Most organizations evaluating cloud service providers treat security certifications as checkboxes rather than operational indicators. This creates a fundamental gap between documented controls and actual data protection—a gap that becomes apparent when incident response, regulatory scrutiny, or federal procurement requirements surface. FedRAMP (Federal Risk and Authorization Management Program) addresses this gap by establishing a standardized security assessment, authorization, and continuous monitoring framework specifically designed for cloud environments handling government data.
Cloud adoption introduces inherent data protection challenges: multi-tenant architectures, dynamic infrastructure, distributed data storage, and shared responsibility models that complicate traditional security approaches. Organizations selling to government agencies or enterprise clients with stringent security requirements need demonstrable, independently verified security postures. FedRAMP provides that verification through rigorous, standardized assessment processes that extend beyond compliance theater into operational security discipline.
What is FedRAMP?
A Clear OverviewFedRAMP is a United States federal government-wide compliance program that provides a standardized approach to security assessment, authorization, and continuous monitoring for cloud products and services. The purpose of FedRAMP is to increase Federal agencies' adoption and secure use of commercial cloud, by providing a standardized, reusable approach to security assessments and authorizations for cloud computing products and services.
Congress passed the FedRAMP Authorization Act in 2022, formally establishing FedRAMP within the General Services Administration. The Act established FedRAMP within GSA and created a FedRAMP Board to provide input and recommendations to the Administrator of GSA. The Act requires OMB to issue guidance defining the scope of FedRAMP, establishing requirements for the use of the program by Federal agencies, and promoting consistency in security assessment practices.
FedRAMP's security baselines are derived from NIST SP 800-53 with a set of control enhancements that pertain to the unique security requirements of cloud computing. A FedRAMP authorization follows the steps in NIST Special Publication 800-37, Risk Management Framework for Information Systems and Organizations, but the control baselines used have been specifically tailored for cloud offerings. This tailoring addresses cloud-specific risks: shared responsibility models, multi-tenancy, virtualization layers, dynamic resource allocation, and distributed data processing that traditional security frameworks don't adequately address.
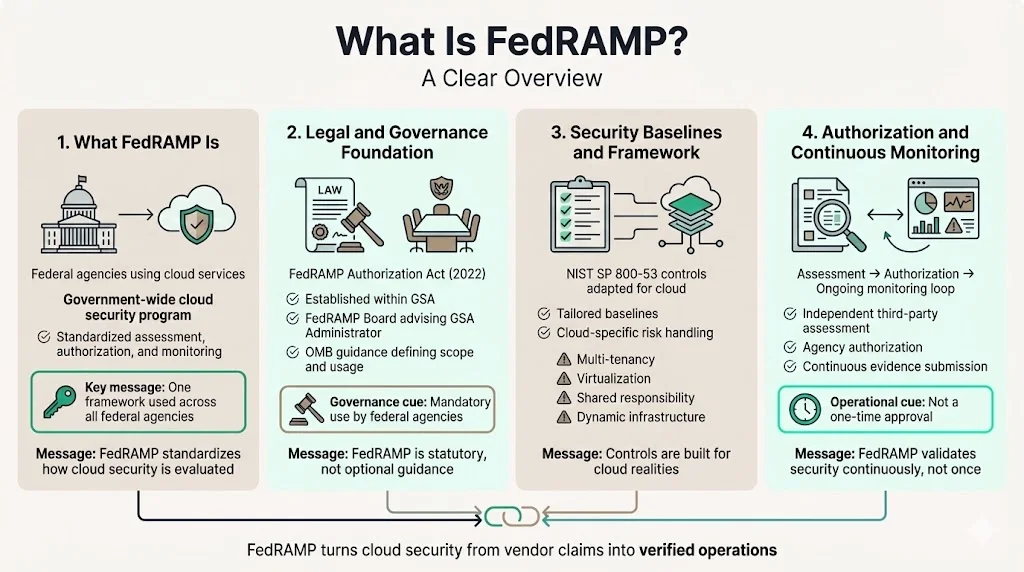
FedRAMP extends beyond static compliance documentation into operational security discipline. The framework mandates documented evidence of control effectiveness, independent third-party assessment, agency authorization, and continuous monitoring—transforming cloud security from vendor assertions into independently verified, continuously validated security postures.
Why FedRAMP Matters for Data Protection
Cloud environments introduce fundamental data protection challenges absent in traditional infrastructure: data distributed across geographically dispersed facilities, dynamic compute resources that scale on demand, shared infrastructure serving multiple tenants, abstracted storage layers complicating data lifecycle management, and complex supply chains involving subprocessors and infrastructure providers. These architectural realities demand security approaches beyond perimeter-based controls and static authorization processes.
FedRAMP addresses these challenges by establishing security requirements specifically designed for cloud architectures. The framework ensures confidentiality through encryption requirements, access controls, and multi-tenant isolation mechanisms; integrity through change management controls, configuration management, and audit logging; and availability through incident response capabilities, business continuity planning, and continuous monitoring of security posture.
Through centralization, FedRAMP reduces duplicative authorization activities, allowing CSPs to deliver and agencies to adopt secure cloud services more efficiently. Rather than requiring cloud service providers to undergo separate security assessments for each federal customer—creating inconsistent security baselines and wasting resources—FedRAMP establishes a single standardized authorization reusable across agencies. This "authorize once, use many times" approach creates operational efficiency while maintaining rigorous security standards.
For enterprise clients evaluating cloud service providers, FedRAMP authorization signals demonstrated commitment to operational security beyond marketing claims. Organizations that achieve FedRAMP authorization have undergone independent assessment of hundreds of security controls, documented their security architectures, demonstrated evidence collection capabilities, and committed to continuous monitoring obligations. This verification extends beyond compliance theater into actual security implementation—a distinction critical for risk management.
The Core FedRAMP Process: Assessment to Authorization
FedRAMP authorization follows a structured lifecycle designed to verify security control implementation, grant formal authorization, and maintain continuous assurance. Understanding this process clarifies why FedRAMP authorization represents substantive security investment rather than documentation exercise.
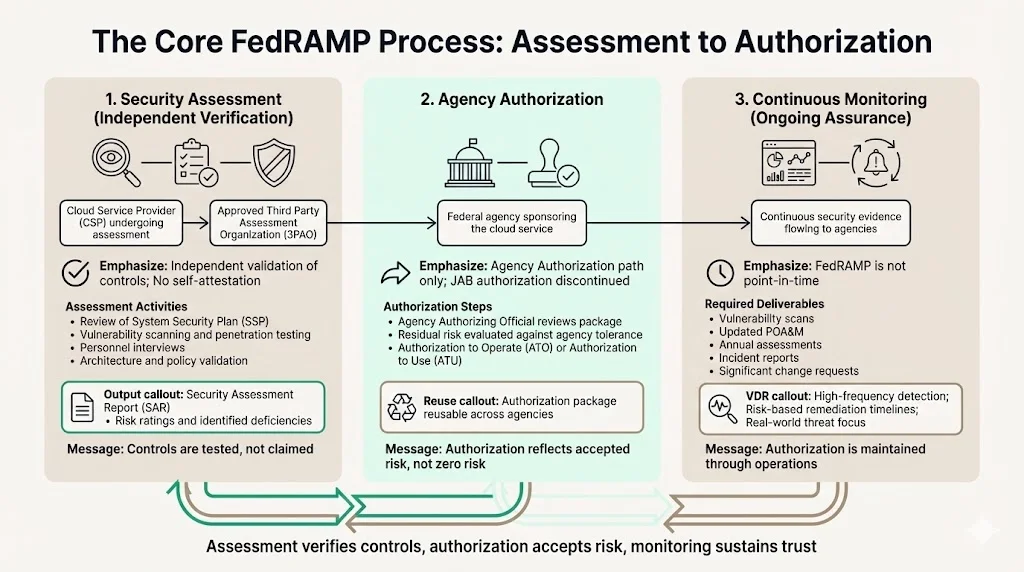
Security Assessment
Third-party assessment organizations (3PAOs) play a critical role in the FedRAMP security assessment process, as they are the independent assessment organizations that verify cloud providers' security implementations and evaluate overall risk posture. FedRAMP requires organizations to have assessments conducted by an approved Third Party Assessment Organization (3PAO) to achieve their security status.
3PAO assessments examine control implementation across technical, operational, and administrative domains. Assessors review system security plans, test technical controls through vulnerability scanning and penetration testing, interview personnel to verify operational procedures, examine documentation demonstrating policy implementation, and validate security architectures against FedRAMP baseline requirements. This assessment produces a Security Assessment Report documenting findings, identifying control deficiencies, and establishing risk ratings for discovered vulnerabilities.
The depth and rigor of 3PAO assessments distinguish FedRAMP from self-attestation approaches. Independent verification ensures control implementation claims withstand scrutiny, identifies gaps requiring remediation before authorization, and provides agencies with objective security posture assessments rather than vendor marketing materials.
Authorization
Agencies leverage the FedRAMP authorization package to issue their own "authorization to operate" (ATO) or "authorization to use" (ATU). In 2024, FedRAMP discontinued the JAB Authorization option, leaving just the Agency Authorization path as the primary route to FedRAMP authorization.
In the Agency Authorization path, CSPs need to find a federal agency to sponsor their CSO as they strive to achieve an Authority to Operate (ATO). The sponsoring agency's Authorizing Official reviews the security assessment package, evaluates residual risks, determines whether those risks align with the agency's risk tolerance, and formally authorizes the cloud service for operational use.
Once a cloud service has completed a FedRAMP authorization process, FedRAMP establishes that the security posture of the product or service has been assessed and is presumptively adequate for use by Federal agencies. This presumption of adequacy enables other agencies to leverage existing authorization packages rather than conducting redundant assessments—though agencies may impose additional requirements based on specific mission needs or data sensitivity.
Continuous Monitoring
FedRAMP authorization isn't a point-in-time certification—it requires sustained security operations and evidence production demonstrating ongoing control effectiveness. To meet continuous monitoring requirements, Agency Authorization CSPs must provide periodic security deliverables (vulnerability scans, updated POA&M, annual security assessments, incident reports, significant change requests) to all agency customers.
The Vulnerability Detection and Response (VDR) standard overhauls continuous monitoring expectations to focus on secure outcomes from real-world context-sensitive decisions about weaknesses and threats, requires persistently recurring detection of weaknesses at much higher frequency and depth than traditional vulnerability scanning requirements, and mandates remediation timeframes appropriate for current threat environments. This continuous monitoring approach ensures security postures remain current as threats evolve, infrastructure changes, and new vulnerabilities emerge.
The continuous monitoring obligation represents the operational discipline that separates genuine security programs from compliance theater. Organizations maintaining FedRAMP authorization must sustain evidence collection capabilities, vulnerability management processes, incident response procedures, and change management controls throughout the authorization period—not just during initial assessment.
FedRAMP and Cloud Service Providers
Per the OMB memorandum, any cloud services that hold federal data must be FedRAMP authorized. This requirement makes FedRAMP authorization mandatory for CSPs targeting federal customers. Beyond regulatory compliance, FedRAMP authorization increasingly influences enterprise procurement decisions as non-government organizations recognize the framework's rigorous security standards.
Cloud service providers pursuing FedRAMP authorization must implement security controls aligned with NIST 800-53 baselines tailored for cloud environments, document their security architectures and operational procedures, undergo independent third-party assessment, establish continuous monitoring capabilities, and maintain evidence collection systems supporting ongoing authorization requirements. This represents significant investment: security control implementation, documentation development, 3PAO assessment costs, remediation of identified deficiencies, and sustained operational overhead for continuous monitoring.
FedRAMP defines impact levels—Moderate and High—determining the scope and rigor of required security controls. Moderate impact level addresses cloud systems where loss of confidentiality, integrity, or availability could cause serious adverse effects on organizational operations, assets, or individuals. High impact level applies when such losses could cause severe or catastrophic adverse effects. Impact level selection drives the control baseline: Moderate requires implementing approximately 325 security controls; High demands roughly 421 controls with enhanced implementation requirements.
Organizations achieving FedRAMP authorization gain competitive advantage beyond federal market access. Enterprise clients evaluating cloud providers increasingly reference FedRAMP as a security baseline, recognizing that FedRAMP-authorized providers have demonstrated security maturity through independent verification. This credibility extends into risk management discussions, procurement evaluations, and vendor security assessments—reducing friction in enterprise sales cycles.
How FedRAMP Maps to Broader Compliance and Security Standards
FedRAMP operates within the broader NIST Risk Management Framework (RMF), adapting RMF's systematic approach to security authorization for cloud-specific requirements. The NIST RMF establishes a disciplined process for integrating security and risk management into system development lifecycles: categorize information systems based on impact, select appropriate security controls, implement those controls, assess control effectiveness, authorize system operation, and continuously monitor security posture.
FedRAMP tailors NIST 800-53 control baselines specifically for cloud architectures, adding requirements addressing multi-tenancy, virtualization security, cloud service models (IaaS, PaaS, SaaS), and shared responsibility between CSPs and customers. This tailoring recognizes that generic security controls require cloud-specific implementation guidance: hypervisor security for virtualized environments, API security for cloud service interfaces, tenant isolation mechanisms for multi-tenant architectures, and data protection controls accounting for distributed storage systems.
Organizations maintaining multiple compliance frameworks—SOC 2, ISO 27001, HIPAA, PCI DSS—find FedRAMP controls provide foundational security implementations supporting other frameworks. FedRAMP's comprehensive control baseline often exceeds requirements of commercial certifications, creating control overlap that reduces total compliance burden. Organizations implementing FedRAMP controls can map those implementations to other framework requirements, leveraging evidence collected for FedRAMP across multiple audit programs.
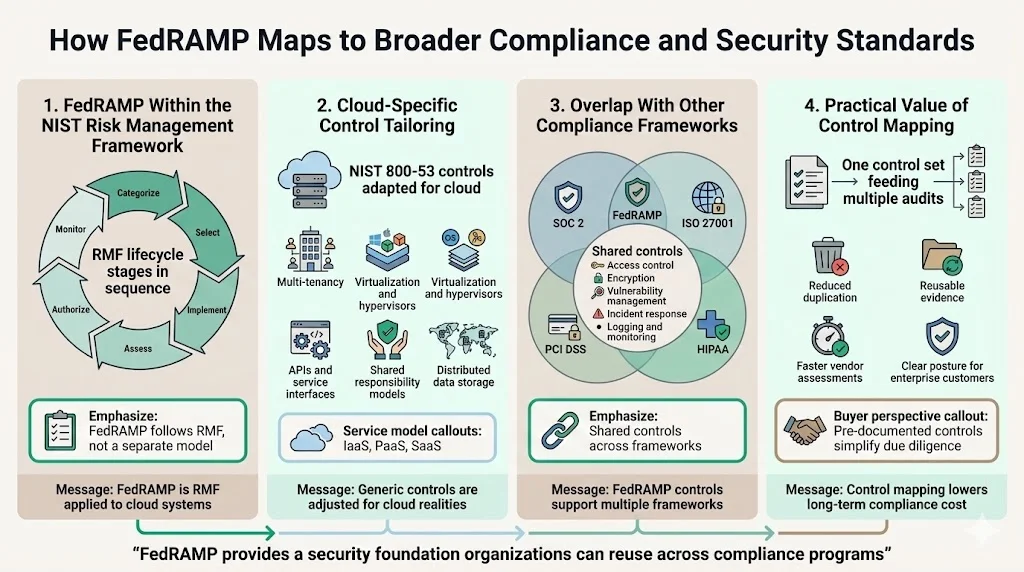
The NIST 800-53 foundation enables control mapping exercises that demonstrate how FedRAMP implementations satisfy requirements across different regulatory regimes. This control mapping clarifies security posture for enterprise clients maintaining their own compliance obligations, accelerates vendor security assessments by providing detailed control documentation, and supports customer audit requirements by offering pre-documented evidence of security control implementation.
Benefits for Enterprises Buying Cloud Services
Enterprise clients evaluating cloud service providers face complex security assessment challenges: verifying vendor security claims, evaluating control implementation effectiveness, assessing ongoing security operations maturity, and determining whether vendor security postures align with internal risk tolerance. FedRAMP authorization simplifies this evaluation by providing independently verified security assessments conducted by accredited third-party organizations.
Organizations can leverage FedRAMP authorization packages during vendor risk assessments, reducing assessment timelines and resource requirements. Rather than conducting comprehensive security audits of every cloud provider, enterprises can review existing FedRAMP documentation, focus additional due diligence on organization-specific requirements not covered by FedRAMP baselines, and expedite procurement decisions based on documented security postures. This efficiency particularly benefits organizations with limited security assessment resources or aggressive cloud adoption timelines.
FedRAMP authorization enables enterprises to benchmark cloud provider security maturity against standardized criteria. The framework's comprehensive control baseline provides objective comparison points across vendors, clarifies security capability differences between providers, and informs risk-based procurement decisions. Organizations can evaluate whether provider security implementations align with their data protection policies, compliance obligations, and risk management frameworks.
For enterprises subject to regulatory requirements—healthcare organizations under HIPAA, financial services firms under GLBA or PCI DSS, organizations handling European personal data under GDPR—FedRAMP-authorized providers demonstrate security practices supporting compliance obligations. While FedRAMP doesn't directly address industry-specific regulations, the framework's rigorous security controls provide foundational protections applicable across regulatory regimes.
Pitfalls and Common Misconceptions
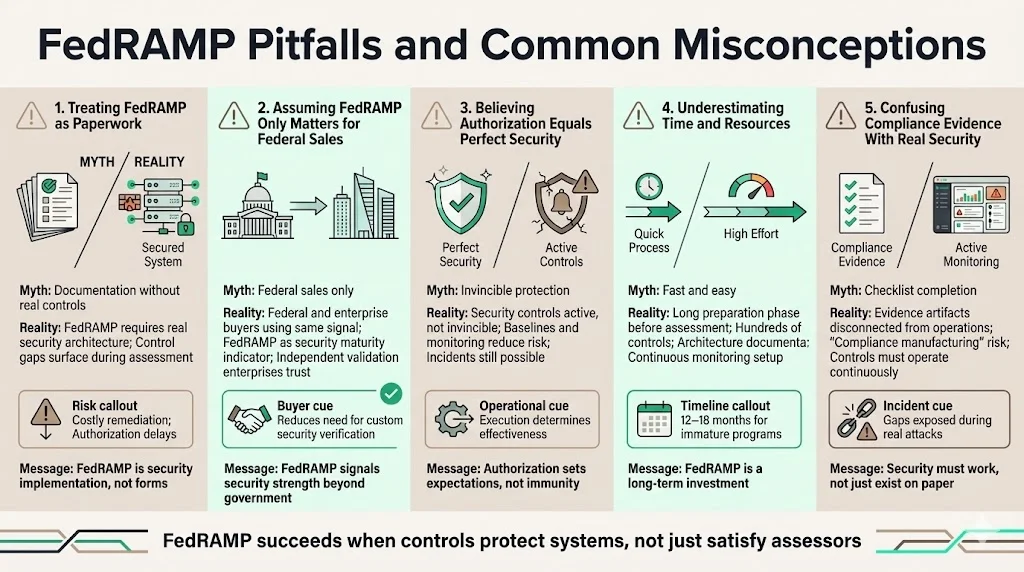
FedRAMP authorization represents substantive security implementation, not bureaucratic paperwork exercise. Organizations treating FedRAMP as documentation project rather than security transformation inevitably face difficulties: inadequate security architectures discovered during assessment, control implementation gaps requiring expensive remediation, continuous monitoring obligations exceeding operational capabilities, and authorization delays stemming from insufficient preparation.
A common misconception holds that FedRAMP only matters for federal sales opportunities. This perspective underestimates FedRAMP's value as a security maturity indicator for enterprise clients. Organizations achieving FedRAMP authorization have demonstrated security capabilities and many enterprises lack internal resources to verify independently. FedRAMP authorization signals investment in operational security beyond marketing claims—a distinction critical for risk-conscious buyers.
Another misconception assumes FedRAMP authorization guarantees perfect security. No framework eliminates all risks, and FedRAMP authorization doesn't prevent security incidents. The framework establishes security baselines, mandates control implementation, requires continuous monitoring, and demands incident response capabilities—but security effectiveness ultimately depends on operational execution. Organizations must maintain the security discipline that earned authorization rather than treating certification as an endpoint.
Cloud service providers commonly underestimate FedRAMP preparation timelines and resource requirements. Achieving authorization requires implementing hundreds of security controls, documenting security architectures and procedures, remediating control deficiencies identified during assessment, and establishing continuous monitoring capabilities. Organizations lacking mature security programs face 12-18 month implementation timelines before 3PAO assessment even begins. Providers should approach FedRAMP as a multi-year security maturity initiative rather than a short-term compliance project.
The distinction between FedRAMP authorization and actual security posture matters. Some organizations focus on generating evidence artifacts satisfying auditors rather than implementing controls that actually protect systems—a "compliance manufacturing" approach that produces documentation without security. This gap becomes apparent during incidents, when documented controls fail to prevent or detect compromise. Genuine FedRAMP authorization requires security controls operating as designed, not security theater satisfying assessment requirements.
Conclusion
FedRAMP establishes rigorous security standards for cloud services through standardized assessment, formal authorization, and continuous monitoring requirements. The framework addresses cloud-specific data protection challenges by tailoring NIST security controls for multi-tenant architectures, shared responsibility models, and distributed infrastructure that characterize modern cloud environments. Organizations achieving FedRAMP authorization demonstrate security maturity through independent third-party verification, documented control implementation, and sustained operational discipline.
For cloud service providers, FedRAMP authorization opens federal market opportunities while enhancing credibility with security-conscious enterprise clients. For enterprises evaluating cloud providers, FedRAMP authorization simplifies vendor risk assessment by providing independently verified security documentation, enables security maturity benchmarking across providers, and supports internal compliance obligations through comprehensive security control baselines. FedRAMP represents operational security investment rather than compliance checkbox—a distinction that matters when security controls must actually protect systems rather than merely impress auditors.
FAQs
1) What is FedRAMP?
FedRAMP (Federal Risk and Authorization Management Program) is a U.S. government-wide program providing standardized security assessment, authorization, and continuous monitoring for cloud products and services. The program establishes security baselines based on NIST 800-53 controls tailored for cloud architectures, requires independent third-party assessment of control implementation, and mandates ongoing monitoring demonstrating sustained security posture. FedRAMP ensures cloud services handling federal data meet consistent security standards across agencies.
2) Who needs FedRAMP authorization?
Any cloud service provider selling to federal agencies handling government data requires FedRAMP authorization. This includes SaaS applications, PaaS platforms, and IaaS infrastructure serving federal customers. Beyond regulatory requirements, many enterprise organizations reference FedRAMP authorization when evaluating cloud provider security maturity, making authorization valuable for CSPs targeting security-conscious commercial clients even without direct federal sales.
3) What are FedRAMP impact levels?
FedRAMP defines impact levels—Moderate and High—determining security control scope and implementation rigor. Moderate impact level applies when loss of confidentiality, integrity, or availability could cause serious adverse effects, requiring approximately 325 security controls. High impact level addresses scenarios where such losses could cause severe or catastrophic effects, demanding roughly 421 controls with enhanced implementation requirements. Impact level selection depends on data sensitivity and system criticality.
4) How long does FedRAMP approval take?
Authorization timelines vary significantly based on security program maturity and preparation thoroughness. Organizations with mature security programs typically achieve authorization in 12-18 months, including control implementation, documentation development, 3PAO assessment, deficiency remediation, and agency authorization. Organizations lacking established security programs may require 24+ months for control implementation before assessment begins. Factors influencing timelines include existing security control maturity, organizational readiness, 3PAO availability, complexity of cloud architecture, and sponsoring agency review processes.
5) Is FedRAMP required for all federal agencies?
Yes, federal agencies must follow FedRAMP processes when authorizing cloud services handling government data. OMB policy mandates agencies use FedRAMP when assessing, authorizing, and continuously monitoring cloud services, ensuring consistent security standards across federal cloud deployments. Agencies leverage FedRAMP authorization packages to issue their own authorization decisions rather than conducting independent assessments, though agencies may impose additional requirements based on specific mission needs or data sensitivity classifications.



.svg)
.svg)
.svg)