Most healthcare-focused companies underestimate whether HIPAA obligations apply to them. They assume compliance requirements belong exclusively to hospitals, clinics, and health plans—a misunderstanding that becomes costly when enforcement actions follow undocumented data sharing or unsecured systems. A "business associate" is any person or entity, other than a member of the workforce of a covered entity, who performs functions or activities on behalf of, or provides certain services to, a covered entity that involve access by the business associate to protected health information. This definition extends regulatory duties far beyond direct care delivery.
Health data security expectations have intensified considerably. The Department of Health and Human Services (HHS) published a Notice of Proposed Rulemaking in January 2025 which, when finalized, will require covered entities to obtain written verifications from their HIPAA business associates that each HIPAA business associate has deployed and is operating technical safeguards that protect the confidentiality, integrity, and availability of PHI maintained on electronic information systems. This means organizations handling protected health information now face heightened scrutiny and mandatory verification processes previously reserved for covered entities alone.
This article provides a practical overview of what qualifies a company as a HIPAA business associate, the security and contractual requirements that follow, and the operational steps required to maintain defensible compliance. It addresses technical decision-makers and business leaders responsible for protecting patient data and managing regulatory exposure.
Understanding the HIPAA Business Associate Concept
By law, the HIPAA Privacy Rule applies only to covered entities – health plans, health care clearinghouses, and certain health care providers. However, most covered entities rely on external vendors, contractors, and service providers to perform essential healthcare functions. When those third parties access, process, or store protected health information, they become subject to HIPAA obligations as business associates.
The distinction between covered entities and business associates matters because it determines which regulatory provisions apply and how liability flows when breaches occur. Covered entities are regulated directly under HIPAA's foundational rules. Business associates are regulated through contractual obligations with covered entities and through direct enforcement authority granted to HHS under the HITECH Act.
The HITECH Act made HIPAA business associates and their downstream subcontractors directly liable for compliance with certain requirements of the HIPAA Rules. The direct liability of HIPAA business associates and downstream subcontractors was codified in the HIPAA Omnibus Final Rule in 2013. This means business associates face enforcement actions independently—not merely as extensions of covered entity liability.
The U.S. Department of Health & Human Services provides detailed guidance on business associate obligations under 45 CFR 160.103, which defines the scope of entities subject to HIPAA requirements and clarifies when contractual safeguards are mandatory.
What Qualifies a Company as a HIPAA Business Associate
The core criterion is straightforward: any organization that creates, receives, maintains, or transmits protected health information on behalf of a covered entity qualifies as a business associate. This includes entities performing services that require routine access to PHI, even when that access is incidental to the primary service provided.
Access alone triggers business associate status. Companies do not need to "handle" PHI in a clinical sense. If systems process, store, or transmit PHI—even temporarily—the organization meets the threshold. This catches many technology vendors, infrastructure providers, and professional service firms off guard.
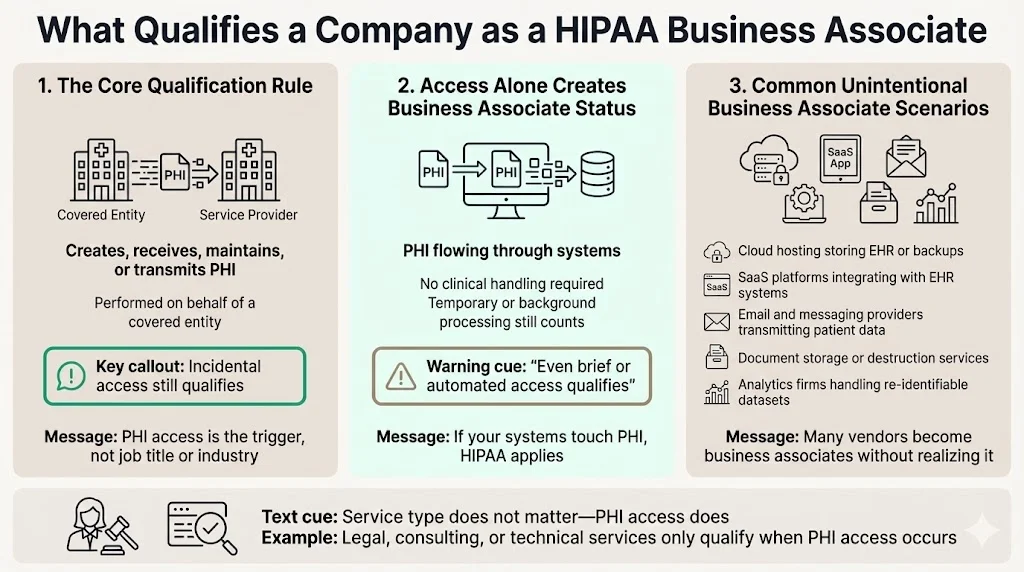
Common scenarios where companies unintentionally become business associates include:
- Cloud hosting providers storing electronic health records or backup data containing PHI
- Software-as-a-service platforms that integrate with EHR systems and cache patient identifiers or clinical notes
- Email and communication vendors transmitting messages containing appointment details, treatment notes, or billing information
- Document storage and destruction services handling paper or digital records containing patient information
- Third-party analytics firms processing de-identified datasets that retain sufficient detail to allow re-identification
HHS' list includes an attorney whose legal services to a health plan include access to PHI. If the attorney does not have access to PHI, they are not a business associate, and no HIPAA Business Associate Agreement is required. This principle applies universally: the trigger is PHI access during service delivery, not the nature of the service itself.
Common Examples of HIPAA Business Associates
Cloud service providers hosting patient data rank among the most common business associates. Whether providing infrastructure-as-a-service, platform-as-a-service, or application hosting, any vendor storing electronic protected health information (ePHI) on behalf of a covered entity qualifies.
Billing, coding, and revenue cycle management vendors routinely access patient demographics, diagnosis codes, procedure details, and insurance information—all categories of PHI. These organizations process claims, manage accounts receivable, and conduct payment reconciliation, requiring sustained access to protected data.
EHR and healthcare software companies provide systems that create, store, and transmit the vast majority of clinical documentation. These vendors manage databases containing comprehensive patient records and must implement administrative, physical, and technical safeguards commensurate with the sensitivity of the data.
Data analytics and reporting firms often receive datasets for population health analysis, quality reporting, or utilization review. Even when data is represented as de-identified, organizations must verify that re-identification risk has been mitigated consistent with Safe Harbor or Expert Determination standards under 45 CFR §164.514.
Legal, accounting, and consulting services become business associates when engagements require reviewing patient records, auditing billing practices, or advising on compliance matters involving PHI. Professional service providers conducting due diligence, forensic investigations, or litigation support regularly encounter protected information and must execute business associate agreements before access begins.
The Role of Data Sharing Agreements in HIPAA Compliance
The HIPAA Rules generally require that covered entities and business associates enter into contracts with their business associates to ensure that the business associates will appropriately safeguard protected health information. The business associate contract also serves to clarify and limit, as appropriate, the permissible uses and disclosures of protected health information by the business associate, based on the relationship between the parties and the activities or services being performed by the business associate.
Written agreements must be executed before PHI access begins. This requirement is not procedural—it is substantive. Not having a valid BAA in place is a direct HIPAA violation—even if no breach occurs. Regulators treat the absence of a signed agreement as evidence of noncompliance, regardless of whether security controls are otherwise robust.
Data sharing agreements support confidentiality obligations by establishing the permitted scope of PHI use, defining security responsibilities, and documenting how both parties will respond when incidents occur. These agreements create enforceable obligations that extend HIPAA's regulatory framework into contractual relationships, making compliance measurable and auditable.
What is a Business Associate Agreement (BAA)
A Business Associate Agreement is a written contract required under HIPAA that defines the responsibilities of a business associate when handling PHI. A written contract between a covered entity and a business associate must: (1) establish the permitted and required uses and disclosures of protected health information by the business associate; (2) provide that the business associate will not use or further disclose the information other than as permitted or required by the contract or as required by law; (3) require the business associate to implement appropriate safeguards to prevent unauthorized use or disclosure of the information, including implementing requirements of the HIPAA Security Rule with regard to electronic protected health information.
Required elements outlined by regulators under 45 CFR §164.504(e)(2) include specifications for how PHI may be used, obligations to report unauthorized disclosures or breaches, requirements to make records available during audits or investigations, and provisions ensuring that subcontractors also execute compliant agreements.
A BAA sets limits on PHI use and disclosure by defining the minimum necessary standard applicable to the relationship, restricting secondary uses unrelated to the service being performed, and requiring that data be returned or destroyed when the contract terminates. These contractual guardrails prevent scope creep and ensure that PHI access remains narrowly tailored to legitimate business purposes.
BAAs support health data security goals by requiring business associates to implement administrative, physical, and technical safeguards consistent with the HIPAA Security Rule, conduct risk assessments, train workforce members, and maintain documentation demonstrating ongoing compliance.
Security and Privacy Safeguards Business Associates Must Apply
Business associates must implement safeguards across three domains mandated by the HIPAA Security Rule: administrative, physical, and technical.
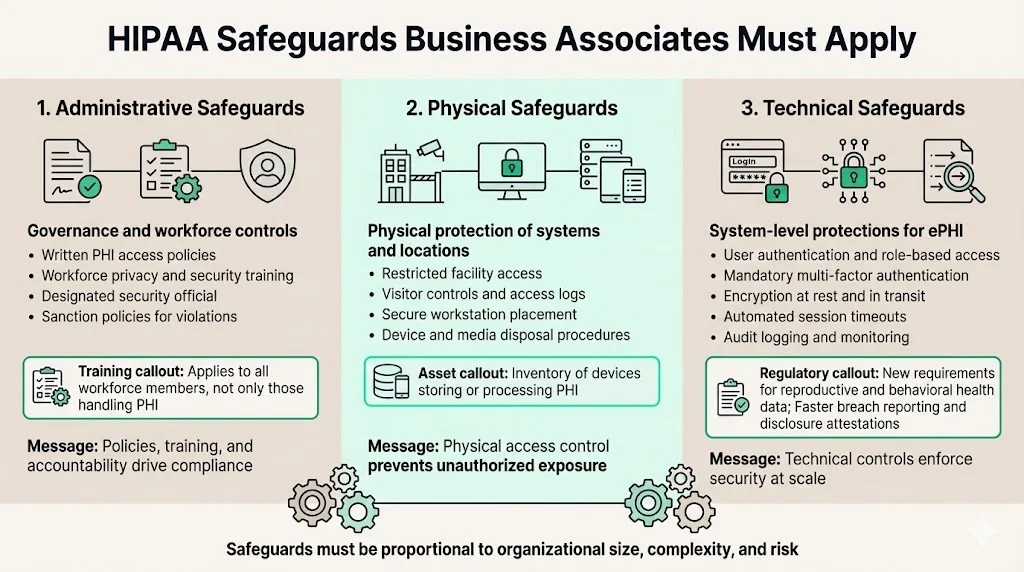
Administrative safeguards include written policies governing PHI access, workforce training programs covering privacy and security obligations, and access controls ensuring that only authorized personnel interact with protected data. Both covered entities and business associates are required to comply with the HIPAA Security Rule training standard, which applies to all members of the workforce regardless of whether they have access to PHI or not. Organizations must designate a security official responsible for policy development and compliance oversight, conduct regular workforce security awareness training, and implement sanction policies for violations.
Physical safeguards address facility access controls, workstation security, and device management. This includes restricting physical access to locations where ePHI is stored, ensuring workstations are positioned to prevent unauthorized viewing, and establishing procedures for the secure disposal of hardware containing protected data. Organizations must document facility access logs, implement visitor controls, and maintain inventories of devices storing or processing PHI.
Technical safeguards encompass user authentication, encryption, audit logging, and transmission security. The 2026 changes include stricter privacy protections for reproductive and behavioral health data, new attestation requirements for PHI disclosures, mandatory MFA, encryption standards for ePHI, and faster breach reporting from business associates. Multi-factor authentication, role-based access controls, and automated session timeouts reduce the risk of unauthorized access. Encryption at rest and in transit protects data confidentiality during storage and transmission. Audit logs capture access events, modifications, and security-relevant activities, enabling forensic investigation when incidents occur.
These safeguards align with HIPAA security standards by implementing controls proportional to the size, complexity, and risk profile of the organization while maintaining flexibility for technology-specific implementation choices.
Security Risk Assessment Expectations
A security risk assessment is required under 45 CFR §164.308(a)(1)(ii)(A) as part of the administrative safeguards standard. Regulators expect business associates to conduct comprehensive reviews identifying threats to ePHI confidentiality, integrity, and availability; evaluating current safeguards; determining residual risk; and documenting remediation plans for identified vulnerabilities.
Organizations must review system configurations, access controls, encryption implementations, backup procedures, incident response capabilities, vendor management practices, and workforce training effectiveness. Assessments should examine both technical infrastructure and operational processes, capturing risks that span technology, personnel, and third-party relationships.
Security risk assessments reduce the chance of a HIPAA violation by surfacing control gaps before regulators or auditors identify them, enabling prioritized remediation based on risk severity, and demonstrating organizational commitment to proactive compliance. Regular assessments provide evidence of continuous monitoring and improvement—factors that influence enforcement decisions when violations occur.
Ongoing review is required, not one-time assessments. Risk profiles evolve as systems change, threats emerge, and business operations expand. Organizations should conduct formal risk assessments annually at minimum, with interim reviews triggered by significant infrastructure changes, new vendor relationships, security incidents, or regulatory updates.
Data Breach Mitigation and Incident Response
The business associate must report any unauthorized use or disclosure of PHI or any security incident or breach of unsecured PHI to the covered entity. HIPAA defines a breach as an unauthorized acquisition, access, use, or disclosure of PHI that compromises its security or privacy, with limited exceptions for unintentional access by authorized workforce members, inadvertent disclosures between authorized persons, and situations where the recipient could not reasonably retain the information.
Required response steps after discovery include immediately securing systems to prevent further unauthorized access, conducting an internal investigation to determine the scope and cause of the breach, assessing whether the breach meets regulatory notification thresholds, and coordinating with covered entities to fulfill reporting obligations.
Under the expected revisions, business associates must report security incidents within 24 hours of discovery. This change aims to tighten breach response across the healthcare data supply chain. Notification timelines require business associates to inform covered entities without unreasonable delay and no later than 60 days after breach discovery. Covered entities must then notify affected individuals, the Secretary of HHS, and in some cases, media outlets—with specific deadlines depending on breach severity.
Responsibilities extend beyond notification. Business associates must provide covered entities with sufficient information to assess breach impact, including the date of discovery, a description of the PHI involved, the number of individuals affected, and remediation steps taken. Strong preparation limits damage and penalties by reducing response time, minimizing the number of affected individuals, demonstrating proactive safeguards, and providing regulators with evidence of good-faith compliance efforts.
Liability and Enforcement After a HIPAA Violation
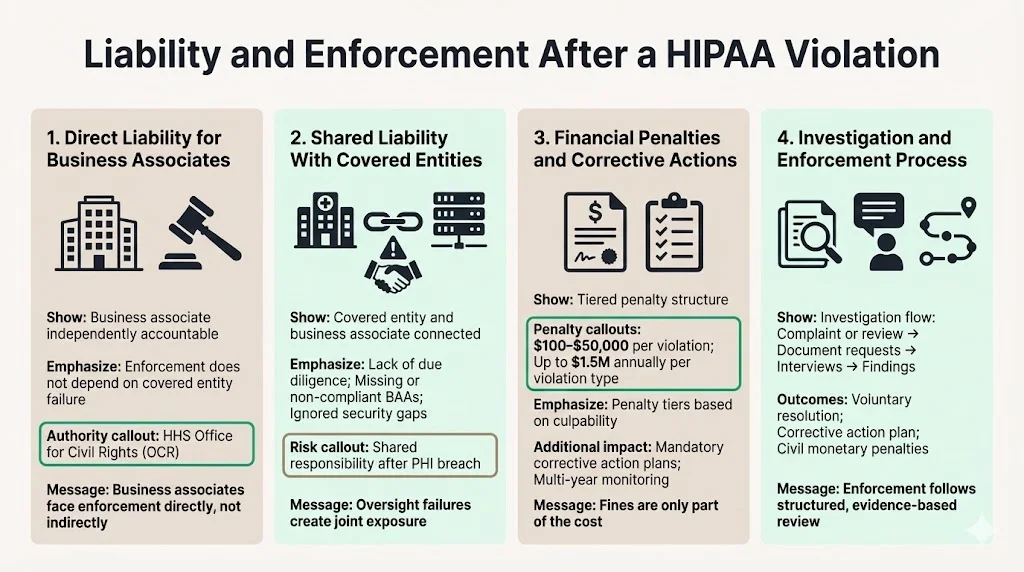
In addition to these contractual obligations, business associates are directly liable for compliance with certain provisions of the HIPAA Rules. This means HHS Office for Civil Rights (OCR) can initiate enforcement actions against business associates independently, without requiring proof that the covered entity failed to fulfill oversight duties.
When a business associate violates HIPAA, liability may be shared with covered entities if the covered entity failed to conduct adequate due diligence, did not execute a compliant BAA, or ignored known security deficiencies. If a covered entity fails to conduct due diligence to ensure a business associate is HIPAA-compliant prior to entering into an agreement, and a breach of unsecured PHI subsequently occurs, the covered entity may be considered liable for the breach.
Under the HIPAA Enforcement Rule, HHS can impose civil monetary penalties ranging from $100 to $50,000 per violation, up to $1.5 million per year per violation type. Penalties are tiered based on the level of culpability, ranging from violations due to reasonable cause to those resulting from willful neglect that is not corrected. Corrective action plans typically accompany financial penalties, requiring organizations to remediate identified deficiencies, implement enhanced monitoring, and submit to multi-year compliance audits.
Enforcement actions usually unfold through complaint-driven investigations or proactive compliance reviews. OCR initiates an inquiry, requests documentation of policies and safeguards, interviews personnel, and assesses whether violations occurred. When violations are substantiated, OCR may pursue voluntary resolution agreements, corrective action plans, or civil monetary penalties depending on severity and the organization's cooperation.
Subcontractors and Downstream Responsibility
A "business associate" also is a subcontractor that creates, receives, maintains, or transmits protected health information on behalf of another business associate. This means that when business associates engage vendors or service providers who will access PHI, those subcontractors become subject to HIPAA requirements and must execute their own business associate agreements.
Flow-down requirements for BAAs obligate primary business associates to ensure subcontractors implement equivalent safeguards, comply with breach notification duties, and make PHI available for audits or investigations. Business associates must obtain BAAs with their own subcontractors if they handle PHI. These downstream agreements must mirror the protections established in the primary BAA between the covered entity and the business associate.
Oversight duties for primary business associates include conducting due diligence before engaging subcontractors, monitoring subcontractor compliance through audits or attestations, and ensuring that contract terms permit termination if HIPAA violations occur. Organizations cannot delegate compliance responsibility—primary business associates remain accountable for subcontractor conduct.
Risks tied to weak vendor management include regulatory liability for subcontractor breaches, reputational damage when downstream vendors fail to protect PHI, operational disruptions when subcontractor relationships must be terminated due to noncompliance, and enforcement actions based on inadequate oversight. Effective vendor management programs establish selection criteria, conduct regular compliance reviews, and maintain documentation demonstrating active supervision.
Practical Compliance Steps for Healthcare-Focused Companies
Identifying whether your company qualifies as a business associate requires mapping data flows between your organization and any covered entities you serve. Document what information systems access, whether PHI is stored temporarily or persistently, and whether services involve creating, modifying, or transmitting protected data. If any service function requires PHI access, business associate status applies.
Reviewing current data flows and PHI access involves conducting system inventories, interviewing personnel about operational processes, analyzing integration points with covered entity systems, and assessing subcontractor relationships. This review should produce a comprehensive data map showing where PHI enters your environment, how it moves between systems, where it is stored, and when it is transmitted externally.
Updating agreements and internal controls means executing compliant BAAs with all covered entities, revising subcontractor agreements to include flow-down provisions, implementing administrative, physical, and technical safeguards consistent with risk assessment findings, and establishing policies governing PHI use, disclosure, and retention.
Building compliance into daily operations requires assigning accountability for HIPAA oversight, conducting workforce training on privacy and security obligations, implementing audit logging and monitoring to detect unauthorized access, establishing incident response procedures, and scheduling regular risk assessments to identify emerging vulnerabilities. Compliance is not a project—it is an operational discipline requiring sustained attention and resource allocation.
Common Mistakes Companies Make
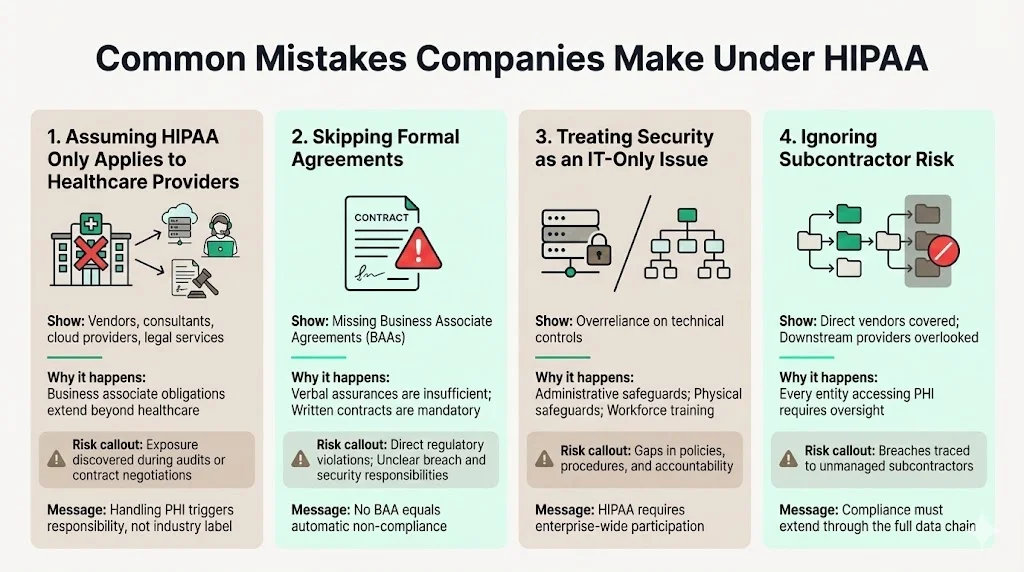
Assuming HIPAA only applies to healthcare providers remains the most pervasive misconception. Technology vendors, consulting firms, legal service providers, and infrastructure companies frequently underestimate their regulatory exposure, only discovering business associate obligations when regulators initiate investigations or covered entities demand BAAs during contract negotiations.
Skipping formal agreements creates direct regulatory violations and leaves both parties without contractual clarity on permitted uses, security requirements, or breach notification duties. Verbal assurances and informal understandings do not satisfy HIPAA's written contract requirement.
Treating security as an IT-only issue ignores the administrative and physical safeguard domains, neglects workforce training requirements, and fails to integrate compliance into business processes. Security is an enterprise-wide discipline requiring participation from legal, operations, human resources, and executive leadership—not merely technical infrastructure teams.
Underestimating subcontractor exposure leads organizations to execute BAAs for direct vendor relationships while overlooking downstream service providers who access PHI on their behalf. Every layer in the data supply chain requires contractual protections and compliance verification. Failure to manage subcontractor risk creates enforcement exposure and operational vulnerabilities that become apparent only after breaches occur.
Conclusion
Understanding the HIPAA business associate role protects both companies and patients by establishing clear accountability for PHI security, reducing breach risk through mandatory safeguards, and creating enforceable contractual frameworks that extend regulatory obligations throughout the healthcare data supply chain. Organizations that recognize business associate status early, implement comprehensive compliance programs, and maintain continuous oversight reduce regulatory exposure while demonstrating commitment to patient privacy.
The long-term value of strong compliance habits extends beyond avoiding penalties. Companies with mature HIPAA programs gain competitive advantage when pursuing healthcare clients, reduce operational disruption from security incidents, and build organizational resilience that supports sustainable growth in regulated markets. Compliance is not overhead—it is foundational infrastructure that enables secure, trustworthy healthcare operations.
Frequently Asked Questions
1) What qualifies a company as a business associate?
A company qualifies as a business associate when it creates, receives, maintains, or transmits protected health information on behalf of a covered entity while performing services or functions for that covered entity. The trigger is PHI access during service delivery, not the nature of the service itself. This includes technology vendors, billing companies, consultants, legal service providers, and any other organization whose operations require routine interaction with patient data.
2) What is a BAA?
A Business Associate Agreement is a written contract required under 45 CFR §164.504(e) that establishes the responsibilities of a business associate when handling PHI. It defines permitted uses and disclosures, requires implementation of administrative, physical, and technical safeguards, obligates the business associate to report breaches, and ensures that subcontractors also comply with HIPAA requirements. The BAA creates enforceable legal obligations that extend regulatory compliance beyond covered entities to their service providers.
3) What safeguards are required?
Business associates must implement administrative safeguards including workforce training, access controls, and written policies; physical safeguards addressing facility access, workstation security, and device management; and technical safeguards encompassing encryption, audit logging, user authentication, and transmission security. These safeguards must be proportional to organizational risk profiles and aligned with HIPAA Security Rule standards under 45 CFR §§164.308–164.312.
4) Who is liable after a breach?
Business associates are directly liable for HIPAA violations and can face enforcement actions independently from covered entities. Liability may be shared when covered entities fail to conduct due diligence, execute compliant BAAs, or oversee business associate compliance adequately. Civil monetary penalties range from $100 to $50,000 per violation, with annual maximums reaching $1.5 million per violation type, depending on culpability level and whether willful neglect was corrected.
5) Do subcontractors count?
Subcontractors count as business associates when they create, receive, maintain, or transmit PHI on behalf of a primary business associate. Primary business associates must execute BAAs with subcontractors that mirror the protections established with covered entities, conduct ongoing oversight, and maintain accountability for subcontractor compliance. Flow-down requirements extend HIPAA obligations throughout the entire data supply chain, making vendor management a critical compliance function.



.svg)
.svg)
.svg)