Most organizations implement IT governance reactively—after an audit failure, a security breach, or a contract negotiation where enterprise clients demand evidence of mature controls. This approach creates a fundamental gap between what leadership believes exists and what auditors actually find when they examine your IT operations, risk management processes, and control effectiveness.
What is COBIT: Definition and Origins
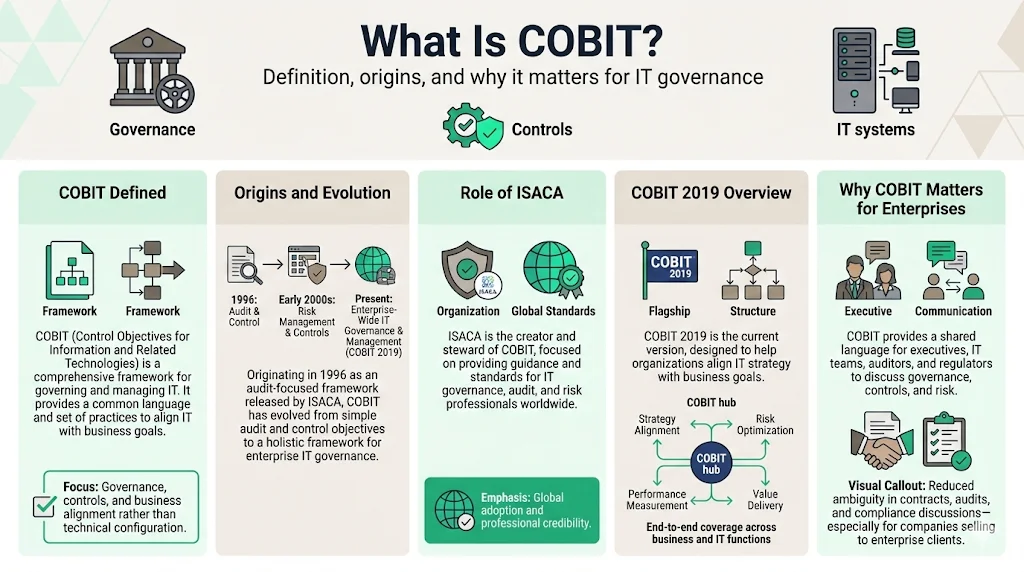
COBIT stands for "Control Objectives for Information and Related Technologies." It's a comprehensive framework that provides organisations with practices, tools, and guidelines to govern and manage IT effectively.
Since 1996, COBIT has evolved to offer practitioners the latest knowledge, tools, and best practices for maximizing the value of IT for businesses all over the world. ISACA (Information Systems Audit and Control Association) first released COBIT as an audit-oriented framework focused on control objectives for information systems. Over successive iterations, COBIT expanded from a narrow audit checklist into a comprehensive IT governance and management framework addressing strategic alignment, value delivery, risk management, resource optimization, and performance measurement.
COBIT 2019, developed by ISACA (an international professional association focused on IT governance), is the latest version of the globally recognised IT governance framework designed to help organisations align IT strategies with business goals. COBIT allows practitioners to govern and manage IT holistically, incorporating all end-to-end business and IT functional areas of responsibility. For organizations selling to enterprise clients, COBIT serves as a common language that business executives, IT teams, auditors, and regulators use to discuss IT governance, control objectives, and risk management—reducing ambiguity in contractual requirements and compliance expectations.
Structure of COBIT: Domains, Processes, and Objectives
COBIT 2019 contains a detailed description of the COBIT Core Model and its 40 governance/management objectives. The framework is structured into five key domains: EDM, APO, BAI, DSS, and MEA.
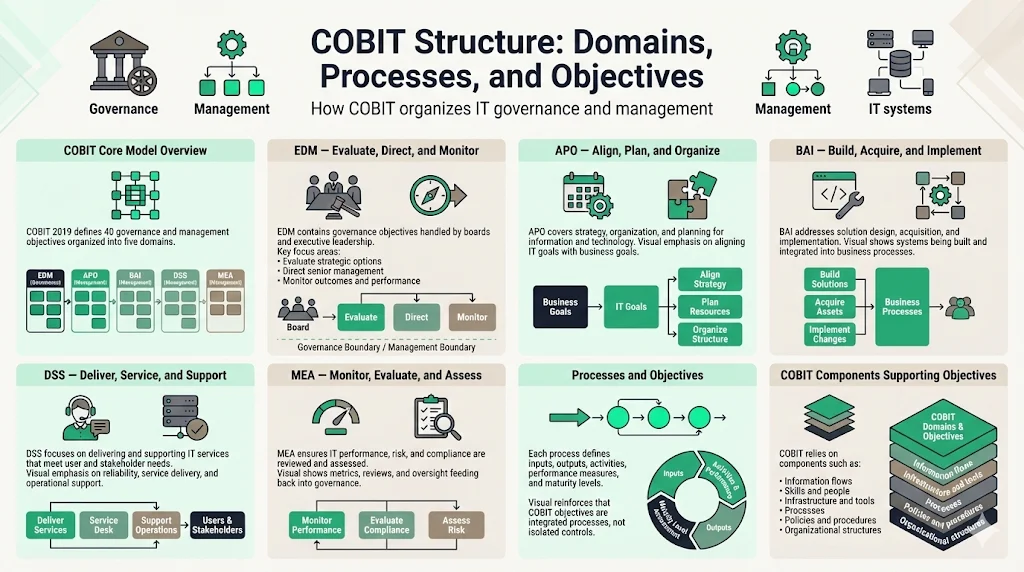
The governance objectives are contained in the Evaluate, Direct and Monitor (EDM) domain. In this domain, the governing body evaluates strategic options, directs senior management on the chosen strategic options and monitors the achievement of the strategy. This domain distinguishes governance activities—performed by boards and executive leadership—from management execution.
The Align, Plan and Organize (APO) domain addresses the overall organization, strategy and supporting activities for information and technology (I&T). The Build, Acquire and Implement (BAI) domain addresses the definition, acquisition and implementation of I&T solutions and their integration in business processes. The aim of the Deliver, Service, and Support (DSS) domain is to deliver and support IT services that meet the needs of customers and stakeholders. The aim of the Monitor, Evaluate, and Assess (MEA) domain is to ensure that IT is managed effectively and efficiently, delivering value to the business.
Each process within these domains defines inputs, outputs, key activities, performance measures, and maturity levels. Control objectives under each process establish requirements ensuring IT supports business needs, manages risk, ensures compliance, and delivers measurable value. COBIT refers to these as governance and management objectives rather than isolated controls—emphasizing that effective IT governance requires integrated processes, not disconnected checklists.
Beyond processes, COBIT uses "components" (formerly called "enablers") to support governance and management. They include 'Information Flows', 'Skills', 'Infrastructure', 'Processes', 'Policies and Procedures', and 'Organizational Structures'. These components acknowledge that implementing control objectives requires organizational structure, defined roles, information architecture, skilled personnel, policies, and technical infrastructure—not just documented procedures.
Why Companies, Especially Those Selling to Enterprises, Should Care
Enterprise clients expect vendors to demonstrate mature IT governance because their own risk, compliance, and audit functions require it. When you sell software, managed services, or technology solutions to large organizations, procurement teams evaluate your governance maturity as part of vendor risk assessments. COBIT provides the structure to meet these expectations systematically rather than reactively assembling evidence during each sales cycle.
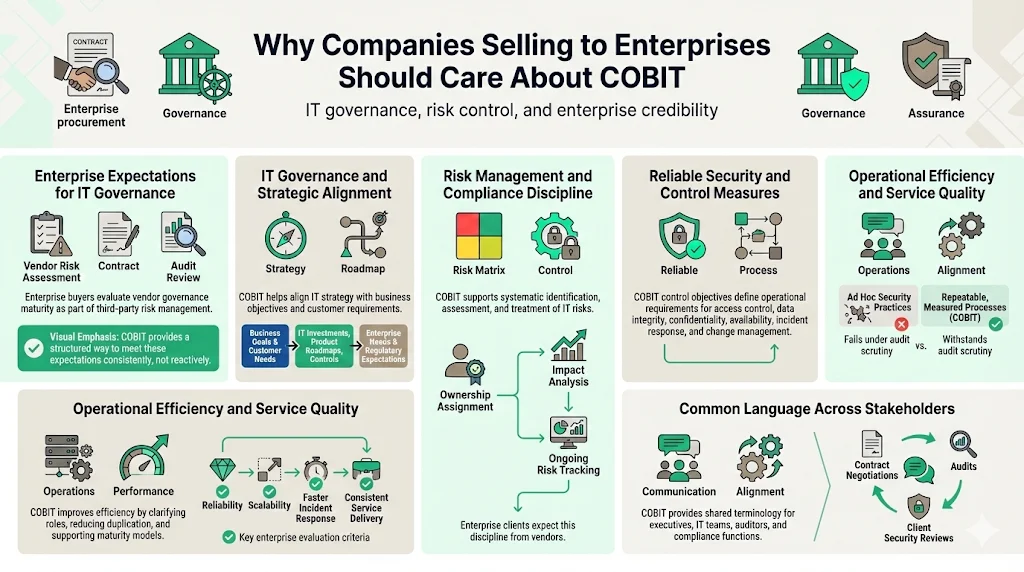
IT governance and strategic alignment: COBIT helps ensure that IT strategies support broader business objectives. For vendors, this means demonstrating that your technology investments, product roadmaps, and operational controls align with customer needs and regulatory requirements—not just internal convenience.
Risk management and compliance: COBIT enables organisations to identify, assess, and mitigate IT-related risks. Using COBIT's risk-oriented processes helps you systematically identify vulnerabilities, assess their impact on confidentiality and availability, assign remediation ownership, and track risk treatment over time. This structured approach satisfies enterprise clients' vendor risk management requirements and supports compliance with contractual obligations, regulatory mandates, and industry-specific standards.
Reliable security and control measures: Control objectives under COBIT processes define security controls, access management, data integrity requirements, confidentiality measures, and system availability standards. These aren't aspirational goals—they're operational requirements with defined inputs, outputs, responsible parties, and performance metrics. Organizations implementing COBIT control objectives establish repeatable processes for access provisioning, vulnerability management, incident response, and change control rather than relying on ad hoc security measures that appear adequate until scrutinized by auditors.
Operational efficiency and quality management: COBIT helps optimize the use of resources, including infrastructure, personnel, and finances. Structured IT processes, capability maturity models, and clearly defined responsibilities streamline operations, improve service delivery quality, and eliminate redundant or conflicting activities. For companies selling to enterprises, operational discipline directly impacts service reliability, incident response times, and the ability to scale without degrading quality—factors enterprise clients assess during vendor evaluations.
Common language across stakeholders: COBIT serves as shared terminology for business executives, IT operations, auditors, compliance teams, and external assessors. This reduces translation overhead during client negotiations, audit preparations, and cross-functional initiatives. When enterprise clients reference COBIT processes or control objectives in contracts or vendor assessments, organizations familiar with the framework understand exactly what's expected without lengthy clarifications.
How COBIT Supports Your Core Concerns
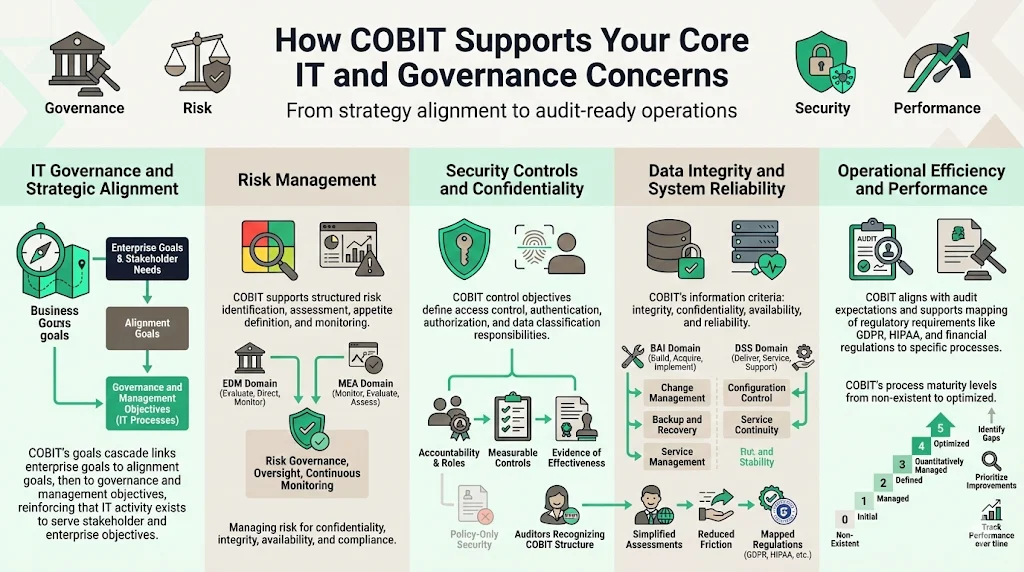
IT governance: COBIT fundamentally addresses IT governance by linking business goals to IT processes through a structured goals cascade. Each governance/management objective and its purpose are defined and then matched up with the related process, Alignment Goals and Enterprise Goals. This cascading structure ensures that every IT activity traces back to stakeholder needs and enterprise objectives rather than existing in isolation.
Risk management: COBIT includes guidance on identifying, assessing, and managing IT and information risks through risk-specific practices, performance metrics, and integration with enterprise risk management frameworks. Processes within the EDM and MEA domains specifically address risk assessment, risk appetite definition, and ongoing risk monitoring—providing repeatable methods for managing threats to confidentiality, integrity, availability, and compliance.
Security controls and confidentiality measures: Control objectives under COBIT processes help define proper access controls, authentication mechanisms, authorization frameworks, data classification schemes, and confidentiality protections. These objectives specify who is accountable for implementing controls, what evidence demonstrates effectiveness, and how to measure control performance—moving beyond generic security policies to operational implementation.
Data integrity and system reliability: COBIT's information criteria include integrity, confidentiality, availability, and reliability—ensuring information is accurate, complete, available when needed, and trustworthy for decision-making. Processes within the BAI and DSS domains address system development controls, change management, configuration management, backup and recovery, and service continuity—all directly impacting data integrity and system reliability.
Auditing standards and compliance requirements: As a widely accepted IT governance framework, COBIT helps meet external compliance mandates and internal audit requirements. Auditors recognize COBIT's structure, making audit preparations more efficient when your governance approach aligns with COBIT domains and control objectives. Organizations using COBIT can map regulatory requirements—GDPR data protection obligations, HIPAA technical safeguards, financial services regulations—to specific COBIT processes, demonstrating comprehensive compliance coverage.
Operational efficiency and performance: Through well-defined processes, capability maturity models, and performance metrics, COBIT promotes efficient resource utilization and improved service delivery. COBIT defines five maturity levels for each process, ranging from "non-existent" to "optimized." This maturity assessment helps organizations identify inefficiencies, prioritize improvements, and track progress toward operational excellence rather than pursuing undefined "best practices."
Practical Steps for Implementation
Most organizations implementing COBIT fail because they treat it as a documentation project rather than an operational discipline. Effective implementation requires systematic assessment, tailored control selection, clear accountability, and ongoing measurement.
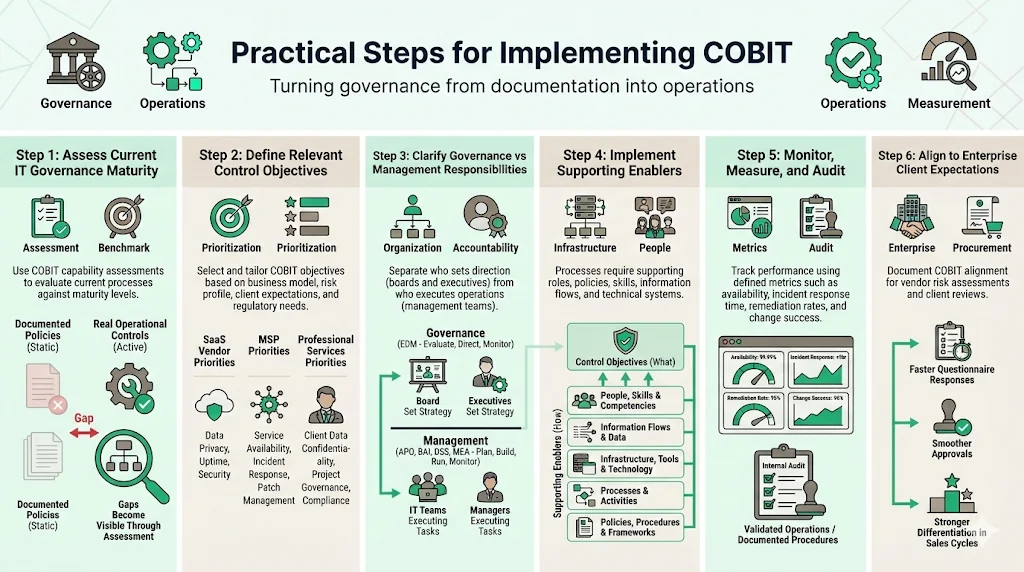
Assess current IT governance maturity: Use COBIT's capability assessment to evaluate existing processes against defined maturity levels. This assessment identifies gaps between current state and target maturity for each relevant process. Organizations typically discover that documented policies exist without corresponding operational controls, or that controls operate inconsistently across teams—gaps that become apparent during audits or security incidents.
Define control objectives relevant to your business context: Not all 40 COBIT objectives apply equally to every organization. Companies selling SaaS products to enterprise clients prioritize different control objectives than managed service providers or consulting firms. Select and tailor objectives based on your risk profile, client expectations, regulatory requirements, and operational model. For example, organizations handling sensitive customer data emphasize access control, data protection, and availability objectives, while firms providing professional services focus more heavily on project management, resource allocation, and knowledge management processes.
Map responsibilities distinguishing governance from management: Boards and executive management are typically accountable for governance processes, while management processes are the domain of senior and middle management. The governance and management objectives in COBIT are grouped into five domains. This distinction prevents confusion about who sets direction (governance) versus who executes operations (management). In practice, many organizations blur this line, resulting in executives performing operational tasks while operational teams lack strategic direction.
Implement supporting enablers: Control objectives fail without supporting organizational structures, policies, skilled personnel, information flows, and technical infrastructure. Implementing COBIT requires defining roles (who is accountable for each objective), documenting procedures (how objectives are achieved), training staff (building necessary skills), establishing information architecture (what data supports decisions), and deploying infrastructure (what systems enable controls). Organizations that focus exclusively on process documentation while neglecting these enablers create governance frameworks that exist only on paper.
Monitor, measure, and audit: Use performance metrics and maturity assessments to track compliance, reliability, security, and operational efficiency over time. COBIT processes specify relevant metrics—service availability percentages, incident response times, vulnerability remediation rates, change success rates—that provide objective evidence of control effectiveness. Regular internal audits verify that documented processes match operational reality, identifying control drift before external auditors or clients discover it.
Align to client expectations: For companies selling to enterprise clients, adherence to COBIT serves as a differentiator during vendor assessments. Document how your IT governance approach aligns with COBIT domains and control objectives, making it easier for client procurement and risk teams to evaluate your maturity. This alignment reduces questionnaire response time, accelerates vendor approvals, and demonstrates operational sophistication that smaller competitors often lack.
Common Pitfalls and What to Watch Out For
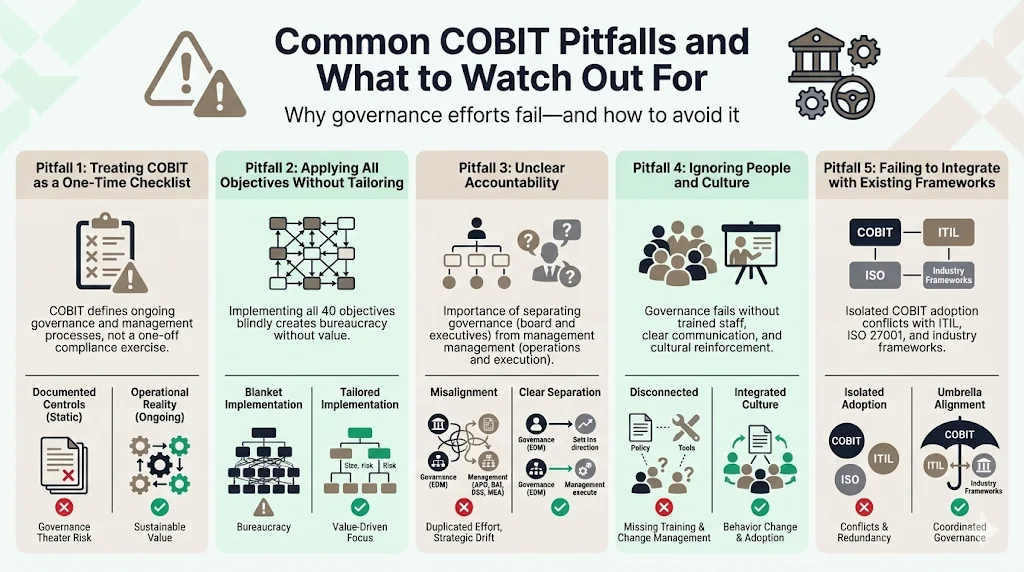
Treating COBIT as a one-time checklist: COBIT describes ongoing governance and management processes, not a certification program with a defined end date. Organizations that implement COBIT to satisfy a specific audit or client requirement, then neglect ongoing process execution, create governance theater—documented controls that don't reflect operational reality. Effective COBIT implementation requires continuous process execution, periodic reassessment, and regular updates as business context changes.
Applying all control objectives blindly: Attempting to implement all 40 governance and management objectives without considering organizational size, risk profile, or business context wastes resources and creates bureaucratic overhead without corresponding value. Smaller organizations require lighter-weight governance than large enterprises. Technology vendors face different risks than healthcare providers. Tailor COBIT implementation to address actual governance needs rather than pursuing comprehensive coverage for its own sake.
Failing to define clear accountability: Ambiguous accountability for governance versus management activities results in duplicated effort, gaps in execution, and confusion during audits. COBIT explicitly distinguishes governance activities (performed by boards and executives) from management activities (performed by operational leadership and staff). Organizations that fail to establish this distinction experience strategic drift (management teams making governance decisions) or operational inefficiency (executives performing management tasks).
Ignoring the human and organizational side: Technical controls, documented policies, and process definitions fail without trained personnel, appropriate organizational culture, and behavioral reinforcement. Organizations implementing COBIT often focus on documentation and technology while neglecting training, change management, and cultural alignment. This creates situations where controls exist but aren't consistently followed, policies are documented but not understood, and processes are defined but not integrated into daily operations.
Overlooking integration with existing frameworks: Most enterprises already use multiple frameworks—ITIL for service management, ISO 27001 for information security, industry-specific compliance frameworks. Implementing COBIT in isolation from these existing frameworks creates conflicting requirements, duplicated effort, and confusion about which framework governs specific activities. Effective COBIT implementation maps to and integrates with existing frameworks rather than replacing them entirely.
How COBIT Fits with Other Frameworks and Standards
COBIT 2019 is specifically designed to play well with others. Guidance is provided to help you integrate the industry standards, guidelines, regulations and best practices unique to your enterprise into your governance solution using COBIT.
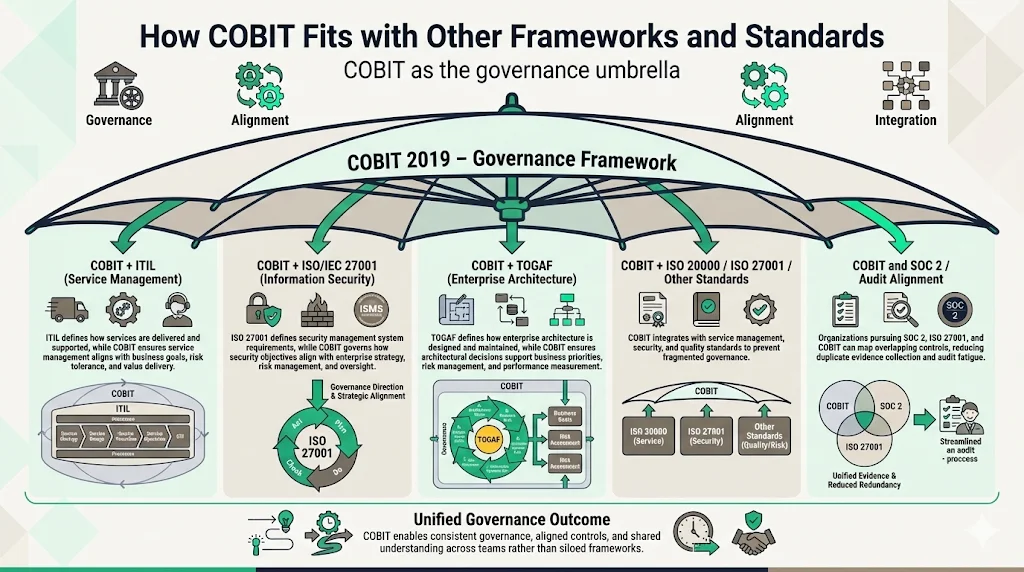
COBIT provides a high-level governance umbrella that works with ITIL (for service management processes), ISO 27001 (for information security management systems), and TOGAF (for enterprise architecture). Rather than choosing between frameworks, mature organizations use COBIT as the governance layer that coordinates and aligns framework-specific implementations. For example, ITIL defines service delivery processes while COBIT provides the governance objectives that ensure service management aligns with business goals, manages risk appropriately, and delivers measurable value.
COBIT 2019 can also integrate with a number of compatible best-practice frameworks and standards, including ITIL, ISO 20,000, and ISO 27,001. This integration capability allows organizations to unify various control, compliance, risk, and governance needs under a single framework—avoiding fragmented governance where different teams implement incompatible approaches. Organizations pursuing SOC 2 attestation, ISO 27001 certification, and COBIT implementation simultaneously can map control requirements across all three, identifying overlaps and eliminating redundant evidence collection.
Real-World Use Cases
SaaS vendor demonstrating governance maturity: A software company selling to enterprise clients implements COBIT internally to structure its IT governance, security operations, and compliance programs. During vendor assessments, the company references specific COBIT processes when responding to security questionnaires, demonstrating mature governance rather than reactive compliance. This approach reduces sales cycle friction and differentiates the vendor from competitors who provide generic security assurances without underlying governance frameworks.
Managed services provider structuring client delivery: A managed security services provider uses COBIT processes to structure service delivery, access control, incident response, and compliance management for clients in regulated industries. The provider maps its service offerings to COBIT domains, demonstrating comprehensive coverage of governance and management objectives. Clients gain confidence that the provider follows structured, repeatable processes rather than ad hoc approaches that vary by individual engineer or client engagement.
Consulting firm conducting governance assessments: An IT advisory firm uses COBIT maturity assessments to audit client IT governance, identifying gaps between current state and target maturity for relevant processes. The assessment produces specific recommendations—strengthen access management processes, implement formal change control, establish service continuity planning—linked to COBIT control objectives. This structured approach provides clients with clear improvement roadmaps rather than generic recommendations disconnected from recognized frameworks.
Conclusion
COBIT remains relevant for enterprise-oriented companies because it directly addresses what large organizations evaluate during vendor assessments—alignment between IT strategy and business goals, systematic risk management, demonstrable security controls, operational quality, and governance discipline. These aren't compliance checkboxes; they're operational capabilities that determine whether your organization can reliably deliver services, respond to incidents, protect customer data, and scale without degrading quality.
Organizations treating COBIT as a documentation exercise create governance theater—policies and procedures that satisfy superficial reviews but fail under operational stress or detailed audits. Effective COBIT implementation establishes operational discipline where documented processes match daily execution, control objectives have clear ownership and accountability, performance metrics provide objective evidence of effectiveness, and governance activities systematically align IT investments with business outcomes.
For B2B companies selling to enterprises, demonstrating COBIT-aligned governance builds trust that generic security assurances cannot. Enterprise clients evaluate vendors based on governance maturity because immature vendors create operational, security, and compliance risks that transfer to clients. Systematic IT governance using COBIT provides the operational foundation and evidence structure that enterprise procurement, risk management, and audit functions require.
Next steps for organizations pursuing COBIT implementation: assess internal governance maturity using COBIT's capability model to establish current state, identify target maturity levels based on business context and stakeholder expectations, tailor relevant control objectives to your operational model and risk profile, implement processes with clear accountability and supporting enablers, establish performance metrics providing objective evidence of effectiveness, and maintain governance discipline over time rather than treating implementation as a project with a defined end date.
FAQs
1) What are control objectives for information?
Control objectives for information define specific requirements and goals for managing IT systems, data, and operations to ensure confidentiality, integrity, availability, compliance, and reliability. In COBIT, these objectives specify what must be achieved within each governance and management process—including who is accountable, what activities are required, what evidence demonstrates effectiveness, and how performance is measured. Control objectives aren't abstract goals; they're operational requirements with defined inputs, outputs, and measurable outcomes that ensure IT supports business needs while managing risk appropriately.
2) What does COBIT stand for Control Objectives for Information and Related Technology?
COBIT stands for "Control Objectives for Information and Related Technologies." The acronym originated when ISACA first released COBIT in 1996 as an audit-oriented framework focused on control objectives for information systems. While the framework has evolved significantly beyond its initial focus—expanding to cover comprehensive IT governance, management, risk, compliance, and value delivery—the original acronym remains. Modern COBIT versions emphasize governance and management objectives rather than narrow control checklists, but the name preserves the framework's historical foundation in control objectives for IT.
3) What is an example of a control objective?
A COBIT control objective example: "Ensure access to systems and data is appropriately authorized, authenticated, and monitored." This objective requires implementing processes for access provisioning (verifying authorization before granting access), authentication mechanisms (confirming user identity), authorization controls (limiting access based on roles and responsibilities), access reviews (periodically verifying access remains appropriate), and audit logging (monitoring access activities for anomalies). The control objective specifies accountable parties (typically IT security or access management teams), required activities (provisioning, review, monitoring), performance metrics (access request fulfillment time, review completion rates, unauthorized access incidents), and maturity levels (from ad hoc manual processes to optimized automated controls). Another example: "Ensure system availability meets business requirements through redundancy, backup, recovery, and continuity planning"—requiring documented availability targets, redundant infrastructure, tested backup procedures, recovery time objectives, and business continuity plans with defined testing frequencies.
4) What are the three control objectives?
While some older IT control frameworks referenced three high-level categories of controls—preventive, detective, and corrective—COBIT 2019 doesn't organize its 40 governance and management objectives into three categories. Instead, COBIT addresses multiple information criteria: effectiveness (achieving intended objectives), efficiency (optimal resource use), confidentiality (protecting sensitive information), integrity (ensuring accuracy and completeness), availability (providing access when needed), compliance (adhering to laws and regulations), and reliability (providing trustworthy information for decisions). Organizations sometimes reference the "CIA triad"—confidentiality, integrity, availability—as core security objectives, but comprehensive IT governance using COBIT addresses all information criteria, not just three. The framework's 40 objectives span five domains covering governance, strategic alignment, solution delivery, service operations, and performance monitoring—far more comprehensive than any three-category simplification.



.svg)
.svg)
.svg)