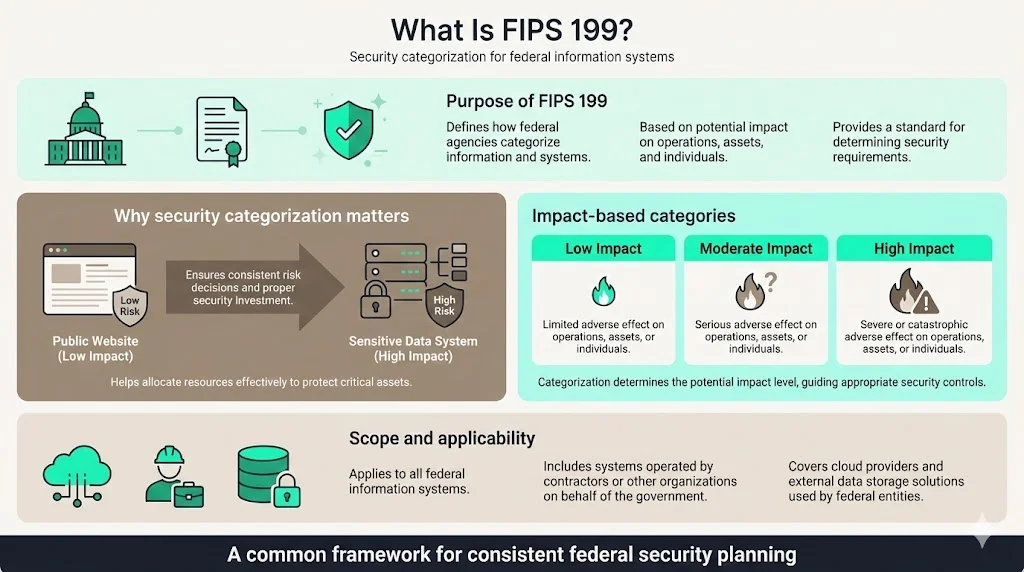
FIPS 199 provides a standard for categorizing federal information and information systems according to an agency's level of concern for confidentiality, integrity, and availability and the potential impact on agency assets and operations should their information and information systems be compromised. Most enterprise vendors pursuing federal contracts treat information categorization as a checkbox exercise rather than a foundational security decision. This approach creates gaps in risk planning and control implementation—gaps that become evident when authorization packages fail to align with actual system criticality or when auditors question the rationale behind security control selection.
For companies selling into federal markets, FIPS 199 determines how federal agencies and their contractors must classify data sensitivity and system impact before implementing security controls. The categorization you document under FIPS 199 directly influences which security requirements apply, how extensive your authorization process becomes, and what level of continuous monitoring your systems require. Understanding this standard means understanding the entry requirements for federal information system authorization.
What FIPS 199 Is
FIPS Publication 199 addresses FISMA's mandate to develop standards for categorizing information and information systems. FIPS 199 and FIPS 200 are mandatory security standards as required by FISMA. The standard establishes a systematic methodology for federal agencies to determine the security category of information and information systems based on potential impact to organizational operations, assets, and individuals.
FIPS 199 exists because federal agencies manage information with vastly different security implications. A public-facing informational website requires fundamentally different protection than systems processing classified intelligence or personally identifiable information. Without a standardized categorization approach, agencies would apply inconsistent risk judgments and misallocate security resources. Security categorization standards provide a common framework and understanding for expressing security, enabling consistent security planning across civilian and national security organizations.
The standard applies to federal information systems regardless of whether data exists in electronic or non-electronic form. This scope encompasses contractor-operated systems processing federal information, cloud service providers seeking FedRAMP authorization, and any third party handling federal data under contract.
What FIPS Stands For
Federal Information Processing Standards represent mandatory requirements for federal agencies. Federal Information Processing Standards Publications (FIPS PUBS) were developed by NIST to guide the categorization of information and information systems. The FIPS series covers diverse technical areas from cryptographic standards to data categorization requirements. FIPS 199 occupies a specific position within this series as the foundational standard for security categorization—the starting point for all subsequent security planning and control selection decisions.
Core Concepts of FIPS 199
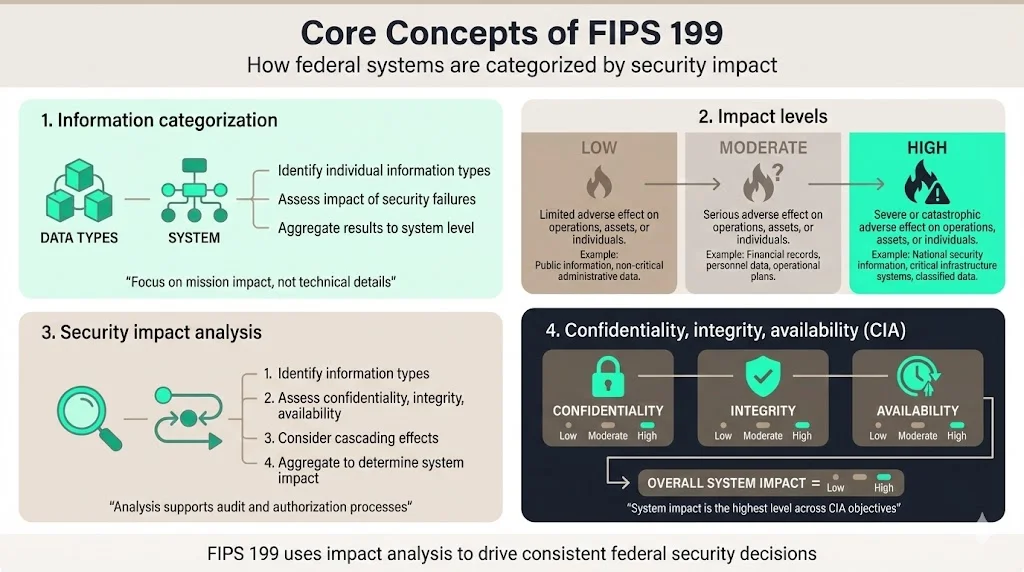
1) Information Categorization
Information categorization means assessing the potential impact if specific information types or systems experience security failures. This process requires analyzing each information type handled by a system and determining consequences of unauthorized access, modification, destruction, or unavailability. Organizations break down information into discrete types based on business function, then evaluate each type independently before aggregating results at the system level.
The categorization methodology requires evaluating information based on organizational mission, not technical characteristics. A customer database might warrant high-impact classification in one agency context but moderate-impact classification in another, depending on the sensitivity of operations that database supports and the consequences of compromise.
2) Data Sensitivity Levels
FIPS 199 establishes three potential levels of risk (low, moderate, and high) for each of the security objectives. These impact levels represent increasing degrees of harm to organizational operations, assets, or individuals.
Low impact applies when security compromise would cause limited adverse effects. A public-facing website publishing non-sensitive agency information typically receives low-impact categorization—brief unavailability causes inconvenience but does not disrupt mission-critical functions or expose sensitive data.
Moderate impact applies when compromise would cause serious adverse effects that significantly degrade mission capability but do not result in catastrophic harm. Internal collaboration systems storing draft policy documents often warrant moderate classification—unauthorized disclosure creates problems requiring remediation but does not fundamentally compromise agency operations or cause severe harm to individuals.
High impact applies when compromise might cause a severe degradation in mission capability, result in major damage to organizational assets, result in major financial loss, or result in severe or catastrophic harm to individuals. Systems processing classified national security information, health records, or financial transaction data frequently receive high-impact categorization. Loss of availability for emergency response systems, compromise of intelligence databases, or unauthorized modification of financial records all represent high-impact scenarios.
3) Security Impact Analysis
Security impact analysis examines the consequences of losing confidentiality, integrity, or availability for specific information types. This analysis precedes categorization decisions and provides the evidentiary basis for impact level assignments. Organizations conduct impact analyses by identifying information types within systems, determining which security objectives apply to each type, and assessing the maximum potential impact of security failures.
Impact analysis requires understanding both immediate consequences and cascading effects. Unauthorized disclosure of employee contact information might seem minor in isolation, but when combined with other compromised data types, could enable social engineering attacks that escalate to more serious breaches. Effective impact analysis considers these compound scenarios and documents the reasoning behind impact level assignments to support audit reviews and authorization decisions.
4) Confidentiality, Integrity, and Availability
FIPS 199 requires Federal agencies to assess their information systems in each of the confidentiality, integrity, and availability categories, rating each system as low, moderate, or high impact in each category. These three security objectives form the framework for all FIPS 199 categorizations.
Confidentiality addresses unauthorized information disclosure. High confidentiality impact applies when disclosure would compromise national security, violate privacy laws, or expose proprietary information causing significant competitive harm. Moderate confidentiality impact applies when disclosure would damage reputation or create compliance complications without catastrophic consequences. Low confidentiality impact applies to information intended for public access or with minimal sensitivity.
Integrity addresses unauthorized modification or destruction of information. Systems processing financial transactions, maintaining authoritative records, or controlling operational technology require high integrity protection—unauthorized changes create incorrect data that stakeholders rely upon for critical decisions. Systems where changes can be detected and corrected through routine processes may warrant moderate integrity ratings.
Availability addresses timely, reliable access to information and services. Emergency response systems, real-time monitoring platforms, and mission-critical operational systems typically require high availability protection—even brief outages disrupt essential functions. Administrative systems tolerating scheduled downtime or delays may warrant moderate or low availability requirements.
Each information system receives three separate impact ratings—one for each security objective. The overall system categorization derives from the highest impact level assigned across all three objectives.
The FIPS 199 Standard in Practice
Applying the Standard to Federal Information Systems
Organizations first determine the security category of their information system in accordance with FIPS Publication 199, derive the information system impact level from the security category in accordance with FIPS 200, and then apply the appropriately tailored set of baseline security controls in NIST Special Publication 800-53. Federal agencies must categorize all information systems before implementing security controls or pursuing authorization. This requirement extends to contractor-owned systems processing federal information under contract.
Agencies document categorization decisions in system security plans and authorization packages. Auditors and authorizing officials review these categorizations to verify that assigned impact levels align with actual system function, data sensitivity, and potential compromise consequences. Incorrect categorization—whether over-categorization consuming excessive resources or under-categorization leaving systems inadequately protected—creates compliance findings and authorization delays.
Steps in Classification
Classification begins with identifying all information types resident in or processed by the system. Organizations reference NIST Special Publication 800-60 for standardized information type taxonomies aligned with federal business functions. Each information type receives provisional confidentiality, integrity, and availability impact ratings based on potential compromise consequences.
The next step involves analyzing the overall system by identifying the highest impact level assigned to any information type for each security objective. A system processing multiple information types inherits the highest rating across all types—if one information type warrants high confidentiality while others warrant only moderate confidentiality, the system receives high confidentiality categorization.
Organizations document rationale supporting each impact level assignment. This documentation must withstand scrutiny from security assessors, authorizing officials, and external auditors who will challenge categorizations appearing inconsistent with system function or information sensitivity. Decision points include determining whether availability requirements reflect actual mission criticality, whether confidentiality ratings account for aggregate disclosure risks across multiple information types, and whether integrity requirements match the consequences of data corruption.
Common challenges include aggregating impact levels when systems process diverse information types with varying sensitivity, distinguishing between information system impact and information type impact, and addressing situations where availability requirements differ based on business hours versus after-hours operations.
Examples of Real Classifications
A federal agency website publishing press releases and public information would typically receive Low-Low-Low categorization (low confidentiality, low integrity, low availability). The information is public, modifications are easily detected and corrected, and brief unavailability causes minimal operational impact.
An internal case management system tracking benefit applications would warrant Moderate-Moderate-Moderate categorization. The system contains personally identifiable information requiring protection (moderate confidentiality), maintains records requiring accuracy for proper benefit determination (moderate integrity), and supports time-sensitive case processing where delays affect service delivery (moderate availability).
A classified intelligence analysis system would receive High-High-High categorization. Unauthorized disclosure compromises national security (high confidentiality), unauthorized modifications could mislead decision-makers during critical operations (high integrity), and unavailability during crisis situations would severely degrade intelligence capabilities (high availability).
Financial transaction processing systems often receive Moderate-High-Moderate or Moderate-High-High categorizations. While individual transaction data may warrant only moderate confidentiality protection, the integrity of financial records demands high protection because unauthorized modifications directly impact monetary assets and regulatory compliance. Availability requirements depend on whether transactions are real-time or batch-processed.
FIPS 199 and Risk Classification
Risk Planning Basics
Security categorization feeds directly into risk assessment and management processes. Impact levels established through FIPS 199 categorization inform risk calculations by defining the potential magnitude of adverse consequences. Organizations conducting risk assessments reference system categorizations to determine risk tolerance thresholds and prioritize remediation efforts—high-impact systems receive more scrutiny and lower risk acceptance thresholds than low-impact systems.
Categorization shapes resource allocation decisions by identifying which systems warrant intensive security investments and continuous monitoring. Federal agencies face budget constraints requiring strategic security resource distribution. FIPS 199 categorizations provide objective criteria for directing resources toward systems where security failures would cause greatest harm.
The categorization also establishes audit frequency and assessment rigor. High-impact systems undergo more frequent security assessments with deeper technical testing than low-impact systems. This risk-based approach focuses assessment resources on systems where vulnerabilities present greatest organizational exposure.
Tie-Ins to Broader Security Planning
Information categories directly determine which security control baselines apply. NIST Special Publication 800-53 defines low, moderate, and high baseline control sets corresponding to FIPS 199 impact levels. A system categorized as high-impact must implement the high baseline—typically 300+ security controls covering administrative, technical, and physical safeguards. Moderate-impact systems implement fewer controls, while low-impact systems implement minimal baselines.
Organizations tailor baseline controls based on specific system characteristics and operating environments, but categorization establishes the starting point for control selection. This connection between categorization and control implementation means FIPS 199 decisions fundamentally shape security architecture, operational processes, and compliance costs.
Authorization processes rely on accurate categorization. Authorizing officials assess whether proposed security controls adequately address risks given system impact levels. Misaligned categorizations—where controls appear insufficient for stated impact levels or excessive given minimal risk—trigger reassessment and delay authorization approval.
FIPS 199 and Compliance
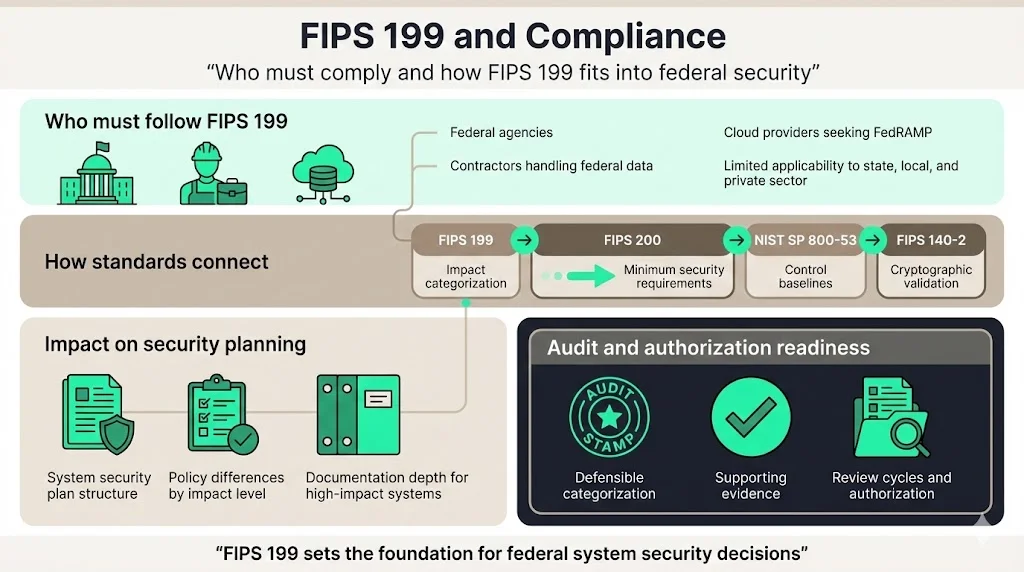
Who Must Follow FIPS 199
All federal agencies must apply FIPS 199 to categorize information and information systems. This mandate extends to every system processing, storing, or transmitting federal information regardless of ownership or operational location. Contractors operating information systems on behalf of federal agencies must categorize those systems according to FIPS 199 when specified in contracts or required by applicable regulations.
Cloud service providers pursuing FedRAMP authorization must categorize their offerings according to FIPS 199 before determining which FedRAMP baseline applies. The categorization determines whether a system qualifies for Low, Moderate, or High FedRAMP authorization—each requiring progressively more extensive security control implementation and assessment procedures.
State and local agencies receiving federal funding for specific programs may face FIPS 199 requirements when grant terms mandate federal information security standards. Private sector organizations generally operate outside FIPS 199 scope unless contractually obligated through federal engagements or choosing to adopt federal standards as best practices.
Relationship to Other Standards
FIPS 200 builds directly on FIPS 199 categorizations. Where FIPS 199 establishes the methodology for categorizing information systems by impact level, FIPS 200 defines minimum security requirements that organizations must meet for each impact category. Organizations cannot implement FIPS 200 without first completing FIPS 199 categorization—the two standards function as sequential steps in a unified compliance framework.
FIPS 140-2 addresses an entirely different compliance domain. While FIPS 199 focuses on categorizing information and systems based on potential impact, FIPS 140-2 establishes requirements for cryptographic modules—the hardware, software, and firmware implementing cryptographic operations. FIPS 140-2 validation becomes relevant after FIPS 199 categorization identifies systems requiring cryptographic protection. High-impact systems typically require FIPS 140-2 validated cryptographic modules, while lower-impact systems may use validated modules without strict mandate.
These standards work together within broader compliance frameworks. FIPS 199 categorization determines which FIPS 200 security requirements apply, which in turn references NIST SP 800-53 control baselines. When those baselines require cryptographic protection, FIPS 140-2 validation ensures cryptographic implementations meet federal standards. The standards create a layered compliance structure rather than competing requirements.
How It Affects Security Planning
FIPS 199 categorizations shape security plan structure and content. System security plans must document the categorization methodology, list all information types and their individual impact ratings, explain the rationale for assigned impact levels, and describe how the overall system categorization derives from information type analysis. Authorization officials review this documentation to verify that security plans address risks appropriate to system impact levels.
The categorization influences policy development by establishing which security policies apply to specific systems. Organizations maintain separate policy sets for low, moderate, and high-impact systems reflecting different control requirements. Categorization also determines documentation rigor—high-impact systems require more detailed security plans, more extensive risk assessments, and more frequent plan updates than low-impact systems.
Audit readiness depends on defensible categorizations. Auditors examining FISMA compliance verify that categorizations reflect actual system characteristics and that implemented controls match assigned impact levels. Organizations must maintain evidence supporting categorization decisions including impact analyses, stakeholder consultations documenting business impact determinations, and periodic categorization reviews confirming continued accuracy as systems evolve.
Authorization Processes and FIPS 199
Foundation for Control Selection
Categorization establishes which NIST SP 800-53 control baseline organizations must implement. The low baseline contains approximately 125 controls, moderate baseline approximately 325 controls, and high baseline approximately 421 controls. Organizations tailor these baselines by adding controls to address specific risks or removing controls inapplicable to their operational environment, but the categorization-derived baseline provides the mandatory starting point.
Authorization packages document how organizations implement baseline controls appropriate to system categorization. Security assessment plans, security assessment reports, and plans of action and milestones all reference system categorization when determining assessment scope, testing depth, and remediation priorities. Authorizing officials evaluate whether security posture adequately addresses risks given system impact levels before granting authority to operate.
Continuous monitoring strategies vary by impact level. High-impact systems require more frequent vulnerability scanning, more rigorous configuration management, and more intensive security event monitoring than lower-impact systems. These requirements flow directly from FIPS 199 categorizations establishing baseline risk profiles.
FedRAMP and Other Frameworks
FedRAMP leverages FIPS 199 categorizations to determine which authorization baseline applies to cloud services. Cloud service providers must categorize their offerings as Low, Moderate, or High impact, then implement corresponding FedRAMP control baselines derived from NIST SP 800-53. FedRAMP Low authorization requires approximately 125 controls, Moderate requires approximately 325 controls, and High requires the full high baseline with additional FedRAMP-specific requirements.
The categorization determines assessment rigor during FedRAMP authorization. Moderate and High authorizations require assessment by accredited third-party assessment organizations conducting detailed security control testing over several months. Low authorizations may follow streamlined processes with less extensive assessment procedures. These procedural differences create significant cost and timeline variations—accurate categorization during planning prevents pursuing inappropriate authorization levels requiring later recategorization and reassessment.
Vendors working under FedRAMP must align their internal categorizations with agency-specific categorizations when agencies adopt FedRAMP-authorized services. Agencies may determine that their specific use case warrants higher categorization than the provider's general authorization addresses. In these situations, agencies require additional security controls beyond baseline FedRAMP requirements, implemented through customer responsibility matrices and supplemental agreements.
Organizations pursuing multiple federal authorizations benefit from consistent categorization approaches. While different agencies may reach different categorization conclusions for the same system based on their specific use cases, vendors should maintain documented categorization methodologies demonstrating systematic, repeatable impact analysis processes that withstand scrutiny across multiple authorization efforts.
Common Pitfalls and Tips

Many organizations categorize entire systems at single impact levels without analyzing individual information types. This approach violates FIPS 199 methodology and creates authorization vulnerabilities. Proper categorization requires identifying each information type, assessing confidentiality, integrity, and availability impacts for each type, then aggregating to determine overall system categorization. Auditors reviewing system security plans expect documented information type analysis, not blanket impact level assertions.
Over-categorization wastes resources by imposing control requirements exceeding actual risk. Organizations sometimes assign high-impact ratings defensively, assuming greater security equals better compliance. This approach consumes budget implementing controls providing minimal risk reduction while diverting resources from systems with genuine high-impact requirements. Impact level assignments must reflect actual compromise consequences, not aspirational security postures.
Under-categorization creates compliance findings and operational vulnerabilities. When categorizations fail to account for aggregate risks across multiple information types or downstream consequences of system failures, organizations implement insufficient controls. Authorizing officials reject authorization requests when categorizations appear inconsistent with system function or data sensitivity.
Structure categorization reviews as formal decision-making processes involving business stakeholders, security personnel, and system owners. Business stakeholders provide mission impact assessments determining availability requirements and consequences of integrity failures. Security personnel analyze confidentiality risks and regulatory requirements. System owners document technical characteristics informing impact analysis. This collaborative approach produces defensible categorizations supported by documented business justification.
Document categorization decisions with specific rationale explaining why each information type received assigned impact levels. Generic statements like "contains PII" provide insufficient justification—auditors expect analysis explaining what specific harm would result from compromise, why that harm warrants the assigned impact level, and how the organization determined impact thresholds. Detailed documentation survives authorization reviews and supports future recategorization when systems evolve.
Review categorizations annually or when systems undergo significant changes. Information systems evolve through functionality additions, data type changes, and integration with other systems. Categorizations based on initial system design may no longer reflect current risk profiles. Formal review processes ensure categorizations remain accurate as systems mature.
Conclusion
FIPS 199 establishes the foundational methodology federal agencies and their contractors must follow to categorize information systems by security impact level. This categorization determines which security control baselines apply, what authorization processes organizations must complete, and how rigorously auditors assess security implementations. Organizations cannot implement federal security requirements without first conducting systematic FIPS 199 categorization—the standard functions as the entry point for all subsequent security planning and compliance activity.
For enterprise companies pursuing federal contracts or FedRAMP authorization, understanding FIPS 199 means understanding how federal agencies evaluate risk and allocate security resources. Accurate categorization during planning prevents authorization delays, ensures appropriate control implementation, and demonstrates security maturity that federal buyers expect. Organizations treating categorization as a compliance formality rather than a strategic risk decision inevitably face reassessment requirements, authorization rejections, or security gaps that incidents expose.
The standard remains relevant as federal information systems increasingly rely on cloud services, contractor-operated infrastructure, and complex supply chains. FIPS 199 provides the common categorization framework enabling consistent security expectations across diverse operational models and organizational boundaries.
FAQ Section
1) What is FIPS 199 used for?
FIPS 199 establishes the mandatory standard federal agencies use to categorize information and information systems by security impact level. Organizations assess potential consequences if systems lose confidentiality, integrity, or availability, then assign low, moderate, or high impact ratings for each security objective. These categorizations determine which security control baselines apply, what authorization processes organizations must complete, and how extensively auditors assess security implementations.
2) How does FIPS 199 classify information types?
FIPS 199 classifies information types by evaluating potential impact in three categories: confidentiality, integrity, and availability. Organizations assess each information type independently, determining whether compromise would cause low, moderate, or high impact to organizational operations, assets, or individuals. The overall system categorization inherits the highest impact level assigned to any information type for each security objective. A system processing one high-confidentiality information type among several moderate-confidentiality types receives high-confidentiality categorization for the entire system.
3) Who must comply with FIPS 199?
Federal agencies must comply with FIPS 199 for all information systems processing, storing, or transmitting federal information. Contractors operating systems on behalf of federal agencies must apply FIPS 199 when specified in contracts or required by applicable regulations. Cloud service providers pursuing FedRAMP authorization must categorize offerings according to FIPS 199 to determine which FedRAMP baseline applies. State and local agencies may face FIPS 199 requirements when federal grants mandate federal security standards for funded programs.
4) How does FIPS 199 affect security planning?
FIPS 199 categorizations determine which NIST SP 800-53 control baselines organizations must implement—low-impact systems require approximately 125 controls while high-impact systems require over 400 controls. Categorization shapes security plan content, policy applicability, assessment rigor, continuous monitoring intensity, and authorization timeline. Organizations document categorization methodology and rationale in system security plans, and authorizing officials verify that implemented controls adequately address risks given assigned impact levels before granting authority to operate.
5) What is the difference between FIPS 199 and 200?
FIPS 199 establishes methodology for categorizing information systems by impact level based on potential compromise consequences. FIPS 200 defines minimum security requirements organizations must implement for each impact category. Organizations apply FIPS 199 first to determine system categorization, then implement FIPS 200 security requirements corresponding to assigned impact levels. The standards function sequentially—FIPS 199 determines what category applies, FIPS 200 specifies minimum requirements for that category.
6) What does FIPS stand for?
FIPS stands for Federal Information Processing Standards. These mandatory standards govern technical requirements for federal agency information systems across diverse domains including security categorization, minimum security requirements, and cryptographic module validation. NIST develops FIPS publications in response to federal mandates requiring standardized approaches to information security and technology implementation across civilian and national security agencies.
7) What is the difference between FIPS 199 and FIPS 140-2?
FIPS 199 focuses on categorizing information and information systems based on potential security impact to organizational operations and assets. FIPS 140-2 establishes security requirements for cryptographic modules—the hardware, software, and firmware implementing encryption and cryptographic functions. FIPS 199 categorization determines overall system security requirements, while FIPS 140-2 validation ensures cryptographic implementations within those systems meet federal standards. High-impact systems typically require FIPS 140-2 validated cryptographic modules as one component of comprehensive security control implementation.
8) What does FIPS 200 do?
FIPS 200 defines minimum security requirements for federal information systems based on FIPS 199 categorizations. The standard specifies 17 security-related areas including access control, incident response, system and communications protection, and risk assessment. Organizations implement these minimum requirements by selecting appropriate controls from NIST SP 800-53 control baselines corresponding to their FIPS 199 impact levels. FIPS 200 establishes the mandatory security baseline all federal systems must meet before receiving authorization to operate.



.svg)
.svg)
.svg)