Most organizations treat security as a deployment checkpoint—something to verify before release. This approach creates a fundamental gap between development velocity and risk mitigation, a gap that becomes apparent when vulnerabilities reach production or audit evidence reveals systemic control failures.
Continuous integration has evolved from a code-quality practice into a security discipline. CI enables developers to merge code changes repeatedly into a shared repository, with each integration triggering automated builds and tests that identify errors earlier than traditional methods. For enterprise software organizations managing SOC 2 attestations, ISO 27001 certification cycles, or GDPR compliance obligations, CI pipelines represent the infrastructure through which security controls are implemented, validated, and documented—not merely where code is assembled.
This article examines how continuous integration supports data protection standards through automated security testing, the specific controls required in CI/CD environments, and actionable guidance for organizations selling to enterprises where compliance expectations determine vendor selection.
What is Continuous Integration?
Continuous Integration is a collaborative working model where developers merge changes into a single code base repeatedly and at short intervals, with each integration triggering an automated build that allows teams to identify and rectify errors much earlier than traditional methods. The practice originated as a quality assurance technique but has become a foundational element of secure software development lifecycles.
Organizations implementing CI establish a central repository where all code changes undergo immediate validation. Rather than accumulating weeks of development work before integration testing, teams commit code multiple times daily, triggering automated builds that compile the application, execute test suites, and report failures within minutes of the commit.
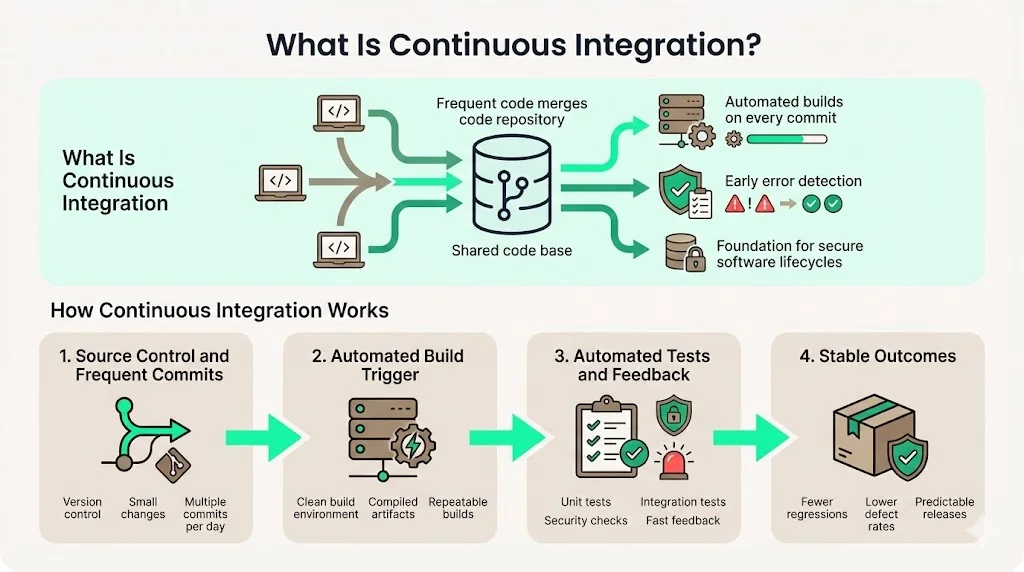
How Continuous Integration Works
CI operates through four interconnected mechanisms:
Source control and frequent commits: Developers commit code changes to a version control system (Git, SVN) multiple times per day rather than holding changes locally for extended periods. Each commit represents a discrete, testable unit of work.
Triggering automated builds: The version control system notifies the CI server of new commits. The CI server retrieves the latest code, compiles it in a clean environment, and produces build artifacts. This automation eliminates "it works on my machine" discrepancies that plague manual build processes.
Running automated tests and reporting failures: Once the build completes, the CI server executes unit tests, integration tests, and—in security-focused implementations—vulnerability scans, dependency checks, and policy validations. Test results return to developers within minutes, enabling immediate remediation while context remains fresh.
Stable and predictable software outcomes: By catching integration failures, broken dependencies, and test regressions immediately, CI prevents the accumulation of technical debt and reduces the defect rate in downstream environments. Developers who incorporate CI/CD tools work 15% more effectively than their peers because testing and deployment problems are solved faster, improving overall efficiency while enhancing speed, repeatability, and quality.
CI vs CD
Continuous Integration and Continuous Delivery represent distinct but complementary practices. CI focuses on integrating code changes frequently with automated builds and tests, while CD extends CI by automating deployments to staging or production environments. CI answers the question "Does this code compile and pass tests?" CD answers "Can this code be deployed to production reliably?"
The distinction matters for compliance documentation. SOC 2 Type II reports require evidence of control effectiveness over time. CI controls—automated testing, code review gates, access restrictions—operate continuously throughout development. CD controls—deployment approvals, rollback mechanisms, production access logs—govern release operations. Both contribute to the audit trail, but they address different control objectives within the Trust Services Criteria.
Why Data Protection Matters for Enterprise Software
Enterprise buyers evaluate vendors through the lens of risk transfer. When an organization processes customer data, manages financial transactions, or handles protected health information, that organization assumes legal liability for data protection failures. Vendor selection decisions hinge on documented proof that security controls exist, operate effectively, and undergo regular validation.
ISO 27001 certification requires establishing an Information Security Management System with documented risk assessments, statement of applicability, and continuous improvement cycles. SOC 2 Type II attestation requires documented evidence of control effectiveness over a minimum six-month observation period. GDPR compliance extends beyond consent management to encompass data minimization principles, purpose limitation, and documented legitimate interests assessments. HIPAA compliance requires implementing administrative, physical, and technical safeguards specifically designed to protect electronic protected health information throughout its lifecycle.
These frameworks share a common requirement: organizations must demonstrate that security is systematic, repeatable, and verifiable—not ad hoc or reactive. CI pipelines provide the infrastructure through which these requirements are satisfied. Every code commit, test execution, vulnerability scan, and deployment creates an audit record. Every policy gate that blocks a build with failing security checks demonstrates control effectiveness. Every automated check that prevents credential exposure or dependency vulnerabilities shows proactive risk mitigation.
Organizations lacking documented CI security controls face predictable audit findings: insufficient evidence of secure development practices, inadequate separation of duties, missing traceability between code changes and test results, and inability to demonstrate continuous compliance validation.
Where Security Fits in Continuous Integration
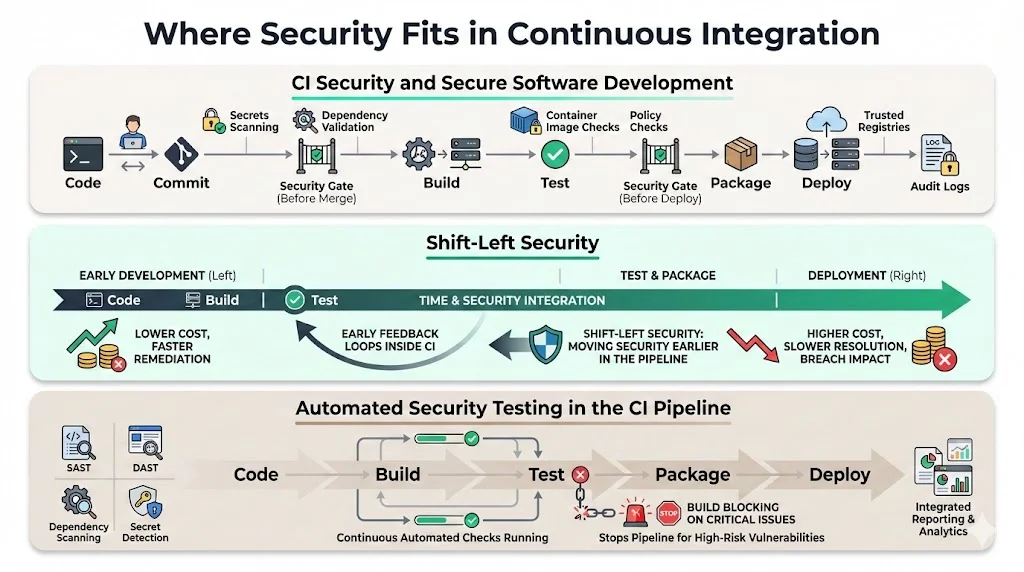
1) CI security and secure software development
CI/CD security refers to practices meant to secure each phase of the development process in the pipeline of continuous integration and deployment. These practices extend beyond application security testing to encompass infrastructure hardening, access controls, secrets management, and audit logging.
Secure development within CI pipelines embeds verification at every stage. Before code merges, automated checks validate that commits don't contain hardcoded credentials, that dependencies lack known critical vulnerabilities, and that new code meets code quality thresholds. Before deployments proceed, additional checks confirm that container images come from trusted registries, that infrastructure configurations comply with security policies, and that required approvals have been obtained.
CI/CD combined with DevSecOps becomes the backbone of modern development practices as organizations move toward faster delivery cycles and secure applications. The integration isn't optional for organizations pursuing enterprise sales—documented security controls in CI pipelines directly support compliance attestation requirements.
2) Shift-left security: what it means and why it matters
Shift-left security integrates security measures early in the software development lifecycle, particularly within the CI/CD pipeline, and by 2025 has become a cornerstone ensuring security is not an afterthought but a fundamental aspect of development.
The term "shift-left" references the traditional software development timeline diagram, where development activities appear on the left and operations/deployment on the right. Shifting security left means performing security validation during development rather than before production release.
The economic rationale is straightforward: identifying a SQL injection vulnerability during code review costs developer time measured in minutes. Discovering the same vulnerability during a pre-production security assessment costs hours of remediation work, retesting, and deployment delays. Finding it after a data breach costs legal fees, regulatory fines, customer notification expenses, and reputational damage measured in millions.
With increasing frequency and sophistication of cyber-attacks, identifying and mitigating vulnerabilities early in the development process is crucial. Organizations selling to enterprises face heightened scrutiny—buyers demand evidence that vendors implement security controls commensurate with the risk their software introduces.
3) Automated security testing in the CI pipeline
Security testing in CI pipelines encompasses multiple scanning techniques, each addressing different vulnerability categories:
Static Application Security Testing (SAST) analyzes source code or compiled binaries without executing the application, identifying patterns that indicate security weaknesses—SQL injection, cross-site scripting, buffer overflows, insecure cryptographic implementations.
Dynamic Application Security Testing (DAST) tests running applications by simulating attacks, identifying runtime vulnerabilities like authentication bypasses, session management flaws, and server misconfigurations.
Dependency scanning examines third-party libraries and packages, comparing versions against vulnerability databases (CVE, GitHub Advisory Database) to identify components with known security issues.
Secret detection scans commits for patterns matching API keys, passwords, private keys, and authentication tokens, preventing credential exposure in version control.
Automated security testing integrates into CI workflows, continuously monitors compliance with regulations, and defines thresholds for code coverage, security scans, and performance benchmarks. These thresholds become compliance controls. A policy that blocks builds containing critical-severity vulnerabilities isn't just a security measure—it's documented evidence of preventive controls for auditors.
CI/CD Security Controls Your Pipeline Should Include
1) Access controls and least privilege
Only authenticated, authorized users should trigger builds, modify pipeline configurations, or access deployment credentials. This requires implementing role-based access control (RBAC) that maps developers to specific permissions, enforcing multi-factor authentication for pipeline access, and logging all authentication attempts.
ISO 27001 Control A.9.2 (User Access Management) and SOC 2 CC6.2 (Logical and Physical Access Controls) require documented evidence that access rights are restricted based on job responsibilities. CI pipeline access logs provide this evidence.
2) Secrets management and credential protection
Attackers have exploited CI/CD pipelines by using exposed secrets to gain initial access, with secrets like private keys and passwords required for authentication between tools and in the build and deployment process.
Effective secrets management requires three mechanisms: storing credentials in dedicated vaults (HashiCorp Vault, AWS Secrets Manager) rather than environment variables or configuration files; rotating credentials regularly with automated workflows; and implementing secret detection tools that scan every commit before merge.
Cloud native CI/CD tools employ numerous secrets to gain access to sensitive systems, creating extensive attack surfaces. Organizations must treat secrets as critical assets requiring the same protection as production database credentials.
3) Dependency and artifact scanning
Modern applications incorporate dozens to hundreds of third-party dependencies—libraries, frameworks, packages—each representing potential supply chain risk. Dependency scanning identifies components with known vulnerabilities, outdated versions, or licensing issues.
Integrating vulnerability scanning tools directly into CI/CD pipelines catches security issues like outdated libraries, misconfigurations, or malicious code before they reach staging or production, with continuous scanning ensuring newly discovered vulnerabilities in images or dependencies aren't missed.
Artifact scanning extends this principle to compiled outputs—container images, deployment packages, compiled binaries. Before artifacts move from build to deployment, scans verify image integrity, check base images for vulnerabilities, and validate that artifacts haven't been tampered with during the build process.
4) Policy checks and compliance gates
Policy gates implement "break the build" logic: if security criteria aren't met, the pipeline halts. Common policies include blocking deployments when critical vulnerabilities exceed defined thresholds, requiring code review approval before merging, preventing deployments that fail compliance checks, and enforcing code coverage minimums.
These gates transform security requirements into enforceable controls. Rather than relying on developers to check vulnerability reports manually, the pipeline prevents insecure code from progressing. Rather than hoping code reviews occur, the pipeline blocks merges without documented approval.
Organizations define thresholds for code coverage, security scans, and performance benchmarks, then implement automated checks to ensure these gates are passed before proceeding. This automation provides the consistency auditors require when evaluating control effectiveness.
5) Audit logs and traceability
Every pipeline action—code commits, build triggers, test executions, deployment approvals, access grants—generates log entries. Comprehensive logging creates an immutable audit trail demonstrating who changed what, when, and whether required approvals were obtained.
SOC 2 CC7.2 (System Monitoring) requires organizations to implement monitoring activities to detect anomalies. ISO 27001 A.12.4 (Logging and Monitoring) requires recording user activities, exceptions, and security events. CI pipeline logs directly satisfy these requirements.
Effective logging requires centralized collection (sending logs to SIEM or log management platforms), retention policies aligned with compliance requirements (typically 12-24 months for SOC 2), and protection against tampering through write-once storage or cryptographic signatures.
How Continuous Integration Helps Meet Data Protection Standards
1) Continuous compliance vs point-in-time testing
Traditional compliance approaches treat security as a periodic activity: conduct a penetration test quarterly, review access controls annually, perform vulnerability scans before major releases. This creates gaps—vulnerabilities introduced between testing cycles go undetected; configuration changes that violate policies aren't identified until the next audit.
CI pipelines enable continuous compliance validation. Every code commit undergoes security scanning. Every configuration change triggers policy checks. Every deployment verifies compliance requirements. Rather than proving security posture on a specific date, organizations demonstrate ongoing control effectiveness through pipeline audit logs showing thousands of automated security checks executed throughout the observation period.
This continuous validation directly supports SOC 2 Type II requirements. Organizations continuously monitor compliance with regulations through automated workflows, generating the sustained evidence auditors require to assess control operating effectiveness over time.
2) Data handling controls built into CI pipelines
Data protection regulations impose specific technical requirements: GDPR Article 32 requires encryption of personal data, data masking in non-production environments, and access controls that enforce data minimization. HIPAA's Security Rule requires encryption of ePHI in transit and at rest, access controls that implement minimum necessary standards, and audit trails of all ePHI access.
CI pipelines enforce these requirements programmatically:
- Automated checks verify that database connection strings use TLS encryption
- Policy gates block deployments that store sensitive data in logs
- Test data generation tools create synthetic datasets, eliminating real customer data from development environments
- Access controls restrict production data access to authorized personnel with business justification
- Deployment scripts implement data retention policies, ensuring test environments purge data on defined schedules
These controls, implemented as code and enforced by the pipeline, provide auditors with objective evidence of systematic data protection—not policy documents describing aspirational practices.
3) Benefits for risk management and audit readiness
CI pipelines with embedded security controls provide four distinct audit advantages:
Objective evidence: Pipeline logs show exactly which security checks ran, what they tested, and whether they passed or failed. This eliminates reliance on subjective assessments or manual checklists.
Continuous operation: Logs spanning the entire observation period demonstrate that controls operated consistently, not just during audit preparation.
Traceability: Every code changes links to commits, which link to build logs, which link to test results, which link to deployment records. Auditors can trace a production deployment back to its origin commit and verify that all required security validations occurred.
Exception reporting: When security checks fail—a developer attempts to commit credentials, a build contains critical vulnerabilities, a deployment lacks required approvals—the pipeline generates evidence of the control failure and the remediation actions taken.
More than 70% of enterprises are expected to adopt DevSecOps practices by 2026, driven by recognition that documented security controls in CI/CD pipelines directly support compliance attestation requirements while improving security outcomes.
Best Practices for Enterprise-Grade CI
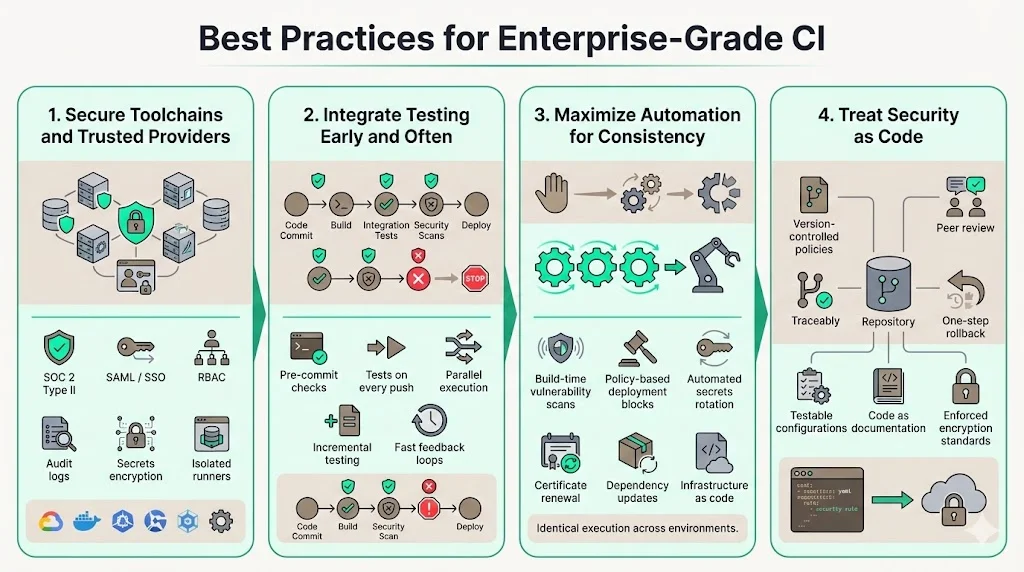
1) Use secure toolchains and trusted providers
CI/CD platforms themselves become part of your security infrastructure and must meet enterprise security standards. Evaluate platforms based on:
- SOC 2 Type II attestation of the CI/CD service provider
- Support for SAML/SSO integration with enterprise identity providers
- Granular RBAC capabilities
- Audit logging of administrative actions
- Encryption of secrets and sensitive pipeline data
- Network isolation options for self-hosted runners
Popular enterprise-grade platforms include GitHub Actions (with GitHub Enterprise), GitLab CI/CD (with GitLab Ultimate), Jenkins (with security plugins and hardened configurations), and AWS CodePipeline integrated with AWS security services.
Platform selection should consider not just feature sets but the security attestations and certifications the vendor maintains—customers will ask the same questions about your software.
2) Integrate testing early and often
Security testing effectiveness correlates with frequency and immediacy. Tests that run on every commit provide faster feedback than tests that run nightly. Tests that fail immediately block problematic code before it accumulates dependencies.
Effective test integration requires:
- Pre-commit hooks that run lightweight checks (secret scanning, code formatting) before code reaches the repository
- Automated build triggers that initiate full test suites on every push or pull request
- Parallel execution that runs multiple test suites simultaneously, reducing total test duration
- Incremental testing that focuses on changed code and its dependencies rather than re-testing the entire codebase
Testing and deployment problems are solved much faster when CI/CD tools provide rapid feedback, boosting overall efficiency. This speed advantage compounds—catching ten vulnerabilities during development costs a fraction of remediating one vulnerability discovered during a customer security review.
3) Maximize automation for consistency
Manual security processes fail predictably: developers forget steps under deadline pressure, security checklists receive cursory reviews, configuration drift occurs across environments. Automation eliminates these failure modes by implementing controls that execute identically every time.
Automation candidates include:
- Vulnerability scanning triggered on every build
- Compliance policy checks that block non-conformant deployments
- Secrets rotation on defined schedules
- Certificate renewal and monitoring
- Dependency updates and testing
- Infrastructure provisioning through infrastructure-as-code templates
Automated builds, unit tests, and security scans using CI tools standardize security checks and ensure consistent validation. This consistency directly satisfies auditor requirements for documented, repeatable controls.
4) Treat security as code
Configuration-as-code principles—managing infrastructure, policies, and security controls through version-controlled code rather than manual configurations—provide several advantages:
Version control: Every policy change, configuration update, and security rule modification exists as a commit with author, timestamp, and change description.
Peer review: Changes undergo code review processes, implementing separation of duties and catching configuration errors before deployment.
Rollback capability: If a policy change causes issues, reverting to the previous version requires a single Git command.
Testing: Security policies and infrastructure configurations can be tested in non-production environments before being applied to production systems.
Documentation: The code itself serves as documentation of exactly how security controls are implemented, eliminating discrepancies between documentation and actual practice.
Treating security as code transforms abstract security requirements into concrete, testable, auditable implementations. Rather than a policy document stating "encryption shall be used for data in transit," the infrastructure code explicitly configures TLS 1.3 with specific cipher suites, and the pipeline verifies this configuration on every deployment.
Real-World Example
A financial technology startup building payment processing infrastructure implemented SOC 2 Type II readiness while maintaining rapid release cycles. Their CI pipeline integrated security controls at multiple stages:
During code review, automated SAST scanning identified a potential SQL injection vulnerability in a payment lookup API. The pipeline blocked the pull request merge, notifying the developer with specific code locations and remediation guidance. The developer implemented parameterized queries, resubmitted the code, and received approval within 90 minutes of the initial commit.
Before staging deployment, dependency scanning flagged a vulnerable version of a JSON parsing library with a known remote code execution flaw. The pipeline automatically opened a pull request with the updated library version, triggered the test suite, and—after tests passed—notified the team for manual review and merge.
At production deployment, policy checks verified that database connection strings used encrypted connections, application containers originated from signed images in the company's private registry, and the deployment had received approval from both the engineering lead and security team.
Throughout the six-month SOC 2 observation period, pipeline audit logs documented 3,847 automated security scans, 127 vulnerability detections (with remediation evidence linked to specific commits), and 100% enforcement of code review requirements before production deployment. These logs provided auditors with objective evidence of control operating effectiveness, contributing to a clean SOC 2 Type II opinion without qualification.
The implementation satisfied both security and business objectives: vulnerabilities were caught before reaching production, audit preparation required minimal manual evidence gathering, and development velocity increased 23% due to faster feedback cycles and reduced security remediation delays.
Conclusion
CI/CD security forms the backbone of modern software development, creating an environment wherein organizations can rapidly create, test, and deploy secure applications. For enterprises selling software where data protection standards determine vendor selection, documented security controls in CI pipelines represent both technical implementation and compliance evidence.
Continuous integration enables security validation at every stage of the development lifecycle—from initial code commit through production deployment. By implementing access controls, secrets management, automated scanning, policy gates, and comprehensive audit logging, organizations transform CI pipelines from build automation into systematic security infrastructure.
The audit advantages are substantial: objective evidence of control effectiveness, continuous validation rather than point-in-time assessments, complete traceability from code changes through deployment, and documented exception handling. These capabilities directly support SOC 2 attestations, ISO 27001 certifications, and regulatory compliance obligations that enterprise buyers require.
Organizations building enterprise-grade software should implement CI security controls not as compliance theater but as operational discipline—systematic practices that catch vulnerabilities before production, document security validation continuously, and provide auditors with evidence that security controls operate effectively over time. This approach satisfies both security requirements and business objectives: reduced risk exposure, faster audit cycles, and documented proof of secure development practices that enterprise buyers demand.
Frequently Asked Questions
1) What is meant by continuous integration?
Continuous Integration is a collaborative working model where developers merge changes into a single code base repeatedly and at short intervals, with each integration triggering an automated build that allows teams to identify and rectify errors much earlier than traditional methods. The practice establishes a central repository where code changes undergo immediate compilation, testing, and validation rather than accumulating changes for periodic integration.
2) What is the difference between CI and CD?
Continuous Integration focuses on integrating code changes frequently with automated builds and tests, while Continuous Delivery extends CI by automating deployments to staging or production environments. CI verifies that code compiles and passes tests; CD verifies that code can be deployed reliably. Both contribute to security and compliance objectives but address different phases of the software delivery lifecycle.
3) What is CI CD in simple terms?
CI/CD represents automated processes for building, testing, and deploying software. Continuous Integration ensures that every code change merges successfully with the existing codebase and passes automated tests. Continuous Delivery automates the release process, enabling teams to deploy validated code to production with minimal manual intervention. Together, these practices reduce time between development and deployment while maintaining quality and security standards.
4) What is an example of continuous integration?
A development team uses GitHub and GitHub Actions to implement CI. When a developer opens a pull request, the CI system automatically retrieves the code changes, compiles the application, runs 850 unit tests, executes SAST scanning, checks dependencies for known vulnerabilities, and verifies code coverage meets the 85% threshold. If all checks pass, the pull request receives automated approval for human review. If any check fails, the developer receives immediate notification with specific failure details and remediation guidance. This automated validation occurs within 4-6 minutes of opening the pull request.
5) How does Continuous Integration (CI) help security?
CI helps security by integrating vulnerability scanning tools directly into pipelines to catch security issues like outdated libraries, misconfigurations, or malicious code before they reach staging or production, with continuous scanning ensuring newly discovered vulnerabilities aren't missed and fixing flaws during the build phase being far easier and cheaper than addressing issues after deployment. CI enables shift-left security practices, automated policy enforcement, secrets detection, and comprehensive audit trails that satisfy compliance requirements while reducing vulnerability exposure.
6) Does CI help meet data protection standards?
CI pipelines directly support data protection compliance by implementing enforceable controls—automated encryption verification, data masking in test environments, access restrictions based on least privilege, and audit logging of all pipeline activities. These controls provide auditors with objective evidence of systematic security practices operating continuously throughout the observation period. Rather than documenting security policies, CI pipelines demonstrate control effectiveness through thousands of automated security checks executed on every code change, generating the sustained evidence required for SOC 2 Type II attestations, ISO 27001 certifications, and regulatory compliance obligations.
7) What security checks should be part of a CI pipeline?
Enterprise-grade CI pipelines should implement: access controls with multi-factor authentication and role-based permissions; secrets management preventing credential exposure in code repositories; static application security testing identifying code-level vulnerabilities; dependency scanning detecting vulnerable third-party libraries; dynamic application security testing validating runtime security; container image scanning for containerized applications; policy gates blocking builds that fail security thresholds; code review requirements enforcing separation of duties; infrastructure-as-code validation for deployment configurations; and comprehensive audit logging documenting all pipeline activities. These checks, executed automatically on every code change, transform security requirements into enforceable controls while generating compliance evidence auditors require.



.svg)
.svg)
.svg)