Most organizations approach HITRUST as another checkbox certification—an add-on credential to satisfy enterprise sales cycles. This creates a fundamental misunderstanding of what HITRUST actually represents: a comprehensive risk management framework that unifies more than 60 regulatory standards, industry frameworks, and authoritative sources into a single, certifiable structure. Organizations treating HITRUST as a simple attestation discover the gap when they attempt certification and encounter the framework's rigorous control requirements, maturity scoring, and evidence collection processes.
What is HITRUST?
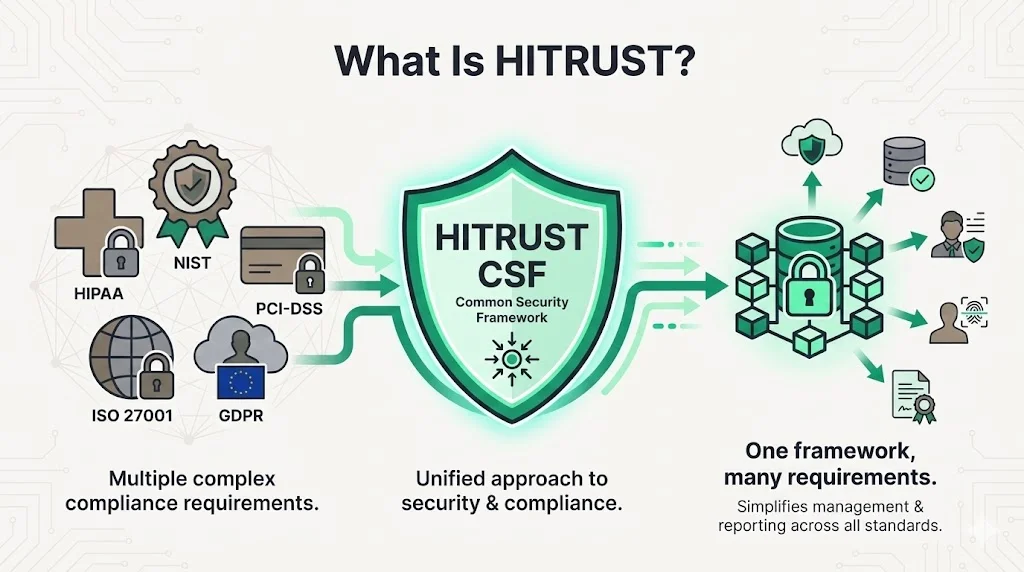
The HITRUST Common Security Framework (CSF) harmonizes over 60 regulations, standards, frameworks, and other authoritative sources into a comprehensive, consistent set of controls to achieve compliance. The framework is maintained by the HITRUST Alliance—a not-for-profit organization that brings together healthcare, technology, business, and information security leaders to establish common security and privacy standards.
HITRUST CSF exists to simplify the compliance landscape for organizations managing sensitive data. Rather than conducting separate assessments for HIPAA, ISO 27001, NIST, PCI-DSS, GDPR, and other regulatory requirements, organizations implement HITRUST controls once and demonstrate compliance across multiple standards simultaneously. HITRUST standardizes the process of designing, implementing, and assessing security controls, providing a unified, risk-based approach for addressing various regulatory mandates.
Although HITRUST originated in healthcare—hence "Health Information" in its name—the framework is industry-agnostic. Financial services, higher education, retail, and IT service providers increasingly leverage HITRUST to streamline compliance and strengthen security posture. HITRUST-certified environments maintain a 99.41% breach-free rate, demonstrating the framework's effectiveness in reducing actual security risk, not just satisfying auditors.
Structure of HITRUST — Domains, Control Categories, Objectives, Controls
Understanding HITRUST's hierarchical structure is essential for organizations navigating certification. The framework organizes security requirements through multiple layers—domains, control categories, objectives, and individual controls—each serving a distinct purpose in risk management and compliance.
Domains
HITRUST CSF consists of 19 domains, each addressing specific areas of risk management and regulatory compliance. The official CSF typically references 19 domains, though the number can vary slightly depending on HITRUST updates and versions.
These domains organize controls into functional areas such as access control, data protection, endpoint and mobile device security, risk management, physical and environmental security, incident response, business continuity, and third-party risk management. These 19 assessment domains include access control, vulnerability management, and data protection. The domain structure allows organizations to target specific risk areas rather than navigate unstructured compliance requirements.
Control Categories, Objectives, Controls and Implementation Levels
HITRUST CSF contains 14 control categories, comprising 49 control objectives and 156 control specifications. Control categories are numbered 0.0 through 0.13.
The 14 control categories include Information Security Management Program, Access Control, Human Resources Security, Physical and Environmental Security, Communications and Operations Management, Information Systems Acquisition Development and Maintenance, Information Security Incident Management, Business Continuity Management, Compliance, Risk Management, and Privacy. Each control category includes control objectives and control specifications, leveraging primary categories from ISO/IEC framework, along with specific categories for information security management programs and risk management practices.
Under categories sit control objectives—49 in total—representing desired outcomes or purposes to be achieved. Under objectives are individual controls: safeguards or countermeasures prescribed to protect confidentiality, integrity, and availability of information. The framework is structured around 14 control categories, 49 control objectives, and 156 control references, supported by more than 1,900 requirement statements.
There are 3 Implementation Levels within the HITRUST CSF framework. Implementation levels determine how strictly controls must be applied based on organizational risk, regulatory requirements, and system-level factors. Organizations with higher risk profiles—those processing large volumes of sensitive data or operating in heavily regulated industries—face more rigorous implementation requirements than smaller organizations with limited data exposure.
Scoring / Maturity / Assessment Scope
Scope defines the information assets, data flows, systems, and infrastructure components included in a HITRUST assessment. Only systems and data within the defined scope receive HITRUST certification coverage. Organizations must clearly document boundaries—what's in scope and what's explicitly excluded—to avoid gaps between certified systems and actual operational environments.
The maturity model provides a rating scheme gauging how thoroughly controls are implemented. HITRUST assessments evaluate organizations across five maturity levels: policy, procedure, implemented, measured, and managed. Each level contributes a weighted percentage to the overall score. Organizations progress from documented policies (lowest maturity) through established procedures, implemented controls, measured effectiveness, and finally managed optimization.
Control maturity scoring determines certification eligibility. To achieve certification, organizations must meet minimum scoring thresholds across all domains. For example, r2 certification requires a minimum score of 62% per domain. This scoring methodology prevents organizations from achieving certification while leaving critical security domains inadequately addressed.
HITRUST Assessment and Certification Process — Key Terms & Phases
Organizations pursuing HITRUST certification navigate a structured assessment process with distinct phases, each requiring specific deliverables and evidence collection.
Readiness Assessment is a self-evaluation allowing organizations to gauge preparation before formal assessment. Organizations use the MyCSF platform to complete questionnaires, identify control gaps, and estimate remediation effort. Readiness assessments provide internal visibility but carry no external validation or certification value.
Validated Assessments + Certification represent formal assessments conducted under the HITRUST Assurance Program, resulting in official certification. These assessments require qualified external assessors and follow standardized methodologies.
Types of validated assessment include:
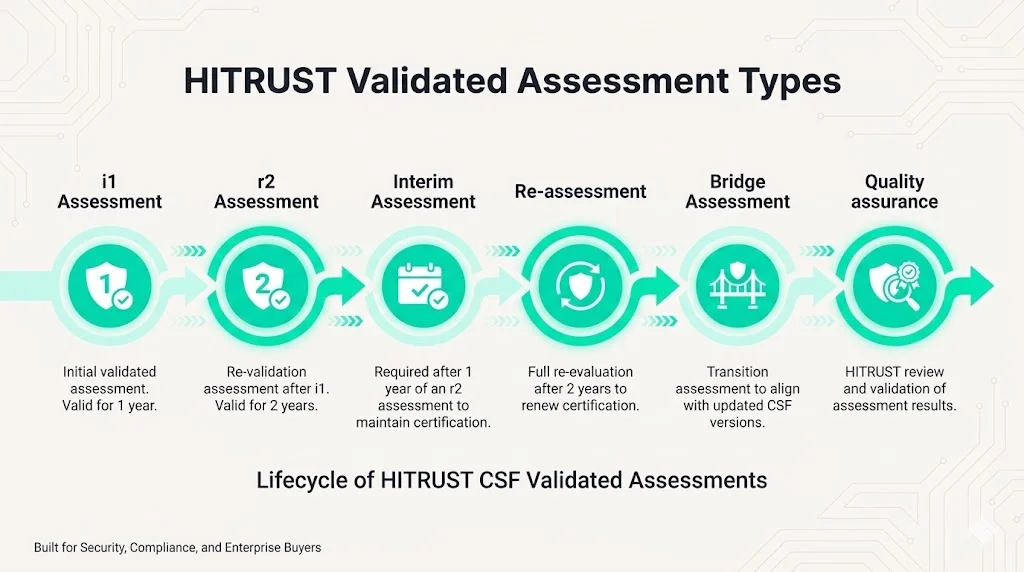
i1 (1-year assessment) targets medium-to-large organizations requiring moderate assurance. The i1 assessment evaluates a subset of controls and provides 12-month certification validity. Organizations use i1 when full r2 rigor isn't required by customers or regulatory obligations.
r2 (Risk-based 2-year assessment) is the most comprehensive and widely recognized HITRUST assessment. Validated assessments must be completed within 90 days of fieldwork initiation. Remediated controls must operate for a minimum period—60 days for policies and procedures, and 90 days for implemented controls—before they can be tested. The r2 assessment provides 24-month certification validity and represents enterprise-grade security assurance.
Interim Assessment occurs at the 12-month mark of r2 certification, confirming continued control effectiveness and compliance. Organizations must demonstrate controls remain operational and effective midway through the certification period.
Re-assessment happens every 24 months or after significant environmental changes (infrastructure migrations, major acquisitions, substantial changes to data flows). Organizations cannot simply renew certification—they must undergo full reassessment demonstrating sustained control implementation.
Bridge Assessment extends r2 certification for 90 days when organizations miss the recertification deadline due to unavoidable circumstances. Bridge assessments provide limited grace periods but require justification and HITRUST approval.
Quality Assurance Review represents the final validation step. HITRUST reviews validated assessments for accuracy, completeness, and adherence to assessment standards before granting certification. Quality assurance catches assessor errors, incomplete evidence, and inconsistent scoring before certification letters are issued.
Key Terms Defined
Cybersecurity: The overall domain HITRUST CSF addresses through 19 domains, 156 controls, and risk management processes designed to protect information systems against threats, vulnerabilities, and unauthorized access.
Compliance: The state organizations achieve by implementing HITRUST controls that satisfy multiple regulatory and industry requirements simultaneously—HIPAA, ISO 27001, NIST, PCI-DSS, GDPR, and others—via a unified framework.
Data protection: The central objective of HITRUST controls—governing how sensitive information (PHI, PII, financial data, intellectual property) is collected, stored, transmitted, processed, and disposed of throughout its lifecycle.
Risk management: Core HITRUST concept requiring organizations to systematically identify threats and vulnerabilities, assess likelihood and impact, implement controls proportionate to risk, and continuously monitor risk posture across all domains.
Information security: The comprehensive field encompassing confidentiality, integrity, and availability (CIA triad) addressed through HITRUST's control categories, objectives, domains, and maturity requirements.
Regulatory standards: The multiple regulations, frameworks, and mandates (HIPAA, ISO 27001, NIST 800-53, PCI-DSS, GDPR, HITECH, SOX) that HITRUST maps into a single control structure, simplifying multi-jurisdictional and cross-industry compliance.
Assessment tools: The mechanisms organizations use to evaluate HITRUST compliance—readiness assessments, validated assessments (i1, r2), maturity scoring, MyCSF platform, and quality assurance reviews that determine certification eligibility.
Certification process: The complete sequence—scope definition, readiness assessment, gap remediation, control implementation, evidence collection, validated assessment, quality assurance review—culminating in formal HITRUST certification valid for 12 or 24 months.
Security framework: HITRUST CSF itself—a structured, hierarchical approach offering organized control categories, objectives, domains, implementation levels, and maturity models to comprehensively manage information security and regulatory compliance.
Controlled environment: The operational outcome organizations achieve by implementing HITRUST controls—an environment where sensitive data receives documented protection, risks are systematically managed, security events are detected and responded to, and compliance is continuously maintained rather than episodically achieved.
Common Misunderstandings & Clarifications
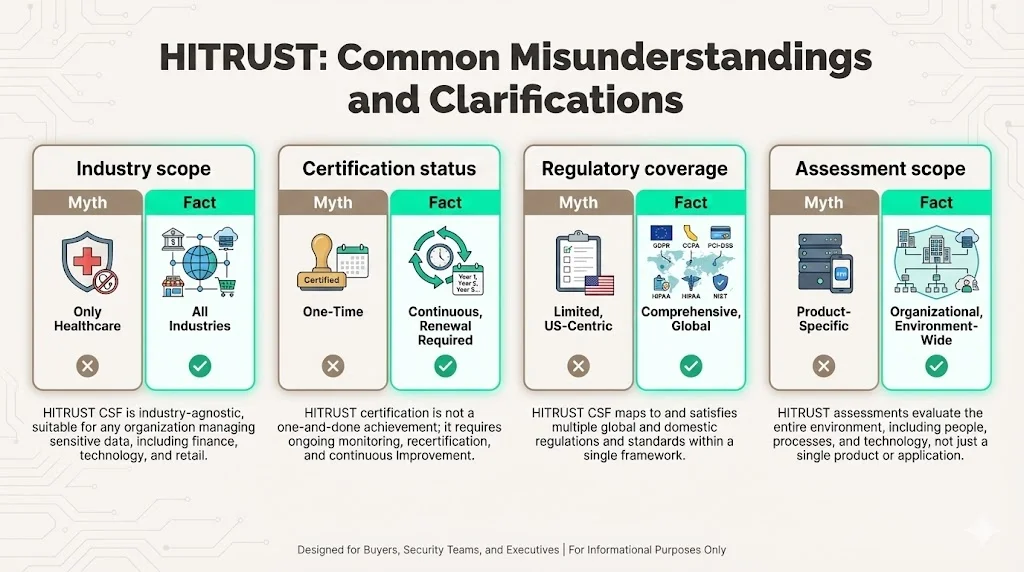
HITRUST is not healthcare-exclusive. Although "Health Information" appears in the name, the framework applies across industries. Financial services firms use HITRUST to demonstrate PCI-DSS and data protection compliance. Technology companies leverage HITRUST for enterprise sales requiring comprehensive security attestation. Any organization handling sensitive data—healthcare, financial, personal, proprietary—benefits from HITRUST's unified compliance approach.
Readiness assessments don't equal certification. Self-assessments conducted through MyCSF provide internal visibility and preparation guidance but carry no external validation. Certification requires validated assessment by HITRUST-authorized external assessors, quality assurance review, and formal approval. Organizations cannot claim HITRUST certification based on self-assessment completion.
HITRUST doesn't replace other regulations. HIPAA, GDPR, PCI-DSS, and ISO 27001 remain legally binding requirements. HITRUST harmonizes these standards into unified controls, allowing organizations to demonstrate compliance with multiple regulations through one assessment. Achieving HITRUST r2 certification shows compliance with mapped regulatory requirements—it doesn't eliminate underlying legal obligations.
Scope limitations matter significantly. Only information assets, systems, and data flows explicitly included in HITRUST assessment scope receive certification coverage. Organizations frequently certify specific applications, environments, or data categories while excluding others. Enterprise customers evaluating vendor HITRUST certifications must verify that certified scope encompasses the systems and data relevant to their engagement. A vendor with HITRUST certification covering development infrastructure provides no assurance about production systems if those weren't scoped.
Conclusion
Organizations preparing for HITRUST certification—or evaluating vendors who claim it—require clarity around the framework's terminology, structure, and assessment processes. HITRUST is not a simple compliance credential obtained through documentation review. It represents systematic implementation of 156 controls across 19 domains, demonstrated through evidence-based assessment, scored against maturity benchmarks, and validated by external assessors before quality assurance approval.
Understanding HITRUST terminology provides an essential foundation for internal preparation and confident engagement with enterprise clients requiring compliance credentials. Organizations can speak accurately about control categories versus domains, distinguish between i1 and r2 assessments, explain implementation levels and maturity scoring, and clarify what their certification scope actually covers.
A HITRUST glossary serves as a living reference. As the framework evolves—new versions incorporate emerging threats, additional authoritative sources, updated control requirements—terminology and processes change. Organizations maintaining HITRUST certification must stay current with framework updates, assessment methodology changes, and evolving industry interpretation of requirements. Staying current with HITRUST terminology isn't academic exercise—it's an operational necessity for sustained compliance and audit readiness.
FAQs
1) What does HITRUST stand for?
HITRUST stands for Health Information Trust Alliance—the not-for-profit organization that created and maintains the HITRUST Common Security Framework (CSF). Despite the healthcare reference in its name, the Alliance develops standards applicable across industries handling sensitive information.
2) What is the glossary of risk?
In HITRUST context, a risk glossary refers to standardized definitions for risk management terminology: risk assessment, risk-based controls, inherent risk, residual risk, risk appetite, implementation levels, threat modeling, and vulnerability management. Consistent risk terminology ensures all stakeholders—security teams, auditors, executives, external assessors—interpret risk concepts identically throughout assessment and ongoing compliance processes.
3) How many domains are in HITRUST?
There are 19 domains in HITRUST CSF. These domains organize the framework's 156 controls into functional areas addressing different aspects of risk management, security operations, and regulatory compliance.
4) What's the difference between HITRUST and HIPAA?
HIPAA is a U.S. federal regulation establishing requirements for protecting Protected Health Information (PHI), applicable to covered entities and business associates in healthcare. HITRUST CSF is a comprehensive security framework and certification program that incorporates HIPAA requirements alongside 60+ other regulatory standards, frameworks, and authoritative sources. Organizations can achieve HITRUST certification demonstrating HIPAA compliance plus alignment with ISO 27001, NIST, PCI-DSS, GDPR, and other standards simultaneously. HITRUST provides the implementation structure, control specifications, maturity model, and assessment methodology; HIPAA establishes the regulatory mandate.



.svg)
.svg)
.svg)