In early 2024, Russian hacktivist attacks on rural water organizations highlighted a fundamental truth: disruption to critical systems creates cascading failures across society. Roughly 70% of all cyberattacks in 2024 involved critical infrastructure—targeting power grids, telecommunications networks, financial systems, and healthcare facilities that millions depend on daily. When these systems fail, the consequences extend far beyond operational downtime.
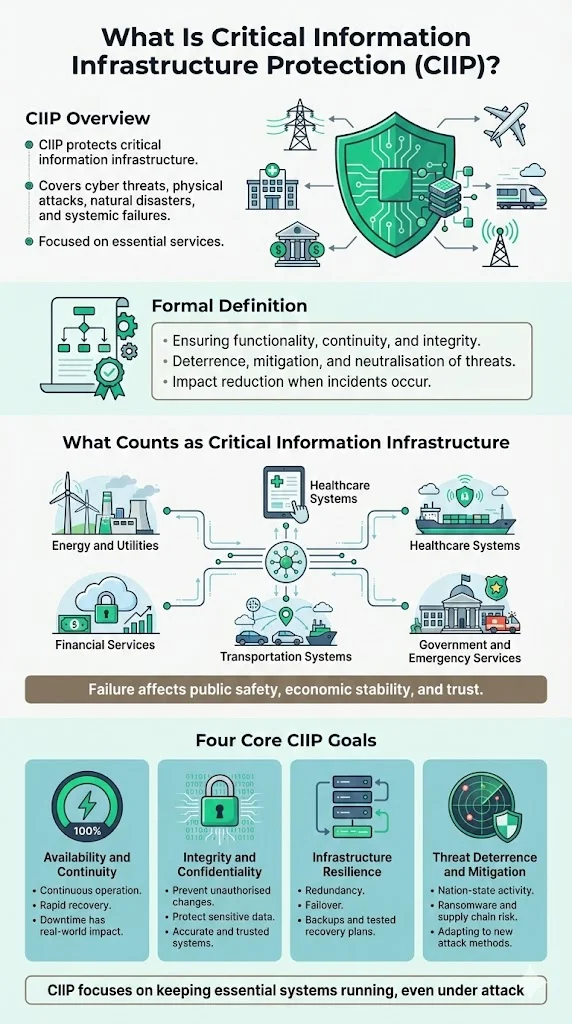
Critical Information Infrastructure Protection (CIIP) represents the comprehensive discipline of safeguarding information and communication systems whose compromise would seriously affect national security, economic stability, public health, or essential services. For enterprises selling to large clients in finance, telecommunications, energy, healthcare, or government sectors, understanding CIIP is not optional—it defines the baseline security and resilience expectations that determine vendor qualification.
This definition explains what CIIP is, why organizations and governments treat it as a national security priority, how protection frameworks operate in practice, and what enterprises must know when serving clients in critical sectors.
What is "Critical Information Infrastructure" (CII)?
Critical Information Infrastructure (CII) encompasses information and communication systems whose failure, compromise, or destruction would seriously affect national security, economic stability, public health and safety, or the continuity of essential government services. These systems form the digital backbone of modern society—the networks, databases, control systems, and applications that enable vital functions across interconnected sectors.
CII typically spans 16 distinct sectors: energy (including electricity generation and distribution), telecommunications, financial services and banking, transportation (air, rail, maritime, road), healthcare and public health, water and wastewater systems, emergency services, government operations, food and agriculture, chemical manufacturing, commercial facilities, information technology, communications, critical manufacturing, dams, and defense industrial base.
These systems qualify as "critical" because of three defining characteristics: interconnectedness across sectors, dependency of essential services on their continuous operation, and potential for cascading failures when compromised. A telecommunications outage doesn't merely disrupt phone calls—it can disable emergency services, halt financial transactions, paralyze transportation coordination, and prevent hospitals from accessing patient records. Critical infrastructure attacks are particularly egregious because they have cascading effects. When a malicious actor compromises a power grid, water supply, or communication network, the impact can ripple across multiple sectors.
What is "Critical Information Infrastructure Protection (CIIP)"?
Critical Information Infrastructure Protection (CIIP) refers to the comprehensive set of measures, strategies, and operational practices aimed at safeguarding critical information infrastructures from cyber threats, physical attacks, natural disasters, and other hazards that could disrupt essential services.
More formally: CIIP encompasses all activities aimed at ensuring the functionality, continuity, and integrity of critical information infrastructure in order to deter, mitigate, and neutralize threats, risks, or vulnerabilities—and to minimize the impact of incidents when they occur.
CIIP operates with four primary goals:
- Maintain availability and continuity of essential services. Critical systems must remain operational during normal conditions and recover rapidly from disruptions. Downtime measured in hours can translate to millions in economic losses and risks to public safety.
- Protect integrity and confidentiality of data and systems. Unauthorized modifications to control systems, financial records, or health data can have consequences as severe as complete system outages. CIIP ensures that data remains accurate, complete, and accessible only to authorized parties.
- Build resilience across infrastructure. Resilience means systems can survive disruptions or recover quickly with minimal impact. This requires redundancy, failover mechanisms, backup systems, and documented recovery procedures tested under realistic scenarios.
- Deter, mitigate, or neutralize risks from evolving threats. Cyber threats to critical infrastructure have grown in both frequency and impact, from nation-state actors conducting espionage to ransomware groups targeting healthcare providers. CIIP adapts defenses to address emerging attack vectors, from zero-day exploits to supply chain compromises.
Key Components and Processes of CIIP
Effective CIIP implementation requires systematic execution across seven interconnected disciplines. Organizations that treat CIIP as a checklist exercise rather than an operational framework inevitably discover gaps when incidents occur.
1) Identification & Classification: The foundation of CIIP is mapping all systems, networks, and assets that qualify as critical infrastructure within your operational environment. This includes not just primary systems but interdependencies—third-party services, cloud providers, telecommunications carriers, and shared infrastructure that could create single points of failure. Classification determines protection priorities based on potential impact of compromise or unavailability.
2) Risk Assessment & Risk Management: Systematic evaluation of threats (nation-state actors, ransomware groups, insider threats, natural disasters), vulnerabilities (unpatched systems, misconfigurations, weak access controls, supply chain exposures), and interdependencies across sectors. Risk management prioritizes remediation based on likelihood and potential impact, allocating resources to address the most consequential vulnerabilities first.
3) Protection Measures: Implementation of layered security controls spanning cyber defenses (network segmentation, zero-trust architecture, endpoint protection, encryption at rest and in transit), physical security (access controls, environmental monitoring, secure facilities), and operational controls (least-privilege access, multi-factor authentication, secure configuration baselines). Protection extends to supply chain security, vetting third-party components and services that could introduce vulnerabilities.
4) Resilience & Redundancy: Architecting systems to survive disruptions through redundancy (backup systems, geographically distributed infrastructure, alternate communication paths), disaster recovery capabilities (documented procedures, tested restoration processes, recovery time objectives), failover mechanisms (automatic switching to backup systems), and business continuity planning that accounts for extended outages.
5) Monitoring, Detection & Incident Response: Continuous monitoring of systems through logging, security information and event management (SIEM), anomaly detection, and threat intelligence integration. Detection capabilities identify indicators of compromise or abnormal behavior before attackers achieve their objectives. Incident response procedures enable rapid containment, investigation, eradication, and recovery—with predefined escalation paths and communication protocols.
6) Governance & Regulatory Compliance Framework: Documented policies, security standards, audit procedures, and regulatory compliance programs that establish accountability for CIIP across organizational levels. This includes coordination between government agencies and private sector entities, information sharing protocols, and adherence to sector-specific regulations that mandate protection standards for critical infrastructure.
7) Awareness, Training & Collaboration: Stakeholder engagement programs, security awareness training, tabletop exercises simulating incident scenarios, and cross-sector information sharing. Human factors remain a persistent vulnerability—social engineering, credential compromise, and configuration errors create entry points that technical controls alone cannot eliminate.
Why CIIP Matters — Real-World Importance
The business case for CIIP extends far beyond compliance obligations. Organizations that implement comprehensive CIIP frameworks demonstrate measurable advantages in risk management, operational resilience, and stakeholder confidence.
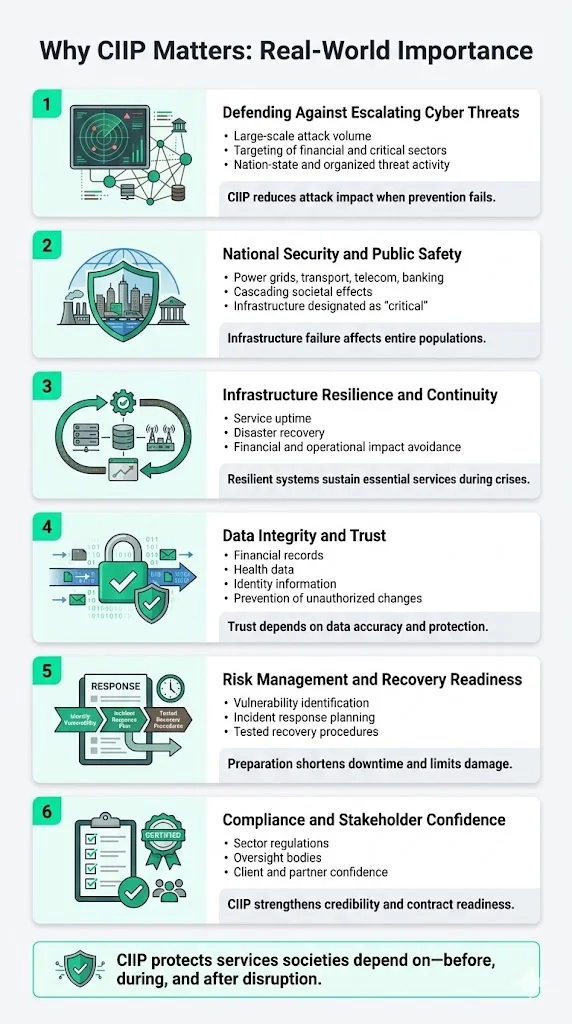
1) Defending against growing cyber threats: Between July and September 2024, BlackBerry detected 600,000 attacks against critical infrastructure, 45 percent of which targeted the financial sector. As infrastructures become more digitalized and interconnected, adversaries exploit these dependencies. The year 2024 witnessed an unprecedented surge in cyberattacks, as nation-state actors from China, Russia, and Iran executed highly sophisticated campaigns targeting critical infrastructure across the globe. CIIP frameworks implement the defenses necessary to deter these attacks and limit damage when prevention fails.
2) Safeguarding national security & public safety: Disruption to power grids, telecommunications, transportation networks, or banking systems can destabilize society and compromise national security. Governments designate certain infrastructure as critical specifically because its failure would have consequences extending beyond individual organizations to affect entire populations. The trend of rising cyberattacks on US critical national infrastructure in 2025 is a clear and present danger to national security and public safety.
3) Ensuring infrastructure resilience and business continuity: The average cost of a data breach in the U.S. reaching $10 million in 2025, more than double the global average. For critical infrastructure operators, costs extend beyond direct financial losses to include regulatory penalties, operational disruption, and reputational damage. Resilient infrastructure supported by CIIP principles enables continuity of services during disasters—whether cyber incidents, physical attacks, or natural events.
4) Protecting data integrity and trust: Critical services handle sensitive data across financial transactions, health records, government operations, and personal identity information. CIIP safeguards data integrity (preventing unauthorized modifications) and confidentiality (restricting access to authorized parties only), preserving the trust that citizens and customers place in essential services. Compromised data integrity in financial systems or healthcare records can have consequences as severe as complete system unavailability.
5) Risk management and disaster recovery readiness: Proactive identification of vulnerabilities, documented incident response procedures, tested recovery capabilities, and established communication protocols reduce both the likelihood of successful attacks and the time required to restore operations when incidents occur. Organizations with mature CIIP programs demonstrate measurably faster recovery times and lower total impact costs.
6) Regulatory compliance and stakeholder confidence: Governments increasingly mandate protection standards for critical infrastructure through sector-specific regulations and national cybersecurity frameworks. Compliance with CIIP requirements helps organizations meet regulatory obligations while building confidence with clients, partners, and oversight bodies. For vendors, demonstrating CIIP-aligned practices becomes a competitive differentiator when competing for contracts with critical sector clients.
CIIP in Practice: How It Plays Out for Enterprises and Governments
1) National-level implementation: Many nations establish dedicated agencies to coordinate CIIP across sectors. India's National Critical Information Infrastructure Protection Centre (NCIIPC), created under the amended Information Technology Act, identifies, notifies, and protects CII across sectors including power, finance, telecommunications, and transportation. These agencies establish protection standards, coordinate incident response, facilitate information sharing, and conduct assessments of critical systems. National-level coordination proves essential because critical infrastructure often spans multiple jurisdictions and involves both public and private sector operators.
2) Cross-sector dependencies and coordinated protection: Modern critical infrastructure exhibits complex interdependencies. Telecommunications infrastructure enables financial transactions. Financial systems support energy sector operations. Energy powers telecommunications networks. Healthcare facilities depend on all three. CIIP frameworks must account for these dependencies—securing one sector in isolation provides incomplete protection when failures in adjacent sectors create cascading disruptions. Coordinated protection requires information sharing protocols, joint exercises, and standardized incident notification procedures across sectors.
3) Private enterprise responsibility: For companies offering services to large organizations in finance, telecommunications, energy, healthcare, or government sectors, CIIP defines expected standards for solution design. This means architecting systems with security controls, redundancy, compliance capabilities, and incident response procedures integrated from initial design rather than added as afterthoughts. Vendors may not operate critical infrastructure directly but become part of the critical supply chain—subject to the same scrutiny and requirements as primary infrastructure operators.
4) Continuous risk assessment & evolving threat landscape: Technology evolution creates new attack surfaces. Cloud computing, Internet of Things devices, remote access infrastructure, and operational technology convergence with information technology all expand the potential entry points for adversaries. Experts are predicting that this trend will only intensify in 2025. As technology progresses, there's a corresponding progression in tactics used by malefactors. CIIP is not a one-time implementation project but an ongoing operational discipline requiring continuous monitoring, regular assessments, updated threat intelligence, and adaptive defenses.
Common Challenges & Considerations
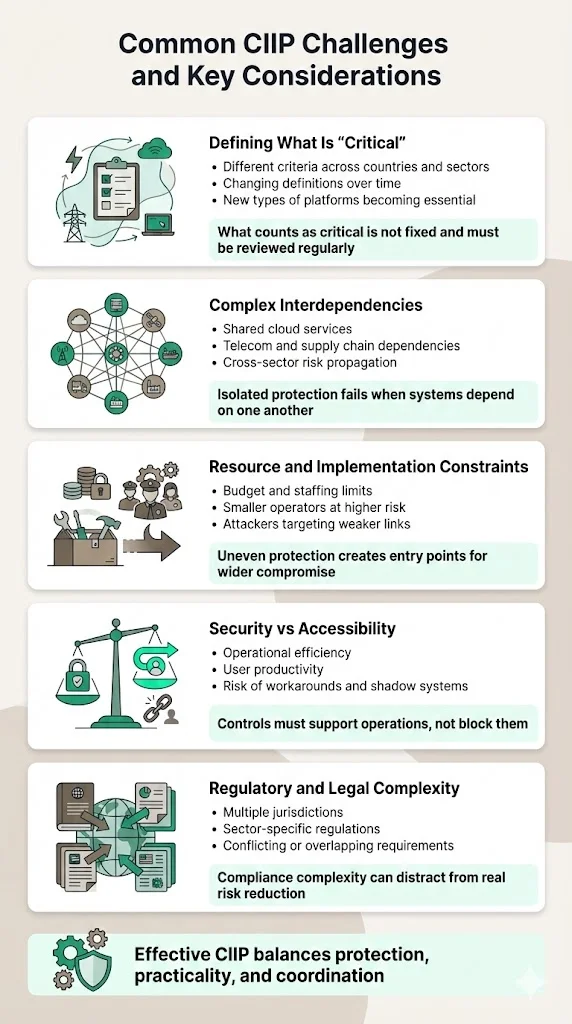
- Defining what counts as "critical": Different countries and sectors apply different criteria for designating infrastructure as critical. What qualifies as critical can change over time as technology evolves and dependencies shift. Social media platforms, for instance, were not considered critical infrastructure two decades ago but now play roles in emergency communications and public safety.
- Complex interdependencies: Systems across sectors are increasingly interconnected through shared telecommunications, cloud services, and supply chains. Securing individual systems without considering dependencies may not provide adequate protection. Comprehensive CIIP requires mapping and addressing interdependencies—a task that demands coordination across organizational boundaries and competitive interests.
- Resource and implementation constraints: Not all organizations possess the resources, expertise, or authority to implement comprehensive CIIP frameworks. Smaller utilities, regional healthcare providers, and municipal governments may lack dedicated security teams or budgets for advanced monitoring tools. This creates protection gaps that adversaries exploit, targeting less-defended infrastructure as entry points to larger networks.
- Balancing security and accessibility/functionality: Overly restrictive controls can hinder operational efficiency, user productivity, or innovation velocity. Security protocols must align with organizational needs and risk tolerance without creating barriers that users circumvent through shadow IT or workarounds. Effective CIIP designs security controls that enable rather than obstruct mission-critical operations.
- Regulatory & legal complexity: Different jurisdictions maintain different legal definitions, compliance requirements, and enforcement mechanisms for critical infrastructure protection. Global enterprises must navigate multiple regulatory regimes simultaneously—complying with European Union directives, United States sector-specific regulations, and national requirements in dozens of countries. Conflicting requirements or inconsistent standards create compliance challenges that divert resources from actual security improvements.
What Enterprises Selling to Other Enterprises Should Know
Clients operating in critical sectors—finance, telecommunications, energy, healthcare, government—maintain substantially higher expectations for vendor security practices than typical commercial customers. These expectations stem from regulatory obligations, operational risk management, and potential consequences of security failures that extend far beyond individual organizations.
Building products and services with CIIP principles integrated from initial design creates competitive differentiation. This includes secure architecture (defense in depth, least privilege, network segmentation), data protection (encryption, access controls, audit logging), redundancy and failover capabilities, compliance with relevant frameworks (ISO 27001, NIST Cybersecurity Framework, SOC 2), and documented incident response procedures. Clients in critical sectors evaluate vendors based on these capabilities during procurement processes.
Expect transparency requirements around security practices, incident response planning, disaster recovery capabilities, supply chain security, and third-party risk management. Critical sector clients will likely request security questionnaires, conduct vendor assessments, require right-to-audit clauses, and mandate notification timelines for security incidents. Organizations unable or unwilling to provide this transparency face disqualification from consideration.
Understanding regulatory frameworks becomes essential. In countries where infrastructure receives formal CII designation, legal obligations attach to operators—and may extend to vendors through contractual requirements or liability provisions. Vendors may find themselves subject to security standards, audit requirements, or incident reporting obligations based on their role in supporting critical infrastructure.
Long-term partnership potential exists for vendors who prioritize CIIP. Digital transformation accelerates across critical sectors as organizations modernize legacy systems, adopt cloud services, implement IoT and automation, and integrate artificial intelligence. These transformations create expanding demand for CIIP-aware services, solutions, and support. Vendors demonstrating genuine security competence—not performative compliance—position themselves for sustained relationships with critical sector clients.
Conclusion
Critical Information Infrastructure Protection represents a fundamental discipline for protecting systems that underpin modern society—from power generation and telecommunications to financial services and healthcare delivery. The stakes extend from national security to business continuity, public safety to data integrity.
For enterprises, particularly vendors serving clients in critical sectors, embracing CIIP principles is not discretionary. It defines the baseline security posture, resilience capabilities, and compliance standards that determine vendor qualification and long-term partnership viability. Organizations that treat CIIP as regulatory overhead rather than operational imperative inevitably face gaps between documented controls and actual security posture—gaps that become apparent when incidents occur or regulatory scrutiny intensifies.
Organizations should assess their systems systematically, classify what counts as critical infrastructure within their operational environment, build robust protection and recovery capabilities, test those capabilities under realistic scenarios, and partner with vendors who demonstrate practiced expertise in CIIP rather than superficial compliance. The question is not whether to implement CIIP but how comprehensively and how quickly—before adversaries exploit the gaps.
FAQ
1) What is critical information infrastructure protection?
Critical Information Infrastructure Protection (CIIP) is the set of strategies, practices, and operational controls aimed at protecting critical information infrastructure (CII)—systems and networks essential for vital services—from cyber threats, physical attacks, natural disasters, and other hazards. CIIP ensures the functionality, integrity, and continuity of infrastructure whose failure would seriously affect national security, economic stability, public health, or essential government services.
2) What is protected critical infrastructure information?
Protected critical infrastructure information refers to data about critical infrastructure—including system architecture, configurations, vulnerabilities, security measures, operational procedures, and assessment results—that must be safeguarded because disclosure could enable adversaries to exploit weaknesses. Many jurisdictions apply specific legal protections and handling requirements to this information, restricting access and imposing penalties for unauthorized disclosure that could compromise infrastructure security.
3) What are the 5 C's in security?
The 5 C's in security frameworks typically refer to Confidentiality, Integrity, Availability, Continuity, and Compliance. Confidentiality ensures data remains accessible only to authorized parties. Integrity prevents unauthorized modifications. Availability maintains system operability and access. Continuity enables sustained operations during disruptions. Compliance demonstrates adherence to regulatory requirements and security standards. These principles capture core objectives of comprehensive security programs across critical infrastructure sectors.
4) Does CISA still exist?
Yes. The Cybersecurity and Infrastructure Security Agency (CISA) remains the core United States federal agency responsible for critical infrastructure protection and cybersecurity coordination. CISA operates within the Department of Homeland Security, providing guidance, threat intelligence, incident response support, and regulatory oversight for critical infrastructure sectors. The agency conducts vulnerability assessments, facilitates information sharing between government and private sector entities, and coordinates national responses to significant cyber incidents affecting critical infrastructure.



.svg)
.svg)
.svg)