Most organizations underestimate the scope of modern cyber threats—in 2024 alone, at least 65 significant cyberattacks occurred worldwide, representing only the most visible incidents. Behind these headline breaches lies a fundamental vulnerability: supply chain partners handling sensitive government data often lack verifiable security controls. The Cyber AB, established as the sole authorized and independent accreditation body of the CMMC Program, addresses this gap by ensuring defense contractors meet rigorous cybersecurity standards before gaining access to controlled unclassified information.
For organizations competing in the defense industrial base, CyberAB represents more than regulatory oversight—it functions as the gatekeeper determining which businesses can participate in Department of Defense contracts. With full CMMC 2.0 implementation rolling out in December 2024, understanding CyberAB's role has shifted from academic interest to business imperative. This definition examines what CyberAB is, how it operates within the CMMC ecosystem, and why technical leaders must understand its impact on market access, security posture, and third-party risk management.
What is CyberAB?
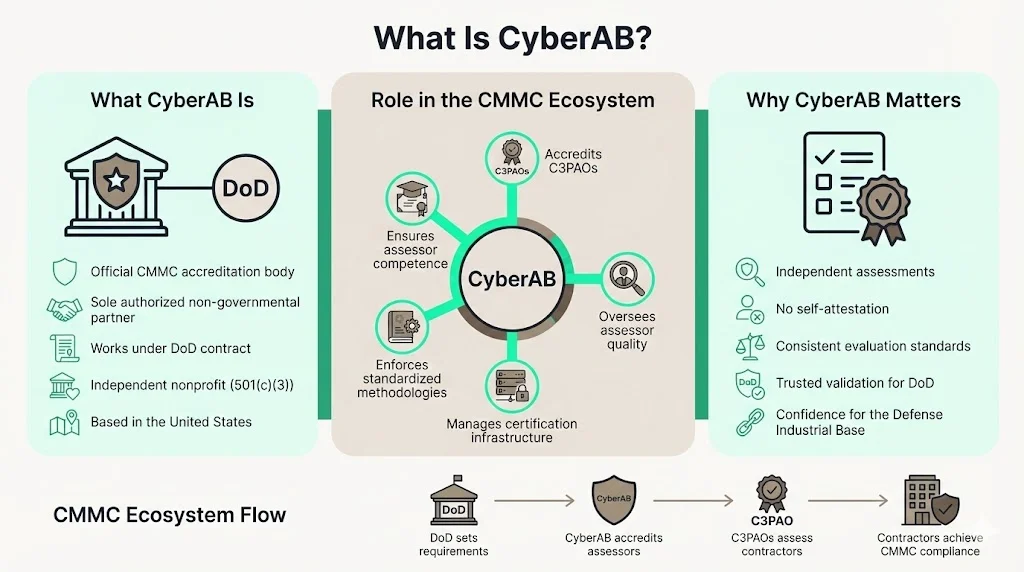
CyberAB (formerly CMMC Accreditation Body CMMC-AB) is the official accreditation body of the Cybersecurity Maturity Model Certification (CMMC) Ecosystem and the sole authorized non-governmental partner of the U.S. Department of Defense in implementing and overseeing the CMMC conformance regime. Operating as a private, independent, Maryland-based nonprofit 501(c)(3) tax-exempt organization, CyberAB serves under contract with the Department of Defense to manage the entire CMMC certification infrastructure.
The primary mission of CyberAB is to authorize and accredit the CMMC Third-Party Assessment Organizations (C3PAOs) that conduct CMMC Assessments of companies within the Defense Industrial Base (DIB). This validation function ensures assessment organizations meet quality standards before conducting compliance evaluations. Unlike self-attestation models that rely on organizational claims, CyberAB enforces independent verification through accredited assessors who demonstrate technical competence and adherence to standardized methodologies.
Brief History and Evolution
The original CMMC Accreditation Body, Inc., was founded in January 2020 to administrate the DoD's implementation of CMMC throughout the Defense Industrial Base. CMMC was published by the DoD in January 2020, while the CMMC-AB was formed simultaneously and rebranded as the Cyber AB in 2022. The rebrand signaled more than cosmetic change. According to CEO Matthew Travis, "The new name, The Cyber AB, provides a more accessible common name and signals the organization's potential future growth" beyond DoD-specific programs.
The initial version of CMMC rolled out as an interim rule in 2020, with work immediately beginning to streamline it and address implementation problems. CMMC 2.0 was announced in late 2021, the Final Rule was published in October 2024, and full CMMC 2.0 implementation began rolling out in December 2024. This evolution reflects lessons learned from initial deployment challenges and industry feedback regarding complexity, cost, and assessment consistency.
How CyberAB Fits into Cyber Security
CyberAB addresses a fundamental security challenge: verifying that organizations implement actual protective controls rather than generating compliance documentation. Traditional self-assessment approaches allowed organizations to claim compliance without independent validation—a gap exploited in supply chain compromises where attackers target less-secured vendors to access protected networks. Recent attacks include the SolarWinds supply line attack, compromised Outlook services, and the ongoing Salt Typhoon attack on telecom companies, demonstrating how adversaries exploit supply chain vulnerabilities.
By requiring third-party assessment through accredited organizations, CyberAB creates accountability for security claims. This structured validation reduces the effectiveness of attacks targeting weak supply chain partners and establishes baseline security expectations across thousands of defense contractors. The framework addresses threats including advanced persistent threats, ransomware, phishing campaigns targeting controlled unclassified information, and insider threats from inadequately secured partner networks.
How CyberAB Operates
Accreditation and Certification Oversight
CyberAB is responsible for establishing, managing, controlling, and administering the CMMC assessment, certification, training, and accreditation processes for the Department of Defense supply chain. This comprehensive mandate extends beyond simple authorization to encompass quality control, ongoing surveillance, and enforcement of assessment standards.
CyberAB's primary role is to authorize and accredit C3PAOs that conduct CMMC assessments of organizations within the DIB. It also manages the professional certification and training aspects of the CMMC Ecosystem, working with partners to develop curricula and examination protocols for CMMC Assessors and CMMC Instructors. This layered approach creates accountability at multiple levels—assessors must demonstrate competence, assessment organizations must maintain quality management systems, and both undergo surveillance to ensure continued compliance with accreditation standards.
The accreditation process evaluates assessment organizations against ISO/IEC 17020 requirements, establishing competence in inspection body operations. In 2024, CyberAB contracted ANAB to assist on the accreditation assessments and surveillance visits of C3PAOs, bringing additional accreditation expertise to the validation process. This partnership ensures assessment organizations meet internationally recognized standards for impartiality, competence, and consistent application of assessment methodologies.
The CMMC Framework Connection
CMMC establishes security practice requirements based on NIST SP 800-171 and NIST SP 800-172, creating three certification levels corresponding to information sensitivity and threat exposure. Organizations handling federal contract information require Level 1 certification, while those processing controlled unclassified information typically require Level 2 or Level 3 depending on contract requirements and risk assessments.
CyberAB outlines the requirements and processes for achieving CMMC certification, building upon existing regulations such as NIST SP 800-171, DFARS 252.204-7012, and others to establish a comprehensive cybersecurity standard. The framework maps security practices to specific control objectives, requiring documented evidence of implementation and effectiveness. Level 2 assessments require demonstration of all 110 NIST SP 800-171 security requirements plus organizational maturity in managing cybersecurity practices.
CyberAB ensures assessment consistency by standardizing evidence collection, evaluation criteria, and reporting formats. The CMMC Assessment Process (CAP) is now available and serves as the required procedural guide for Authorized C3PAOs to use on CMMC Level 2 certification assessments. This standardization prevents assessor interpretation variance and establishes objective criteria for determining compliance with security practice requirements.
Ecosystem Functions
CyberAB has launched an enhanced Marketplace, a core capability that brings together the many interested parties and service providers involved in CMMC. This marketplace functions as a registry where defense contractors identify accredited assessment organizations, certified assessors, and approved training providers. The transparency created by this centralized directory reduces information asymmetry and helps organizations select qualified partners.
Beyond marketplace functions, CyberAB maintains ongoing policy development, assessment methodology refinement, and training program updates. As threat landscapes evolve and new attack vectors emerge, CyberAB updates guidance to ensure assessments remain relevant to actual security risks rather than becoming a compliance theater disconnected from operational reality. This adaptive approach prevents the framework from becoming obsolete as adversary capabilities advance.
Why CyberAB Matters to Businesses
Impact on Enterprise-Level Security Preparedness
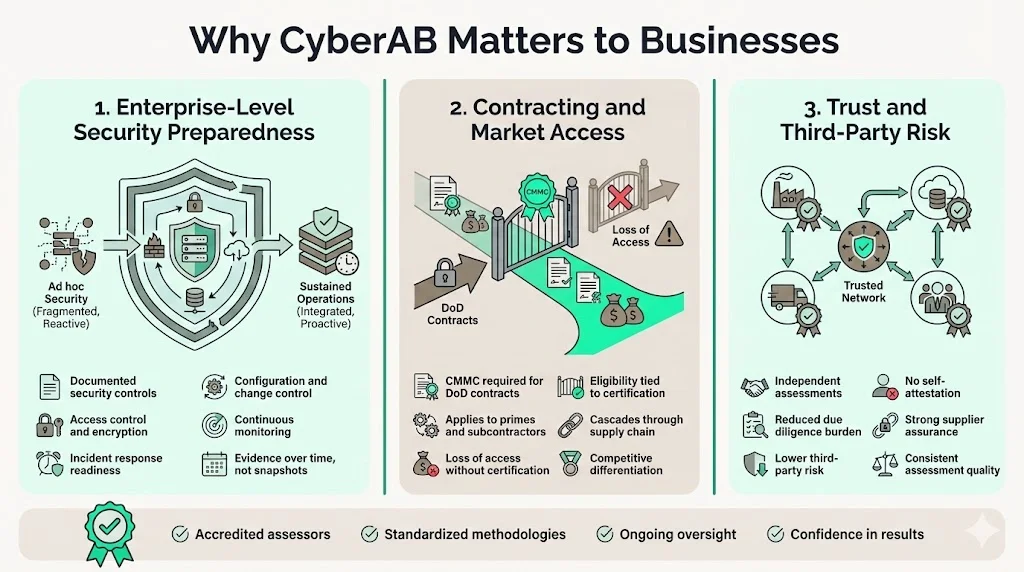
Organizations pursuing CMMC certification must implement documented security controls spanning access control, incident response, system hardening, encryption, network segmentation, vulnerability management, and security awareness training. These requirements force systematic evaluation of security architecture, identification of control gaps, and remediation of vulnerabilities that may have persisted for years due to resource constraints or competing priorities.
The assessment process requires evidence demonstrating control effectiveness over time—not point-in-time compliance snapshots. Organizations must show configuration management, change control, continuous monitoring, and documented responses to security events. This evidence-based approach compels organizations to build sustainable security operations rather than implementing temporary controls for audit purposes then reverting to insecure practices.
For many organizations, CMMC preparation represents the first comprehensive security infrastructure review conducted by external parties with deep technical expertise. This independent perspective often identifies blind spots, misconfigurations, and architectural weaknesses internal teams overlook due to familiarity or resource limitations. The result improves resilience against ransomware, business email compromise, credential theft, and other threats targeting organizations regardless of defense contractor status.
Implications for Contracting and Market Access
Organizations handling CUI or working with the DoD must achieve the appropriate CMMC certification level to be eligible for contract awards. This requirement fundamentally changes competitive dynamics within the defense industrial base—security posture directly impacts business development capability. Organizations lacking certification cannot compete for contracts requiring CMMC compliance, effectively excluding them from significant market segments.
The certification requirement extends beyond prime contractors to subcontractors at all tiers handling controlled unclassified information. Organizations serving as second, third, or fourth-tier suppliers must achieve certification if their contract performance involves CUI access or processing. This cascading requirement affects thousands of businesses across diverse industries—from software developers to manufacturing firms to professional services organizations.
Forward-looking organizations position CMMC certification as competitive differentiation rather than mere compliance obligation. Certification demonstrates investment in security infrastructure, commitment to protecting sensitive information, and capacity to meet rigorous operational standards. For businesses targeting enterprise clients beyond the defense sector, CMMC certification signals security maturity that reduces third-party risk concerns.
Trust and Third-Party Risk
Enterprise organizations increasingly evaluate supplier security posture before establishing business relationships. Data breaches originating from compromised suppliers create liability exposure, regulatory scrutiny, and reputational damage for affected organizations. Third-party risk management programs require vendors to demonstrate security controls through independent assessments rather than self-attestation questionnaires.
CMMC certification provides verifiable evidence of security control implementation validated by accredited assessors operating under standardized methodologies. This independent verification reduces due diligence burden for enterprise clients evaluating supplier security. Rather than conducting proprietary security assessments of each vendor, organizations can rely on CMMC certification as baseline security assurance.
The accreditation structure managed by CyberAB increases confidence in assessment quality. Knowing that C3PAOs undergo accreditation against ISO/IEC 17020 requirements and face ongoing surveillance creates accountability absent in unregulated assessment markets where competence varies dramatically. This quality assurance distinguishes CMMC assessments from vendor-provided security attestations lacking independent validation.
Business Challenges and Considerations
Preparing for CMMC Assessments
Organizations pursuing CMMC certification must implement system security plans documenting security requirements, control implementations, and operational procedures. This documentation requires security architecture clarity often absent in organically-evolved IT environments where systems accumulated incrementally without comprehensive security design.
Gap assessments identify discrepancies between current state and CMMC requirements, revealing control deficiencies requiring remediation. Common gaps include inadequate access control, missing multifactor authentication, incomplete asset inventories, absent or inadequate incident response procedures, insufficient security awareness training, and inadequate configuration management. Remediation typically requires 4-8 months depending on gap severity and organizational complexity.
Evidence collection presents operational challenges for organizations lacking mature security operations. CMMC assessments require documented proof of control effectiveness—security logs, access reviews, vulnerability scan results, incident response records, training completion records, and change management documentation. Organizations without established processes for generating and retaining this evidence must implement systems supporting ongoing evidence collection before assessment readiness.
Costs and Timeframes
CMMC certification requires investment in security infrastructure improvements, staff training, policy development, evidence collection systems, and assessment fees. Total costs vary based on organizational size, current security posture, scope of systems processing controlled unclassified information, and required certification level. Organizations with mature security programs face lower remediation costs than those starting from minimal baseline security.
Assessment costs for Level 2 certification typically range from $30,000 to $150,000+ depending on organizational complexity, number of facilities, system architecture, and assessor rates. Organizations should budget additional internal labor costs for evidence preparation, assessor coordination, and remediation of findings identified during assessment. These costs represent investments in security infrastructure producing value beyond compliance—improved incident response capability, reduced breach risk, and enhanced operational resilience.
Timeline considerations require early planning. Organizations beginning CMMC preparation should allocate 6-12 months for gap remediation, evidence collection system implementation, and internal process maturation before scheduling formal assessment. Rushed preparation typically produces superficial compliance failing to address underlying security deficiencies, increasing failure risk and requiring reassessment with additional costs.
Global and Regulatory Considerations
CMMC requirements apply to any organization handling DoD controlled unclassified information regardless of geographic location. International suppliers serving U.S. defense contractors must achieve CMMC certification to continue participation in supply chains involving CUI. This extraterritorial reach creates compliance obligations for organizations outside U.S. jurisdiction but economically dependent on defense sector business.
CyberAB currently has no connection to ISO 27001 certification—ISO security standards have their own governing bodies and certification standards. Organizations maintaining ISO 27001 certification cannot claim automatic CMMC compliance—separate assessments against different standards apply. While ISO 27001 and CMMC share common security principles, control mappings differ and independent validation by accredited C3PAOs remains mandatory.
Organizations operating globally must navigate multiple compliance frameworks without reciprocity between standards. GDPR compliance addresses data privacy through different requirements than CMMC's security focus. HIPAA technical safeguards protect health information under distinct regulatory authority. Businesses subject to multiple frameworks must implement comprehensive security programs satisfying diverse regulatory expectations while avoiding duplicative investments in non-overlapping requirements.
Practical Steps for Business Leaders
Starting Your CyberAB/CMMC Journey
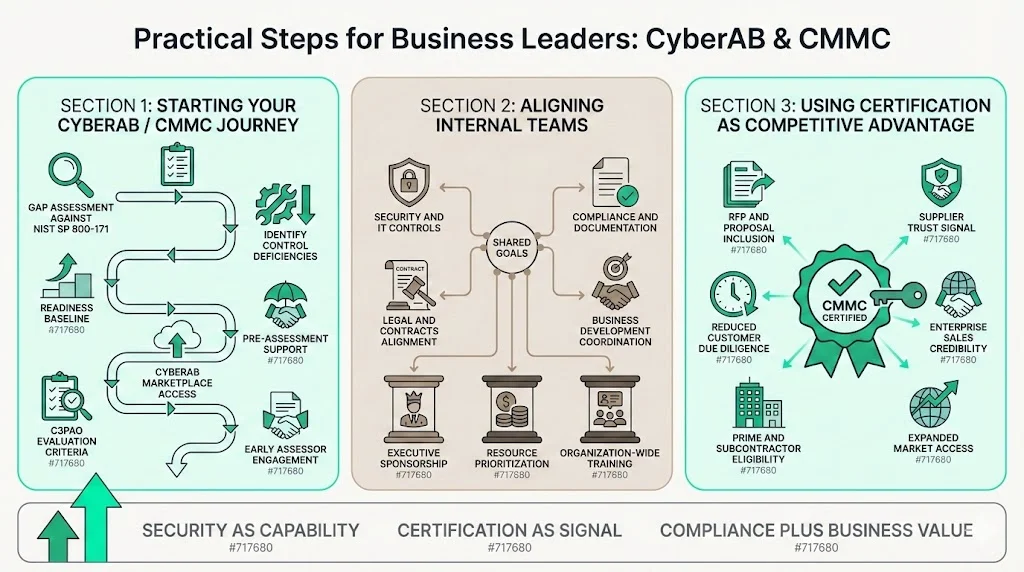
Organizations beginning CMMC preparation should conduct comprehensive gap assessments comparing current security controls against NIST SP 800-171 requirements. This assessment identifies specific control deficiencies requiring remediation and establishes baseline understanding of certification readiness. Many organizations engage consultants with CMMC expertise to conduct preliminary assessments providing implementation roadmaps.
The CyberAB Marketplace provides access to accredited assessors and organizations approved to conduct CMMC certifications. Organizations should evaluate multiple C3PAOs based on industry expertise, assessment approach, geographic coverage, and client references. Early C3PAO engagement often includes pre-assessment activities identifying gaps and providing remediation guidance before formal assessment scheduling.
Document current security practices systematically—even organizations with strong security often lack documentation proving control implementation. Assessment readiness requires written policies, procedure documentation, system security plans, configuration standards, and records demonstrating ongoing security operations. Organizations should implement documentation practices sustainable beyond initial certification, supporting continuous compliance rather than point-in-time audit preparation.
Aligning Internal Teams
CMMC preparation requires coordination across security, IT operations, compliance, legal, contracts, and business development functions. Security teams implement technical controls while compliance teams manage documentation and evidence collection. IT operations maintains systems supporting security requirements while business development leverages certification in competitive positioning.
Executive leadership must provide resources, establish priorities, and resolve competing demands affecting CMMC preparation. Organizations treating certification as an isolated compliance project rather than security infrastructure investment typically struggle with resource allocation, deadline pressure, and inadequate control implementation. Leadership should frame CMMC as an operational capability enhancement producing security improvements beyond certification requirements.
Training programs must extend beyond security teams to employees handling controlled unclassified information. CMMC requires documented security awareness training covering threat recognition, incident reporting, acceptable use policies, and data handling procedures. Organizations should implement training programs supporting ongoing awareness rather than annual checkbox exercises disconnected from actual security practices.
Using Certification as Competitive Advantage
Organizations achieving CMMC certification should highlight compliance status in requests for proposals, capability statements, and business development materials. Certification demonstrates security investment distinguishing certified organizations from competitors lacking validated security controls. For enterprises evaluating suppliers, CMMC certification reduces due diligence burden and signals commitment to information protection.
Security maturity extends beyond defense sector business. Enterprise clients across industries increasingly require supplier security assessments as third-party risk management standard practice. Organizations positioning CMMC certification as broader security capability—not merely DoD compliance obligation—create competitive differentiation in enterprise sales cycles where security posture influences buying decisions.
Certification provides opportunities for market expansion into contracts previously inaccessible due to security requirements. Organizations can pursue prime contractor opportunities requiring CMMC compliance or position as preferred subcontractors for primes seeking certified supply chain partners. This market access represents tangible business value justifying certification investment beyond compliance cost avoidance.
Conclusion
CyberAB functions as the validation authority ensuring CMMC assessments measure actual security implementation rather than compliance theater. By accrediting assessment organizations, certifying assessors, and standardizing evaluation methodologies, CyberAB creates accountability in certification processes that directly impact defense industrial base security posture. For organizations competing in government markets, CyberAB represents the gatekeeper determining market access through security validation.
The broader significance extends beyond defense contracting. Independent security validation through accredited third parties establishes trust in supplier relationships where information protection determines business viability. Organizations treating CMMC as isolated compliance requirements miss opportunities to strengthen security infrastructure, reduce breach exposure, and differentiate security capabilities in enterprise markets. Security investment produces compliance as a natural outcome—the inverse approach of manufacturing compliance artifacts without implementing genuine controls ultimately fails when subjected to independent assessment by qualified evaluators operating under CyberAB oversight.
FAQs
Q1: What is CyberAB?
CyberAB is a nonprofit accreditation body serving as the official accreditation body of the Cybersecurity Maturity Model Certification Ecosystem and the sole authorized non-governmental partner of the U.S. Department of Defense in implementing and overseeing the CMMC conformance regime.
Q2: Why was CyberAB created?
CyberAB was created to bring impartial, consistent oversight to CMMC certification processes protecting controlled unclassified information against cyber threats. The organization validates that assessment organizations meet quality standards before conducting compliance evaluations, ensuring assessments measure actual security implementation rather than self-attestation claims.
Q3: How does CyberAB affect CMMC certification?
CyberAB authorizes and accredits the C3PAOs that conduct CMMC assessments of companies within the Defense Industrial Base. CyberAB ensures assessments follow standardized methodologies, assessors demonstrate technical competence, and certification decisions reflect objective evaluation against established criteria—making CMMC certification meaningful through independent validation.
Q4: Is CyberAB the same as CMMC?
No. CMMC is the cybersecurity framework establishing security practice requirements based on NIST standards. CyberAB manages the accreditation and certification ecosystem implementing CMMC—accrediting assessment organizations, certifying assessors, standardizing evaluation methodologies, and maintaining quality oversight. CMMC defines what security controls organizations must implement; CyberAB validates that assessments measuring compliance meet quality standards.
Q5: Who needs to pay attention to CyberAB updates?
Any organization targeting DoD contracts, participating in defense supply chains at any tier, or serving enterprise clients requiring validated security controls should monitor CyberAB updates. Changes to assessment procedures, certification requirements, or marketplace listings directly affect compliance strategies, assessment preparation, and business development capabilities for organizations dependent on CMMC certification for market access.



.svg)
.svg)
.svg)