Most organizations selling software or services to public-sector clients overlook a critical regulatory threshold: if your systems touch criminal-justice data, the Federal Bureau of Investigation holds you to the same security standards it imposes on law enforcement itself. This requirement isn't negotiable, and the learning curve is steep.
CJIS—Criminal Justice Information Services—represents both an FBI division and a comprehensive security policy framework governing how criminal justice information must be protected. For vendors, cloud providers, and enterprise-software companies targeting law-enforcement or public-safety markets, CJIS compliance determines contract eligibility, operational viability, and legal exposure.
This glossary term explains what the CJIS acronym means, who must comply, what the security policy requires, and how businesses should evaluate their obligations when handling criminal-justice data or serving law-enforcement clients.
What is Criminal Justice Information Services (CJIS)—Explanation of the Acronym and Scope
CJIS stands for Criminal Justice Information Services—a division within the Federal Bureau of Investigation and the policy framework that governs criminal-justice data security across the United States.
The CJIS Division gives state, local, and federal law enforcement and criminal justice agencies access to criminal justice information (CJI). The division operates as a centralized hub providing data and information services to law enforcement, the intelligence community, national security agencies, and authorized third parties including noncriminal justice organizations conducting background checks or employment screening.
CJIS encompasses multiple databases and systems that facilitate interagency cooperation and public safety. Key systems include the National Crime Information Center (NCIC), which provides real-time access to warrant information, stolen property records, and missing persons data; the Integrated Automated Fingerprint Identification System (IAFIS), which processes fingerprint and biometric identification requests; and criminal history background-check services supporting employment screening, licensing, and security clearances. These systems form the backbone of law-enforcement information sharing, enabling coordinated responses across jurisdictions and supporting investigations from local traffic stops to federal counterterrorism operations.
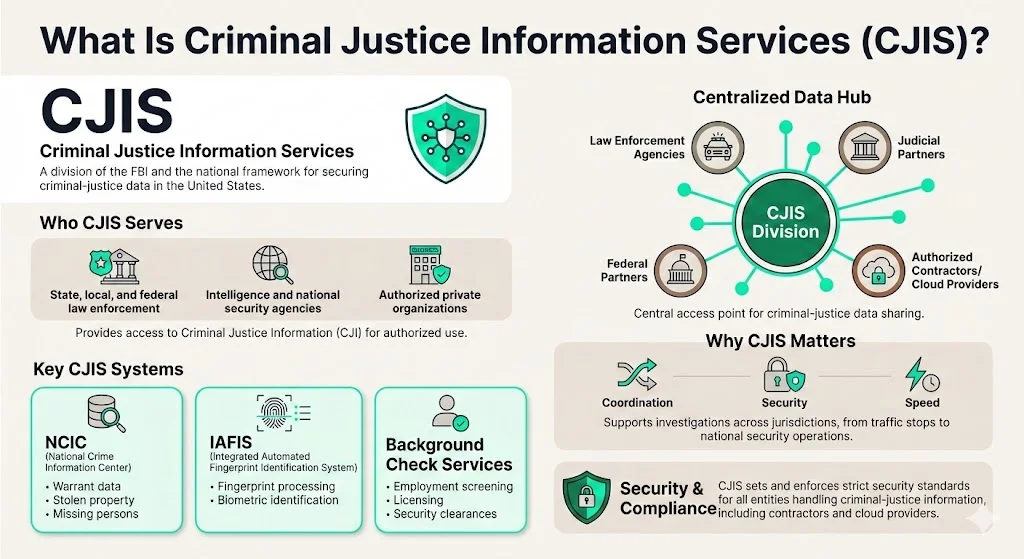
The CJIS Division doesn't just operate databases—it establishes and enforces the security standards that govern how all entities, including private contractors and cloud providers, must handle criminal-justice information.
Why CJIS Matters: Data Security, Public Safety & Interagency Cooperation
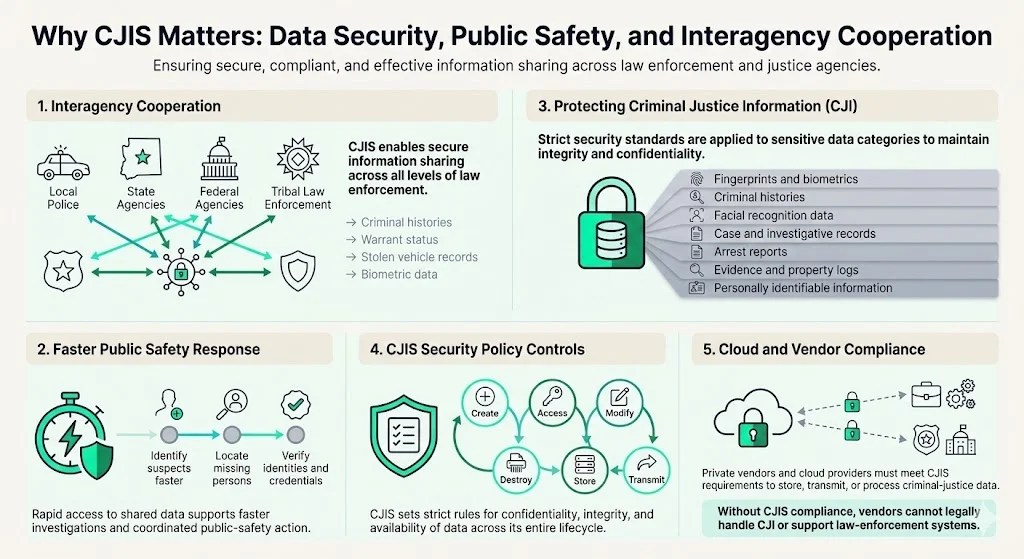
CJIS facilitates information sharing across law-enforcement agencies at every level—local police departments, state bureaus of investigation, federal agencies, and tribal law enforcement. This interoperability enables rapid access to criminal histories, warrant status, stolen vehicle records, and biometric data, supporting coordinated public-safety responses and reducing the time required to identify suspects, locate missing persons, or verify credentials.
The framework protects sensitive criminal justice and personal data defined as Criminal Justice Information (CJI). CJI includes, for example, fingerprint records and criminal histories—but the scope extends further to encompass biometric data such as facial recognition records, case files, investigative records, arrest reports, property and evidence logs, and personally identifiable information linked to criminal-justice proceedings. This data carries legal protections under federal and state statutes, and unauthorized access or disclosure triggers civil liability and potential criminal penalties.
The CJIS Security Policy provides guidance for the creation, viewing, modification, transmission, dissemination, storage, and destruction of CJI. The policy establishes strict controls governing confidentiality, integrity, and availability of data throughout its lifecycle—whether data resides in on-premises servers, cloud storage, backup systems, or mobile devices, and whether it's transmitted via secure networks, encrypted email, or API connections.
CJIS compliance matters acutely for private vendors and cloud providers because law-enforcement agencies increasingly rely on external technology partners for software platforms, managed services, cloud infrastructure, data analytics, and records-management systems. Law enforcement and other government agencies in the United States must ensure that their use of cloud services for the transmission, storage, or processing of CJI complies with the CJIS Security Policy. Without CJIS compliance, vendors cannot legally access, store, or process criminal-justice data—effectively disqualifying them from law-enforcement contracts and public-safety technology markets.
What Does CJIS Compliance Require: The Security Framework & Standards
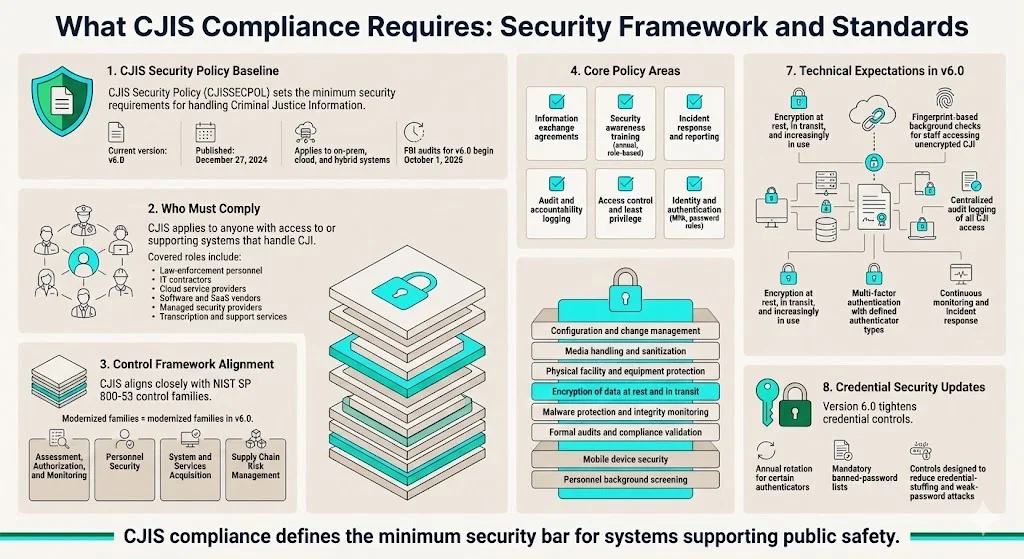
The CJIS Security Policy—often abbreviated as CJISSECPOL—establishes the baseline security requirements for all entities handling CJI. The FBI's CJIS Security Policy v6.0 (Dec 27, 2024) is the current baseline for how state, local, and higher-ed public safety programs must protect that data—regardless of whether systems run on-prem, in the cloud, or hybrid. FBI CJIS audit of version 6.0 will start on October 1, 2025, establishing the enforcement timeline for agencies and vendors.
This Policy applies to every individual—contractor, private entity, noncriminal justice agency representative, or member of a criminal justice entity—with access to, or who operate in support of, criminal justice services and information. The policy's reach extends beyond law-enforcement personnel to encompass IT contractors, cloud-service providers, software vendors, transcription services, managed-security providers, and any entity that creates, accesses, stores, transmits, or destroys CJI.
The policy organizes requirements into control families corresponding closely with NIST SP 800-53, the foundational security-control framework for federal information systems. Version 6.0 contains modernized control families of Assessment, Authorization, & Monitoring, Personnel Security, System and Services Acquisition, and Supply Chain Risk Management. The 13 core policy areas include information-exchange agreements establishing legal frameworks for data sharing; security-awareness training requiring annual role-based instruction for all personnel with CJI access; incident-response procedures defining detection, reporting, and remediation protocols; audit and accountability controls mandating centralized logging with time synchronization and defined retention periods; access-control mechanisms limiting CJI access to authorized users based on need-to-know principles; and identity and authentication requirements including multi-factor authentication for remote access and password policies incorporating banned-password lists.
Additional domains cover configuration management ensuring secure baseline configurations and change-control processes; media protection governing handling, storage, and sanitization of devices containing CJI; physical-protection controls securing facilities, equipment, and media against unauthorized access; system and communications protection requiring encryption of CJI in transit and at rest; information-integrity controls implementing malware protection and system monitoring; formal audits establishing compliance-verification mechanisms; personnel security mandating background checks for individuals with unescorted access to CJI or unencrypted CJI access; and mobile-device security governing smartphones, tablets, and laptops accessing CJI.
For cloud service providers and vendors, compliance requires technical implementation and contractual commitments. All private contractors who process CJI must sign the CJIS Security Addendum, a uniform agreement approved by the US Attorney General that helps ensure the security and confidentiality of CJI required by the Security Policy. This addendum commits contractors to maintaining security programs consistent with federal and state requirements and limits CJI use to authorized purposes.
Version 6.0 reinforces that the policy is architecture-independent and explicitly empowers agencies to tune implementations to risk while still meeting the common baseline. Cloud providers must implement encryption for data at rest, in transit, and increasingly in use; enforce multi-factor authentication with defined authenticator-type requirements; conduct personnel screening including fingerprint-based criminal-history checks for employees accessing unencrypted CJI; establish audit logging capturing all CJI access events; and demonstrate continuous monitoring and incident-response capabilities.
Version 6.0 spells out which authenticator types must change annually and the use of a "banned password" list—addressing credential-stuffing attacks and weak-password risks that compromise law-enforcement systems.
Who Needs CJIS Compliance: Agencies and Private Businesses
Law-enforcement agencies at every jurisdictional level require CJIS compliance: local police departments, county sheriffs, state police and bureaus of investigation, federal law-enforcement agencies, and tribal law enforcement accessing CJI databases or maintaining criminal-justice records.
Private contractors, vendors, and cloud service providers must comply when their services involve CJI. This includes cloud-infrastructure providers hosting law-enforcement applications or data; software-as-a-service platforms managing criminal records, case files, or evidence; managed-security providers monitoring law-enforcement networks; transcription services processing interrogation recordings or court proceedings; data-analytics firms analyzing criminal-justice datasets; body-camera vendors storing video evidence; records-management-system providers; computer-aided-dispatch software vendors; jail-management-system operators; and IT support firms maintaining law-enforcement technology infrastructure.
Third-party service providers supporting criminal-justice functions—even when not directly accessing CJI—may require compliance depending on their system access and data-handling roles. An IT contractor managing servers that store CJI requires compliance even if they don't routinely view criminal records. A cloud provider hosting applications that process CJI requires compliance regardless of whether provider personnel access customer data.
For enterprise-software sellers, CJIS compliance becomes a qualification threshold. If your platform, infrastructure, or services will be used by law-enforcement customers to handle criminal-justice information—or if your systems will integrate with CJIS databases—you cannot compete for contracts without demonstrating compliance. There are CJIS Management Agreements covering criminal justice agencies in 47 states and the District of Columbia, creating a nationwide compliance requirement for vendors serving law-enforcement markets.
What Happens If You Don't Comply—Risks for Businesses

Noncompliance with CJIS requirements triggers immediate operational and legal consequences. Law-enforcement agencies lose access to CJIS databases and criminal-justice information systems when they fail audits or violate security-policy requirements—disrupting investigations, preventing warrant verifications, and eliminating access to fingerprint databases and criminal histories.
For private entities, noncompliance results in contract termination, legal liability, and potential criminal charges. Vendors handling CJI without proper agreements, security controls, or personnel screening violate federal requirements governing criminal-justice information. State statutes typically establish criminal penalties for unauthorized CJI access or disclosure, and civil liability attaches when data breaches compromise criminal-justice information.
Reputational damage compounds financial and legal risks. Law-enforcement agencies operate in a tightly networked professional community where security failures become widely known. A vendor experiencing a CJI breach or compliance failure loses credibility across the entire law-enforcement market, as agencies share information about contractor performance and security incidents through professional associations, state CJIS systems officers, and the FBI CJIS Advisory Policy Board.
Operational disruption extends beyond individual vendor relationships. Agencies relying on noncompliant systems must migrate to alternative platforms mid-contract, recreate functionality, and retrain personnel—investments that create reluctance to adopt vendor solutions without verified compliance. For vendors, remediation requires comprehensive security-program restructuring, potentially including facility modifications for physical security, personnel screening for existing employees, system-architecture changes to implement encryption and access controls, and formal audit processes to demonstrate compliance—efforts requiring 6-12 months and substantial capital investment.
What Businesses Should Do If They Sell to Entities That Need CJIS Compliance
Evaluate whether your services involve handling CJI by examining your platform's data flows, storage architecture, and integration points with law-enforcement systems. Cloud storage, managed services, software platforms, data-processing tools, and infrastructure supporting law-enforcement clients typically require compliance if they access, store, transmit, or process criminal-justice information.
Review the CJIS Security Policy comprehensively—examine the control families and map requirements to your existing security practices. Assess gaps in access control, encryption implementation, audit logging, physical security, personnel screening, incident response, security-awareness training, and configuration management. Version 6.0 emphasizes encryption for data at rest and in transit, multi-factor authentication enforcement, personnel background checks for unencrypted CJI access, and supply-chain risk management for third-party components.
If your infrastructure operates in cloud environments, implement encryption with customer-controlled keys, restrict cloud-provider personnel access to encrypted data only, establish audit trails capturing all access events, and document security controls demonstrating compliance with CJIS requirements. Commercial cloud providers including Microsoft Azure Government, Amazon Web Services GovCloud, and Google Cloud have achieved CJIS compliance for their infrastructure—but customer applications and configurations require separate compliance verification.
Sign required agreements, typically the CJIS Security Addendum, with each state where your law-enforcement clients operate. States administer CJIS compliance through Criminal Justice Information Services officers and State Identification Bureaus, and each jurisdiction maintains specific agreement templates and approval processes. Identify the CJIS Systems Officer in each relevant state and initiate the agreement process early—approvals require security-program review and can extend 90-180 days.
Implement strong identity and authentication practices including multi-factor authentication for all remote access to systems handling CJI, password policies incorporating banned-password lists and annual credential rotation for specified authenticator types, and role-based access control limiting CJI access to personnel with documented need-to-know justification. Establish security-awareness training programs delivering annual instruction to all employees who create, store, transmit, or access CJI—including IT staff, support personnel, and contractors.
Deploy comprehensive audit logging capturing all CJI access events, system modifications, authentication attempts, and security-relevant activities; centralize logs with time synchronization ensuring forensic reliability; protect log integrity through access controls and encryption; retain logs per policy requirements; and establish monitoring processes alerting security teams to anomalous access patterns or potential incidents.
Build incident-response processes defining detection mechanisms, escalation procedures, notification requirements to affected agencies and CJIS authorities, containment and remediation protocols, and post-incident analysis. Law-enforcement agencies require rapid notification of security incidents affecting CJI, and delayed or inadequate responses trigger compliance violations.
How CJIS Connects to Broader Themes: Public Safety, Data Security & Enterprise Tech
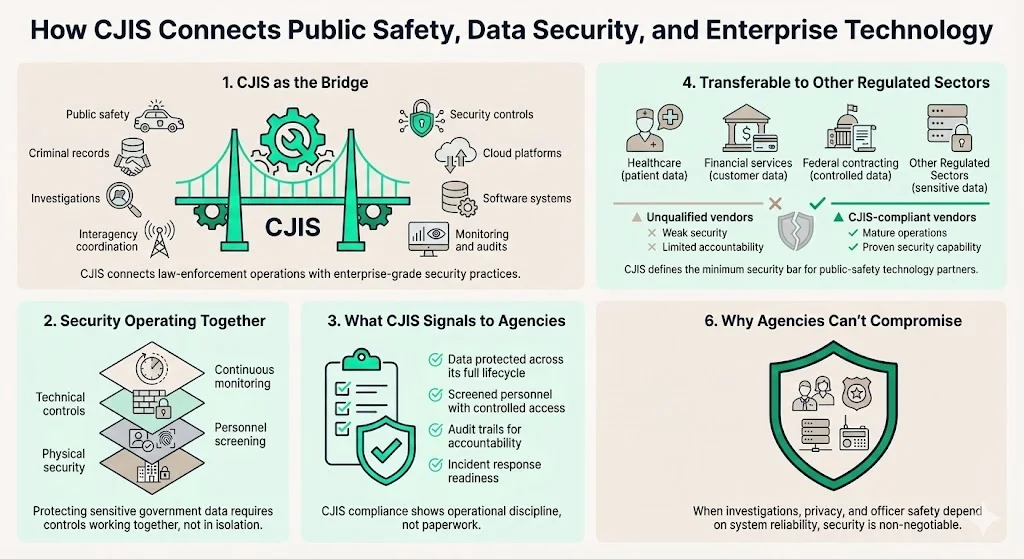
CJIS bridges law-enforcement operational needs—public safety, criminal-records management, interagency coordination, and investigative support—with enterprise-grade security and technology practices. The framework demonstrates that protecting sensitive government data requires technical controls, personnel screening, physical security, and continuous monitoring operating in concert.
For enterprises, compliance transcends checkbox exercises. CJIS compliance signals to law-enforcement clients that your organization understands the sensitivity of criminal-justice information, implements controls protecting data throughout its lifecycle, screens personnel accessing sensitive systems, maintains audit trails supporting accountability, and responds effectively to security incidents. These capabilities transfer to other regulated sectors—healthcare organizations managing HIPAA data, financial institutions protecting customer information, and federal contractors handling controlled unclassified information recognize similar control requirements.
As governments and criminal-justice agencies adopt cloud-based platforms, software-driven workflows, and mobile technologies, CJIS establishes the security threshold separating professional vendors from unqualified suppliers. Agencies cannot compromise on security when criminal investigations, victim privacy, and officer safety depend on data confidentiality and system availability. Vendors meeting CJIS requirements demonstrate operational maturity and security competence that differentiates them in competitive procurements.
Conclusion
CJIS—Criminal Justice Information Services—represents more than an acronym. It's a comprehensive security framework and policy structure governing how criminal-justice data must be protected across its lifecycle, enforced by the FBI and administered through state-level authorities across 47 states and the District of Columbia.
For businesses targeting law-enforcement, public-safety, or criminal-justice markets, understanding CJIS and implementing compliant systems determines market access. The security policy's control requirements—encryption, multi-factor authentication, personnel screening, audit logging, incident response, and physical security—establish baseline expectations that professional vendors must meet.
Organizations planning to engage criminal-justice agencies should assess their platforms early, identify compliance gaps, implement required controls, and secure necessary agreements before pursuing contracts. The alternative—attempting to retrofit compliance after winning business—creates implementation delays, cost overruns, and reputational damage that eliminate competitive advantage and threaten client relationships.
Frequently Asked Questions (FAQ)
1) What does CJIS stand for?
CJIS stands for Criminal Justice Information Services—both the FBI division that administers criminal-justice databases and information systems, and the security policy framework governing how Criminal Justice Information must be protected.
2) What is a CJIS security clearance?
CJIS security clearance refers to the personnel-security requirements individuals and vendors must satisfy to access Criminal Justice Information. Requirements include fingerprint-based criminal-history background checks for personnel with unescorted physical access to CJI systems or logical access to unencrypted CJI, security-awareness training completed annually, signed acknowledgment of security responsibilities, and compliance with access-control policies limiting CJI access to authorized purposes. Cloud providers and contractors must conduct these background checks for employees accessing systems containing CJI, and agencies verify clearance status during audits.
3) What is CJIS compliance for law enforcement?
CJIS compliance means adhering to the CJIS Security Policy providing guidance for the creation, viewing, modification, transmission, dissemination, storage, and destruction of CJI. Law-enforcement agencies must implement required controls across 13 policy areas including access control, audit and accountability, security-awareness training, incident response, identity and authentication, configuration management, encryption, physical security, personnel screening, and mobile-device security. Compliance ensures confidentiality, integrity, and availability of criminal-justice information while enabling interagency data sharing and supporting investigative operations.
4) Who needs CJIS compliance?
All law-enforcement agencies—local police departments, county sheriffs, state police, federal agencies, and tribal law enforcement—accessing CJI databases or maintaining criminal-justice records require CJIS compliance. Private contractors, cloud providers, software vendors, transcription services, managed-security providers, data-analytics firms, and any entity storing, processing, or transmitting CJI must comply. This includes companies providing infrastructure, applications, or services to law-enforcement clients when those systems handle criminal-justice information. Vendors serving law-enforcement markets cannot compete for contracts without demonstrating CJIS compliance and signing required security addendums.



.svg)
.svg)
.svg)