The Department of Defense developed Cloud Computing Impact Levels as a standardized way to classify information systems and data based on the level of protection they require. Organizations selling cloud services or IT solutions into defense, federal government, or enterprise markets with high security demands must understand this framework—it directly influences contract eligibility, security architecture, and operational overhead.
DoD Impact Levels map the sensitivity or confidentiality level of information to be stored and processed against the potential impact of an event that results in the loss of confidentiality, integrity, or availability of that information. This classification framework ensures vendors implement proportional security controls: handling public data requires fundamentally different infrastructure than protecting mission-critical national security systems.
This article defines the Impact Level framework, explains how each level (IL2, IL4, IL5, IL6) translates into specific security requirements, details the assessment criteria organizations use to select the appropriate IL, and outlines implementation considerations for enterprise vendors targeting government or high-security commercial clients.
What are DoD Impact Levels?
Established by the Defense Information Systems Agency (DISA), the DoD Cloud Computing Security Requirements Guide (CC SRG) outlines the IL framework. The framework classifies cloud systems and data based on damage potential from unauthorized disclosure, modification, or destruction. While the CC SRG originally defined six levels, IL1 and IL3 are effectively deprecated—commercial Cloud Service Providers (CSPs) focus on IL2, IL4, IL5, and IL6.
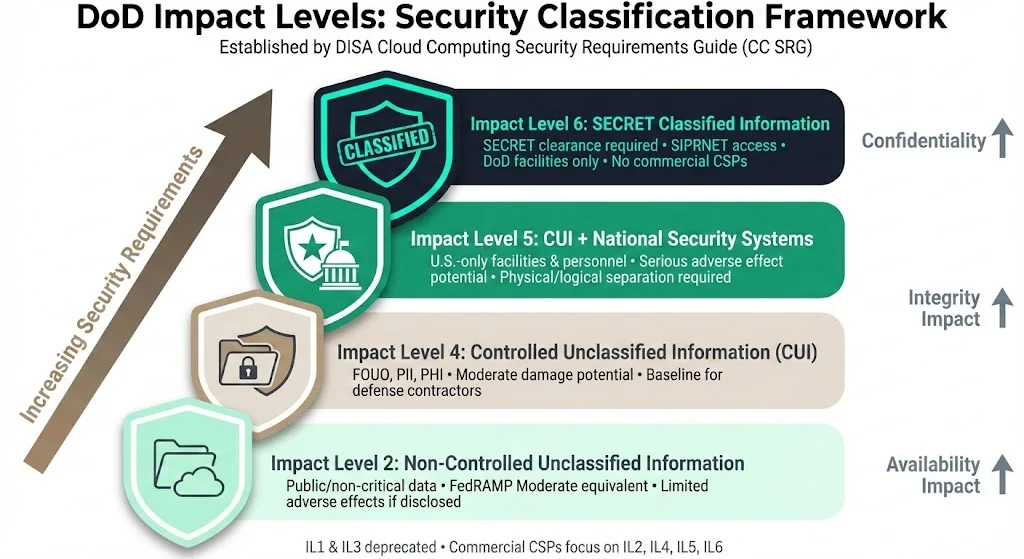
Impact Level 2 (IL2): Non-Controlled Unclassified Information
FedRAMP Moderate aligns with Impact Level 2, the lowest level of authorization under the CC SRG, applicable to CSOs that store, process or transmit publicly available or non-critical mission data. IL2 encompasses administrative data, internal communications, and non-sensitive documentation where unauthorized disclosure would have limited adverse effects. The baseline security requirements for IL2 are equivalent to those of FedRAMP Moderate; in 2019, DISA enabled DoD IL2 data to be hosted on CSOs authorized at the FedRAMP Moderate level without requiring additional written authorization.
Impact Level 4 (IL4): Controlled Unclassified Information
IL4 safeguards Controlled Unclassified Information (CUI), including FOUO, PII, and PHI, and necessitates advanced security controls to prevent unauthorized access. IL4 applies to non-national security systems handling CUI where compromise could cause moderate damage to organizational operations or mission effectiveness. This level represents the baseline for most defense contractors and enterprise vendors handling sensitive but unclassified data. IL4 requires more stringent personnel vetting, infrastructure controls, and monitoring than IL2.
Impact Level 5 (IL5): CUI and Unclassified National Security Information
Impact level 5 is used to host non-public, unclassified National Security System (NSS) system data or non-public, unclassified data where unauthorized disclosure could be expected to have a serious adverse effect on organizational operations, organizational assets, or individuals, including CUI and/or other mission data that may require a higher level of protection than that afforded by IL4. CSPs must comply with all IL4 controls and nine additional requirements specific to IL5: data must reside in U.S.-controlled facilities, and only U.S. citizens can access the systems and data. IL5 demands physical and logical separation of government data from non-government entities and requires systems to support continuity of operations during crises.
Impact Level 6 (IL6): Classified Information Up to SECRET
The Department of Defense's Impact Level 6 marks the highest security standard for managing classified information, designed to safeguard critical national security data, as a specialized framework for handling SECRET-level classified information systems. Data must be stored in U.S.-based facilities with access limited to U.S. citizens holding SECRET clearances, and external connectivity is mediated through the Secret Internet Protocol Network (SIPRNET). Commercial providers are not authorized to host IL6 data. IL6 requires dedicated, isolated infrastructure within highly secure DoD facilities.
The progression from IL2 to IL6 reflects escalating security demands across three dimensions: confidentiality levels (from public to SECRET-classified), integrity impact (from administrative accuracy to mission-critical precision), and availability impact (from routine operations to national security continuity). Each IL increase imposes additional requirements for personnel clearance, hosting location, tenant isolation, and control implementation—translating directly into architectural complexity and operational cost.
The assessment criteria & risk analysis behind Impact Levels
The DoD mission owner—the agency, unit, or organization sponsoring the system—defines the required Impact Level based on the sensitivity of the data and the mission's operational needs. This determination follows structured risk analysis using FIPS 199 standards and the Committee on National Security Systems Instruction (CNSSI) 1253, which provide frameworks for categorizing information systems based on security objectives.
Assessment criteria include:
- Information sensitivity: What classification or control marking applies to the data? Public information, CUI with specific markings (such as For Official Use Only, Controlled Technical Information, or Law Enforcement Sensitive), unclassified national security information, or classified data up to SECRET each map to different ILs.
- Damage potential: What operational, mission, or national security consequences would result from unauthorized disclosure, modification, or destruction? A breach of publicly releasable data causes reputational harm; compromise of mission-critical CUI degrades operational effectiveness; exposure of national security systems undermines strategic capabilities.
- Integrity impact: How critical is data accuracy and completeness to mission success? Administrative records tolerate higher error rates than targeting coordinates or intelligence assessments. Systems requiring high integrity assurance—where unauthorized modification could cause serious mission failure—demand IL5 or IL6.
- Availability impact: What is the acceptable downtime or degradation threshold? Routine administrative systems can tolerate interruptions; command-and-control systems supporting combat operations cannot. High availability requirements, especially for national security systems, drive organizations toward IL5 or IL6 with their continuity-of-operations mandates.
Risk analysis synthesizes these factors: if the system processes CUI related to weapons systems development and compromise would severely degrade defense capabilities, the mission owner specifies IL4 or IL5 depending on whether the system qualifies as a National Security System. If the data includes classified operational plans, IL6 becomes mandatory regardless of other considerations.
System security requirements scale proportionally with IL designation. IL2 demands approximately 325 security controls aligned with FedRAMP Moderate; IL4 adds DoD-specific controls for CUI protection; IL5 authorization requires meeting over 450 of the strictest security requirements; IL6 imposes the full complement of controls for classified systems. Vendors must architect solutions accordingly—network segmentation, encryption standards, access control mechanisms, audit logging, incident response protocols, and supply chain risk management all intensify as IL increases.
How DoD Impact Levels support data protection standards
The IL framework operationalizes data protection by translating abstract security principles into concrete, auditable requirements. Organizations gain four strategic advantages:
1) Clear confidentiality baselines: By classifying data into Impact Levels, organizations establish explicit confidentiality thresholds. Teams understand which data requires basic access controls (IL2) versus which demands multi-factor authentication, U.S.-citizen-only access, and physical isolation (IL5/IL6). This clarity prevents both over-investment in low-risk data and under-protection of sensitive information.
2) Mandatory control implementation: Each IL specifies required security controls derived from NIST SP 800-53. These controls address access control, audit and accountability, configuration management, identification and authentication, incident response, system and communications protection, and 15 other control families. Vendors cannot selectively implement convenient controls while ignoring expensive ones—the IL designation mandates a comprehensive baseline, ensuring consistent protection across confidentiality, integrity, and availability dimensions.
3) Framework interoperability: CSPs can use FedRAMP baselines or even draw on their existing FedRAMP ATO to reduce their assessment package workload, as long as they add the controls and parameters in Appendix D of the CSP SRG. This reciprocity allows organizations to build layered compliance: achieve FedRAMP Moderate as a foundation, then increment to IL4 for CUI handling, then IL5 for national security systems. Rather than rebuilding architectures from scratch, vendors extend existing frameworks.
4) Risk-proportional resource allocation: The IL framework helps organizations allocate security spending rationally. Public-facing applications with no CUI justify IL2 investments (approximately 325 controls, achievable with commercial cloud infrastructure). Defense contractor collaboration platforms handling CUI require IL4 (additional controls for CUI marking, handling, and transmission). Mission-critical intelligence systems demand IL5 (U.S.-only personnel, dedicated facilities, enhanced monitoring). This tiered approach prevents the dual failures of under-securing sensitive systems and over-securing routine data.
For enterprise vendors targeting government or highly regulated commercial clients, IL alignment provides competitive differentiation. A vendor with IL4 Provisional Authorization can credibly state: "We implement the 400+ security controls required for CUI protection under DISA Cloud Computing Security Requirements Guide, including enhanced access control, incident response, and supply chain risk management specific to defense applications." This specificity builds trust with procurement teams evaluating vendor security posture.
5) Vendors can architect modular offerings: an IL2-compliant platform handles routine collaboration; an IL4 instance supports CUI workflows for defense contractors; an IL5 environment serves national security missions. This tiering allows vendors to capture multiple market segments while managing the cost differential—IL5 infrastructure requires 60-80% more investment than IL2 due to personnel clearance, facility requirements, and enhanced controls.
The IL framework inherently supports data protection standards by anchoring security requirements to risk. Confidentiality protections scale with classification level; integrity controls intensify with mission criticality; availability requirements increase with operational dependencies. Organizations implementing IL-aligned architectures demonstrate not just compliance with DoD standards, but adherence to fundamental data protection principles applicable across regulatory regimes.
Implementation considerations for enterprise vendors
Organizations pursuing DoD contracts or serving enterprise clients with defense-related data requirements must systematically align their offerings with Impact Levels. The implementation process follows this sequence:

1) Data classification and IL determination:
Catalog all data types your system will process, store, or transmit. Apply CUI marking guidelines from NIST SP 800-171 and defense-specific classification guides. Determine whether any data qualifies as national security information. Map data sensitivity to preliminary IL: public/routine data suggests IL2; CUI indicates IL4; mission-critical CUI or national security data requires IL5; classified information demands IL6. Engage potential DoD customers early—mission owners make final IL determinations, and misalignment causes costly rework.
2) Control gap analysis and remediation:
Compare current security controls against the target IL baseline. DISA issued guidance that the Cloud Computing SRG is transitioning from NIST 800-53 Rev 4 to NIST 800-53 Rev 5. Organizations must implement Rev 5 controls, which include updated requirements for supply chain risk management, enhanced incident response, and strengthened configuration management. Identify control gaps—common deficiencies include insufficient audit logging, inadequate encryption for data at rest and in transit, missing continuous monitoring capabilities, and insufficient supply chain visibility. Prioritize remediation of high-impact gaps: access control failures create immediate vulnerability; documentation deficiencies delay authorization but don't compromise security.
3) Infrastructure and personnel requirements:
All personnel with access to DoD data must undergo background checks and security clearances commensurate with the impact level; non-US citizens are generally not permitted to access data at IL4 and above. For IL2, basic background checks suffice; IL4 requires citizenship verification and favorable background investigations; IL5 demands U.S. citizenship and clearance eligibility; IL6 requires active SECRET clearances for all personnel with system access.
Infrastructure location becomes critical at higher ILs: IL2 and IL4 tolerate commercial data centers within U.S. boundaries; IL5 and IL6 require dedicated DoD or federal facilities. Vendors pursuing IL5/IL6 must either operate within DoD-managed infrastructure or invest in purpose-built facilities meeting stringent physical security requirements—armed guards, biometric access controls, TEMPEST shielding, and continuous surveillance.
4) Authorization process:
To deploy at IL4 or higher, cloud service providers must obtain a DoD Provisional Authorization (PA) from DISA. The PA process requires: comprehensive System Security Plan documenting all implemented controls; Security Assessment Report from a DoD-recognized Third Party Assessment Organization (3PAO); Plan of Action and Milestones addressing any control deficiencies; continuous monitoring plan demonstrating ongoing security posture visibility. Achieving IL6 compliance is a complex, time-consuming process that can take months or even years, depending on system complexity and associated risk levels. IL4 typically requires 6-9 months from assessment initiation to PA issuance; IL5 extends to 12-18 months given personnel clearance timelines and enhanced control validation.
5) Operational adjustments:
Update incident response procedures to meet DoD reporting timelines—most incidents involving CUI require notification within hours, not days. Implement continuous monitoring and diagnostics meeting DISA requirements for vulnerability scanning frequency, log aggregation, and security information correlation. Adjust vendor and supply chain management: components in IL5/IL6 systems require provenance verification and often domestic sourcing to mitigate supply chain risk.
6) Common implementation pitfalls:
- IL inflation expectations: Enterprise clients sometimes demand IL5 capability for workloads that genuinely require only IL4. Vendors must educate customers on the significant cost differential—IL5 implementations typically cost 2-3x IL4 equivalents due to personnel clearance, facility requirements, and enhanced controls. Propose IL4 for standard CUI workflows, reserving IL5 for confirmed national security systems.
- Underestimating personnel requirements: All personnel with access to DoD data must undergo background checks and security clearances commensurate with the impact level. Background investigations for IL5 clearance eligibility take 6-12 months; SECRET clearances for IL6 require 12-18 months. Organizations pursuing higher ILs must staff with pre-cleared personnel or accept extended timelines.
- Scope creep during implementation: Initial assessments often identify 20-40 control deficiencies requiring remediation. Organizations underestimate the architectural changes required—implementing proper tenant isolation for IL5 might require complete infrastructure redesign, not just configuration adjustments. Budget 30-40% contingency for scope expansion during remediation.
- Communication gaps with mission owners: Vendors sometimes build to a target IL without confirming the mission owner's actual requirements. The mission owner makes the final IL determination—vendors who assume IL4 suffices, then discover the customer needs IL5, face complete re-architecture. Engage DoD customers before committing to infrastructure investments.
7) Sales and marketing integration:
Articulate IL capability clearly in enterprise sales materials: "Our platform holds DoD Impact Level 4 Provisional Authorization, enabling defense contractors and enterprises to process, store, and transmit Controlled Unclassified Information in compliance with NIST SP 800-171 and DFARS 252.204-7012 requirements." Specify control domains covered: access control, incident response, system and communications protection, configuration management. Quantify the compliance value: "Our IL4 authorization eliminates 400+ control implementation and assessment requirements for defense contractors, reducing your compliance timeline from 12-18 months to 60-90 days for system-specific authorization."
For vendors serving multiple market segments, position IL tiers as capability statements: "Our IL2 environment supports routine government collaboration; our IL4 infrastructure enables CUI workflows for defense industrial base members; our roadmap includes IL5 capability for customers with national security system requirements." This messaging demonstrates security maturity while managing customer expectations about capability boundaries and cost structures.
Conclusion
DoD Impact Levels translate abstract data sensitivity classifications into concrete security and infrastructure requirements. The framework establishes clear thresholds: IL2 for public and routine data, IL4 for Controlled Unclassified Information, IL5 for mission-critical national security systems, IL6 for classified data up to SECRET. Each level specifies mandatory controls addressing confidentiality, integrity, and availability proportional to damage potential from compromise.
Organizations selling into defense, federal government, or enterprise markets with high security demands must understand IL distinctions. Defense contractors cannot participate in programs involving CUI without IL4-compliant infrastructure; vendors supporting national security missions require IL5 capability; classified work demands IL6. The authorization process, personnel requirements, and infrastructure investments scale significantly across ILs—IL5 implementations typically require 2-3x the investment of IL4, driven by U.S.-citizen-only staffing, dedicated facilities, and 450+ security controls.
Assess your current security posture against IL requirements. If you handle or plan to handle CUI for defense customers, begin IL4 remediation now—the 6-9 month authorization timeline delays contract execution. Map your data classification to appropriate ILs, identify control gaps, budget for infrastructure and personnel requirements, and engage potential DoD customers to confirm IL alignment before committing to implementation. Organizations that align early gain competitive advantage in defense and high-security enterprise markets; those that defer IL compliance face contract ineligibility and costly re-architecture.
FAQs
1) What are the different levels of clearance for DoD?
The U.S. government maintains three primary personnel security clearance levels: Confidential, Secret, and Top Secret. These clearances authorize individuals to access classified national security information at corresponding classification levels. Confidential clearance (the lowest tier) permits access to information whose unauthorized disclosure could damage national security; Secret clearance covers information whose disclosure could cause serious damage; Top Secret clearance (the highest tier) applies to information whose compromise could cause exceptionally grave damage to national security.
Clearance levels directly connect to DoD Impact Levels for system authorization. IL6 systems handling SECRET-classified data require all personnel with system access—administrators, developers, operators—to hold active SECRET clearances. IL5 systems typically require U.S. citizenship and clearance eligibility (favorable background investigation) even when processing unclassified national security information. IL4 requires U.S. citizenship verification but not formal clearances, since CUI remains unclassified. IL2 imposes no clearance requirements beyond basic background checks. Organizations pursuing higher Impact Levels must either hire pre-cleared personnel or accept 12-18 month timelines for SECRET clearance processing, significantly affecting staffing costs and project schedules.
2) What are the different levels of DoD 8570?
DoD Directive 8570.01 (now superseded by DoD 8140, though "8570" remains common shorthand) established the Information Assurance Workforce Improvement Program, defining certification requirements for cybersecurity personnel. The framework specifies three primary categories with multiple levels each:
- Information Assurance Technical (IAT): Personnel implementing, maintaining, and operating information systems. IAT Level I requires Security+ or equivalent certification for help desk and support roles; IAT Level II requires Security+ CE or CCNA Security for security administrators; IAT Level III demands CASP+ or CISA for senior security engineers and architects.
- Information Assurance Management (IAM): Personnel managing and overseeing information assurance functions. IAM Level I requires Security+ CE or GSLC for junior IA managers; IAM Level II requires CAP or CISM for program-level IA managers; IAM Level III demands CISM or CISSP-ISSMP for senior leadership positions.
- Cyber Service Provider (CSSP): Specialized roles including incident responders, auditors, and analysts. CSSP categories include Infrastructure Support, Incident Responder, Auditor, and Forensics Analyst, each with specific certification requirements such as CEH, GCIH, GCIA, or CISA depending on role.
DoD 8570/8140 requirements intersect with Impact Level implementations by defining minimum qualifications for personnel operating IL-compliant systems. An IL5 environment requires not just U.S. citizenship and clearance eligibility, but also appropriately certified cybersecurity personnel—typically IAT Level II minimum for system administrators, IAT Level III for security engineers, and IAM Level II for security program managers. Vendors pursuing DoD Provisional Authorizations must staff programs with personnel holding both required certifications and appropriate clearances, compounding the personnel cost and availability challenges at higher Impact Levels.
3) What are the FedRAMP impact levels?
FedRAMP (Federal Risk and Authorization Management Program) classifies Cloud Service Offerings into three impact levels based on FIPS 199 categorization: Low, Moderate, and High. These levels reflect the potential impact to federal operations, assets, or individuals if confidentiality, integrity, or availability of the system is compromised.
- FedRAMP Low: Applies to cloud systems processing publicly available data or information with minimal impact from compromise. Low-impact systems implement approximately 125 security controls. Examples include public-facing websites and general collaboration tools with no sensitive data.
- FedRAMP Moderate: Addresses systems with moderate-impact data—unauthorized disclosure could have serious adverse effects on operations or individuals. Moderate baseline requires approximately 325 security controls. Most federal cloud deployments target FedRAMP Moderate, covering applications handling personally identifiable information, financial data, or operational information.
- FedRAMP High: Applies to systems with high-impact data whose compromise could cause severe or catastrophic damage to agency operations or mission capabilities. High baseline demands approximately 421 security controls with enhanced rigor for access control, encryption, monitoring, and incident response.
DoD Impact Levels build upon FedRAMP foundations: IL2 aligns with FedRAMP Moderate, sharing the 325-control baseline with DoD-specific additions; IL4 and IL5 align approximately with FedRAMP High but include DoD-specific controls for CUI handling, national security systems, and enhanced supply chain risk management; IL6 exceeds FedRAMP High by addressing classified information requirements. The reciprocity between frameworks allows vendors to leverage FedRAMP authorizations as starting points for DoD Impact Level authorizations, reducing assessment burden—a FedRAMP Moderate authorization provides approximately 80% of requirements for IL2; FedRAMP High covers roughly 70% of IL4 requirements. Vendors serving both civilian federal agencies and DoD benefit from pursuing FedRAMP authorizations first, then incrementally adding DoD-specific controls for Impact Level compliance.
4) What are the levels of CMMC?
The Cybersecurity Maturity Model Certification (CMMC) version 2.0 establishes cybersecurity standards for the Defense Industrial Base, protecting Controlled Unclassified Information in the defense supply chain. CMMC 2.0 (the current framework, distinct from the original five-level version) defines three levels of cybersecurity hygiene and compliance:
- CMMC Level 1 (Foundational): Addresses basic cyber hygiene through 17 practices aligned with FAR 52.204-21 requirements. Level 1 applies to contractors handling Federal Contract Information (FCI)—information provided by or generated for the government under contract, but not intended for public release. Level 1 requires annual self-assessment without third-party validation.
- CMMC Level 2 (Advanced): Implements 110 security practices from NIST SP 800-171, addressing Controlled Unclassified Information protection. Level 2 applies to contractors processing, storing, or transmitting CUI—the vast majority of defense contractors fall into this category. Organizations must conduct annual self-assessments; DoD may require third-party assessment for high-priority programs.
- CMMC Level 3 (Expert): Adds requirements from NIST SP 800-172 (Enhanced Security Requirements for CUI) to the 110 practices of Level 2, totaling approximately 130 practices. Level 3 applies to contractors supporting programs with advanced persistent threat risk or handling the most sensitive CUI. Level 3 requires triennial third-party assessment by CMMC Third Party Assessment Organizations (C3PAOs).
CMMC and DoD Impact Levels address related but distinct aspects of defense cybersecurity. CMMC applies to defense contractors' internal networks and systems handling FCI or CUI—the contractor's own infrastructure. DoD Impact Levels apply to cloud service providers and systems hosted for DoD use. A defense contractor might require CMMC Level 2 for their internal engineering systems while also needing access to a cloud platform with IL4 authorization for collaboration with government customers. Contractors supporting national security programs might need both CMMC Level 3 for their internal systems and access to IL5 cloud infrastructure for mission-critical applications. Both frameworks reflect increasing security maturity and control rigor, and both impose significant compliance costs—CMMC Level 3 assessment and maintenance typically costs $75,000-150,000 annually; IL5 Provisional Authorization for a cloud service requires $500,000-1,000,000+ investment depending on architecture complexity.



.svg)
.svg)
.svg)