By 2025, there will be 152,200 IoT devices connecting to the internet per minute. Enterprise environments now deploy sensors, actuators, gateways, and connected infrastructure at scale—from manufacturing floors to building management systems, healthcare devices to supply chain logistics. This rapid proliferation creates a compounding security challenge: each device represents a potential entry point for attackers, a source of unencrypted data transmission, and a maintenance burden that most organizations lack the expertise to manage.
An IoT security compliance framework provides a structured methodology for securing Internet of Things devices, ecosystems, and services throughout their lifecycle. These frameworks establish technical controls, risk assessment processes, and evidence-gathering requirements that enable device manufacturers, vendors, and enterprise operators to demonstrate security assurance systematically. For companies selling IoT solutions to enterprise clients, framework compliance has become a procurement prerequisite—not merely a competitive differentiator, but a baseline expectation for vendor evaluation. Unpatched firmware is responsible for 60% of IoT security breaches. Organizations buying connected devices require proof that vendors implement authentication, encryption, vulnerability management, and incident response capabilities before they will deploy those devices within their infrastructure.
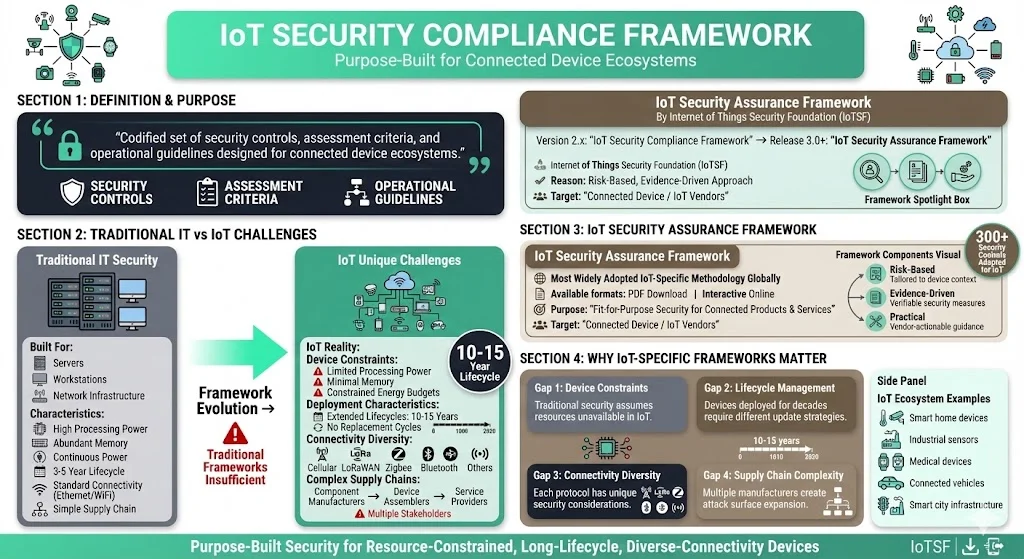
What is an IoT Security Compliance Framework?
An IoT security compliance framework is a codified set of security controls, assessment criteria, and operational guidelines designed specifically for the unique challenges of connected device ecosystems. Unlike traditional IT security frameworks developed for servers, workstations, and network infrastructure, IoT frameworks address device constraints (limited processing power, minimal memory, constrained energy budgets), extended deployment lifecycles (often 10-15 years without replacement), diverse connectivity models (cellular, LoRaWAN, Zigbee, Bluetooth), and complex supply chains involving multiple component manufacturers.
The IoT Security Assurance Framework is now available as a downloadable PDF or interactive online version. It is a powerful and practical resource that helps Connected Device / IoT vendors provide fit-for-purpose security in their products and services. The Internet of Things Security Foundation (IoTSF) developed what was originally termed the "IoT Security Compliance Framework" through version 2.x; from Release 3.0 forward, the organization renamed it the "IoT Security Assurance Framework" to better reflect its risk-based, evidence-driven approach. This framework represents the most widely adopted IoT-specific compliance methodology globally.
Key Components and How It Works
It is a guide and expert reference which leads the user through a risk management process to determine security objectives and how to achieve them. The framework employs a questioning and evidence-gathering process that spans device design, development, deployment, and operational lifecycle phases. Rather than prescribing one-size-fits-all controls, it uses a risk-based classification system where devices are categorized by their security impact—enabling proportionate control selection based on the consequences of compromise.
The framework addresses multiple audiences: device manufacturers implementing security during product development, IoT service providers operating device ecosystems, and enterprises procuring and deploying IoT solutions. Each stakeholder uses the framework to establish baseline security expectations, document control implementation, and produce audit evidence demonstrating compliance posture.
Relationship to Other Frameworks and Standards
IoTSF Release 3.0 aligned explicitly with ETSI EN 303 645 (the European standard for consumer IoT cybersecurity) and NIST SP 8259 (foundational cybersecurity activities for IoT device manufacturers). This mapping enables organizations to demonstrate compliance across multiple regulatory and procurement requirements simultaneously—a critical efficiency when enterprise customers demand adherence to jurisdiction-specific mandates.
Traditional IT security frameworks like ISO/IEC 27001 or NIST SP 800-53 were architected for managed computing environments with regular patching cycles, administrative access controls, and centralized security operations. IoT introduces fundamentally different constraints: devices deployed in physically insecure locations, firmware updates requiring over-the-air mechanisms with cryptographic verification, authentication schemes that must function on microcontrollers with 256KB of memory, and network protocols operating on constrained bandwidth. IoT-specific frameworks address these realities directly rather than forcing device security into inappropriate control structures.
Why Enterprises and IoT Vendors Need It
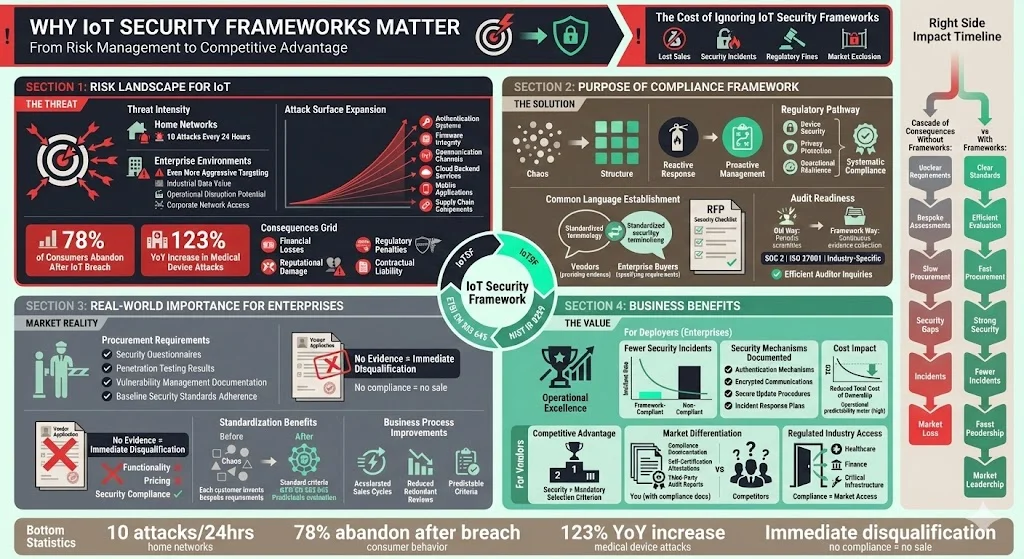
1) Risk Landscape for IoT
The global IoT ecosystem faces an average of 10 attacks every 24 hours on home network devices. Enterprise environments face even more aggressive targeting due to the value of industrial data, operational disruption potential, and access to corporate networks through poorly segmented IoT infrastructure. The attack surface expands geometrically as device counts increase: authentication systems, firmware integrity, communication channels, cloud backend services, mobile applications, and supply chain components all require securing.
78% of consumers saying they'd stop using a company's services after a major IoT-related breach. Beyond direct financial losses from incidents, organizations face reputational damage, regulatory penalties under privacy regimes like GDPR or HIPAA, and contractual liability when compromised IoT devices expose customer data or disrupt services. Healthcare organizations face particular risks as attacks on medical devices increased by 123% year over year.
2) Purpose of a Compliance Framework
IoT security compliance frameworks provide structure to manage device security proactively rather than reactively. They establish a common language between vendors and enterprise buyers—enabling procurement teams to specify security requirements in RFPs and vendors to demonstrate compliance through documented evidence. For industries facing regulatory mandates around device security, privacy protection, or operational resilience, frameworks offer a systematic pathway to satisfying those obligations.
Frameworks enable audit readiness through continuous evidence collection rather than periodic scrambles to document controls. When enterprises undergo SOC 2, ISO 27001, or industry-specific audits, IoT device security becomes a material component of their overall security posture. Organizations that can demonstrate vendor compliance with recognized IoT frameworks satisfy auditor inquiries efficiently.
3) Real-World Importance for Enterprise Clients
Enterprise procurement processes increasingly require IoT vendors to complete security questionnaires, provide penetration testing results, document vulnerability management procedures, and demonstrate adherence to baseline security standards. Vendors unable to produce this evidence face immediate disqualification from enterprise opportunities—regardless of product functionality or pricing.
Framework compliance streamlines vendor risk assessment by providing standardized evaluation criteria. Rather than each enterprise customer inventing bespoke security requirements and conducting independent assessments, recognized frameworks enable buyers to specify "IoTSF compliance" or "ETSI EN 303 645 conformance" as procurement prerequisites. This standardization accelerates sales cycles, reduces redundant security reviews, and creates predictable evaluation criteria for both parties.
4) Business Benefits
Organizations deploying IoT solutions based on framework-compliant devices experience fewer security incidents during operations. Documented authentication mechanisms, encrypted communications, secure update procedures, and incident response plans reduce the probability of breaches and limit the impact when incidents occur. This operational predictability reduces the total cost of ownership for IoT deployments.
Vendors demonstrating framework compliance gain competitive advantage in enterprise markets where security assurance has become a mandatory selection criterion. The ability to provide compliance documentation, self-certification attestations, or third-party audit reports differentiates vendors from competitors unable to substantiate their security claims. In regulated industries—healthcare, finance, critical infrastructure—this differentiation often determines market access entirely.
Core Areas and Controls within the Framework
IoT security compliance frameworks organize controls into domains addressing the complete device lifecycle and ecosystem security. The following sections detail these control areas and their technical implementation within IoT contexts.

1) Device Authentication and Identity Management
Every IoT device must possess a unique, verifiable identity that enables the system to distinguish authorized devices from unauthorized ones. Framework requirements mandate unique device identifiers assigned during manufacturing, cryptographic credentials (typically X.509 certificates or hardware-backed keys), and root of trust implementations ensuring identity integrity.
Authentication controls prevent unauthorized devices from joining networks, accessing backend services, or exfiltrating data. For enterprise IoT deployments involving thousands of sensors or actuators, centralized identity management becomes operationally critical—frameworks specify requirements for certificate lifecycle management, credential rotation, and revocation mechanisms.
Technical implementations include hardware security modules (HSMs) or trusted platform modules (TPMs) providing tamper-resistant key storage, certificate-based mutual TLS for device-to-cloud authentication, and provisioning processes establishing device identity during manufacturing rather than field deployment. These controls prevent device impersonation attacks and ensure only authenticated devices access enterprise systems.
2) Access Control
Access control limits device functions, administrative interfaces, network access, and data operations based on role-based or attribute-based policies. Frameworks require principle of least privilege—devices possess only the permissions necessary for their designated function, administrators access only the systems relevant to their responsibilities.
Control implementations include multi-factor authentication for administrative access to device management platforms, role-based access control (RBAC) systems governing which users can modify device configurations, and logging mechanisms recording all administrative actions for audit purposes. For devices deployed in physically accessible locations, frameworks mandate disabling unnecessary physical ports (USB, JTAG) and requiring authenticated access to debugging interfaces.
Network-level access control through segmentation isolates IoT devices from corporate networks, preventing lateral movement if devices become compromised. VLANs, firewall rules, and zero trust network architectures implement this segmentation while maintaining necessary connectivity to backend services.
3) Data Encryption and Network Security
Nearly all IoT traffic lacks encryption with 98% of data transmissions readable by interceptors. Framework requirements mandate encryption for data at rest (stored on devices or backend systems) and data in transit (transmitted across networks). Acceptable encryption standards specify minimum key lengths, approved algorithms (AES-256, RSA-2048 or stronger), and protocols (TLS 1.2 minimum, preferably TLS 1.3).
Network security controls include encrypted communication protocols, certificate verification preventing man-in-the-middle attacks, secure connection establishment procedures, and protection against protocol-level vulnerabilities. For constrained devices unable to implement full TLS stacks, frameworks specify lightweight alternatives like DTLS (Datagram Transport Layer Security) or hardware encryption accelerators enabling cryptographic operations within device power budgets.
Implementation requires devices reject unencrypted connections, validate server certificates during connection establishment, implement certificate pinning where appropriate, and use separate encryption keys per device rather than shared credentials across device populations.
4) Secure Firmware Updates and Vulnerability Management
Firmware represents the operational software running on IoT devices—unlike traditional IT systems with frequent patching cycles, IoT firmware updates occur infrequently and require robust security mechanisms to prevent malicious firmware installation. Framework controls mandate cryptographically signed firmware images, secure boot processes verifying firmware integrity before execution, and rollback protection preventing downgrade attacks to vulnerable firmware versions.
Vulnerability management encompasses identifying security flaws, assessing their severity using CVSS scoring, prioritizing remediation, and deploying patches through secure update mechanisms. Frameworks require documented vulnerability disclosure processes, security update commitments specifying support duration, and procedures for notifying customers of critical vulnerabilities requiring immediate patching.
Technical implementation includes over-the-air (OTA) update mechanisms with encrypted firmware delivery, atomic update procedures preventing devices from bricking during update failures, and staged rollout strategies enabling validation before fleet-wide deployment. Organizations must maintain firmware bill of materials (SBOM) documenting all software components, facilitating rapid vulnerability identification when new CVEs affect dependencies.
5) Risk Assessment and Threat Detection
Risk assessment methodologies within IoT frameworks require organizations to classify devices by criticality, identify potential threat actors and attack vectors, evaluate likelihood and impact of compromise scenarios, and select proportionate controls based on risk levels. High-risk devices (medical equipment, industrial control systems, building access controls) demand more stringent security controls than low-risk devices (environmental sensors, occupancy monitors).
Threat detection systems monitor device behavior for anomalies indicating compromise—unusual network traffic patterns, unexpected command sequences, authentication failures, or configuration changes. Framework requirements specify logging capabilities capturing security-relevant events, centralized log aggregation enabling correlation analysis, and alerting mechanisms notifying security operations teams of suspicious activity.
Implementation approaches include network traffic analysis identifying devices communicating with unauthorized destinations, behavioral baselines detecting deviations from normal device operation, and integration with security information and event management (SIEM) platforms providing enterprise-wide visibility into IoT security events.
6) Incident Response, Audit and Monitoring, Compliance Auditing
Even with comprehensive preventive controls, security incidents will occur—frameworks require documented incident response plans specific to IoT environments. These plans specify detection procedures, containment strategies (network isolation, device shutdown), investigation methodologies (forensic data collection from constrained devices), remediation steps (firmware updates, credential rotation), and post-incident review processes.
Audit and monitoring controls establish continuous verification that security controls function as intended. Framework requirements include automated monitoring of device authentication logs, periodic vulnerability scans of device firmware, configuration audits verifying devices maintain secure settings, and evidence collection documenting control effectiveness for compliance assessments.
Compliance auditing provides assurance to enterprise customers that vendors maintain security posture over time rather than achieving compliance momentarily during initial certification. Frameworks specify self-assessment procedures, third-party audit requirements for high-risk deployments, and conformity assessment processes producing attestation reports. IoTSF members can also download a free configurable tool which assists in the compliance and self-certification process.
7) Privacy Protection and Security Policies
IoT devices frequently collect personal information—location data, behavioral patterns, health metrics, biometric identifiers—triggering privacy regulations like GDPR, CCPA, or HIPAA. Framework privacy controls mandate data minimization (collecting only necessary information), purpose limitation (using data solely for disclosed purposes), consent management, and data subject rights enablement (access, deletion, portability).
Security policies document organizational commitments to IoT security throughout device lifecycles. Policies address vendor responsibilities for security updates, end-of-life procedures when devices no longer receive support, supply chain security requirements for component suppliers, and customer responsibilities for secure deployment and operation. Clear policy documentation enables enterprise buyers to evaluate vendor security maturity and establish contractual obligations.
Building and Implementing an IoT Security Compliance Framework in Practice
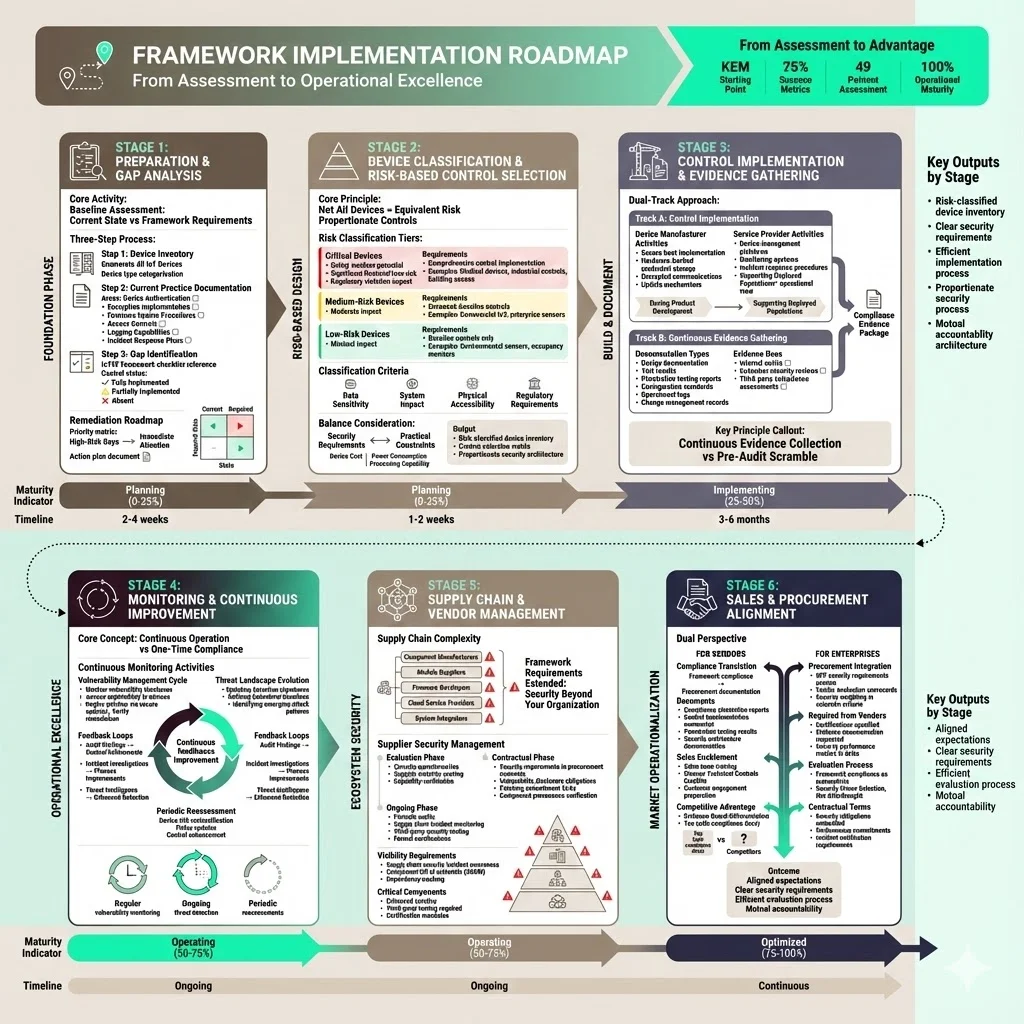
1) Preparation and Gap Analysis
Organizations begin framework implementation by inventorying existing IoT devices, documenting current security practices, and identifying gaps between present state and framework requirements. This baseline assessment examines device authentication mechanisms, encryption implementation, firmware update procedures, access controls, logging capabilities, and incident response plans.
The IoTSF framework provides detailed checklists enabling systematic gap identification across all control domains. Organizations document which controls are fully implemented, partially implemented, or absent—creating a remediation roadmap prioritizing high-risk gaps for immediate attention.
2) Device Classification and Risk-Based Control Selection
Not all IoT devices present equivalent risk—frameworks employ risk-based classification enabling proportionate control selection. Critical devices (those whose compromise would cause safety incidents, significant financial loss, or regulatory violations) require comprehensive control implementation. Lower-risk devices implement baseline controls without the operational overhead of maximum-security configurations.
Classification criteria include the sensitivity of data handled by devices, potential impact of device compromise on other systems, physical accessibility enabling tampering, and regulatory requirements specific to device functions. This risk-based approach balances security requirements with practical constraints of device cost, power consumption, and processing capabilities.
3) Control Implementation and Evidence Gathering
Control implementation maps each framework requirement into device design specifications, development practices, deployment procedures, and operational processes. Device manufacturers implement secure boot, hardware-backed credential storage, encrypted communications, and update mechanisms during product development. Service providers establish device management platforms, monitoring systems, and incident response procedures supporting deployed device populations.
Evidence gathering occurs continuously rather than as a pre-audit activity. Organizations maintain design documentation, test results, penetration testing reports, configuration standards, operational logs, and change management records demonstrating control effectiveness. This evidence satisfies internal audits, customer security reviews, and third-party compliance assessments.
4) Monitoring and Continuous Improvement
IoT security frameworks require continuous operation rather than one-time compliance achievement. New vulnerabilities emerge regularly—organizations must monitor vulnerability databases, assess applicability to deployed devices, and deploy patches through secure update mechanisms. Threat landscapes evolve—monitoring systems require updating detection signatures and behavioral baselines to identify emerging attack patterns.
Frameworks emphasize feedback loops where audit findings, incident investigations, and threat intelligence inform control refinements. Organizations periodically reassess device risk classifications as deployment contexts change, update policies reflecting new regulatory requirements, and enhance controls addressing identified weaknesses.
5) Supply Chain and Vendor Management
IoT supply chains involve component manufacturers, module suppliers, firmware developers, cloud service providers, and system integrators—each introducing potential security vulnerabilities. Framework requirements extend to supply chain partners: organizations must evaluate supplier security practices, specify security requirements in procurement contracts, verify component provenance, and maintain visibility into supply chain security incidents.
Vendor management processes include security questionnaires assessing supplier maturity, contractual terms requiring vulnerability disclosure and patching commitments, and periodic audits verifying ongoing compliance. For critical components, organizations may require third-party security testing or formal certifications demonstrating supplier adherence to security standards.
6) Sales and Procurement Alignment
IoT vendors selling to enterprise clients must translate framework compliance into procurement-friendly documentation. This includes compliance attestation reports, control implementation summaries, penetration testing results, and security architecture documentation addressing customer evaluation criteria. Sales teams require training to discuss technical security controls credibly during customer engagements.
Enterprise procurement processes incorporate framework requirements into RFPs, vendor evaluation scorecards, and contractual security obligations. Procurement teams specify required certifications, request evidence documentation, and establish security performance metrics in service level agreements. This alignment ensures security considerations drive vendor selection rather than becoming afterthoughts following procurement decisions.
Real-World Use Cases and Benefits
Vendor Differentiator and Market Trust
IoT vendors demonstrating IoTSF compliance or alignment with ETSI EN 303 645 gain immediate credibility with enterprise security teams evaluating device purchases. The ability to provide framework compliance documentation, third-party audit reports, and detailed control implementation descriptions differentiates vendors from competitors offering vague security assurances without substantiation.
In competitive procurement scenarios, framework compliance often serves as a qualifying criterion—vendors lacking compliance documentation face elimination during initial vendor screening regardless of product functionality or pricing advantages. This market dynamic makes framework adoption a strategic necessity for vendors targeting enterprise customers.
Procurement Risk Mitigation for Enterprise Customers
Enterprise organizations deploying IoT solutions face vendor risk: devices may contain vulnerabilities, lack secure update mechanisms, or provide insufficient visibility for security monitoring. Requiring vendor compliance with recognized frameworks transfers some risk accountability to vendors while providing enterprises with standardized evaluation criteria.
Procurement teams incorporate framework requirements into vendor risk assessments, using compliance status as a primary decision factor. This standardization reduces the burden of conducting independent security evaluations for each vendor while ensuring baseline security expectations are met across IoT purchases.
Regulatory Readiness and Global Applicability
Regulatory bodies worldwide are implementing mandatory IoT security requirements. The European Union's Radio Equipment Directive, California's IoT security law (SB-327), and United Kingdom's Product Security and Telecommunications Infrastructure Act establish baseline device security mandates. Organizations achieving framework compliance proactively address these regulatory requirements rather than scrambling to meet compliance deadlines.
Framework alignment with multiple standards (ETSI EN 303 645, NIST SP 8259) enables organizations to satisfy diverse regulatory regimes through unified security implementations. This efficiency proves particularly valuable for vendors operating in multiple jurisdictions with varying device security mandates.
Case Examples
Industrial IoT vendors manufacturing sensors for smart factories implement IoTSF framework controls during product development: unique device certificates enabling authentication, encrypted MQTT communications to backend systems, signed firmware with OTA update capabilities, and comprehensive logging supporting incident investigation. These vendors provide enterprise customers with compliance documentation, penetration testing results, and SBOM files—enabling rapid security assessment and procurement approval.
Smart building vendors deploying access control systems, HVAC monitoring, and occupancy sensors demonstrate encryption of all network communications, role-based administrative access to management platforms, network segmentation isolating building systems from corporate networks, and documented incident response procedures. This compliance evidence satisfies enterprise security reviews and supports SOC 2 audit requirements for facility management.
Metrics and KPIs to Track
Organizations measure framework compliance effectiveness through quantitative metrics: percentage of deployed devices meeting authentication requirements, mean time to patch vulnerabilities after disclosure, number of security incidents involving IoT devices, and compliance audit findings over time. These metrics provide objective evidence of security posture improvement.
Operational metrics include customer security review cycle time (reduced when compliance documentation is readily available), vendor risk assessment costs, and time required to respond to new vulnerability disclosures. Business metrics capture competitive advantage: win rates in procurement competitions requiring framework compliance, customer retention among security-conscious accounts, and market positioning relative to competitors lacking compliance documentation.
Linking to Regulatory Standards and Frameworks
How IoTSF Maps to Broader Standards
IoTSF Release 3.0 explicitly aligns with ETSI EN 303 645 (European consumer IoT cybersecurity baseline) and NIST SP 8259 (IoT device manufacturer core baseline). This mapping enables organizations to demonstrate multi-framework compliance simultaneously—satisfying European regulatory requirements, U.S. federal procurement standards, and industry-specific security expectations through unified control implementations.
Control mapping documents specify how individual framework requirements satisfy multiple regulatory mandates. Authentication controls meeting IoTSF requirements simultaneously address ETSI provisions for unique device identification and NIST requirements for device identity management. This convergence reduces compliance burden compared to addressing each standard independently.
Other Frameworks Enterprise Clients May Know
Enterprise security teams operate within established governance, risk, and compliance (GRC) frameworks: ISO/IEC 27001 for information security management systems, NIST SP 800-53 for federal system security controls, PCI DSS for payment card security, and SOC 2 for service organization controls. IoT security must integrate with these enterprise frameworks rather than operating as isolated device security.
Organizations map IoT framework controls to enterprise framework requirements: device authentication satisfies ISO 27001 access control objectives, encryption addresses SOC 2 confidentiality criteria, vulnerability management supports NIST continuous monitoring requirements. This integration ensures IoT security contributes to overall compliance posture rather than creating separate compliance obligations.
Why IoT-Specific Matters
Traditional IT security frameworks assume computing environments with regular patching cycles, administrative access, and centralized management—assumptions that fail for IoT deployments. Devices operate for years without replacement, reside in physically insecure locations enabling tampering, run on constrained hardware unable to support full security stacks, and connect through diverse protocols beyond standard TCP/IP networking.
IoT-specific frameworks address these unique constraints: lightweight cryptography for resource-constrained devices, secure boot mechanisms for firmware integrity, over-the-air update procedures for deployed device populations, and supply chain security for complex component ecosystems. Attempting to apply generic IT frameworks to IoT devices results in either inappropriate control selection (requiring capabilities devices lack) or inadequate security (ignoring IoT-specific vulnerabilities).
Integration Path for Enterprises
Enterprise IT and security teams integrate IoT frameworks into existing GRC programs by treating IoT as a specialized asset class within broader information security management. Security policies extend to cover IoT device procurement, deployment standards specify IoT security baselines, risk assessments incorporate IoT-specific threat scenarios, and audit programs include IoT control verification.
Procurement processes incorporate IoT framework requirements into vendor evaluation criteria. Security operations extend monitoring and incident response capabilities to IoT environments. Compliance teams map IoT framework controls to enterprise audit requirements, demonstrating how device security satisfies overall compliance obligations.
Challenges and Pitfalls to Watch
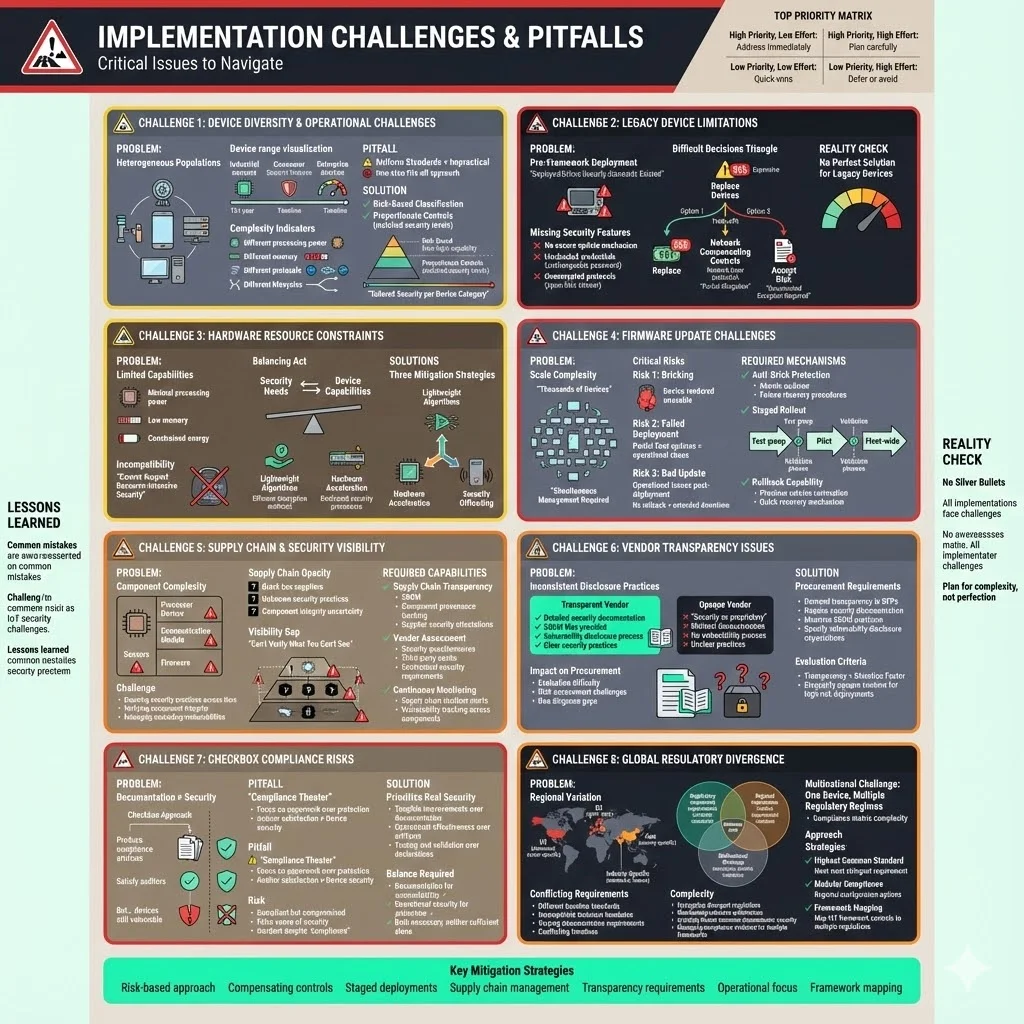
1) Device Diversity and Operational Challenges
- Heterogeneous Device Populations: Security frameworks must account for a wide range of devices, from industrial sensors with long lifespans (15+ years) to consumer-grade devices with limited security features.
- Risk-Based Classification: Applying uniform security standards is impractical; risk-based classification and selecting proportionate controls are critical to effectively managing diverse devices.
2) Legacy Device Limitations
- Lack of Security Features: Older devices, deployed before the advent of security frameworks, often lack secure update mechanisms, use hardcoded credentials, and rely on unencrypted protocols.
- Difficult Decisions: Organizations face tough choices, including:
- Replacing devices, which can be costly
- Implementing network-level compensating controls
- Accepting higher risk with documented exceptions
- Replacing devices, which can be costly
3) Constraints of Hardware Resources
- Limited Security Capabilities: Devices with minimal processing power, memory, and energy cannot support resource-intensive security operations.
- Balancing Security and Capability: Frameworks must balance security needs with device capabilities by selecting lightweight algorithms, using hardware acceleration, or offloading security tasks to gateways.
4) Firmware Update Challenges
- Logistics at Scale: Managing over-the-air updates to thousands of devices is complex and requires:
- Mechanisms to prevent devices from bricking during failures
- Staged rollouts to validate updates before full deployment
- Rollback capabilities in case of operational issues after updates
- Mechanisms to prevent devices from bricking during failures
5) Supply Chain and Security Visibility
- Component Complexity: Devices often contain components (processors, communication modules, sensors, firmware) from multiple suppliers, each potentially introducing vulnerabilities.
- Supply Chain Transparency: Organizations struggle to ensure security practices across the supply chain and verify the integrity of components.
6) Vendor Transparency Issues
- Inconsistent Security Disclosure: Some manufacturers offer detailed security documentation, including SBOM files and vulnerability disclosure processes, while others treat security as proprietary and are opaque about their practices.
- Procurement Requirements: Enterprises must demand transparency from vendors, including clear security documentation, during the procurement process.
7) Risks of Checkbox Compliance
- Documentation vs. Operational Security: Focusing solely on producing compliance artifacts can satisfy auditors but does not ensure devices are protected against compromise.
- Genuine Security Improvement: Framework adoption should prioritize tangible security improvements over meeting checkbox compliance requirements.
8) Global Regulatory Divergence
- Conflicting Requirements: Device security mandates vary across regions, such as the European Union, the U.S., Asia, and specific industries.
- Navigating Complexity: Organizations with multinational operations must navigate differing regulations while maintaining a cohesive security architecture.
Future Trends in IoT Security Compliance
Regulatory pressure on IoT device security continues intensifying. Jurisdictions worldwide are implementing mandatory baseline security requirements for consumer and enterprise devices. Future frameworks will likely become referenced directly in legislation, transforming voluntary best practices into legal obligations with penalties for non-compliance.
Vendor certification schemes will proliferate as markets demand independent validation of security claims. Rather than self-attestation, enterprises will require third-party testing laboratories to verify device compliance with framework requirements—similar to existing certification regimes for wireless standards or safety compliance.
Continuous monitoring and behavioral analytics will supplement static compliance assessments. Traditional audit approaches verify controls exist at a point in time; future frameworks will emphasize continuous assurance through runtime monitoring, anomaly detection, and automated verification that controls function as intended throughout device lifecycles.
Supply chain transparency requirements will mandate component pedigree tracking, provenance verification, and SBOM documentation. Organizations will demand visibility into every software library, hardware component, and subcontractor involved in device manufacturing—enabling rapid vulnerability identification and supply chain attack detection.
AI and machine learning integration will enhance threat detection in IoT networks. Behavioral baselines established through machine learning will identify compromised devices exhibiting anomalous communication patterns, command sequences, or operational behaviors. These detection capabilities will become framework requirements as the technology matures.
Extended device lifecycles will require sustained compliance mechanisms. As IoT devices remain deployed for 10-15 years, frameworks will specify minimum support commitments, end-of-life procedures, and mechanisms for maintaining security when vendors cease device support or exit markets entirely.
Conclusion
IoT security compliance frameworks provide the structured methodology vendors and enterprises require to manage the security risks inherent in connected device ecosystems. These frameworks address the unique challenges IoT introduces—constrained devices, extended lifecycles, complex supply chains, diverse connectivity—with technical controls specifically designed for these environments rather than attempting to force IoT into traditional IT security models.
For vendors selling IoT solutions to enterprise clients, framework adoption represents a strategic imperative. Enterprise procurement processes increasingly require demonstrated compliance as a qualification criterion; vendors unable to provide framework attestation, control documentation, and security evidence face immediate disqualification regardless of product capabilities. Organizations like the IoT Security Foundation have established recognized frameworks mapping to multiple regulatory standards—enabling vendors to satisfy diverse customer requirements through unified compliance efforts.
The implementation methodology is systematic: baseline assessment identifying current gaps, risk-based device classification enabling proportionate control selection, comprehensive control implementation across device lifecycles, continuous monitoring and evidence gathering, and supply chain security extending requirements to component suppliers. This is not checkbox compliance—frameworks demand operational security controls that genuinely protect devices from compromise while producing compliance as a documented outcome.
Organizations should audit their current IoT device portfolios against recognized frameworks like IoTSF, map existing controls to framework requirements, prioritize gap remediation based on risk, and build compliance evidence supporting customer security reviews and internal audits. Security compliance properly implemented becomes a business enabler: accelerating procurement cycles, reducing vendor risk assessment costs, differentiating vendors in competitive markets, and establishing the foundation for genuine operational security rather than performative assurance theater.
FAQs
Q1. What is the IoTSF security compliance framework?
The Internet of Things Security Foundation (IoTSF) Security Compliance Framework is a set of guidelines and best practices aimed at ensuring the secure design, development, and deployment of IoT (Internet of Things) devices and their associated ecosystems. The framework now operates as the "IoT Security Assurance Framework" from Release 3.0 forward, providing risk-based security guidance for device manufacturers, service providers, and enterprise operators.
Q2. What are the 5 frameworks of NIST?
The core functions of the NIST Cybersecurity Framework (CSF) are: Identify, Protect, Detect, Respond, and Recover. These five functions provide a high-level strategic view of cybersecurity risk management applicable across industries and organizational types, including IoT security implementations.
Q3. What are the 5 C's of IoT?
In a compliance and security context, the "5 C's" of IoT are: Connectivity (secure device communications), Continuity (operational resilience and availability), Compliance (adherence to regulatory and framework requirements), Coexistence (interoperability with existing systems), and Cybersecurity (comprehensive protection throughout device lifecycles).
Q4. What is IoT compliance?
IoT compliance means ensuring IoT devices, systems, and services meet appropriate security, privacy, interoperability, and regulatory standards and frameworks. It involves implementing defined controls, undergoing audit or verification processes, and providing documented evidence that devices or solutions satisfy specified criteria—enabling enterprise customers to assess vendor security posture systematically rather than through ad hoc evaluation.



.svg)
.svg)
.svg)