Most organizations treat supply chain security as a collection of tactical measures—locks, cameras, insurance policies—rather than a systematic discipline integrated across operations. This approach creates vulnerabilities that become apparent when disruptions occur: stolen shipments, compromised goods, regulatory violations, or catastrophic delays that cascade through the entire supply chain. Global transportation has reached a point where organizations face sensitive security gaps, including threats from terrorism, smuggling, cyber-attacks, brand integrity protection, and product safety.
ISO 28000 provides the framework to address these risks through documented, auditable security management processes that span the entire supply chain—from raw material sourcing through final delivery.
What is ISO 28000?
ISO 28000 specifies requirements for a security management system, including aspects relevant to the supply chain, and is applicable to all types and sizes of organizations—commercial enterprises, government agencies, and non-profit organizations—which intend to establish, implement, maintain, and improve a security management system. The standard addresses security across transport, warehousing, storage, manufacturing, information management, financing, and all transit points where vulnerabilities can emerge.
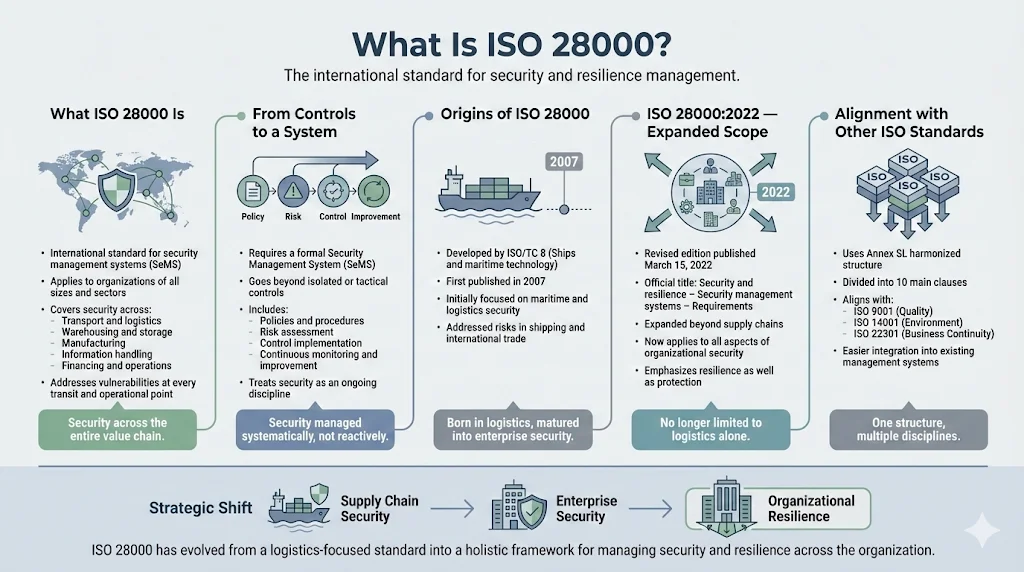
Unlike tactical security measures that address isolated risks, ISO 28000 requires organizations to implement a Security Management System (SeMS)—a structured approach encompassing policies, procedures, risk assessments, controls, and continuous monitoring across all supply chain activities.
History and Evolution
ISO 28000 was originally developed by ISO/TC 8 on "Ships and maritime technology" and published in 2007. That initial version focused specifically on supply chain security management within maritime and logistics contexts.
The revised version of ISO 28000 was published on March 15, 2022. This second edition—formally titled "Security and resilience – Security management systems – Requirements"—represents a fundamental expansion of scope. ISO 28000:2022 is divided into 10 main clauses and has adopted the harmonized structure and standardized text set out by Annex SL. This alignment with the common ISO management-system structure means organizations already certified to ISO 9001 (quality), ISO 14001 (environmental), or ISO 22301 (business continuity) can integrate security management into existing frameworks with substantially reduced effort.
The limitations of security within the supply chain were eliminated so that now it is clear that ISO 28000 can be used throughout all aspects of security of the organization, and can be applied beyond the supply chain to all aspects of the organization. This represents a strategic shift: ISO 28000 now addresses organizational security holistically, not merely logistics security.
What ISO 28000 Covers
ISO 28000 focuses on aspects critical to manage and assure security risks, including financing, manufacturing, information management and transportation, in-transit storage and warehousing of goods. The standard requires organizations to systematically assess security environments, identify vulnerabilities across dependencies and interdependencies, implement appropriate controls, and continuously monitor security performance.
Risk assessment and risk treatment form the core of the standard. Organizations must identify security-related risks—those that threaten people, assets, infrastructure, information, or operations—analyze their potential impact, evaluate their likelihood, and implement controls to prevent, mitigate, or respond to those risks. ISO 28000 specifies requirements for the organization to assess the security environment in which it operates including its supply chain, determine if adequate security measures are in place to effectively manage security-related risks, and align security processes and controls.
ISO 28000-2022 can easily be integrated with other major management system standards, like ISO 9001, which is an advantage for organizations looking to incorporate security aspects into other existing management systems. This integration capability reduces duplication of effort, enables unified audits, and positions security as a component of enterprise-wide risk management rather than an isolated function.
Official Title and Related Standards
The formal title of the current standard is "Security and resilience – Security management systems – Requirements" (ISO 28000:2022). This title reflects the broadened scope beyond supply chain to encompass organizational resilience.
ISO 28000 anchors a family of related standards that provide implementation guidance, audit requirements, and sector-specific applications. Key related standards include:
- ISO 28001: "Security management systems for the supply chain – Best practices for implementing supply chain security, assessments and plans – Requirements and guidance." This standard offers practical guidance on developing security plans, conducting security assessments, and implementing supply chain security practices. ISO 28001 is a guidance document, not a certification standard.
- ISO 28003: Specifies requirements for bodies providing audit and certification of supply chain security management systems—used by certification bodies to ensure consistent audit practices.
- ISO 28004 (Parts 1-4): Guidelines for implementing ISO 28000, with specific parts addressing medium and small seaport operations, small and medium businesses, and alignment with ISO 28001 objectives.
Organizations pursuing certification focus on ISO 28000 itself; the related standards provide implementation roadmaps and sector-specific interpretation.
Why Businesses Should Care: Impact on Enterprises
Strengthening Supply Chain and Logistics Security
Certified organizations have identified the security risks within their supply chain and implemented the appropriate measures in production, storage, distribution, and transportation of goods. This structured approach moves beyond reactive incident response to proactive vulnerability identification across every node in the supply chain.
Through documented risk assessments, organizations map threats at each stage: theft during transit, tampering in warehousing, data breaches in information systems, sabotage at manufacturing sites, delays at customs, or integrity failures at supplier facilities. Controls are then implemented based on risk severity—physical security measures, access controls, personnel vetting, information security protocols, emergency response plans, and supplier security requirements.
Organizations operating complex, multi-geography supply chains face compounded risks. ISO 28000 provides the systematic framework to manage security across disparate facilities, carriers, partners, and regulatory jurisdictions—reducing exposure to theft, sabotage, delays, damage, compliance violations, and operational interruptions.
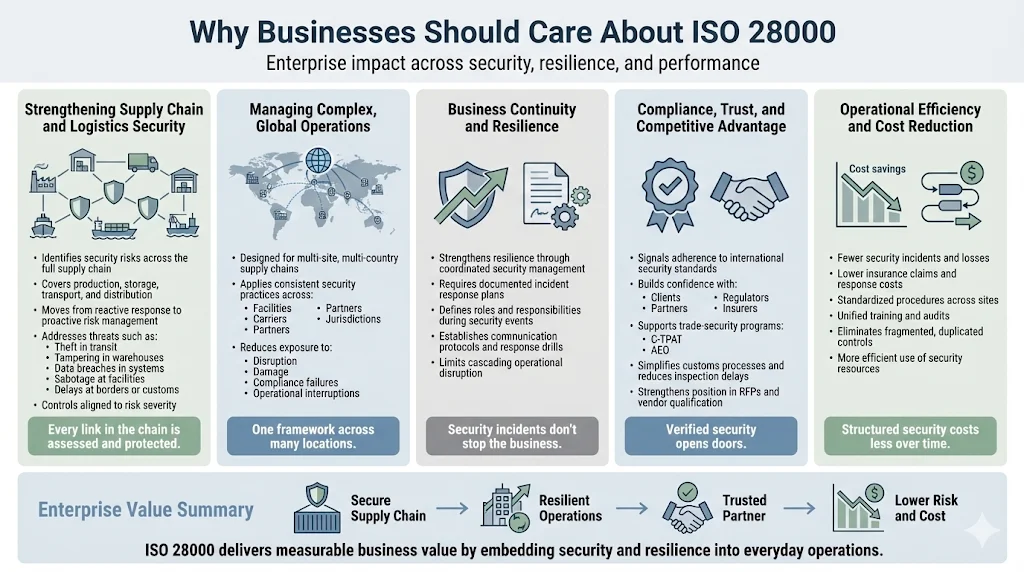
Business Continuity and Resilience
ISO 28000:2022 enhances the organization's resilience by an effective, coordinated and integrated application of its security management system. Security incidents don't merely result in immediate losses; they trigger cascading disruptions that can halt operations, breach customer commitments, damage reputation, and expose organizations to regulatory penalties.
The standard requires organizations to develop security plans that enable rapid response to incidents, minimizing impact on operations and business continuity. This includes defining roles and responsibilities during security events, establishing communication protocols, implementing incident response procedures, and conducting drills to verify readiness.
For companies serving enterprise clients—where contractual service level agreements, regulatory compliance obligations, and reputational considerations demand high reliability—documented security management and demonstrated resilience capabilities become competitive necessities rather than optional enhancements.
Compliance, Trust, and Competitive Advantage
ISO 28000:2022 certification signals a commitment to global security standards. For firms operating in high-risk zones, this can enhance credibility with international partners, insurers, and regulators. Certification demonstrates to clients, partners, auditors, and regulators that the organization has implemented formal, auditable security controls—not merely asserted security competence but proven it through independent third-party verification.
Cross-border regulations such as the U.S. Customs Trade Partnership Against Terrorism (C-TPAT) and the European Union's Authorised Economic Operator (AEO) programs are reinforcing demand for ISO-based SeMS frameworks as a mark of compliance and trustworthiness. Many international trade-security programs recognize ISO 28000 as evidence of robust supply chain security, simplifying customs procedures, expediting border crossings, and reducing inspection delays.
Organizations competing for enterprise contracts increasingly encounter security requirements in RFPs and vendor qualification processes. ISO 28000 certification provides documented proof of security capabilities, differentiation in competitive evaluations, and access to opportunities where certification is a prerequisite.
Operational Efficiency and Cost Savings
ISO 28000 delivers cost savings through reduction in security incidents and potential risk reduction in corporate insurance premiums. Systematic security management reduces incidents of theft, damage, delays, and losses—lowering direct costs, insurance claims, emergency response expenses, and reputational damage.
Standardized security practices streamline operations: consistent procedures across facilities, unified training programs, integrated risk management processes, and coordinated audits across multiple management systems. Organizations maintaining separate, fragmented security measures face duplication of effort, inconsistent practices, gaps in coverage, and inefficient resource allocation. ISO 28000 consolidates security management under a single framework, reducing overhead and enabling more effective resource deployment.
Who Should Comply with ISO 28000
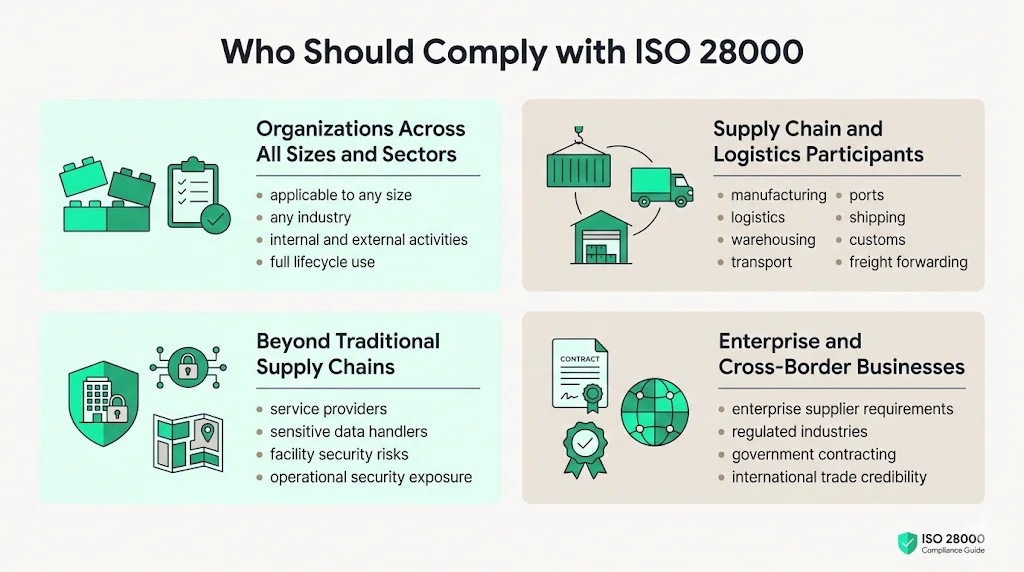
ISO 28000 is applicable to all types and sizes of organizations which intend to establish, implement, maintain and improve a security management system. It provides a holistic and common approach and is not industry or sector specific, and can be used throughout the life of the organization and applied to any activity, internal or external, at all levels.
The standard applies to any organization participating in supply chain activities: manufacturing, logistics, warehousing, transportation, storage, distribution, freight forwarding, port operations, shipping, customs brokerage. After the revision, ISO 28000:2022 can be applied beyond the supply chain to all aspects of the organization. This means service companies handling sensitive information, organizations managing facilities with security vulnerabilities, or businesses facing operational security risks can benefit from certification.
Organizations selling to enterprise clients—particularly those in regulated industries, government contracting, or international trade—encounter heightened security expectations. Enterprise buyers increasingly require suppliers and vendors to demonstrate formal security capabilities through certification, contractual security obligations, or vendor assessment programs. ISO 28000 provides the documented evidence enterprise clients demand.
Businesses operating across borders benefit significantly from certification. International shipping, cross-border logistics, customs clearance, and regulatory compliance become substantially more efficient when organizations demonstrate adherence to internationally recognized security standards. Certification adds credibility with foreign regulators, simplifies compliance verification, and accelerates trade-security program approvals.
Benefits of ISO 28000 Certification
Organizations pursuing certification realize multiple strategic and operational benefits:
Improved Supply Chain Security and Risk Mitigation: Systematic identification and treatment of vulnerabilities across all supply chain nodes—reducing theft, damage, delays, disruptions, and compliance violations through documented controls.
Enhanced Credibility with Enterprise Clients and Partners: Independent third-party certification demonstrates security competence to clients, partners, regulators, and auditors—building trust and enabling access to contracts requiring formal security standards.
Competitive Advantage in Vendor Selection: Certification differentiates organizations in competitive bid evaluations, RFP responses, and vendor qualification processes—particularly for enterprise clients with security requirements or regulatory obligations.
Efficiency Gains and Cost Savings: Fewer security incidents translate to reduced losses, lower insurance premiums, decreased emergency response costs, and avoided reputational damage. Standardized security practices streamline operations, reduce duplication, and enable integrated audits across multiple management systems.
Facilitated Compliance with Trade-Security Requirements: Certification simplifies compliance with international trade-security programs such as C-TPAT and AEO, expedites customs procedures, reduces border inspection delays, and demonstrates adherence to regulatory security obligations.
Integration with Broader Management Systems: Alignment with the ISO management-system structure (Annex SL) enables organizations to integrate security management with existing quality, environmental, and business continuity systems—creating unified enterprise governance frameworks and reducing management overhead.
Certification Process: How to Get ISO 28000 Certified
Achieving ISO 28000 certification requires systematic implementation of a Security Management System followed by independent third-party audit. The typical certification path includes:
1. Preliminary Assessment and Gap Analysis: Assess existing security practices, policies, procedures, and controls against ISO 28000 requirements. Identify gaps, deficiencies, and areas requiring development or enhancement. This assessment establishes the scope of implementation effort and resource requirements.
2. Implementation of Security Management System (SeMS): Develop and document the required elements:
- Security policy establishing organizational commitment and security objectives
- Risk assessment methodology and documented risk assessments across operations
- Security controls addressing identified risks (physical, procedural, technical)
- Security plans defining response procedures for incidents and emergencies
- Documentation of policies, procedures, responsibilities, and processes
- Training programs ensuring personnel competence in security practices
- Monitoring and measurement processes to track security performance
Implementation timeframes vary based on organizational complexity, existing security maturity, scope of operations, and resource allocation. Organizations with established management systems (ISO 9001, ISO 14001) can leverage existing structures, reducing implementation time.
3. Internal Audit and Corrective Actions: Conduct internal audits to verify SeMS implementation, test effectiveness of controls, identify non-conformities, and validate documentation completeness. Address findings through corrective actions, process adjustments, and documentation updates.
4. External Third-Party Audit and Certification: Engage an accredited certification body to perform formal audit. The audit typically occurs in two stages:
- Stage 1 (Documentation Review): Auditor reviews SeMS documentation, policies, procedures, and risk assessments to verify completeness and alignment with ISO 28000 requirements.
- Stage 2 (Implementation Audit): Auditor conducts on-site examination of operations, interviews personnel, observes processes, examines evidence, and verifies that documented systems are implemented and effective.
Successful audit results in certification issuance. Minor non-conformities may require corrective action before certification is granted.
5. Ongoing Review, Monitoring, and Improvement: Certification requires continuous maintenance. Organizations conduct surveillance audits (typically annually) and recertification audits (typically every three years) to verify continued compliance, system effectiveness, and continuous improvement. Security risks evolve—new threats emerge, operations change, regulations update—requiring ongoing system adaptation.
The revision adopted the PDCA management systems structure in expanding ISO 28000 to bring the elements of this standard in congruence with related standards such as ISO 9001, ISO 14001 and in particular ISO 22301. Organizations already using other ISO management systems can relatively smoothly integrate SeMS implementation with existing structures, reducing duplication and enabling coordinated audits.
Challenges and Considerations for Businesses
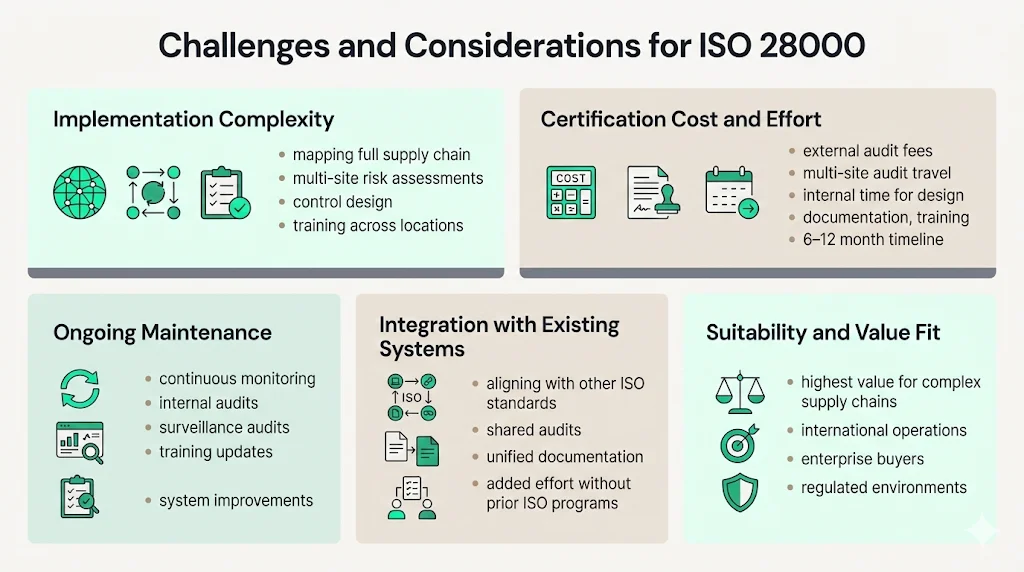
While ISO 28000 delivers substantial benefits, organizations should understand implementation realities:
Implementation Complexity: Establishing comprehensive SeMS across global supply chains requires significant effort—mapping all supply chain nodes, conducting thorough risk assessments, developing security controls for diverse operations, documenting procedures, training personnel across multiple locations, and implementing monitoring systems. Organizations with complex, multi-geography operations face proportionally greater implementation challenges.
Certification Cost and Effort: Certification expenses include both external audit fees and internal resource investment. External costs—certification body fees, audit expenses, travel costs for multi-site audits—vary based on organizational size, scope, and geographic dispersion. Internal costs—personnel time for gap analysis, system design, documentation, training, internal audits, and corrective actions—often exceed external expenses. Organizations should budget 6-12 months for initial implementation depending on complexity and existing security maturity.
Ongoing Maintenance Requirements: Developing and maintaining a security management system requires time, expertise, and financial investment. Certification is not a one-time achievement but requires continuous monitoring, periodic audits, system updates as risks evolve, and sustained management attention. Organizations must allocate ongoing resources for internal audits, surveillance audits, corrective actions, training updates, and system improvements.
Integration with Existing Systems: Although ISO 28000 aligns with other ISO standards, integration requires deliberate effort—mapping security processes to existing management structures, coordinating audit schedules, unifying documentation systems, and training personnel on integrated approaches. Organizations without existing ISO certifications face greater implementation effort.
Suitability Assessment: Organizations with simple logistics operations, low security risk profiles, minimal regulatory requirements, or limited enterprise client exposure may find the certification cost and effort disproportionate to benefits. Certification delivers maximum value to organizations with complex supply chains, international operations, enterprise clients requiring security standards, or regulatory obligations demanding documented security management.
Practical Steps for Enterprise-Focused Sellers Considering ISO 28000
Organizations evaluating ISO 28000 certification should follow a structured approach:
1. Map Your Entire Supply Chain: Document all nodes—manufacturing facilities, warehouses, storage locations, transport routes, distribution centers, packaging operations, information systems, financial flows—where security vulnerabilities might exist. Include both internal operations and external partners, suppliers, carriers, and service providers.
2. Conduct Preliminary Risk Assessment: Identify where threats exist—theft, tampering, sabotage, data breaches, access violations, delays, compliance failures—and evaluate their potential impact and likelihood. Prioritize risks based on severity and probability.
3. Define Certification Scope: Determine which operations, geographies, and activities will be included in certification. Organizations can pursue full supply chain certification, partial scope (e.g., logistics operations only), or phased implementation starting with high-priority operations.
4. Budget for Implementation: Allocate resources for internal effort (gap analysis, system development, documentation, training, internal audits) and external costs (certification body fees, consultant support if needed, audit expenses). Plan for 6-12 months initial implementation depending on complexity.
5. Select Accredited Certification Body: Engage a certification body accredited to audit ISO 28000 and experienced in supply chain security. Request proposals, compare audit approaches, verify accreditation, and confirm sector experience relevant to your operations.
6. Prepare for Implementation: Assign responsibility for SeMS development, allocate personnel resources, establish project timelines, develop documentation frameworks, and plan training programs. Organizations with existing ISO management systems should leverage those structures for integration.
7. Plan Ongoing Maintenance: Establish processes for continuous monitoring, periodic internal audits, management review meetings, corrective action tracking, and system improvement. Budget for annual surveillance audits and triennial recertification audits.
8. Communicate Certification to Stakeholders: Once certified, leverage certification in client communications, marketing materials, RFP responses, vendor qualification submissions, and contract negotiations. Use certification as proof of security capabilities and competitive differentiator.
Conclusion
Supply chain security risks are neither hypothetical nor manageable through tactical measures alone. Organizations face documented, evolving threats—theft, sabotage, cyber-attacks, disruptions, compliance violations—that demand systematic, auditable security management frameworks. ISO 28000 provides that framework: structured risk assessment, documented controls, continuous monitoring, and independent verification of security capabilities.
ISO 28000:2022 is a certifiable standard, and in 2016, the countries with the highest number of certificates were India (425), Japan (299), Spain (231), US (223) and UK (197). Adoption continues expanding across industries recognizing that supply chain security directly impacts operational continuity, regulatory compliance, customer trust, and competitive positioning.
ISO 28000 isn't exclusively for logistics firms. Any organization handling goods, managing storage, coordinating transport, or processing information flows within supply chains can benefit. For companies targeting enterprise clients—where security standards, compliance obligations, and vendor qualification requirements are increasingly stringent—certification transitions from optional enhancement to strategic necessity.
Decision-makers at enterprise-facing companies should evaluate ISO 28000 not merely as compliance documentation but as strategic infrastructure: it builds trust with clients, reduces operational risk, facilitates international trade, enables regulatory compliance, and supports long-term stability in an environment where supply chain vulnerabilities represent existential threats.
Common Questions
1) What is the ISO 28000 standard?
ISO 28000:2022 Security and resilience — Security management systems — Requirements specify requirements for a security management system, including aspects relevant to the supply chain. It provides a framework for organizations to systematically manage security risks across all operations, not limited to supply chain activities.
2) What is the title of ISO 28000?
The current version (2022) is formally titled "Security and resilience – Security management systems – Requirements." This reflects the expanded scope beyond the supply chain to encompass broader organizational security and resilience.
3) What is the cost of ISO 28000 certification?
ISO does not publish fixed certification costs. Expenses depend on organizational size, supply chain complexity, certification scope (geographic coverage, number of facilities, operational diversity), existing security maturity, chosen certification body, and geographic region. Costs include both external audit fees and internal resource investment for gap analysis, system implementation, documentation, training, and internal audits. Organizations should request quotes from accredited certification bodies after preliminary assessment to receive accurate cost estimates based on specific circumstances.
4) What is ISO 28001 certification?
ISO 28001 is titled "Security management systems for the supply chain – Best practices for implementing supply chain security, assessments and plans – Requirements and guidance." It provides guidance on implementing supply chain security practices, developing security plans, and conducting security assessments. ISO 28001 is a guidance standard, not a certification standard—organizations certify to ISO 28000, using ISO 28001 as implementation guidance.
5) How does ISO 28000 improve supply chain security?
By establishing processes for risk assessment, organizations can effectively identify, analyze, and evaluate security-related risks, then implement controls and strategies to prevent security-related risks or mitigate and treat those that cannot be prevented. The standard requires systematic analysis across transport, storage, warehousing, information systems, manufacturing, and transit operations—implementing physical, procedural, and managerial controls to mitigate threats including theft, damage, sabotage, and disruptions. Continuous monitoring, performance evaluation, and improvement processes ensure the system adapts as risks evolve.
6) Who needs to comply with ISO 28000?
Any organization participating in supply chain activities—manufacturing, warehousing, logistics, transport, storage, distribution—or handling goods, products, materials, or services involving storage or transit. The 2022 revision expanded applicability beyond traditional supply chain players to any organization seeking to formalize security management across operations. Organizations targeting enterprise clients often face security requirements in contracts, vendor qualifications, or regulatory compliance obligations where ISO 28000 certification provides required evidence.
7) What are the benefits of ISO 28000 certification?
Benefits include improved supply chain and organizational security through systematic risk management; enhanced trust, credibility, and reputation with clients, partners, and regulators; competitive advantage in enterprise procurement and vendor selection processes; operational efficiency and cost savings from reduced incidents, streamlined processes, and potential insurance premium reductions; facilitated compliance with international trade-security programs such as C-TPAT and AEO, enabling smoother customs procedures; and ability to integrate security management with existing quality, environmental, and business continuity systems for unified enterprise governance.
8) How do I get ISO 28000 certified?
Begin with gap analysis comparing current security practices against ISO 28000 requirements. Implement a Security Management System including security policies, risk assessments, documented controls, security plans, procedures, training, and monitoring processes. Conduct internal audits to verify system effectiveness and address non-conformities. Engage an accredited certification body to perform formal audit—typically including Stage 1 documentation review and Stage 2 implementation audit. Upon successful audit, certification is issued. Maintain compliance through surveillance audits (typically annual) and recertification audits (typically every three years), continuously monitoring and improving security practices as risks evolve.



.svg)
.svg)
.svg)