Most organizations describe cybersecurity as "protecting our systems," yet struggle to articulate what security actually means in measurable terms. This definitional gap creates fundamental vulnerabilities—a lack of clarity that becomes apparent when executives cannot assess vendor capabilities, prioritize security investments, or establish accountability across teams.
Security in cybersecurity represents the systematic practice of protecting digital systems, networks, data, and operations from unauthorized access, attacks, damage, and disruption. For enterprise decision-makers, understanding this definition matters because procurement decisions, compliance attestations, and incident response capabilities all depend on a shared understanding of what constitutes adequate security. Without definitional precision, organizations invest in fragmented tools that address symptoms rather than building cohesive security infrastructure.
What Does Security Mean in Cyber Security?
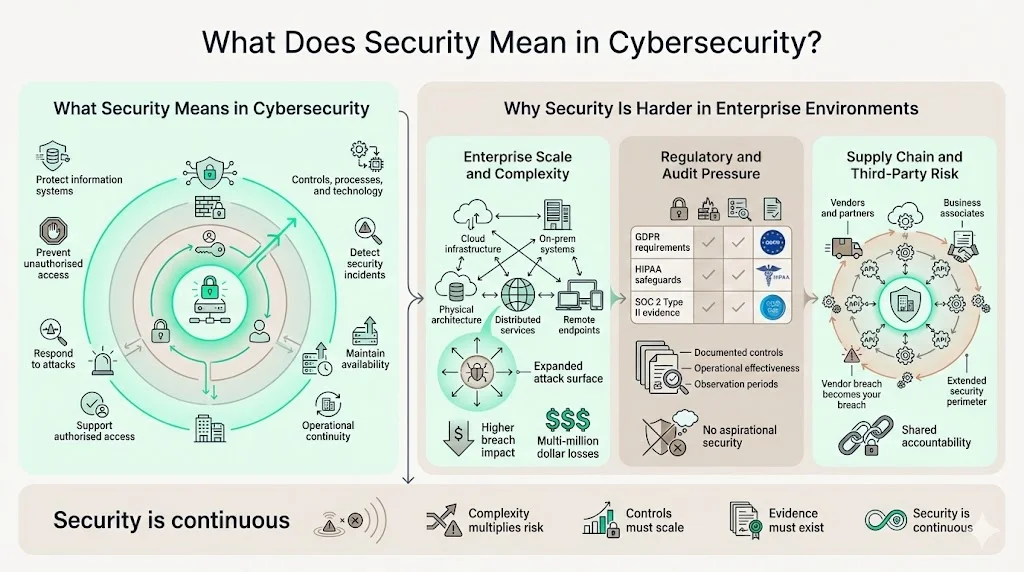
Security in cybersecurity is the discipline of implementing controls, processes, and technologies that protect information systems against digital threats while maintaining authorized access and operational continuity. This encompasses three concurrent objectives: preventing unauthorized access to sensitive assets, detecting and responding to security incidents, and maintaining system availability under both normal operations and attack conditions.
How It Applies to Enterprise Contexts
Enterprise environments require structured security approaches due to operational complexity that exceeds small business environments. Organizations with distributed systems across cloud infrastructure, on-premises data centers, and remote endpoints face exponentially more attack surfaces than single-location operations. A 2024 IBM study found the average data breach cost reached $4.88 million, with enterprise breaches often exceeding $10 million when regulatory penalties and business disruption compound direct remediation costs.
Enterprises also operate under heightened regulatory scrutiny. GDPR compliance requires documented technical and organizational measures protecting personal data. HIPAA mandates specific administrative, physical, and technical safeguards for electronic protected health information throughout its lifecycle. SOC 2 Type II attestations demand evidence of control effectiveness over minimum 6-month observation periods. These regulatory frameworks don't accept aspirational security—they require documented proof of implemented controls.
Supply chain complexity further elevates enterprise security requirements. Third-party vendors, business associates, and integration partners extend your security perimeter beyond direct control. A vendor breach becomes your breach when customer data is compromised through a supplier's inadequate security posture.
The Core Principles: Confidentiality, Integrity, and Availability (CIA Triad)
The CIA Triad establishes the foundational objectives that define effective security programs. These three principles—confidentiality, integrity, and availability—provide the framework against which security controls are designed, implemented, and measured.
Confidentiality
Confidentiality ensures that sensitive information remains accessible only to authorized individuals, systems, and processes. This principle protects data from unauthorized disclosure through access controls, encryption, and authentication mechanisms.
Enterprise confidentiality requirements extend beyond preventing external breaches to include internal access restrictions. Employee access to customer financial records, proprietary research, or strategic planning documents must follow the principle of least privilege—granting only the minimum access required for legitimate job functions. GDPR's data minimization principle and HIPAA's minimum necessary standard both operationalize confidentiality through access limitation requirements.
Integrity
Integrity guarantees that data remains accurate, consistent, and unaltered except through authorized modifications. This principle protects against both malicious tampering and unintentional corruption that could compromise business decisions, regulatory compliance, or system operations.
For enterprises, integrity failures carry consequences beyond immediate data loss. Financial reporting systems with compromised data integrity produce inaccurate statements that violate SEC requirements and undermine investor confidence. Medical records altered through security breaches create patient safety risks and HIPAA violations. Supply chain data corruption cascades through procurement, inventory management, and fulfillment operations.
Technical controls supporting integrity include cryptographic hashing to detect unauthorized changes, version control systems maintaining audit trails, and database transaction controls preventing partial updates that create inconsistent states.
Availability
Availability ensures that authorized users can access systems and data when operationally required. This principle addresses both malicious denial-of-service attacks and system failures that disrupt business continuity.
Enterprise availability requirements typically exceed consumer service expectations. E-commerce platforms experiencing one hour of downtime during peak shopping periods may lose millions in revenue and suffer lasting customer attrition. Healthcare systems must maintain electronic health record access during emergencies when patient care depends on immediate information availability. Financial services operate under strict uptime requirements where system unavailability triggers regulatory reporting obligations.
Availability controls include redundant infrastructure, distributed denial-of-service mitigation, backup and recovery procedures, and incident response capabilities that restore operations within defined recovery time objectives.
Why the CIA Triad Matters for Security
The CIA Triad provides the conceptual foundation underlying security frameworks, compliance requirements, and control implementations. ISO 27001 control objectives map directly to confidentiality, integrity, and availability protection. SOC 2 Trust Services Criteria evaluate how organizations safeguard these three principles. NIST Cybersecurity Framework functions—Identify, Protect, Detect, Respond, Recover—operationalize CIA Triad protection across the risk management lifecycle.
Security programs that prioritize technology investments without reference to CIA principles often implement disconnected tools that fail to address actual risk. The Triad forces strategic clarity: which assets require confidentiality protection, which systems have integrity dependencies, and what availability requirements drive business continuity planning.
Key Components That Strengthen Security
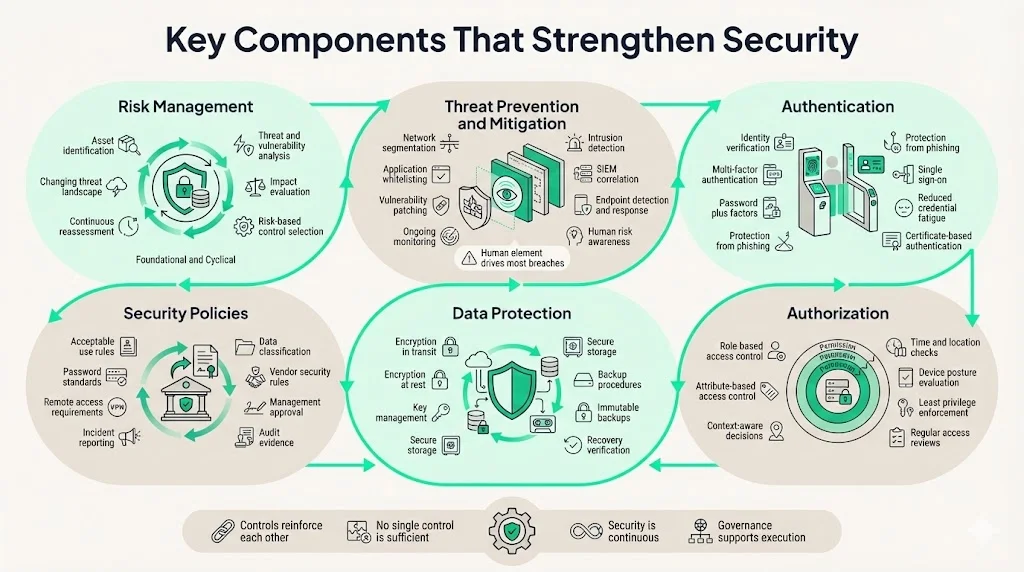
Risk Management
Risk management in cybersecurity represents the continuous process of identifying assets and threats, assessing vulnerability exposure, evaluating potential impact, and implementing controls that reduce risk to acceptable levels. Unlike project-based security initiatives with defined endpoints, risk management operates as an ongoing discipline responding to evolving threats, changing business operations, and newly discovered vulnerabilities.
NIST Special Publication 800-37 establishes the Risk Management Framework requiring organizations to categorize information systems, select and implement security controls, assess control effectiveness, authorize system operations, and continuously monitor security posture. This cyclical approach recognizes that security adequacy isn't static—controls effective against last year's threat landscape may prove insufficient against current attack techniques.
Threat Prevention & Mitigation
Effective security requires both preventing threats before they compromise systems and mitigating impact when prevention fails. Prevention controls include network segmentation limiting lateral movement after initial compromise, application whitelisting preventing unauthorized software execution, and vulnerability management patching known security flaws before exploitation.
Mitigation capabilities assume that determined attackers will eventually breach perimeter defenses. Intrusion detection systems identify suspicious network traffic patterns indicating compromise. Security information and event management platforms correlate logs across distributed systems to detect attack indicators that individual systems miss. Endpoint detection and response tools monitor host behavior for malicious activity that signature-based antivirus fails to catch.
The 2024 Verizon Data Breach Investigations Report found that 68% of breaches involved a human element, highlighting that technology-only approaches prove insufficient. Security awareness training, phishing simulation programs, and incident response exercises address the human factors that often provide attackers their initial access.
Authentication
Authentication verifies that users, devices, or systems are who they claim to be before granting access to protected resources. Enterprise authentication has evolved beyond username-password combinations that prove vulnerable to credential theft, phishing attacks, and password reuse across services.
Multi-factor authentication requires users to present multiple verification factors: something they know (password), something they have (hardware token or mobile device), or something they are (biometric identifier). This approach ensures that credential compromise alone proves insufficient for unauthorized access.
For enterprise deployments, single sign-on systems centralize authentication while reducing password fatigue that drives users toward weak credentials. Certificate-based authentication provides stronger assurance for system-to-system communication protecting API access and service accounts.
Authorization
While authentication verifies identity, authorization determines what authenticated users can access and which actions they can perform. Role-based access control assigns permissions based on job functions rather than individual user grants, simplifying administration across organizations with hundreds or thousands of employees.
Attribute-based access control extends role models by evaluating contextual factors including time of day, geographic location, device security posture, and data sensitivity classifications. A user authorized to access customer records from corporate networks during business hours may face additional authentication requirements when accessing the same data from public networks at unusual times.
Authorization failures create two types of risk: excessive permissions that violate least privilege principles, and insufficient access that disrupts legitimate business operations. Regular access reviews identifying unnecessary permissions help maintain authorization accuracy as job responsibilities change.
Data Protection
Data protection encompasses the technical controls safeguarding information throughout its lifecycle—during creation, transmission, storage, use, and destruction. Encryption transforms readable data into ciphertext that remains unintelligible without decryption keys, protecting confidentiality even when storage media or network traffic is intercepted.
Transport Layer Security encrypts data in transit between systems, preventing network eavesdropping during internet transmission. Full-disk encryption and database encryption protect data at rest against theft of physical devices or unauthorized access to storage systems.
Beyond encryption, data protection requires backup procedures ensuring recovery from ransomware attacks, hardware failures, or accidental deletion. Backup integrity verification confirms that recovery procedures actually work before disasters occur. Immutable backup storage prevents attackers from destroying backup copies during ransomware attacks.
Security Policies
Security policies establish the formal rules, standards, and procedures governing how organizations protect information assets and respond to security events. These documented requirements translate abstract security objectives into specific behavioral expectations and technical configurations.
Effective policies address acceptable use of corporate systems, password requirements, remote access procedures, incident reporting obligations, data classification standards, and vendor security requirements. Policies also define roles and responsibilities, establishing accountability for security decisions and incident response actions.
ISO 27001 certification requires documented information security policies approved by management and communicated to relevant personnel. SOC 2 auditors evaluate whether organizations follow their documented policies and maintain evidence demonstrating policy compliance. Without clear policies, organizations lack the governance foundation supporting consistent security practices across business units, geographies, and operational contexts.
How These Components Work Together in an Enterprise Setting
Security effectiveness emerges from integrated implementation across people, processes, and technology—not from fragmented tools deployed without strategic coordination. Authentication and authorization controls prove ineffective when security policies fail to define access requirements or when employees lack training recognizing social engineering attacks. Data protection encryption provides limited value when key management processes store decryption keys alongside encrypted data.
Consider SOC 2 compliance: achieving Type II attestation requires implementing technical controls (multi-factor authentication, encryption, logging), documented processes (access reviews, vulnerability management, incident response), and personnel practices (security awareness training, background checks, separation of duties). Organizations treating compliance as a technology purchase rather than an operational discipline inevitably face audit findings and security gaps.
This integrated approach builds resilient security posture that adapts to evolving threats. Risk management processes identify emerging vulnerabilities, security policies define response requirements, technical controls implement protective measures, and trained personnel execute procedures during both normal operations and incident response.
Common Enterprise Security Challenges
System Complexity: Enterprise environments spanning cloud infrastructure, legacy on-premises systems, mobile devices, and third-party integrations create visibility gaps where security teams cannot effectively monitor all assets or enforce consistent controls. Organizations with 10,000+ endpoints across multiple geographies face fundamentally different security challenges than small businesses with centralized systems.
Access Balance: Restrictive security controls that impede legitimate business operations drive users toward shadow IT solutions outside security team visibility. Conversely, permissive access policies prioritizing convenience over security expand attack surfaces and violate regulatory requirements. Finding appropriate balance requires understanding business workflows, risk tolerance, and regulatory obligations.
Regulatory Compliance: Organizations operating across multiple jurisdictions navigate overlapping and sometimes conflicting requirements. GDPR's data localization requirements may conflict with business continuity strategies relying on geographically distributed backups. HIPAA's documentation requirements differ from ISO 27001's evidence expectations despite addressing similar security objectives. Companies allocating 550-600 hours annually to compliance management still report feeling unprepared for audits when treating compliance as annual initiatives rather than continuous security operations.
Threat Evolution: Attack techniques advance continuously as adversaries develop new exploitation methods and security tools improve detection capabilities. Ransomware attacks that once targeted individual workstations now compromise backup systems and threaten operational technology. Supply chain attacks exploit trusted vendor relationships rather than directly attacking hardened enterprise perimeters. Security programs designed around yesterday's threats prove inadequate against current adversary capabilities.
Practical Steps for Enterprise Buyers
When evaluating cybersecurity solutions and managed service providers, assess capabilities against enterprise requirements rather than feature checklists that fail to address actual security outcomes.
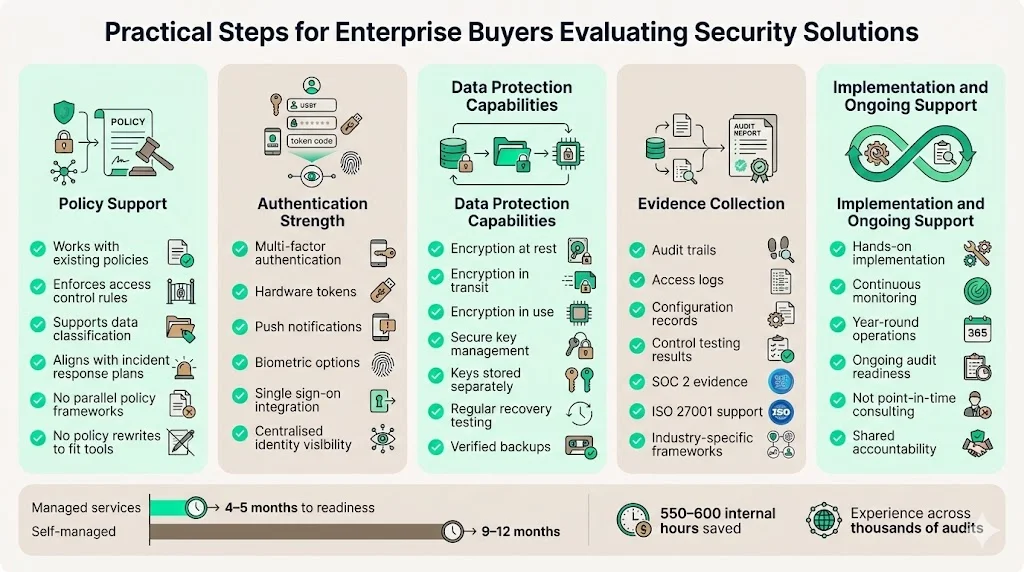
Policy Support: Verify that solutions integrate with documented security policies rather than requiring policy revision to accommodate tool limitations. Effective platforms enforce existing access control policies, data classification standards, and incident response procedures without creating parallel policy frameworks.
Authentication Strength: Require multi-factor authentication supporting multiple verification methods (hardware tokens, push notifications, biometrics) rather than single-factor implementations vulnerable to credential theft. Evaluate single sign-on integration reducing password proliferation while maintaining centralized authentication visibility.
Data Protection Capabilities: Confirm encryption covers data at rest, in transit, and in use. Assess key management procedures ensuring that encryption keys remain protected separately from encrypted data. Verify backup integrity through regular recovery testing rather than assuming backup success without validation.
Evidence Collection: Compliance readiness requires documented proof of control effectiveness, not just implemented security tools. Solutions should generate audit trails, access logs, configuration records, and control testing evidence supporting SOC 2, ISO 27001, or framework-specific requirements relevant to your industry.
Implementation Support: Managed security services should provide hands-on implementation, not just advisory guidance ending after initial deployment. Year-round security operations, continuous monitoring, and sustained audit readiness prove more valuable than point-in-time consulting engagements that leave internal teams responsible for ongoing security management.
Organizations achieve security readiness in 4-5 months with managed services combining platform capabilities and dedicated expertise, compared to 9-12 months for self-managed approaches requiring 550-600 hours of internal investment annually. This time difference stems from practiced implementation experience across 6,000+ completed audits rather than learning compliance requirements through trial and error.
Conclusion
Security in cybersecurity represents the systematic protection of digital systems, networks, data, and operations through integrated controls addressing confidentiality, integrity, and availability. This definition matters for enterprise organizations because procurement decisions, compliance attestations, regulatory obligations, and incident response capabilities all depend on shared understanding of security requirements and adequate implementation.
Effective security emerges from coordinated implementation across technical controls, documented processes, and trained personnel—not fragmented tools deployed without strategic integration. Organizations building genuine security infrastructure that produces compliance as a natural outcome invest in risk management, authentication and authorization controls, data protection, and security policies that govern behavior consistently across complex enterprise environments.
FAQ Section
1. What does security mean in cyber security?
Security in cybersecurity is the practice of protecting digital systems, networks, and data from unauthorized access, attacks, and disruption while maintaining availability for legitimate users. It encompasses technical controls, documented processes, and personnel practices working together to safeguard confidentiality, integrity, and availability.
2. Why is the CIA triad important?
The CIA Triad—confidentiality, integrity, and availability—provides the foundational principles underlying security frameworks, compliance requirements, and control implementations. These three objectives guide security planning by clarifying which assets require protection, what threats pose the greatest risk, and how controls should function. ISO 27001, SOC 2, and NIST frameworks all structure requirements around protecting these three principles.
3. Is cybersecurity only a technical issue?
Cybersecurity requires coordinated implementation across people, processes, and technology. Technical controls prove ineffective when personnel lack training to recognize phishing attacks or when documented processes fail to define incident response procedures. Data breach investigations consistently find that human factors contribute to the majority of security incidents, highlighting that technology alone cannot address security comprehensively.
4. Who owns security in an enterprise?
Security responsibility is shared across organizational levels with distinct accountabilities. Executive leadership establishes security strategy, allocates resources, and accepts residual risk after controls are implemented. Security teams design controls, monitor systems, and manage incident response operations. Individual employees follow security policies, complete required training, and report suspicious activity. Effective security requires all three groups executing their respective responsibilities rather than treating security as solely an IT department concern.
5. How do policies support cybersecurity?
Security policies translate abstract security objectives into specific behavioral expectations and technical requirements. Documented policies define acceptable use standards, access control procedures, incident reporting obligations, and vendor security requirements. These formal rules enable consistent security practices across business units, provide governance foundations required for compliance frameworks like ISO 27001 and SOC 2, and establish accountability for security decisions and incident response actions.



.svg)
.svg)
.svg)