Most organizations assess cybersecurity risk using qualitative methods—high, medium, low color charts that generate board presentations without enabling actual decisions. This approach creates a fundamental disconnect between security operations and business strategy, leaving executives unable to answer basic questions: How much risk exposure do we actually carry? What does a potential breach cost? Where should we allocate limited security budgets?
The FAIR Risk Framework (Factor Analysis of Information Risk) is a standard quantitative framework for understanding, analyzing, and quantifying information risk in financial terms, unlike traditional qualitative assessments. FAIR has become the only international standard Value at Risk (VaR) model for cybersecurity and operational risk.
Understanding FAIR matters because enterprise buyers demand vendors demonstrate measurable security postures. Organizations selling to regulated industries or enterprise accounts face increasing scrutiny around quantified risk assessments, audit readiness, and the ability to articulate security investments in business terms. FAIR provides the methodology to translate technical vulnerabilities into financial impact—the language executive stakeholders and procurement teams actually understand.
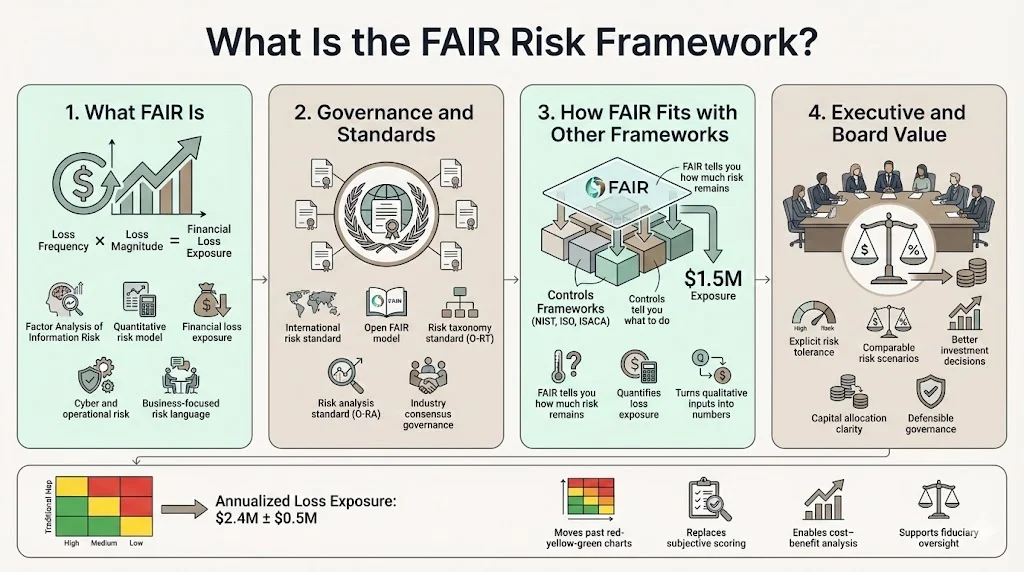
What Is the FAIR Risk Framework?
FAIR (Factor Analysis of Information Risk) is the only international standard Value at Risk (VaR) model for cybersecurity and operational risk. FAIR is a standard taxonomy and quantitative risk analysis model for cybersecurity and operational risk that helps cybersecurity, risk management and business executives measure, manage and communicate risk from the business perspective, in financial terms.
The Open Group has chosen FAIR as the international standard information risk management model, publishing two standards: O-RT (Risk Taxonomy Standard) and O-RA (Risk Analysis Standard), comprising Open FAIR. The Open Group maintains FAIR through a rigorous consensus standards process involving more than 500 member organizations including major technology and consulting firms.
FAIR's risk analysis capabilities complement existing risk management frameworks, filling the gap by providing a proven and standard risk quantification methodology that can be leveraged on top of frameworks like NIST, ISO, and ISACA. While frameworks such as NIST Cybersecurity Framework or ISO 27001 prescribe what security controls to implement, they leave risk quantification methodology largely undefined. FAIR addresses this gap by providing the analytical engine that transforms qualitative control assessments into quantified loss exposure.
The framework originated from a fundamental management challenge: executives needed meaningful measurements to make effective comparisons and well-informed security investment decisions. The FAIR quantitative risk analysis model was conceived as a way to provide meaningful measurements so that it could satisfy management's desire to make effective comparisons and well-informed decisions. Traditional risk matrices using subjective probability scales failed to answer questions about acceptable loss exposure levels or cost-effective control implementation.
FAIR strengthens corporate governance by establishing explicit risk tolerance thresholds based on quantified loss exposure rather than subjective color-coded heat maps. This enables boards and executive leadership to set defensible risk appetites, allocate capital efficiently across security initiatives, and demonstrate due diligence in risk oversight—critical requirements for organizations subject to regulatory scrutiny or fiduciary obligations.
Core Principles of the FAIR Model
Quantitative vs Qualitative Risk Assessment
FAIR provides a model for understanding, analyzing and quantifying cyber risk and operational risk in financial terms, unlike risk assessment frameworks that focus their output on qualitative color charts or numerical weighted scales. Quantitative analysis produces probability distributions and monetary loss estimates rather than subjective categories. This distinction matters because "medium risk" provides no actionable information for resource allocation decisions, while "15% probability of $2-4 million loss annually" enables cost-benefit analysis of specific controls.
Organizations relying on qualitative assessments inevitably face resource allocation conflicts when multiple "high priority" findings compete for limited budgets. Quantitative methods eliminate this ambiguity by expressing risk in comparable units—dollars of probable loss exposure—enabling direct comparison across disparate risk scenarios.
Key Components of FAIR Risk Assessment
The FAIR model assigns a financial value to risk based upon two factors: loss event frequency (the time frame during which a cyber threat actor could affect an identified asset) and loss magnitude (the losses that could stem from the loss event). Both loss event frequency and loss magnitude break down into subcategories that enable a detailed, nuanced understanding of risk.
Loss Event Frequency decomposes into Threat Event Frequency (how often threat agents act against assets) and Vulnerability (the probability that threat actions result in loss events). This separation allows analysts to independently assess threat landscape changes versus control effectiveness—critical for evaluating security investments that reduce vulnerability without affecting threat frequency.
Probable Loss Magnitude encompasses multiple loss forms: productivity losses from inability to deliver products or services, response costs including forensics and remediation, replacement costs for compromised assets, competitive advantage losses, fines and judgments from regulatory penalties, and reputation damage affecting customer relationships. FAIR-MAM (Materiality Assessment Model) helps cyber risk managers consider all applicable forms of loss given specific risk scenarios and develop more accurate and defensible loss estimates using historical or industry benchmark data, which can be used reactively during cybersecurity events and proactively when performing quantitative risk assessments.
The mathematical relationship between these factors produces a loss exposure distribution rather than a single point estimate, explicitly acknowledging uncertainty in both frequency and magnitude estimates. This probabilistic approach provides decision-makers with ranges—minimum expected loss, most likely loss, maximum probable loss—that reflect analytical confidence levels and support risk-informed decisions under uncertainty.
Being able to quantify cyber risk is at the core of any effective risk management program; after all, "You cannot manage what you don't measure." FAIR enables transparency practices through structured risk assessment by requiring explicit documentation of assumptions, data sources, and analytical methods. This auditability distinguishes FAIR from subjective assessments where risk ratings often reflect individual analyst bias rather than consistent, repeatable analysis.
Why Enterprises Use FAIR
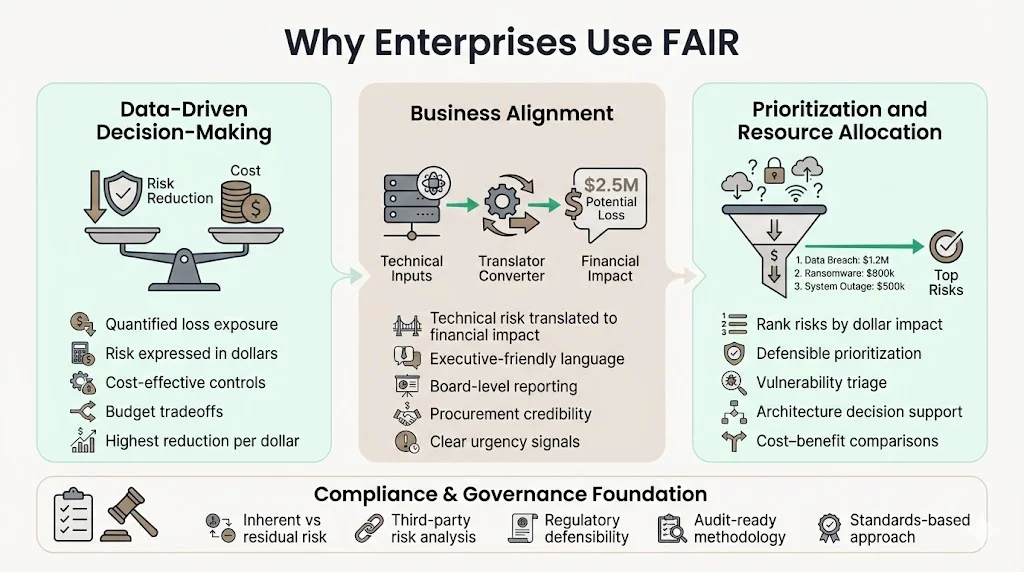
1) Data-Driven Decision-Making
Quantifying cybersecurity risk using the FAIR model offers significant advantages in strategic risk management by clearly articulating risks financially, empowering organizations to make informed decisions, effectively communicating with stakeholders, and proactively managing cybersecurity investments. Organizations allocate security budgets based on competing initiatives claiming critical importance. FAIR analysis determines which initiatives actually reduce loss exposure most cost-effectively.
The responsibility of mature risk professionals is not simply to help their organizations manage risk, but to manage it cost-effectively, and if an organization is able to manage risk more cost-effectively than its competition, then it wins on that level. This economic perspective on security spending supports ethical decision-making by ensuring resources flow toward controls that genuinely protect the organization rather than satisfying compliance checkbox exercises.
2) Business Alignment
Technical security teams typically describe risks in terms of vulnerabilities, exploits, and threat actors—language that fails to resonate with business executives focused on revenue, margins, and shareholder value. Not all organizational leaders are familiar with cybersecurity terminology, and frameworks other than FAIR provide complex insights that are challenging for non-technical members to understand, but FAIR presents results in simple financial terms that decision-makers and team members can easily understand, making the dollar loss help anyone realize the severity of risks and prioritization of cybersecurity defensive measures.
This translation capability proves essential when CISOs present risk posture to boards or when vendors demonstrate security maturity to enterprise procurement teams. A FAIR analysis showing "$4.2 million annual loss exposure from unpatched database vulnerabilities" communicates urgency and justification for remediation investment in ways that "23 critical vulnerabilities identified" cannot achieve.
3) Prioritization and Resource Allocation
FAIR enables precise identification of critical risks and efficient allocation of cybersecurity budgets. Organizations facing hundreds of identified vulnerabilities, compliance gaps, and security improvement opportunities lack objective methods to sequence remediation efforts. FAIR analysis quantifies which scenarios represent highest dollar loss exposure, enabling defensible prioritization based on risk reduction per dollar invested.
This prioritization extends beyond vulnerability management to strategic security architecture decisions. When evaluating whether to implement multi-factor authentication, network segmentation, or enhanced endpoint detection, FAIR analysis estimates loss exposure reduction for each option, supporting cost-benefit comparisons that traditional qualitative assessments cannot provide.
Regulatory frameworks allow for both qualitative and quantitative risk management approaches, but FAIR adoption helps satisfy requirements with a formal, standards-based approach to measure inherent and residual risks, demonstrate financial and operational impact of cyber incidents, and assess third-party and supply-chain vulnerabilities. Organizations subject to SEC cybersecurity disclosure rules, GDPR data protection impact assessments, or HIPAA security risk analyses increasingly rely on FAIR to demonstrate systematic, defensible risk evaluation methodologies to regulators and auditors.
FAIR vs Other Risk Models
Comparing Qualitative and Quantitative Approaches
Risk frameworks from organizations such as NIST, ISO, OCTAVE, and ISACA prescribe the need to quantify risk but leave it up to practitioners to figure it out, with some silent on how to compute risk and frameworks such as NIST 800-30 attempting to measure risk but falling short as they rely on qualitative scales and flawed definitions.
Traditional qualitative models assign risks to categories—typically 3x3 or 5x5 matrices plotting likelihood against impact using subjective scales. These approaches generate consistent problems: different analysts assign different ratings to identical scenarios based on personal risk tolerance; "high" probability means different things across different assessments; ordinal scales (low/medium/high) cannot be meaningfully aggregated or compared; and executive stakeholders cannot determine whether "medium risk" warrants investment or acceptance.
Quantitative FAIR analysis produces probability distributions and monetary loss estimates—cardinal measurements enabling mathematical operations, aggregation across risk scenarios, and direct comparison with security control costs. The measurement precision supports decision impact that qualitative categories fundamentally cannot provide: determining whether proposed $500,000 security investment is cost-justified requires knowing whether it reduces annual loss exposure by more than $500,000.
Integration with Compliance Standards
FAIR is not a cybersecurity framework like NIST CSF and cannot be used as a framework, but is a complementary methodology that works alongside frameworks like NIST, ISO 2700x, and other industry-standard frameworks, also complementing risk assessment frameworks such as ISO/IEC 27002, ITIL, OCTAVE, COBIT, and COSO by providing a scientific and quantitative approach to risk analysis.
Organizations implement ISO 27001 information security management systems or adopt NIST Cybersecurity Framework profiles to establish control baselines and security programs. FAIR operates as the analytical layer that quantifies residual risk remaining after control implementation, enabling measurement of whether security programs actually achieve acceptable loss exposure levels. By using FAIR in conjunction with risk management processes such as ISO 27005, organizations gain comprehensive identification and classification of risks, detailed quantitative analysis and prioritization of risks, and alignment of cybersecurity efforts with business outcomes through financial quantification.
The complementary relationship means FAIR enhances rather than replaces existing frameworks. Organizations continue using NIST CSF for security program structure, ISO 27001 for ISMS implementation, and FAIR for quantifying whether implemented controls reduce loss exposure to acceptable levels.
Qualitative insights still matter alongside FAIR's quantitative outputs. Qualitative assessments identify risk scenarios, describe threat actor capabilities and motivations, and capture expert judgment about emerging threats. FAIR transforms these qualitative inputs into quantified loss exposure estimates, combining subject matter expertise with structured analytical methods to produce defensible risk measurements.
Implementing FAIR in Your Organization
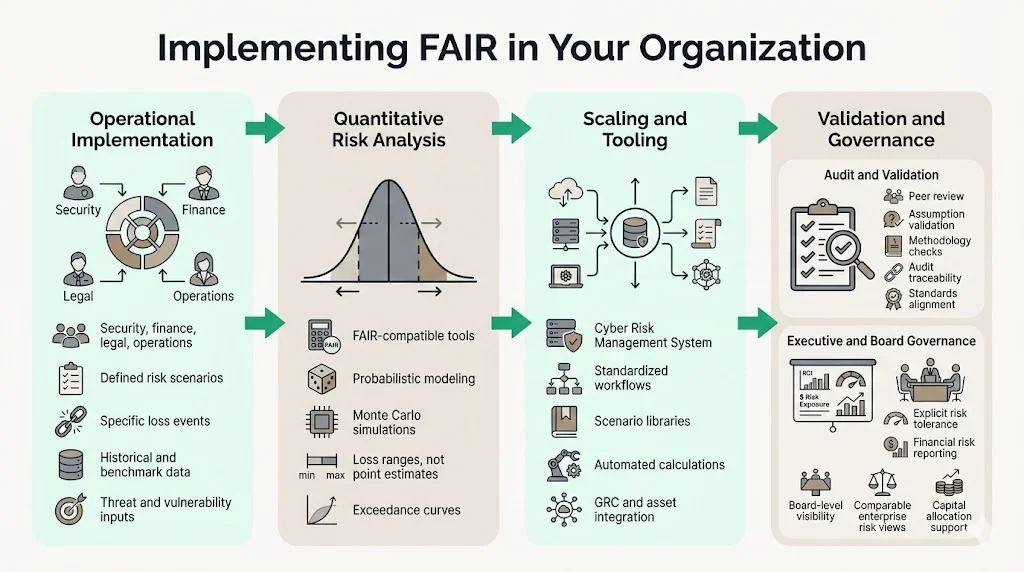
Operational Implementation Steps
Establish cross-functional teams including cybersecurity, finance, and operational risk professionals. FAIR implementation requires collaboration across functions because accurate loss estimates demand input from business units owning affected assets, finance teams understanding cost structures, legal counsel assessing regulatory exposure, and security practitioners evaluating control effectiveness.
Clearly articulate and document plausible cyber risk scenarios relevant to your organization, including data breaches, ransomware attacks, and unauthorized access incidents, then collect historical incident data, industry benchmarks, threat intelligence, and vulnerability reports, as reliable data is critical for accurate FAIR assessments. Scenario definition requires specificity—"data breach" proves too broad for meaningful analysis, while "unauthorized database access exposing 100,000 customer PII records via unpatched SQL injection vulnerability" provides the concrete detail FAIR analysis demands.
Data collection represents the most resource-intensive implementation phase. Organizations require historical loss data from prior incidents, industry benchmark data reflecting similar organizations' loss experiences, threat intelligence indicating attack frequency for relevant threat actor populations, and vulnerability data showing control gaps enabling loss events. Implementing FAIR can pose challenges including data availability and quality, as obtaining reliable data to support precise analysis can be difficult, and complexity requires specialized skills and training in probabilistic modeling and statistical analysis.
Using FAIR-compatible software tools, perform probabilistic analysis that produces quantified risk assessments, with results typically expressed as ranges or distributions capturing uncertainty and variability. Monte Carlo simulation techniques generate loss exceedance curves showing probability of losses exceeding specific thresholds—essential information for determining risk tolerance levels and appropriate risk transfer mechanisms like cyber insurance.
Scaling and Tool Selection
A Cyber Risk Management System (CRMS) is necessary for operationalizing the FAIR Framework by ensuring processes are efficient, repeatable, and actionable, centralizing the data and workflows needed for managing the entire cyber risk management process. Organizations conducting dozens or hundreds of FAIR analyses annually require technology platforms that standardize scenario documentation, maintain libraries of loss data and distribution parameters, automate Monte Carlo calculations, and generate consistent reporting formats.
Tool selection should prioritize platforms integrating with existing GRC systems, vulnerability management tools, and asset inventories to reduce duplicate data entry. FAIR analysis quality depends on current, accurate asset and vulnerability data—manual data collection creates sustainability challenges that undermine long-term program viability.
Validation Through Auditing
Auditing processes validate FAIR outcomes by reviewing scenario definitions for completeness, examining data sources and assumptions for reasonableness, verifying calculation methodologies against FAIR standards, and comparing risk estimates against historical loss experiences. Validate assumptions regularly through peer reviews and scenario analyses. Organizations establishing FAIR programs should implement peer review requirements where senior risk analysts validate scenarios and estimates produced by junior analysts before presenting to leadership.
Internal audit teams increasingly scrutinize enterprise risk management processes, including cyber risk quantification methodologies. FAIR's status as an international standard and explicit documentation requirements facilitate audit validation—auditors can verify whether analyses follow established taxonomy and calculation methods, unlike qualitative assessments based on undocumented expert judgment.
Strengthening Corporate Governance
Risk management consists of decisions and execution, with those decisions related to the risk governance that the organization decides to implement, and what an organization actually gets in terms of risk is a function of execution within the context of those decisions. FAIR strengthens corporate governance by aligning risk results with leadership goals through explicit, measurable risk tolerance statements.
Boards increasingly demand cyber risk reporting in financial terms comparable to other enterprise risks. FAIR enables this reporting standardization, allowing board risk committees to evaluate cyber risk exposure using the same Value at Risk frameworks applied to credit risk, operational risk, and market risk in other business areas. This consistency supports integrated enterprise risk management and informed capital allocation across all risk categories.
Common Challenges and Best Practices
Typical Adoption Obstacles
Data availability and quality challenges represent the primary FAIR implementation barrier. Organizations lack historical loss data for low-frequency, high-impact events, forcing reliance on industry benchmarks that may not reflect specific organizational risk profiles. Threat intelligence rarely provides the statistical frequency data FAIR analysis requires, necessitating expert estimation methods that introduce uncertainty.
Organizational culture presents challenges as transitioning from qualitative assessments to a quantitative approach demands significant cultural and procedural adjustments. Security practitioners accustomed to qualitative risk assessments resist probabilistic analysis requirements, viewing confidence intervals and distribution parameters as unnecessary complexity. Leadership teams unfamiliar with statistical reasoning may misinterpret probability distributions, expecting single "correct" answers rather than ranges reflecting analytical uncertainty.
FAIR relies mainly on probability, and although these probabilities are not baseless, they are not entirely accurate because of the different nature of cyber-attacks and their damage. Critics correctly note that low-frequency, high-impact cyber events lack the statistical history enabling actuarial precision. However, this criticism applies equally to qualitative assessments—subjective "low probability" ratings contain identical uncertainty, simply without explicit acknowledgment.
Implementation Best Practices
Addressing challenges involves careful planning, training initiatives, and gradual integration into organizational practices. Organizations should start with high-value assets and well-understood risk scenarios where loss data exists, building analytical capability and stakeholder confidence before tackling low-frequency scenarios requiring extensive expert estimation.
Combine FAIR with other risk frameworks rather than attempting wholesale replacement of existing processes. Organizations already conducting ISO 27001 risk assessments or NIST CSF implementation should overlay FAIR analysis on existing scenario identification and control evaluation work, adding quantification without discarding established programs.
Use iterative reviews for continuous improvement rather than expecting analytical perfection in initial implementations. FAIR analyses improve as organizations accumulate incident data, refine loss magnitude estimates based on actual events, and calibrate threat frequency assumptions against observed attack patterns. Document assumptions explicitly to enable systematic updating as new information emerges.
IT environments are dynamic in the digital age, with new threats and vulnerabilities identified frequently, and config updates, patches, upgrades, and new code releases being continuous features of the modern technology landscape, so understanding current risk exposure requires a calculation engine to keep up with daily changes and to take swift, targeted, and efficient action to keep risk exposure at acceptable levels. Risk mitigation strategies based on FAIR insights require continuous monitoring rather than annual assessment cycles. Organizations implementing FAIR should establish automated data feeds updating asset inventories, vulnerability status, and threat intelligence inputs, enabling near-real-time risk exposure recalculation as conditions change.
Case Examples or Hypothetical Scenarios
Quantifying Cyber Risk in Financial Terms
Consider an enterprise SaaS provider evaluating ransomware risk to their production infrastructure. Traditional qualitative assessment rates this "high probability, high impact"—providing no decision-making value when competing against other "high" rated risks for limited security budget.
FAIR analysis decomposes the scenario: Threat Event Frequency estimates ransomware groups target similar SaaS providers 8-12 times annually based on threat intelligence. Vulnerability analysis determines 35% probability that attacks bypass existing email filtering and endpoint protection controls, resulting in Loss Event Frequency of 2.8-4.2 events annually. Loss Magnitude analysis estimates $3-7 million per incident including ransom payments, system recovery costs, customer notification expenses, regulatory fines under data protection laws, and revenue losses during service outages. This produces annual loss exposure of $8.4-29.4 million with $15 million most likely estimated.
This quantified analysis transforms prioritization decisions. When the security team proposes $2 million investment in enhanced endpoint detection and response capabilities expected to reduce vulnerability by 60%, executives can evaluate whether $1.7 million annual cost justifies estimated $9 million annual loss exposure reduction. The same cost-benefit analysis proves impossible with qualitative "high risk" ratings.
Regulatory Requirements and Compliance Reporting
An enterprise healthcare technology vendor faces HIPAA security rule compliance requirements and customer audit demands for documented risk assessments. Their previous qualitative assessments satisfied minimal compliance requirements but failed to support actual security investment decisions.
Implementing FAIR enables the organization to quantify protected health information (PHI) breach scenarios in financial terms reflecting HIPAA civil monetary penalties, state breach notification costs, class action litigation exposure, and customer contract penalties. These quantified estimates support demonstrable compliance with HIPAA's required risk analysis provisions while simultaneously informing budget allocation toward controls reducing breach probability.
When enterprise healthcare customers audit the vendor's security program, FAIR-based risk reporting demonstrates sophisticated risk management maturity exceeding typical vendor assessments. The quantified approach provides customer security teams with concrete evidence supporting vendor risk acceptance decisions rather than subjective assurances of "adequate" security.
Conclusion
The FAIR quantitative risk analysis model defines risk management as the combination of personnel, policies, processes and technologies that enable an organization to cost-effectively achieve and maintain an acceptable level of loss exposure, defining the necessary building blocks for implementing effective cyber risk management programs. Organizations treating cybersecurity as a technical discipline rather than a business risk management function inevitably struggle to justify security investments, prioritize competing initiatives, and communicate risk posture to executive stakeholders.
FAIR provides the analytical framework that transforms cybersecurity from compliance exercise into strategic risk management discipline. For companies selling to enterprise clients, understanding FAIR demonstrates risk management maturity that procurement teams increasingly demand. Organizations articulating security posture in quantified financial terms differentiate themselves from competitors relying on generic compliance certifications and subjective security assurances.
Research shows quantitative approaches like FAIR are reshaping decision-making at senior leadership and board levels. The shift toward quantified cyber risk assessment reflects broader enterprise recognition that cybersecurity represents a material business risk requiring the same rigorous analysis applied to financial, operational, and strategic risks. FAIR enables this analytical discipline as part of mature risk management programs where security investments face the same cost-benefit scrutiny as other capital allocation decisions.
FAQ Section
1) What is the FAIR Risk Framework?
The FAIR Model (Factor Analysis of Information Risk) is a quantitative risk analysis framework that helps organizations assess and quantify cyber risks in monetary terms. FAIR decomposes risk into measurable factors including Loss Event Frequency and Probable Loss Magnitude, applying probabilistic analysis to produce financial loss exposure estimates rather than subjective risk ratings.
2) Why do enterprises use FAIR for cyber risk?
FAIR empowers organizations to make informed decisions, effectively communicate with stakeholders, and proactively manage cybersecurity investments by clearly articulating risks financially. Quantifying risk in financial terms enables cost-benefit analysis of security controls, defensible budget allocation across competing initiatives, and board-level risk reporting using the same Value at Risk frameworks applied to other enterprise risks.
3) How is FAIR different from qualitative risk models?
Unlike traditional risk assessments which focus on qualitative measures (high, medium, low), FAIR provides metrics about dollars and cents. Qualitative models produce ordinal categories that cannot be mathematically aggregated or compared with control costs. FAIR generates probability distributions and monetary loss estimates—cardinal measurements enabling cost-benefit analysis and objective prioritization based on risk reduction per dollar invested.
4) Who should own FAIR inside a company?
FAIR implementation typically resides within risk management functions, with ownership shared among Chief Information Security Officers responsible for security program effectiveness, enterprise risk management leaders coordinating cross-functional risk assessment, and quantitative risk analysts performing FAIR calculations. Effective programs establish cross-functional teams including cybersecurity, finance, legal, and business unit representatives contributing scenario definitions, loss estimates, and control effectiveness assessments.
5) Is FAIR required for compliance?
Regulatory frameworks allow for both qualitative and quantitative risk management approaches, but FAIR adoption helps satisfy requirements with a formal, standards-based approach. FAIR itself is not mandated by specific regulations, but it supports meeting compliance standards requiring documented risk assessments, including ISO 27001 risk treatment requirements, HIPAA security risk analysis provisions, GDPR data protection impact assessments, and SEC cybersecurity risk management disclosure rules. Organizations using FAIR demonstrate systematic, defensible risk evaluation methodologies to regulators and auditors.



.svg)
.svg)
.svg)