Most organizations deploy perimeter defenses like firewalls and assume they provide sufficient protection. This approach creates a critical blind spot—firewalls block unauthorized connections but cannot identify malicious activity already inside the network or sophisticated attacks that bypass initial defenses. An Intrusion Detection System (IDS) addresses this gap by continuously monitoring network traffic and system activity to detect signs of malicious behavior, policy violations, or unauthorized access attempts.
An IDS is a cybersecurity solution that watches network communications and host-level events to identify threat patterns and anomalous behavior indicative of compromise. Unlike firewalls that prevent intrusions through access control rules, IDS focuses on detection and alerting—providing visibility into threats that have penetrated perimeter defenses or originate from within the organization. This distinction is fundamental: IDS generates alerts and forensic evidence for security teams to investigate and respond, rather than automatically blocking traffic.
The global intrusion detection system / intrusion prevention system (IDS / IPS) market was valued at USD 5.7 billion in 2024 and is estimated to register a CAGR of 7.3% between 2025 and 2034. In 2023, 51% of the cybercrimes targeting enterprises in the US were network intrusions, and Business Email compromise followed with 26%. These metrics underscore why IDS has become essential infrastructure for organizations maintaining audit readiness across frameworks like SOC 2, ISO 27001, PCI-DSS, and HIPAA.
How Intrusion Detection Systems Work
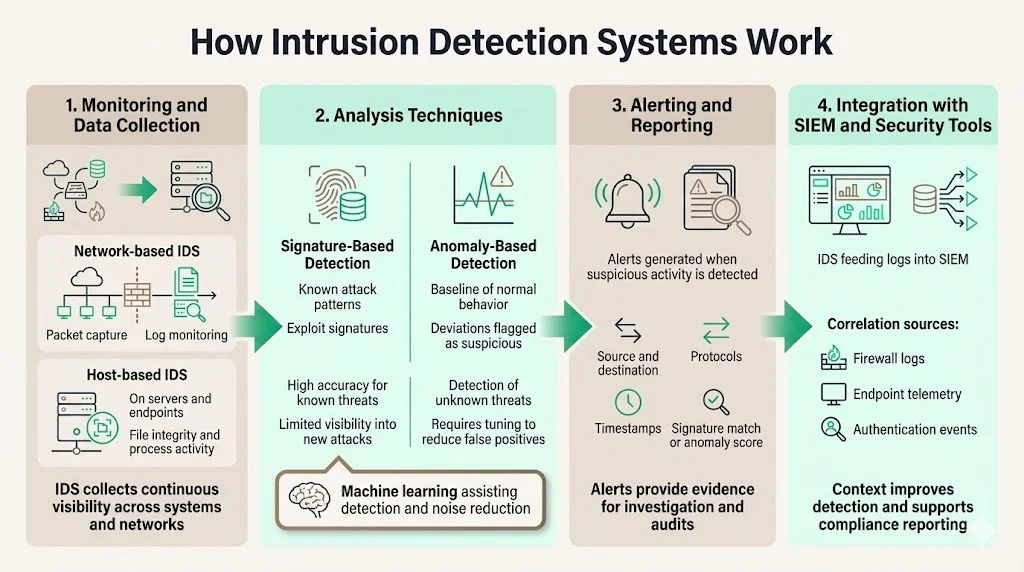
Monitoring and Data Collection
IDS captures network packets at strategic points throughout your infrastructure—typically at subnet boundaries, near firewalls, or on critical servers. Host-based IDS monitors system logs, file integrity, and process activity on individual endpoints. This continuous data collection creates a comprehensive record of all network communications and system events, providing the raw material for threat analysis.
Analysis Techniques
The most well-known variants are signature-based detection (recognizing bad patterns, such as exploitation attempts) and anomaly-based detection (detecting deviations from a model of "good" traffic, which often relies on machine learning).
Signature-based detection compares observed traffic against databases of known threat signatures—patterns that match documented exploits, malware communications, or attack methodologies. This approach delivers high accuracy for known threats but cannot detect zero-day attacks or novel intrusion techniques.
Anomaly-based detection establishes baselines of normal network behavior and system activity, then flags deviations that may indicate compromise. This method identifies previously unknown threats and insider attacks but requires careful tuning to minimize false positives. Artificial intelligence and machine learning are now being incorporated in IDS and IPS systems by organizations to assist with managing security events, while potentially helping to decrease false positives and enhance response to issues in real time.
Alerting and Reporting
When IDS identifies suspicious activity, it generates alerts that security teams investigate to determine whether the event represents an actual threat or benign anomaly. These alerts include context about the suspected intrusion—source and destination addresses, protocols involved, matched signatures or anomaly scores, and timestamps. This evidence becomes critical during incident response investigations and compliance audits, demonstrating that your organization maintains continuous monitoring capabilities.
Integration with SIEM and Security Tools
Modern IDS deployments feed logs and alerts into Security Information and Event Management (SIEM) platforms, where correlation engines combine IDS data with firewall logs, endpoint telemetry, and authentication events. This integration provides richer context for threat detection and creates the comprehensive audit trails compliance frameworks require.
Types of IDS
Based on Deployment Location
Network-based IDS (NIDS) monitors traffic flowing across network segments. Deployed at strategic chokepoints—subnet boundaries, DMZ interfaces, or upstream of critical servers—NIDS analyzes packets in real time to identify attack patterns. Network-based IDS accounts for more than 20% of the share in the global intrusion detection/prevention system market. Organizations typically deploy NIDS where they need visibility into aggregate traffic flows without installing agents on individual systems.
Host-based IDS (HIDS) runs as software on individual servers, workstations, or endpoints. HIDS monitors system calls, log files, file integrity, and application behavior to detect compromise at the host level. This approach provides deeper visibility into system-level activity but requires agent installation and management on each protected host.
Based on Detection Method
Signature-based IDS relies on predefined patterns of known attacks. These systems compare network traffic or system events against threat signature databases that vendors update as new exploits emerge. Signature-based detection delivers minimal false positives for documented threats but cannot identify novel attack vectors.
Anomaly-based IDS uses behavioral analysis and statistical modeling to establish normal baselines, then alerts on deviations. This method detects zero-day exploits and insider threats that signature-based systems miss, though it requires ongoing tuning to reduce false positive rates as network behavior evolves.
IDS vs. IPS (Intrusion Prevention System)
Some IDS products have the ability to respond to detected intrusions. Systems with response capabilities are typically referred to as an intrusion prevention system (IPS).
The fundamental distinction: IDS operates in detection mode, generating alerts for security teams to investigate and respond. IPS functions inline with network traffic, actively blocking detected threats in real time based on configured policies. IDS provides visibility and forensic evidence; IPS provides automated prevention.
Organizations frequently deploy both technologies in complementary roles. IDS monitors network segments where blocking risks interrupting legitimate business operations—you gain threat visibility without risking false-positive disruptions. IPS protects critical perimeter entry points and high-risk segments where automated blocking provides acceptable risk-reward tradeoffs. This layered approach balances comprehensive detection with selective prevention, ensuring security teams maintain visibility while IPS handles unambiguous threats.
The choice between detection and prevention also impacts compliance evidence. IDS generates detailed logs of all detected events—including those ultimately determined benign—creating comprehensive audit trails that document your monitoring posture. IPS logs focus on prevented threats, which may satisfy certain control requirements but provide less visibility into the broader threat landscape your organization faces.
Why IDS Matters for Enterprise Security
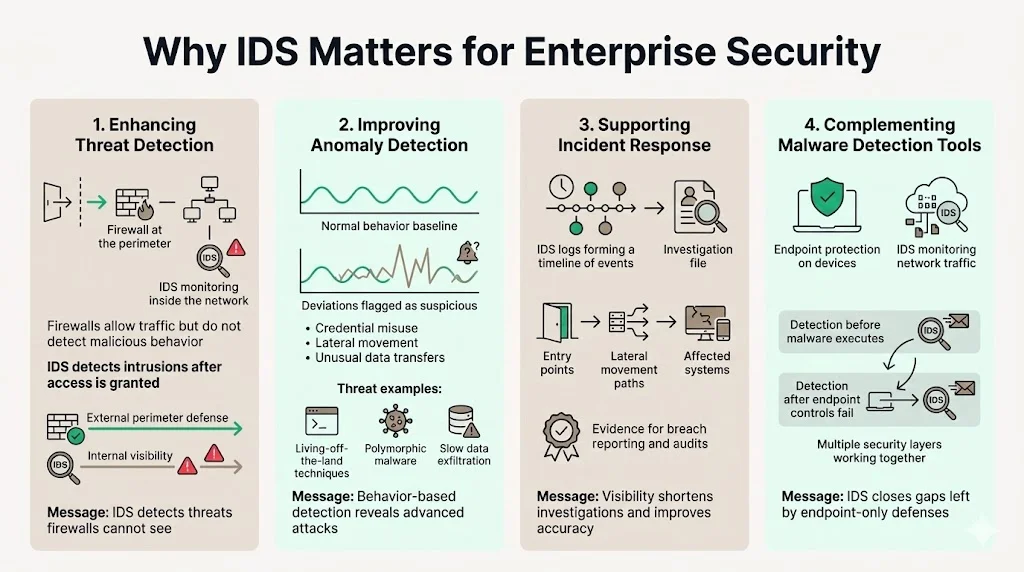
Enhancing Threat Detection
Firewalls enforce access policies at network boundaries but cannot inspect encrypted traffic contents or identify malicious behavior within permitted connections. Firewalls limit access between networks to prevent intrusion and do not signal an attack from inside the network. An IDS describes a suspected intrusion once it has taken place and signals an alarm. An IDS also watches for attacks that originate from within a system. This internal visibility becomes critical as attackers increasingly compromise credentials or exploit trusted relationships rather than breaching perimeter defenses directly.
Improving Anomaly Detection
Advanced threats employ tactics that evade signature-based detection—polymorphic malware, living-off-the-land techniques using legitimate administrative tools, and slow-burn exfiltration that mimics normal data transfers. Anomaly-based IDS flags unusual patterns that may indicate these sophisticated attacks: authentication attempts from unexpected geographic locations, lateral movement between systems that don't typically communicate, or data transfers during unusual hours. These behavioral signals enable security teams to identify threats before significant damage occurs.
Supporting Incident Response
When security incidents occur, IDS logs provide forensic evidence that incident response teams use to determine attack scope, entry vectors, and lateral movement paths. This documented timeline proves essential during breach investigations and satisfies regulatory notification requirements that demand accurate accounting of compromised systems and data. Organizations lacking comprehensive IDS coverage face significantly longer investigation timelines and incomplete incident reconstructions.
Complementing Malware Detection Tools
Endpoint antivirus and malware detection tools focus on identifying malicious code on individual systems. IDS monitors network-level indicators—command-and-control communications, exploitation attempts, and data exfiltration—that may occur before malware fully executes or after it disables endpoint protections. This complementary visibility ensures threats don't evade detection by compromising a single security layer.
IDS and Compliance
Audit Trails and Log Retention
Compliance frameworks mandate documented evidence that organizations actively monitor their environments for security threats. IDS logs satisfy these requirements by creating timestamped records of all detected events, investigation outcomes, and response actions. These audit trails demonstrate continuous monitoring posture during SOC 2 Type II observation periods, ISO 27001 surveillance audits, and regulatory examinations.
Meeting Regulatory Requirements
Financial services organizations commanded 29.1% spending in 2024, spurred by PCI DSS 4.0 and anti-fraud mandates. PCI-DSS explicitly requires intrusion detection systems that monitor traffic at the perimeter of cardholder data environments and alert personnel to suspected compromises. ISO/IEC 27001:2022 control 8.16 addresses monitoring requirements for detecting anomalous behavior and potential security incidents. HIPAA Security Rule technical safeguards include audit controls that document system activity—requirements that IDS logs directly satisfy.
GDPR Article 32 requires implementing appropriate technical measures to ensure ongoing confidentiality, integrity, and availability of processing systems—language that encompasses continuous monitoring for unauthorized access. Organizations demonstrating IDS deployment, documented alert procedures, and evidence of incident investigations strengthen their security posture documentation during regulatory audits and breach investigations.
The evidence IDS generates becomes particularly valuable during compliance attestations. Auditors examining SOC 2 Common Criteria CC7.2 (system monitoring) or ISO 27001 Annex A controls request documentation that monitoring systems exist, function continuously, and produce investigated alerts. IDS logs, alert tickets, and remediation records provide this evidence chain, demonstrating that monitoring controls operate effectively throughout observation periods rather than being performative implementations activated only during audit windows.
Best Practices for Deploying IDS
Where to Deploy
Strategic IDS placement maximizes threat visibility while managing implementation costs. Deploy NIDS at network perimeter boundaries to monitor all traffic entering and leaving your environment—this positioning detects external attack attempts and data exfiltration. Position additional NIDS sensors on internal subnet boundaries separating network segments with different trust levels or data sensitivity classifications. Deploy HIDS on critical servers hosting sensitive data, authentication systems, and applications subject to compliance requirements.
Cloud environments require specialized deployment considerations. Network-based monitoring in the public cloud relies on virtual appliances, cloud-native IDS services, or VPC flow logs analyzed by threat detection platforms. Host-based agents provide consistent visibility across hybrid deployments spanning on-premises data centers and multiple cloud providers.
Tuning and Maintenance
IDS implementations require ongoing tuning to reduce false positive rates that overwhelm security teams and cause alert fatigue. Establish behavioral baselines during an initial observation period when you know network activity represents normal operations. Regularly update signature databases as vendors release new threat intelligence. Customize detection rules to reflect your environment's specific applications, protocols, and legitimate administrative activities that might otherwise trigger alerts.
Organizations should allocate 75-150 hours annually for IDS tuning, signature updates, and alert procedure refinement—significantly less than the 550-600 hours required for comprehensive compliance program management, but essential for maintaining detection effectiveness.
Integration with Broader Security Stack
IDS delivers maximum value when integrated with your complete security infrastructure. Configure IDS to forward logs to your SIEM platform for correlation with firewall events, authentication logs, and endpoint telemetry. Establish automated workflows that create incident tickets when IDS generates high-priority alerts, ensuring security teams investigate promptly. Integrate IDS threat intelligence with firewall and IPS rule sets, enabling automated blocking of confirmed threats while maintaining IDS visibility into potential false positives.
Managed vs. In-House Monitoring
IDS generates continuous alert streams that require expert analysis to distinguish genuine threats from benign anomalies. Organizations face a fundamental choice: build internal security operations center (SOC) capabilities to monitor and investigate IDS alerts, or engage managed security service providers who perform 24/7 monitoring as an operational service.
In-house SOC operations demand significant investment—security analysts with threat detection expertise, documented investigation procedures, and sufficient staffing for round-the-clock coverage. Managed services provide immediate access to practiced expertise and established investigation workflows, converting capital expenditure into operational expense while ensuring IDS investments produce actionable security outcomes rather than ignored alert queues.
Common Challenges and Limitations
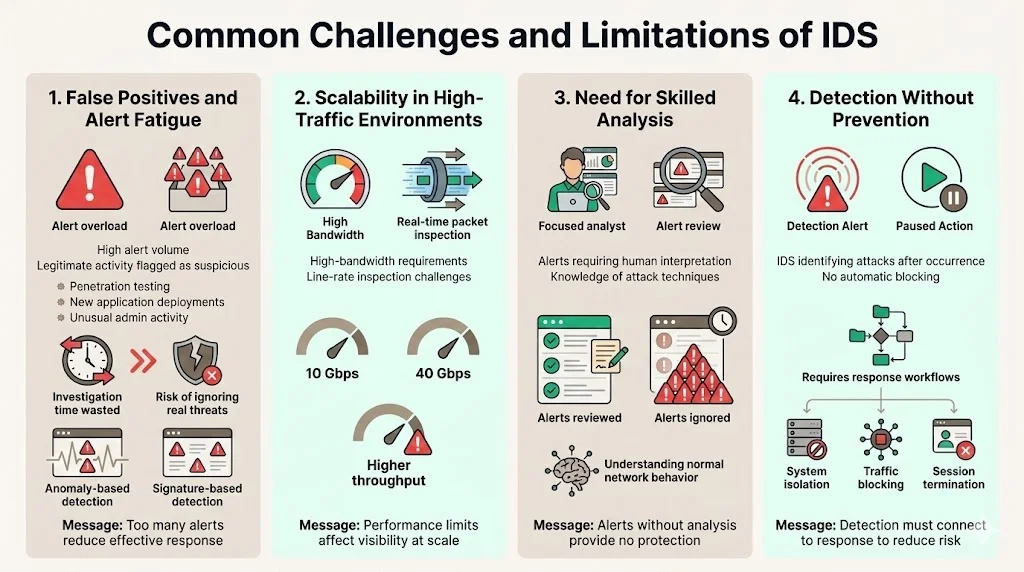
False positive rates represent the primary challenge organizations face deploying IDS. Anomaly-based detection generates alerts for legitimate but unusual activity—authorized penetration tests, new application deployments, or administrative actions outside normal patterns. Each false positive consumes investigation time, and excessive false positives cause alert fatigue that degrades response to genuine threats. Signature-based systems minimize false positives but miss novel attacks entirely.
Scalability in high-traffic environments presents technical challenges. IDS analyzing packets in real time must process traffic volumes without introducing latency or dropping packets during inspection. Organizations operating high-throughput networks—e-commerce platforms during seasonal peaks, financial services processing trading volumes, or content delivery networks—require IDS appliances or architectures capable of line-rate inspection at 10Gbps, 40Gbps, or higher data rates.
Expert analysis requirements limit IDS effectiveness for organizations lacking security expertise. IDS generates alerts, but determining whether alerts represent genuine threats requires understanding attack methodologies, normal network behavior, and contextual factors that distinguish malicious activity from legitimate operations. Organizations deploying IDS without corresponding analytical capabilities accumulate unexamined alerts that provide no security value.
Detection without prevention means IDS alone does not stop attacks—it identifies them after they occur. Organizations must establish incident response procedures that translate IDS alerts into containment actions: isolating compromised systems, blocking malicious traffic sources, or terminating unauthorized access sessions. Without these response workflows, IDS provides historical forensic evidence but does not reduce actual risk exposure during active intrusions.
Conclusion
Intrusion detection systems provide the continuous monitoring visibility that enterprises require to detect threats bypassing perimeter defenses, identify insider threats and policy violations, and generate compliance evidence demonstrating active security posture. IDS complements firewalls, endpoint protection, and other security controls by monitoring for malicious behavior rather than simply enforcing access policies—a distinction that becomes critical as attackers increasingly compromise credentials and exploit trusted relationships.
Organizations implementing IDS as part of comprehensive security programs gain earlier threat detection, detailed forensic evidence for incident investigations, and documented monitoring that satisfies audit requirements across SOC 2, ISO 27001, PCI-DSS, HIPAA, and GDPR frameworks. The evidence IDS generates—timestamped logs of detected events, documented investigations, and remediation actions—directly supports compliance attestations by demonstrating that monitoring controls operate continuously throughout observation periods.
Effective IDS deployment requires strategic placement across network segments and critical systems, ongoing tuning to manage false positive rates, integration with SIEM platforms and incident response workflows, and expert analysis to distinguish genuine threats from benign anomalies. Organizations choosing between in-house SOC operations and managed security services should recognize that IDS technology provides value only when combined with practiced expertise that translates alerts into effective security outcomes.
FAQs
Q1. What is an IDS and how does it work?
An Intrusion Detection System monitors network traffic and system activity to identify signs of malicious behavior or unauthorized access. IDS uses signature-based detection—matching traffic patterns against known threat databases—or anomaly-based detection that identifies deviations from normal behavior baselines. When suspicious activity is detected, IDS generates alerts that security teams investigate, providing visibility into threats that bypass perimeter defenses.
Q2. What types of IDS exist?
Network-based IDS (NIDS) monitors traffic across network segments from strategic points, analyzing packets for threat patterns. Host-based IDS (HIDS) runs on individual servers and endpoints, monitoring system logs, file integrity, and process activity. Signature-based IDS compares traffic against known threat patterns, while anomaly-based IDS flags deviations from established behavioral baselines. Organizations frequently deploy multiple types for comprehensive coverage.
Q3. How is IDS different from IPS?
IDS operates in detection mode—it monitors traffic, identifies suspicious activity, and generates alerts for security teams to investigate. IPS (Intrusion Prevention System) functions inline with network traffic and actively blocks detected threats in real time. IDS provides visibility and forensic evidence without risking false-positive disruptions, while IPS delivers automated prevention for unambiguous threats. Many organizations deploy both technologies in complementary roles.
Q4. Does IDS help with compliance audits?
IDS logs provide essential evidence for compliance frameworks including SOC 2, ISO 27001, PCI-DSS, HIPAA, and GDPR. These timestamped records document continuous monitoring posture, detected events, investigation outcomes, and response actions—directly satisfying audit requirements that organizations maintain active threat detection capabilities. PCI-DSS explicitly mandates IDS monitoring at cardholder data environment perimeters, while ISO 27001 control 8.16 addresses anomaly detection requirements.
Q5. Where should IDS be deployed?
Deploy network-based IDS at perimeter boundaries monitoring traffic entering and leaving your environment, and on internal subnet boundaries separating segments with different trust levels or data sensitivity classifications. Position host-based IDS on critical servers hosting sensitive data, authentication systems, and applications subject to compliance requirements. Cloud environments require virtual appliances, cloud-native IDS services, or host-based agents providing consistent visibility across hybrid deployments.



.svg)
.svg)
.svg)