Most organizations implement authentication and access controls yet fail to prevent unauthorized access incidents that cascade into data breaches, regulatory penalties, and customer trust erosion. This gap reflects a fundamental misunderstanding: preventing unauthorized access requires continuous operational discipline across logical systems, physical infrastructure, and human behavior—not simply deploying authentication tools or conducting annual audits.
Unauthorized access represents one of the most consequential cybersecurity risks enterprises face. The following definition, real-world examples, compliance implications, and prevention framework demonstrate why treating unauthorized access as a foundational security concern—rather than an isolated technical problem—determines organizational resilience.
What Is "Unauthorized Access"?
Unauthorized access occurs when a person gains logical or physical access without permission to a network, system, application, data, or other resource, according to the National Institute of Standards and Technology (NIST). The term also encompasses any access that violates the stated security policy—meaning even legitimate users can commit unauthorized access by exceeding their authorized scope or privileges.
This definition establishes two critical dimensions: unauthorized access applies both to external attackers without any legitimate credentials and to internal actors who misuse their existing permissions. Organizations must defend against both threat vectors simultaneously.
What Counts as "Access"—Logical vs. Physical
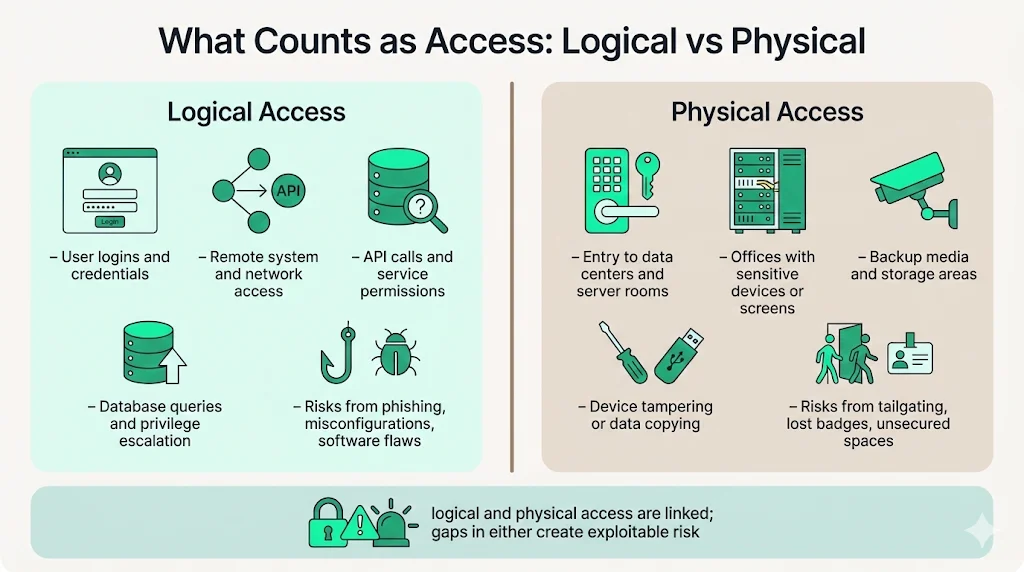
Unauthorized access manifests across two distinct categories requiring different controls:
Logical Access encompasses digital entry points: authentication via login credentials, remote system connections, network access from unauthorized devices, API calls exceeding granted permissions, database queries beyond authorized scope, or privilege escalation within applications. Logical access violations occur when attackers exploit software vulnerabilities, steal credentials through phishing, leverage misconfigured cloud resources, or bypass authentication mechanisms.
Physical Access includes unauthorized entry to facilities housing sensitive infrastructure: data centers, server rooms, offices containing unencrypted devices, storage areas with backup media, or spaces where employees handle confidential information. Physical unauthorized access enables attackers to directly manipulate hardware, install malicious devices, copy data from unattended systems, or observe credentials and sensitive information displayed on screens.
Both categories constitute unauthorized access under security frameworks and regulatory standards. Organizations neglecting physical security controls while investing exclusively in logical access protections create exploitable gaps—attackers frequently combine physical and logical attack vectors.
Why It Matters—Link to Core Security Goals (CIA Triad)
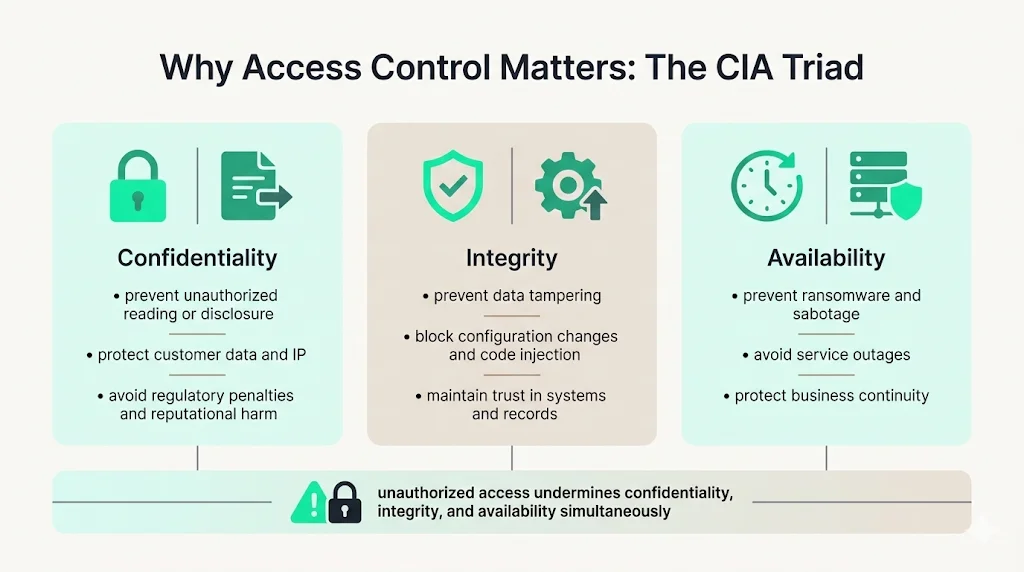
Data access can lead to a data breach when access is achieved or given to an unauthorized person or system. Within information security, preventing unauthorized access directly supports the CIA triad: confidentiality, integrity, and availability.
Confidentiality: Unauthorized access enables attackers to read, exfiltrate, or disclose sensitive information including customer data, intellectual property, financial records, trade secrets, and regulated data subject to GDPR, HIPAA, or other privacy laws. Once confidentiality is breached, organizations face regulatory penalties, competitive disadvantage, and reputational damage.
Integrity: Attackers gaining unauthorized access can modify data, alter system configurations, inject malicious code, manipulate financial records, or sabotage operational systems. Integrity violations undermine trust in organizational data and can produce cascading operational failures.
Availability: Unauthorized access frequently precedes denial-of-service attacks, ransomware deployment, system sabotage, or resource exhaustion that renders critical systems unavailable. Business continuity depends on preventing unauthorized actors from disrupting production environments.
Use Cases & Real-World Scenarios
Unauthorized access manifests through multiple attack patterns, each requiring distinct preventive controls.
1) External Cyberattacks
External threat actors exploit software vulnerabilities, misconfigured systems, weak authentication, and social engineering to gain unauthorized system access. In February 2024, Bank of America announced a breach that compromised the information of 57,028 customers through a ransomware group known as LockBit that accessed customer information through Infosys McCamish financial services software, a third-party vendor.
Attacks targeting authentication weaknesses, unpatched vulnerabilities, exposed APIs, or default credentials provide initial unauthorized access. Once inside perimeter defenses, attackers perform lateral movement, privilege escalation, and data exfiltration—transforming initial unauthorized access into comprehensive breaches affecting thousands or millions of records.
2) Insider Threats (Malicious or Accidental)
Employees, contractors, and third-party vendors with legitimate credentials represent significant unauthorized access risk when they exceed authorized privileges, misuse access for personal gain, or accidentally expose systems through negligence. Insider threats prove particularly difficult to detect because insiders possess valid credentials and familiarity with security controls.
Malicious insiders may exfiltrate intellectual property before departing for competitors, manipulate financial systems for fraud, sabotage infrastructure in retaliation for perceived grievances, or sell access credentials to external attackers. Accidental insider violations include accessing systems outside job responsibilities, misconfiguring permissions that expose sensitive data, or failing to follow security protocols that protect against unauthorized access.
3) Exploitation of Misconfigurations & Weak Controls
Misconfigured cloud storage buckets, overly permissive access control lists, open firewall ports, default passwords on administrative accounts, and inadequate network segmentation create unauthorized access opportunities that require no sophisticated attack techniques. Attackers continuously scan for these exposures using automated tools.
Organizations deploying cloud infrastructure without implementing least-privilege principles frequently discover publicly accessible databases, storage buckets containing customer data, or administrative interfaces exposed to the internet. These misconfigurations represent preventable unauthorized access vectors resulting from insufficient security rigor during implementation.
4) Non-Digital / Physical Scenarios
Unauthorized physical entry to facilities enables attackers to bypass network security controls entirely. Physical access to data centers, server rooms, or offices allows attackers to directly manipulate hardware, install keyloggers or network taps, boot systems from external media to extract data, photograph sensitive documents, or observe credentials entered by legitimate users.
Physical unauthorized access also includes tailgating behind authorized personnel, exploiting inadequate visitor management, accessing facilities during off-hours when security presence diminishes, or social engineering building management to grant access under false pretenses. Organizations investing heavily in logical security while neglecting physical access controls create exploitable vulnerabilities.
5) Consequences for Enterprises
Unauthorized access incidents produce immediate and long-term organizational damage:
Data theft and intellectual property loss directly impact competitive positioning. Stolen customer lists, proprietary algorithms, product roadmaps, pricing strategies, or research data benefit competitors and eliminate market advantages developed through years of investment.
Financial fraud and theft occur when attackers gain unauthorized access to payment systems, manipulate transactions, redirect funds, or steal payment card information for resale. Financial system compromises produce direct monetary losses and trigger extensive forensic investigation costs.
System sabotage and service disruption affect business continuity when unauthorized actors delete critical data, deploy ransomware, manipulate operational systems, or overwhelm resources. Downtime costs escalate rapidly for enterprises dependent on real-time systems serving customers or managing production environments.
Reputational damage and customer trust erosion represent the silent but substantial cost of unauthorized access incidents. Enterprise customers evaluating vendors scrutinize security posture and incident history—significant breaches eliminate vendors from consideration regardless of product quality or pricing.
How Unauthorized Access Relates to Data Breaches & Compliance
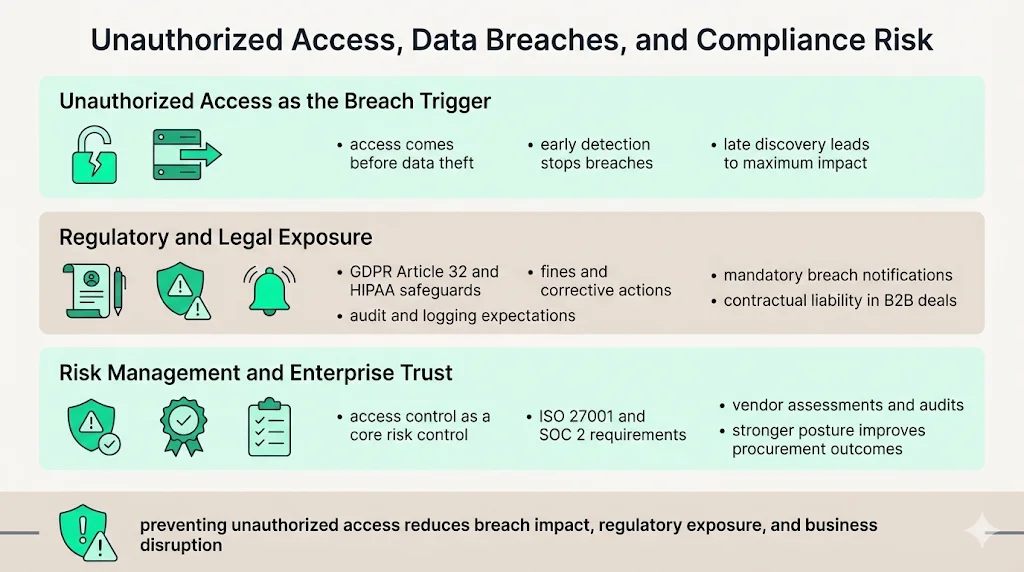
1) Unauthorized Access as a Root Cause of Data Breaches
A data breach occurs when unauthorized individuals gain access to confidential data stored in organizational systems. Unauthorized access represents the mechanism through which most data breaches occur—attackers must first gain unauthorized system access before they can locate, copy, and exfiltrate protected information.
This sequence matters for incident response: organizations detecting unauthorized access attempts early can prevent progression to data breaches. Conversely, organizations discovering unauthorized access only after data exfiltration occurs face maximum regulatory penalties, notification obligations, and reputational damage.
2) Regulatory and Legal Risk for Enterprises
Compliance frameworks and data protection regulations explicitly require organizations to prevent unauthorized access to sensitive data. GDPR Article 32 mandates "appropriate technical and organizational measures" to ensure security, specifically referencing protection against unauthorized processing. HIPAA Security Rule requires administrative, physical, and technical safeguards preventing unauthorized access to electronic protected health information (ePHI).
This incident highlights the critical importance of data security in financial services, where organizations handle vast amounts of sensitive customer data. Regulatory investigations following unauthorized access incidents examine whether organizations implemented required controls, conducted regular risk assessments, maintained audit logs, and responded appropriately when unauthorized access was detected.
Penalties for unauthorized access incidents resulting from inadequate controls include substantial fines, mandatory corrective action plans, ongoing monitoring by regulators, and in severe cases, suspension of operations or loss of certifications required to operate in regulated industries. Beyond regulatory penalties, unauthorized access triggers breach notification obligations—requiring organizations to inform affected individuals, regulatory bodies, and in some jurisdictions, the public.
For B2B enterprises, unauthorized access incidents create contractual liability when customer data is compromised. Enterprise service agreements typically include security representations, indemnification clauses, and termination rights triggered by security incidents—making unauthorized access a business continuity threat beyond regulatory compliance.
3) Role in Risk Management & Security Posture
Preventing unauthorized access constitutes foundational risk management. Organizations demonstrating robust unauthorized access prevention—through documented controls, regular testing, continuous monitoring, and incident response capabilities—reduce likelihood and impact of security incidents across multiple risk categories.
Security frameworks including ISO 27001, SOC 2, and NIST Cybersecurity Framework emphasize access control as a critical control domain. ISO 27001 Annex A includes multiple access control requirements covering user access management, user responsibilities, system and application access control, and physical access control. SOC 2 Trust Services Criteria address logical and physical access controls as fundamental to achieving security, availability, and confidentiality objectives.
Enterprise customers conducting vendor risk assessments evaluate unauthorized access prevention capabilities through questionnaires, audits, and penetration testing results. Demonstrable control effectiveness—evidenced through certifications, third-party assessments, and documented security operations—differentiates vendors in competitive procurement processes.
Prevention & Mitigation: Best Practices for Enterprises
Preventing unauthorized access requires layered controls addressing authentication, authorization, monitoring, configuration management, and organizational culture.
1) Strong Access Control & Authentication Policies
Implement password complexity requirements exceeding minimum standards: 14+ character passwords combining uppercase, lowercase, numbers, and special characters. Prohibit password reuse across systems and enforce 90-day rotation for privileged accounts. Eliminate default credentials on all systems, applications, and network devices—default credentials represent the most exploited unauthorized access vector.
Deploy multifactor authentication (MFA) universally, particularly for administrative access, remote access, and systems handling sensitive data. MFA dramatically reduces unauthorized access risk by requiring attackers to compromise multiple independent factors—significantly increasing attack difficulty and cost.
2) Least-Privilege & Role-Based Access Control (RBAC)
Assign minimum permissions necessary for users to perform job functions. Implement role-based access control mapping organizational roles to specific system permissions, then assign users to roles rather than granting individual permissions. This approach scales effectively across large organizations while maintaining audit trails showing permission rationale.
Conduct quarterly access reviews verifying that current permissions align with current job responsibilities. Remove access immediately upon role changes, terminations, or contract completions. Dormant accounts with valid credentials represent high-risk unauthorized access vectors—automated deprovisioning eliminates this exposure.
3) Continuous Monitoring & Logging
Implement security information and event management (SIEM) systems aggregating logs from authentication systems, network devices, applications, databases, and cloud platforms. Configure alerting for unauthorized access indicators: failed authentication attempts exceeding thresholds, access from unusual geographic locations, privilege escalation attempts, access during off-hours, or anomalous data access patterns.
Retain logs for a minimum 12 months supporting forensic investigations and compliance requirements. Protect log integrity through write-once storage or cryptographic signing—attackers gaining unauthorized access frequently attempt log deletion to conceal activity.
4) Secure Configuration & Patch Management
Maintain vulnerability management programs identifying, prioritizing, and remediating security vulnerabilities within defined service-level agreements. Critical vulnerabilities in internet-facing systems require remediation within 15 days; high-severity vulnerabilities within 30 days.
Implement configuration management ensuring systems deploy with secure baseline configurations: disable unnecessary services, close unused ports, remove default accounts, enable security logging, and enforce encryption for data at rest and in transit. Conduct quarterly configuration audits detecting drift from approved baselines.
5) Endpoint Security & Network Segmentation
Deploy endpoint detection and response (EDR) solutions on all devices accessing corporate networks. EDR tools detect and block unauthorized access attempts, malware execution, lateral movement, and data exfiltration attempts originating from compromised endpoints.
Segment networks isolating production systems from development environments, separating systems by sensitivity level, and restricting lateral movement between network segments. Network segmentation limits unauthorized access impact—attackers compromising one segment cannot automatically pivot to access more sensitive systems.
6) Regular Security Testing & Vulnerability Assessments
Conduct annual penetration testing by qualified third parties simulating unauthorized access attempts against external and internal systems. Penetration testing identifies exploitable vulnerabilities that automated scanning misses—particularly logic flaws, business process vulnerabilities, and complex attack chains.
Implement continuous vulnerability scanning supplemented by quarterly manual assessments. Automated scanning identifies known vulnerabilities; manual assessments evaluate misconfigurations, weak access controls, and architectural security weaknesses enabling unauthorized access.
7) Employee Training & Insider Threat Awareness
Deliver security awareness training quarterly addressing phishing recognition, social engineering tactics, password security, physical security protocols, and data handling requirements. Tailor training to role-specific risks: developers receive secure coding training; administrators receive privileged access management training; executives receive targeted attack awareness.
Implement insider threat programs monitoring for unauthorized access indicators: unusual data access patterns, excessive file downloads, access to systems outside job scope, or behavioral changes correlating with security policy violations. Balance monitoring with privacy considerations and transparency about monitoring scope and purpose.
Enterprise Compliance Relevance
Why Enterprises (Selling to Other Enterprises) Should Care
Enterprise buyers incorporate security requirements into vendor selection criteria, contract terms, and ongoing vendor risk management. Organizations demonstrating inadequate unauthorized access prevention fail vendor assessments, lose competitive opportunities, or face contract termination following security incidents.
Financial services firms, healthcare organizations, government contractors, and regulated industries mandate specific security certifications—SOC 2 Type II, ISO 27001, FedRAMP, or HITRUST—as prerequisites for vendor consideration. These certifications require documented unauthorized access prevention controls, regular testing, continuous monitoring, and incident response capabilities. Achieving and maintaining certifications requires 400-600 annual hours without managed service support—organizations lacking resources to maintain compliance lose market access.
Building Trust & Adding Value as a Vendor / Service Provider
Security posture differentiation influences purchase decisions when product functionality and pricing achieve parity. Demonstrating robust unauthorized access prevention through third-party certifications, transparent security documentation, customer-controlled security assessments, and proactive security communication positions vendors as low-risk partners.
Enterprise customers evaluate vendor security maturity during due diligence through questionnaires, on-site audits, architecture reviews, and penetration testing results. Organizations articulating comprehensive unauthorized access prevention strategies—backed by documented controls, regular testing, and measurable security metrics—accelerate sales cycles and command premium pricing reflecting reduced customer risk.
Legal and Regulatory Obligations (Depending on Geography, Industry)
Organizations processing European Economic Area resident data must comply with GDPR requirements preventing unauthorized access to personal data. GDPR Article 5 establishes integrity and confidentiality principles requiring "appropriate security of the personal data, including protection against unauthorized or unlawful processing."
Healthcare organizations subject to HIPAA must implement safeguards preventing unauthorized access to protected health information. HIPAA Security Rule specifies administrative safeguards (security management processes, workforce security, information access management), physical safeguards (facility access controls, workstation security, device and media controls), and technical safeguards (access control, audit controls, integrity controls, transmission security).
Payment card industry organizations must achieve PCI DSS compliance requiring unauthorized access prevention through access control measures, network security controls, vulnerability management, and monitoring. Non-compliance results in increased transaction fees, audit requirements, or loss of payment processing capabilities—existential threats for commerce-dependent businesses.
Most organizations allocate substantial resources to authentication systems while underinvesting in access monitoring, privilege management, and continuous validation—producing security controls satisfying auditors without preventing determined attackers from gaining unauthorized access. Preventing unauthorized access requires operational discipline across technical controls, process enforcement, and organizational culture rather than deploying additional security products.
Organizations treating unauthorized access prevention as continuous operational discipline rather than annual compliance activity develop security postures that actually protect systems, data, and business operations. This approach produces compliance outcomes as natural byproducts of genuine security implementation—establishing credibility with enterprise customers, regulators, and auditors who increasingly distinguish between performative compliance and operational security.
FAQs
1) What constitutes unauthorized access?
Unauthorized access occurs when a person gains logical or physical access without permission to a network, system, application, data, or other resource. This includes both external attackers without legitimate credentials and internal users exceeding authorized privileges. Any access that violates the stated security policy constitutes unauthorized access regardless of whether the actor possesses valid credentials.
2) How do you prevent unauthorized access in your systems?
Prevention requires layered controls: strong authentication with multifactor authentication, least-privilege access control limiting permissions to job requirements, continuous monitoring detecting anomalous access patterns, regular patching addressing known vulnerabilities, network segmentation limiting lateral movement, endpoint security protecting devices, security testing identifying weaknesses, and employee training reducing social engineering effectiveness. No single control prevents unauthorized access—defense in depth combining multiple independent controls provides effective protection.
3) What are the legal implications of unauthorized access?
Unauthorized access triggering data breaches produces regulatory penalties under GDPR, HIPAA, CCPA, and sector-specific regulations. Organizations must notify affected individuals, regulatory authorities, and in some jurisdictions, media outlets—creating reputational damage beyond financial penalties. Contractual liabilities arise when customer data is compromised, potentially including indemnification obligations, service credits, or contract termination. Industries handling regulated data face heightened scrutiny: financial services organizations may face enforcement actions from multiple regulators; healthcare organizations risk civil monetary penalties and corrective action plans requiring ongoing monitoring.
4) How does unauthorized access relate to data breaches?
Unauthorized access represents the mechanism through which data breaches occur. Attackers must first gain unauthorized system access before locating and exfiltrating protected data. Organizations detecting unauthorized access attempts early can prevent progression to data breaches through incident response, containment, and remediation. Data breaches discovered after data exfiltration trigger maximum regulatory penalties, mandatory notifications, forensic investigation costs, and reputational damage—making early unauthorized access detection critical to minimizing breach impact.
5) What are best practices to avoid unauthorized access?
Implement strong authentication policies requiring complex passwords and multifactor authentication. Deploy role-based access control granting minimum necessary permissions and conduct quarterly access reviews. Maintain continuous monitoring with automated alerting for suspicious access patterns. Establish vulnerability management programs remediating security weaknesses within defined timeframes. Segment networks limiting lateral movement following initial compromise. Conduct regular penetration testing and vulnerability assessments identifying exploitable weaknesses. Deliver ongoing security awareness training addressing phishing, social engineering, and security policy requirements. Most importantly, treat unauthorized access prevention as continuous operational discipline rather than annual compliance activity—security controls must function effectively daily, not simply during audit periods.



.svg)
.svg)
.svg)