Enterprise buyers evaluate vendors through a security-first lens. During initial reviews, RFPs, and due diligence questionnaires, they consistently ask whether suppliers maintain an Information Security Management System—and whether that ISMS is ISO 27001 certified. This inquiry stems from fundamental risk management: organizations cannot afford to rely on vendors who lack structured, repeatable security operations. Ad hoc security programs create unpredictable risk exposure, particularly when sensitive data, infrastructure access, or regulatory obligations are involved. Most organizations have security controls, but without an ISMS, those controls tend to be disorganized and disjointed—implemented as point solutions to specific situations rather than systematic protection.
What Does ISMS Stand For?
ISMS stands for Information Security Management System. The term "management system" carries specific meaning: it denotes organizational infrastructure designed to direct and control security activities systematically. An ISMS is a set of policies and procedures designed to protect an organization's information assets, establishing ownership, accountability, and ongoing oversight across security functions.
Organizations maintain management systems for quality (ISO 9001), environmental impact (ISO 14001), and business continuity (ISO 22301). An ISMS applies this structured approach specifically to information security, creating repeatable processes that persist beyond individual personnel or projects. This management system structure ensures security remains embedded in business operations rather than existing as isolated technical initiatives.
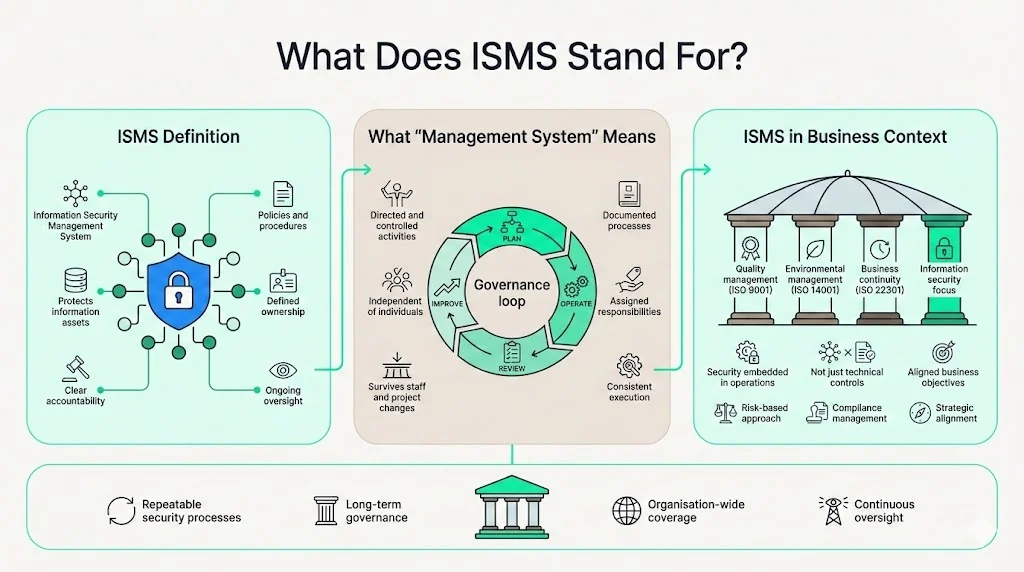
Core Purpose of an ISMS
An ISMS exists to protect sensitive business and customer data through risk-based security operations. It helps organizations protect sensitive company information, mitigate security threats, comply with legal and regulatory requirements, and enhance their cybersecurity posture. Rather than implementing controls because they appear on generic checklists, ISMS requires organizations to identify specific risks to their information assets, assess potential impact and likelihood, then deploy controls proportional to actual risk exposure.
This approach supports information assurance—the confidence that information remains confidential, maintains integrity, and stays available to authorized users when needed. ISO 27001 defines requirements for implementing an effective ISMS based on four essential criteria: availability, integrity, confidentiality, and traceability of data and services. These criteria apply across information types: customer records, intellectual property, financial data, employee information, and operational systems.
An ISMS enables consistent decision-making around security by establishing documented methodologies for evaluating risks, selecting controls, responding to incidents, and measuring effectiveness. When acquisitions occur, new products launch, or third-party integrations are proposed, the ISMS provides a framework for assessing security implications and implementing appropriate safeguards.
Key Components of an ISMS
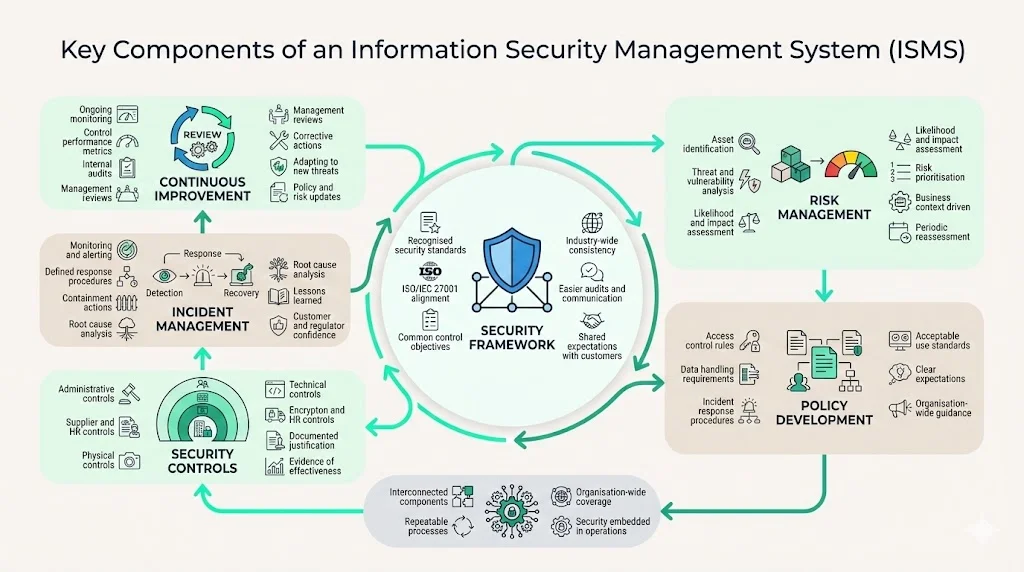
Security Framework
Security frameworks provide structure and shared language for implementing ISMS requirements. Rather than inventing proprietary security methodologies, organizations typically align their ISMS with widely accepted cybersecurity standards. ISO/IEC 27001 is the world's best-known standard for information security management systems, defining requirements an ISMS must meet. Frameworks establish common control objectives, enabling consistent security practices across industries and facilitating communication with customers, auditors, and regulators who reference the same standards.
Risk Management
Risk management forms the foundation of every ISMS. Organizations must identify assets requiring protection, assess threats and vulnerabilities affecting those assets, evaluate likelihood and impact of potential security events, then prioritize risks based on business context. This analysis drives control selection: high-risk scenarios demand stronger safeguards, while lower-risk situations may warrant basic protections. Risk assessments are not one-time exercises—ISMS requires periodic reassessment as systems change, threats evolve, and business operations expand.
Policy Development
Security policies establish expectations for how personnel, systems, and processes handle information assets. Effective policies address access control (who can access what resources under which conditions), data handling (classification, storage, transmission, and disposal requirements), incident response (detection, reporting, investigation, and remediation procedures), and acceptable use (approved activities involving company systems and data). Policies provide the governance layer that translates security objectives into operational requirements.
Security Controls
Controls are the specific measures organizations implement to reduce risk. These include technical measures such as data encryption, antivirus software, and logging, as well as organizational measures covering human resources security, project risk management, and supplier relations. Administrative controls establish procedures and responsibilities, technical controls leverage security technologies, and physical controls protect facilities and hardware. ISMS requires documenting which controls are implemented, why they were selected, how they operate, and evidence demonstrating their effectiveness.
Incident Management
Even comprehensive security controls cannot eliminate all risk. ISMS requires documented incident management capabilities: detecting security events through monitoring and alerting, responding according to defined procedures, containing damage, investigating root causes, and capturing lessons learned. Enterprise customers scrutinize incident response plans because they reveal whether vendors can handle breaches professionally, notify affected parties appropriately, and implement corrective actions that prevent recurrence.
Continuous Improvement
ISO 27001 promotes a culture of continual improvement in information security practices, requiring regular monitoring, performance evaluation, and periodic reviews to help organizations adapt to evolving threats. ISMS is not a static certification milestone—it demands ongoing measurement, internal audits, management reviews, and corrective actions. Organizations collect metrics on control effectiveness, track security incidents, review risk assessments when circumstances change, and update policies as regulations evolve.
How ISMS Supports Enterprise Compliance
Organizations serving enterprise customers face diverse compliance requirements: industry regulations (HIPAA for healthcare, PCI DSS for payment processing), regional privacy laws (GDPR in Europe, CCPA in California), and customer-specific security mandates. An ISMS provides the systematic framework required to meet these obligations without treating each as isolated compliance projects.
Rather than implementing separate control sets for each regulation, organizations map ISMS controls to multiple compliance requirements simultaneously. A documented access control procedure supporting ISO 27001 certification typically satisfies corresponding HIPAA technical safeguards, GDPR security requirements, and SOC 2 access criteria. This control mapping reduces redundant effort and ensures consistent implementation across compliance frameworks.
ISMS makes audits faster and less disruptive because required evidence already exists within the management system. Organizations maintaining documented policies, risk assessments, control descriptions, and monitoring records can respond to audit requests efficiently. Auditors examining ISO 27001 certification, regulatory assessments, or customer security reviews evaluate the same ISMS documentation rather than requiring separate artifacts for each engagement.
ISMS and ISO 27001: How They Connect
As per the ISO Survey 2022, over 70,000 certificates were reported in 150 countries across all economic sectors, establishing ISO 27001 as the globally recognized standard for information security management. ISO 27001 specifies requirements for establishing, implementing, maintaining, and continually improving an information security management system. The standard defines what an ISMS must include: documented scope, risk assessment methodology, security policies, control implementation, competence requirements, operational procedures, performance monitoring, internal audit processes, and management review cycles.
Organizations can operate an ISMS without pursuing ISO 27001 certification, but the standard provides the authoritative framework most enterprises reference when evaluating vendor security programs. ISO 27001 certification demonstrates that an independent, accredited auditor verified the ISMS meets international requirements—transforming self-assessed security claims into third-party validated attestation.
The ISMS acts as the foundation for ISO 27001 compliance. Conformity with ISO 27001 means an organization has implemented a system to manage risks related to data security, and that this system respects all best practices and principles in the International Standard. Without an operational ISMS—documented policies, implemented controls, risk assessment processes, and continuous monitoring—ISO 27001 certification cannot be achieved or maintained.
Is ISMS Required for ISO 27001?
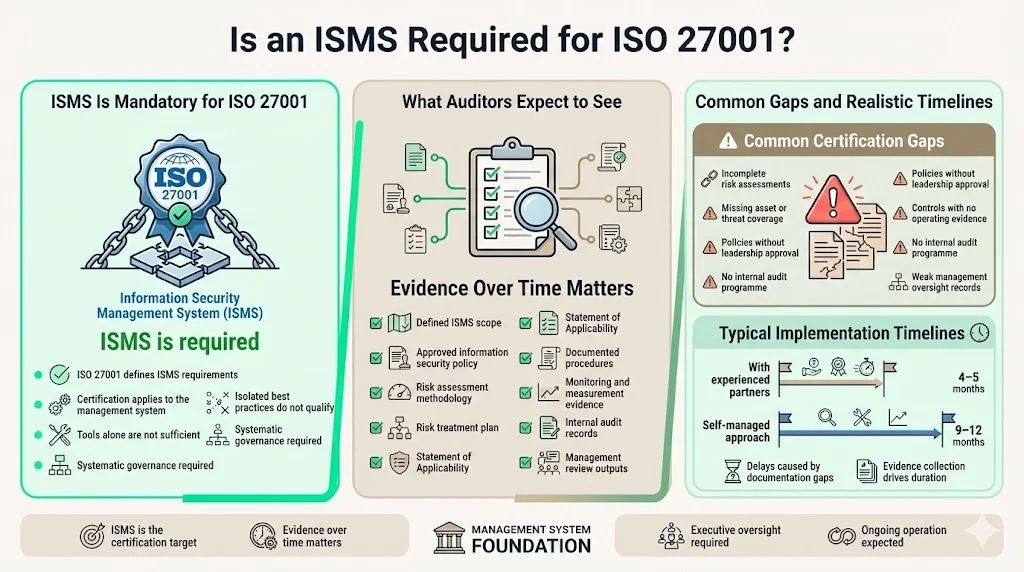
Yes. Organizations with an ISMS that meet the standard's requirements can choose to have it certified by an accredited certification body following successful completion of an audit. An ISMS is not optional for ISO 27001—the standard exists specifically to define ISMS requirements. Organizations cannot obtain ISO 27001 certification by implementing security tools or adopting isolated best practices; they must establish the complete management system infrastructure the standard prescribes.
Auditors expect to see documented evidence across all ISMS components: scope definition establishing boundaries of the management system, information security policy approved by leadership, risk assessment and treatment methodology, Statement of Applicability identifying which controls are implemented and why, documented procedures for operational processes, evidence of control effectiveness through monitoring and measurement, internal audit results, and management review records demonstrating ongoing oversight.
The preliminary audit includes checks for existence and completeness of key documentation such as the organization's information security policy, Statement of Applicability, and Risk Treatment Plan. Common gaps delaying certification include incomplete risk assessments that fail to cover all assets or threat scenarios, policies lacking management approval or periodic review, controls deployed without documented procedures or evidence of effectiveness, missing internal audit programs, and inadequate management review demonstrating executive oversight. Organizations pursuing ISO 27001 certification should allocate 4-5 months for ISMS implementation when working with experienced compliance partners, compared to 9-12 months for self-managed approaches.
Who Maintains an ISMS?
ISMS maintenance requires shared ownership across organizational functions. Executive leadership provides strategic direction, approves policies, allocates resources, and conducts management reviews. Security teams design controls, monitor effectiveness, respond to incidents, and recommend improvements. IT operations implement technical controls, maintain security infrastructure, and support evidence collection. Legal and compliance functions interpret regulatory requirements, review contractual obligations, and ensure alignment with privacy laws. Human resources manages personnel security, delivers training, and enforces acceptable use policies.
ISO 27001 emphasizes the importance of management commitment to information security and the need to involve all relevant stakeholders in development and implementation of the ISMS. Typical roles include an Information Security Officer or CISO responsible for overall ISMS direction, control owners accountable for implementing and maintaining specific security measures, internal auditors verifying control effectiveness, risk owners identifying and assessing threats to their business functions, and executive leadership approving risk treatment decisions.
Organizations lacking dedicated security resources often engage managed security and compliance services to establish and operate their ISMS. This approach provides immediate access to experienced security professionals who implement controls within existing infrastructure, collect and organize audit evidence, conduct internal assessments, track remediation, and maintain continuous compliance—reducing internal team investment from 550-600 hours annually to approximately 75 hours for oversight and strategic decisions.
How Often Should an ISMS Be Reviewed?
ISMS reviews occur on multiple cycles. Internal reviews happen continuously as personnel monitor security controls, track incidents, and assess control effectiveness through ongoing operations. Organizations typically conduct formal risk reassessments quarterly or when significant changes occur: new systems deployed, major acquisitions completed, expanded data processing activities, or material security incidents.
The ISMS should be monitored and reviewed regularly to ensure effectiveness, including monitoring control effectiveness, reviewing risk assessments, conducting internal audits, and seeking stakeholder feedback. Management reviews—executive-level assessments of ISMS performance—should occur at least annually, examining audit findings, security metrics, compliance status, risk assessment changes, and improvement opportunities. These reviews result in documented decisions regarding resource allocation, policy updates, and strategic security direction.
ISO 27001 certification is valid for three years, with mandatory annual follow-up audits to ensure the certified party maintains an up-to-date ISMS. Organizations must complete surveillance audits demonstrating continued compliance approximately 12 and 24 months after initial certification, followed by recertification audit at the three-year mark.
Triggers for out-of-cycle updates include regulatory changes requiring new controls or procedures, significant security incidents revealing control gaps, major business changes such as mergers or new product lines, third-party audit findings identifying deficiencies, and customer security requirements exceeding current ISMS scope. All organizations must transition to the ISO 27001:2022 standard by October 31, 2025, with revisions including updates reflecting modern business practices and emerging threats.
Does ISMS Apply to Cloud Environments?
ISMS applies regardless of infrastructure model—on-premises data centers, cloud providers, hybrid architectures, or SaaS applications. ISMS scope can encompass cloud-based services across all channels and interfaces, including personnel, information technology systems, applications, policies, procedures, standards, tools, utilities, and data used in executing those services. The management system addresses how organizations select cloud providers, define security requirements in contracts, configure cloud resources according to security policies, monitor cloud infrastructure for threats, and manage data protection in shared responsibility environments.
Cloud environments introduce shared responsibility considerations: cloud providers secure underlying infrastructure while customers remain responsible for data protection, access management, application security, and compliance. ISMS must document this division of responsibility, verify provider controls through SOC 2 reports or ISO 27001 certificates, and implement compensating controls for gaps. For example, cloud providers typically manage physical data center security and hypervisor hardening, while customers configure network security groups, encryption keys, identity access management, and data backup procedures.
Managing third-party and vendor risk becomes critical when cloud services process sensitive data or connect to core systems. ISMS requires documented vendor assessment procedures: evaluating security posture during procurement, defining contractual security obligations, reviewing compliance certifications, monitoring vendor performance, and reassessing risk when vendors make infrastructure changes. Organizations cannot outsource security accountability—the ISMS must demonstrate that cloud and SaaS vendors are selected, configured, and monitored according to risk-based criteria aligned with the organization's own security requirements.
Business Benefits of an ISMS for Companies Selling to Enterprises
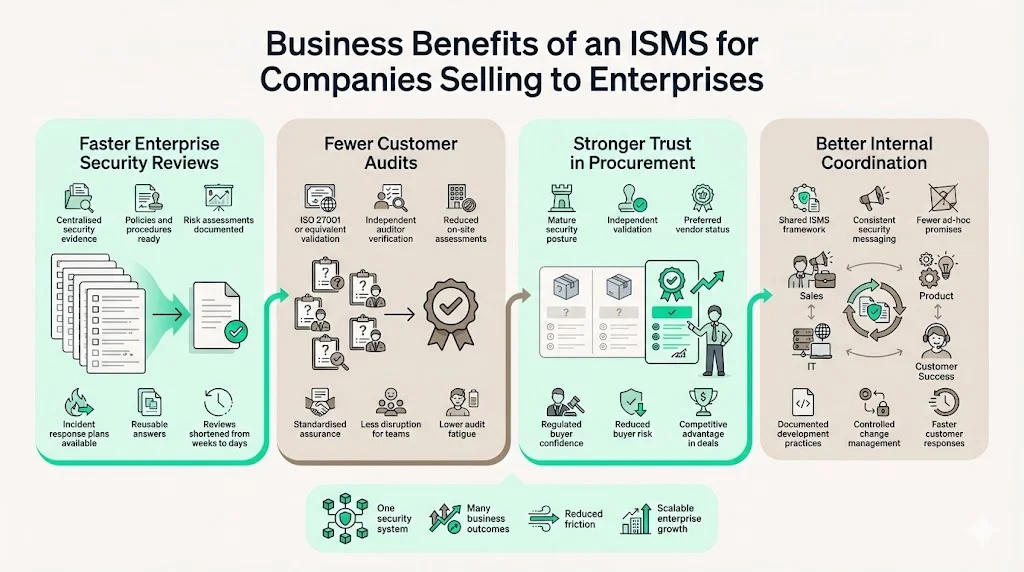
Organizations targeting enterprise markets gain competitive advantages through documented ISMS operations. Security reviews and vendor questionnaires complete faster because required evidence already exists: security policies, risk assessments, control descriptions, incident response procedures, and compliance certifications. Rather than scrambling to answer hundreds of security questions during each sales cycle, vendors with operational ISMS reference centralized documentation, often reducing security review duration from weeks to days.
Fewer custom audits from customers result when vendors maintain ISO 27001 certification or equivalent third-party validated ISMS. Enterprise buyers increasingly accept standardized security attestations rather than conducting redundant on-site assessments. A vendor presenting ISO 27001 certification demonstrates that an independent auditor verified comprehensive security controls—substantially reducing the need for customer-specific security evaluations.
Stronger trust signals during procurement differentiate vendors in competitive situations. When multiple suppliers offer comparable functionality and pricing, enterprise buyers prioritize those demonstrating mature security programs through ISMS certification. This becomes decisive in regulated industries where customers face liability for vendor security failures: healthcare organizations selecting business associates under HIPAA, financial institutions evaluating service providers under GLBA, or European companies assessing processors under GDPR.
Better internal coordination around security emerges as different departments reference the same ISMS framework. Sales teams understand which security certifications the organization maintains and can articulate security capabilities consistently. Product development follows documented secure development procedures. IT operations implement changes according to defined change management processes. Customer success responds to security inquiries using approved documentation. This alignment reduces miscommunication, prevents unauthorized security commitments, and ensures consistent execution across customer-facing activities.
Common ISMS Misunderstandings
"ISMS is just paperwork": This characterization confuses documented evidence with actual security operations. ISMS requires both implementing controls and documenting their operation. Organizations manufacturing compliance artifacts without corresponding security controls fail audits and, more importantly, remain fundamentally insecure. Effective ISMS means deployed controls protect systems—policies reflect actual practices, access lists match documented authorization procedures, monitoring detects real threats, and incident response plans work during actual security events.
"ISMS is only for large companies": The ISO 27001 standard provides companies of any size and from all sectors of activity with guidance for establishing, implementing, maintaining, and continually improving an information security management system. While implementation complexity scales with organizational size, fundamental ISMS principles apply universally: document security policies, assess risks systematically, implement appropriate controls, monitor effectiveness, and improve continuously. Small organizations benefit from structured security approaches, particularly when competing for enterprise customers who evaluate vendor security regardless of company size.
"Once built, it runs itself": ISMS demands sustained attention and resources. The ISMS should be continually improved to ensure it remains effective. Threats evolve, systems change, regulations update, and business operations expand—requiring corresponding ISMS adjustments. Organizations treating ISMS as completed projects rather than ongoing operational disciplines experience control drift: policies become outdated, risk assessments fail to cover new systems, monitoring loses effectiveness, and audit readiness degrades. Successful ISMS operations require dedicated ownership, regular internal reviews, prompt incident response, continuous risk assessment, and management engagement.
Conclusion
Understanding what ISMS means—and what it requires operationally—matters increasingly in enterprise markets where security due diligence precedes purchase decisions. Data theft, cybercrime, and liability for privacy leaks are risks all organizations must factor in, requiring strategic thinking about information security needs and how they relate to business objectives, processes, size, and structure. Organizations selling to regulated industries, processing sensitive data, or competing for major contracts face escalating expectations for documented security programs supported by third-party validation.
An ISMS transforms security from ad hoc technical implementations into systematic risk management embedded in business operations. This structured approach supports long-term security effectiveness while simultaneously enabling compliance across multiple frameworks, accelerating enterprise sales cycles, and reducing audit burden. Most importantly, an effective ISMS produces actual security—controls that protect systems, processes that detect threats, and capabilities that respond to incidents—rather than documentation artifacts disconnected from operational reality.
Structured security programs have become expected rather than optional. Enterprise buyers recognize that vendors lacking ISMS cannot demonstrate consistent security practices, respond predictably to incidents, or maintain compliance as regulations evolve. Organizations implementing ISMS—particularly those pursuing ISO 27001 certification—signal operational maturity that differentiates them competitively while building genuine security infrastructure supporting sustainable business growth.
FAQs
1. What does ISMS stand for?
ISMS stands for Information Security Management System—a systematic framework combining policies, procedures, processes, and controls designed to protect information assets and manage security risks. The term emphasizes structured management of security operations rather than isolated technical implementations.
2. Is ISMS required for ISO 27001?
Yes. ISO 27001 specifically defines requirements for establishing, implementing, maintaining, and improving an ISMS. Organizations cannot obtain ISO 27001 certification without first building the complete management system infrastructure the standard prescribes, including documented scope, policies, risk assessments, controls, monitoring procedures, internal audits, and management reviews.
3. Who maintains an ISMS?
ISMS maintenance requires shared ownership: executive leadership provides strategic direction and resource allocation, security teams design and monitor controls, IT implements technical safeguards, legal interprets regulatory requirements, and HR manages personnel security. Typical roles include Information Security Officers responsible for overall direction, control owners maintaining specific security measures, and internal auditors verifying effectiveness.
4. How often should an ISMS be reviewed?
Internal reviews occur continuously through operational monitoring. Formal risk reassessments typically happen quarterly or when significant changes occur. Management reviews examining overall ISMS performance should occur at least annually. ISO 27001 certified organizations undergo surveillance audits approximately every 12 months and recertification every three years. Out-of-cycle reviews occur when regulatory changes, security incidents, business changes, or audit findings require immediate updates.
5. Does ISMS apply to cloud environments?
Yes. ISMS applies regardless of infrastructure model—on-premises, cloud, hybrid, or SaaS. The management system addresses cloud provider selection, contractual security requirements, shared responsibility boundaries, configuration management, threat monitoring, and vendor risk assessment. Organizations remain accountable for data protection even when using cloud services, requiring documented procedures for evaluating provider controls and implementing compensating measures for gaps.



.svg)
.svg)
.svg)