Most organizations treat network security as a series of discrete application-layer controls, overlooking the foundation of secure data transport at the network layer. This oversight becomes apparent when data traverses untrusted networks—where unencrypted packets expose sensitive information to interception, manipulation, and unauthorized access. Encapsulating Security Payload (ESP) is a fundamental component of the IPsec protocol suite, used to secure IPv4 and IPv6 communications by authenticating and encrypting each IP packet in a communication session. Understanding ESP becomes critical in 2026 as enterprises confront an expanding threat landscape driven by IoT proliferation, increased regulatory scrutiny around data protection, and the complexity of securing distributed edge environments. This definition clarifies what ESP is, how it integrates with compliance frameworks, and the technical considerations enterprises must address when implementing network-layer encryption across diverse device fleets.
What is ESP? (in Cybersecurity)
ESP or Encapsulating Security Payload is an individual protocol in IPsec, responsible for the CIA triad of security (Confidentiality, Integrity, Availability), which is considered significant only when encryption is carried along with them. Encapsulating Security Payload (ESP) provides confidentiality, connectionless data integrity, data origin authentication, an anti-replay service (a form of partial sequence integrity), and limited traffic-flow confidentiality. The Encapsulating Security Payload operates as an IPsec protocol identified by IP protocol number 50, functioning by adding both a header and trailer to an IP packet, creating a secure envelope around the original payload data.
The distinction between ESP and its sibling protocol Authentication Header (AH) centers on encryption capability. Unlike its counterpart, the Authentication Header (AH), ESP provides confidentiality, data integrity, and origin authentication for IP packets through robust encryption mechanisms, while AH only provides integrity and authentication. This difference renders AH largely obsolete in modern implementations—encryption without authentication exposes systems to cut-and-paste cryptographic attacks, while authentication without encryption leaves data readable to any network observer.
ESP operates in two distinct modes that enterprises must understand when architecting secure network architectures. In transport mode, only the payload of the IP packet is usually encrypted or authenticated. In tunnel mode, the entire IP packet is encrypted and authenticated, then encapsulated into a new IP packet with a new IP header. Tunnel Mode encrypts and authenticates the entire original IP packet, encapsulating it within a new IP header, enabling gateway-to-gateway communications and supporting complex network topologies, and represents the standard implementation for site-to-site VPN connections and remote access scenarios.
Clarifying terminology: "ESP" refers exclusively to Encapsulating Security Payload. "EPS" does not exist as a standard cybersecurity acronym and likely represents a mis-term. "CSP" means Cloud Service Provider in most enterprise contexts, bearing no relation to ESP. Some compliance frameworks use "ESP" to mean External Service Provider, but that usage applies to vendor management contexts, not network encryption protocols.
Why ESP Matters for Enterprise Cybersecurity
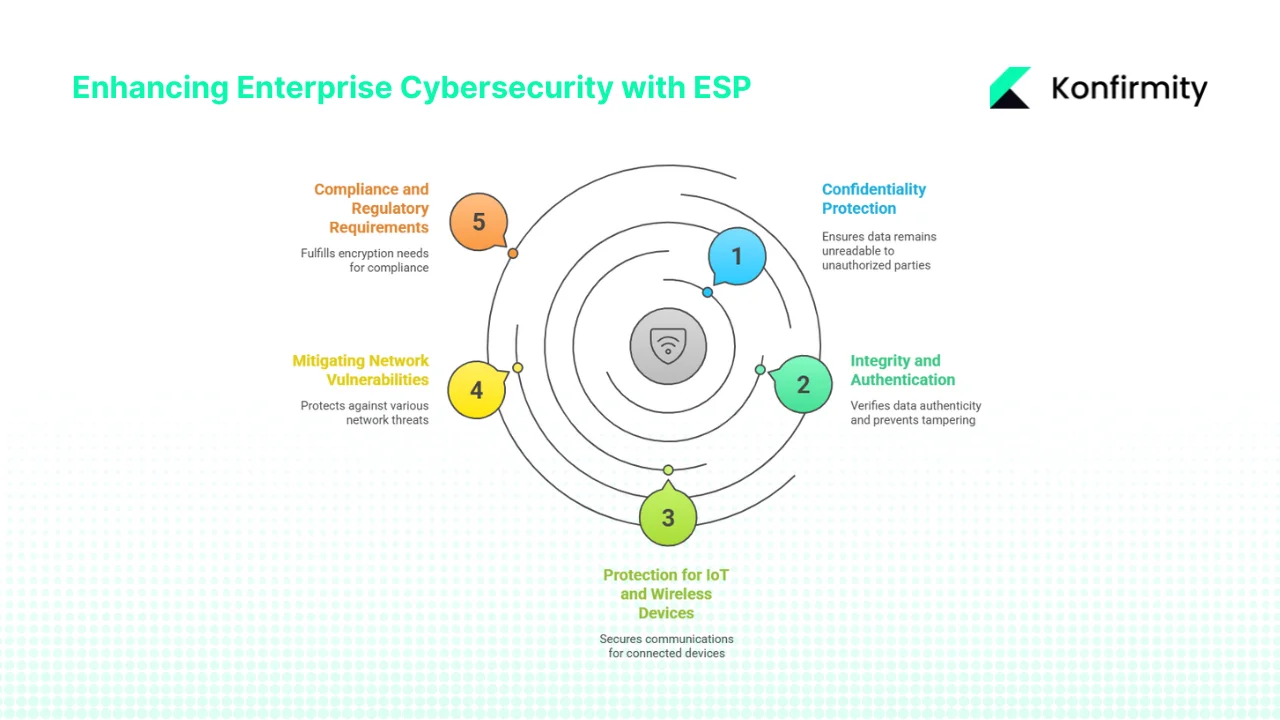
1. Confidentiality Protection
- Key Feature: The primary security contribution of ESP is confidentiality.
- How it works: ESP uses symmetric-key encryption algorithms, like Advanced Encryption Standard (AES), to encrypt payload data.
- Benefits: This ensures that even if data packets are intercepted, their contents remain unreadable to unauthorized parties.
- Scope: The encryption protects all data traveling through enterprise networks, whether it's between branch offices, remote workers, or IoT devices in industrial settings.
2. Integrity and Authentication
- Verifying Data: ESP addresses a crucial security need—ensuring that data is both authentic and unaltered.
- Mechanism: ESP uses cryptographic hash functions, such as Hash-based Message Authentication Code (HMAC), to detect any changes to packet data.
- Authentication: ESP confirms that network endpoints have valid credentials before establishing secure sessions, which is critical for device authentication frameworks.
3. Protection for IoT and Wireless Devices
- Expanding IoT: ESP is vital for enterprises deploying large numbers of connected devices, such as sensors and medical devices.
- Security Layer: ESP secures communications at the network layer for devices that may lack strong application-layer security.
- Outcome: It creates a protective layer for vulnerable IoT endpoints, ensuring they are encrypted and authenticated.
4. Mitigating Network Vulnerabilities
- Increased Attack Surfaces: As enterprises adopt cloud, remote access, and edge computing, the attack surface grows.
- Threat Mitigation: ESP helps protect against various network threats, such as eavesdropping, packet injection, replay attacks, and man-in-the-middle attacks.
- Replay Protection: It uses a monotonically increasing sequence number for each packet to prevent replay attacks, with a separate counter for each security association.
5. Compliance and Regulatory Requirements
- Encryption Mandates: Various security frameworks require encryption of data in transit.
- Key Regulations: Standards such as ISO 27001, NIST SP 800-53, GDPR Article 32, and HIPAA all have encryption requirements.
- ESP's Role: ESP fulfills these encryption needs at the network layer, providing clear, auditable evidence of cryptographic protection for compliance assessments.
ESP and Compliance — What Enterprise Sellers Should Know
ISO 27001:2022 requires organizations to establish cryptographic controls (Annex A 8.24) covering encryption of information in transit across networks. ESP implementations provide documented evidence that data traversing untrusted networks receives cryptographic protection. Auditors assess whether encryption algorithms meet current standards, whether key management practices prevent unauthorized access, and whether the organization maintains logs demonstrating continuous protection.
NIST SP 800-53 Rev. 5 includes multiple controls addressing encrypted communications: SC-8 (Transmission Confidentiality and Integrity), SC-13 (Cryptographic Protection), and SC-17 (Public Key Infrastructure Certificates). ESP directly satisfies SC-8 requirements by encrypting packet payloads and authenticating data origin. Organizations must document which encryption algorithms ESP employs, demonstrate key lifecycle management, and prove that network transport security integrates with broader access control policies.
GDPR Article 32 mandates "encryption of personal data" as a technical measure ensuring appropriate security. When personal data moves across networks—between data centers, to cloud environments, or through partner connections—ESP provides the encryption that GDPR requires. Organizations must demonstrate that encryption extends across all network paths where personal data travels, not merely at application endpoints.
HIPAA Security Rule Technical Safeguards (§164.312) require addressable encryption and decryption controls for electronic protected health information (ePHI) during transmission. Healthcare organizations commonly implement ESP in tunnel mode for connections between facilities, for remote clinician access, and for medical device communications. Audit documentation must show that ePHI never traverses networks in plaintext, that ESP configurations use FIPS-validated encryption modules, and that key management prevents unauthorized decryption.
ESP's role extends to device-level security controls increasingly scrutinized in compliance frameworks. Secure boot ensures devices load only authenticated firmware before network connectivity establishes. Firmware security prevents unauthorized code execution that could compromise ESP sessions. Device authentication verifies endpoint identity before ESP tunnel establishment. Vulnerability management ensures devices receive patches addressing ESP implementation flaws. These controls interconnect—a device with compromised firmware might leak unencrypted data even when ESP appears configured correctly.
Remote management of devices depends on secure network transport. When administrators push firmware updates, modify configurations, or collect logs from edge devices, ESP protects these management sessions. Compliance frameworks increasingly require that all remote administrative access occurs through encrypted channels with mutual authentication. ESP tunnel mode provides this protection, creating dedicated encrypted pathways for management traffic separate from production data flows.
Enterprise buyers evaluating vendors should pose specific questions about ESP implementation: Which ESP modes does the device support (transport, tunnel, or both)? Which encryption algorithms and key lengths are available (AES-128, AES-256, ChaCha20)? Does the device support hardware-accelerated cryptography to minimize performance impact? How does key management occur (manual pre-shared keys, certificate-based authentication, automated key rotation)? What audit logging captures ESP session establishment, failures, and key lifecycle events? Can the device interoperate with ESP implementations from other vendors, or does proprietary configuration create lock-in?
Key Technical Considerations for Implementing ESP in Enterprise Environments

Choosing encryption protocols within ESP determines both security strength and performance characteristics. Encryption is typically achieved using algorithms like AES (Advanced Encryption Standard) or 3DES (Triple Data Encryption Algorithm). Modern implementations should deploy AES-GCM (Galois/Counter Mode) combining encryption and authentication in a single operation, providing both confidentiality and integrity with minimal performance overhead. Organizations should avoid deprecated algorithms including 3DES, DES, and RC4. ChaCha20-Poly1305 offers an alternative to AES for environments where hardware AES acceleration is unavailable, providing comparable security with better software performance on constrained devices.
Device authentication must occur before ESP session establishment. Enterprises face a fundamental security gap when devices can initiate ESP tunnels without proving their identity—compromised or rogue devices could establish encrypted sessions that bypass security monitoring. Certificate-based authentication using X.509 certificates provides the strongest device identity verification, allowing organizations to issue unique credentials to each device, revoke compromised certificates, and audit which devices established connections. Pre-shared keys offer simpler configuration but create operational challenges in large deployments where key rotation becomes complex.
Firmware security and secure boot create the foundation for trustworthy ESP implementations. Devices with compromised firmware might appear to negotiate ESP sessions correctly while simultaneously exfiltrating unencrypted data through separate channels. Secure boot verifies that devices load only cryptographically signed firmware before network initialization. Firmware security ensures that devices can receive updates addressing ESP implementation vulnerabilities without introducing malicious code. Organizations should verify that device vendors provide signed firmware updates, publish vulnerability disclosures, and maintain firmware security through the device lifecycle.
Wireless communication security with ESP requires addressing specific challenges beyond wired network deployments. NAT traversal becomes essential as wireless devices frequently operate behind network address translation. Since the ESP protocol with IP protocol number 50 doesn't have any ports, per se it is not suited for Port Address Translation, the standard method of traversing a NAT router for the TCP and UDP protocols, but RFC 3948 proposes encapsulating ESP packets in UDP datagrams, which then allows applying Port Address Translation. Mobility introduces additional complexity—devices moving between wireless access points must re-establish ESP sessions without dropping connections. Variable link quality on wireless networks affects ESP performance, as encryption and authentication processing adds overhead to already constrained bandwidth.
Network vulnerabilities persist even with ESP deployment. ESP protects data in transit between network endpoints, but it does not address application-layer vulnerabilities, device compromise through physical access, weak authentication at application layers, or vulnerabilities in unencrypted network management protocols. Unlike Authentication Header (AH), ESP in transport mode does not provide integrity and authentication for the entire IP packet, but in tunnel mode, where the entire original IP packet is encapsulated with a new packet header added, ESP protection is afforded to the whole inner IP packet (including the inner header) while the outer header remains unprotected. Organizations must deploy defense-in-depth strategies combining ESP with application security, endpoint protection, and network segmentation.
Access control and intrusion detection systems complement ESP rather than replace it. ESP encrypts the channel, preventing passive eavesdropping, but intrusion detection systems monitor for suspicious connection patterns, unusual data volumes, or connections originating from unexpected sources. Access control policies determine which devices can establish ESP sessions, to which destinations, and during which time windows. Network monitoring tracks ESP session metadata including connection duration, packet counts, and session termination reasons, detecting anomalies that might indicate compromised devices or insider threats.
Remote management and monitoring of ESP sessions requires systematic logging and key lifecycle management. Organizations must track which devices established ESP sessions, when sessions began and ended, which encryption parameters were negotiated, whether authentication succeeded or failed, and when keys rotate. Key lifecycle management addresses generation, distribution, storage, rotation, and revocation. Vulnerability management extends to ESP implementations themselves—vendors periodically disclose vulnerabilities in IPsec stacks requiring firmware updates.
Vendor ecosystem compatibility and interoperability issues create practical deployment challenges. For tunnel mode, the entire IP packet along with the new packet header is encapsulated. Mixed device environments combining legacy equipment, modern IoT devices, and cloud services must negotiate compatible ESP parameters. Legacy devices may support only weak encryption algorithms that modern security policies prohibit. Cloud providers implement ESP differently across platforms, requiring organizations to test interoperability before production deployment. Transport versus tunnel mode decisions affect how traffic flows through network infrastructure—tunnel mode creates virtual point-to-point connections simplifying routing but adding encapsulation overhead, while transport mode reduces overhead but requires more complex routing configurations.
Use‐Cases: ESP in Action for Enterprises
Securely connecting regional offices via VPN tunnels represents the most established ESP use case. Organizations deploy ESP in tunnel mode between office locations, encrypting all inter-office traffic as it traverses internet connections. The outer IP header carries source and destination addresses of VPN gateways at each office, while the encrypted inner IP packet contains actual source and destination addresses of communicating systems. This architecture provides transparent encryption—applications and users require no modifications, as the network infrastructure handles ESP processing.
Protecting IoT device fleets in smart-factory and industrial settings demonstrates ESP's role in operational technology environments. Manufacturing facilities deploy thousands of sensors, actuators, and controllers communicating across industrial networks. ESP secures communications between these devices and central management systems, preventing unauthorized observers from capturing production data or injecting malicious commands. Industrial protocols often lack native encryption—wrapping these protocols in ESP tunnels provides cryptographic protection without requiring application-layer modifications.
Wireless communication between mobile devices and enterprise networks leverages ESP to strengthen security on inherently untrusted wireless links. When employees connect smartphones, tablets, or laptops through public Wi-Fi or cellular networks, ESP tunnels protect all traffic from device to corporate VPN gateway. This protection extends beyond web browsing to include email synchronization, file access, voice calls, and internal application traffic. ESP provides this protection at the network layer, requiring no modifications to individual applications.
Remote device management for edge devices combines secure boot, firmware security, device authentication, and ESP transport into comprehensive security architecture. Edge computing deployments place processing capacity at remote locations—retail stores, utility substations, cell towers, or customer premises. Administrators must securely access these devices for configuration, monitoring, and updates. ESP tunnels protect management traffic, device authentication prevents unauthorized access, secure boot ensures devices boot only trusted firmware, and firmware security allows safe updates addressing newly discovered vulnerabilities.
Threat detection and incident response change when deploying ESP. Encrypted traffic prevents traditional deep packet inspection from examining payload content, shifting threat detection toward metadata analysis. Security teams monitor ESP session establishment patterns, identify anomalous connection sources, track data volume fluctuations, detect connections to known malicious IP addresses, and correlate ESP session activity with endpoint behavior. When incidents occur, ESP logs provide evidence of which devices communicated, when sessions occurred, and whether authentication succeeded—critical data for forensic investigation.
Challenges and Limitations
Encryption and authentication processing introduces computational overhead that can impact network performance, though modern network processors and dedicated cryptographic hardware mitigate these concerns, but administrators must consider throughput requirements during capacity planning. Legacy devices and resource-constrained IoT endpoints often lack hardware cryptographic acceleration, forcing ESP processing onto general-purpose CPUs. This creates measurable latency and reduces throughput, particularly when devices handle numerous simultaneous connections. Organizations must benchmark ESP performance on actual device hardware under realistic traffic loads before deploying at scale.
Key management complexity escalates rapidly in large enterprise deployments. An organization with 10,000 IoT devices potentially manages 10,000 unique device certificates or pre-shared keys. Key rotation—replacing cryptographic keys periodically to limit exposure from potential compromise—requires updating keys across this entire fleet without service interruption. Certificate expiration causes service outages when devices lose network connectivity because their credentials are no longer valid. Revocation of compromised keys must propagate quickly across all network infrastructure to prevent unauthorized access.
ESP is not a security panacea. Network-layer encryption addresses specific threat vectors—eavesdropping, packet injection, replay attacks—but leaves other vulnerabilities unmitigated. Application-layer vulnerabilities persist regardless of ESP deployment. Firmware bugs in ESP implementations themselves have created exploitable vulnerabilities. Device compromise through physical access allows attackers to extract ESP keys directly from device memory. Weak authentication mechanisms granting ESP access to unauthorized users render encryption meaningless. Organizations must view ESP as one control within defense-in-depth strategies, not a complete security solution.
Wireless environments and IoT deployments retain security gaps even with ESP. Physical attack vectors remain—attackers with physical access can tamper with devices, extract credentials from hardware, or replace legitimate devices with malicious alternatives. Device tampering might go undetected if organizations lack hardware attestation capabilities verifying device integrity. Weak authentication at the device enrollment phase might allow rogue devices to obtain valid ESP credentials during initial provisioning.
Vendor claims of "AES encryption" require scrutiny to verify complete security implementation. Some vendors implement ESP with strong encryption but fail to deploy device authentication, allowing any device to establish tunnels. Others omit secure boot, permitting compromised firmware to bypass ESP protections. Still others implement encryption without authentication, exposing deployments to cut-and-paste cryptographic attacks. Enterprise buyers must verify that vendors implement the complete security stack: secure boot, firmware integrity, device authentication, strong encryption algorithms, proper key management, and comprehensive audit logging.
Compliance check-boxes versus actual security represents a persistent challenge. Organizations sometimes enable ESP to satisfy audit requirements without implementing complementary controls ensuring genuine protection. Just enabling ESP tunnel mode between offices means nothing if weak pre-shared keys allow unauthorized tunnel establishment, if devices lack firmware security allowing malicious code execution, if logging is insufficient to detect misuse, or if vulnerability management fails to patch known ESP implementation flaws. Auditors increasingly scrutinize not merely whether ESP is enabled, but whether the implementation actually provides the security properties that compliance frameworks require.
Best Practices for Enterprises (and for Vendors Selling to Enterprises)
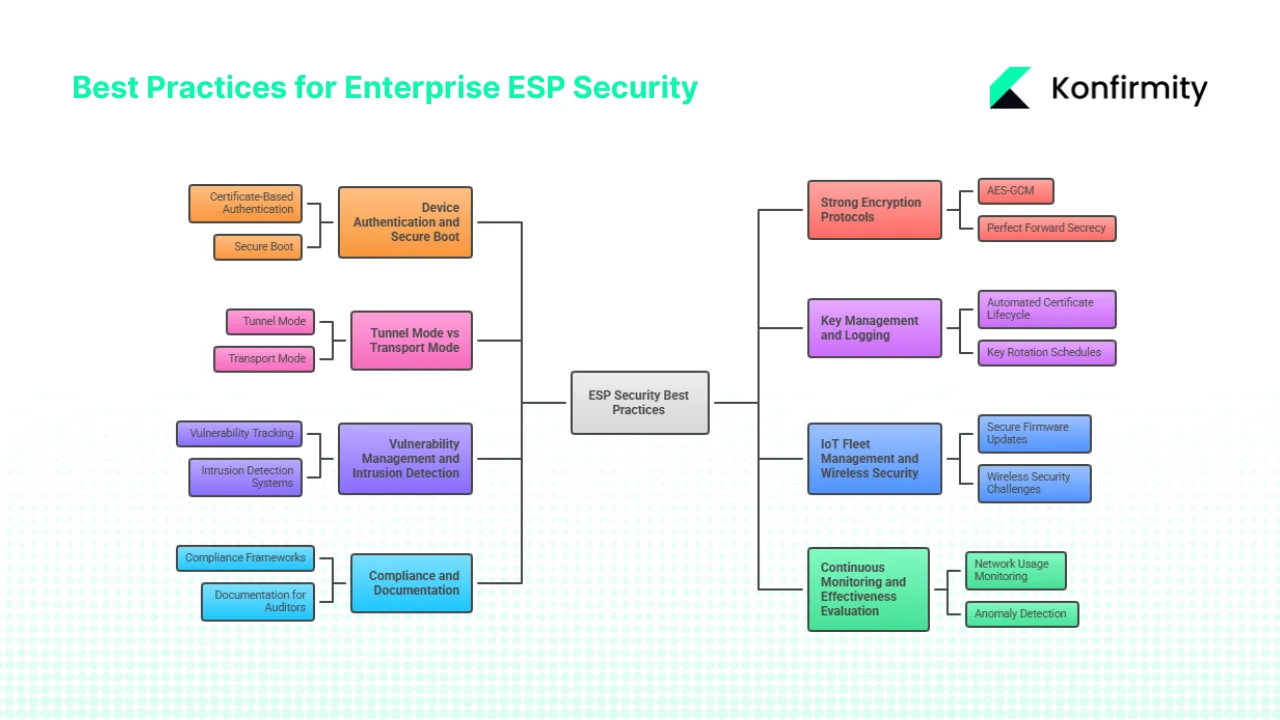
1. Device Authentication and Secure Boot
- Ensure device authentication and secure boot are operational before relying on ESP for network security.
- Implement certificate-based device authentication using unique per-device credentials issued through a managed public key infrastructure.
- Deploy secure boot to verify cryptographic signatures on firmware before allowing network initialization.
- Configure ESP to reject connections from unauthenticated devices, even if they present valid encryption parameters.
- These measures prevent rogue devices from establishing tunnels and compromised devices from participating in encrypted communications.
2. Strong and Current Encryption Protocols
- Adopt AES-GCM with 256-bit keys as the default encryption algorithm for new implementations.
- Disable deprecated algorithms such as 3DES, DES, MD5, and SHA-1.
- Implement perfect forward secrecy using Diffie-Hellman key exchange to ensure that long-term key compromises don’t expose previously captured traffic.
- Configure ESP to prefer hardware-accelerated encryption where available, improving performance while maintaining security.
3. Tunnel Mode vs Transport Mode
- Use tunnel mode for site-to-site or cloud-edge connectivity, which provides simpler routing and complete IP packet protection across untrusted infrastructure.
- Use transport mode for host-to-host communications, where routing complexity is acceptable, and marginal performance improvements matter.
- Be aware that transport mode does not protect the outer IP header, potentially exposing source and destination address information.
4. Key Management and Logging
- Automate certificate lifecycle management to handle issuance, renewal, and revocation without manual intervention.
- Set appropriate key rotation schedules based on the environment’s risk level. For sensitive environments, rotate keys monthly; for less sensitive environments, quarterly or annually.
- Implement comprehensive logging of ESP session details, including session establishment, authentication successes and failures, encryption parameter negotiation, session duration, and termination reasons.
- Retain logs as required by compliance frameworks, typically from 90 days to 7 years.
5. Vulnerability Management and Intrusion Detection
- Track published vulnerabilities in ESP implementations and deploy updates across the device fleet within defined timeframes.
- Deploy intrusion detection systems to monitor for suspicious ESP session patterns, including unusual connection times or unexpected data volumes.
- Implement access control policies to restrict which devices can establish ESP sessions, and monitor authentication credentials and time windows.
6. IoT Fleet Management and Wireless Security
- Plan for remote management, firmware updates, firmware security, and wireless communication security alongside your network transport architecture.
- Implement secure firmware updates with digitally signed firmware, atomic updates, and rollback capabilities.
- Address wireless security challenges such as NAT traversal, mobility between access points, and variable link quality.
- Provision sufficient network capacity to handle ESP encryption overhead on wireless links.
7. Compliance and Documentation
- Integrate ESP deployment into compliance frameworks by mapping implementation details to specific control requirements.
- Document which encryption algorithms ESP uses and demonstrate compliance with control specifications in frameworks like ISO 27001, NIST, or industry-specific standards.
- Ensure key management practices align with cryptographic key management controls, and provide evidence that logging captures security-relevant events for audit trails.
- Create documentation that allows auditors to verify ESP implementation compliance without needing deep technical investigation.
8. Continuous Monitoring and Effectiveness Evaluation
- Continuously monitor network usage to identify unexpected changes in encrypted traffic volumes.
- Implement anomaly detection to identify unusual ESP session behaviors.
- Track intrusion detection system alerts for attack attempts targeting ESP infrastructure.
- Review authentication failures to detect misconfigured devices or unauthorized access attempts.
- Measure device behavior to correlate network activity with expected operational patterns, helping detect threats like compromised devices or insider threats that could bypass ESP encryption.
Looking Ahead — 2026 and Beyond
The Enhanced Encapsulating Security Payload (EESP) protocol builds on the existing IP Encapsulating Security Payload (ESP) protocol, designed to modernize and overcome limitations in the ESP protocol by adding Session IDs, changing some previously mandatory fields to optional, and moving the ESP trailer into the EESP header. IoT expansion continues driving demand for lighter-weight ESP implementations suitable for severely constrained devices. Emerging protocols address resource limitations on devices with minimal processing power, limited battery capacity, or restrictive bandwidth constraints. Edge computing architectures place more processing at network periphery, requiring encrypted transport protecting data between edge nodes and centralized infrastructure.
ESP evolution integrates with zero-trust network models treating all network traffic as potentially hostile regardless of source location. Traditional perimeter-based security assumed traffic originating within the corporate network was trustworthy—an assumption that device compromise and insider threats have rendered obsolete. Zero-trust architectures require continuous authentication and authorization for every connection attempt. ESP provides the cryptographic foundation for zero-trust networks, but implementations must extend beyond basic tunnel establishment to include continuous device attestation, dynamic policy enforcement, and real-time risk scoring.
Coupling ESP with machine-learning-based threat detection represents a significant evolution in security monitoring. Traditional signature-based detection fails against encrypted traffic—packet inspection cannot examine encrypted payloads. Machine learning analyzes ESP session metadata including connection timing, packet size distributions, inter-packet delays, session durations, and data volumes. These behavioral characteristics enable anomaly detection identifying compromised devices, malware communications, or data exfiltration attempts even when traffic is encrypted. Organizations increasingly deploy analytics platforms correlating ESP session metadata with endpoint behavior, user activity, and threat intelligence.
Regulatory shifts continue demanding stronger encryption and more comprehensive privacy protections. Supply-chain security requirements extend to devices themselves—regulators increasingly require that device vendors demonstrate firmware security, secure boot implementation, vulnerability disclosure practices, and long-term support commitments. These requirements tie directly to network layer security because compromised devices undermine ESP protection. Emerging regulations in the EU, US, and other jurisdictions mandate specific encryption standards, key management practices, and audit logging capabilities that organizations must implement through ESP and complementary controls.
For companies selling into enterprise clients, articulating complete security architecture becomes a competitive differentiator. Customers no longer accept vendor claims of "enterprise-grade security" without specific technical validation. Successful vendors document precisely how their solutions implement ESP, which modes and algorithms they support, how device authentication occurs, how firmware security protects against compromise, and how the entire stack integrates with customer compliance frameworks. Organizations evaluate vendors based on their ability to explain the complete path from secure boot through device authentication through ESP tunnel establishment through application-layer security—understanding that weakness at any layer compromises the entire architecture.
Conclusion
ESP cybersecurity establishes foundational protection for enterprise networks by providing confidentiality through encryption, integrity through cryptographic authentication, and protection against replay attacks at the network transport layer. Organizations pursuing SOC 2, ISO 27001, HIPAA, or GDPR compliance must demonstrate encryption of data in transit—ESP fulfills this requirement when properly implemented with strong algorithms, robust key management, and comprehensive logging. ESP addresses specific network-layer threats including eavesdropping, packet injection, and man-in-the-middle attacks that persist even when application-layer security is strong.
ESP represents one control within comprehensive security architecture, not a complete solution. Organizations must pair ESP network-layer encryption with device security including firmware integrity and secure boot, access control policies restricting which devices can establish connections, vulnerability management ensuring timely patching of ESP implementation flaws, and threat detection monitoring for suspicious behaviors that might indicate compromise. This defense-in-depth approach recognizes that attackers target the weakest link—comprehensive protection requires securing every layer from hardware through firmware through network through application.
For companies selling to enterprise clients, demonstrating how your solution implements or integrates with ESP provides competitive advantage when buyers evaluate security capabilities. Technical decision-makers assess whether devices support both transport and tunnel modes, which encryption algorithms are available, whether hardware cryptographic acceleration improves performance, how device authentication occurs, what key management capabilities exist, and how audit logging captures security-relevant events. Business leaders evaluate whether vendor security implementations satisfy compliance framework control requirements that auditors will verify. Articulating these technical capabilities clearly, backed by documentation and implementation evidence, positions vendors as security partners rather than merely technology suppliers.
FAQs
1) What is ESP in cyber security?
ESP stands for Encapsulating Security Payload, and it is a fundamental component of the IPsec protocol suite used to secure IPv4 and IPv6 communications by authenticating and encrypting each IP packet in a communication session, providing confidentiality by encrypting the payload of the IP packet. ESP operates at the network layer, protecting data as it moves across untrusted networks through encryption, authentication, and integrity verification. Organizations deploy ESP primarily in VPN implementations, securing connections between offices, protecting remote access, and encrypting IoT device communications.
2) What is the difference between ESP and AH?
Unlike its counterpart, the Authentication Header (AH), ESP provides confidentiality, data integrity, and origin authentication for IP packets through robust encryption mechanisms, while AH only provides integrity and authentication without encryption. AH verifies that packets have not been tampered with and confirms sender identity, but it leaves data readable to anyone who intercepts it. ESP encrypts the payload making data unreadable to unauthorized parties while also providing authentication and integrity. Most modern implementations deploy ESP rather than AH because encryption without authentication is insecure, and authentication without encryption fails to protect confidentiality.
3) What is EPS in cyber security?
"EPS" does not represent a standard cybersecurity protocol or acronym. This term likely represents a mis-spelling or confusion with "ESP" (Encapsulating Security Payload). In some contexts, organizations use "ESP" to mean "External Service Provider" when discussing vendor management and third-party risk in compliance frameworks—but this usage addresses vendor relationships, not network encryption protocols. When evaluating security documentation or vendor claims, verify the intended meaning of any acronym because confusion between network security protocols and vendor management terminology leads to misunderstanding of actual security capabilities.
4) What is the difference between ESP and CSP?
ESP (Encapsulating Security Payload) is a network-layer encryption protocol within the IPsec suite that encrypts and authenticates IP packets as they traverse networks. CSP typically means Cloud Service Provider—organizations such as AWS, Azure, or Google Cloud that deliver computing resources over the internet. These terms address completely different domains: ESP is a technical protocol implementing cryptographic protection, while CSP describes business entities providing infrastructure services. In some compliance contexts, "ESP" might refer to External Service Provider in vendor management frameworks, creating potential confusion. Organizations should clarify terminology when discussing security requirements to ensure all parties understand whether the conversation addresses network encryption protocols, cloud infrastructure providers, or third-party vendor relationships.



.svg)
.svg)
.svg)