Most companies handling health data view HIPAA as a regulatory burden rather than a foundational security discipline. This mindset creates a critical gap between documentation and actual data protection—a gap that becomes evident when breaches occur, federal audits begin, or business partners demand proof of safeguards. HIPAA laws establish mandatory federal standards for protecting sensitive patient health information and govern how covered entities and their business associates handle, store, and transmit protected health information (PHI). The financial exposure is substantial: penalties range from $100 to $50,000 per violation, with annual maximums reaching $1.5 million per violation category. Beyond fines, healthcare privacy failures erode patient trust, disqualify vendors from contracts, and expose organizations to civil litigation.
This guide provides technical decision-makers and compliance leaders with a practical framework for understanding HIPAA's core requirements, identifying where obligations apply within your organization, and implementing controls that protect both patient confidentiality and business continuity.
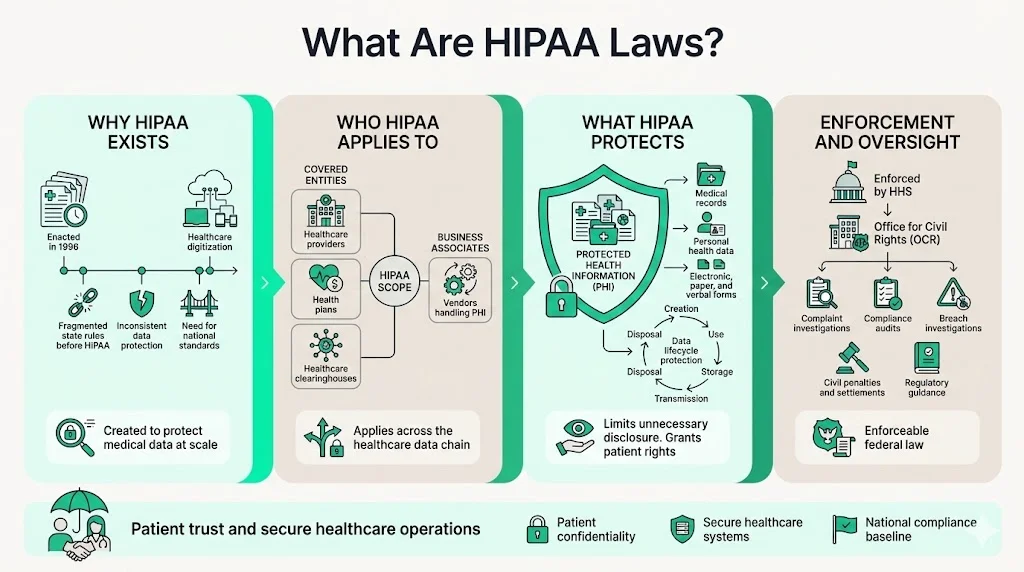
What Are HIPAA Laws?
The Health Insurance Portability and Accountability Act (HIPAA), enacted in 1996, established national standards to protect individuals' medical records and other personal health information. Congress created HIPAA to address systemic vulnerabilities in healthcare data handling as the industry transitioned to electronic systems. Prior to HIPAA, no uniform federal standard governed medical records security or patient confidentiality, leaving health information exposed across fragmented state regulations and inconsistent provider practices.
HIPAA laws apply to covered entities—healthcare providers, health plans, and healthcare clearinghouses—as well as business associates that handle PHI on their behalf. The legislation established baseline requirements for safeguarding protected health information throughout its lifecycle: creation, transmission, storage, and disposal. HIPAA supports patient confidentiality by limiting unnecessary disclosures, granting individuals rights over their own health data, and mandating technical controls to prevent unauthorized access.
The U.S. Department of Health and Human Services (HHS) Office for Civil Rights (OCR) enforces HIPAA laws through compliance audits, breach investigations, and penalty assessments. OCR investigates complaints filed by individuals, conducts proactive compliance reviews, and publishes guidance on regulatory interpretations.
Who Must Comply With HIPAA Laws
HIPAA obligations extend far beyond hospitals and physician practices. Covered entities include healthcare providers who transmit health information electronically, health plans that provide or pay for medical care, and healthcare clearinghouses that process health information. This encompasses dentists, chiropractors, pharmacies, nursing homes, mental health providers, insurance companies, HMOs, employer-sponsored health plans, and government programs including Medicare and Medicaid.
Business associates are individuals or entities that perform functions or activities on behalf of covered entities that involve the use or disclosure of PHI. This category includes IT vendors managing electronic health records, cloud service providers hosting medical data, billing companies processing claims, legal firms reviewing patient files, consultants conducting compliance audits, and third-party administrators managing health plans. Business associates must sign Business Associate Agreements (BAAs) that contractually bind them to HIPAA requirements.
Many organizations incorrectly assume HIPAA applies only to direct patient care. In practice, any vendor accessing, storing, or transmitting PHI—even if only viewing data during system maintenance—qualifies as a business associate. Companies providing analytics services, marketing platforms handling patient communications, and SaaS tools integrated with practice management systems frequently overlook their obligations until contract negotiations or audits reveal the gap.
What Is Protected Health Information (PHI)
Protected health information includes any individually identifiable health information held or transmitted by a covered entity or business associate in any form—electronic, paper, or oral. PHI encompasses medical diagnoses, treatment records, prescription histories, lab results, billing information, insurance claims, appointment schedules, and medical imaging. Individually identifiable means the data includes demographic identifiers such as names, addresses, dates of birth, Social Security numbers, medical record numbers, or biometric identifiers that could reasonably identify a specific individual.
Daily operations generate PHI across multiple formats. Electronic PHI (ePHI) includes data stored in electronic health records, transmitted via email, backed up to cloud storage, or exchanged through health information exchanges. Paper PHI comprises printed medical charts, faxed prescriptions, insurance forms, and written intake documents. Oral PHI involves verbal discussions about patient care between providers, phone conversations with patients, or hallway consultations where patient names and conditions are mentioned.
The distinction between PHI and de-identified data matters significantly for compliance scope. Data becomes de-identified—and exempt from most HIPAA requirements—only when all 18 specified identifiers are removed and the covered entity has no reasonable basis to believe the information could identify an individual. Organizations frequently underestimate how much information qualifies as PHI, particularly metadata like IP addresses in system logs or timestamps in appointment reminders that can be combined with other data to re-identify patients.
The HIPAA Privacy Rule
The Privacy Rule establishes national standards for the protection of PHI by setting limits and conditions on uses and disclosures without patient authorization. The rule creates enforceable patient rights while defining when covered entities may use or disclose protected health information for treatment, payment, and healthcare operations without explicit consent.
Patients have the right to access their medical records, request corrections to inaccurate information, receive an accounting of disclosures, and request restrictions on how their PHI is used or shared. Covered entities must provide individuals with a Notice of Privacy Practices explaining how their information may be used, deliver copies of medical records within 30 days of request, and honor reasonable restrictions on disclosures to health plans when patients pay out-of-pocket in full.
The Privacy Rule permits specific uses and disclosures without authorization: treatment activities require unfettered information sharing between providers; payment operations allow disclosure to insurers and billing services; healthcare operations encompass quality improvement, case management, and business planning activities. Beyond these categories, covered entities must obtain written patient authorization before disclosing PHI for marketing purposes, selling patient data, or releasing psychotherapy notes.
Organizations must maintain comprehensive privacy policies documenting permissible uses, patient rights procedures, complaint processes, and designated privacy officials responsible for implementation. These policies require regular review as operational practices evolve and must be accessible to all workforce members handling PHI.
The HIPAA Security Rule
The Security Rule specifically addresses electronic protected health information (ePHI) and requires covered entities and business associates to implement administrative, physical, and technical safeguards to ensure the confidentiality, integrity, and availability of ePHI.
Administrative safeguards establish the foundation for medical records security through risk analysis, risk management processes, workforce security procedures, and contingency planning. Organizations must conduct comprehensive risk assessments identifying threats to ePHI, implement risk mitigation strategies, assign security responsibilities to specific individuals, enforce sanctions against workforce members who violate policies, and maintain business continuity plans for emergency access to critical health data.
Physical safeguards protect the systems and facilities housing ePHI. This includes facility access controls restricting physical entry to data centers and workstations, workstation security policies governing device placement and usage, device and media controls tracking hardware throughout its lifecycle, and secure disposal procedures ensuring data destruction when equipment is retired or repurposed.
Technical safeguards control electronic access to ePHI and protect data during transmission. Required controls include unique user authentication, emergency access procedures, automatic logoff after inactivity periods, encryption of data at rest and in transit, audit controls logging system activity, and integrity controls detecting unauthorized ePHI alterations.
The Privacy Rule establishes what uses and disclosures are permitted; the Security Rule mandates how electronic systems must be configured to enforce those limitations. While the Privacy Rule governs all PHI formats, the Security Rule applies exclusively to ePHI—though organizations with any electronic health data must implement comprehensive Security Rule controls. This distinction becomes critical during audits when investigators assess whether technical implementations actually enforce documented privacy policies.
HIPAA Compliance Requirements for Companies
HIPAA compliance requires organizations to conduct regular risk assessments, implement policies and procedures addressing all required standards, train workforce members on privacy and security practices, and maintain documentation demonstrating ongoing compliance efforts.
Risk analysis forms the cornerstone of HIPAA compliance. Organizations must systematically identify where ePHI exists within their environment, catalog potential threats and vulnerabilities affecting that data, assess current security measures, and determine the likelihood and impact of potential breaches. Risk management processes then prioritize remediation based on threat severity, implement security measures addressing identified gaps, document decisions regarding risk acceptance when complete mitigation proves infeasible, and continuously monitor effectiveness of controls.
Policy and procedure documentation must address every applicable standard within the Privacy, Security, and Breach Notification Rules. This includes data access controls, minimum necessary standards limiting PHI exposure to what's required for specific tasks, incident response procedures, workforce sanction policies, Business Associate Agreement templates, and patient rights request workflows. Policies require regular review and updates reflecting operational changes, technology implementations, or regulatory guidance.
Workforce training extends beyond annual compliance videos. Effective programs educate staff on recognizing PHI across formats, identifying permitted uses versus situations requiring patient authorization, responding to suspected security incidents, handling patient rights requests, and understanding individual accountability under HIPAA. Training must be documented with attendance records, provided to new workforce members within a reasonable time of hire, and refreshed when policies change or audit findings reveal knowledge gaps.
Compliance responsibilities span departments: IT implements technical safeguards and maintains audit logs; HR conducts background checks and manages workforce sanctions; Legal negotiates Business Associate Agreements and responds to regulatory investigations; Operations enforces minimum necessary policies and physical access controls; Leadership allocates resources and establishes accountability structures. Organizations treating HIPAA as solely an IT or compliance function inevitably discover gaps when cross-functional workflows expose PHI through uncontrolled pathways.
Data Breach Prevention Under HIPAA Laws
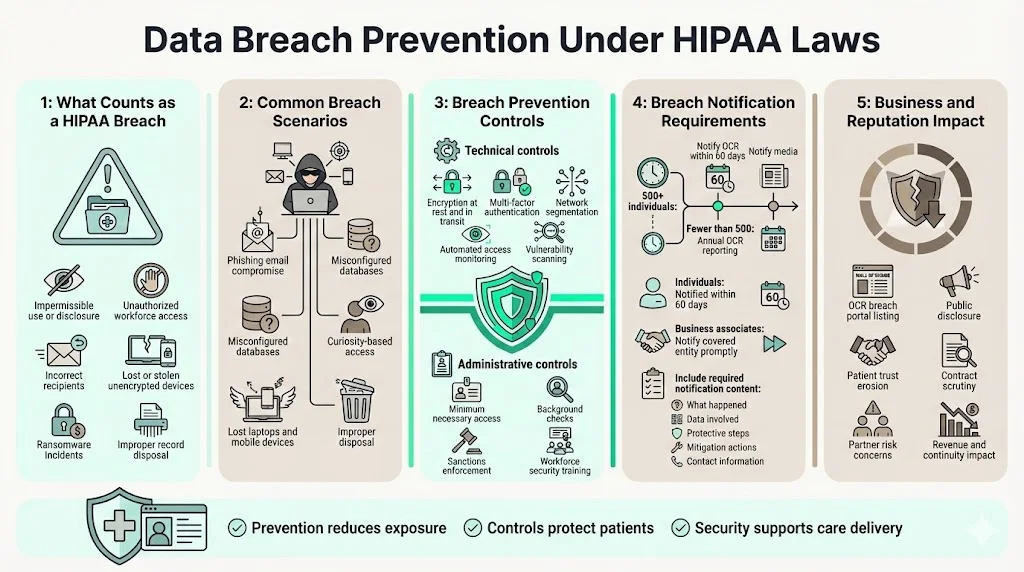
A breach under HIPAA is an impermissible use or disclosure of PHI that compromises the security or privacy of the information. This includes unauthorized access by workforce members lacking a legitimate need, PHI transmitted to incorrect recipients, stolen devices containing unencrypted health data, ransomware attacks encrypting medical records, and improper disposal of records without adequate destruction.
Common causes of healthcare data breaches include hacking and IT incidents, unauthorized access or disclosure by workforce members, theft or loss of physical devices, and improper disposal of records. Phishing attacks compromising email accounts with patient communications, misconfigured databases exposing records to the internet, workforce members accessing celebrity or family member records out of curiosity, and unencrypted laptops stolen from vehicles represent scenarios that trigger breach notification requirements.
Data breach prevention requires layered controls addressing both technical and human vulnerabilities. Technical measures include encryption of ePHI at rest and in transit, multi-factor authentication for system access, network segmentation isolating health data from general corporate systems, automated monitoring detecting anomalous access patterns, and regular vulnerability scanning identifying exploitable weaknesses. Administrative measures include minimum necessary access controls, background checks for workforce members with PHI access, sanctions consistently enforced against policy violations, and security awareness training addressing current threat vectors.
When a breach affects 500 or more individuals, covered entities must notify OCR within 60 days and notify prominent media outlets. For breaches affecting fewer than 500 individuals, entities must notify OCR annually. Affected individuals must be notified within 60 days of breach discovery regardless of breach size. Notification must include a description of the breach, types of information involved, steps individuals should take to protect themselves, what the organization is doing to investigate and prevent recurrence, and contact information for questions. Business associates discovering breaches must notify the covered entity without unreasonable delay and no later than 60 days from discovery.
Breach prevention directly impacts business continuity. Organizations appearing on OCR's public "breach portal"—listing all breaches affecting 500+ individuals—face reputational damage, patient attrition, and increased scrutiny from business partners demanding evidence of improved controls before contract renewal.
HIPAA Enforcement and Penalties
OCR enforces HIPAA through investigations triggered by complaints, breach reports, and compliance reviews, with authority to impose civil monetary penalties and refer cases for criminal prosecution. OCR investigates every breach affecting 500+ individuals, responds to patient complaints alleging privacy violations, and conducts proactive desk audits and on-site investigations targeting specific industries or compliance areas.
Violations are categorized into four tiers based on culpability. Tier 1 involves violations the entity was unaware of and could not have realistically prevented through reasonable diligence (minimum $100 per violation, maximum $25,000 annually). Tier 2 applies when violations should have been known but resulted from reasonable cause rather than willful neglect (minimum $1,000 per violation, maximum $100,000 annually). Tier 3 addresses violations due to willful neglect that are corrected within 30 days (minimum $10,000 per violation, maximum $250,000 annually). Tier 4 involves willful neglect without timely correction (minimum $50,000 per violation, maximum $1.5 million annually per violation category).
Criminal penalties can be imposed for knowing violations, with fines up to $50,000 and one year imprisonment for basic violations, up to $100,000 and five years for violations under false pretenses, and up to $250,000 and ten years for violations with intent to sell or use PHI for commercial advantage, personal gain, or malicious harm.
The financial impact extends beyond federal penalties. State attorneys general may bring civil actions on behalf of state residents, private lawsuits may follow breach disclosures, and business partners frequently terminate contracts or demand costly remediation as conditions of continued relationships. Organizations experiencing breaches averaged $10.93 million in total costs during 2023 according to IBM's Cost of a Data Breach Report—substantially exceeding direct regulatory fines. Reputational damage compounds financial losses as patients switch providers, referral sources question data handling practices, and negative media coverage persists.
HIPAA Laws and Third Parties
Business associates must comply with the same HIPAA requirements as covered entities regarding the PHI they handle, and covered entities remain liable for ensuring their business associates implement adequate safeguards. This shared accountability means covered entities cannot outsource HIPAA compliance risk—they must conduct due diligence before engaging vendors, execute comprehensive Business Associate Agreements, and monitor ongoing compliance.
Business Associate Agreements must specify permitted uses and disclosures of PHI, prohibit unauthorized use or disclosure, require business associates to implement administrative, physical, and technical safeguards, mandate breach notification to the covered entity, ensure business associates obtain similar agreements with their subcontractors, outline procedures for PHI return or destruction upon contract termination, and authorize covered entity access to business associate records for compliance verification.
Organizations frequently discover HIPAA gaps during vendor assessments. Cloud infrastructure providers, email service vendors, customer relationship management platforms, payment processors handling billing information, and even shredding services destroying medical records qualify as business associates requiring BAAs. Technology vendors claiming they are "HIPAA compliant" without willingness to sign BAAs should raise immediate concerns—HIPAA establishes no vendor certification, and compliance occurs only through contractual commitments.
Before engaging third parties, organizations should request evidence of the vendor's HIPAA compliance program including recent risk assessments, security policies, workforce training documentation, and business continuity plans. Review the vendor's breach history through OCR's public breach portal and assess their cyber insurance coverage. Verify encryption capabilities, access logging, and incident response procedures during technical due diligence. Smaller vendors with limited security resources present elevated risk regardless of BAA terms—contractual obligations provide legal recourse but don't prevent breaches.
Practical Steps to Stay Aligned With HIPAA Laws
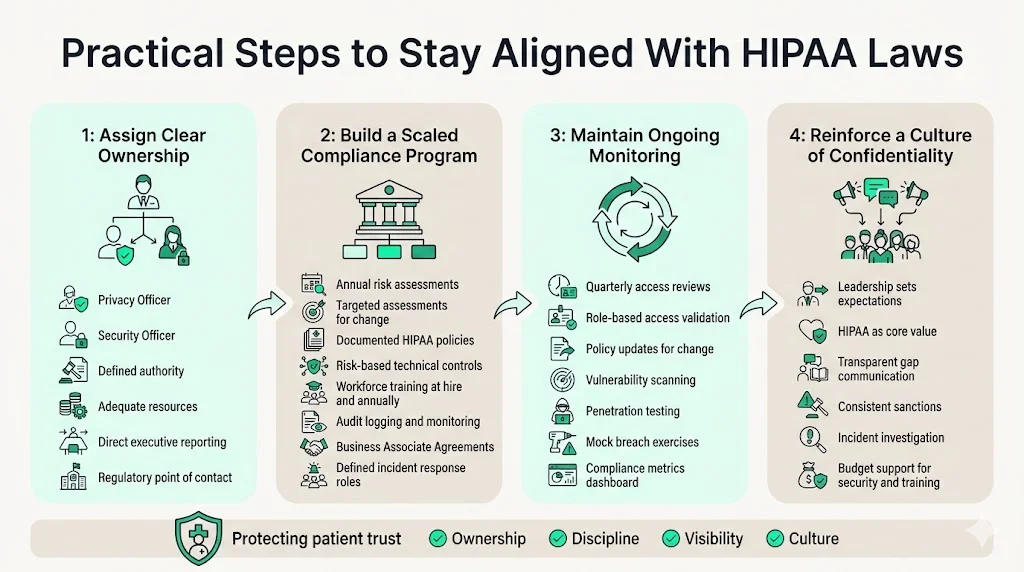
Building sustainable HIPAA compliance begins with appointing a Privacy Officer and Security Officer (roles that may be held by one individual in smaller organizations) with defined authority, adequate resources, and direct reporting lines to executive leadership. These officers coordinate risk assessments, maintain policy documentation, oversee training programs, investigate incidents, and serve as primary contacts for regulatory inquiries.
Establish a compliance program scaled to organizational size and complexity. This includes conducting annual comprehensive risk assessments supplemented by targeted assessments when implementing new technologies or business processes, documenting policies addressing all applicable HIPAA standards, implementing technical controls based on risk assessment findings, conducting workforce training at hire and annually thereafter, maintaining audit logs and monitoring for security incidents, executing Business Associate Agreements with all applicable vendors, and establishing incident response procedures with defined roles and escalation paths.
Ongoing monitoring prevents compliance drift as operations evolve. Quarterly access reviews ensure workforce members retain only necessary PHI access based on current roles. Regular policy reviews address changes in business practices, technology implementations, or regulatory guidance. Vulnerability scanning and penetration testing identify technical weaknesses before exploitation. Mock breach scenarios test incident response capabilities and identify gaps in communication protocols. Compliance metrics tracking training completion, policy acknowledgment, access review status, and open risk findings provide leadership visibility into program health.
Creating a culture of patient confidentiality requires consistent messaging from leadership that HIPAA represents core business values rather than regulatory overhead. Celebrate compliance successes, communicate transparently about identified gaps and remediation efforts, investigate all suspected violations regardless of severity, enforce workforce sanctions consistently, and allocate adequate budget for security tools, compliance staff, and training programs. Organizations where leadership treats HIPAA as perfunctory inevitably experience workforce members adopting the same attitude—creating vulnerabilities that become apparent during incidents or investigations.
Conclusion
HIPAA laws establish mandatory baseline requirements for protecting patient health information, but compliance represents more than satisfying auditors. Organizations implementing controls that genuinely safeguard PHI—rather than generating documentation artifacts—build patient trust, reduce breach risk, maintain business partner relationships, and avoid regulatory penalties that fundamentally threaten financial stability.
The connection between compliance posture and business outcomes becomes evident during critical moments: when enterprise customers require SOC 2 reports demonstrating comprehensive data protection, when breach investigations reveal whether controls actually functioned as documented, when insurance carriers assess cyber liability based on implemented safeguards. Treating HIPAA as an operational discipline embedded within security infrastructure produces sustainable compliance as a natural outcome rather than an annual scramble before audits.
For organizations handling protected health information, HIPAA compliance cannot be delegated to a single department or satisfied through policy documents disconnected from daily operations. It requires cross-functional commitment, adequate resource allocation, continuous monitoring, and leadership accountability for both regulatory requirements and the patient confidentiality those requirements were designed to protect.
FAQ Section
1) What are HIPAA laws?
HIPAA laws are federal regulations enacted through the Health Insurance Portability and Accountability Act of 1996 that establish mandatory standards for protecting patient health information. These laws govern how covered entities and business associates must handle, store, transmit, and dispose of protected health information, establishing specific requirements for privacy policies, security controls, breach notification, and patient rights. HIPAA applies across all formats—electronic, paper, and oral communications—and is enforced by the U.S. Department of Health and Human Services Office for Civil Rights through investigations, audits, and financial penalties.
2) Who must comply with HIPAA?
Covered entities—healthcare providers conducting electronic transactions, health plans, and healthcare clearinghouses—must comply with HIPAA along with their business associates. Business associates include any vendor, contractor, or service provider that accesses, stores, transmits, or processes protected health information on behalf of covered entities, encompassing IT vendors, cloud service providers, billing companies, legal firms, consultants, and third-party administrators. Common gray areas include employers who sponsor health plans (HIPAA applies to the plan administration function but not general employment records), health apps not connected to covered entities, and vendors who claim they merely host data without accessing it (if the vendor has any technical ability to view PHI, business associate obligations typically apply).
3) What is protected health information?
Protected health information is any individually identifiable health information held or transmitted by a covered entity or business associate in any form—electronic, paper, or oral. This includes medical diagnoses, treatment records, prescription histories, lab results, billing information, insurance claims, appointment schedules, and any data containing identifiers such as names, addresses, dates of birth, Social Security numbers, or medical record numbers that could reasonably identify a specific patient. Real examples include patient charts, email messages discussing treatment, voicemails about test results, billing statements, and database records linking diagnoses to patient identifiers. PHI exists across clinical, billing, scheduling, and administrative systems throughout healthcare operations.
4) What happens if a company violates HIPAA?
HIPAA violations result in civil monetary penalties ranging from $100 to $50,000 per violation depending on culpability level, with annual maximums reaching $1.5 million per violation category. Violations involving willful neglect carry minimum penalties of $10,000 per violation; uncorrected willful neglect requires minimum $50,000 penalties. Criminal violations can result in fines up to $250,000 and imprisonment up to ten years for violations involving intent to sell PHI or obtain commercial advantage. Beyond federal enforcement, organizations face state attorney general actions, private civil litigation, breach notification costs, forensic investigation expenses, reputational damage, patient attrition, and business partner contract terminations. The total business impact of healthcare breaches averages $10.93 million according to recent industry studies, substantially exceeding direct regulatory fines.
5) Does HIPAA apply to vendors and service providers?
HIPAA applies to vendors and service providers that access, store, transmit, or process protected health information on behalf of covered entities, classifying them as business associates with direct compliance obligations. Business associates must implement the same administrative, physical, and technical safeguards required of covered entities, sign Business Associate Agreements establishing contractual obligations, conduct risk assessments, maintain policies and procedures, train their workforce, and report breaches to covered entities within 60 days of discovery. This applies to cloud hosting providers, IT support vendors, billing services, email platforms handling patient communications, analytics companies processing health data, and any subcontractors used by business associates. Covered entities cannot outsource HIPAA liability—they remain responsible for ensuring business associates maintain adequate safeguards through due diligence, contractual agreements, and ongoing monitoring.



.svg)
.svg)
.svg)