Most organizations approach cloud infrastructure as a technical procurement decision—selecting vendors based on feature comparisons and pricing models. This perspective fundamentally misses the strategic reality: choosing a Cloud Service Provider shapes your security posture, compliance obligations, operational resilience, and ultimately your ability to meet regulatory requirements when selling into enterprise markets or handling sensitive data.
What is a CSP in Cloud Computing?
A cloud service provider, or CSP, is an IT company that provides on-demand, scalable computing resources like computing power, data storage, or applications over the internet. When enterprises reference "CSP in cloud computing," they're describing the entity supplying the cloud environment, infrastructure, platforms, or software that organizations consume to run operations without maintaining physical data centers.
The acronym CSP stands for Cloud Service Provider—a term occasionally confused with other computing contexts, but within cloud infrastructure discussions, it specifically identifies the vendor delivering cloud resources. Cloud-based service models are typically defined as IaaS (infrastructure as a service), PaaS (platform as a service), or SaaS (software as a service). This distinction matters because each service model fundamentally alters the division of security and operational responsibility between the CSP and your organization.
CSPs operate across multiple deployment models—public cloud, private cloud, hybrid configurations, and multi-cloud architectures. The big three—Google Cloud, Microsoft Azure, and Amazon Web Services (AWS)—are considered the established leaders, though numerous specialized providers serve specific industries, regulatory requirements, or technical capabilities.
Purpose of a CSP in Cloud Computing
Enterprises engage CSPs for reasons extending beyond infrastructure outsourcing. Understanding these drivers helps frame vendor selection as a strategic decision rather than a cost-reduction exercise.
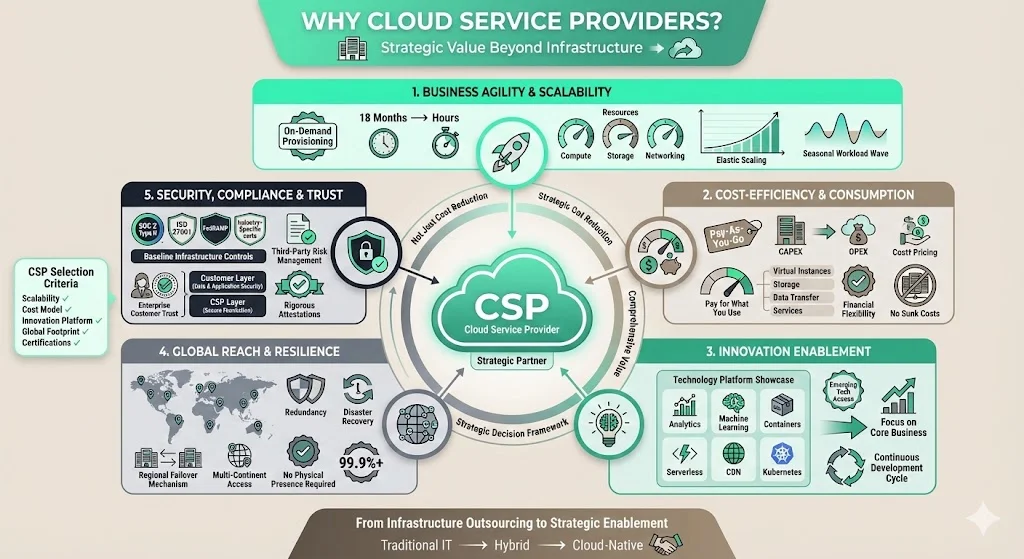
1) Business Agility and Scalability
CSPs deliver on-demand resource provisioning, enabling organizations to scale compute, storage, and networking capacity without capital investment cycles. This operational model eliminates the 12-18 month lead times typically associated with physical data center expansion, allowing enterprises to respond to market demands or seasonal workload fluctuations within hours.
2) Cost-Efficiency and Consumption Models
CSPs use a pay-as-you-go or subscription-based billing model. Customers are billed based on the resources they consume, which can include virtual instances, storage, data transfer, and additional services like databases or content delivery networks. This shifts capital expenditure (CAPEX) to operational expenditure (OPEX), improving financial flexibility and eliminating sunk costs in underutilized infrastructure.
3) Innovation Enablement
CSPs provide ready-access platforms for analytics, machine learning, containerization, serverless computing, and global content delivery. Many top cloud service providers are continuously developing new cloud-based services around emerging technologies like containerization, edge computing, machine learning, and Kubernetes. This allows enterprises to focus engineering resources on core business differentiation rather than infrastructure operations.
4) Global Reach and Resilience
CSPs operate geographically distributed data centers with built-in redundancy, disaster recovery capabilities, and regional failover mechanisms. Organizations gain access to infrastructure spanning multiple continents without establishing physical presence or negotiating colocation agreements in dozens of markets.
5) Security, Compliance and Trust
While enterprises retain ultimate responsibility for their security posture, partnering with CSPs that maintain rigorous security certifications establishes baseline infrastructure controls. CSPs seeking to serve regulated industries pursue attestations including SOC 2 Type II, ISO 27001, FedRAMP authorization, and industry-specific certifications—critical when organizations must demonstrate third-party risk management to auditors or enterprise customers.
Real-World Importance of CSPs for Enterprise Clients
The CSP selection decision carries lasting consequences for security architecture, regulatory compliance, vendor dependencies, and operational costs. Organizations treating this as a simple procurement exercise discover these implications during audits, incidents, or contract renewals.

1) Strategic Vendor Decision
CSP choice determines not just technical capabilities but control boundaries. IaaS models provide maximum flexibility with corresponding management responsibility. SaaS offerings reduce operational overhead while constraining customization. PaaS environments balance these considerations but require architectural alignment with provider-specific abstractions. Each model shifts where your security team implements controls versus relying on CSP-managed infrastructure.
2) Shared Responsibility Model
The shared responsibility model defines which security and compliance obligations belong to the CSP versus the customer organization. CSPs manage physical security, network infrastructure, hypervisor layers, and foundational services. Enterprises remain accountable for identity and access management, data encryption and classification, application security, configuration management, and incident response within their cloud environments. Misunderstanding these boundaries creates security gaps that become apparent during breaches or compliance audits.
3) Regulatory and Compliance Exposure
CSPs must support regulatory standards relevant to your industry and geographic operations—GDPR for European data subjects, HIPAA for healthcare information, CMMC for defense contractors processing controlled unclassified information. The CSP's certifications establish necessary but insufficient conditions for compliance. Your organization must implement additional controls, maintain evidence, and ensure configurations align with regulatory requirements. Auditors evaluate your implementation, not merely the CSP's attestations.
4) Security Posture and Risk Reduction
CSPs deliver baseline infrastructure security including physical data center controls, network segmentation, distributed denial-of-service mitigation, and hardware lifecycle management. Organizations must layer identity governance, encryption key management, security monitoring, threat detection, vulnerability remediation, and access controls atop this foundation. The CSP provides secure infrastructure; you're responsible for secure usage.
5) Business Continuity and Disaster Recovery
CSPs enable multi-region architectures, automated backups, and geographic redundancy that would require substantial investment if self-managed. However, organizations must design for high availability—CSPs provide the infrastructure capabilities; you implement the architectural patterns. Single-region deployments remain vulnerable to regional outages regardless of CSP reliability.
6) Cost of Mis-Choosing or Mis-Configuring CSPs
Vendor selection errors create long-term consequences: architectural lock-in to proprietary services, unexpected egress fees when migrating data, compliance gaps discovered during audits, or insufficient geographic coverage for data residency requirements. Cloud misconfigurations represent another critical risk—misconfigured access controls, exposed storage buckets, or overly permissive network rules create security incidents regardless of underlying CSP infrastructure security. For companies selling to enterprise clients, understanding CSP capabilities and limitations differentiates your advisory credibility and service integration approach.
Key Security, Compliance and Operational Dimensions
Enterprise CSP evaluation requires examining specific security and compliance dimensions that determine whether the provider supports your regulatory obligations and risk tolerance.
1) Cloud Security
Cloud security encompasses protecting infrastructure, platform, and service layers from threats while maintaining confidentiality, integrity, and availability. The shared responsibility model means CSPs secure the cloud infrastructure while customers secure their workloads, data, applications, and access patterns within that infrastructure. This division requires clear understanding: CSPs prevent physical server compromise; you prevent credential compromise and lateral movement within your cloud environment.
2) Data Protection and Encryption
Data encryption at rest and in transit represents baseline requirements for regulated industries. CSPs typically provide encryption capabilities including key management services, but organizations must implement encryption policies, manage key lifecycle, control key access, and maintain separation between data and encryption keys. Compliance frameworks require demonstrating encryption implementation, not merely CSP capability existence.
3) Access Control and Identity Management
Identity and Access Management (IAM) governs who accesses cloud resources and what actions they perform. CSPs provide IAM frameworks; enterprises define access policies, implement least privilege principles, configure multi-factor authentication, establish identity federation, and monitor privileged access. Overly permissive IAM policies create the most common cloud security misconfigurations—granting broader access than necessary violates least privilege and increases breach impact.
4) Security Policies and Threat Detection
Organizations must establish policies governing cloud resource provisioning, configuration standards, acceptable usage, and change management. Threat detection requires aggregating logs from cloud services, analyzing for anomalies, correlating events across services, and responding to indicators of compromise. CSPs offer security monitoring tools; enterprises integrate these into security operations workflows and incident response procedures.
5) Incident Response
Cloud incident response requires coordinating with CSP notification procedures, understanding CSP forensic capabilities and limitations, maintaining evidence chain of custody, and executing remediation within shared responsibility boundaries. Incident response plans must define when CSP involvement becomes necessary, how to request support, and which forensic capabilities the CSP provides versus which your team must perform.
6) Network Security
Cloud networking introduces virtual networks, software-defined segmentation, cloud-native firewalls, VPN connectivity, and zero trust architectures. CSPs provide network security capabilities; enterprises design network segmentation, configure security groups, implement micro-segmentation, and establish connectivity between cloud and on-premises environments. Network misconfiguration represents a frequent attack vector—overly permissive security groups or inadequate segmentation enable lateral movement after initial compromise.
7) Regulatory Standards and Compliance
CSP compliance certifications demonstrate infrastructure security but don't grant automatic compliance to customers. Organizations must map CSP controls to their compliance requirements, implement compensating controls where gaps exist, maintain evidence of control effectiveness, and undergo independent audits. SOC 2 Type II, ISO 27001, FedRAMP, and industry-specific certifications indicate CSP maturity, but your compliance depends on how you use those services.
8) Privacy Management
Data privacy requires understanding data jurisdiction, implementing cross-border transfer mechanisms, honoring data subject rights, and maintaining data residency compliance. CSPs operate multi-region infrastructure; enterprises select appropriate regions, configure data replication boundaries, implement data classification, and maintain processing records. GDPR, CCPA, and similar regulations hold data controllers accountable regardless of CSP processing location.
9) Risk Assessment and Security Audits
Vendor risk assessment examines CSP security posture, financial stability, operational maturity, and compliance certifications. This includes reviewing SOC 2 reports, penetration testing results, incident history, and business continuity capabilities. Ongoing risk management requires periodic reassessment, monitoring CSP security advisories, tracking CSP compliance status, and auditing your cloud environment configurations independently.
Choosing the Right CSP: What Enterprises Should Evaluate
CSP selection requires evaluating multiple dimensions beyond feature checklists and pricing comparisons.
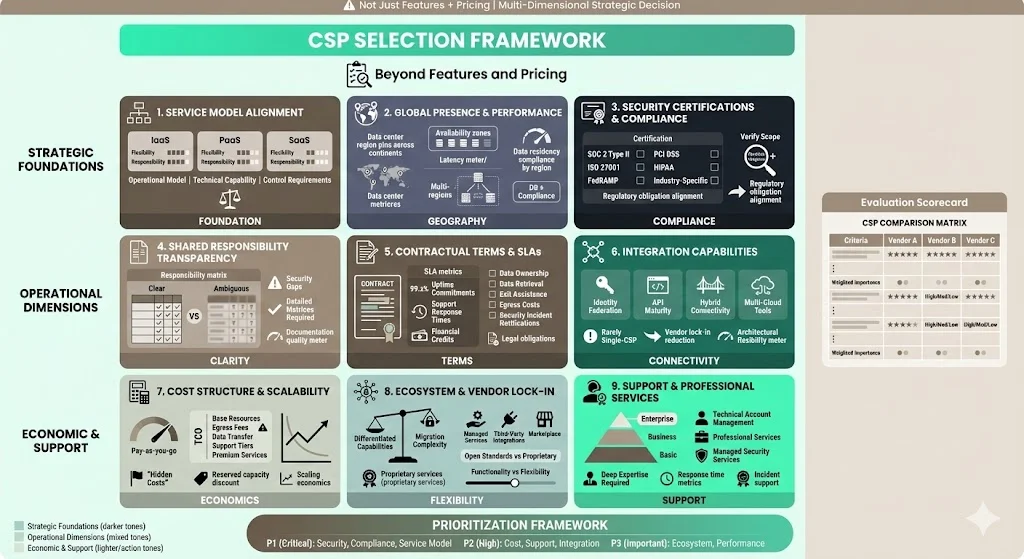
1) Service Model Alignment
Determine whether IaaS, PaaS, or SaaS best aligns with your operational model, technical capabilities, and control requirements. IaaS provides maximum flexibility with maximum operational responsibility. SaaS minimizes operational overhead with constrained customization. PaaS balances these considerations for application development workloads.
2) Global Presence and Performance
Evaluate data center regions, availability zones, network latency to your user populations, and geographic coverage for data residency requirements. Multi-region capabilities enable disaster recovery and compliance with localization mandates.
3) Security Certifications and Compliance Regimes
Review CSP attestations relevant to your regulatory obligations—SOC 2 Type II for baseline security controls, ISO 27001 for information security management, FedRAMP for government workloads, PCI DSS for payment processing, HIPAA for healthcare data, and industry-specific certifications. Verify certification scope covers relevant services and regions.
4) Shared Responsibility Transparency
CSPs should clearly document which security and compliance responsibilities belong to the provider versus customer. Ambiguity in shared responsibility creates security gaps and compliance failures. Evaluate whether the CSP provides detailed responsibility matrices across service offerings.
5) Contractual Terms and SLAs
Examine service level agreements for uptime commitments, support response times, and financial credits for service disruptions. Review data ownership terms, data retrieval procedures, exit assistance, and egress cost structures. Understand notification obligations for security incidents, legal requests, or service changes.
6) Integration Capabilities
Assess identity federation support, API maturity, hybrid connectivity options, and multi-cloud tooling compatibility. Enterprises rarely operate single-CSP environments—integration flexibility prevents architectural constraints and reduces vendor lock-in severity.
7) Cost Structure and Scalability
Understand billing models, cost optimization tools, reserved capacity discounts, and scaling economics. Evaluate total cost of ownership including egress fees, data transfer costs, support tier pricing, and premium service charges. Hidden costs often emerge after initial deployment.
8) Ecosystem and Vendor Lock-In
Consider managed services availability, third-party integrations, marketplace ecosystems, and proprietary versus open-standard services. Deep integration with CSP-proprietary services increases functionality while increasing migration complexity. Balance differentiated capabilities against architectural flexibility.
9) Support and Professional Services
Evaluate support tier options, technical account management availability, professional services capabilities, and managed security service offerings. Enterprise workloads require responsive support with deep technical expertise, particularly during incidents or complex implementations.
Real-World Use Cases and Scenarios
Enterprise Data Center Migration
A financial services organization migrates legacy applications from owned data centers to CSP infrastructure, gaining elastic scalability and reducing capital expenditure cycles. The migration requires re-architecting network security controls, implementing cloud-native identity management, encrypting data at rest with customer-managed keys, and maintaining SOC 2 and PCI DSS compliance across hybrid environments. Cost savings materialize after rightsizing instances and implementing autoscaling—initial lift-and-shift migrations often increase costs before optimization.
SaaS Provider Global Expansion
A SaaS vendor uses CSP PaaS services to deploy application infrastructure across multiple continents, serving global customers with reduced latency. The architecture requires implementing data residency controls per jurisdiction, encrypting customer data with isolated key management per tenant, establishing identity federation for enterprise customer SSO requirements, and maintaining SOC 2 Type II attestation covering cloud infrastructure. Misconfigured access controls during rapid scaling create security incidents exposing customer data.
Multi-Region Disaster Recovery Implementation
An enterprise deploys production workloads across multiple CSP regions to satisfy business continuity requirements and regulatory data sovereignty mandates. The architecture implements active-passive failover, continuous data replication within geographic boundaries, and automated failover procedures. Testing reveals RTO and RPO assumptions require architectural changes—asynchronous replication introduces data loss potential during regional failures. The implementation demonstrates that CSP infrastructure capabilities enable disaster recovery, but organizations must design, implement, test, and maintain the architecture.
Common Pitfalls:
Organizations frequently misconfigure S3 bucket permissions, granting public read access to sensitive data. Overly permissive IAM roles violate least privilege, enabling lateral movement after credential compromise. Inadequate key management stores encryption keys alongside encrypted data, negating encryption benefits. Misunderstanding shared responsibility leads to assuming CSP manages application security, access controls, or data protection—responsibilities that remain with the customer regardless of service model.
For companies selling to enterprise clients, understanding CSP capabilities, shared responsibility boundaries, and common implementation challenges positions your services as critical: migration planning, security architecture design, compliance mapping, configuration auditing, and managed security operations fill gaps between CSP infrastructure and enterprise security requirements.
Conclusion
A Cloud Service Provider in cloud computing represents far more than infrastructure outsourcing—it's the foundation upon which enterprises build security architectures, meet compliance obligations, and deliver operational resilience. The CSP supplies on-demand computing resources across IaaS, PaaS, and SaaS models, but selecting the appropriate provider requires evaluating security certifications, shared responsibility clarity, compliance regime support, geographic coverage, integration capabilities, and true cost of ownership.
Organizations treating CSP selection as a technical procurement decision discover strategic consequences during audits, security incidents, or enterprise sales cycles. The shared responsibility model means CSPs provide secure infrastructure while enterprises implement secure configurations, access controls, encryption, monitoring, and incident response. Regulatory compliance requires CSP baseline certifications plus customer-implemented controls, documented evidence, and independent attestation.
For companies selling into enterprise markets, demonstrating sophisticated understanding of CSP capabilities, shared responsibility boundaries, and implementation complexities differentiates advisory credibility. Services that wrap around CSP infrastructure—migration planning, security architecture, compliance integration, configuration auditing, continuous monitoring—address the gap between CSP infrastructure capabilities and enterprise security requirements. The vendor that helps enterprise clients navigate CSP complexity, implement controls correctly, and maintain audit readiness delivers tangible value beyond the CSP relationship itself.
Assess your current cloud vendor strategy against regulatory mandates, security requirements, and operational maturity. Evaluate whether your CSP selections support compliance obligations for your target markets. Identify opportunities to differentiate service offerings around CSP partnerships, filling gaps between infrastructure provision and enterprise security needs.
FAQs
1) What is a CSP in the cloud?
A cloud service provider, or CSP, is an IT company that provides on-demand, scalable computing resources like computing power, data storage, or applications over the internet. CSPs deliver cloud infrastructure, platforms, and software that organizations consume without maintaining physical data centers.
2) What is CSP in computing?
In cloud computing contexts, CSP refers to Cloud Service Provider—the entity supplying cloud services including infrastructure, platforms, and applications. While the acronym occasionally appears in other computing domains, within cloud discussions it specifically identifies the vendor delivering cloud resources and capabilities.
3) What does CSP stand for?
CSP stands for Cloud Service Provider. This identifies the company or organization that delivers computing resources, storage, networking, platforms, and applications over the internet using on-demand, scalable infrastructure that customers access without owning physical hardware.
4) Is AWS a CSP?
Yes. Amazon Web Services (AWS) operates as a Cloud Service Provider, offering infrastructure, platform, and software services globally. AWS represents one of the three largest CSPs alongside Microsoft Azure and Google Cloud, providing IaaS, PaaS, and various managed services across multiple regions worldwide.



.svg)
.svg)
.svg)