Most organizations implementing cryptographic protections assume that encryption alone delivers security. This approach overlooks a fundamental reality: cryptographic implementations fail not because algorithms are weak, but because the modules executing those algorithms lack validated security controls. FIPS 140-3 (Federal Information Processing Standard Publication 140-3) is a U.S. government computer security standard used to approve cryptographic modules, with the title "Security Requirements for Cryptographic Modules." Organizations operating in regulated industries—or selling to enterprise customers who do—require cryptographic modules validated against this standard to demonstrate verifiable security posture rather than aspirational compliance claims.
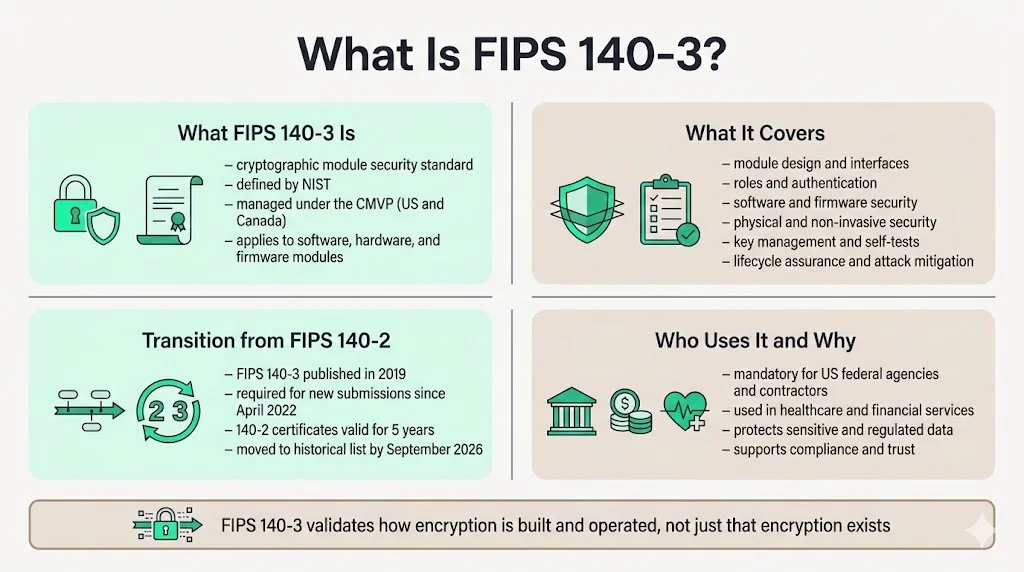
What Is FIPS 140-3?
FIPS 140 is a set of security requirements for cryptographic modules defined by the National Institute of Standards and Technology (NIST) and managed by both the United States and Canada as part of the Cryptographic Module Validation Program (CMVP). The security requirements cover areas related to the secure design, implementation and operation of a cryptographic module, including cryptographic module specification, interfaces, roles and authentication, software/firmware security, operating environment, physical security, non-invasive security, sensitive security parameter management, self-tests, life-cycle assurance, and mitigation of other attacks.
FIPS 140-3 was initially published on March 22, 2019 and supersedes FIPS 140-2. As of April 1, 2022, FIPS PUB 140-3 Security Requirements for Cryptographic Modules supersedes FIPS 140-2 for new submissions, with products certified to FIPS 140-2 remaining valid for 5 years after validation. Existing FIPS 140-2 certificates will not be revoked but will be moved to the Historical List as of September 21, 2026.
The cryptographic modules are produced by the private sector or open source communities for use by the U.S. government and other regulated industries such as financial and health-care institutions that collect, store, transfer, share and disseminate sensitive information. While FIPS 140-3 validation is mandatory for federal agencies and their contractors handling Sensitive But Unclassified (SBU) information, organizations operating in regulated industries like healthcare and finance often use FIPS 140-3 encryption to remain compliant and protect sensitive information.
Why FIPS 140-3 Matters for Enterprise Security
Procurement specifications increasingly require FIPS 140-3 validated modules as a non-negotiable baseline. This requirement extends beyond government contracts—enterprise security teams recognize that cryptographic validation provides independently verified assurance that modules implement approved algorithms correctly and maintain security controls throughout their operational lifecycle. Organizations claiming "bank-grade encryption" or "military-grade security" without FIPS validation are making unsubstantiated security assertions that collapse under regulatory scrutiny.
The standard provides four increasing, qualitative levels of security intended to cover a wide range of potential applications and environments. This tiered approach allows organizations to specify validation levels appropriate to their risk profile—Level 2 for general enterprise applications, Level 3 for high-value transactions or healthcare data, Level 4 for cryptographic infrastructure protecting critical systems. For many organizations, requiring FIPS certification at FIPS 140-2 and FIPS 140-3 level 3 is a good compromise between effective security, operational convenience, and choice in the marketplace.
Beyond regulatory compliance, FIPS 140-3 validation serves as a market differentiator. Vendors lacking validated cryptographic modules face immediate disqualification from government procurement and encounter increasing resistance from enterprise security teams conducting vendor risk assessments. The validation demonstrates that third-party laboratories have tested your cryptographic implementation against documented security requirements—not merely that your engineering team believes the implementation is secure.
Breaking Down the FIPS 140-3 Framework
Security Levels Explained
FIPS 140-3 Level 1 is the entry-level security standard for cryptographic modules, requiring the correct implementation and usage of approved cryptographic algorithms, emphasizing detailed documentation and evidence through rigorous testing. Level 1 establishes baseline requirements: approved algorithms correctly implemented, basic functional testing, documented security policies. This level provides no physical security requirements—the module may be software executing on general-purpose computing hardware.
FIPS 140-3 Level 2 adds tamper evidence and role-based authentication to control physical access and ensure clear separation of roles and services. Physical security mechanisms at this level detect but do not prevent tampering. Level 2 adds requirements for physical tamper-evidence and role-based authentication. Organizations deploy Level 2 modules in controlled environments where physical access is restricted through procedural controls.
FIPS 140-3 Level 3 introduces mechanisms for tamper resistance, identity-based authentication, and stricter separation between interfaces and critical security parameters to prevent unauthorized access. Level 3 also requires the module to detect and react to out-of-range voltage or temperature through environmental failure protection (EFP), or alternatively undergo environmental failure testing (EFT). Tamper-resistant enclosures, identity-based authentication replacing role-based controls, and physical or logical separation of interfaces distinguish Level 3 from lower tiers.
FIPS 140-3 Level 4, the highest security level, includes robust protections against environmental and physical attacks such as side channel and fault injection attacks, ensuring modules operate securely under extreme conditions and incorporate advanced hardware security techniques. EFP and protection against fault injection is required as well as multi-factor authentication. Level 4 modules implement active tamper response mechanisms—detecting attacks triggers cryptographic key zeroization. These modules address sophisticated threat models including differential power analysis and electromagnetic emanation attacks.
FIPS 140-3 vs. FIPS 140-2
Understanding the evolution from FIPS 140-2 to 140-3 matters because many vendors continue operating under legacy certifications while claiming current compliance. FIPS 140-3 specifies security requirements at every stage of cryptographic module creation—design, implementation, and deployment phases—not just post-completion. This lifecycle approach requires demonstrating security controls during development, not merely validating the finished product.
While FIPS 140-2 assumed that all modules were hardware modules, FIPS 140-3 addresses hardware, firmware, software, hybrid software, and hybrid firmware modules, with FIPS140-2 IG 1.9 restricting hybrid modules to Level 1 validation while FIPS 140-3 has no restriction to the level at which a hybrid module may be validated. Organizations implementing software-based cryptographic modules or hybrid architectures combining hardware acceleration with software fallback now have clear certification paths at higher security levels.
The standard introduces trusted channels instead of trusted paths, reflecting modern distributed computing architectures where cryptographic operations span multiple processing contexts. FIPS 140-3 introduces new enhancements including stricter integrity test requirements, key zeroization required for ALL unprotected Sensitive Security Parameters (SSP) at all levels including public keys, and roles, services, and authentication that must be met by a cryptographic module's implementation not through policy or rules, for example password size restrictions.
The goal of FIPS 140-3 is to be more closely aligned to international ISO/IEC standards and better suited to today's technologies through ISO/IEC 19790:2012, with this alignment to international standards allowing for a seamless transition to FIPS 140-3, greater interoperability and ensuring consistent security practices across the globe. Organizations operating globally benefit from reduced certification complexity when a single validation satisfies both U.S. federal requirements and international procurement standards.
How FIPS 140-3 Fits Into Enterprise Compliance
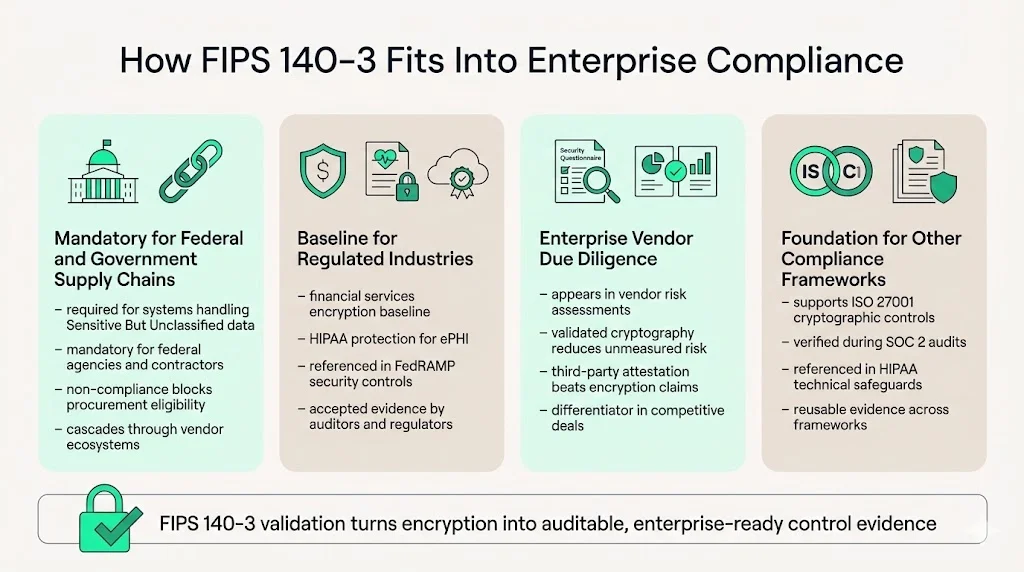
Federal agencies require FIPS 140-3 validated modules for any system processing Sensitive But Unclassified information. Government contractors inheriting these requirements discover that non-compliance eliminates them from procurement consideration regardless of technical capabilities or pricing advantages. This creates cascading validation requirements throughout supply chains—if your product handles government data at any point, validation becomes mandatory.
Regulated industries adopt FIPS 140-3 as a security baseline even when not legally mandated. Financial institutions implementing payment processing systems, healthcare organizations protecting electronic health records under HIPAA, and cloud service providers seeking FedRAMP authorization all reference FIPS validation in their security control frameworks. The validation provides documented evidence that cryptographic implementations meet specific technical requirements—evidence that auditors and regulators accept without requiring independent cryptographic analysis.
Vendors pursuing enterprise customers encounter FIPS requirements in security questionnaires and vendor risk assessments. Organizations conducting vendor due diligence recognize that unvalidated cryptography represents unmeasured risk. Two vendors offering functionally equivalent products compete on validated security controls, not marketing claims about encryption strength. The vendor with current FIPS 140-3 certificates documents security posture through third-party attestation; the vendor without validation asks customers to trust unverified implementation quality.
Integration with broader compliance frameworks positions FIPS validation as a foundational control. ISO 27001 implementations reference cryptographic module validation as evidence for multiple control objectives. SOC 2 auditors examining encryption controls verify that cryptographic modules maintain current FIPS certificates. HIPAA technical safeguards for electronic protected health information (ePHI) specify FIPS-validated encryption for data at rest and in transit.
The Certification Process & Timeline
The CMVP is a joint effort between the National Institute of Standards and Technology and the Canadian Centre for Cyber Security, with the goal of promoting the use of validated cryptographic modules and providing Federal agencies with a security metric to use in procuring equipment containing validated cryptographic modules, where vendors of cryptographic modules use independent, accredited Cryptographic and Security Testing (CST) laboratories to have their modules tested.
Organizations pursuing validation engage accredited CST laboratories to conduct testing against FIPS 140-3 requirements. The process begins with documentation submission—security policy, algorithm certificates, interface specifications, physical security mechanisms, operational guidance. Testing laboratories examine source code, conduct functional testing of cryptographic operations, verify algorithm implementations, and assess physical security controls appropriate to the target security level.
Validation timelines vary significantly based on module complexity, target security level, and laboratory capacity. Simple software modules targeting Level 1 may complete validation in 6-9 months. Hardware security modules pursuing Level 3 validation with custom cryptographic implementations typically require 12-18 months from initial submission to certificate issuance. Hybrid modules implementing multiple cryptographic boundaries extend timelines further as each boundary requires independent validation.
Products certified to FIPS 140-2 can remain valid for 5 years after validation. Organizations maintaining validated modules must plan recertification cycles, particularly when updating module versions, modifying cryptographic implementations, or changing operational environments. Minor updates may qualify for revalidation rather than complete recertification, reducing timeline and testing scope.
Common Use Cases for FIPS 140-3 Certified Products
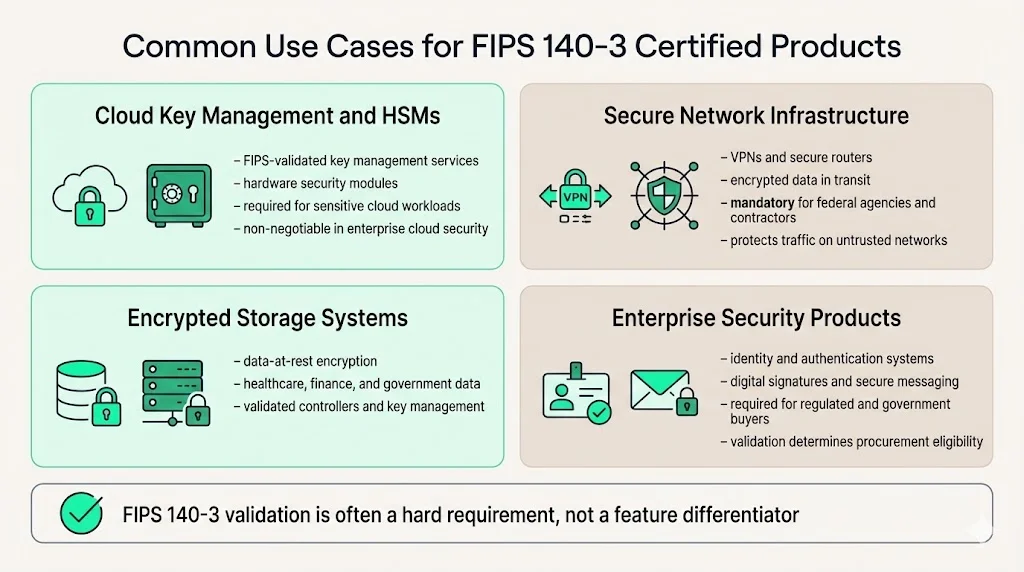
Cloud service providers implement FIPS 140-3 validated modules for encryption key management services, ensuring that customer cryptographic keys remain protected by validated hardware security modules throughout their lifecycle. Organizations migrating sensitive workloads to cloud environments specify FIPS validation as a non-negotiable requirement in their cloud security architecture.
Network infrastructure—VPN concentrators, secure routers, encrypted communication systems—deploys validated cryptographic modules to protect data in transit across untrusted networks. Federal agencies and their contractors cannot deploy network devices lacking current FIPS certificates regardless of functional capabilities or cost advantages.
Storage systems protecting sensitive data at rest implement FIPS validated encryption controllers and key management infrastructure. Healthcare organizations storing electronic health records, financial institutions maintaining transaction databases, and government agencies managing citizen information all require validated encryption modules for data protection controls.
Enterprise products incorporating cryptographic functionality—authentication systems, digital signature platforms, secure messaging applications—pursue FIPS validation to address procurement requirements from government and regulated industry customers. Without validation, these products face immediate disqualification during vendor evaluation regardless of feature completeness or market positioning.
Preparing Your Product Roadmap for FIPS 140-3
Product teams designing cryptographic functionality must incorporate FIPS requirements from initial architecture rather than treating validation as a post-development certification exercise. Lifecycle assurance requires vendors to demonstrate adequate internal testing on a module in addition to validation lab testing. Organizations implementing cryptographic modules without documented development security controls discover that retroactive validation requires extensive re-engineering.
Algorithm selection drives validation feasibility and timeline. NIST maintains approved algorithm lists—modules implementing non-approved algorithms or using approved algorithms with non-compliant parameters cannot achieve validation regardless of implementation quality. Organizations designing custom cryptographic implementations face significantly extended timelines compared to those leveraging pre-validated cryptographic libraries.
Hardware versus software module strategies involve security level tradeoffs. Software modules executing on general-purpose operating systems face limitations achieving higher security levels due to insufficient physical security and operating environment controls. Hardware security modules provide stronger physical protections but increase product cost and complexity. FIPS 140-3 addresses hardware, firmware, software, hybrid software, and hybrid firmware modules, improving on FIPS 140-2 by providing a clear path to implementing and certifying hybrid modules that can make use of technologies like Java Native Interface (JNI) for supporting hardware acceleration while also allowing the module to still be functional using pure Java if the hardware acceleration is not available.
Documentation requirements exceed typical product documentation standards. FIPS validation requires security policies detailing every cryptographic operation, interface specification defining cryptographic boundaries, operator guidance describing secure configuration and operation, and design documentation demonstrating security control implementation. Organizations treating validation documentation as an afterthought face extended timelines when laboratories identify gaps requiring substantial documentation revision.
Testing approaches must address both functional correctness and security control effectiveness. Algorithm testing verifies that cryptographic implementations produce correct outputs for known test vectors. Security control testing examines authentication mechanisms, key management procedures, self-test operations, and error handling. Organizations conducting internal testing aligned with FIPS requirements before laboratory submission reduce validation cycles and avoid costly remediation.
FIPS 140-3 represents the minimum validated security baseline for cryptographic modules protecting sensitive information in government and regulated industry environments. Organizations building products for these markets discover that validation is not optional—procurement specifications eliminate unvalidated products during initial vendor screening. The standard provides independently verified assurance that cryptographic implementations maintain security controls throughout design, implementation, deployment, and operation. Vendors investing in FIPS validation differentiate through documented security posture rather than unsubstantiated marketing claims about encryption strength.
FAQs
1) What is FIPS 140-3?
FIPS 140-3 (Federal Information Processing Standard Publication 140-3) is a U.S. government computer security standard used to approve cryptographic modules, titled "Security Requirements for Cryptographic Modules." It establishes technical requirements for cryptographic module design, implementation, and operation across four security levels.
2) Who needs FIPS 140-3 validation?
The standard is applicable to all federal agencies that use cryptographic-based security systems to protect sensitive information in computer and telecommunication systems, and shall be used in designing and implementing cryptographic modules that federal departments and agencies operate or are operated for them under contract. Government contractors, regulated industries including healthcare and finance, and vendors selling to enterprise customers with security requirements increasingly require FIPS validation.
3) What changed from FIPS 140-2 to 140-3?
FIPS 140-3 specifies security requirements at every stage of cryptographic module creation—design, implementation, and deployment phases—not just post-completion. The standard addresses hardware, firmware, software, and hybrid modules with no restrictions on security levels for hybrid implementations, introduces trusted channels, aligns with ISO/IEC 19790:2012 international standards, and implements stricter requirements for authentication complexity and key zeroization.
4) How long does FIPS certification take?
Validation timelines range from 6-9 months for basic software modules targeting Level 1 to 12-18 months for hardware security modules pursuing Level 3 validation. Duration depends on module complexity, target security level, algorithm implementation approach, documentation completeness, and accredited laboratory testing capacity. Products certified to FIPS 140-2 can remain valid for 5 years after validation.
5) Does FIPS certification apply to software only?
FIPS 140-3 addresses hardware, firmware, software, hybrid software, and hybrid firmware modules. Unlike FIPS 140-2 which primarily focused on hardware implementations, FIPS 140-3 provides comprehensive certification paths for pure software modules, hardware security modules, and hybrid architectures combining both approaches.



.svg)
.svg)
.svg)