Most organizations implement security controls reactively—after a breach, during an audit scramble, or when an enterprise prospect demands documentation. This approach creates a fundamental gap between operational security and documented governance, a gap that becomes immediately apparent during vendor security assessments or regulatory examinations.
An information security policy functions as the foundational governance document that defines how an organization protects data, systems, and users. It establishes clear rules, assigns accountability, and creates enforceable standards for cybersecurity guidelines, risk management, and policy compliance. For vendors pursuing enterprise customers, this document serves as the first proof point of security maturity.
This definition covers what an information security policy is, why it matters in enterprise sales contexts, how it supports compliance frameworks, and how organizations should maintain it as a living operational document rather than a static audit artifact.
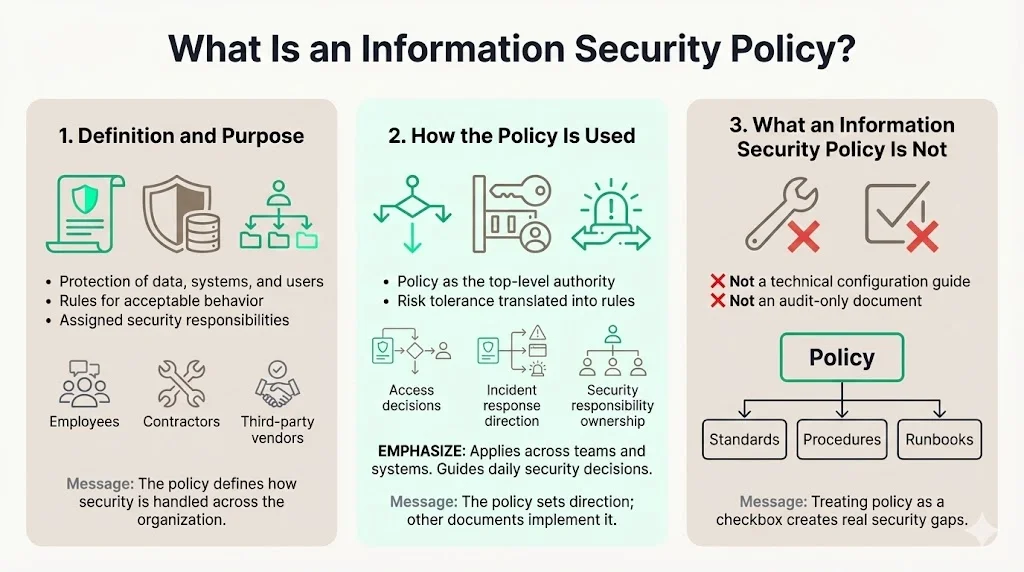
What Is an Information Security Policy?
An information security policy is a formal document that defines how an organization protects data, systems, and users from unauthorized access, disclosure, modification, or destruction. It establishes rules for acceptable behavior, assigns security responsibilities across roles, and outlines consequences for policy violations.
The policy serves as the authoritative source for security decisions, guiding everything from access control configurations to incident response procedures. It translates business risk tolerance into actionable security requirements that apply to employees, contractors, third-party vendors, and anyone with access to organizational resources.
What it is not
An information security policy is not a technical implementation manual detailing firewall configurations or encryption protocols. Those details belong in supporting standards, procedures, and runbooks that sit beneath the policy layer.
It is also not a document written solely to satisfy auditors during annual assessments. Organizations treating the policy as a compliance checkbox rather than operational guidance inevitably face gaps between documented controls and actual security posture—gaps that become apparent during incidents or regulatory scrutiny.
Core goals of an information security policy
The policy exists to protect data confidentiality, integrity, and availability by establishing clear boundaries around acceptable use and security practices. It reduces risk exposure by defining how threats are identified, assessed, and mitigated across the organization.
Equally important, it sets explicit expectations for everyone with system access. Employees understand what constitutes acceptable use. Contractors know their security obligations. Executives understand their governance responsibilities. This clarity reduces confusion during incidents and creates accountability during audits.
Why Information Security Policies Matter in Enterprise Sales
1) Enterprise buyer expectations
Enterprise security reviews now precede nearly every significant procurement decision. Security questionnaires typically contain 200-400 questions, with the first section focused on governance documentation—starting with the information security policy.
Buyers evaluate whether vendors have documented security controls before examining technical implementations. A missing or inadequate policy signals organizational immaturity, often triggering additional scrutiny, extended review cycles, or disqualification from consideration.
2) Trust and deal velocity
Organizations with comprehensive, current security policies move through vendor assessments 40-60% faster than those producing documentation reactively during reviews. The policy demonstrates that security operates as a continuous discipline rather than an audit-driven project.
This documented maturity in cybersecurity and risk management directly impacts deal velocity. Security teams can reference existing policy rather than drafting custom responses. Legal teams can negotiate contract terms with confidence in existing controls. Executive stakeholders can approve deals without extended risk committee reviews.
3) Vendor risk management pressure
Enterprises face regulatory and contractual accountability for third-party security failures. When a vendor suffers a breach exposing customer data, the enterprise bears reputational damage, notification costs, and potential regulatory penalties.
This accountability drives increasingly rigorous vendor risk management programs. Enterprise security teams now require documented policies as a prerequisite for vendor onboarding. A weak or missing policy can block procurement entirely, regardless of product capabilities or pricing.
Key Elements of an Information Security Policy
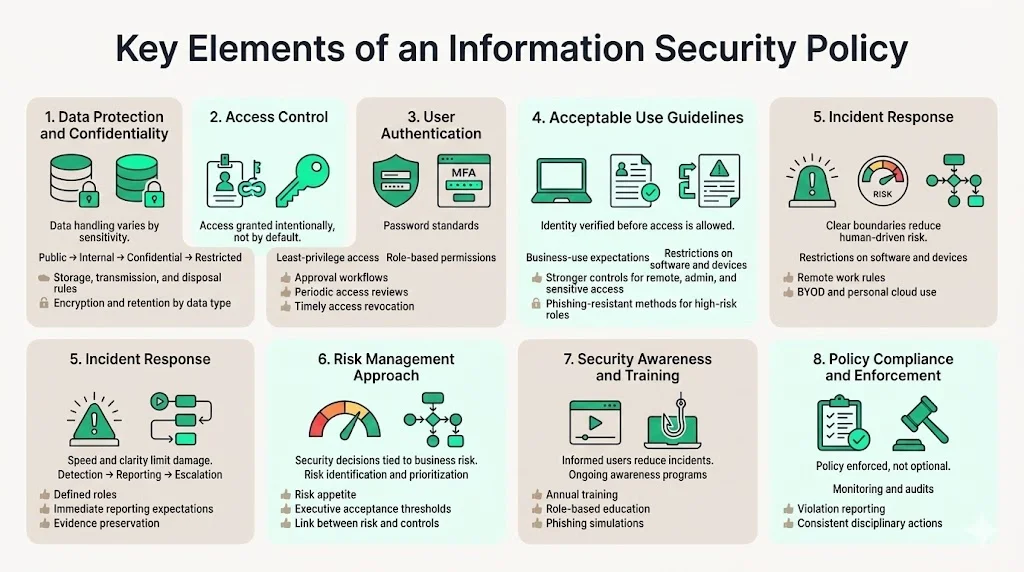
1) Data protection and data confidentiality
The policy defines how data is classified based on sensitivity and business impact. It establishes rules for storing, processing, transmitting, and disposing of each data classification level.
Organizations typically implement three to five classification tiers—such as public, internal, confidential, and restricted—with corresponding handling requirements. The policy specifies encryption requirements, retention periods, and approved storage locations for each tier.
2) Access control
Access control provisions establish least-privilege principles, ensuring users receive only the minimum permissions necessary for their roles. The policy defines role-based access models, approval workflows for elevated privileges, and review frequencies for standing access.
It also addresses access revocation during role changes, leaves of absence, and terminations. Organizations with mature access control policies reduce excessive permissions by 60-75% compared to those managing access reactively.
3) User authentication
Authentication standards specify password complexity requirements, rotation frequencies, and prohibitions on credential sharing. The policy mandates multi-factor authentication for specific access scenarios—typically remote access, administrative functions, and access to sensitive data.
Organizations increasingly require phishing-resistant authentication methods such as hardware tokens or biometric verification for high-risk access, moving beyond SMS-based codes that remain vulnerable to interception.
4) Acceptable use guidelines
Acceptable use provisions define how employees may use systems, devices, and networks for business purposes. The policy establishes restrictions on personal use, prohibitions on unauthorized software installation, and rules governing remote work environments.
It addresses bring-your-own-device scenarios, personal cloud storage services, and use of company resources for outside business activities. Clear acceptable use standards reduce security incidents caused by employee behavior by 35-50%.
5) Incident response
Incident response sections define how security events are identified, reported, and escalated. The policy assigns roles during investigations, establishes communication protocols, and sets expectations for evidence preservation.
It specifies reporting timelines—typically requiring immediate reporting of suspected breaches—and outlines consequences for delayed or concealed reporting. Organizations with documented incident response policies contain breaches 45% faster than those responding reactively.
6) Risk management approach
The policy establishes how security risks are identified, assessed, prioritized, and tracked over time. It defines risk appetite, specifying which risk levels require executive acceptance and which demand immediate remediation.
Risk management provisions ensure security investments align with business priorities rather than operating as isolated technical exercises. The policy connects risk assessments to control implementation, creating a documented rationale for security decisions.
7) Security awareness and training
Training requirements specify how often employees complete security awareness education and what topics that training must cover. The policy typically mandates annual general awareness training plus role-specific training for developers, system administrators, and anyone handling sensitive data.
It establishes expectations for phishing simulation programs, security champion networks, and continuous awareness campaigns. Organizations with documented training requirements experience 60% fewer security incidents attributable to employee behavior.
8) Policy compliance and enforcement
Compliance provisions define how adherence is monitored, measured, and enforced. The policy establishes audit rights, log retention requirements, and violation reporting mechanisms.
It outlines disciplinary consequences ranging from additional training to termination depending on violation severity and intent. Clear enforcement provisions transform the policy from aspirational guidance into enforceable operational requirements.
Common Enterprise Use Cases
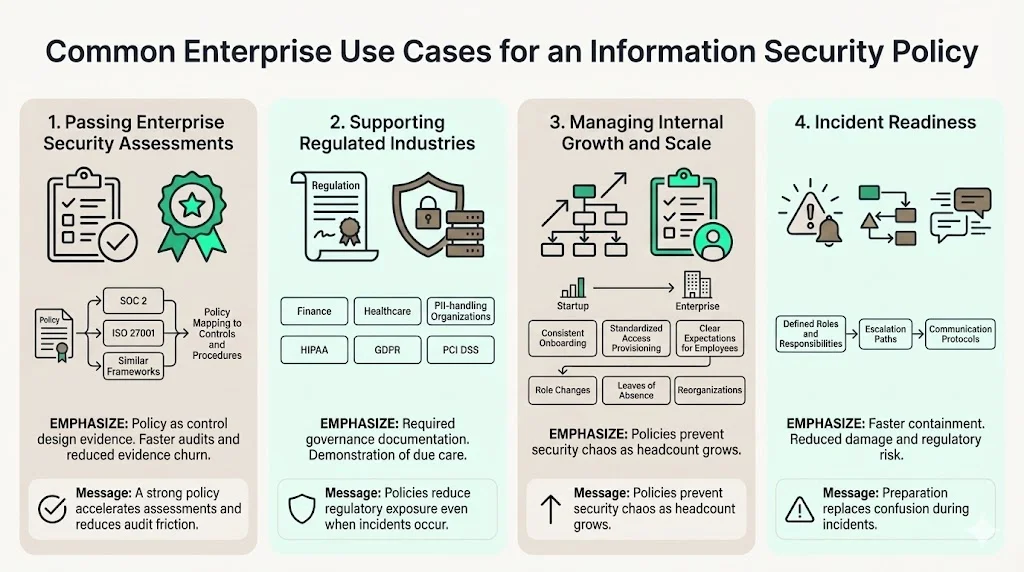
Passing enterprise security assessments
The information security policy serves as foundational evidence for SOC 2, ISO 27001, and similar security frameworks. SOC 2 requires documented policies as evidence of control design, with auditors verifying that documented policies align with implemented controls.
During assessments, auditors request the policy first, using it as a roadmap for subsequent control testing. A comprehensive policy reduces evidence collection time by 30-40% by providing clear references to supporting procedures and technical controls.
Supporting regulated industries
Organizations in finance, healthcare, and sectors handling personally identifiable information face regulatory obligations requiring documented security governance. HIPAA, GDPR, PCI DSS, and sector-specific regulations explicitly require security policies addressing data protection, access control, and incident response.
The policy demonstrates due diligence to regulators during examinations. Organizations without documented policies face significantly higher penalties during regulatory enforcement actions compared to those demonstrating governance intent even if technical controls failed.
Managing internal growth and scale
Startups operating with informal security practices face operational chaos when scaling to 50, 100, or 500 employees. The information security policy creates consistent onboarding procedures, standardized access provisioning, and clear security expectations for new hires.
It also addresses access changes during role transitions, leaves of absence, and reorganizations. Organizations implementing policies before reaching 100 employees reduce security-related operational incidents by 50-70% compared to those documenting practices reactively.
Incident readiness
Security incidents create high-pressure situations where confusion compounds damage. A documented policy reduces decision-making paralysis by establishing clear roles, escalation paths, and communication protocols before incidents occur.
Organizations with documented incident response policies contain breaches in days rather than weeks, reducing both technical damage and regulatory exposure. The policy also provides legal protection by demonstrating preparedness and due care during post-incident investigations.
Information Security Policy and Compliance Relevance
Role in security frameworks and standards
The information security policy appears as a required control in virtually every major security framework. ISO 27001 mandates an information security policy in Annex A control 5.1. SOC 2 Trust Services Criteria require documented policies demonstrating control design for confidentiality, availability, and privacy commitments.
The policy functions as a top-level governance document, with supporting standards, procedures, and technical controls implementing policy requirements. Auditors verify this hierarchy, confirming that implemented controls trace back to documented policy provisions.
Audit and legal relevance
During security audits, the policy demonstrates due care—that the organization took reasonable steps to protect data and systems. It shows intent and structure, differentiating negligent security practices from good-faith efforts undermined by sophisticated attacks.
This distinction matters significantly during breach investigations, regulatory enforcement actions, and civil litigation. Organizations with comprehensive, followed policies face 40-60% lower regulatory penalties compared to those lacking documented governance when breaches occur.
Third-party and customer assurance
Enterprise customers increasingly require vendors to share security policies during procurement evaluations. The policy serves as tangible evidence of security maturity, allowing buyers to assess governance quality without extensive on-site audits.
It signals operational discipline beyond marketing claims. Organizations willing to document and share security commitments demonstrate accountability, while those resisting transparency raise red flags during vendor risk assessments.
Ownership and Governance
Who owns the information security policy?
Security leadership—typically the CISO, Chief Security Officer, or VP of Security—owns the information security policy. In organizations without dedicated security roles, IT leadership assumes ownership, though this creates potential conflicts between operational convenience and security rigor.
Executive sponsorship matters significantly for policy effectiveness. Policies championed only by mid-level security staff lack enforcement authority and face resistance during implementation. Board-level or C-suite endorsement signals that security operates as a business priority rather than a technical constraint.
Cross-functional input
Effective policies require input from legal, human resources, IT operations, and compliance teams. Legal teams ensure policies align with regulatory obligations and contractual commitments. HR teams verify that employment policies and security requirements integrate appropriately.
IT operations teams confirm that policy requirements remain technically feasible and operationally sustainable. Compliance teams verify that policies satisfy framework requirements across all applicable standards. This cross-functional collaboration keeps the policy realistic and enforceable rather than aspirational.
Documentation and approval flow
Mature organizations maintain version control for policy documents, tracking changes over time and retaining superseded versions for audit purposes. The policy follows a formal approval flow—typically security leadership drafts, executive committee reviews, and the CEO or Board approves.
This documented approval demonstrates governance rigor during audits. Auditors verify not just that a policy exists, but that appropriate authority formally adopted it and that employees acknowledged their obligations.
Maintaining and Updating the Policy
How often it should be reviewed
Organizations should review the information security policy at least annually, with formal sign-off documenting that leadership confirmed its continued accuracy and relevance. Many frameworks explicitly require annual policy reviews as an ongoing control activity.
Reviews should assess whether policy provisions remain aligned with current business operations, technology environments, and threat landscapes. Policies unchanged for multiple years signal stale governance disconnected from operational reality.
Triggers for updates
Beyond annual reviews, specific events should trigger policy updates. New regulations affecting the organization—such as GDPR, CCPA, or sector-specific requirements—demand policy revisions ensuring compliance with new obligations.
Significant security incidents, especially those revealing control gaps, require policy reviews to address root causes. Major infrastructure changes, cloud migrations, or acquisition integrations introduce new security considerations requiring policy updates. Changes in third-party vendor relationships, particularly for critical services, warrant policy reviews addressing vendor risk management.
Communicating updates
Policy updates require active communication, not passive document replacement. Organizations should require employees to review and acknowledge significant policy changes, creating documented evidence of awareness.
Training programs should incorporate policy updates, ensuring employees understand not just that rules changed but why and how the changes affect their work. Organizations treating policy updates as communication events rather than documentation exercises achieve 70% higher adherence rates.
Consequences of Not Following the Policy
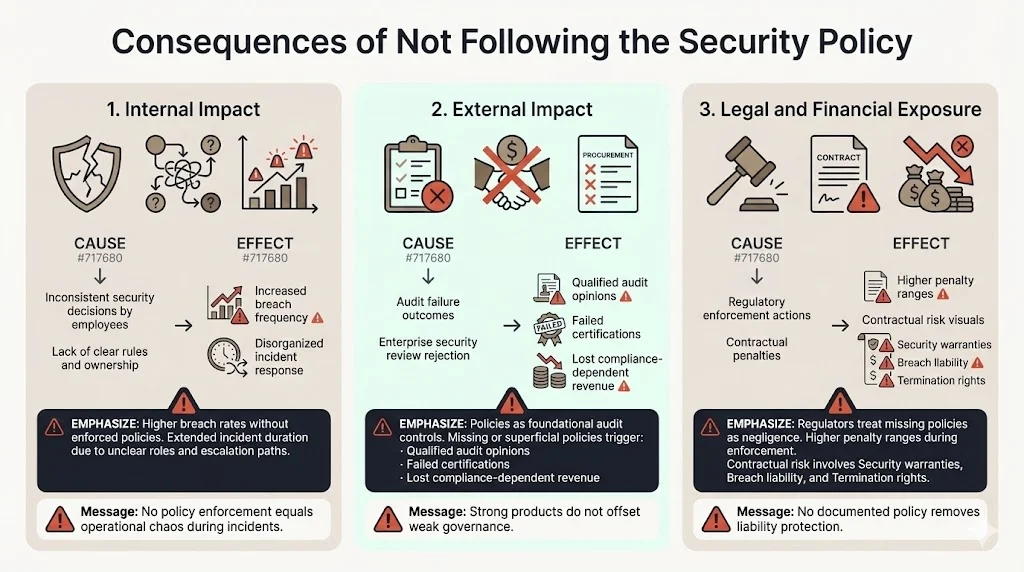
Internal impact
Organizations operating without enforced security policies experience 200-300% higher breach rates compared to those with documented, followed policies. Without clear rules, employees make inconsistent security decisions, creating gaps attackers exploit.
Incidents become significantly more chaotic without documented response procedures. Organizations lack clear roles, escalation paths, and communication protocols, extending incident duration and compounding damage.
External impact
Failed audits represent the most immediate external consequence. SOC 2, ISO 27001, and similar frameworks treat the information security policy as a foundational control. Missing or inadequate policies result in qualified audit opinions or failed certifications, eliminating compliance-dependent revenue opportunities.
Enterprise deals collapse when security reviews reveal missing or superficial policies. Vendors without documented governance face disqualification from enterprise procurement regardless of product capabilities, pricing, or existing relationships.
Legal and financial exposure
Regulatory penalties escalate dramatically when organizations lack documented security policies. Regulators interpret missing policies as negligence, imposing maximum penalty ranges during enforcement actions.
Contractual penalties arise when vendor breaches violate customer agreements. Customers increasingly include security warranties in procurement contracts, with breach penalties ranging from liability caps to contract termination rights. Organizations without policies demonstrating due care face full liability exposure rather than limited damages.
Conclusion
An information security policy functions as the foundational governance document demonstrating that security operates as a continuous operational discipline rather than a reactive project. For organizations pursuing enterprise customers, the policy serves as the first proof point of security maturity—preceding technical implementations in buyer evaluation sequences.
The policy creates enforceable standards for data protection, access control, incident response, and risk management. It reduces breach probability, accelerates vendor assessments, and provides legal protection during regulatory examinations. Organizations with comprehensive, current policies move through enterprise sales cycles 40-60% faster while experiencing significantly fewer security incidents.
Treat the information security policy as a living business document requiring continuous maintenance, cross-functional input, and executive sponsorship. The policy should reflect actual operational practices, not aspirational statements disconnected from daily security decisions. This alignment between documented governance and implemented controls transforms the policy from a compliance checkbox into a strategic asset supporting both security outcomes and business growth.
Frequently Asked Questions (FAQ)
1) What is an information security policy?
An information security policy is a formal document that defines how an organization protects its data, systems, and users from unauthorized access, disclosure, modification, or destruction. It establishes rules for acceptable behavior, assigns security responsibilities, and outlines consequences for violations.
2) Why do enterprises need a formal security policy?
Enterprises need formal security policies to manage risk systematically, meet compliance requirements across frameworks like SOC 2 and ISO 27001, and create consistent security behavior across employees, contractors, and vendors. The policy also serves as evidence of due care during regulatory examinations and breach investigations.
3) Who owns and maintains the policy?
Security leadership—typically the CISO, Chief Security Officer, or VP of Security—owns the information security policy. Effective policies require input from legal, HR, IT operations, and compliance teams to ensure requirements remain realistic, enforceable, and aligned with regulatory obligations.
4) How often should it be updated?
Organizations should review the policy at least annually, with additional updates triggered by new regulations, significant security incidents, major infrastructure changes, or business transformations such as acquisitions. Policies unchanged for multiple years signal stale governance disconnected from operational reality.
5) What happens if a policy is not followed?
Organizations operating without enforced policies experience 200-300% higher breach rates, failed compliance audits, lost enterprise sales opportunities, and significantly higher regulatory penalties during enforcement actions. Internally, incidents become more chaotic without documented response procedures, extending damage and recovery time.



.svg)
.svg)
.svg)