What is ISO 27001?
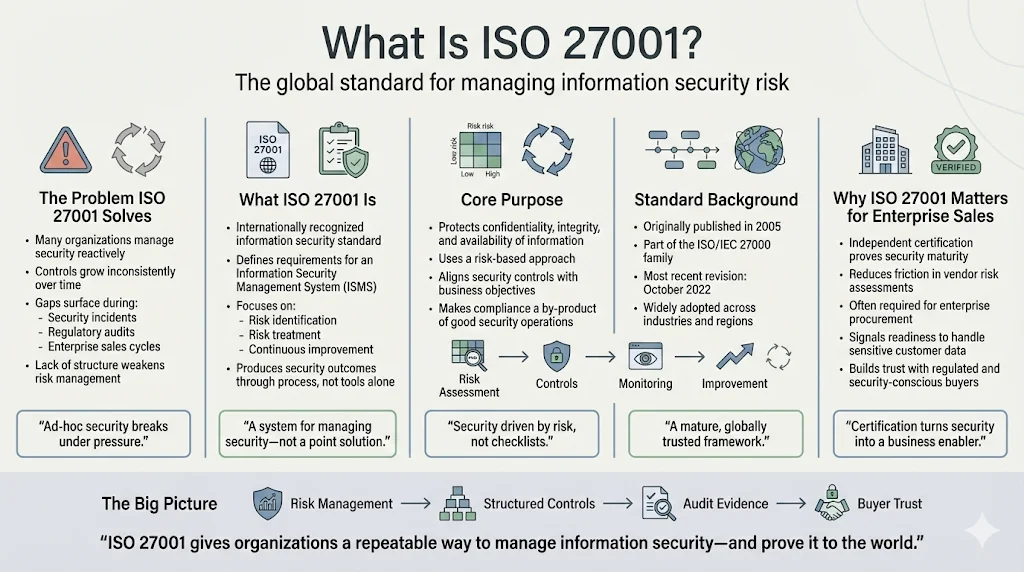
Most organizations struggle with information security management because they lack systematic frameworks—treating security as a reactive effort rather than a continuous discipline. This creates fundamental gaps in how organizations protect information assets, gaps that become apparent during security incidents, regulatory audits, or when attempting to close enterprise deals. ISO 27001 addresses this by providing a structured, internationally recognized framework for managing information security risks.
ISO/IEC 27001 is an international standard that specifies requirements for establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS). Published originally in 2005 and most recently revised in October 2022, the standard forms part of the broader ISO/IEC 27000-series governing information security and cybersecurity management. The core objective: protect information assets by establishing a systematic, risk-based security management framework that produces compliance as a natural outcome of proper security operations.
For organizations selling to enterprise clients, ISO 27001 certification represents more than a badge of compliance—it demonstrates third-party verified evidence that your security infrastructure meets international standards. Enterprise buyers increasingly require vendors to maintain ISO 27001 certification as a prerequisite for procurement consideration, particularly when vendor systems process sensitive customer data or integrate with corporate infrastructure.
How ISO 27001 Works — The ISMS Framework
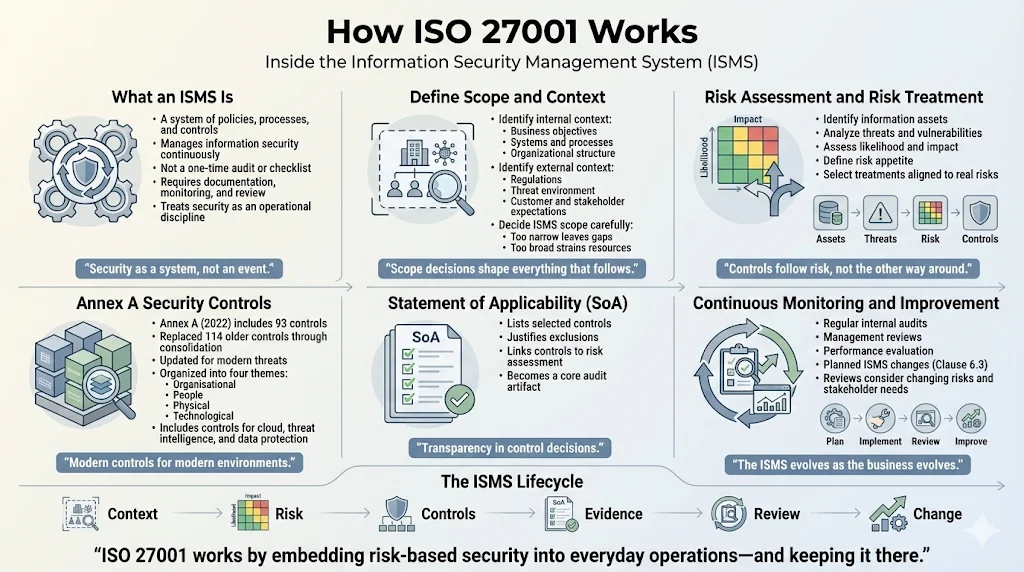
An Information Security Management System constitutes a set of policies, processes, controls, and organizational measures designed to manage security continuously rather than episodically. Unlike point-in-time security assessments, an ISMS requires ongoing monitoring, documentation, and refinement—treating security posture as an operational discipline requiring sustained attention and resources.
Defining Scope & Context
Implementation begins by identifying the "context of the organization"—both internal factors (business objectives, information systems, organizational structure) and external issues (regulatory landscape, threat environment, stakeholder expectations). Organizations must determine which business units, data assets, processes, and systems fall under ISMS scope. Scoping decisions carry strategic implications: too narrow and critical assets remain unprotected; too broad and resource requirements become prohibitive.
Risk Assessment & Treatment
ISO 27001 mandates a risk-based approach rather than prescriptive control implementation. Organizations must identify information assets, evaluate potential threats and vulnerabilities, assess risk likelihood and impact, then select appropriate controls to mitigate risks aligned with defined risk appetite. This methodology ensures security measures address actual organizational risks rather than generic checklists divorced from business context.
Security Controls from Annex A
The 2022 revision restructured Annex A from 114 controls to 93 controls—merging 24 controls for simplification, updating 58 controls, and introducing 11 new controls addressing emerging threats including cloud computing, threat intelligence, and data security. These controls are organized into four themes: Organisational, People, Physical, and Technological.
Organizations select applicable controls based on risk assessment findings, documenting justifications for control exclusions in a Statement of Applicability. This flexibility allows security programs tailored to organizational context while maintaining alignment with international standards.
Continuous Monitoring & Improvement
ISO 27001:2022 explicitly requires organizations to evaluate ISMS performance, not merely monitor it, with management reviews now mandating consideration of changing stakeholder needs and expectations. Regular internal audits, management reviews, and performance measurements ensure the ISMS remains effective as business conditions, threat landscapes, and regulatory requirements evolve. The 2022 revision introduced Clause 6.3, requiring that changes to the ISMS be carried out in a planned manner—formalizing change management as a core ISMS function.
Key Principles Underlying ISO 27001
The standard protects the "CIA triad"—Confidentiality, Integrity, and Availability—as foundational information security principles. Confidentiality ensures information access restricted to authorized individuals; Integrity guarantees data accuracy and completeness; Availability ensures authorized users can access information when needed.
Leadership commitment represents a non-negotiable requirement. Senior management must demonstrate involvement through policy approval, resource allocation, objective definition, and accountability assignment. Organizations treating ISO 27001 as an IT department initiative rather than an enterprise governance program inevitably fail to achieve meaningful security posture improvements—producing documentation that satisfies auditors on paper while leaving systems fundamentally vulnerable.
What ISO 27001 Certification Means for Businesses
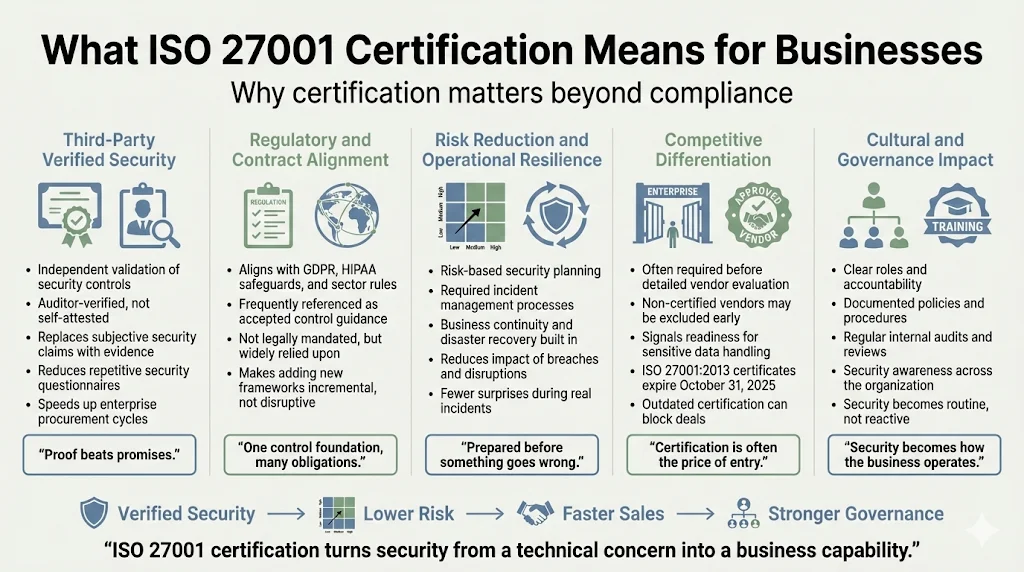
Third-Party Verified Security Posture
Certification provides independent attestation that your organization implements documented security controls meeting international standards. For enterprise sales cycles, certification eliminates lengthy security questionnaire processes and vendor risk assessments—replacing subjective security claims with objective, auditor-verified evidence. This proves particularly valuable when competing against non-certified vendors, where security assertions lack independent validation.
Regulatory & Contractual Alignment
ISO 27001 aligns with numerous data protection and privacy regulations globally, including GDPR, HIPAA technical safeguards, and various sector-specific requirements. While the standard itself carries no legal mandate, many regulations reference ISO 27001 controls as acceptable implementation guidance. Organizations maintaining ISO 27001 certification often find compliance with additional frameworks requires incremental rather than wholesale effort, as control foundations already exist.
Risk Mitigation & Operational Resilience
Structured risk assessment combined with appropriate control implementation reduces probability and impact of security incidents, data breaches, and operational disruptions. The standard mandates incident management processes, business continuity planning, and disaster recovery capabilities—ensuring organizations can maintain operations during adverse events rather than discovering capability gaps during actual incidents.
Competitive Differentiation
Enterprise procurement increasingly filters vendors based on security certifications before detailed evaluation begins. Organizations lacking ISO 27001 certification may find themselves excluded from consideration regardless of product capabilities or pricing. The transition deadline for organizations certified to ISO 27001:2013 is October 31, 2025—after which 2013-based certificates become invalid, potentially impacting vendor qualification status for enterprise clients requiring current certification.
Cultural & Governance Improvements
Implementation establishes structured policies, defined roles and responsibilities, regular audit cycles, and management review processes. These mechanisms embed security awareness throughout organizational culture rather than treating security as ad-hoc technical measures. Employee training requirements, access control procedures, and documented security policies create accountability frameworks extending beyond IT teams to encompass all personnel handling information assets.
The Implementation Process
Organizations pursuing ISO 27001 certification typically follow this sequence:
1. Define Scope & Understand Context (Clauses 4.1–4.3)
Determine which business units, data assets, processes, and systems require ISMS coverage. Document internal and external factors influencing information security, identify interested parties and their expectations, establish ISMS boundaries.
2. Obtain Leadership Commitment & Craft Security Policy (Clause 5)
Secure executive sponsorship, assign information security responsibilities, allocate resources. Develop high-level Information Security Policy demonstrating management commitment, defining objectives, establishing accountability. The policy requires top management approval, communication to relevant stakeholders, and regular review cycles.
3. Conduct Risk Assessment & Select Controls (Clause 6)
Identify information assets requiring protection, evaluate threats and vulnerabilities, assess risk likelihood and impact. Select relevant controls from Annex A based on risk treatment decisions, documenting selections and exclusions in Statement of Applicability.
4. Implement Controls (Clauses 7–8)
Deploy selected organizational, technical, physical, and procedural controls. This phase requires substantial effort: configuring technical controls (encryption, access management, network security), establishing physical security measures, implementing procedural controls (change management, incident response), developing documentation.
5. Document Processes & Establish Monitoring (Clause 9)
Create policies, procedures, work instructions supporting ISMS operations. Establish monitoring mechanisms, define performance metrics, schedule internal audits, conduct management reviews. Documentation must demonstrate control effectiveness over time—auditors require evidence spanning observation periods, not point-in-time snapshots.
6. Continuously Improve (Clause 10)
Implement corrective and preventive actions based on audit findings, monitoring results, and changing risk landscape. Update controls, policies, and procedures as business needs evolve, new threats emerge, or technologies change.
7. Undergo Certification Audit
Engage accredited third-party certification body to conduct Stage 1 (documentation review) and Stage 2 (implementation assessment) audits. Auditors verify ISMS meets ISO 27001 requirements, controls operate effectively, and the organization demonstrates commitment to continuous improvement. Certification requires surveillance audits annually and recertification every three years.
Challenges & Implementation Considerations
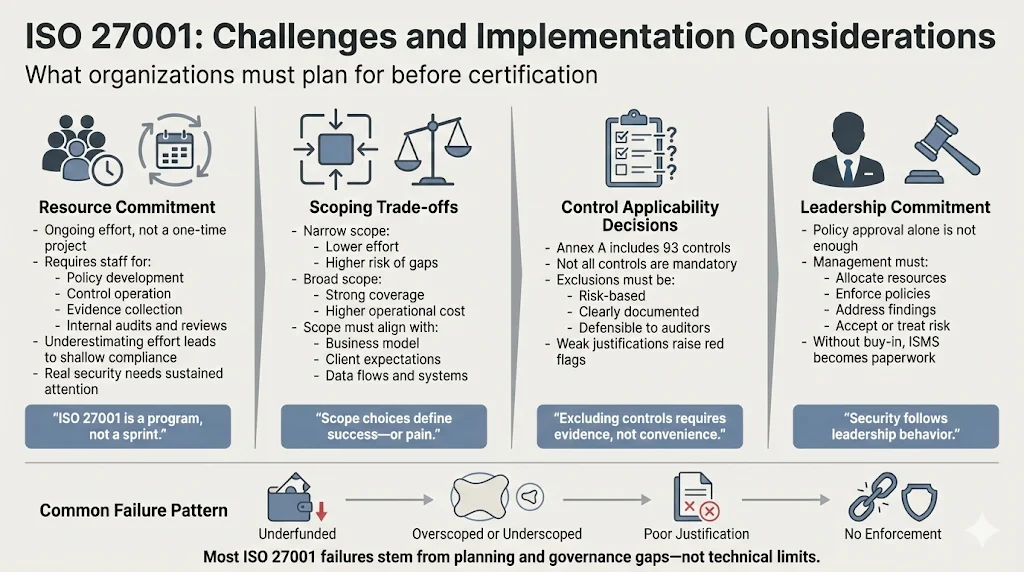
Resource Commitment Requirements
ISO 27001 implementation demands sustained resource investment—not a one-time project with defined endpoints. Organizations must allocate personnel for policy development, control implementation, evidence collection, internal audits, management reviews, and ongoing monitoring. Companies underestimating this commitment frequently achieve superficial compliance—documentation satisfying auditors without underlying security substance.
Scoping Trade-offs
Narrow scopes reduce implementation burden but may exclude critical assets or fail to satisfy enterprise client expectations. Broad scopes provide comprehensive coverage but multiply resource requirements and operational impacts. Organizations must balance business flexibility against compliance obligations—particularly when ISMS requirements conflict with existing workflows or architectural decisions.
Control Applicability Justification
While Annex A offers 93 controls, organizations need not implement every control—but must justify exclusions through documented risk assessment. Auditors scrutinize control exclusions carefully, particularly for controls addressing common threat vectors. Unjustified exclusions signal inadequate risk assessment or security posture gaps.
Management Buy-in Criticality
Without genuine leadership commitment extending beyond ceremonial policy signatures, ISMS implementation devolves into compliance theater—documentation exercises producing artifacts rather than security improvements. Effective implementation requires management willing to enforce policies, allocate resources, address non-conformances, and prioritize security alongside business objectives.
Impact on Enterprise Client Relationships
Enterprise organizations increasingly mandate vendor security certifications as contractual requirements, particularly for vendors processing customer data, integrating with corporate systems, or providing critical business services. ISO 27001 certification satisfies these requirements, streamlining procurement processes and reducing vendor risk assessment overhead.
Non-certified vendors face extended sales cycles, exhaustive security questionnaires, on-site security audits, and increased scrutiny—often finding procurement teams require security exception approvals at executive levels. These friction points disadvantage vendors competing against certified alternatives, regardless of actual security posture differences.
Certification also demonstrates capability to handle sensitive data appropriately, satisfy data protection and privacy expectations, and maintain security controls meeting regulatory standards relevant to enterprise operations. This proves essential when selling to regulated industries—financial services, healthcare, government—where vendor security deficiencies create compliance risks for buyer organizations.
Maintaining ISMS — Long-term Security Posture
Organizations treating ISO 27001 certification as a destination rather than a starting point inevitably experience security posture degradation. The standard explicitly requires continuous improvement—security controls must evolve as threats emerge, technologies advance, business models change, and regulatory landscapes shift.
Effective ISMS operations require embedding security awareness throughout organizational culture through regular training, clear communication of security responsibilities, and accountability for security policy adherence. Security cannot remain an IT department concern—it must extend to all personnel handling information assets, from customer-facing teams to finance departments to executive management.
The ISMS framework supports related security disciplines: business continuity management, data protection and privacy programs, vendor risk management, incident response capabilities, and regulatory compliance initiatives. Organizations leveraging ISMS foundations for these adjacent programs achieve operational efficiencies while strengthening overall security posture.
Frequently Asked Questions
1) What does having ISO 27001 mean?
ISO 27001 certification means your organization follows an internationally accepted standard for managing information security through a documented ISMS. It signals to clients, partners, and regulators that you systematically identify risks, implement appropriate controls, monitor security effectiveness, and continuously improve security posture. Certification provides third-party verified evidence that security claims withstand independent audit scrutiny—differentiating your organization from competitors making unsubstantiated security assertions.
2) What are the 6 key security areas under ISO 27001?
ISO 27001:2022 organizes Annex A controls into four themes—Organisational, People, Physical, and Technological—rather than six formal categories. However, practitioners commonly categorize security focus areas based on control domains: access control, cryptography, physical security, incident management, asset management, and business continuity. These groupings derive from risk assessment priorities and operational security disciplines rather than official ISO 27001 structure, but reflect how organizations typically organize ISMS implementation efforts.
3) What are the three principles of ISO 27001?
The three foundational principles are Confidentiality, Integrity, and Availability—collectively known as the CIA triad. Confidentiality ensures information access restricted to authorized individuals; Integrity guarantees information accuracy, completeness, and protection from unauthorized modification; Availability ensures authorized users can access information and systems when needed. All ISO 27001 controls ultimately protect one or more of these principles, with organizations prioritizing based on information asset criticality and business impact assessments.
4) Is ISO 27001 a legal requirement?
No. ISO 27001 represents a voluntary international standard, not a legal mandate. However, numerous regulations, laws, and contractual requirements reference ISO 27001 controls or certification as acceptable compliance demonstration. Many enterprise procurement contracts mandate vendor ISO 27001 certification as contractual obligation. Organizations in regulated industries often find ISO 27001 implementation satisfies portions of regulatory technical safeguard requirements, though certification alone rarely constitutes complete regulatory compliance.



.svg)
.svg)
.svg)