compliance management, security engineering, risk management, internal audit, and consulting across the defense industrial base. These positions typically command 15-25% salary premiums compared to equivalent roles without specialized compliance credentials. CCP serves as a prerequisite for advanced Certified CMMC Assessor certification, providing a career path toward higher-compensation assessment roles. For organizations, internal CCP expertise enables self-directed compliance preparation, reducing external consulting costs by 40-60% during CMMC readiness and ongoing maintenance. CCP-trained personnel conduct gap analyses, develop required documentation, guide remediation planning, and manage continuous compliance activities efficiently. Organizations demonstrate credibility to enterprise clients and prime contractors through formal credentials evidencing institutional compliance commitment beyond contractual minimums.
8) What are the career opportunities for a Certified CMMC Professional?
CCP credentials open diverse career paths including: Compliance Officers managing CMMC certification for defense contractors and maintaining continuous compliance obligations; Security Engineers implementing technical controls required for CMMC Level 2 across network security, access control, cryptography, and system integrity domains; Risk Managers conducting gap analyses, prioritizing remediation activities, and coordinating assessment preparation; Internal Auditors performing readiness reviews, evaluating control effectiveness, and identifying compliance deficiencies requiring correction; Compliance Consultants advising multiple organizations on CMMC preparation, documentation development, and readiness strategies; and positions within Registered Practitioner Organizations (RPOs) supporting clients throughout the defense industrial base. CCP also provides the foundation for advancement to Certified CMMC Assessor roles conducting official assessments through C3PAOs. Given that fewer than 1% of the estimated 80,000 organizations requiring Level 2 certification have achieved it, sustained demand exists for CCP-credentialed professionals throughout defense supply chains.
9) What are the different levels of CMMC certification?
CMMC 2.0 establishes three certification levels scaled to information sensitivity and program criticality. Level 1 applies to organizations handling Federal Contract Information (FCI)—basic contract-related data requiring foundational protection through 17 security practices derived from FAR 52.204-21. Organizations self-assess annually with senior leadership affirmation. Level 2 applies to organizations handling Controlled Unclassified Information (CUI)—sensitive data requiring protection through all 110 controls from NIST SP 800-171 Revision 2. Most Level 2 contracts require third-party assessment by C3PAOs beginning November 10, 2026. Level 3 applies to organizations supporting the most critical national security programs, requiring implementation of NIST SP 800-172 controls addressing advanced persistent threats and government-led assessments. Organizations must achieve Level 2 certification before pursuing Level 3. The tiered structure ensures security requirements align proportionally with information sensitivity and program importance throughout the defense industrial base.



.svg)
.svg)
.svg)