Most organizations underestimate the breadth of the FTC Safeguards Rule. They assume compliance applies only to traditional banks—a misconception that leaves mortgage brokers, payday lenders, tax preparers, and even auto dealerships exposed to regulatory action and data breach liability.
The Safeguards Rule requires financial institutions under FTC jurisdiction to have measures in place to keep customer information secure. The purpose of the Federal Trade Commission's Standards for Safeguarding Customer Information – the Safeguards Rule, for short – is to ensure that entities covered by the Rule maintain safeguards to protect the security of customer information. This regulation, codified as 16 CFR Part 314, establishes mandatory administrative, technical, and physical safeguards for protecting non-public personal information of consumers.
For enterprise-selling companies, the Safeguards Rule creates a compliance chain. If you provide services to mortgage brokers, fintech platforms, credit counselors, or collection agencies, you function as a service provider within the regulatory framework. Your security posture directly affects your client's audit readiness and regulatory exposure. Vendor risk assessments, contractual safeguards requirements, and evidence collection now flow upstream to your organization—whether you recognized the obligation or not.
The terms "data security," "financial institutions," "cybersecurity compliance," and "regulatory requirements" define the Safeguards Rule landscape. Understanding this regulation means understanding how your products, services, and security infrastructure either support or undermine your clients' compliance obligations.
FTC Safeguards Rule: Origin and regulatory evolution

Congress recognized the importance of securing consumers' sensitive financial information when it passed the GLBA, which required the FTC to promulgate the Safeguards Rule. The Gramm-Leach-Bliley Act of 1999 mandated federal agencies to establish standards for protecting consumer financial data. The Safeguards Rule took effect in 2003, establishing baseline requirements for information security programs.
The FTC amended it in 2021 to make sure the Rule keeps pace with current technology. While preserving the flexibility of the original Safeguards Rule, the revised Rule provides more concrete guidance for businesses. The Final Rule adds provisions designed to provide covered financial institutions with more guidance on how to develop and implement specific aspects of an overall information security program, such as access controls, authentication, and encryption. It adds provisions designed to improve the accountability of financial institutions' information security programs, such as by requiring periodic reports to boards of directors or governing bodies.
The FTC further amended the Rule in 2023 to require covered entities to report certain data breaches and security incidents. Those breach notification requirements took effect in May 2024. The amendment requires financial institutions to notify the FTC as soon as possible, and no later than 30 days after discovery, of a security breach involving the information of at least 500 consumers.
These amendments represent a fundamental shift from principles-based guidance to prescriptive technical controls. Organizations treating the Safeguards Rule as static compliance documentation now face material gaps when regulators examine actual security implementations.
Who must comply: coverage and applicability
The Rule defines "financial institution" in a way that's broader than how people may use that phrase in conversation. What matters are the types of activities your business undertakes, not how you or others categorize your company.
Section 314.2(h) of the Rule lists 13 examples of the kinds of entities that are financial institutions under the Rule, including mortgage lenders, payday lenders, finance companies, mortgage brokers, account servicers, check cashers, wire transferors, collection agencies, credit counselors and other financial advisors, tax preparation firms, non-federally insured credit unions, and investment advisors that aren't required to register with the SEC. The 2021 amendments to the Safeguards Rule add a new example of a financial institution – finders.
The Final Rule expands the definition of "financial institution" to include entities engaged in activities the Federal Reserve Board determines to be incidental to financial activities. This expansion captures entities that facilitate financial transactions without directly providing financial products—payment processors, data aggregators, and certain technology platforms operating within the financial ecosystem.
The Final Rule exempts financial institutions that collect less customer information from certain requirements. The Final Rule exempts financial institutions that collect information about fewer than 5,000 consumers from the written risk assessment, incident response plan and annual reporting requirements. This threshold provides limited relief for smaller operations but does not eliminate core security obligations.
For enterprises selling to covered entities, understanding applicability means mapping your role in the compliance chain. If your software processes customer information on behalf of a mortgage lender, you are a service provider subject to contractual safeguards requirements and vendor oversight obligations. Your client's auditor will examine your controls, request evidence of your security program, and assess whether you introduce unacceptable risk.
Core requirements: building the information security program
The Safeguards Rule mandates that covered financial institutions develop, implement, and maintain a comprehensive information security program encompassing administrative, technical, and physical safeguards.
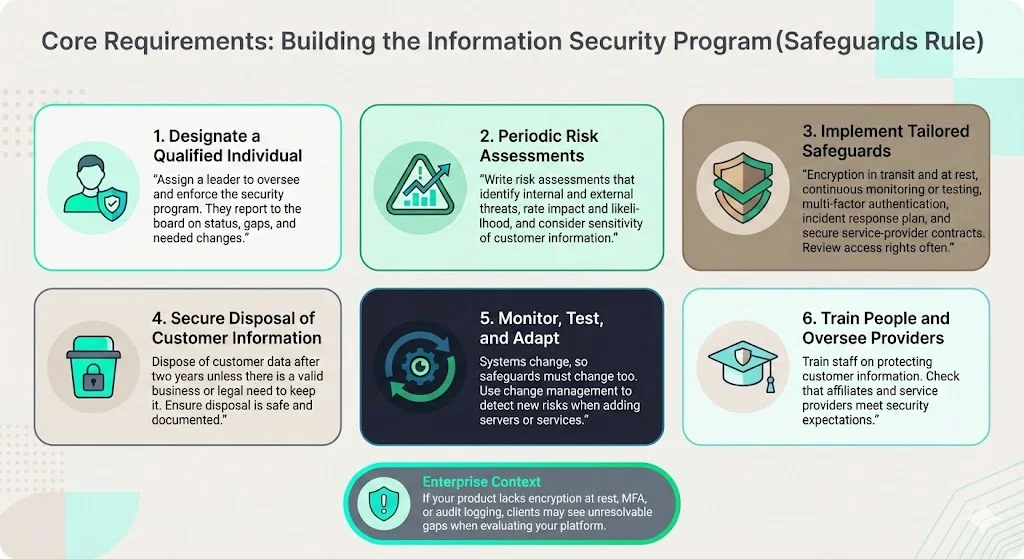
1) Designate a Qualified Individual
Covered entities must designate a "Qualified Individual" responsible for overseeing, implementing, and enforcing the information security program. This individual reports directly to the board of directors or equivalent governing body on program status, compliance gaps, and recommended changes.
2) Conduct periodic risk assessments
The Final Rule specifies criteria that financial institutions must include in their risk assessments, and specifies that such assessments must be in writing. Risk assessments must identify reasonably foreseeable internal and external threats to the security, confidentiality, and integrity of customer information. Assessments evaluate the likelihood and potential damage of these threats, considering the sensitivity of customer information and the complexity of systems and operations.
3) Implement tailored safeguards
The Final Rule requires covered financial institutions to implement specific safeguards, including: (1) encryption for all customer information in transit and at rest (subject to certain exceptions where compensating controls are implemented); (2) continuous monitoring or periodic penetration testing and vulnerability assessments; (3) multi-factor authentication for any individual accessing an information system (or a reasonably equivalent or more secure access control approved in writing by a "qualified individual"); (4) a written incident response plan; and (5) steps to select and retain service providers capable of maintaining appropriate safeguards for customer information, including contractually requiring service providers to implement such safeguards, and periodically assessing service providers based on the risk they present.
The Safeguards Rule requires your company to implement and periodically review access controls. Determine who has access to customer information and reconsider on a regular basis whether they still have a legitimate business need for it.
4) Dispose of customer information securely
Securely dispose of customer information no later than two years after your most recent use of it to serve the customer. The only exceptions: if you have a legitimate business need or legal requirement to hold on to it or if targeted disposal isn't feasible because of the way the information is maintained.
5) Monitor, test, and adapt
Changes to an information system or network can undermine existing security measures. For example, if your company adds a new server, has that created a new security risk? Because your systems and networks change to accommodate new business processes, your safeguards can't be static. The Safeguards Rule requires financial institutions to build change management into their information security program.
6) Train personnel and oversee service providers
Companies covered by the Rule are responsible for taking steps to ensure that their affiliates and service providers safeguard customer information in their care. This requirement extends compliance obligations to vendors, SaaS providers, cloud infrastructure partners, and any third party accessing or processing customer information.
For enterprise-selling companies, these requirements define how your clients will evaluate your offerings. If your platform lacks encryption at rest, does not support multi-factor authentication, or cannot provide audit logs demonstrating continuous monitoring, you introduce compliance gaps your clients cannot remediate through compensating controls alone.
Role in data security, privacy, and risk management
The Safeguards Rule drives operational security beyond performative compliance. It mandates confidentiality, integrity, and availability of consumer financial data through documented, tested, and continuously monitored controls.
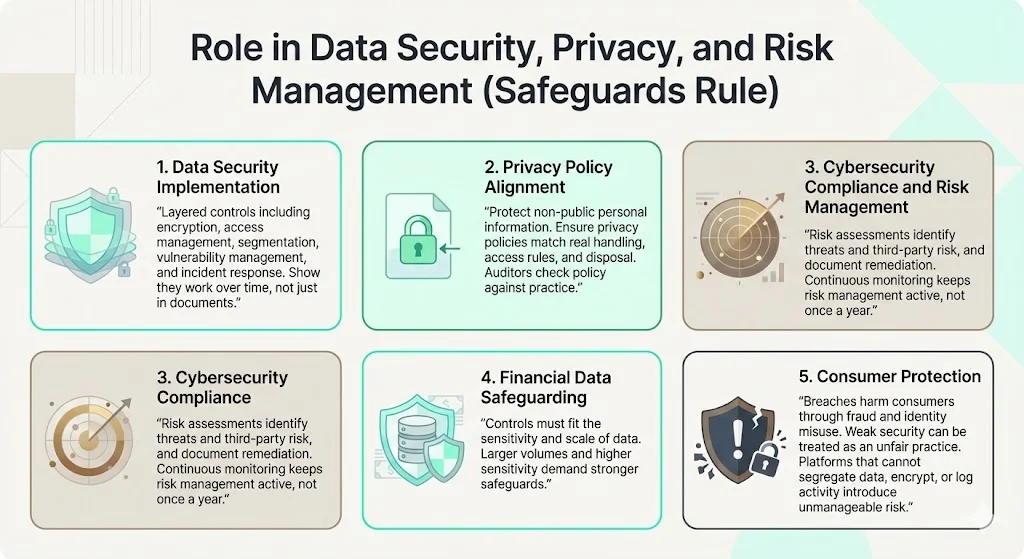
1) Data security implementation
The regulation addresses data security through layered technical controls—encryption, access management, network segmentation, vulnerability management, and incident response. Organizations must demonstrate these controls function effectively over time, not simply exist in policy documentation.
2) Privacy policy alignment
The Safeguards Rule protects non-public personal information of consumers. This includes any personally identifiable financial information collected, processed, or maintained by covered entities. Privacy policies must align with actual data handling practices, access restrictions, and disposal procedures. Auditors verify alignment between stated policies and implemented controls.
3) Cybersecurity compliance and risk management
The rule integrates cybersecurity compliance into enterprise risk management frameworks. Risk assessments must identify threats specific to the organization's data environment, evaluate third-party vendor risk, and document remediation strategies. Continuous monitoring requirements ensure that risk management remains an ongoing operational discipline rather than an annual exercise.
4) Financial data safeguarding
Given the regulation's focus on customer information in financial contexts, organizations must implement controls appropriate to the sensitivity and volume of data processed. A mortgage broker handling thousands of loan applications requires materially different safeguards than a tax preparer serving individual clients, though both remain subject to the Rule's core requirements.
5) Consumer protection mandate
The regulatory aim extends beyond institutional security to consumer harm prevention. Data breaches affecting covered entities directly harm consumers through identity theft, fraud, and unauthorized account access. The FTC views inadequate security as an unfair trade practice that violates consumer protection statutes.
For B2B enterprises, mapping how your solution helps clients meet regulatory requirements—or introduces unmanageable risk—determines whether you enable compliance or obstruct it. If your platform cannot segregate customer data by client tenant, cannot demonstrate encryption implementation, or lacks audit trail capabilities, you undermine your clients' ability to satisfy regulatory obligations.
Regulatory and business security implications
1) Regulatory requirements and documentation
The Safeguards Rule mandates written information security programs, documented risk assessments, written incident response plans, and board-level reporting. Organizations must maintain evidence demonstrating ongoing compliance—control testing results, vulnerability scan reports, penetration testing findings, vendor risk assessments, and access review documentation.
2) Enforcement and penalties
The FTC enforces the Safeguards Rule through administrative proceedings, consent orders, and civil penalties. Non-compliance triggers investigation when breaches occur, consumer complaints accumulate, or regulatory examinations reveal deficiencies. Enforcement actions result in mandatory corrective measures, ongoing compliance monitoring, and reputational damage that affects customer trust and competitive positioning.
Organizations found in violation face consent orders requiring comprehensive security program overhauls, independent assessments every two years for 20 years, and detailed reporting to the FTC on all security incidents and program changes. These obligations impose long-term operational costs and external scrutiny that extend far beyond initial penalties.
3) Service provider and third-party implications
Companies selling to enterprise clients must understand their position in the compliance chain. When your client is a covered financial institution, you inherit contractual obligations to implement appropriate safeguards, provide evidence of security program effectiveness, and submit to vendor risk assessments.
Vendor oversight requirements mean your clients will demand security questionnaire responses, SOC 2 reports, penetration testing results, and detailed documentation of your encryption implementation, access controls, and incident response capabilities. Inability to provide this evidence eliminates you from consideration by compliance-conscious prospects.
4) Strategic business benefits
Organizations implementing robust Safeguards Rule compliance gain competitive differentiation. Financial institutions selecting service providers prioritize vendors demonstrating mature security programs, documented compliance, and audit readiness. Your security posture becomes a sales enabler rather than a barrier to enterprise deals.
Compliance also reduces incident likelihood and impact. Organizations with documented risk assessments, tested incident response plans, and continuous monitoring identify threats earlier, contain breaches faster, and limit damage to customer data and business operations.
5) Framework complementarity
Safeguards Rule compliance aligns with broader security frameworks including ISO 27001 and SOC 2. Risk assessment methodologies, control implementation requirements, and continuous monitoring mandates overlap substantially. Organizations pursuing multiple certifications can leverage shared control implementations, unified evidence collection, and integrated risk management processes. This approach reduces compliance overhead while strengthening actual security posture.
Recent updates and amendments
The FTC announced an amendment to the Rule that will require non-banking financial institutions within the FTC's jurisdiction to report data breaches affecting 500 or more people. This October 2023 amendment fundamentally changes incident response obligations for covered entities.
Major changes in the 2021 amendments
The 2021 final rule introduced prescriptive technical requirements that eliminated ambiguity around acceptable security practices. Key changes included mandatory encryption for customer information in transit and at rest, multi-factor authentication requirements, continuous monitoring or periodic penetration testing mandates, and written incident response plan obligations.
The Final Rule expands the definition of "financial institution" to include entities engaged in activities that the Federal Reserve Board determines to be incidental to financial activities, harmonizing the FTC's Safeguards Rule with the safeguards rules of other federal agencies. This expansion captured previously unregulated entities operating at the periphery of financial services.
Breach notification requirements
Such an event requires notification if unencrypted customer information has been acquired without the authorization of the individual to which the information pertains. The notice to the FTC must include certain information about the event, such as the number of consumers affected or potentially affected.
The breach notification amendment became effective May 2024, imposing 30-day reporting deadlines for incidents affecting 500 or more consumers. Organizations must now maintain breach detection capabilities, incident classification procedures, and FTC reporting workflows as operational requirements.
Compliance timelines
Different entity types faced staggered compliance deadlines following the 2021 amendments. While most covered entities had to comply by December 2022, the FTC extended certain deadlines by six months to accommodate implementation challenges. Auto dealerships, specifically called out in the amendments, faced compliance obligations that required substantial security program buildouts for an industry historically lacking formal information security infrastructure.
Upcoming considerations
Organizations should monitor FTC guidance on service provider obligations, potential threshold changes for breach notification, and expanded definitions of covered activities. As financial services increasingly blend with technology platforms, the boundary of "financial institution" continues expanding. Enterprises operating in fintech, embedded finance, or payment facilitation should proactively assess whether regulatory coverage applies or will apply as their business models evolve.
Practical steps for enterprise-selling companies
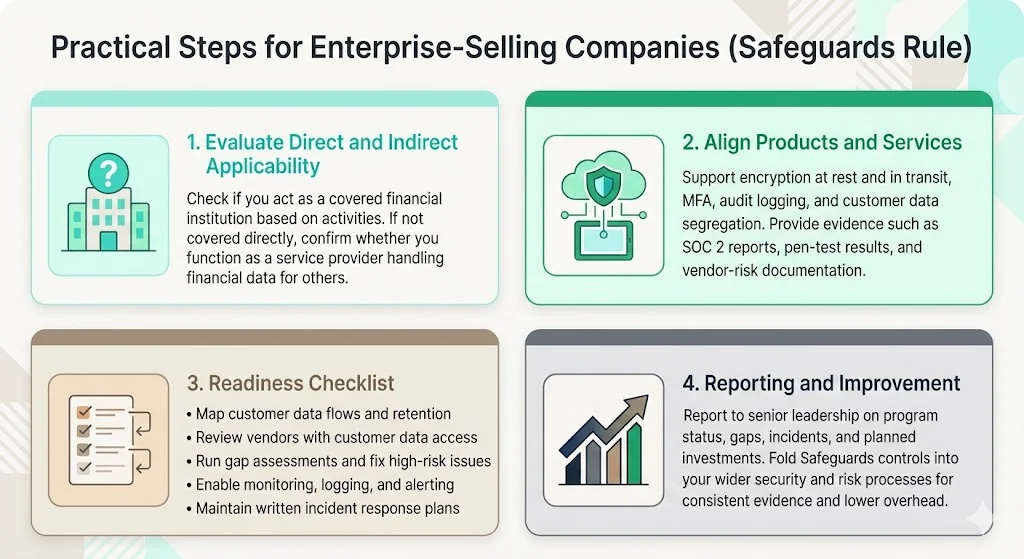
1) Evaluate direct and indirect applicability
Determine whether your organization qualifies as a covered financial institution based on business activities, not industry classification. If you facilitate financial transactions, provide financial advisory services, or engage in activities incidental to financial services, you likely fall within regulatory scope.
If you are not directly covered, assess whether you serve as a service provider to covered entities. Software platforms processing mortgage application data, payment processors handling transaction information, and cloud infrastructure hosting customer financial records all function as service providers subject to contractual safeguards obligations.
2) Align products and services with compliance requirements
Ensure your technical architecture supports encryption at rest and in transit, implements multi-factor authentication, provides detailed audit logging, and enables customer data segregation. If your platform cannot meet these requirements, you create compliance obstacles your clients cannot overcome.
Support clients' risk assessment and evidence collection by documenting your security controls, providing SOC 2 Type II reports, conducting annual penetration testing, and maintaining vendor risk assessment documentation. Position these capabilities as table stakes for enterprise sales, not optional add-ons.
3) Readiness checklist
- Map customer information flows throughout your systems. Identify where data enters your environment, how it moves between systems, where it is stored, and when it is deleted. Document retention periods, encryption status, and access controls at each stage.
- Identify all vendor relationships involving customer information access or processing. Assess whether vendors implement appropriate safeguards, whether contracts require compliance with security standards, and whether you conduct periodic vendor risk assessments.
- Conduct gap assessments comparing your information security program against Safeguards Rule requirements. Identify missing controls, inadequate documentation, and untested procedures. Prioritize remediation based on risk severity and regulatory mandate.
- Implement continuous monitoring, logging, and alerting capabilities. Establish processes for reviewing logs, investigating anomalies, and escalating security events. Document monitoring activities to demonstrate ongoing compliance.
- Develop written incident response plans specifying roles, responsibilities, escalation procedures, notification requirements, and recovery processes. Test plans through tabletop exercises and updates based on lessons learned.
4) Best practices for reporting and improvement
Establish regular reporting cadences to senior leadership and boards of directors on information security program status, compliance gaps, incident trends, and recommended investments. Document decisions, resource allocations, and risk acceptances to demonstrate governance oversight.
Treat the Safeguards Rule as foundational security practice rather than isolated compliance requirement. Integrate mandated controls into broader security operations, vulnerability management programs, and risk management frameworks. Organizations managing multiple compliance obligations should unify control implementations, evidence collection, and assessment processes to reduce overhead while strengthening security posture.
Sector-specific considerations
Auto dealerships
Auto dealerships represent a sector explicitly addressed in the Safeguards Rule amendments. These organizations collect extensive customer information during vehicle financing processes—Social Security numbers, income verification, credit reports, and banking details. Historically, dealerships lacked formal information security programs, leaving customer data vulnerable to breach.
The amendments imposed comprehensive security obligations on an industry unprepared for rigorous cybersecurity compliance. Dealerships now must designate Qualified Individuals, conduct written risk assessments, implement encryption and multi-factor authentication, and develop incident response plans. Compliance required substantial investment in technology infrastructure, personnel training, and ongoing monitoring capabilities.
Fintech and financial service providers
Fintech companies operating as service providers to traditional financial institutions face cascading compliance obligations. If you provide payment processing, data aggregation, credit decisioning, or customer identity verification services to banks, credit unions, or non-bank lenders, you inherit Safeguards Rule obligations through contractual requirements and vendor oversight mandates.
Your clients will require evidence of your security program effectiveness—SOC 2 reports, penetration testing results, vulnerability management documentation, and incident response capabilities. Inability to demonstrate mature security programs eliminates you from vendor consideration by compliance-conscious financial institutions.
Service provider scenario
When your enterprise client is a covered financial institution, vendor risk management becomes central to their compliance strategy. Your client must select service providers capable of maintaining appropriate safeguards, contractually require you to implement such safeguards, and periodically assess the risk you present.
This means your security posture directly affects your client's audit outcomes. If auditors identify deficiencies in your controls, your client faces findings, remediation obligations, and potential regulatory scrutiny. Your inadequate security becomes their compliance failure.
Contracts will specify security requirements, audit rights, breach notification obligations, and indemnification provisions. Expect annual security questionnaires, on-site assessments, and requests for detailed technical documentation. Organizations lacking mature security programs or unwilling to submit to vendor oversight will lose enterprise opportunities to competitors demonstrating compliance readiness.
Illustrative liability scenario
Consider a mortgage broker using a cloud-based loan origination platform. The broker, as a covered financial institution, must ensure the platform vendor implements appropriate safeguards. If the vendor suffers a breach exposing borrower information, the mortgage broker faces FTC enforcement action for inadequate vendor oversight—even though the breach occurred at the vendor.
The broker must demonstrate it conducted due diligence before vendor selection, contractually required appropriate safeguards, and periodically assessed vendor security posture. Failure to document these activities creates regulatory liability. The vendor, meanwhile, faces breach notification obligations, customer notification costs, reputational damage, and potential loss of all clients subject to Safeguards Rule requirements.
Challenges and pitfalls
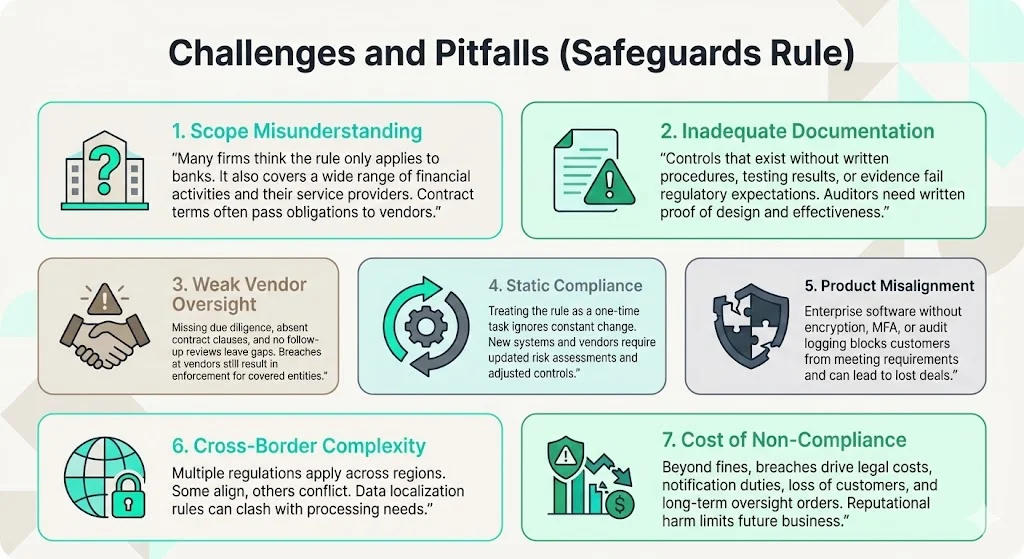
1) Scope misunderstanding
The most common error is assuming "we're not a bank, so the rule doesn't apply." The Rule defines "financial institution" in a way that's broader than how people may use that phrase in conversation. Tax preparation firms, mortgage brokers, payday lenders, collection agencies, and auto dealerships all qualify as financial institutions regardless of how they self-identify.
Service providers make parallel errors, assuming they bear no compliance obligations because they don't directly interact with consumers. Service provider obligations flow through contractual requirements and vendor oversight mandates. Your client's regulatory obligations become your contractual obligations.
2) Inadequate documentation
Organizations implement security controls without documenting their design, implementation, or effectiveness testing. Auditors require written risk assessments, documented control procedures, testing results, and evidence of ongoing monitoring. Controls that exist but lack documentation fail to satisfy regulatory requirements.
3) Weak vendor oversight
Covered entities select service providers without conducting security due diligence, fail to include contractual safeguards requirements, and never reassess vendor risk after initial onboarding. When breaches occur at service providers, covered entities face enforcement action for inadequate vendor management—regardless of where the security failure originated.
4) Static compliance approaches
Organizations treat the Safeguards Rule as a one-time implementation rather than continuous operational discipline. Because your systems and networks change to accommodate new business processes, your safeguards can't be static. The Safeguards Rule requires financial institutions to build change management into their information security program.
Technology environments evolve constantly—new applications, cloud migrations, vendor changes, personnel turnover. Security programs must adapt to these changes through updated risk assessments, modified controls, and revised procedures. Organizations conducting annual compliance reviews discover material gaps only when incidents occur or auditors identify deficiencies.
5) Product misalignment
Enterprise software vendors build products without considering customer compliance obligations. Platforms lacking encryption capabilities, unable to support multi-factor authentication, or missing audit logging functionality create unresolvable compliance gaps for covered entity customers. Sales teams discover late in procurement cycles that their offerings cannot satisfy regulatory requirements, losing deals to competitors offering compliance-ready solutions.
6) Cross-border complexity
Multinational organizations face overlapping regulatory regimes—GDPR in Europe, PIPEDA in Canada, state-level privacy laws in the US, and sector-specific regulations like the Safeguards Rule. Managing customer information across jurisdictions requires understanding which regulations apply to specific data sets, implementing controls satisfying multiple frameworks simultaneously, and documenting compliance with each applicable regime.
Organizations attempt to identify the "highest common denominator" of requirements, implementing controls that satisfy all regulations. This approach works when regulatory mandates align but breaks down when requirements conflict—such as data localization mandates versus cross-border processing needs.
7) Cost of non-compliance
Beyond regulatory fines, non-compliance imposes broader business costs. Breaches result in notification expenses, credit monitoring obligations, legal liability, and customer attrition. Regulatory enforcement triggers multi-year consent orders requiring independent assessments, ongoing FTC reporting, and operational restrictions.
Reputational damage affects competitive positioning. Financial institutions that suffer breaches lose customer trust, face increased scrutiny from regulators, and experience difficulty attracting new business. For service providers, a single breach can eliminate entire customer segments unwilling to accept vendor risk.
Conclusion
Most organizations recognize data security obligations only after breaches occur or regulators investigate. By that point, remediation costs exceed prevention investments by orders of magnitude, and reputational damage persists for years.
The FTC Safeguards Rule applies far beyond traditional banking—extending to mortgage lenders, payday lenders, tax preparation firms, auto dealerships, and countless service providers within the financial ecosystem. Understanding applicability, implementing required controls, and maintaining audit readiness represent baseline expectations for organizations handling customer financial information.
For enterprises selling to covered entities, the Safeguards Rule defines how prospects evaluate vendor risk, assess product capabilities, and structure service provider relationships. Your security program either enables enterprise sales or eliminates you from consideration. Companies treating compliance as operational discipline rather than annual obligation gain competitive advantage, reduce incident likelihood, and position security maturity as strategic differentiator.
Assess your exposure, map customer information flows, implement required controls, and document program effectiveness. Support your clients' compliance efforts by demonstrating security maturity through SOC 2 attestations, penetration testing results, and detailed control documentation. The regulatory landscape continues evolving—organizations establishing strong security foundations adapt efficiently to new requirements while competitors scramble to achieve basic compliance.
Frequently asked questions
1) What is the FTC Safeguard Rule for auto dealers?
Auto dealers that provide financing or facilitate loan applications qualify as financial institutions under the Safeguards Rule. They must implement comprehensive information security programs including designated Qualified Individuals, written risk assessments, encryption of customer information, multi-factor authentication, continuous monitoring, incident response plans, and vendor oversight procedures. Auto dealerships collecting fewer than 5,000 consumer records receive limited exemptions from written risk assessment and incident response plan requirements but remain subject to core security obligations. The industry faced compliance deadlines requiring substantial security infrastructure investments for organizations historically lacking formal cybersecurity programs.
2) What is the main requirement of the FTC Safeguards Rule for a tax return preparer?
Tax return preparers must develop, implement, and maintain written information security programs protecting customer information through administrative, technical, and physical safeguards. This includes designating a Qualified Individual to oversee the security program, conducting periodic written risk assessments, implementing encryption for customer data in transit and at rest, establishing multi-factor authentication, performing continuous monitoring or periodic penetration testing, training personnel, managing service provider risk, developing written incident response plans, and reporting security program status to governing bodies. Tax preparers must also report breaches affecting 500 or more consumers to the FTC within 30 days of discovery. These requirements apply regardless of firm size, though preparers maintaining information on fewer than 5,000 consumers receive limited exemptions from certain documentation requirements.
3) When was the FTC Safeguards Rule created?
Congress recognized the importance of securing consumers' sensitive financial information when it passed the GLBA, which required the FTC to promulgate the Safeguards Rule. The Gramm-Leach-Bliley Act was enacted in 1999, and the Safeguards Rule took effect in 2003. The FTC amended it in 2021 to make sure the Rule keeps pace with current technology. The FTC further amended the Rule in 2023 to require covered entities to report certain data breaches and security incidents.
4) What is the GLBA vs FTC Safeguards Rule?
The Gramm-Leach-Bliley Act is the 1999 federal statute requiring financial institutions to protect consumer financial information. The FTC Safeguards Rule is the regulation implementing GLBA's security requirements for non-bank financial institutions under FTC jurisdiction. Multiple federal agencies issued safeguards rules implementing GLBA for institutions under their regulatory authority—banking regulators for banks, the SEC for registered investment advisors, the CFTC for commodity trading firms. The FTC's version applies to financial institutions not regulated by other agencies, including mortgage lenders, payday lenders, tax preparers, auto dealerships, collection agencies, and non-registered investment advisors. While all safeguards rules stem from GLBA's statutory mandate, each agency's regulation contains specific requirements, exemptions, and enforcement mechanisms tailored to the institutions under its jurisdiction.



.svg)
.svg)
.svg)