Most organizations treat cybersecurity frameworks as aspirational guidelines rather than operational blueprints. This approach creates a disconnect between documented security policies and actual protection capabilities—a disconnect that becomes apparent when misconfigurations enable breaches or when auditors scrutinize actual control implementation. CIS (Center for Internet Security) operates as a nonprofit organization formed in October 2000, with a mission to help people, businesses, and governments protect themselves against pervasive cyber threats. When enterprises reference "CIS Security," they're describing the organization's comprehensive suite of frameworks and guidance—specifically, CIS Benchmarks (secure configuration standards) and CIS Critical Security Controls (prioritized safeguards)—that provide prescriptive, actionable security measures rather than theoretical recommendations.
For technical decision-makers at organizations serving enterprise clients, understanding CIS offerings matters because implementing the CIS Controls creates an on-ramp to comply with PCI DSS, HIPAA, GDPR, and other industry regulations. More fundamentally, these frameworks address the operational reality that most successful attacks exploit basic security hygiene failures—unpatched systems, misconfigured infrastructure, and inadequate access controls—rather than sophisticated zero-day exploits.
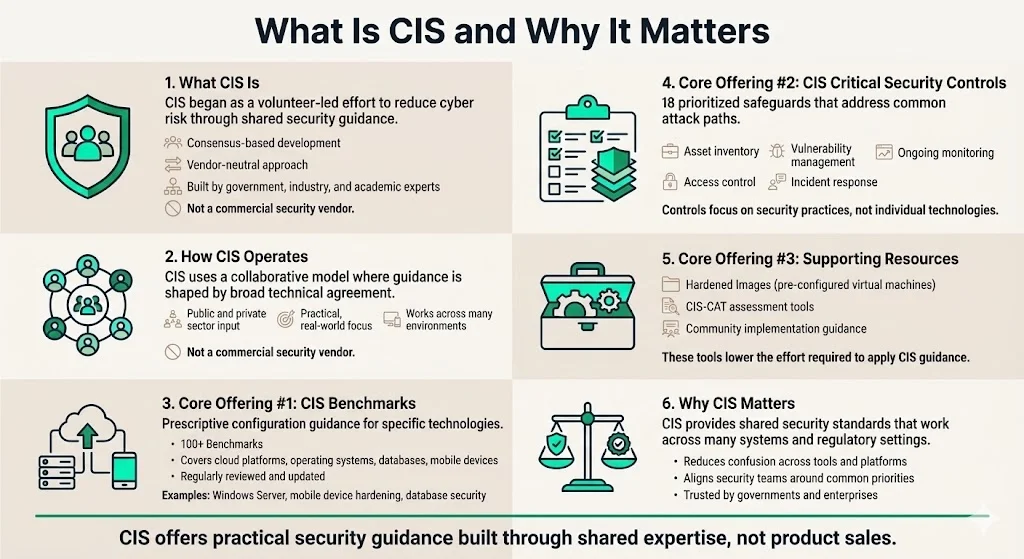
What is CIS? (and why it matters)
CIS began as a volunteer-based initiative to create actionable, consensus-based security configuration benchmarks aimed at helping organizations decrease cyber risk, evolving into a significant entity in cybersecurity coordination at the national level. The organization operates through a collaborative, vendor-agnostic model that distinguishes it from commercial security vendors selling proprietary solutions.
CIS delivers three core offerings that enterprises rely on:
CIS Benchmarks — These provide prescriptive configuration guidelines for specific technologies. Currently, CIS has 100-plus benchmarks to harden the configurations of cloud platforms, databases, desktop and server software, mobile devices, and operating systems. Each Benchmark undergoes continuous community review and regular updates; for instance, recent releases include updated guidance for Windows Server configurations, mobile device hardening, and database security standards.
CIS Critical Security Controls — Formerly known as the SANS Critical Security Controls, the CIS Controls represent a set of 18 prioritized safeguards to mitigate the most prevalent cyber-attacks against modern systems and networks. Unlike Benchmarks that focus on specific technologies, Controls address broader security practices spanning asset inventory, vulnerability management, access control, incident response, and continuous monitoring.
Additional Resources — CIS provides Hardened Images (pre-configured virtual machine templates aligned to Benchmarks), CIS-CAT (automated configuration assessment tools), and community-driven implementation guidance that reduces the technical burden of adopting these frameworks.
CIS operates through a collaborative, nonpartisan, vendor-agnostic operating model—meaning recommendations emerge from consensus among government agencies, private sector practitioners, and academic researchers rather than commercial interests. This consensus-based development process produces frameworks that work across diverse technology environments and regulatory contexts.
Key Concepts: Benchmarks vs Controls
Organizations frequently conflate CIS Benchmarks with CIS Controls, treating them as interchangeable when they serve complementary but distinct purposes.
CIS Benchmarks address the question: "How should this specific technology be configured securely?" They provide detailed, prescriptive guidance for hardening individual systems—operating systems, cloud platforms, network devices, databases, containers, and applications. A Benchmark specifies exact configuration parameters: which services to disable, which ports to close, which logging settings to enable, which encryption standards to enforce. Benchmarks typically define two implementation levels—Level 1 (baseline security suitable for most environments with minimal operational impact) and Level 2 (defense-in-depth configurations appropriate for high-security environments that may require additional operational considerations).
CIS Controls address the broader question: "What security capabilities must our organization implement across our entire environment?" The CIS Critical Security Controls are a prescriptive, prioritized, and simplified set of best practices that consist of Safeguards requiring one specific action each. Rather than technology-specific settings, Controls define organizational capabilities: maintaining complete asset inventories, implementing vulnerability management processes, enforcing access control policies, establishing incident response procedures, and ensuring audit log management.
The CIS Controls are grouped into Implementation Groups (IGs), allowing organizations to use risk assessment to determine the appropriate level of IG (one through three) for their organization. Implementation Group 1 addresses small organizations with limited security resources, IG2 targets mid-sized enterprises with moderate risk exposure, and IG3 serves organizations facing sophisticated threats or strict regulatory requirements.
The complementary nature matters operationally: Controls define what security capabilities you need; Benchmarks specify how to configure your infrastructure to support those capabilities. An organization might implement CIS Control 4 (Secure Configuration of Enterprise Assets and Software) by applying specific CIS Benchmarks for their Linux servers, Windows endpoints, AWS environment, and Oracle databases.
What CIS Security Covers — Security Domains & Topics
CIS frameworks map comprehensively across security domains that enterprises must address for audit readiness and genuine protection:
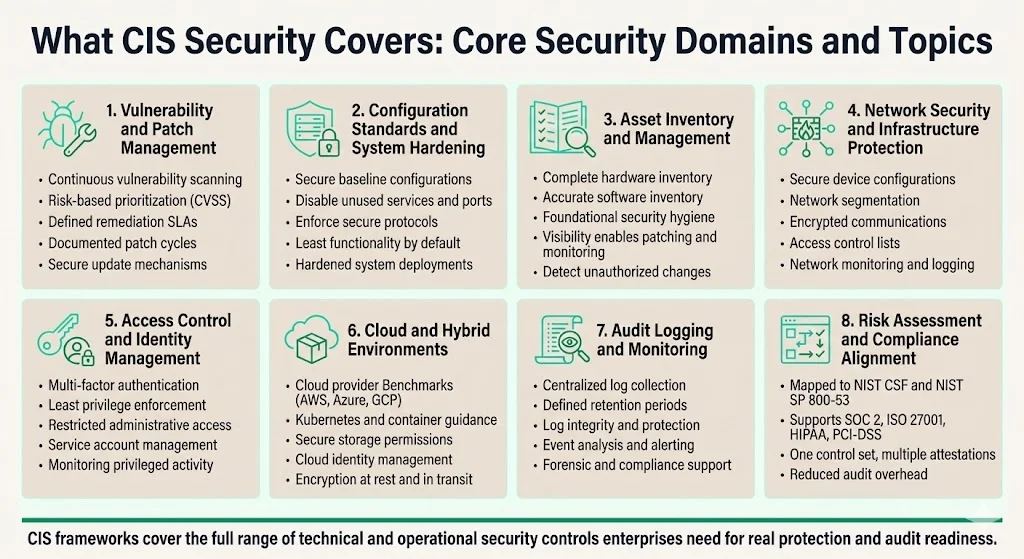
1) Vulnerability and Patch Management — CIS Controls require continuous vulnerability assessment and systematic remediation tracking. This addresses the operational reality that unpatched vulnerabilities represent the most common initial access vector. Controls specify automated vulnerability scanning, risk-based prioritization (incorporating CVSS scoring), defined remediation SLAs, and documented patching cycles. Benchmarks complement this by defining secure update mechanisms and configuration settings that reduce exploitable attack surface.
2) Configuration Standards and System Hardening — Benchmarks provide the detailed specifications for secure baseline configurations. This includes disabling unnecessary services, closing unused ports, enforcing secure protocols, implementing principle of least functionality, and establishing hardened defaults. Organizations serving enterprise clients use these standards to demonstrate that systems are deployed in known-secure states rather than vendor default configurations that prioritize ease-of-use over security.
3) Asset Inventory and Management — CIS Controls emphasize complete, accurate inventory of hardware and software assets as foundational requirements. Almost all successful cyber attacks exploit poor cyber hygiene like unpatched software, poor configuration management, and outdated solutions; the CIS Controls include foundational security measures to achieve essential hygiene. Without knowing what assets exist, organizations cannot secure them, patch them, or detect unauthorized changes.
4) Network Security and Infrastructure Protection — Benchmarks cover network devices (routers, switches, firewalls), providing configuration guidance for secure network segmentation, encrypted communications, access control lists, and logging requirements. Controls address network-level defenses including boundary protection, controlled access, and monitoring for unauthorized network connections.
5) Access Control and Identity Management — Multiple CIS safeguards address authentication, authorization, and privileged access management. This includes enforcing multi-factor authentication, implementing least privilege principles, restricting administrative privileges, managing service account credentials, and monitoring privileged account usage. Benchmarks specify technical implementations (password policies, account lockout settings, privilege separation) while Controls define organizational processes.
6) Cloud and Hybrid Environments — CIS maintains specific Benchmarks for major cloud providers (AWS, Azure, Google Cloud) and cloud-native technologies (Kubernetes, Docker). These address cloud-specific risks: identity and access management in cloud consoles, storage bucket permissions, network security groups, logging configurations, and encryption for data at rest and in transit.
7) Audit Logging and Monitoring — Controls require comprehensive audit log management—collection, retention, protection, and analysis of security-relevant events. This supports incident detection, forensic investigation, and compliance evidence requirements. Benchmarks specify which events must be logged, retention periods, log protection mechanisms, and centralized log aggregation.
8) Risk Assessment and Compliance Alignment — The CIS Controls can be downloaded from CIS, along with various mappings to other frameworks such as the National Institute of Standards and Technology (NIST) Cybersecurity Framework, NIST Special Publication 800-53, and many others. These documented mappings enable organizations to demonstrate how CIS implementation addresses multiple compliance requirements simultaneously—a significant efficiency gain when managing SOC 2, ISO 27001, HIPAA, or PCI-DSS attestations.
How Businesses — Especially Those Selling to Enterprise Clients — Can Use CIS Security
Organizations pursuing enterprise customers face rigorous security scrutiny during vendor assessments, contractual negotiations, and ongoing audits. Adopting CIS frameworks addresses this operational reality through multiple mechanisms:
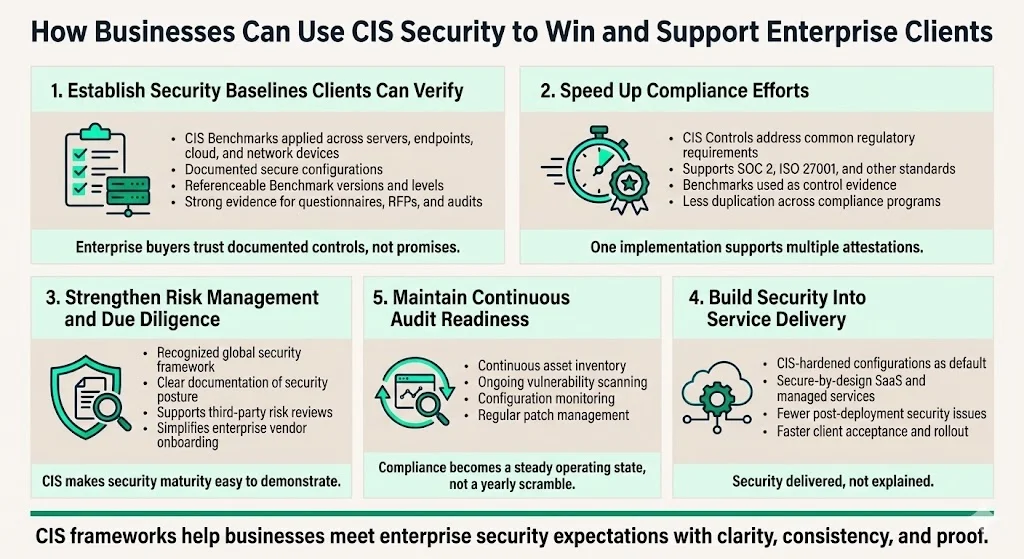
1) Establish Demonstrable Security Baselines — Enterprise clients evaluate vendors based on documented security practices, not assurances. Implementing CIS Benchmarks across servers, endpoints, cloud infrastructure, and network devices creates verifiable evidence of secure configurations. Organizations can reference specific Benchmark versions and implementation levels in security questionnaires, RFP responses, and vendor security assessments—providing auditors and clients concrete validation rather than generic claims.
2) Accelerate Compliance Programs — Most regulatory frameworks and industry standards require secure configurations, vulnerability management, access controls, and continuous monitoring. CIS implementation addresses these requirements systematically. Organizations pursuing SOC 2 Type II attestation find that CIS Controls map to Trust Services Criteria; those seeking ISO 27001 certification can reference CIS Benchmarks as evidence of Annex A control implementation. This reduces the resource investment required to achieve multiple certifications simultaneously.
3) Support Risk Management and Due Diligence — Enterprise procurement processes include security due diligence, third-party risk assessments, and ongoing vendor risk management. Organizations that follow CIS frameworks can document their security posture using globally recognized standards. This satisfies client risk management requirements and streamlines vendor onboarding—particularly important when competing against larger vendors with dedicated security teams.
4) Integrate Security into Service Delivery — For companies offering SaaS, managed services, or cloud-based solutions, incorporating CIS-compliant configurations as standard delivery practice differentiates offerings. Rather than promising security, organizations deliver infrastructure pre-hardened according to recognized standards. This reduces post-deployment security exceptions, accelerates client acceptance, and minimizes security-related delays in deployment cycles.
5) Maintain Continuous Audit Readiness — Modern systems and software are dynamic in nature; by enacting the CIS Controls, organizations support their assets' evolving needs in a meaningful way and align security efforts with business goals. Continuous asset inventory, vulnerability scanning, configuration monitoring, and patch management—all CIS Control requirements—transform compliance from annual projects into sustained operational capabilities. This operational model prevents the rushed remediation efforts that characterize organizations treating audits as events rather than ongoing states.
Practical Steps to Implement CIS Security in Your Company
CIS adoption requires systematic implementation rather than aspirational policy documents:
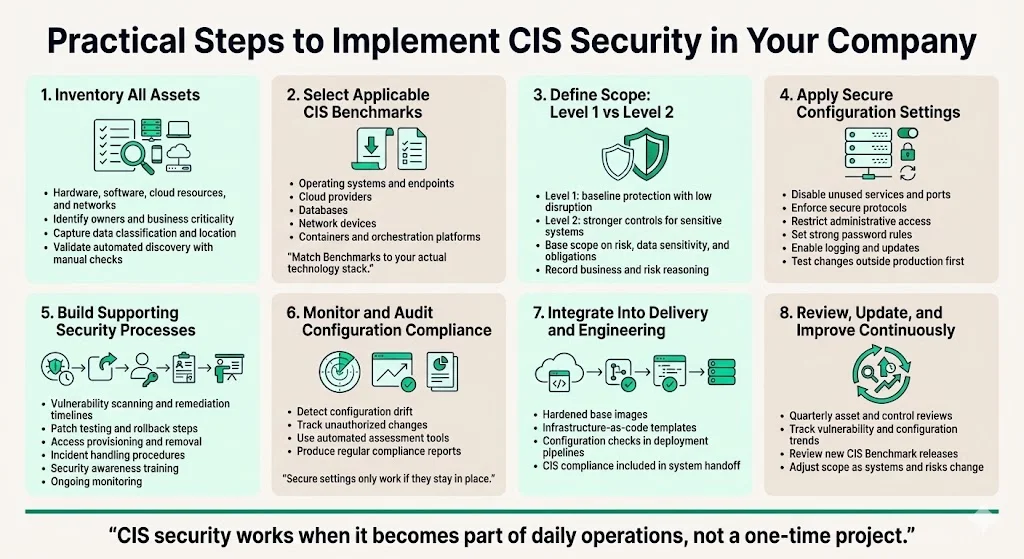
1. Inventory All Assets — Begin by cataloging every hardware device, software application, cloud resource, and network component across your environment. This foundational step supports every subsequent control. Use automated discovery tools where possible, but verify completeness manually—shadow IT, forgotten development environments, and orphaned cloud resources represent common gaps. Document asset owners, business criticality, data classifications, and network locations.
2. Select Relevant CIS Benchmarks — Identify which Benchmarks apply to your technology stack. Organizations typically require Benchmarks for operating systems (Linux distributions, Windows Server, macOS), cloud providers (AWS, Azure, GCP), databases (MySQL, PostgreSQL, Microsoft SQL Server, Oracle), network devices (Cisco, Palo Alto Networks), and container technologies (Docker, Kubernetes). Download current Benchmark versions from CIS—they're freely available.
3. Define Implementation Scope: Level 1 vs Level 2 — Assess which Benchmark level suits each asset based on data sensitivity, regulatory requirements, and operational constraints. Level 1 provides baseline security with minimal operational impact—appropriate for most business systems. Level 2 implements defense-in-depth configurations suitable for systems processing sensitive data, supporting compliance requirements, or facing elevated threat exposure. Document scope decisions with business and risk justifications.
4. Apply Configuration Settings Systematically — Implement Benchmark recommendations methodically: disable unnecessary services and protocols, close unused network ports, enforce secure communication standards, restrict administrative access, implement secure password policies, enable comprehensive logging, and configure automatic update mechanisms. Test configuration changes in non-production environments first to identify operational impacts before production deployment.
5. Establish Security Controls and Processes — Implement organizational capabilities defined in CIS Controls: vulnerability scanning and remediation workflows with defined SLAs, patch management cycles with testing and rollback procedures, access control provisioning and deprovisioning processes, incident response procedures, security awareness training programs, and continuous monitoring capabilities. These processes transform technical configurations into sustained security operations.
6. Monitor and Audit Configuration Compliance — Configuration drift—the gradual deviation from secure baselines—represents a persistent challenge. CIS offers a free hosted software product called the CIS Controls Assessment Tool (CIS-CAT) that allows organizations to track and prioritize the implementation of the CIS Controls. Use automated scanning tools to detect configuration changes, unauthorized modifications, and compliance deviations. Generate regular compliance reports documenting adherence to implemented Benchmarks.
7. Integrate into Development and Service Delivery — For organizations delivering systems or services to enterprise clients, embed CIS compliance into standard delivery processes. Build Hardened Images for common deployment scenarios, automate Benchmark application in infrastructure-as-code templates, incorporate security configuration validation in DevOps pipelines, and document CIS compliance as part of system handoff procedures.
8. Conduct Regular Reviews, Risk Assessments, and Updates — CIS Benchmarks receive regular updates addressing new vulnerabilities, emerging threats, and evolving technologies. Establish quarterly reviews of asset inventory accuracy, vulnerability management effectiveness, configuration compliance status, and security control maturity. Monitor CIS releases for updated Benchmark versions and assess applicability to your environment. This continuous improvement cycle maintains security posture as technology environments evolve.
Benefits & Limitations — What CIS Helps With and Where You Need Caution
Benefits
CIS frameworks provide globally recognized standards that satisfy due diligence requirements across industries and regulatory contexts. Organizations reference CIS implementation in client contracts, security questionnaires, and audit responses as evidence of systematic security practices. This recognition accelerates vendor assessments, reduces repetitive security documentation requests, and differentiates vendors in competitive evaluations.
Configuration vulnerabilities—systems deployed with insecure defaults, unnecessary services enabled, weak authentication requirements, inadequate logging—represent root causes in the majority of breaches. CIS Benchmarks directly address these common attack vectors through prescriptive hardening guidance. Organizations implementing Benchmarks systematically reduce exploitable attack surface.
The community-driven development model ensures CIS guidance remains current with threat landscapes, technology changes, and operational practices. Thousands of cybersecurity practitioners from around the world use the CIS Controls and contribute to their development via a community consensus process. This collective expertise produces frameworks applicable across diverse technology environments, vendor solutions, and organizational scales.
CIS implementation creates comprehensive audit evidence supporting multiple compliance requirements simultaneously—SOC 2, ISO 27001, HIPAA, PCI-DSS, and state-specific cybersecurity regulations. Organizations maintain documented security configurations, vulnerability management records, access control policies, and monitoring capabilities that auditors require for attestation. This efficiency reduces compliance costs compared to managing framework-specific implementations separately.
Limitations and Challenges
Level 2 Benchmark recommendations and advanced CIS Controls may conflict with application functionality, user workflows, or operational requirements. Organizations must evaluate each recommendation against business needs—some security measures require exceptions or compensating controls. This assessment requires technical expertise to understand security implications of deviations.
Proper implementation demands security engineering knowledge, configuration management capabilities, and ongoing operational commitment. Small organizations without dedicated security staff may struggle with technical complexity, particularly when applying Benchmarks across diverse technology stacks or implementing continuous monitoring Controls. This resource requirement must be considered during planning.
CIS compliance reduces risk exposure but doesn't guarantee immunity from compromise. Frameworks address infrastructure and operational security but don't encompass application security vulnerabilities, social engineering attacks, or insider threats. Organizations require layered defenses: secure development practices, security awareness training, threat intelligence, incident response capabilities, and business continuity planning beyond CIS scope.
Configuration compliance requires sustained vigilance. Systems drift from secure baselines through routine changes, emergency fixes, software updates, and human error. Maintaining CIS compliance demands continuous monitoring, regular audits, automated compliance scanning, and systematic remediation of deviations—this represents ongoing operational investment rather than one-time project work.
How CIS Security Fits Into Broader Cybersecurity Strategy
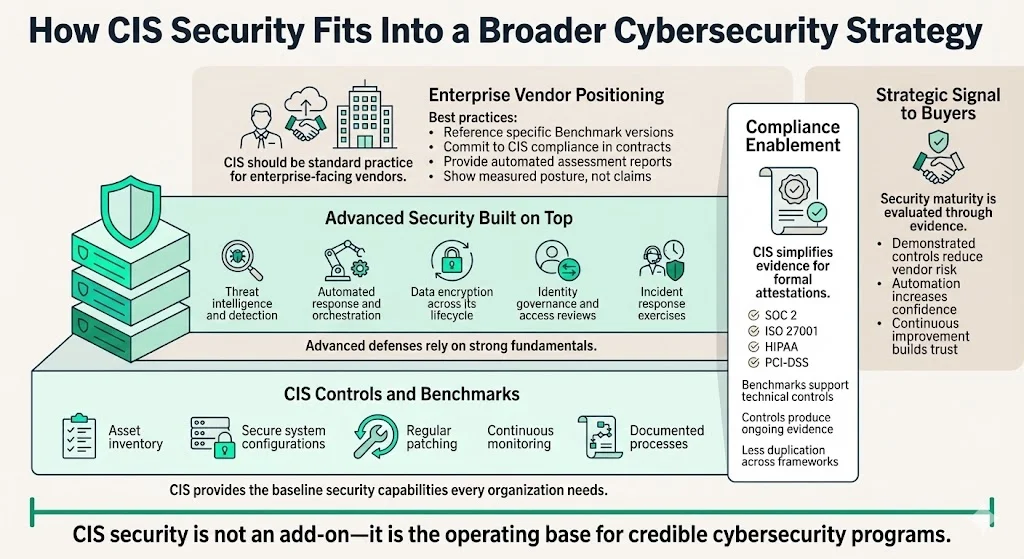
CIS Controls and Benchmarks function as foundational security infrastructure—essential baseline capabilities upon which organizations layer additional security practices. This foundation addresses fundamental security hygiene: systems are inventoried, configured securely, patched regularly, monitored continuously, and managed through documented processes.
Organizations then build advanced capabilities: threat intelligence programs identifying relevant adversary tactics and indicators of compromise, security orchestration and automated response reducing detection-to-remediation timelines, encryption protecting data throughout its lifecycle, identity governance ensuring appropriate access provisioning, and tabletop exercises validating incident response readiness.
For organizations pursuing compliance attestations—SOC 2, ISO 27001, HIPAA, PCI-DSS—CIS implementation provides practical baseline controls. ISO 27001 requires documented Information Security Management Systems with risk assessments and control implementation; CIS Benchmarks serve as technical implementation specifications for many Annex A controls. SOC 2 requires evidence of control effectiveness over observation periods; CIS Control implementation with automated monitoring generates continuous compliance evidence.
Organizations serving enterprise clients should position CIS compliance as standard security practice embedded in service delivery. During vendor security assessments, reference specific Benchmark versions implemented across infrastructure. In client contracts, commit to maintaining CIS-compliant configurations with regular audit validation. During security reviews, provide CIS-CAT compliance reports demonstrating measured security posture rather than unsubstantiated assurances.
The strategic positioning matters: enterprises evaluate vendors based on demonstrated security capabilities, not marketing claims. CIS adoption—particularly when coupled with automated compliance monitoring and continuous improvement processes—signals operational security maturity that satisfies procurement requirements and reduces perceived vendor risk.
Conclusion
Most organizations serving enterprise clients face identical security requirements regardless of industry: demonstrate secure configurations, maintain vulnerability management, implement access controls, enable continuous monitoring, and provide audit evidence. CIS Security—the comprehensive suite of Benchmarks and Controls—provides prescriptive, actionable guidance addressing these requirements systematically. Organizations that invest in complete asset inventory, rigorous configuration management, systematic patch cycles, and continuous compliance monitoring build security infrastructure that produces both genuine protection and audit readiness as natural outcomes. CIS frameworks don't represent comprehensive security programs—but properly implemented CIS baselines make advanced security capabilities more effective and compliance programs more efficient. For technical decision-makers evaluating security investments, CIS adoption delivers measurable risk reduction and accelerated compliance timelines—typically requiring 75 collective implementation hours annually versus 550-600 hours for ad-hoc security management approaches.
FAQ
1) What is CIS in security?
CIS stands for the Center for Internet Security, a nonprofit organization formed in October 2000, with a mission to help people, businesses, and governments protect themselves against pervasive cyber threats. Its core offerings include CIS Benchmarks (secure configuration standards for specific technologies) and CIS Controls (prioritized cybersecurity safeguards addressing broader security capabilities).
2) Is CIS a good company to work for?
CIS operates as a mission-driven, nonprofit organization dedicated to making the connected world a safer place. It's not a conventional commercial employer—individuals typically engage with CIS through community contribution to Benchmark development, participation in working groups, or employment supporting the organization's mission-driven programs.
3) Can you make $500,000 a year in cyber security?
Compensation in cybersecurity varies significantly based on role seniority, geographic market, organization size, and specialization. Senior leadership positions—CISO at large enterprises, partner-level consulting roles, executive security architecture positions—particularly in high-cost metropolitan areas, may command substantial compensation packages. However, this reflects labor market dynamics rather than framework adoption or certification achievement.
4) Who is CIS security?
"CIS security" refers to the frameworks, standards, and resources produced by the Center for Internet Security—specifically CIS Benchmarks (prescriptive configuration guidance for technologies), CIS Controls (prioritized security safeguards), CIS Hardened Images (pre-configured virtual machine templates), and CIS-CAT (automated compliance assessment tools). It represents a comprehensive approach to infrastructure hardening and security operations rather than a single product or service.



.svg)
.svg)
.svg)