Most organizations pursue ISO 27001 certification with minimal understanding of how to translate requirements into operational reality. This gap creates implementation delays, compliance gaps, and security frameworks that satisfy auditors without protecting systems—a pattern that becomes apparent when client due diligence reveals immature processes or incidents expose control failures.
ISO/IEC 27003 is a guidance standard that supports the implementation of an Information Security Management System (ISMS) in accordance with ISO/IEC 27001. For organizations serving enterprise clients—where security questionnaires, vendor assessments, and contractual compliance requirements determine deal velocity—ISO 27003 provides the implementation roadmap that determines whether your ISMS functions as genuine security infrastructure or performative documentation.
This definition clarifies ISO 27003's scope, its relationship to ISO 27001 and ISO 27002, its practical application across ISMS implementation phases, and why enterprise-focused companies require structured guidance to build security governance that withstands rigorous client scrutiny.
What is ISO 27003?
ISO/IEC 27003:2017 provides explanation and guidance on ISO/IEC 27001:2013. Within the ISO/IEC 27000 series of information security standards, ISO 27003 serves a distinct function: it helps organizations understand and apply the requirements of ISO 27001, offering practical advice rather than prescriptive steps. While ISO 27001 is a certifiable standard, ISO 27003 is not; it serves purely as a reference document.
The standard's full designation—Information technology — Security techniques — Information security management systems — Guidance—signals its purpose. ISO 27001 defines what must be implemented; ISO 27003 explains how to approach implementation based on organizational context, industry, scale, and risk profile.
The latest version, ISO 27003:2017, aligns with the 2013 revision of ISO 27001 and presents guidance in a structure that matches the standard, making it easier to follow. This structural alignment allows practitioners to reference ISO 27003 clause-by-clause while implementing ISO 27001 requirements—reducing ambiguity during scope definition, risk assessment planning, control implementation, and documentation.
ISO 27003 is not prescriptive by design. Organizations of differing sizes, sectors, regulatory environments, and technical maturity levels adapt the guidance to their specific circumstances rather than following mandatory implementation steps.
Why ISO 27003 Matters — Purpose & Benefits
The standard is especially useful during the early stages of an ISO 27001 project. It helps define scope, understand context, identify stakeholders, and interpret control requirements clearly. These foundational steps determine whether an ISMS aligns with actual business operations or becomes a compliance artifact disconnected from security realities.
ISO 27003 addresses critical planning activities: establishing organizational context, defining ISMS boundaries, identifying interested parties and their security expectations, documenting requirements, and allocating resources. For enterprise-serving organizations, these planning steps directly affect vendor assessment outcomes—clients evaluate whether your ISMS scope meaningfully covers systems processing their data, whether risk assessments address threats relevant to their industry, and whether your security governance demonstrates executive accountability.
The guidance supports setting information security objectives, planning risk assessment methodologies, defining risk treatment approaches, assigning roles and responsibilities, and establishing policy frameworks. Although ISO 27003 is not mandatory, its structured recommendations help reduce ambiguity, improve project planning, and ensure consistency across the implementation.
Beyond initial implementation, ISO 27003 provides flexibility for organizations at different maturity stages. Startups building their first ISMS use it differently than established enterprises upgrading legacy security programs—both benefit from the same guidance framework adapted to their operational scale and complexity.
For companies competing in enterprise markets, ISO 27003 enables a systematic approach to security governance that translates into measurable business advantages: faster vendor assessment cycles, stronger responses to security questionnaires, documented evidence for contractual compliance requirements, and operational security posture that reduces incident likelihood and business continuity disruption.
How ISO 27003 Works — Core Structure & What It Covers
The sections of ISO/IEC 27003:2017 mirror those of the requirements standard, breaking down each section into three main parts – Required Activity, Explanation, and Guidance – as well as an area for any additional information that the standard user should know. Required Activity is the content from ISO/IEC 27001. This structure allows direct comparison between requirements and implementation approaches.
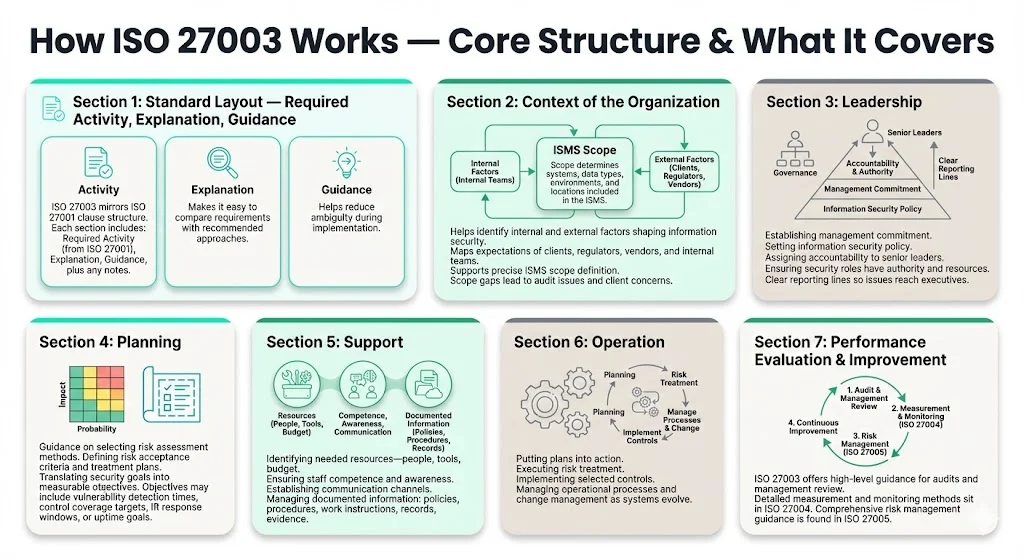
Context of the Organization
Section 4.2 of ISO/IEC 27003:2017, "Understanding the needs and expectations of interested parties", includes the following Required Activity: "The organization determines interested parties relevant to the ISMS and their requirements relevant to information security." The guidance helps identify internal and external factors affecting information security, map stakeholder expectations—including enterprise clients, regulators, third-party vendors, and internal departments—and define ISMS scope with precision.
Scope definition determines what systems, data types, business processes, physical locations, and organizational units fall within ISMS boundaries. For SaaS companies, this might include production infrastructure, customer data processing systems, development environments with access to production data, and third-party integrations. Scope ambiguity creates audit findings and client concerns when systems processing sensitive data fall outside documented ISMS boundaries.
Leadership
ISO 27003 addresses establishing top-management commitment, creating information security policy, and assigning accountability for security outcomes. Enterprise clients assess whether security governance includes executive-level ownership—CISOs or designated security leadership with authority and resources to implement controls, respond to incidents, and drive continuous improvement.
The guidance clarifies how to document policy frameworks that align with business objectives, communicate security expectations across organizational levels, and establish reporting structures that ensure security matters reach executive decision-makers.
Planning
Risk assessment and treatment planning represents the foundation of ISO 27001 compliance. ISO 27003 guides organizations in selecting risk assessment methodologies, defining risk acceptance criteria, establishing risk treatment options, and documenting risk management processes.
Setting information security objectives requires measurable targets aligned with business priorities. ISO 27003 helps translate abstract security goals into specific, auditable objectives—reducing mean time to detect vulnerabilities, achieving specific control coverage percentages, maintaining incident response timeframes, or meeting availability targets for critical systems.
Support
Resource allocation, competence requirements, awareness programs, communication mechanisms, and documented information management determine whether ISMS implementation succeeds operationally. ISO 27003 provides guidance on identifying necessary resources—personnel, technology, budget—and ensuring teams possess required skills for control implementation and maintenance.
Documentation requirements extend beyond policies to include procedures, work instructions, records, and evidence artifacts. The guidance addresses creating, updating, controlling, and retaining documented information that satisfies audit requirements while supporting operational security activities.
Operation
Implementing and controlling processes to meet security requirements translates planning into action. ISO 27003 guides executing risk treatment plans, implementing selected controls, managing operational procedures, and establishing change management processes that maintain security posture as infrastructure and business processes evolve.
Performance Evaluation & Improvement
The monitoring, measurement, analysis and evaluation criteria in 27001 are out of scope. ISO 27003 doesn't give detailed guidance on the information security risk management requirements either. While ISO 27003 addresses internal audit planning and management review processes, detailed performance measurement, metric development, and continuous monitoring methodologies are covered by companion standards—specifically ISO/IEC 27004 for measurement and ISO/IEC 27005 for comprehensive risk management.
ISO 27003 & Other Relevant Standards — How It Fits In
ISO 27003 functions within an ecosystem of interrelated information security standards. Understanding these relationships clarifies when to reference each standard during ISMS development.
ISO 27001: Requirements vs. Guidance
ISO 27001 establishes certifiable requirements for ISMS establishment, implementation, maintenance, and improvement. It defines mandatory elements—documented policies, risk assessment processes, control implementation, performance evaluation, continual improvement cycles. Organizations seek ISO 27001 certification to demonstrate compliance with these requirements.
ISO 27003 translates requirements into actionable implementation approaches. ISO 27001 requires "determining interested parties relevant to the ISMS," ISO 27003 explains how to identify those parties, what factors to consider, and how to document stakeholder requirements. The relationship is prescriptive requirements versus practical implementation guidance.
ISO 27002: Control Implementation vs. ISMS Structure
ISO 27002 lists the common control objectives and best practices to use as an implementation guide while choosing and implementing controls to gain information security. ISO 27003, on the other hand, explains the requirements of 27001 and offers guidance on implementing those.
ISO 27002 provides a catalog of organizational, technical, and physical security controls—access control mechanisms, cryptographic protections, incident response procedures, business continuity planning, supplier security. Organizations select applicable controls based on risk assessment outcomes, then implement them according to ISO 27002 guidance.
ISO 27003 addresses the management system structure surrounding those controls—how to establish governance, plan implementation projects, allocate resources, assign responsibilities, and integrate controls into operational processes. Organizations need both: ISO 27003 for ISMS architecture and project planning, ISO 27002 for control-level implementation.
ISO 27004 and ISO 27005: Monitoring and Risk Management
ISO 27004 - The standard guides the monitoring, measurement, analysis and evaluation of information technology security. When organizations require detailed performance metrics, measurement frameworks, or evaluation methodologies, ISO 27004 provides guidance beyond ISO 27003's scope.
ISO 27005 delivers comprehensive risk management guidance—risk identification techniques, risk analysis methodologies, risk evaluation criteria, and risk treatment strategies. Organizations conducting complex risk assessments or operating in high-risk environments reference ISO 27005 for detailed risk management processes that complement ISO 27003's implementation focus.
Real-World Importance of ISO 27003 for Companies Serving Enterprises
Enterprise procurement processes increasingly require documented security governance before contract execution. Vendor assessment questionnaires probe ISMS maturity, control implementation depth, risk management rigor, and continuous monitoring capabilities. Organizations without structured approaches to these areas face extended sales cycles, unfavorable contractual terms, or disqualification from competitive opportunities.
ISO 27003 enables systematic ISMS development aligned with enterprise client expectations. Rather than reactive security—implementing controls in response to client demands or audit findings—organizations following ISO 27003 guidance build proactive security frameworks that address common enterprise requirements before due diligence begins.
This approach produces transparent, auditable security posture. When enterprise clients request evidence of risk assessment processes, policy frameworks, control implementation, or governance accountability, organizations with ISO 27003-guided ISMS provide documentation demonstrating mature security practices rather than assembling ad-hoc responses.
Scalability represents another advantage. Organizations experiencing growth—expanding customer base, adding infrastructure, entering new markets, or acquiring companies—require security frameworks that scale without fundamental redesign. ISO 27003 guidance produces ISMS architectures that accommodate organizational evolution through defined change management, documented procedures, and adaptable governance structures.
Compliance requirements multiply as organizations serve clients across industries and jurisdictions—GDPR for European data, HIPAA for healthcare information, financial services regulations, sector-specific mandates. ISMS built following ISO 27003 provides the governance foundation supporting multiple compliance frameworks simultaneously, reducing duplicative effort and conflicting control implementations.
Risk mitigation extends beyond compliance to operational resilience. Organizations suffering security incidents face immediate costs—incident response, forensic investigation, remediation, notification—and long-term consequences including client attrition, reputational damage, regulatory scrutiny, and increased insurance premiums. ISMS developed with ISO 27003 guidance establishes preventive controls, detective mechanisms, and response capabilities that reduce incident likelihood and impact severity.
When & How to Use ISO 27003 — Practical Advice for Enterprise-Serving Companies
Organizations should reference ISO 27003 during initial ISMS planning—before control selection, before documentation creation, before resource allocation. Early-stage guidance prevents common implementation failures: scope definitions that exclude critical systems, risk assessments disconnected from business context, governance structures lacking executive accountability, or documentation unsuitable for audit purposes.
The standard proves particularly valuable when:
- Defining ISMS scope: Determining which business units, processes, systems, data classifications, and physical locations require inclusion based on stakeholder requirements, regulatory obligations, and risk exposure.
- Establishing governance: Creating policy frameworks, assigning security roles and responsibilities, ensuring top-management commitment, and building communication channels between security teams and executive leadership.
- Planning risk assessment: Selecting methodologies appropriate to organizational complexity, defining risk criteria aligned with business risk tolerance, establishing treatment approaches that balance security effectiveness with operational feasibility.
- Allocating resources: Identifying personnel requirements, technology investments, budget allocations, and timeline commitments necessary for successful implementation.
- Preparing for certification: Building documentation, establishing evidence collection processes, implementing internal audit programs, and addressing management review requirements before engaging external auditors.
- Organizations should combine ISO 27003 with complementary standards: ISO 27002 for control-level implementation guidance, ISO 27004 for measurement frameworks if detailed metrics are required, and ISO 27005 for comprehensive risk management in complex or high-risk environments.
Selective application is appropriate. Not every organization requires every element of ISO 27003 guidance. Smaller organizations with straightforward operations may simplify certain aspects; larger enterprises with complex regulatory environments may expand beyond basic guidance with additional frameworks and methodologies.
Limitations & What ISO 27003 Does Not Cover (By Design)
ISO 27003 is guidance, not certification criteria. Organizations implementing every ISO 27003 recommendation achieve structured ISMS implementation but do not automatically qualify for ISO 27001 certification—certification requires independent audit against ISO 27001 requirements.
The standard does not specify which security controls to implement. Control selection derives from risk assessment outcomes, regulatory requirements, contractual obligations, and business context. Although ISO/IEC 27003 is a basic guide, be aware it does not give detailed guidance on implementing all aspects of ISO 27001. Organizations requiring control-level implementation guidance reference ISO 27002.
Detailed monitoring, measurement, and performance evaluation methodologies fall outside ISO 27003 scope. Organizations developing comprehensive metric frameworks, measurement programs, or evaluation systems require ISO 27004. Similarly, complex risk management processes—advanced risk analysis techniques, quantitative risk assessment, or sophisticated risk modeling—require ISO 27005 rather than the foundational risk guidance in ISO 27003.
Technical implementation specifics are absent by design. ISO 27003 does not prescribe technology platforms, security tools, network architectures, or technical configurations. These decisions depend on organizational infrastructure, threat landscape, budget constraints, and technical capabilities—factors too variable for generic guidance.
Organizations at different maturity levels require different guidance depth. Startups implementing first-generation ISMS may find certain ISO 27003 elements unnecessarily complex for their scale; mature enterprises may need additional frameworks beyond ISO 27003 to address their operational complexity.
Example Scenario: SaaS Company Implementing ISMS for Enterprise Clients
A software-as-a-service platform serving mid-market customers pursues enterprise accounts where security requirements include formal ISMS, regular audits, and comprehensive control implementation. Current security consists of informal practices, undocumented policies, and reactive control deployment—insufficient for enterprise procurement processes.
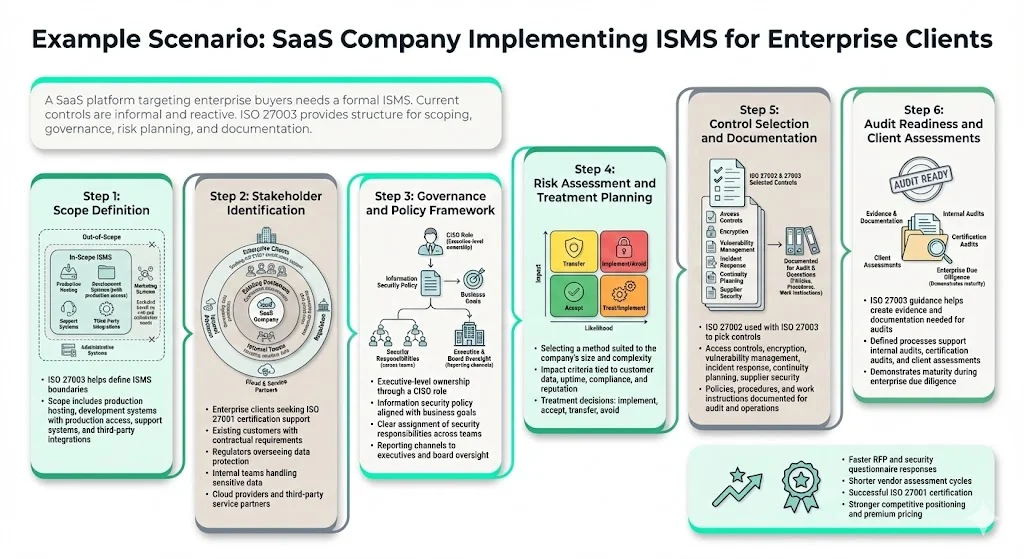
Step 1: Scope Definition Using ISO 27003 Guidance
The company references ISO 27003 to define ISMS scope covering production infrastructure hosting customer data, development environments with production access, customer support systems containing sensitive information, and third-party integrations processing customer data. Administrative systems and marketing infrastructure fall outside initial scope based on risk assessment and stakeholder requirements.
Step 2: Stakeholder Identification and Requirements
ISO 27003 guides identifying interested parties: enterprise prospects requiring ISO 27001 certification, existing customers with contractual security requirements, regulatory bodies overseeing data protection, employees handling sensitive information, cloud infrastructure providers, and third-party service providers with system access. Documentation captures each stakeholder's security expectations and compliance obligations.
Step 3: Governance and Policy Framework
Following ISO 27003 leadership guidance, the company establishes executive-level security accountability through a designated CISO role, creates information security policy aligned with business objectives, and assigns security responsibilities across engineering, operations, and support teams. Communication protocols ensure security matters reach executive decision-makers and board oversight.
Step 4: Risk Assessment and Treatment Planning
ISO 27003 helps select risk assessment methodology appropriate to organizational scale and technical complexity. The company defines risk criteria based on potential impact to customer data, service availability, regulatory compliance, and business reputation. Risk treatment planning produces documented decisions for control implementation, risk acceptance, risk transfer through insurance and contracts, and risk avoidance through scope limitations.
Step 5: Control Selection and Documentation
Using ISO 27002 alongside ISO 27003 guidance, the company selects controls addressing identified risks: access control mechanisms, encryption for data in transit and at rest, vulnerability management processes, incident response procedures, business continuity planning, and supplier security requirements. Policies, procedures, and work instructions document control implementation for operational use and audit evidence.
Step 6: Audit Readiness and Client Assessments
ISO 27003 guidance on documented information and evidence collection enables the company to prepare for internal audits, external certification audits, and client security assessments. Systematic documentation, defined processes, and governance accountability demonstrate security maturity that satisfies enterprise due diligence requirements.
Outcome: The structured approach enables faster proposal responses, stronger security questionnaire completion, reduced vendor assessment cycles, and successful ISO 27001 certification—differentiating the company in competitive enterprise pursuits and supporting premium pricing based on demonstrated security governance.
Conclusion
ISO 27003 provides the implementation roadmap that determines whether ISO 27001 certification represents genuine security maturity or performative compliance. Organizations serving enterprise clients require structured approaches to ISMS development—security governance that withstands rigorous due diligence, risk management aligned with business context, control implementation producing operational protection, and documentation supporting both audit requirements and security operations.
While ISO 27003 does not replace technical control implementation or substitute for certification, it establishes the foundation enabling credible ISMS development. Organizations attempting ISO 27001 certification without structured implementation guidance frequently encounter scope ambiguity, inadequate risk assessment, governance gaps, and documentation failures that delay certification and undermine security effectiveness.
Organizations should assess their scale, complexity, regulatory environment, and client requirements to determine how ISO 27003 guidance applies to their circumstances. Selective adaptation based on organizational context produces more effective results than rigid adherence to guidance designed for generic application across diverse industries and organizational types.
FAQs
Q1: What is the difference between ISO 27001 and ISO 27003?
ISO 27001 defines requirements for establishing, implementing, maintaining, and improving an ISMS—it specifies what must be done and serves as the certifiable standard. ISO 27003 is a guidance standard that supports the implementation of an ISMS in accordance with ISO 27001, helping organizations understand and apply the requirements of ISO 27001, offering practical advice rather than prescriptive steps. ISO 27003 explains how to approach implementation; ISO 27001 establishes mandatory requirements for certification.
Q2: What is the difference between ISO 27002 and ISO 27003?
ISO 27002 provides a code of practice containing security control objectives and implementation guidance—a catalog of organizational, technical, and physical controls addressing specific security domains like access control, cryptography, incident management, and business continuity. ISO 27003 guides ISMS structure, governance, planning, and management system implementation rather than individual control deployment. Organizations use ISO 27002 to select and implement controls identified through risk assessment; they use ISO 27003 to build the management system framework surrounding those controls.
Q3: What is the latest version of ISO 27003?
The latest version, ISO 27003:2017, aligns with the 2013 revision of ISO 27001. ISO/IEC 27003:2017 remains the current version as of 2025. Organizations implementing ISO 27001:2022—the most recent ISO 27001 revision—should note that while ISO 27003:2017 references the 2013 version, the core guidance principles remain applicable to current ISMS implementation projects.
Q4: What is the difference between ISO 27001 and ISO 27002?
ISO 27001 establishes ISMS requirements—what organizations must implement to achieve certification, including documented policies, risk assessment processes, control implementation, performance evaluation, and continual improvement. ISO 27002 provides detailed guidance on selecting and implementing specific security controls—technical safeguards, procedural protections, and organizational measures protecting information assets. ISO 27001 requires control implementation based on risk assessment; ISO 27002 explains how to implement those controls effectively across diverse security domains.



.svg)
.svg)
.svg)