Most organizations competing for Department of Defense contracts treat cybersecurity requirements as administrative checkboxes rather than operational imperatives. This approach creates a fundamental gap between stated compliance and actual security posture—a gap that becomes critically apparent when CMMC certification requirements enter contract language. The DoD reported over 12,000 cyber incidents affecting defense contractors between 2018 and 2023, demonstrating why self-attestation alone no longer suffices. CMMC certification represents a structural shift: third-party verification of cybersecurity controls before contract awards, not after breaches occur.
What Is CMMC Certification?
Cybersecurity Maturity Model Certification (CMMC) is a Department of Defense regulatory framework that verifies cybersecurity practices and controls before contractors can handle Federal Contract Information (FCI) or Controlled Unclassified Information (CUI). FCI is unclassified information not intended for public release that is provided by or generated for the Government under a contract. CUI is unclassified information the Government creates or possesses that a law, regulation, or Government-wide policy requires or permits an agency to handle using safeguarding or dissemination controls.
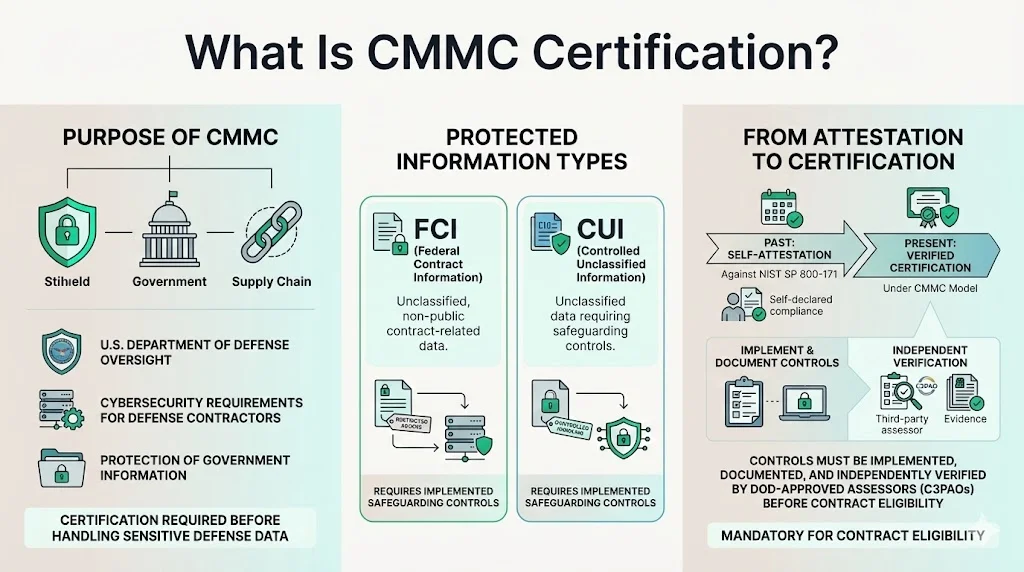
The Department of Defense created CMMC in 2019 to transition from self-attestation mechanisms after a series of breaches in the supply chain. Unlike previous compliance approaches where defense contractors self-assessed their cybersecurity readiness against NIST SP 800-171, CMMC moves to a certification-based approach verified by DoD-approved third-party assessors known as CMMC Third Party Assessor Organizations (C3PAOs). This represents a fundamental shift from attestation to validation—contractors must demonstrate implemented controls through documented evidence and independent assessment before contract award eligibility.
Why CMMC Matters for Companies
The defense industrial base faces increasingly frequent and complex cyberattacks, creating cascading risk across supply chains. CMMC addresses this systemic vulnerability by requiring verified cybersecurity implementation rather than self-reported compliance. For organizations pursuing DoD contracts, CMMC certification directly determines contract eligibility—noncompliant contractors will be ineligible for contract awards.
Beyond contract access, CMMC requirements establish baseline security infrastructure that reduces organizational exposure to cyber incidents. Organizations handling CUI face heightened scrutiny because compromised information can affect national security operations. CMMC impacts the $768 billion Defense industry, representing 3.2% of United States GDP, demonstrating the program's economic scope.
The consequences of non-compliance extend beyond missed contract opportunities. The Department of Justice's Civil Cyber-Fraud Initiative actively pursues False Claims Act actions against defense contractors for alleged failures to comply with cybersecurity requirements in the DFARS. Additionally, DoD reserves the right to investigate contractors that have achieved CMMC certification to verify continued compliance, and investigations revealing inadequate control implementation may result in contract termination and other contractual remedies.
CMMC 2.0: The Current Framework
The CMMC Program final rule became effective December 16, 2024. The DFARS Final Rule was published in the Federal Register on September 10, 2025, with a 60-day window before clauses begin appearing in contracts, meaning contractors could see DFARS 252.204-7021 requirements starting November 10, 2025.
CMMC 2.0 streamlines requirements to three levels of cybersecurity and aligns requirements at each level with well-known and widely accepted NIST cybersecurity standards. This revision reduced complexity from the original five-level model while maintaining rigorous security controls. The framework integrates directly into Defense Federal Acquisition Regulation Supplement (DFARS) clauses, making CMMC certification a contractual prerequisite rather than a voluntary standard.
Understanding the Three CMMC Levels
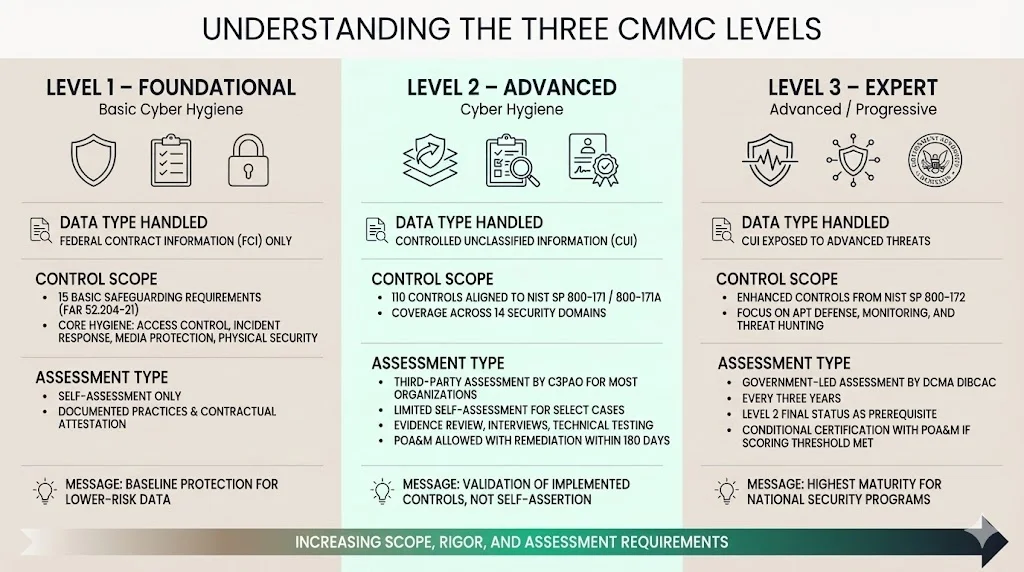
Level 1 – Foundational
Level 1 targets organizations handling Federal Contract Information without Controlled Unclassified Information. CMMC Level 1 Self-Assessment requires compliance with the 15 basic safeguarding requirements to protect FCI as set forth in FAR clause 52.204-21. These controls address fundamental cybersecurity hygiene: access control mechanisms, basic incident response procedures, media protection, and physical security measures.
Level 1 self-assessment is the term for the activity performed by an organization to evaluate its own information system. No third-party assessment is required at this level—organizations document their implementation of required practices and affirm compliance through contractual attestation. This approach recognizes that FCI, while sensitive, does not present the same risk profile as CUI.
Level 2 – Advanced
Level 2 applies to organizations handling Controlled Unclassified Information. CMMC mandates contractors and subcontractors handling CUI obtain third-party assessments and certifications verifying their compliance with the 110 cybersecurity controls set forth in National Institute of Standards & Technology Special Publication 800-171A. These controls span 14 security domains including access control, audit and accountability, configuration management, identification and authentication, incident response, risk assessment, security assessment, system and communications protection, and system and information integrity.
Self-assessments can be performed for a small subset of level 2 organizations, while the remaining Level 2 organizations will be required to hire a Certified Third-Party Assessor Organization (C3PAO) to conduct their assessment. The determination of which organizations require third-party assessment versus self-assessment depends on contract-specific requirements and the sensitivity of CUI handled. The CMMC rule is built on the assumption that contractors have already implemented NIST SP 800-171, as CMMC was created to validate NIST 800-171 implementation.
Assessment rigor at Level 2 includes documentation review, interview validation, and technical testing of implemented controls. Assessors verify that policies exist, personnel understand requirements, and technical configurations match documented procedures. Organizations may receive conditional certification if they document deficiencies in a Plan of Action and Milestones (POA&M), provided they meet scoring thresholds and commit to remediation within 180 days.
Level 3 – Expert
Level 3 represents the highest maturity tier, designed for organizations protecting CUI against Advanced Persistent Threats (APTs). A CMMC Level 3 Assessment is conducted by the Defense Contract Management Agency (DCMA) Defense Industrial Base Cybersecurity Assessment Center (DIBCAC) to validate implementation of selected DoD-defined security requirements set forth in NIST SP 800-172. These enhanced security requirements add proactive threat hunting, advanced monitoring capabilities, and protective measures against sophisticated nation-state adversaries.
Level 3 assessments are conducted every three years, with a Final Level 2 status for information systems within the Level 3 CMMC Assessment Scope serving as a prerequisite to undergo a Level 3 certification assessment. Only government-led assessors conduct Level 3 evaluations, reflecting the national security sensitivity of programs requiring this level. POA&Ms are permitted for select Level 3 requirements if the assessment score divided by the total number of security requirements is greater than or equal to 0.8, with a Conditional Level 3 status indicating there are POA&M items that must be closed and assessed within 180 days.
Who Needs CMMC Certification
DoD developed the Cybersecurity Maturity Model Certification Program to assess DoD cybersecurity requirements pertaining to Federal Contract Information and Controlled Unclassified Information. This includes prime contractors directly awarded DoD contracts and subcontractors at any tier within the supply chain who handle FCI or CUI.
DoD contractors and subcontractors handling FCI or CUI must achieve a specific CMMC level as a condition of contract award. The required level is specified in the contract solicitation based on the information types the contractor will access, store, process, or transmit. The program outlines the process for requiring protection of information flowed down to subcontractors, meaning prime contractors must verify that their supply chain partners meet appropriate CMMC levels before engaging them on covered contracts.
Even small businesses operating as third- or fourth-tier subcontractors fall within CMMC scope if they handle covered information. The certification requirement flows down through subcontract agreements, creating contractual obligations independent of direct DoD relationships. Organizations may find themselves subject to CMMC requirements through commercial agreements with prime contractors who embed these terms in their vendor agreements.
The Certification Process
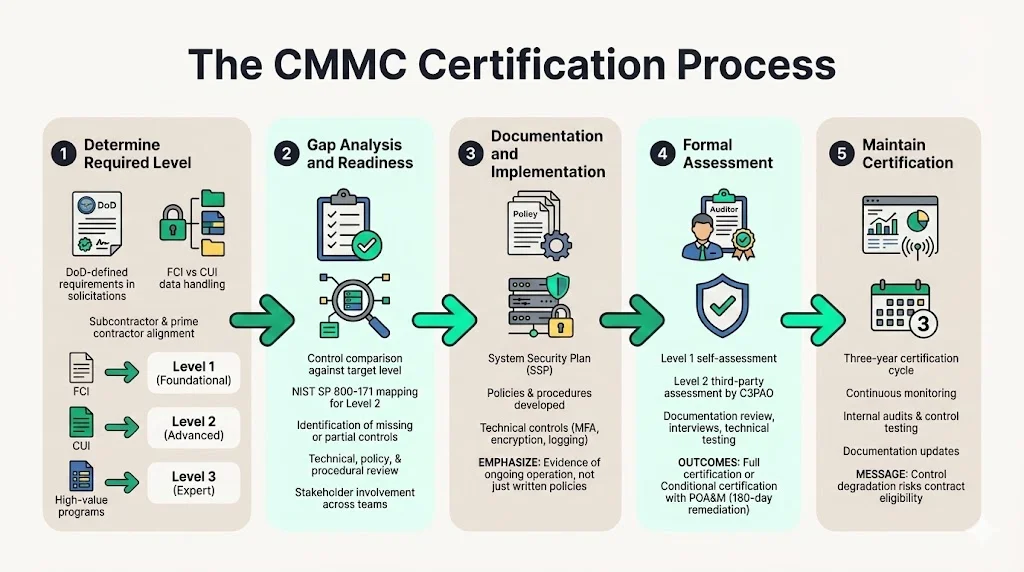
1) Determine Your Required Level
DoD Program Managers determine the type of CMMC assessment based on the type of data (FCI or type of CUI) handled and managed by the contractor and subcontractors in the performance of a contract. Review solicitation language for specified CMMC level requirements. If pursuing subcontract work, confirm requirements with the prime contractor. Organizations handling only FCI typically require Level 1, while CUI handling necessitates Level 2. Level 3 applies only to specific high-value programs with advanced threat environments.
2) Gap Analysis & Readiness Assessment
Compare current security practices against required controls for your target level. Conduct systematic assessment of technical configurations, documented policies, implemented procedures, and evidence collection mechanisms. Identify gaps between current state and required practices across all control families. For Level 2 organizations, map existing controls to NIST SP 800-171 requirements, documenting which controls are fully implemented, partially implemented, or not implemented.
Engage internal stakeholders across IT operations, security teams, compliance functions, and business units to understand existing capabilities. Review system security plans, network diagrams, access control matrices, incident response playbooks, and vulnerability management processes. This readiness assessment establishes baseline maturity and informs remediation priorities.
3) Documentation and Implementation
Create comprehensive documentation demonstrating control implementation. Required artifacts include System Security Plans (SSPs) describing the information system boundary, data flows, security controls, and responsible parties. Develop policies and procedures addressing each required practice area. Implement technical controls such as multi-factor authentication, encryption, logging and monitoring, vulnerability scanning, and configuration management.
Establish evidence collection procedures demonstrating continuous control operation. This includes access logs, vulnerability scan reports, patch management records, security training completion documentation, incident response records, and risk assessment outputs. Documentation must demonstrate not just that policies exist, but that controls operate effectively over time.
4) Formal Assessment
For Level 1, complete self-assessment documentation and maintain records supporting attestation. For Level 2 organizations requiring third-party assessment, C3PAOs are authorized by the CMMC Accreditation Board to conduct these third-party assessments. Entities handling CUI and expecting to be subject to CMMC Level 2 external assessments should engage C3PAOs to plan their assessments, as C3PAOs will be in high demand and scheduling early assessments may avoid potential C3PAO scheduling constraints.
During assessment, C3PAOs review documentation, interview personnel, and conduct technical testing to verify control implementation. The assessment validates that documented policies align with actual practices and that technical configurations match security requirements. Organizations receive a final certification if all requirements are met, or conditional certification with POA&M items requiring remediation within 180 days.
5) Maintaining Certification
CMMC certification is valid for three years, after which organizations must undergo re-assessment to maintain their CMMC status. Between assessments, organizations must maintain continuous compliance with certified controls. This requires ongoing monitoring, periodic internal audits, security control testing, and documentation updates reflecting system changes.
Implement continuous monitoring capabilities tracking control effectiveness metrics. Conduct quarterly internal assessments verifying controls remain operational. Update documentation when system changes affect security boundaries, data flows, or control implementations. Maintain evidence repositories demonstrating sustained compliance throughout the certification period. Organizations that allow controls to degrade risk failed re-assessment and potential contract implications.
Common Challenges and Practical Tips
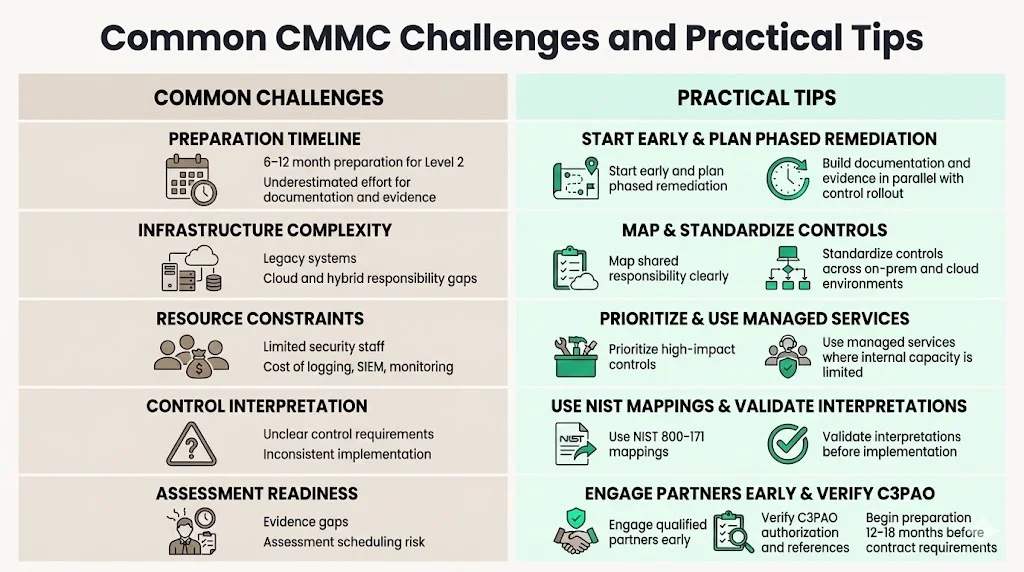
Organizations take an average of 6-12 months to prepare for a CMMC Level 2 assessment. This timeline reflects the complexity of implementing 110 security controls across diverse technical environments while maintaining business operations. Organizations frequently underestimate the effort required for documentation development, evidence collection automation, and technical remediation.
Integrating CMMC controls with existing infrastructure presents technical and operational challenges. Legacy systems may not support required security capabilities such as multi-factor authentication or encryption. Cloud environments introduce complexity around responsibility matrices and shared control implementations. Organizations operating hybrid environments must implement consistent controls across on-premises and cloud systems.
Resource constraints affect smaller organizations disproportionately. Implementing advanced logging, Security Information and Event Management (SIEM) platforms, vulnerability management programs, and continuous monitoring capabilities requires budget allocation and specialized expertise. Organizations lacking dedicated security staff struggle to interpret control requirements and design appropriate implementations.
Many organizations engage specialized partners—managed security service providers, compliance consultants, or C3PAO organizations—to accelerate readiness. These partners provide gap assessments, remediation roadmaps, technical implementation support, and assessment preparation. Organizations should verify partner credentials, request client references, and confirm C3PAO authorization status before engagement. Starting preparation early—12-18 months before contract solicitations requiring certification—provides adequate time for systematic implementation without operational disruption.
Benefits Beyond Compliance
CMMC certification strengthens overall cybersecurity posture beyond DoD contract requirements. Implementing NIST SP 800-171 controls establishes security foundations applicable to other regulatory frameworks including HIPAA, state privacy laws, and international standards. Organizations find that controls addressing access management, encryption, incident response, and vulnerability management reduce exposure across their entire threat landscape, not just government contracts.
Certification adds credibility with enterprise clients evaluating vendor security practices. Commercial customers increasingly require security attestations during vendor risk assessments. CMMC certification provides third-party validation demonstrating mature security programs, differentiating certified organizations in competitive evaluations. This credibility extends to cyber insurance underwriting, where insurers recognize certified organizations as lower-risk and may offer favorable premium terms.
Investment in security infrastructure reduces incident likelihood and associated costs. Organizations with mature access controls, logging, and monitoring detect threats earlier and respond more effectively. This operational resilience protects intellectual property, customer data, and business continuity—outcomes valuable independent of compliance mandates.
Conclusion
CMMC certification represents a fundamental shift in how the Department of Defense verifies contractor cybersecurity capabilities. With the final rule effective December 16, 2024, and contract clauses appearing starting November 10, 2025, organizations competing for DoD contracts face immediate certification requirements. The average 6-12 month preparation timeline means organizations must begin gap assessments, remediation planning, and implementation efforts now to maintain contract eligibility.
CMMC is not a project with a defined endpoint—it establishes ongoing operational requirements maintained throughout three-year certification periods. Organizations treating CMMC as administrative compliance rather than security infrastructure investment will struggle during assessments and re-assessments. Those that implement genuine security controls protecting sensitive information will find certification validates capabilities while strengthening overall cyber resilience.
FAQs
1) What is CMMC certification?
A certification program by the U.S. Department of Defense that verifies a company's cybersecurity practices and controls before they can handle certain sensitive government information or win relevant contracts. CMMC moved from self-attestation to third-party validation of security control implementation.
2) Who is required to meet CMMC requirements?
Companies, contractors, and subcontractors in the Defense Industrial Base handling Federal Contract Information (FCI) or Controlled Unclassified Information (CUI). Requirements flow down through contract terms to subcontractors at any tier handling covered information.
3) What are the current CMMC levels?
Three levels: Level 1 (Foundational) for FCI protection with 15 basic safeguarding requirements and self-assessment; Level 2 (Advanced) for CUI protection aligned with NIST SP 800-171's 110 security controls requiring third-party assessment for most organizations; Level 3 (Expert) for CUI protection against advanced threats with NIST SP 800-172 enhanced requirements and government-led assessment.
4) How long does CMMC certification take?
Organizations typically require 6-12 months from start to certification, depending on current security maturity, scope of systems handling covered information, and complexity of technical environment. Organizations with mature NIST SP 800-171 implementations may achieve certification faster, while those starting from baseline capabilities require longer preparation periods.
5) What happens if a contractor fails CMMC?
Contractors not certified at the required level are ineligible for DoD contract awards. Organizations may also face contract termination on existing agreements if they fail to maintain certification or if post-certification investigations reveal inadequate control implementation. The Department of Justice's Civil Cyber-Fraud Initiative pursues False Claims Act actions against contractors misrepresenting cybersecurity compliance.



.svg)
.svg)
.svg)