Most organizations deploy firewalls and assume perimeter security is sufficient. This creates a critical vulnerability—firewalls filter traffic based on predefined rules but lack the capacity to inspect and neutralize sophisticated attacks that exploit legitimate ports and protocols. An Intrusion Prevention System (IPS) addresses this gap by analyzing network traffic in real time, identifying malicious behavior, and automatically blocking threats before they reach critical systems.
An IPS system functions as an active enforcement layer within enterprise cybersecurity infrastructure. Unlike passive monitoring tools, IPS sits inline with network traffic, inspecting packets as they traverse the network and terminating connections that exhibit malicious characteristics. This real-time prevention capability positions IPS as a foundational component of defense-in-depth strategies, complementing firewalls, endpoint detection, and security information and event management (SIEM) platforms. For organizations pursuing regulatory compliance under frameworks like PCI-DSS, HIPAA, or ISO 27001, IPS provides documented evidence of continuous threat monitoring and automated security controls—requirements explicitly outlined in technical implementation specifications.
What Is an IPS System?
An Intrusion Prevention System (IPS) is a network security technology that monitors network traffic for malicious activity and automatically blocks or prevents detected threats. IPS operates inline with network traffic, analyzing data packets in real time and enforcing security policies by terminating connections, dropping malicious packets, or blocking source IP addresses before threats reach protected assets.
The distinction between IPS and Intrusion Detection Systems (IDS) is operational: IDS passively monitors traffic and generates alerts when suspicious activity is detected, requiring human intervention to respond. IPS extends detection capabilities with automated prevention, actively intercepting and neutralizing threats without manual intervention. This automated response reduces mean time to containment—a critical metric when malware propagation or data exfiltration can occur within minutes of initial compromise.
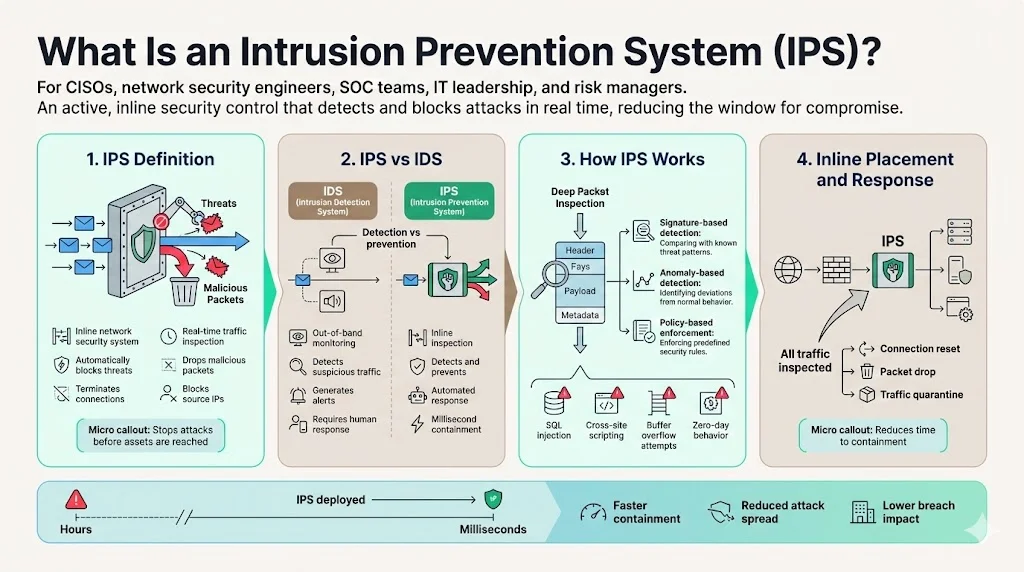
How IPS Works
IPS systems analyze network traffic through deep packet inspection, examining packet headers, payloads, and behavioral patterns against multiple detection methodologies. Signature-based detection compares traffic against databases of known attack patterns, identifying threats like SQL injection, cross-site scripting, and buffer overflow attempts through pattern matching. Anomaly-based detection establishes baseline traffic behavior and flags deviations that indicate zero-day exploits or novel attack techniques. Policy-based detection enforces organizational security policies, blocking traffic that violates defined access controls or protocol specifications regardless of malicious intent.
The IPS vs IDS comparison in practice centers on placement and authority. IDS deploys out-of-band, receiving traffic copies via network taps or span ports, while IPS deploys inline, requiring all traffic to pass through inspection before reaching destinations. IDS generates alerts for security teams to investigate and remediate manually. IPS executes predefined responses automatically—blocking malicious traffic, resetting connections, or quarantining suspicious packets—reducing response time from hours to milliseconds.
Placement in the Network
IPS typically deploys inline immediately behind perimeter firewalls, positioned to inspect all traffic entering or exiting protected network segments. This placement provides coverage after initial firewall filtering eliminates obviously unauthorized traffic, allowing IPS to focus on sophisticated threats that exploit legitimate ports and protocols. In segmented network architectures, organizations deploy additional IPS instances at internal boundaries—between data center zones, separating production from development environments, or protecting critical infrastructure segments.
Firewall integration occurs through multiple mechanisms. Some vendors provide unified threat management appliances combining firewall and IPS capabilities in single devices. Distributed architectures use policy coordination, where firewalls handle Layer 3-4 filtering while IPS performs Layer 7 application inspection, with both systems sharing threat intelligence feeds to block identified attackers across all enforcement points. This integration increases threat coverage while reducing management overhead through centralized policy administration.
Key Functional Components
1) Real-Time Monitoring
Real-time monitoring provides continuous visibility into network traffic patterns, protocol usage, and data flows across enterprise infrastructure. IPS analyzes every packet traversing monitored network segments, maintaining session state tables that track connection lifecycles from initiation through termination. This comprehensive visibility enables detection of multi-stage attacks that spread across multiple sessions or exhibit malicious behavior only when traffic is analyzed in aggregate rather than individual packets.
2) Automated Threat Response
IPS executes predefined responses automatically when threat conditions are detected, eliminating delays inherent in human-dependent incident response processes. Response actions include dropping malicious packets, sending TCP reset commands to terminate suspicious connections, blocking source IP addresses temporarily or permanently, and triggering additional security controls like firewall rule updates or SIEM alert escalation. Automated response reduces attacker dwell time—the period between initial compromise and detection—from industry averages of 200+ days to minutes or seconds for covered attack vectors.
3) Threat Detection and Prevention
Signature-based detection identifies known threats through pattern matching against continuously updated signature databases containing indicators of compromise from recent malware campaigns, exploit techniques, and command-and-control communication patterns. Anomaly-based detection builds statistical models of normal network behavior—typical bandwidth consumption, standard protocol sequences, expected application traffic patterns—and flags deviations exceeding defined thresholds. This dual-method approach provides coverage against both cataloged threats and novel attack techniques that lack established signatures.
Types of IPS Systems
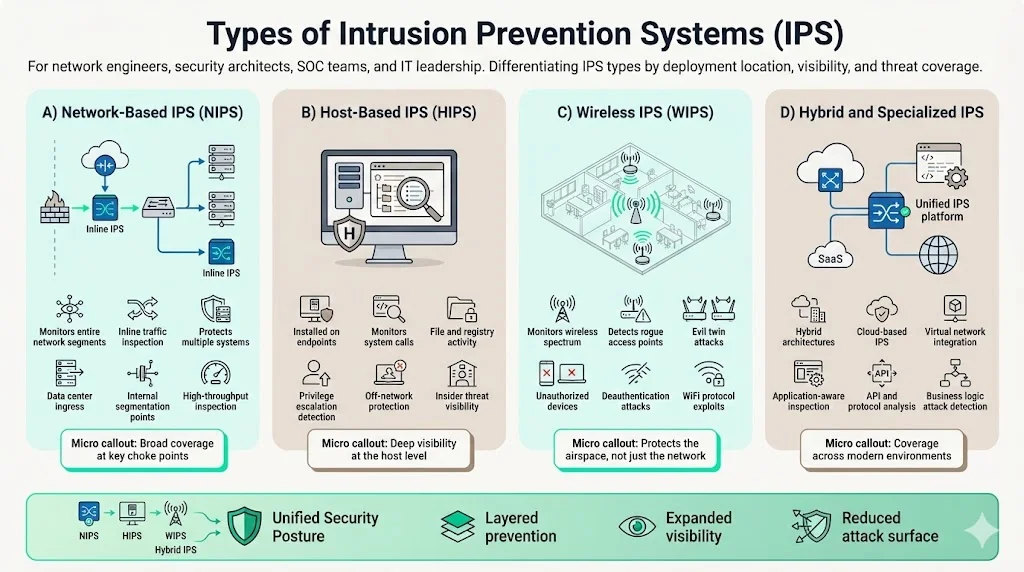
A. Network-Based IPS (NIPS)
Network-Based IPS monitors traffic across entire network segments, deploying at strategic inspection points to provide perimeter and internal threat coverage. NIPS analyzes all traffic traversing monitored links regardless of source or destination, making it ideal for protecting multiple systems simultaneously. Enterprise deployments typically position NIPS at internet gateways, data center ingress points, and inter-segment boundaries where traffic volume justifies dedicated inspection appliances.
B. Host-Based IPS (HIPS)
Host-Based IPS installs directly on endpoints—servers, workstations, or mobile devices—monitoring system calls, file system access, registry modifications, and network connections originating from or terminating at protected hosts. HIPS provides granular visibility into application behavior and system-level activities invisible to network-based monitoring, detecting malware executing in memory, unauthorized privilege escalation, or malicious processes masquerading as legitimate applications. HIPS deployment complements NIPS by protecting systems during off-network operation and detecting insider threats that bypass network security controls.
C. Wireless IPS (WIPS)
Wireless IPS specializes in monitoring radio frequency spectrum and 802.11 protocol traffic, detecting rogue access points, evil twin attacks, wireless eavesdropping, and protocol-level exploits targeting WiFi infrastructure. WIPS deploys dedicated sensors across physical facilities to provide comprehensive wireless coverage, identifying unauthorized devices attempting to connect to enterprise networks and detecting wireless-specific attack vectors like deauthentication floods or WPA2 key reinstallation attacks.
D. Hybrid and Other Variants
Organizations increasingly deploy hybrid IPS architectures combining multiple detection approaches to maximize threat coverage while optimizing resource allocation. Cloud-based IPS protects cloud-native infrastructure and software-as-a-service environments, integrating with virtual network functions and cloud security posture management platforms. Application-aware IPS performs deep inspection of specific protocols—HTTP/HTTPS, database queries, API calls—to detect application-layer attacks that exploit business logic rather than infrastructure vulnerabilities.
How IPS Fits with Other Network Security Tools
Integration with Firewalls
IPS and firewalls provide complementary security capabilities when deployed in coordinated architectures. Firewalls enforce network access policies based on source/destination addresses, ports, and protocols, blocking unauthorized connection attempts at Layer 3-4. IPS inspects allowed traffic that passes firewall rules, analyzing application-layer content and behavioral patterns to detect threats exploiting legitimate protocols. This layered approach prevents attacks that manipulate authorized services—web application exploits delivered via HTTPS, SQL injection through database ports, or malware concealed in permitted file transfers.
Firewall integration enhances threat coverage by enabling dynamic policy updates based on IPS detections. When IPS identifies a compromised internal system attempting command-and-control communication, it triggers firewall rule creation blocking that host's external access until remediation completes. This automated coordination prevents lateral movement and data exfiltration without requiring manual security team intervention for every detected incident.
Relationship With IDS
The distinction between detection and prevention defines IDS and IPS operational differences. IDS deploys passively, generating alerts when suspicious activity matches detection signatures but requiring security analysts to investigate findings and execute manual responses. IPS extends IDS capabilities with inline deployment and automated prevention, blocking detected threats immediately while simultaneously generating alerts for security team review. Organizations often deploy both technologies, using IPS at critical control points requiring automated protection while positioning IDS for comprehensive monitoring where false positive risks make automated blocking unsuitable.
Working with SIEM and Other Tools
IPS integrates with SIEM platforms through standardized logging formats and threat intelligence feeds, contributing real-time attack data to centralized security monitoring and incident response workflows. SIEM correlation engines analyze IPS alerts alongside firewall logs, endpoint detection findings, and authentication records to identify multi-vector attacks spanning multiple security domains. This integration enables security operations centers to detect sophisticated threats exhibiting indicators across multiple systems—phishing emails followed by network reconnaissance followed by data access anomalies—that individual security tools cannot recognize in isolation.
Use Cases for IPS Systems
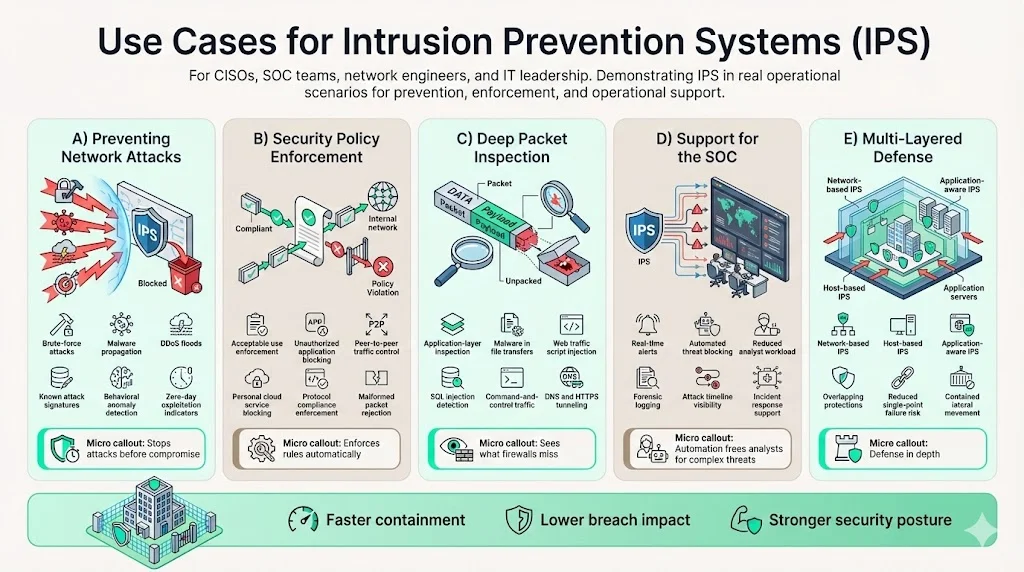
A. Preventing Network Attacks
IPS blocks diverse attack vectors including brute-force authentication attempts, malware propagation, distributed denial-of-service floods, and zero-day exploits targeting unpatched vulnerabilities. Signature-based detection stops known attack patterns immediately, while anomaly detection identifies novel techniques by recognizing behavioral deviations from established baselines. For zero-day threats lacking published signatures, behavioral analysis detects exploitation attempts through unusual protocol sequences, unexpected privilege escalation, or abnormal data exfiltration patterns characteristic of successful compromises.
B. Security Policy Enforcement
IPS enforces organizational security policies by blocking traffic violating defined acceptable use standards, protocol specifications, or data handling requirements. Policy-based controls prevent unauthorized application usage—blocking peer-to-peer file sharing, personal cloud storage, or social media access from restricted networks—and enforce protocol compliance by dropping malformed packets or non-standard protocol implementations that could exploit parsing vulnerabilities in downstream systems.
C. Deep Packet Inspection
IPS examines packet payloads beyond header information, reconstructing application-layer data streams to detect threats concealed within legitimate protocols. Deep packet inspection identifies malware embedded in file transfers, malicious scripts injected into web traffic, SQL commands within database queries, and command-and-control communications tunneled through DNS or HTTPS. This content-level analysis detects threats invisible to traditional firewall filtering, which examines only network and transport layer headers.
D. Support for SOC (Security Operations Center)
IPS feeds automated alerts and threat intelligence to security operations centers, providing real-time visibility into attack attempts and enabling coordinated incident response across enterprise infrastructure. Automated blocking capabilities reduce SOC workload by neutralizing routine threats without analyst intervention, allowing security teams to focus on sophisticated attacks requiring human judgment. IPS logs provide forensic evidence supporting incident investigation, documenting attack timelines, affected systems, and automated response actions taken.
E. Multi-Layered Defense
IPS supports defense-in-depth strategies by providing threat prevention at multiple network layers simultaneously. Combined deployment of network-based, host-based, and application-aware IPS creates overlapping security controls that prevent single-point failures from compromising entire environments. This layered architecture ensures attacks blocked at perimeter defenses cannot exploit internal systems, while endpoint protections prevent threats introduced through removable media or compromised remote access channels from propagating across networks.
IPS and Compliance Relevance
Why IPS Matters for Regulations
IPS implementation directly supports technical requirements within multiple regulatory frameworks. PCI-DSS Requirement 11.4 mandates intrusion detection and prevention systems monitoring cardholder data environments. HIPAA Security Rule §164.312(b) requires transmission security controls including integrity controls and encryption for electronic protected health information, with IPS providing documented enforcement of data flow restrictions. ISO 27001 Control A.13.1.1 addresses network controls, requiring organizations to implement appropriate measures protecting information in networks—a requirement satisfied through IPS deployment providing continuous monitoring and threat prevention.
Documentation and Audit Readiness
IPS generates comprehensive logs documenting detected threats, automated responses executed, and ongoing monitoring activities required for compliance audits. These logs provide evidence of continuous security controls operation—demonstrating to auditors that technical safeguards actively protect regulated data rather than existing as configured but unmonitored systems. Audit evidence requirements under SOC 2 security criteria mandate documentation of monitoring activities and incident response actions, with IPS logs satisfying both requirements through automated timestamped records of detections and preventions.
Reducing Risk in Compliance Reporting
Automated threat prevention reduces breach scope and associated regulatory penalties by containing compromises before attackers access sensitive data. GDPR Article 83 penalty calculations consider technical measures implemented to minimize data protection risks, with documented IPS deployment demonstrating organizational commitment to state-of-the-art security controls. Faster detection and automated response capabilities reduce notification obligations under breach disclosure requirements—many regulations exempt security incidents where technical controls prevented unauthorized data access, a condition IPS helps establish through documented threat blocking.
Implementation Best Practices
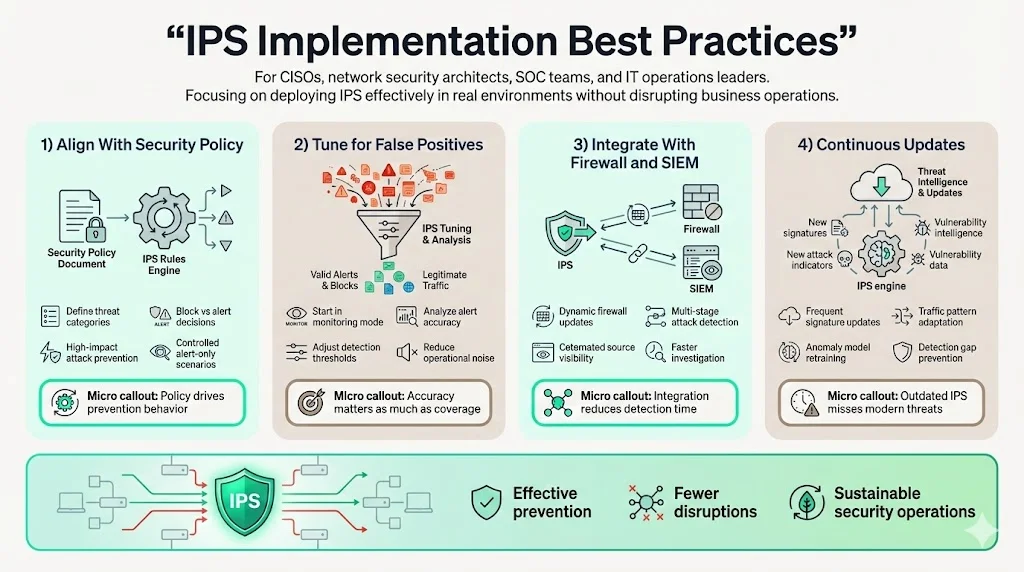
1) Align With Security Policy
Define clear threat policies before IPS deployment, documenting which attack categories warrant automated blocking versus alert-only monitoring. Policy development requires balancing security objectives with operational continuity—overly aggressive blocking policies disrupt legitimate business processes, while permissive configurations allow preventable compromises. Organizations with mature risk management programs base IPS policies on threat modeling outcomes, prioritizing automated prevention for high-impact attack vectors while using alert-based detection for less critical threats where false positive risks outweigh compromise consequences.
2) Tune for False Positives
Balance detection sensitivity with operational continuity through systematic tuning processes that reduce false positive rates without degrading threat coverage. Initial deployments typically operate in monitoring mode, logging detected threats without automated blocking while security teams analyze alert accuracy and adjust detection thresholds. Tuning efforts focus on anomaly detection baselines—refining traffic models to distinguish normal business activities from genuine threats—and signature customization, disabling generic signatures triggering excessive false positives in specific environments while maintaining protection against relevant attack vectors.
3) Integrate with Firewall and SIEM
Coordinate IPS with existing security infrastructure through standardized integration mechanisms. Firewall integration enables dynamic policy updates based on IPS threat intelligence, automatically blocking source addresses identified in active attacks across all enforcement points. SIEM integration provides centralized visibility into security events spanning multiple domains, enabling correlation of IPS alerts with authentication logs, endpoint detections, and application security findings to identify multi-stage attacks. Integration reduces mean time to detection for sophisticated threats exhibiting indicators across multiple security controls.
4) Continuous Updates
Maintain current detection capabilities through regular signature updates, anomaly model refinement, and threat intelligence feed integration. Signature databases require frequent updates—often daily—to incorporate indicators of compromise from recent malware campaigns and newly disclosed vulnerabilities. Anomaly detection models need periodic retraining to reflect legitimate changes in network traffic patterns from business growth, application deployments, or operational changes. Organizations falling behind on updates face detection gaps allowing recent threats to bypass outdated signature sets.
Challenges and Limitations
False positive detections remain the primary operational challenge in IPS deployment, occurring when legitimate traffic matches threat signatures or deviates from behavioral baselines sufficiently to trigger prevention actions. Excessive false positives disrupt business operations by blocking authorized applications, degrading user experience, and generating alert fatigue among security teams drowning in routine investigations. Organizations must invest substantial tuning effort balancing detection sensitivity with operational requirements—a process requiring deep understanding of both normal business traffic patterns and attacker techniques.
Performance degradation occurs when IPS throughput capacity cannot sustain network traffic volumes, introducing latency that impacts application responsiveness and user experience. Deep packet inspection requires significant processing resources, particularly for encrypted traffic requiring SSL/TLS decryption before content analysis. High-bandwidth environments—multi-gigabit internet connections or data center interconnects—demand IPS appliances with hardware acceleration capabilities or distributed architectures load-balancing inspection across multiple devices to maintain wire-speed performance.
Automated response capabilities require careful constraint to prevent business disruption from overly aggressive blocking policies. IPS systems detecting potential threats in traffic supporting critical business processes face difficult decisions between blocking suspicious activity and maintaining operational continuity. Organizations must define clear escalation procedures determining which threat categories warrant immediate automated blocking versus alert-only responses allowing manual investigation before taking prevention actions that might impact business operations.
Conclusion
Intrusion Prevention Systems provide essential threat coverage for enterprise cybersecurity programs, extending perimeter defenses beyond static firewall rules to include real-time traffic analysis and automated threat neutralization. IPS addresses the fundamental limitation of traditional security controls—their inability to detect and prevent sophisticated attacks exploiting legitimate protocols and authorized network access. Through continuous monitoring, deep packet inspection, and automated prevention capabilities, IPS reduces attacker dwell time from months to minutes while providing documented evidence of ongoing security controls operation required for regulatory compliance.
The core value of IPS emerges from its operational model: inline deployment enabling immediate threat prevention rather than detection requiring manual response. Organizations implementing IPS as part of defense-in-depth strategies gain overlapping security controls protecting against perimeter breaches, internal threats, and application-layer attacks simultaneously. Combined with proper tuning, continuous updates, and integration with complementary security tools, IPS transforms enterprise networks from passively filtered environments into actively defended infrastructure that neutralizes threats before they compromise protected assets.
FAQs
1. What is the difference between an IPS system and a firewall?
Firewalls filter traffic based on source/destination addresses, ports, and protocols defined in access control lists, blocking unauthorized connection attempts at network and transport layers. IPS inspects deeper into packet payloads and traffic behavior, detecting and preventing threats that exploit legitimate protocols and authorized ports—attacks that pass firewall rules but exhibit malicious characteristics through content analysis or behavioral patterns.
2. Can IPS detect zero-day threats?
IPS detects zero-day threats primarily through anomaly-based detection, which identifies attacks by recognizing behavioral deviations from established baselines rather than matching known signatures. Effectiveness depends on baseline accuracy and detection sensitivity tuning—overly permissive baselines miss novel attacks, while overly strict thresholds generate excessive false positives requiring investigation and potentially blocking legitimate activities.
3. How does IPS contribute to compliance?
IPS satisfies regulatory requirements for continuous security monitoring, intrusion detection capabilities, and technical safeguards protecting sensitive data during transmission and processing. Compliance frameworks like PCI-DSS, HIPAA, and ISO 27001 explicitly require intrusion detection or prevention systems monitoring protected environments. IPS logs provide audit evidence demonstrating ongoing security controls operation and documenting incident response actions—essential for compliance reporting and audit readiness.
4. Should IPS be cloud-based or on-premises?
IPS deployment model depends on infrastructure architecture and workload location. On-premises IPS protects traditional data centers and physical office networks, providing hardware-accelerated inspection at wire speed for high-bandwidth environments. Cloud-based IPS protects cloud-native infrastructure, integrating with virtual networks and cloud security platforms while scaling elastically with workload demand. Hybrid organizations typically deploy both models, positioning IPS at each location where workloads operate.
5. What are common integration points for IPS?
IPS integrates with firewalls for coordinated policy enforcement and dynamic blocking based on threat intelligence, SIEM platforms for centralized security monitoring and incident correlation, endpoint protection platforms for coordinated response across network and host defenses, threat intelligence feeds for continuous signature updates, and network access control systems for automated quarantine of compromised devices detected through traffic analysis.



.svg)
.svg)
.svg)