Telecom and enterprise networking face a fundamental transformation: proprietary hardware appliances that once defined network architecture are being replaced by software-based functions running on general-purpose infrastructure. This shift—network function virtualization (NFV)—decouples network capabilities from dedicated hardware, enabling organizations to deploy, scale, and manage network services with unprecedented agility. For vendors selling to large enterprises, service providers, infrastructure firms, and cloud/edge operators, understanding ETSI NFV is no longer optional—it defines the architectural foundation, interoperability requirements, and competitive landscape of modern network infrastructure.
Most organizations attempting NFV deployments encounter a critical challenge: the absence of standardized frameworks creates vendor lock-in, integration complexity, and operational risk. This gap becomes apparent when attempting to deploy multi-vendor virtual network functions (VNFs), implement NFV management and orchestration (MANO) systems, or integrate with software-defined networking (SDN) architectures. The European Telecommunications Standards Institute (ETSI) established the NFV framework specifically to address these challenges through reference architectures, functional blocks, and standardized interfaces that enable true interoperability.
This article defines the ETSI NFV framework, examines its architectural components—NFV Infrastructure (NFVI), Virtual Network Functions (VNFs), and NFV Management and Orchestration (MANO)—presents concrete enterprise-oriented use cases, and analyzes compliance and standardization relevance for vendors pursuing enterprise clients. Understanding ETSI NFV is essential for positioning offerings around service chaining, orchestration platforms, network automation, and cloud infrastructure.
What is ETSI NFV?
Network function virtualization (NFV) decouples network functions—routing, firewalling, load balancing, intrusion detection—from dedicated hardware appliances, running them as software on general-purpose compute, storage, and network resources. Rather than deploying proprietary boxes for each network function, NFV enables organizations to deploy software-based implementations on standard infrastructure, whether on-premises data centers, public cloud, or edge environments.
ETSI NFV specifically refers to the standardization framework developed by the European Telecommunications Standards Institute (ETSI) to define reference architectures, functional blocks, interfaces, and protocols for NFV deployments. ETSI's Industry Specification Group (ISG) NFV has developed over 100 different specifications and reports for the virtualization of network functions, with focus on enabling multi-vendor interoperability, lifecycle management, and operational consistency across deployments.
The framework matters because it addresses fundamental business realities: reducing capital expenditures on specialized hardware, lowering operational expenses through automation, accelerating service rollout from months to weeks, and eliminating vendor lock-in through standardized interfaces. For enterprise-selling vendors, ETSI NFV provides the architectural blueprint for delivering managed network services, enabling service chaining across multiple VNFs, and supporting dynamic scaling based on demand—capabilities that differentiate modern offerings from traditional hardware-centric approaches.
Origins and evolution
ETSI established the Industry Specification Group (ISG) NFV in 2012, driven by major service providers seeking to transform network economics. The initial white paper, "Network Functions Virtualisation: An Introduction, Benefits, Enablers & Call for Action," articulated the business case: telecom networks contained increasingly diverse proprietary hardware, creating escalating costs, deployment delays, and operational complexity. Virtualization offered a path to agility, vendor independence, and infrastructure efficiency.
The ETSI ISG NFV community has evolved through several phases, its publications have moved from pre-standardization studies to detailed specifications, organized as Release 1, Release 2, Release 3, and subsequent releases. Each release cycle adds capabilities: Release 5 includes support for virtualized RAN, multi-tenancy in NFV, and Green NFV, addressing energy efficiency and sustainable infrastructure. Release 4 completed container-related functionalities such as support for container cluster management, recognizing the industry's shift toward cloud-native architectures.
Ongoing work encompasses cloud-native network functions (CNFs) running in containerized environments, edge deployments for distributed network functions closer to end users, and deeper integration with SDN for programmable network control. New virtualization technologies such as support for containerized VNFs and container infrastructure management are tackled in studies and on-going normative specifications work. For vendors targeting enterprise clients, this evolution signals that ETSI NFV remains actively developed to support emerging deployment models—from campus networks to private 5G installations.
Core concepts and components
ETSI NFV defines three architectural pillars:
NFV Infrastructure (NFVI) comprises the hardware resources (compute, storage, network), virtualization layer (hypervisors or container platforms), and resource abstractions that host virtual network functions. NFVI provides the underlying substrate—whether physical servers in enterprise data centers, cloud instances, or edge nodes—on which VNFs execute.
Virtual Network Functions (VNFs) represent software implementations of network functions traditionally delivered as hardware appliances. Examples include virtual firewalls, load balancers, WAN optimizers, intrusion detection systems, and mobile core network functions. VNFs run on NFVI and can be instantiated, scaled, or terminated through orchestration systems.
NFV Management and Orchestration (MANO) provides the control plane: lifecycle management of VNFs and network services, resource orchestration across NFVI, onboarding of new VNF packages, scaling operations, and termination. MANO translates business intent—"deploy a firewall → load balancer → IDS service chain"—into infrastructure actions, automating the provisioning, configuration, and monitoring of virtualized network functions.
The relationship with software-defined networking (SDN) is complementary: while NFV virtualizes network functions, SDN virtualizes network connectivity and control. SDN enables dynamic provisioning of overlay networks, traffic steering for service chains, and programmable forwarding policies that connect VNFs. Together, NFV and SDN create programmable, software-defined network infrastructure where both functions and connectivity are orchestrated through automation.
ETSI NFV specifications describe and specify virtualization requirements, NFV architecture framework, functional components and their interfaces, as well as the protocols and the APIs for these interfaces. This standardization enables interoperability: VNFs from vendor A can run on NFVI from vendor B, managed by MANO systems from vendor C—provided all adhere to ETSI NFV specifications.
ETSI NFV Architecture – Deep Dive
The ETSI NFV reference architecture, defined in ETSI GS NFV-002 and related documents, establishes functional blocks, reference points, and interfaces that enable multi-vendor NFV deployments. The architecture comprises three domains: NFVI (the infrastructure), VNFs (the virtualized functions), and MANO (the orchestration and management layer).
Key functional blocks include:
- NFV Orchestrator (NFVO): Orchestrates network services across NFVI resources, manages network service lifecycles, and coordinates VNF instantiation.
- VNF Manager (VNFM): Manages individual VNF instances—lifecycle operations, scaling, healing, and configuration.
- Virtualised Infrastructure Manager (VIM): Controls and manages NFVI resources (compute, storage, network), interfacing with hypervisors or cloud platforms.
- Service, VNF and Infrastructure Descriptors: Standardized templates (YAML/JSON-based) describing VNF packages, network service topologies, and resource requirements.
Reference points define standardized interfaces: Or-Vnfm (orchestrator to VNF manager), Ve-Vnfm (VIM to VNFM), Os-Ma-nfvo (orchestrator to external OSS/BSS systems). These interfaces enable interoperability—MANO components from different vendors can communicate using standardized protocols and data models defined in ETSI GS NFV-SOL specifications.
For enterprise-selling vendors, this architecture dictates integration requirements: orchestration platforms must support standard descriptors, lifecycle APIs, and resource management interfaces to claim ETSI NFV conformance.
NFV Infrastructure (NFVI) details
NFVI provides compute (CPU, memory), storage (persistent volumes, object storage), and network resources (physical NICs, virtual switches, overlay networks). The virtualization layer abstracts hardware through hypervisors (KVM, VMware ESXi) or container platforms (Kubernetes), presenting resources as pools that MANO can allocate dynamically.
Achieving "carrier-grade" reliability in virtualized environments presents specific challenges: VNFs must meet availability requirements (99.999% uptime for critical functions), latency constraints (sub-millisecond forwarding for network functions), and throughput demands (multi-gigabit packet processing) that proprietary hardware once guaranteed. Vendors must implement hardware acceleration (SR-IOV, DPDK for high-performance packet processing), redundancy mechanisms (active-active VNF clustering), and resource isolation (CPU pinning, NUMA awareness) to deliver production-grade performance.
For enterprise clients evaluating NFV-based offerings, NFVI design determines performance, scalability, and operational reliability. Vendors must transparently communicate infrastructure architecture, performance benchmarks, and availability guarantees backed by SLAs.
Virtual Network Functions (VNFs)
VNFs implement network functions in software, decoupled from underlying hardware. Enterprise-relevant examples include virtual firewalls (Palo Alto VM-Series, Fortinet FortiGate-VM), virtual load balancers (F5 BIG-IP VE, HAProxy), SD-WAN edge functions, WAN optimizers, IDS/IPS systems, and session border controllers. In telecom contexts, VNFs encompass mobile core functions (MME, SGW, PGW for LTE; AMF, SMF, UPF for 5G) and IP Multimedia Subsystem (IMS) components.
Service chaining links multiple VNFs into a network service (NS): traffic flows sequentially through a chain—firewall → IDS → load balancer → application—with SDN controllers steering packets through each function. Service chains enable composable network architectures where services are constructed by combining reusable VNF building blocks. For managed service providers, service chaining differentiates offerings: enterprise clients can select security + performance + optimization as pre-configured chains, deployed rapidly through orchestration.
The shift from hardware appliances to VNFs fundamentally changes procurement, deployment, and operations. Traditional network functions required physical installation, specialized configuration, and hardware refresh cycles measured in years. VNFs deploy in minutes through automated orchestration, scale horizontally by instantiating additional instances, and update through software releases rather than hardware replacements—compressing service deployment from months to weeks.
NFV Management and Orchestration (MANO)
MANO provides control intelligence: resource orchestration across NFVI pools, lifecycle management of VNFs and network services, onboarding of VNF packages, automated scaling based on load, performance monitoring, and healing operations when failures occur.
Key building blocks include:
- NFVO: Orchestrates end-to-end network services, selecting NFVI resources, coordinating VNFM operations, and interfacing with external OSS/BSS systems.
- VNFM: Manages individual VNF lifecycles—instantiation, configuration, scaling (adding/removing VNF instances), healing (restarting failed instances), and termination.
- VIM: Interfaces with virtualization platforms (OpenStack, VMware vCloud, Kubernetes) to allocate compute, storage, and network resources.
- Container Infrastructure Service Manager (CISM) and Container Infrastructure Resources (CIR): Support management of CIS clusters which serve as the underlay of both cloud-native environments and virtualized resource environments, recognizing containerized workload requirements.
Orchestration platforms translate business intent into infrastructure actions. When an enterprise client requests "deploy SD-WAN service with firewall + WAN optimizer at 50 branch locations," the orchestration platform selects appropriate NFVI resources, instantiates VNF instances, configures network connectivity through SDN, and monitors service health—automating processes that once required weeks of manual configuration.
Network automation is central to MANO value: automated VNF onboarding eliminates manual integration, policy-driven scaling responds to traffic patterns without human intervention, and self-healing detects failures and restores service automatically. For enterprise-selling vendors, robust orchestration platforms differentiate managed service offerings by enabling rapid service provisioning, predictable operations, and reduced dependence on specialized engineering resources.
Role of SDN and convergence with NFV
Software-defined networking (SDN) separates control planes (routing decisions, traffic policies) from data planes (packet forwarding), centralizing network control in software controllers. SDN enables dynamic overlay networks, traffic steering based on policies, and programmable connectivity—capabilities that complement NFV by providing the network fabric connecting VNFs.
In NFV architectures, SDN controllers provision virtual networks connecting VNF instances, implement service chaining by steering traffic through VNF sequences, and enable multi-tenancy through network isolation. For example, an enterprise SD-WAN deployment uses NFV to run edge functions (firewall, WAN optimizer) as VNFs and uses SDN to create overlay tunnels connecting branch VNFs to data center resources, dynamically routing traffic based on application requirements.
From a vendor perspective, combined NFV + SDN offerings deliver programmable network infrastructure: enterprises gain flexibility to compose services from VNF building blocks, agility to modify network connectivity through software, and automation to orchestrate both functions and connectivity. This convergence enables "network as code" models where entire network architectures are defined, deployed, and modified through declarative templates—capabilities that differentiate modern managed services from traditional hardware-centric offerings.
Operating models: from hardware appliances to virtualised network functions
Traditional network functions deployed as dedicated hardware appliances: a firewall required a physical security appliance, a load balancer required specialized ADC hardware, and WAN optimization required proprietary boxes at each location. This model imposed long procurement cycles (weeks to order and install hardware), inflexible capacity (over-provisioning for peak demand), and vendor lock-in (proprietary hardware tied to specific vendors).
Virtualized network functions transform this model: VNFs deploy on standard infrastructure through automated orchestration, scale dynamically by adding instances during demand spikes, and update through software releases independent of hardware. An enterprise requiring firewall capacity at a new branch location deploys a virtual firewall in minutes through orchestration rather than waiting weeks for hardware shipment and installation.
Benefits for enterprise-selling vendors include faster time to market (provision managed services in days rather than months), reduced specialized hardware costs (leveraging standard cloud infrastructure), more agile service deployment (modify service chains through orchestration), and subscription-based business models (offer network functions as a service, scaling charges with consumption).
Enterprise clients gain flexibility to match network capacity to actual demand, agility to deploy new services rapidly, and reduced vendor lock-in through standardized VNF interfaces. Vendors offering managed service layers built on NFV architectures deliver these benefits while absorbing the operational complexity of orchestration, lifecycle management, and multi-vendor integration.
Use Cases for ETSI NFV
Telecom service provider use cases
Virtualized mobile core functions represent a primary NFV use case: 4G EPC components (MME, SGW, PGW, PCRF) and 5G core functions (AMF, SMF, UPF, PCF) deploy as VNFs on cloud infrastructure, enabling service providers to scale capacity dynamically, deploy network slicing for differentiated services, and reduce hardware costs through infrastructure consolidation.
Virtualised customer-premises equipment (vCPE) delivers enterprise network functions—firewalls, SD-WAN, routing—as VNFs hosted in service provider data centers or on universal CPE devices at customer sites. Rather than deploying specialized hardware at each enterprise location, service providers provision VNFs through orchestration, simplifying installation and enabling rapid service modifications.
Edge computing and distributed NFV place network functions closer to end users—processing data at edge nodes rather than centralized data centers to reduce latency, support real-time applications, and minimize backhaul bandwidth. Edge NFV deployments support use cases like content delivery, IoT processing, and augmented reality applications requiring sub-10ms latency.
Enterprise-oriented use cases
Enterprise WAN and SD-WAN with virtualized functions: Organizations deploying SD-WAN increasingly adopt NFV architectures where edge functions (firewall, IDS/IPS, load balancer, WAN optimizer) run as VNFs on cloud infrastructure or branch appliances. Rather than deploying dedicated hardware at each branch, enterprises deploy universal CPE devices hosting VNFs provisioned through central orchestration. This model reduces hardware costs, accelerates branch onboarding, and enables rapid service modifications—adding security functions or bandwidth optimization through software rather than hardware installation.
Network service chaining for enterprise applications: Complex enterprise applications require multiple network functions: inbound traffic passes through firewall → IDS → load balancer → WAN optimizer before reaching application servers. NFV enables service chaining where MANO systems provision VNF sequences and SDN controllers steer traffic through the chain. Enterprises modify service chains dynamically—adding or removing functions based on security policies, compliance requirements, or performance needs—without physical network reconfiguration.
Multi-tenant managed service models: Vendors offering "network function as a service" built on NFV architectures can support multiple enterprise clients on shared infrastructure through multi-tenancy. Each client receives isolated VNF instances, dedicated network slices, and independent management while the vendor consolidates infrastructure, achieving economies of scale. This model enables subscription-based pricing (charge per VNF instance, per bandwidth consumed) and rapid service provisioning (onboard new clients in hours through orchestration).
Private 5G and campus network deployments: Enterprises deploying private 5G networks for manufacturing facilities, warehouses, or campuses use NFV to host 5G core functions (AMF, SMF, UPF) on edge infrastructure. Studies on virtualized RAN and 5G deployments support these use cases, enabling organizations to deploy private networks using standard ETSI NFV architectures. NFV provides the flexibility to deploy network functions on-premises for data sovereignty, scale capacity based on device counts, and integrate with enterprise IT systems.
Cloud-native network functions (CNFs) migration: Organizations transitioning to cloud-native architectures deploy CNFs—containerized network functions running on Kubernetes—rather than VM-based VNFs. Container-related functionalities have been completed, such as support for container cluster management, enabling MANO systems to orchestrate CNFs alongside traditional VNFs. For enterprise cloud and edge deployments, CNFs offer faster instantiation, higher density, and tighter integration with cloud-native tooling (service meshes, observability platforms) compared to VM-based VNFs.
Business value for vendors selling to enterprise clients
Time to market: NFV-based offerings enable vendors to provision network services in days rather than months. Orchestration automates VNF deployment, configuration, and integration, eliminating manual processes. Vendors can respond to RFPs with rapid proof-of-concept deployments, demonstrate working services during sales cycles, and onboard clients faster—accelerating revenue recognition.
Cost efficiencies: Replacing specialized hardware with standard cloud infrastructure reduces capital expenditures. Vendors consolidate multiple client workloads on shared NFVI through multi-tenancy, achieving infrastructure utilization rates of 60-80% compared to 20-30% for dedicated hardware. Operational automation reduces labor costs—orchestration handles provisioning, scaling, and healing operations that once required manual intervention.
Flexibility and scalability: NFV enables vendors to support changing enterprise demand dynamically. Clients requiring additional firewall capacity receive new VNF instances through orchestration rather than hardware procurement. Service chaining modifications happen through configuration updates rather than physical rewiring. This flexibility differentiates managed service offerings by enabling rapid adaptation to client needs.
Differentiation and business model innovation: Vendors offering managed network services built on NFV architectures differentiate through software-based agility, multi-vendor ecosystems (supporting best-of-breed VNFs), and subscription models (network functions as a service). Rather than selling hardware with maintenance contracts, vendors offer outcome-based services—guaranteed security posture, assured application performance—delivered through orchestrated VNF chains.
Challenges and considerations
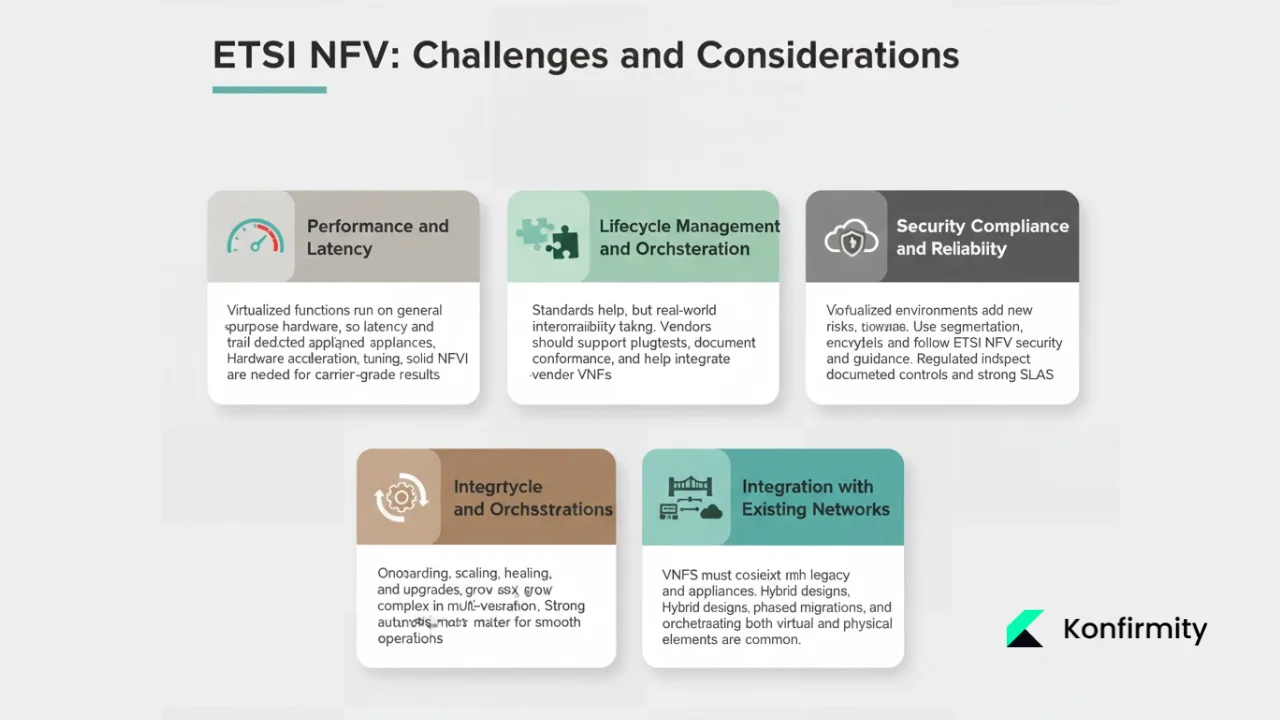
1) Performance and latency: Virtualized network functions introduce overhead compared to specialized hardware. VNFs running on general-purpose computers may exhibit higher latency (microseconds vs. nanoseconds for hardware ASICs) and lower throughput (tens of Gbps vs. hundreds of Gbps for dedicated appliances). Achieving carrier-grade performance requires hardware acceleration (SR-IOV, DPDK), resource tuning (CPU pinning, huge pages), and careful NFVI design. Enterprise clients must understand performance trade-offs: virtualization offers flexibility at potential cost to raw performance.
2) Interoperability across vendors: While ETSI NFV defines standardized interfaces, real-world interoperability requires rigorous testing. VNFs from different vendors may interpret specifications differently, creating integration challenges. Vendors must participate in plugfests (ETSI NFV Plugtests events testing multi-vendor interoperability), document conformance to specific specification versions, and provide integration support for complex multi-vendor deployments.
3) Lifecycle management and orchestration complexity: MANO systems must handle VNF onboarding (validating packages, integrating with orchestration), automated scaling (monitoring load, triggering instance creation), healing (detecting failures, restarting VNFs), and upgrades (rolling out new VNF versions without service disruption). Orchestration complexity increases with multi-vendor environments—each VNF may require vendor-specific VNFM components. Robust automation, comprehensive testing, and operational runbooks are essential.
4) Integration with existing networks and legacy hardware: Enterprise networks contain legacy infrastructure—physical routers, switches, appliances—that must coexist with virtualized functions. NFV deployments require hybrid architectures where VNFs interoperate with physical devices, complicating network design and management. Vendors must provide clear migration paths: phased transitions where VNFs gradually replace hardware, hybrid orchestration managing both virtual and physical elements, and integration with existing network management systems.
5) Security, compliance, and reliability: Virtualized environments introduce new attack surfaces: hypervisor vulnerabilities, VM escape exploits, container security issues, and orchestration platform compromises. ETSI NFV Security specifications handle security aspects for virtualized environments and deployments, addressing attestation, trust, and security management. Enterprise clients in regulated industries (finance, healthcare, government) require documented security controls, compliance with frameworks (NIST, ISO 27001), and reliability guarantees backed by SLAs. Vendors must implement comprehensive security—network segmentation, VNF isolation, encrypted management channels—and document security architectures for compliance audits.
Compliance and Standardization Relevance
The importance of standardization
Frameworks like ETSI NFV matter because they enable multi-vendor interoperability, reduce vendor lock-in, and provide common reference architectures that lower integration risk. Without standardization, NFV deployments become proprietary: VNFs work only with specific MANO systems, orchestration platforms support limited VNF catalogs, and enterprises face vendor lock-in comparable to traditional hardware environments.
NFV deployments and use cases have been limited due to integration challenges and a lack of standards, but ETSI's NFV specifications seek to address those challenges by creating interoperable platforms. For vendors selling to enterprise clients, aligning with ETSI NFV standards demonstrates commitment to open ecosystems, simplifies integration with client infrastructure and third-party systems, and reduces risk for clients concerned about long-term vendor viability.
Enterprises evaluating NFV-based offerings prioritize vendors demonstrating standards compliance: the ability to integrate with existing orchestration platforms, support for industry-standard VNF descriptors, and participation in interoperability testing. Standards alignment becomes a competitive differentiator—evidence of engineering maturity and commitment to customer choice rather than proprietary lock-in.
How ETSI NFV influences compliance for vendors and enterprises
For vendors: Conformity to ETSI NFV specifications serves as a selling point during enterprise procurement. Vendors referencing specific specification compliance (ETSI GS NFV-SOL 001 for VNF descriptors, ETSI GS NFV-SOL 003 for lifecycle APIs) demonstrate technical credibility and interoperability readiness. Vendors participating in ETSI plugfests—multi-vendor interoperability events testing NFV implementations—can cite third-party validation of conformance, differentiating from competitors with untested implementations.
For enterprises: When adopting virtualized network services, enterprises expect vendors to align with ETSI NFV standards to reduce future migration risk. Standards-compliant deployments enable enterprises to switch MANO platforms, integrate VNFs from multiple vendors, and avoid proprietary lock-in. In procurement processes, enterprises increasingly require vendors to document standards conformance, provide descriptor templates following standard formats, and demonstrate interoperability with reference implementations.
In regulated industries: Organizations in telecom, finance, healthcare, and government sectors face regulatory requirements for reliability, availability, and security. Virtualized network functions must meet the same mandates as hardware predecessors: 99.999% availability for critical services, audit trails for security events, disaster recovery capabilities, and data sovereignty controls. ETSI NFV specifications provide the architectural baseline—standardized management interfaces, security controls, monitoring capabilities—that enable regulatory compliance. Enterprises can reference ETSI NFV compliance when demonstrating due diligence to auditors and regulators.
Key specifications and documents to be aware of
ETSI GS NFV-002 (NFV Architectural Framework): Defines functional blocks (NFVO, VNFM, VIM, NFVI), reference points, and architectural principles. This foundational document establishes the NFV architecture that subsequent specifications detail.
ETSI GS NFV-SOL series: Specifies descriptors, RESTful APIs, and protocols for VNF lifecycle management. Key documents include:
- SOL001: VNF descriptor specification (TOSCA-based templates describing VNF topology, resource requirements, and dependencies)
- SOL002: VNF lifecycle management interface (APIs for instantiation, scaling, healing, termination)
- SOL003: VNF lifecycle operation granting and subscription/notification interfaces
- SOL005: NFV-MANO interface specifications for network service management
- SOL006: VNF package structure and content
Release documentation: The specification of new features and capabilities in planned releases had as outcome subsequent tranches referenced as Release 2, Release 3, continuing through Release 5 and beyond. Each release addresses emerging requirements: Release 4 completed container support, Release 5 adds energy efficiency and multi-tenancy. Vendors should track release evolution to align implementations with current specifications.
Security specifications (ETSI GS NFV-SEC series): Handle security aspects for virtualized environments and deployments, including certificate management, attestation, security management interfaces, and threat models specific to virtualized network functions.
Implications for enterprise-selling vendors' offerings
Vendors must ensure infrastructure and platforms support NFV architecture: NFVI providing virtualization abstraction, VNF catalog including multiple vendor options, and MANO systems implementing standard interfaces. Orchestration platforms must support ETSI descriptor formats (TOSCA-based VNF and NS descriptors), implement lifecycle APIs (SOL002, SOL003, SOL005), and handle standard reference points for NFVO-VNFM and VNFM-VIM communication.
For managed services, compliance with standards enables multi-vendor interoperability, service chaining across heterogeneous VNFs, and partner ecosystems where vendors collaborate rather than compete on proprietary integration. Vendors can offer enterprises choice—select best-of-breed VNFs from multiple vendors—while maintaining unified orchestration and management.
Marketing and sales positioning should reference ETSI NFV readiness: "Our orchestration platform implements ETSI GS NFV-SOL interfaces, supports standard VNF descriptors, and has been validated at ETSI NFV Plugtests events." This messaging differentiates vendors as committed to open standards and interoperability rather than proprietary lock-in.
For compliance audits, enterprises may request documentation of standards adherence: which ETSI NFV specifications are implemented, conformance test results, and integration with standard MANO systems. Vendors should maintain documentation mapping their implementations to specific specification versions, providing evidence for enterprise procurement and compliance reviews.
Future trends and what vendors need to watch
Cloud-native network functions (CNFs): The industry shift toward containerized workloads continues—CNFs running on Kubernetes replace VM-based VNFs for faster instantiation, higher density, and cloud-native tooling integration. ETSI NFV specifications increasingly address container management, Kubernetes integration, and cloud-native orchestration patterns. Vendors must support hybrid environments managing both VNFs and CNFs.
Edge computing and distributed NFV: Edge deployments place network functions at enterprise campus locations, retail sites, factory floors, and branch offices rather than centralized data centers. Distributed NFV architectures require orchestration across multiple sites, resource management for constrained edge infrastructure, and resilience designs handling intermittent connectivity. Enterprise use cases—private 5G, IoT processing, real-time analytics—drive edge NFV adoption.
Automation and AI/ML in orchestration: Network automation evolves from scripted workflows to autonomous operations using AI/ML: anomaly detection triggering automated healing, predictive scaling based on traffic forecasts, and intent-based management translating business policies into infrastructure configurations. Vendors integrating AI/ML capabilities into orchestration platforms differentiate through reduced operational overhead and proactive issue resolution.
Emerging regulatory and compliance frameworks: As virtualized network infrastructure becomes critical for enterprise operations, regulatory frameworks increasingly reference NFV standards. Compliance requirements may mandate standards-based architectures, interoperability testing, and security controls aligned with ETSI specifications. Vendors must monitor regulatory developments in key verticals (telecom, finance, healthcare) and align offerings with emerging compliance requirements.
Practical Considerations for Vendors When Selling to Enterprises
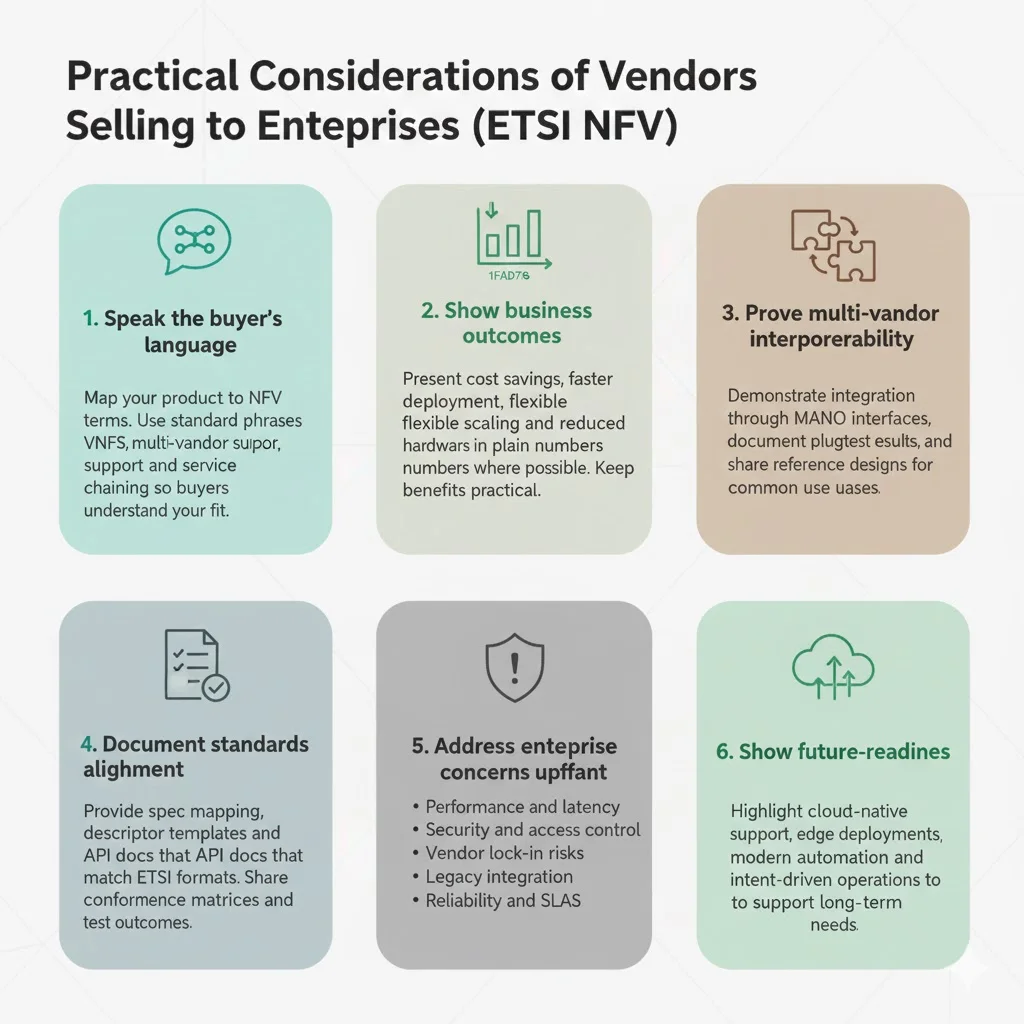
Vendors positioning NFV-based offerings to enterprise clients should map products explicitly to semantic keywords: "We support NFV architecture via our software-defined networking platform, enabling orchestration of virtual network functions across cloud infrastructure with automated service chaining." This language connects technical capabilities to standardized terminology that enterprise buyers recognize.
Position benefits in business terms: cost savings through infrastructure consolidation (quantified: "reduce branch hardware costs by 60-70% through universal CPE hosting VNFs"), agility through rapid service deployment ("provision new branch locations in hours through orchestration versus weeks for hardware"), scalability supporting dynamic demand ("scale firewall capacity 3x during seasonal peaks without hardware procurement"), and vendor independence through multi-vendor VNF ecosystems.
Build proof-points demonstrating multi-vendor interoperability: show how VNFs from different vendors integrate through standard MANO interfaces, document conformance testing at ETSI plugfests, and provide reference architectures for common deployment scenarios (SD-WAN with multi-vendor VNFs, security service chains, private 5G with CNFs).
Be transparent about compliance and standards alignment: include documentation mapping implementations to specific ETSI NFV specifications, provide descriptor templates and API documentation following standard formats, cite interoperability testing results, and maintain conformance matrices showing which specification versions are supported. This transparency builds enterprise confidence and simplifies procurement evaluations.
Address enterprise concerns directly: performance and latency considerations (provide benchmark data, explain hardware acceleration approaches), security controls (document isolation mechanisms, encryption, access controls), vendor lock-in risks (demonstrate multi-vendor support, provide migration paths), integration with legacy infrastructure (show hybrid architectures managing virtual and physical elements), and service reliability (offer SLAs with availability guarantees, document redundancy designs).
Highlight future-proofing: mention cloud-native support (CNF management on Kubernetes), edge deployment capabilities (distributed orchestration, resource-constrained environments), and automation maturity (AI-driven anomaly detection, intent-based management). These capabilities signal ongoing investment and architectural flexibility supporting enterprise evolution.
Conclusion
ETSI NFV represents the standardization framework that underpins network function virtualization for telecom service providers and enterprise networking environments. The framework defines reference architectures, functional blocks (NFVI, VNFs, MANO), standardized interfaces, and interoperability specifications that enable multi-vendor NFV deployments, reducing vendor lock-in and integration complexity.
For vendors selling to enterprise clients, understanding and aligning with ETSI NFV standards is a competitive asset. Standards conformance demonstrates commitment to interoperability, simplifies integration with client infrastructure, and differentiates offerings through ecosystem openness rather than proprietary lock-in. Enterprise buyers increasingly prioritize vendors demonstrating NFV architecture support, orchestration platform capabilities, network automation maturity, and service chaining flexibility—capabilities directly enabled by ETSI NFV frameworks.
Organizations should assess their architectures against ETSI NFV specifications, document compliance with relevant standards (particularly NFV-SOL series for descriptors and APIs), participate in interoperability testing to validate multi-vendor integration, and build enterprise-facing value propositions around virtualization agility, automation efficiency, and flexibility. The transformation from hardware-centric to software-defined network infrastructure creates opportunities for vendors offering managed services, subscription-based models, and outcome-driven engagements—provided implementations align with standardized frameworks that enterprises trust and auditors recognize.
FAQ
Q1: What's the difference between NFV and SDN?
NFV (Network Function Virtualization) decouples network functions from hardware, running them as software (VNFs) on general-purpose infrastructure. SDN (Software-Defined Networking) separates the network control plane from the data plane, centralizing routing decisions and traffic policies in software controllers. NFV virtualizes the functions; SDN virtualizes the connectivity. They complement each other: NFV provides virtualized network functions while SDN provides programmable network connectivity, enabling orchestrated service chains where SDN controllers steer traffic through sequences of VNFs.
Q2: What does VNFs mean, and how are they different from traditional network functions?
Virtual Network Functions (VNFs) are software implementations of network functions—firewalls, load balancers, routers, IDS/IPS—that are traditionally deployed as dedicated hardware appliances. VNFs run on standard compute infrastructure (servers,



.svg)
.svg)
.svg)