Most enterprise procurement processes now specify Common Criteria certification for IT products, yet many vendors selling into regulated sectors remain unclear about what ISO/IEC 15408 actually requires. This creates a procurement barrier—vendors without proper evaluation documentation lose enterprise deals to competitors who understand the evaluation framework. In 2026, as supply-chain security scrutiny intensifies and government contracts increasingly mandate third-party security validation, understanding ISO 15408 becomes a competitive necessity for product vendors.
ISO/IEC 15408—commonly known as the Common Criteria for Information Technology Security Evaluation—provides the international standard framework for evaluating security properties of IT products and systems. For vendors targeting enterprise clients, large organisations, or government contracts, this standard represents the difference between being qualified to bid and being excluded from consideration.
This definition addresses what ISO 15408 is, how its evaluation structure works, why it matters for vendors serving enterprise markets, and how organisations should approach certification strategically in 2026.
What is ISO 15408?
ISO/IEC 15408 establishes the general concepts and principles of IT security evaluation and specifies the general model of evaluation used as the basis for evaluation of security properties of IT products. The standard originated from efforts to unify disparate national security evaluation criteria—Canadian TCSEC, European ITSEC, and similar frameworks—into a single internationally recognised standard. ISO published the current edition, ISO/IEC 15408:2022, in August 2022 and represents the fourth edition of the standard.
Unlike organisational security frameworks that evaluate management systems, ISO 15408 evaluates specific products or systems against defined security functional and assurance requirements. The standard is designed for evaluating the security properties of IT products, not administrative or business processes. This product-focused approach makes ISO 15408 uniquely relevant for software vendors, hardware manufacturers, and integrated system providers selling into markets where security validation is a procurement requirement.

The structure of the standard
ISO/IEC 15408 comprises multiple parts addressing different aspects of evaluation. Part 1 provides the introduction and general model, establishing core concepts and evaluation principles. Part 2 defines security functional components—the security capabilities a product must demonstrate. Part 3 defines the assurance requirements of the ISO/IEC 15408 series and includes the individual assurance components from which the evaluation assurance levels are composed, and the criteria for evaluation of Protection Profiles and Security Targets. Part 5 provides packages of security assurance and security functional requirements, including the evaluation assurance levels (EAL) and the composed assurance packages.
The Target of Evaluation (TOE) is the set of software, firmware and/or hardware possibly accompanied by guidance, which is the subject of an evaluation. A Protection Profile (PP) is an implementation-independent statement of security needs for a TOE. The Security Target (ST) is the vendor's document specifying how their product meets security requirements—either conforming to an existing PP or defining requirements independently. These three concepts form the foundation of every ISO 15408 evaluation.
Core goals and scope
ISO 15408 addresses confidentiality, integrity, and availability of IT products and systems through two dimensions: functionality and assurance. Security functional requirements define what the product does to enforce security policies—access control mechanisms, audit capabilities, cryptographic operations, identification and authentication. Security assurance requirements define how the product is developed, tested, and maintained to provide confidence that security functions operate correctly and cannot be easily subverted.
The standard does not address purely organisational controls, administrative policies, or legal compliance frameworks. A product certified under ISO 15408 demonstrates specific security capabilities and development rigour—not that the deploying organisation manages it properly or operates within a compliant security programme. This distinction matters: vendors need ISO 15408 for product validation; organisations deploying those products typically need ISO 27001 for their security management system.
Key concepts for product vendors and enterprise clients
1) Security functional requirements (SFRs)
Security functional requirements specify the security behaviours a product must exhibit. These include user data protection, identification and authentication, security management, privacy, protection of security functions, resource utilisation, access control, and audit capabilities. For vendors, SFRs represent the testable security features enterprise buyers evaluate during procurement. A firewall claiming to enforce network segmentation must demonstrate specific access control and audit functions. An authentication system must prove it implements appropriate identification, authentication, and session management capabilities.
Enterprise clients examining vendor certifications should verify that SFRs align with their security requirements. A product evaluated against weak or irrelevant SFRs provides limited assurance, regardless of its evaluation level.
2) Security assurance requirements (SARs) and assurance levels
Security assurance requirements address how rigorously a product is developed and evaluated. There are 7 Evaluation Assurance Levels (EALs) with varying levels of security assurance requirements. EAL1 represents functionally tested products with minimal assurance activities. EAL2 adds structural testing. EAL3 requires methodically tested and checked development. EAL4—the most commonly pursued level—requires methodically designed, tested, and reviewed development with vulnerability analysis. EAL5 through EAL7 represent progressively rigorous semi-formal and formal methods, typically reserved for high-security government or military applications.
Higher EALs require substantially more development discipline, documentation, testing, and evaluation effort. Most commercial products target EAL2 through EAL4. Some national evaluation schemes are phasing out EAL-based evaluations and only accept products for evaluation that claim strict conformance with an approved PP, reflecting a shift toward standardised Protection Profiles rather than vendor-defined evaluation targets.
3) Protection Profiles and Security Targets
Protection Profiles standardise security requirements for categories of products. Government agencies and industry consortia publish PPs defining the security expectations for firewalls, operating systems, mobile devices, network devices, and other product classes. A vendor building a network firewall can evaluate their product against the Network Device Protection Profile rather than defining requirements from scratch. This standardisation benefits enterprise procurement—buyers can compare products evaluated against the same PP, knowing the security requirements are consistent.
Security Targets document how a specific product satisfies requirements. The ST identifies the TOE, defines the security problem the product addresses, specifies security objectives, and details the security functional and assurance requirements the product meets. For enterprise buyers, the ST reveals what the vendor actually evaluated—not marketing claims, but documented, tested security capabilities. Vendors submit STs to accredited evaluation labs; successful evaluation results in certification.
4) Security levels, criteria development and evaluation methodology
Evaluation Assurance Levels function as security levels within ISO 15408, though this terminology can mislead. EALs measure evaluation rigour and development discipline, not absolute security strength. A product at EAL2 might provide stronger security than an EAL4 product if it implements better security functions—the EAL indicates only how thoroughly those functions were evaluated and how disciplined the development process was.
The standard provides the criteria framework; evaluation methodology is detailed in ISO/IEC 18045, the Common Evaluation Methodology. Accredited evaluation facilities conduct assessments according to this methodology, examining documentation, reviewing design, conducting testing, and verifying that security functions operate as claimed. National schemes—operated by agencies like NIAP in the United States, BSI in Germany, ANSSI in France, and similar bodies—accredit evaluation labs and issue certifications.
5) Trusted computing, software assurance and system integrity
ISO 15408 evaluation supports trusted computing objectives by providing independent verification that a product implements security functions correctly and was developed with appropriate rigour. For enterprise clients concerned about supply-chain security, this third-party validation reduces risk. Software assurance—confidence that software is built securely, tested thoroughly, and maintained properly—is demonstrated through assurance requirements and evaluation activities. System integrity requirements ensure products protect themselves from tampering, maintain security functions under stress, and fail securely when attacked.
Vendors achieving ISO 15408 certification can credibly claim their products underwent independent security evaluation. Enterprise buyers gain documented evidence of security capabilities rather than relying on vendor self-assessment.
Why ISO 15408 matters for businesses selling to enterprise clients
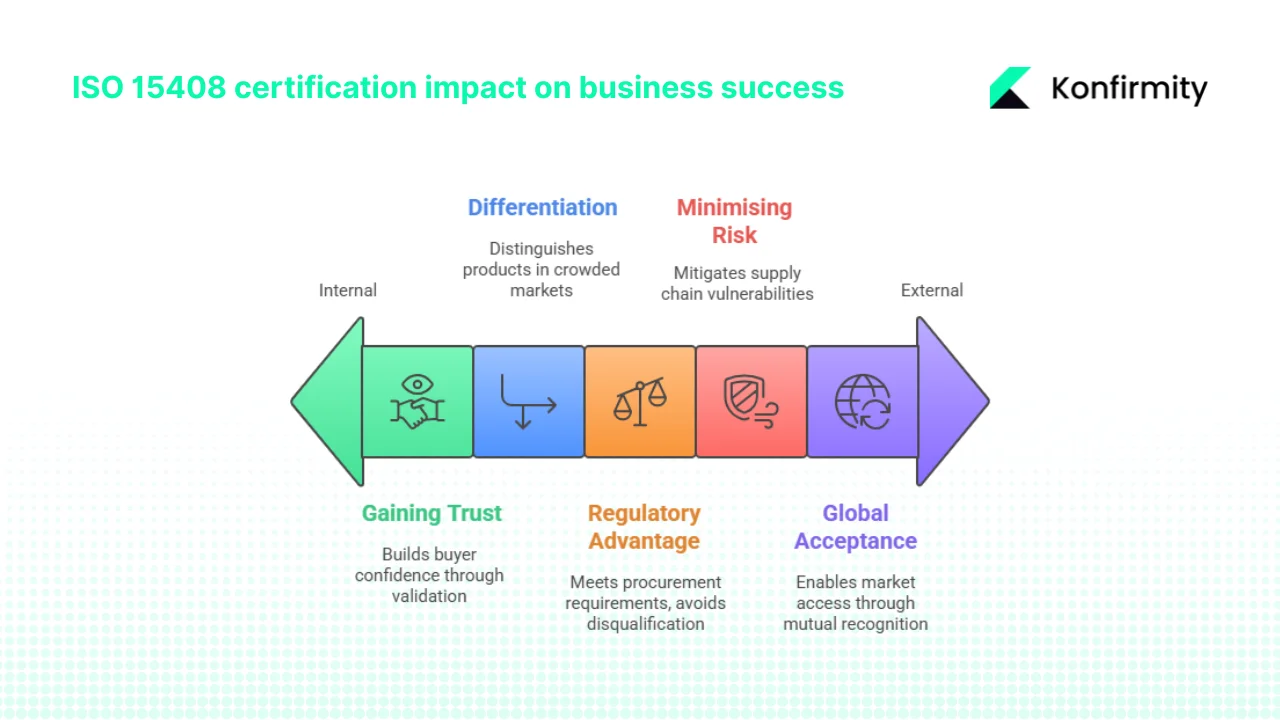
1) Gaining enterprise buyer trust
Enterprise procurement increasingly requires evidence of third-party security validation. Security questionnaires demand certifications, independent assessments, and documented security capabilities. Vendors without recognised security evaluation face skepticism—enterprise security teams have limited capacity to audit every vendor's security claims independently. ISO 15408 certification provides standardised, internationally recognised validation that security functions exist and were independently tested. For vendors competing in risk-averse enterprise markets, this certification translates vendor claims into verifiable facts.
2) Competitive differentiation
In markets where multiple vendors offer similar functionality, security evaluation distinguishes products. When two firewall vendors propose equivalent features but one holds ISO 15408 certification against the Network Device Protection Profile and the other relies on marketing materials, the certified vendor wins security-conscious buyers. This differentiation intensifies in regulated sectors—financial services, healthcare, critical infrastructure—where security failures create regulatory consequences and reputational damage.
3) Regulatory and contractual advantage
Government procurement in numerous countries requires or strongly favours ISO 15408 evaluated products. United States federal agencies follow NIAP requirements for certain product categories. European defence and critical infrastructure procurement references Common Criteria certification. Vendors without appropriate evaluation face automatic disqualification from high-value contracts. Beyond government, enterprises in regulated industries incorporate ISO 15408 requirements into vendor contracts, particularly for products processing sensitive data or controlling critical systems. Being evaluation-ready when these procurement requirements emerge provides timing advantages over competitors scrambling to initiate evaluation after losing bids.
4) Minimising risk in the supply chain
Supply-chain security dominates enterprise risk discussions in 2026. Organisations deploying third-party products need assurance those products won't introduce vulnerabilities into their infrastructure. ISO 15408 evaluation examines not just product functionality but also development practices, vulnerability management processes, and secure lifecycle management. Enterprise clients incorporating evaluated products into their systems can document supply-chain risk mitigation efforts to their own regulators, auditors, and stakeholders. Vendors providing ISO 15408 certification become lower-risk procurement choices.
5) Scalability and global acceptance
ISO 15408 operates as an international standard with mutual recognition agreements among national schemes. A product certified under the Common Criteria Recognition Arrangement gains acceptance across member nations without requiring separate evaluations in each jurisdiction. For vendors selling globally, this recognition provides market access efficiency. A single evaluation opens procurement opportunities across North America, Europe, and Asia-Pacific markets participating in recognition agreements—substantially more efficient than pursuing country-specific certifications.
How businesses should approach ISO 15408 for 2026 and beyond
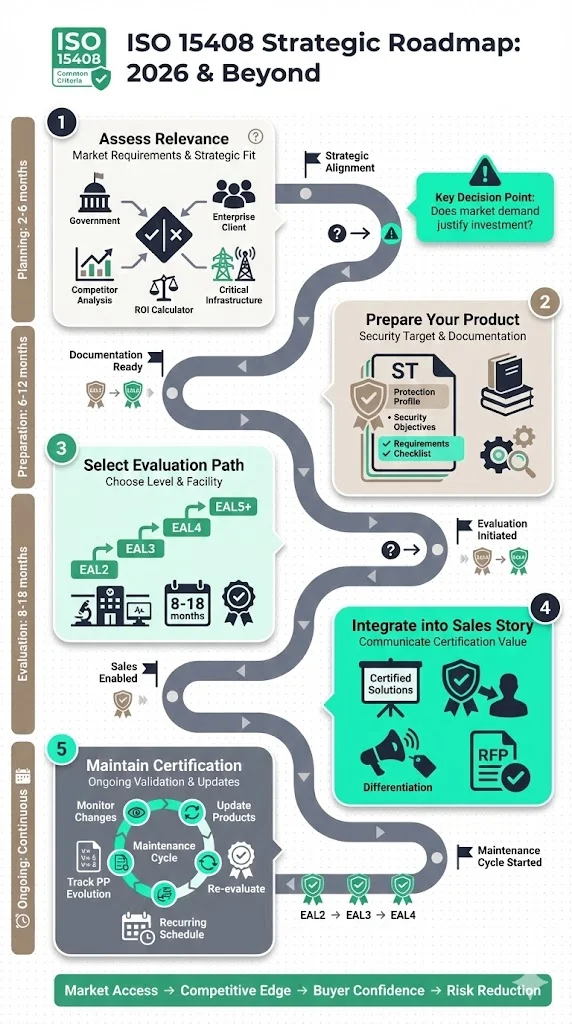
1) Assessing whether it's relevant for your product
Not every product requires ISO 15408 certification. Evaluation demands significant investment in time, resources, and evaluation facility fees. Vendors should assess market requirements systematically: Are target customers government agencies or defence contractors with explicit evaluation requirements? Do enterprise RFPs increasingly request security certifications? Are competitors achieving certification and using it competitively? Do products handle particularly sensitive data or control critical infrastructure? If answers indicate growing certification expectations, pursuing ISO 15408 becomes strategically necessary rather than optional.
For products serving consumer markets or small businesses without evaluation requirements, investment in ISO 15408 certification likely exceeds benefits. Focus evaluation resources where they create procurement advantages and contract wins.
2) Preparing your product for evaluation
Evaluation preparation begins with defining your Security Target. Identify applicable Protection Profiles for your product category. If relevant PPs exist, conform to them—this simplifies evaluation and improves market acceptance. If no PP applies, construct an ST defining your security problem, security objectives, and security requirements. Select security functional requirements addressing your product's security capabilities. Determine appropriate security assurance requirements based on target market expectations and competitive positioning.
Development and testing processes must align with chosen assurance requirements before evaluation begins. EAL4 evaluation examines design documentation, interface specifications, security architecture, testing procedures, configuration management, and vulnerability assessment processes. Products developed without appropriate documentation, testing discipline, or security focus require substantial remediation before evaluation can proceed. Factor evaluation preparation into product development timelines—retrofitting security and documentation after development proves expensive and time-consuming.
3) Selecting the evaluation path and level
Choose evaluation level based on market requirements, competitive landscape, and product risk profile. EAL2 provides basic structural testing assurance suitable for lower-risk commercial products. EAL3 and EAL4 represent methodical development and testing, appropriate for enterprise products handling sensitive data or controlling important systems. EAL5 and above apply primarily to government, defence, and critical national infrastructure where rigorous formal methods justify the substantial cost and timeline impact.
Evaluations are carried out in licensed facilities, with frequency driven by particular needs such as changes or new features of a certified product, expiry of an existing certification, or the need to achieve a higher EAL. Engage accredited evaluation facilities early in the planning process. Evaluation labs assess ST feasibility, estimate evaluation duration, and identify development gaps requiring remediation. Evaluation timelines vary by product complexity and assurance level but typically range from 8 to 18 months for EAL4 evaluations of moderately complex products.
4) Integrating into your sales and marketing story
ISO 15408 certification provides differentiation only when communicated effectively. Sales collateral should specify certification details: evaluation level achieved, Protection Profile conformance, certifying body, and certification date. Avoid vague claims like "security certified"—enterprise buyers require specifics. Train sales teams to articulate what certification means: independent third-party evaluation verified that security functions operate as documented and development followed rigorous practices. This positions certification as evidence supporting security claims rather than the claim itself.
Marketing should reference certification in contexts where it creates buyer confidence: government procurement, regulated industries, enterprise security discussions, supply-chain security conversations. Position certification as risk reduction for buyers—evaluated products require less intensive vendor security assessment by procurement teams.
5) Post-evaluation strategies and considerations
Certification maintenance requires ongoing attention. Product updates, new features, or architecture changes may invalidate certification, requiring re-evaluation. Establish change management processes identifying security-relevant modifications triggering re-evaluation. Budget for periodic re-evaluation as products evolve. Certification validity varies by scheme and product—some certifications remain valid indefinitely if the product doesn't change, others require periodic recertification regardless of product changes.
Monitor Protection Profile evolution. National schemes periodically update PPs to address emerging threats or technology changes. Products certified against outdated PPs may lose competitive advantage as buyers demand conformance with current PPs. Plan re-evaluation cycles accounting for PP updates and market expectations.
Challenges and considerations for 2026
Evaluation costs remain substantial. Evaluation facility fees, internal staff time for documentation and testing preparation, and potential product modifications to meet assurance requirements collectively require six-figure investments for typical commercial products at EAL3 or EAL4. Vendors must justify this investment through contract wins and market access that certification enables.
Threat landscapes evolve continuously. Products certified five years ago may meet original security requirements but fail to address current attack techniques. Certification alone doesn't guarantee security—maintaining robust vulnerability management, patch processes, and security monitoring remains essential. Enterprise buyers increasingly recognise this distinction, demanding evidence of ongoing security operations alongside static certification.
Cloud services, containerised applications, and software-as-a-service models challenge traditional ISO 15408 evaluation approaches designed for discrete products with defined boundaries. Protection Profiles for cloud and virtualised environments exist but continue evolving. Vendors in these spaces should monitor scheme guidance on evaluating dynamic, multi-tenant, and continuously updated services.
Aligning ISO 15408 with complementary standards creates strategic advantages. Vendors achieving ISO 15408 certification for products while maintaining ISO 27001 certification for development operations demonstrate comprehensive security commitment. This combination addresses product security (ISO 15408) and organisational security management (ISO 27001), providing enterprise buyers with confidence in both what the vendor builds and how they operate.
ISO 15408 vs other standards for enterprise sales
ISO 27001 vs ISO 15408
ISO/IEC 27001 establishes requirements for Information Security Management Systems—the organisational processes, policies, and controls managing information security holistically across an enterprise. ISO 27001 certification demonstrates an organisation operates systematic security management covering risk assessment, control implementation, incident response, business continuity, and continuous improvement. It evaluates organisational practices, not specific products.
ISO 15408 evaluates individual IT products or systems against defined security functional and assurance requirements. It examines what a product does (security functions) and how rigorously it was developed (assurance activities). ISO 15408 certification demonstrates a specific product underwent independent security evaluation.
For vendors: ISO 15408 validates product security; ISO 27001 validates operational security management. Optimal positioning involves both—ISO 15408 certifies the products you sell; ISO 27001 certifies how your organisation develops, maintains, and supports those products. For enterprise clients procuring products: demand ISO 15408 certification for products you deploy; pursue ISO 27001 certification for your own organisation's security management.
Other relevant standards and certifications
ISO 15408 complements cryptographic module standards like FIPS 140-2 and FIPS 140-3, which specifically evaluate cryptographic implementations. Products requiring both cryptographic validation and broader security evaluation pursue both certifications. Supply-chain security frameworks increasingly reference ISO 15408 as evidence of product security validation. Procurement standards in various sectors specify Common Criteria certification as baseline requirements.
Trusted computing initiatives rely on ISO 15408 evaluation to verify security capabilities of hardware roots of trust, secure boot mechanisms, and trusted execution environments. Software assurance frameworks incorporate ISO 15408 principles when evaluating development practices and security testing rigour.
Which standard to choose for enterprise-client markets
Product vendors targeting enterprise or government markets should prioritise ISO 15408 when products handle sensitive data, control critical infrastructure, or face explicit procurement requirements for security evaluation. Internal development organisations should pursue ISO 27001 for comprehensive security management. Vendors demonstrating both—ISO 15408 for products, ISO 27001 for operations—achieve maximum enterprise buyer confidence. The combination signals security commitment across both offerings and organisational practices.
Impact of ISO 15408 on product development, sales and partnerships
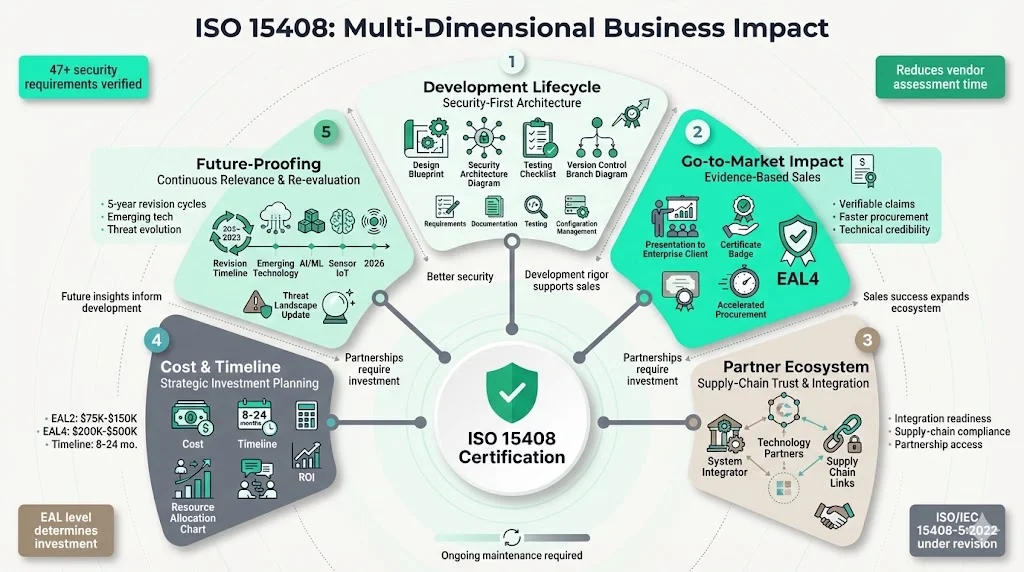
1) Impact on product development lifecycle
Pursuing ISO 15408 evaluation fundamentally changes development practices. Security requirements must be specified during design, not retrofitted after development. Architecture documentation must detail security mechanisms, interfaces, and trusted boundaries. Testing procedures must verify security functions systematically with documented test cases and results. Configuration management must track security-relevant changes and maintain version control rigour. Vulnerability assessment processes must identify and remediate weaknesses before evaluation.
These practices improve product security regardless of certification outcome. Development teams building with evaluation requirements in mind produce more secure, better-documented products. The discipline required for ISO 15408 assurance translates into better software engineering generally.
2) Impact on go-to-market and sales conversations
Certified products enable sales conversations grounded in verifiable evidence rather than claims. Instead of asserting "our product is secure," sales teams reference specific evaluation results: "Our product achieved EAL4 certification under ISO 15408, evaluated against the Application Software Protection Profile. Independent evaluation verified 47 security functional requirements across access control, audit, cryptography, identification and authentication, and security management." This specificity resonates with technical buyers conducting vendor security assessments.
Security certifications accelerate procurement cycles. Enterprise security teams reviewing vendors can accept ISO 15408 certification as evidence rather than conducting lengthy internal security assessments. This reduces time from initial contact to contract signature—particularly valuable in competitive sales situations.
3) Partner and ecosystem implications
System integrators and technology partners increasingly require upstream vendors to provide evaluated components. An integrator building a secure communications platform for government clients needs constituent products—operating systems, databases, encryption modules, authentication systems—certified under ISO 15408. Vendors providing uncertified components create integration barriers or disqualify the entire solution from consideration. Being evaluation-ready maintains ecosystem position and partnership opportunities.
Supply-chain trust extends beyond direct customers. Enterprises deploying your product must satisfy their own stakeholders, regulators, and auditors about supply-chain security. ISO 15408 certification provides documentary evidence these enterprises use to demonstrate supply-chain risk management. Your certification becomes their risk mitigation documentation.
4) Cost, timeline and resource implications
Evaluation costs vary by product complexity, chosen assurance level, and evaluation facility rates. EAL2 evaluations of straightforward products may cost $75,000 to $150,000 in evaluation facility fees plus internal staff time. EAL4 evaluations of complex products range from $200,000 to $500,000 in evaluation fees, with internal effort adding substantially more. Timeline from evaluation initiation to certification typically ranges from 8 to 24 months depending on product readiness, evaluation level, and evaluation facility capacity.
Internal resource commitments include security architects defining security requirements, developers remediating identified gaps, technical writers producing evaluation documentation, test engineers executing security test suites, and product managers coordinating evaluation activities. For organisations without existing security-focused development practices, preparation costs exceed evaluation costs.
These investments require executive commitment and multi-year planning. Organisations pursuing evaluation should budget appropriately and align certification timelines with product roadmaps and market entry strategies.
5) Future-proofing and staying relevant in 2026
Threat landscapes evolve continuously. Products certified in 2020 addressed 2020 threat models. Six years later, attack techniques have advanced and security expectations have shifted. Maintaining certification relevance requires periodic re-evaluation, continuous vulnerability management, and security update processes that don't invalidate certification. A standard is customarily revised every five years and ISO/IEC 15408-5:2022, Common Criteria's latest version, is currently at the stage of being revised, indicating ongoing evolution of evaluation criteria.
Emerging technologies present evaluation challenges. Cloud-native applications, containerised microservices, machine learning systems, and IoT devices operate differently than traditional software products ISO 15408 originally addressed. Protection Profiles for these technologies continue developing. Vendors in emerging technology spaces should engage with evaluation schemes and PP development communities to influence how evaluation adapts to new architectures.
Conclusion
ISO/IEC 15408 provides the international standard framework for IT product security evaluation, enabling vendors to demonstrate security capabilities through independent third-party assessment. For businesses selling to enterprise clients, government agencies, or regulated industries, ISO 15408 certification increasingly represents a procurement prerequisite rather than a competitive differentiator. Products without appropriate evaluation face disqualification from high-value contracts and skepticism from security-conscious buyers.
While evaluation requires substantial investment—typically $150,000 to $500,000 in direct costs plus significant internal effort—the market access, competitive positioning, and supply-chain trust benefits justify this investment for vendors targeting security-sensitive markets. The development discipline required for evaluation produces more secure products regardless of certification outcome, improving overall product quality and reducing vulnerability exposure.
For 2026 and beyond, vendors should assess ISO 15408 relevance based on target market requirements, competitive landscape, and regulatory environment. Products serving government, defence, critical infrastructure, financial services, or healthcare sectors face growing evaluation expectations. Beginning evaluation planning early—ideally during product design rather than after development—reduces costs and accelerates certification. Organisations treating ISO 15408 as strategic market access rather than compliance burden gain competitive advantages in enterprise procurement processes.
The standard continues evolving to address emerging technologies and threat landscapes. Vendors committing to ISO 15408 evaluation should plan for ongoing re-evaluation, continuous security improvement, and active engagement with Protection Profile development communities shaping future evaluation requirements.
FAQs
1) What is the purpose of ISO 15408?
ISO 15408 provides a consistent set of standards for the security functionality of IT systems as well as the assurance procedures used to evaluate these products during security assessments, giving buyers a measure to assess the security characteristics of IT products and enabling sellers to have their goods independently assessed and certified. The standard enables product vendors to demonstrate security capabilities through third-party evaluation and helps enterprise buyers compare products based on standardised security criteria rather than marketing claims.
2) What is the difference between ISO 27001 and ISO 15408?
ISO 27001 certifies an organisation's Information Security Management System—the processes, policies, and controls managing information security across the entire organisation. ISO 15408 certifies individual IT products or systems, evaluating specific security functions and development assurance. Vendors need ISO 15408 to validate product security; organisations need ISO 27001 to demonstrate systematic security management. Optimal security posture involves both: ISO 15408 for products you sell, ISO 27001 for how your organisation operates.
3) What is the cost of ISO 15408 certification?
Certification costs vary significantly based on product complexity, chosen Evaluation Assurance Level, and evaluation facility rates. EAL2 evaluations typically cost $75,000 to $150,000 in evaluation facility fees. EAL4 evaluations range from $200,000 to $500,000 in direct evaluation costs. Internal resource commitments—security architects, developers, technical writers, test engineers, and project managers—add substantial additional costs. Total investment including preparation, evaluation, and internal effort typically ranges from $200,000 to $800,000 for commercial products at EAL3 or EAL4. Timelines range from 8 to 24 months from evaluation initiation to certification.
4) What is the ISO standard for Common Criteria?
ISO/IEC 15408 is also known as Common Criteria for Information Technology Security Evaluation, and often abbreviated as Common Criteria or CC. The standard and Common Criteria are synonymous—different names for the same international framework for IT product security evaluation.



.svg)
.svg)
.svg)