Most organizations view compliance frameworks as static certification targets rather than operational disciplines. This approach becomes problematic when cyber attacks increase in frequency and sophistication—creating gaps that surface during security incidents or regulatory reviews. APRA Prudential Standard CPS 234 aims to ensure APRA-regulated entities take measures to be resilient against information security incidents, including cyber attacks, by maintaining information security capability commensurate with vulnerabilities and threats.
APRA continues embedding CPS 234 across regulated sectors, monitoring banks, insurers, and superannuation funds to ensure they meet standards. For enterprise sellers serving financial sector clients, understanding CPS 234 requirements is essential—not merely for contractual compliance, but because your security posture directly impacts your clients' regulatory standing. APRA currently supervises institutions holding $6.5 trillion in assets, making information security governance a material concern for boards, audit committees, and procurement teams evaluating third-party relationships.
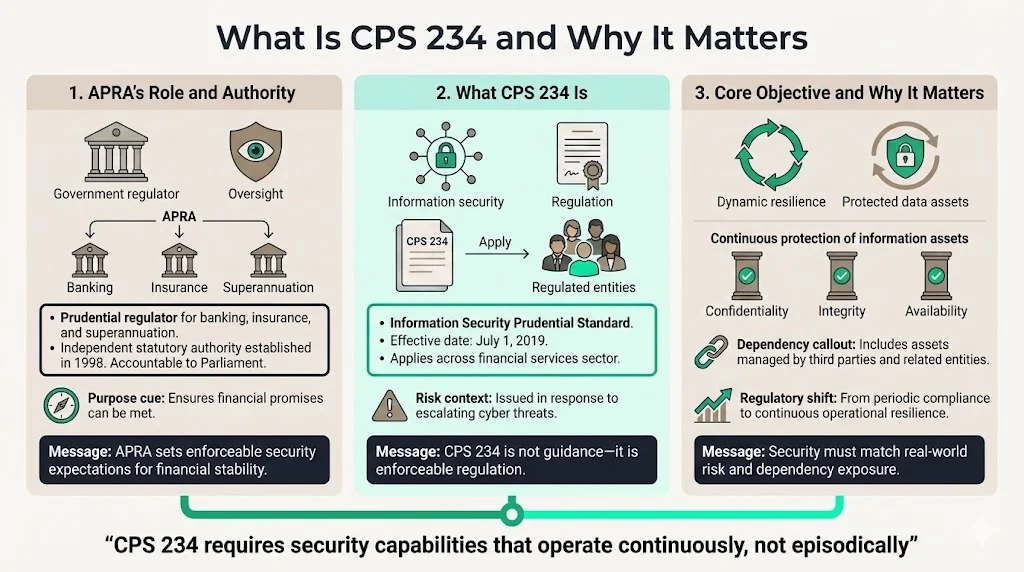
What Is CPS 234 and Why It Matters
The Australian Prudential Regulation Authority (APRA) establishes and enforces prudential security standards designed to ensure financial promises made by regulated entities are met within a stable, efficient, and competitive financial services sector. APRA is a statutory authority established in 1998 by the Australian Government, accountable to Parliament but acting independently to supervise institutions performing insurance, superannuation, and banking activities.
CPS 234 is a mandatory information security regulation issued by APRA that took effect on July 1, 2019, requiring regulated entities to strengthen information security frameworks in response to escalating cyber risk across the financial sector.
Core Objective
The goal is to minimize the likelihood and impact of information security incidents on the confidentiality, integrity, or availability of information assets, including those managed by related parties or third parties. CPS 234 shifts the regulatory focus from periodic compliance activities to continuous operational resilience—requiring entities to maintain security capabilities proportional to their threat environment and dependency chain, not simply achieve audit checkmarks.
Who Must Comply with CPS 234
CPS 234 applies to all APRA-regulated entities: authorized deposit-taking institutions (ADIs), including foreign ADIs, credit unions, banks, and non-operating holding companies authorized under the Banking Act; general insurers, including Category C insurers, non-operating holding companies authorized under the Insurance Act, and parent entities of Level 2 insurance groups. This also extends to life insurers, superannuation funds, and private health insurers operating under APRA supervision.
If your organization provides technology services, cloud infrastructure, or data processing capabilities to these regulated entities, CPS 234 creates direct third-party obligations for your security program. APRA-regulated entities must employ vendor risk management practices to reduce the likelihood and impact of incidents involving related or third parties. This means procurement teams at banks, insurers, and superannuation funds evaluate suppliers against CPS 234 control expectations during vendor assessments, contract negotiations, and ongoing relationship management.
Enterprise sellers often underestimate the rigor of APRA-driven IT audit processes. Financial institutions face intensified supervision and potential enforcement action when third-party relationships introduce security gaps. Your ability to demonstrate systematic control implementation and evidence collection directly influences contract viability and renewal.
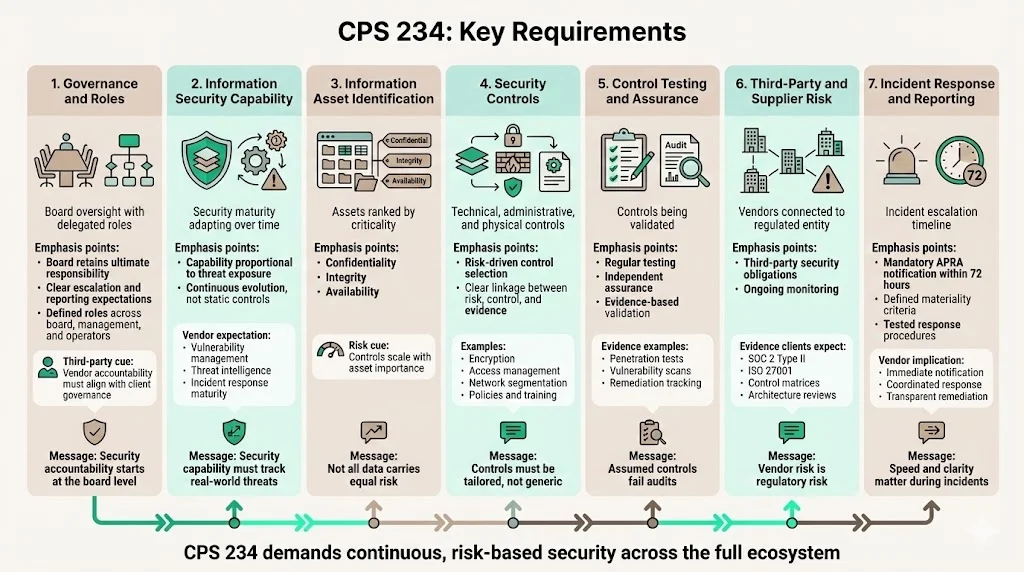
CPS 234 Key Requirements
1) Governance and Roles
The Board of an APRA-regulated entity is ultimately responsible for CPS 234 compliance and must ensure the entity maintains information security commensurate with the size and extent of threats to information assets, enabling continued sound operation. The Board can delegate security roles and responsibilities to sub-committees, management committees, or individuals, provided the Board clearly outlines how it expects to be engaged regarding information security, including escalation of risks, issues, and reporting.
Entities must have clearly defined information security-related roles and responsibilities of the Board, senior management, governing bodies, and individuals with responsibility for decision-making, approval, oversight, operations, and other information security functions. This governance structure extends to third parties—vendors must articulate accountability frameworks that align with client governance expectations.
2) Information Security Capability
Organizations must maintain information security capability proportional to threat exposure and vulnerability profile. This requirement is neither static nor formulaic; capability assessments must account for evolving threat landscapes, technology dependencies, and attack surface expansion. Ensure the organization's information security capabilities can handle emerging threats and existing vulnerabilities to maintain efficient and effective operations.
For third-party vendors, this translates to demonstrated maturity in vulnerability management, threat intelligence integration, security operations, and incident response. Clients expect evidence that your security program evolves in tandem with the threat environment—not reactive remediation following audit findings.
3) Information Asset Identification
Information assets should be classified according to their importance (based on the impact of availability loss) and confidentiality (based on the impact of confidentiality and integrity loss). Entities must inventory and classify critical and sensitive data assets, aligning control rigor with asset importance.
This requirement forces organizations to move beyond generic data classification schemes toward risk-based frameworks that distinguish between operational data, regulatory records, customer PII, and business-critical intellectual property. Control implementation must be proportional to asset criticality—auditors verify that high-risk assets receive appropriately robust protection.
4) Security Controls
Tailored information security controls must be implemented based on asset criticality and threat context. Generic control catalogs satisfy neither CPS 234 requirements nor actual security needs. The standard requires senior management to establish and maintain a comprehensive security policy framework, manage cyber risk, implement robust security controls, and define clear accountability for security roles and responsibilities.
Control documentation must demonstrate clear linkage between identified risks, control design, and implementation evidence. This includes technical controls (encryption, access management, network segmentation), administrative controls (policies, procedures, training), and physical controls where relevant.
5) Control Testing and Assurance
Entities must have incident response plans and be able to respond effectively to potential security incidents. Systematic testing and assurance over security controls is mandatory—entities must verify control effectiveness through regular assessments, not assume controls function as designed.
This requirement aligns with IT audit cycles and continuous improvement processes. All remaining CPS 234 tripartite assessments are due to be submitted to APRA, reflecting APRA's expectation that entities engage independent assessors to validate control effectiveness. For vendors, this means maintaining audit-ready evidence: penetration test results, vulnerability scan reports, control test documentation, and remediation tracking.
6) Third-Party and Supplier Risk
Third-party risk management represents a critical CPS 234 requirement with direct implications for enterprise sellers. Entities must ensure third parties that process organizational data maintain information security standards. Regulated entities evaluate vendor security through comprehensive assessments, contract security schedules, and ongoing monitoring.
Expect clients to request SOC 2 Type II reports, ISO 27001 certifications, detailed control matrices, architecture reviews, and evidence of continuous monitoring. Evaluate the information security capabilities of third parties with access to the organization's information assets. Organizations that cannot demonstrate systematic vendor risk management face regulatory scrutiny and potential enforcement.
7) Incident Response and Reporting
CPS 234 requires finance firms to report material cybersecurity incidents to APRA within 72 hours. Clear incident management procedures must be established, tested, and maintained. Material security incidents trigger mandatory notification obligations—entities must have defined criteria for materiality assessment and escalation protocols.
When an obvious data breach or other security incident is discovered, businesses must respond in a timely manner. This creates contractual implications for vendors: security incidents affecting client data require immediate notification, coordination on incident response, and transparent communication regarding impact scope and remediation timelines.
Step-by-Step Compliance Guide
1) Build Strong Governance
Establish board and senior leadership accountability for information security. This begins with formal board reporting structures, risk committee oversight, and executive ownership of security outcomes. Link information security governance into existing enterprise compliance programs, ensuring CPS 234 requirements integrate with broader risk management frameworks rather than operating as isolated initiatives.
Document governance structures clearly: define escalation paths, approval authorities, risk acceptance criteria, and reporting cadences. Auditors verify that governance exists not merely on paper but through demonstrable engagement—board minutes, risk register reviews, and security investment decisions.
2) Map Your Information Assets
Create a data classification scheme tied to data protection standards and regulatory requirements. Begin with comprehensive asset discovery: applications, databases, file repositories, cloud services, and third-party systems. Classify assets based on confidentiality requirements, integrity criticality, and availability dependencies.
This inventory becomes the foundation for risk-based control implementation. High-criticality assets warrant enhanced controls—encryption at rest and in transit, privileged access management, enhanced monitoring, and stricter change control. Document asset ownership, data flows, and dependencies to support both compliance evidence and operational security.
3) Implement and Document Controls
Reference established frameworks like NIST Cybersecurity Framework or ISO 27001 where relevant, but ensure controls address CPS 234-specific requirements around confidentiality, integrity, and availability. Implementation without documentation provides zero compliance value—auditors require evidence of control design, implementation, and operating effectiveness.
Control documentation should include policy statements, procedure guides, technical configuration standards, and responsibility assignments. Maintain evidence repositories that capture control execution: access reviews, vulnerability remediation records, security awareness training completion, and change management approvals.
4) Perform Regular Risk Assessments
Schedule periodic risk management reviews aligned with internal audit calendars and regulatory examination cycles. Risk assessments must be systematic, not ad hoc responses to incidents or audit findings. Evaluate threat environment changes, technology landscape evolution, business process modifications, and third-party relationship additions.
Document risk assessment methodology, identified risks, risk ratings, treatment decisions, and residual risk acceptance. Board and senior management must review and approve material risk decisions—demonstrating governance engagement and accountability for security posture.
5) Test and Refine Controls
Regular control testing and gap remediation distinguishes operational security from performative compliance. Testing methodologies should include automated control monitoring, manual testing procedures, independent assessments, and penetration testing where appropriate.
Capture evidence for audits and compliance reviews: test plans, test results, identified deficiencies, remediation plans, and closure verification. Continuously update information security capabilities as threats and vulnerabilities evolve. Control refinement based on test results and threat intelligence demonstrates maturity and continuous improvement.
6) Prepare for Incident Response
Develop and test incident playbooks covering detection, containment, eradication, recovery, and post-incident review. Integrate reporting triggers for APRA notifications, ensuring materiality thresholds are clearly defined and escalation procedures documented.
Test incident response capabilities through tabletop exercises and simulations. Document lessons learned and incorporate improvements into response procedures. For vendors, establish client notification protocols and communication templates—incident response effectiveness directly impacts client relationships and regulatory standing.
How CPS 234 Supports Data Protection Standards
CPS 234 aligns with global expectations around data protection, confidentiality, and handling of sensitive information. The standard reinforces strong cyber hygiene practices: data minimization, purpose limitation, encryption, access controls, and breach notification. This alignment creates strategic advantages for organizations serving multiple regulatory jurisdictions—CPS 234 compliance supports GDPR, CCPA, and other privacy framework requirements.
Robust information security reduces risk exposure across operational, reputational, and regulatory dimensions. Organizations demonstrating CPS 234 alignment strengthen client trust by showing audit readiness, systematic control implementation, and continuous security improvement. For enterprise sellers, this translates to reduced procurement friction, faster contract cycles, and stronger competitive positioning.
Common Compliance Challenges and Mitigation
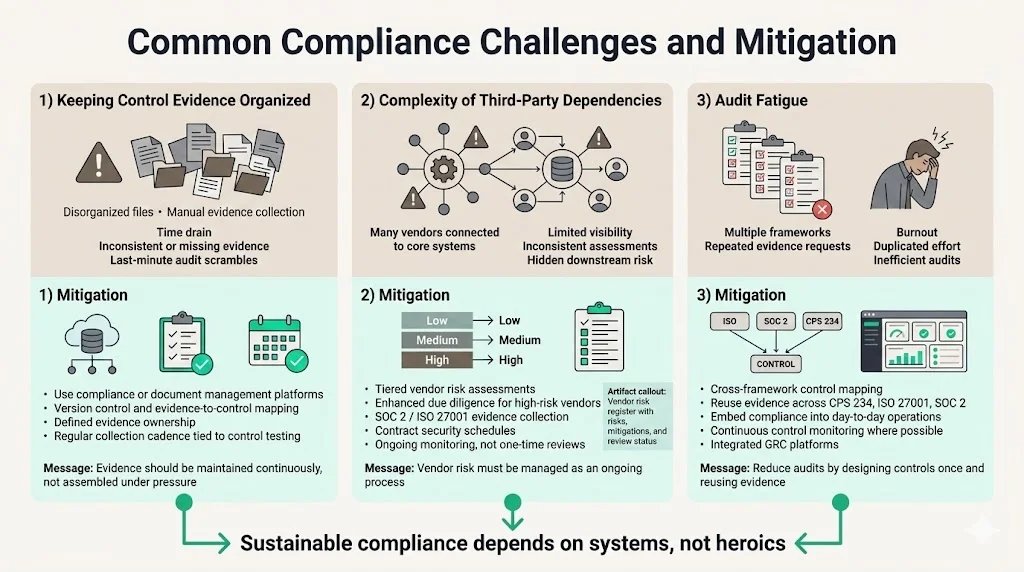
1) Keeping Control Evidence Organized
Evidence collection and organization represents a persistent challenge across compliance programs. Manual evidence gathering consumes significant resources while introducing gaps and inconsistencies. Use compliance platforms or document management systems designed for audit evidence—centralized repositories with version control, automated collection where possible, and clear evidence-to-control mapping.
Establish evidence collection cadences aligned with control testing schedules. Assign clear ownership for evidence maintenance and implement quality reviews to verify completeness and accuracy before audit cycles.
2) Complexity of Third-Party Dependencies
Third-party ecosystems create inherent complexity and control gaps. Organizations typically maintain dozens or hundreds of vendor relationships, each representing potential security exposure. Implement tiered vendor assessment approaches based on risk criticality: enhanced due diligence for high-risk vendors, streamlined assessments for low-risk relationships.
Regular vendor assessments and continuous risk monitoring must replace point-in-time evaluations. Leverage vendor questionnaires, third-party attestations (SOC 2, ISO 27001), contract security schedules, and automated vendor risk platforms where appropriate. Maintain vendor risk registers documenting assessment results, identified risks, mitigation requirements, and ongoing monitoring activities.
3) Audit Fatigue
Multiple compliance frameworks, overlapping control requirements, and continuous audit cycles create organizational fatigue. Embed compliance checks into regular business processes rather than treating audits as discrete events. Map controls across frameworks to identify overlaps—evidence supporting CPS 234 requirements often satisfies ISO 27001, SOC 2, or other framework controls.
Implement continuous control monitoring where feasible, reducing manual testing burden while providing real-time visibility into control effectiveness. Invest in integrated GRC platforms that centralize control documentation, evidence management, and cross-framework mapping—reducing duplication and streamlining audit preparation.
Conclusion
CPS 234 represents more than regulatory compliance for enterprise sellers—it defines baseline security expectations across Australia's $6.5 trillion financial services sector. Organizations treating CPS 234 as an isolated checklist miss the strategic opportunity: demonstrating systematic information security controls, robust governance, and continuous improvement positions vendors as trusted partners rather than procurement risks.
The standard's emphasis on third-party risk management means your security posture directly influences client audit outcomes and regulatory standing. Cybersecurity compliance, risk management, and information security controls function as strategic enablers—differentiating capable vendors from those manufacturing compliance artifacts without implementing actual security.
Organizations achieving CPS 234 alignment invest 75 collective hours annually maintaining compliance, compared to 550-600 hours for entities managing fragmented control environments. This efficiency stems from integrated approaches: unified evidence repositories, automated control monitoring, cross-framework control mapping, and systematic governance structures. CPS 234 compliance produces genuine security outcomes while satisfying regulatory requirements—the discipline that ultimately protects organizations when security incidents occur.
FAQ
1) Who must comply with CPS 234?
Entities regulated by APRA, including banks, insurers, superannuation funds, authorized deposit-taking institutions, and similar financial institutions. This extends to holding companies and foreign entities operating under Australian financial services regulation.
2) What systems are in scope?
All systems holding or processing critical information assets—both internal and third-party. Scope determination follows asset classification requirements: systems containing high-criticality or sensitive data require enhanced controls and assurance activities.
3) What evidence is expected?
Documentation of policies, controls, testing results, risk assessments, control effectiveness evidence, and incident response readiness. Evidence must demonstrate systematic implementation and ongoing operation—not theoretical control design. Expect requests for board meeting minutes, risk committee reports, control test results, vulnerability management records, access review evidence, and third-party assessments.
4) How often are controls reviewed?
At least annually, and whenever significant changes occur to threaten the environment, technology infrastructure, or business operations. CPS 234 stresses systematic testing and evaluation commensurate with threat exposure—high-risk controls warrant more frequent assessment than low-risk controls.
5) What happens after an incident?
The entity must respond, escalate internally, and report material incidents within 72 hours per defined procedures. Incident response includes containment, eradication, recovery, and post-incident review. Material incidents trigger APRA notification obligations, requiring clear documentation of incident scope, impact assessment, response actions, and remediation plans.



.svg)
.svg)
.svg)