Most organizations implement security testing, vulnerability scanning, and penetration testing programs—yet lack a structured process for what happens when external researchers discover vulnerabilities in their products. This creates a fundamental gap between defensive security operations and external vulnerability reporting—a gap that becomes apparent when security researchers contact legal departments instead of security teams, when vulnerabilities are disclosed publicly before vendors can remediate, or when enterprises discover their vendors have no documented process for handling security reports.
The goal of vulnerability disclosure is to reduce the risk associated with exploiting vulnerabilities. Organizations that sell software, hardware, or online services to enterprise clients need a standardized approach to receiving, processing, and disclosing vulnerability information. ISO/IEC 29147 provides the international standard framework for establishing this capability.
What is ISO 29147?
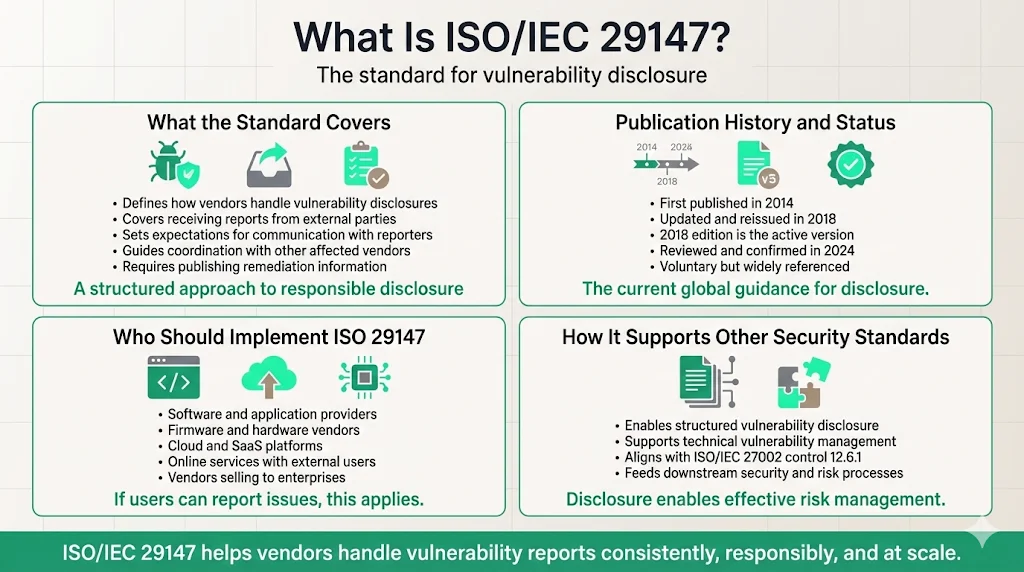
ISO/IEC 29147:2018 provides requirements and recommendations to vendors on the disclosure of vulnerabilities in products and services. The standard establishes protocols for vendors to receive vulnerability reports from external parties, communicate with reporters, coordinate with other affected vendors, and publish remediation information to users.
ISO/IEC 29147 was initially published in 2014. It was withdrawn and updated in 2018. The 2018 edition represents the current version, reviewed and confirmed in 2024. This document is applicable to vendors who choose to practice vulnerability disclosure to reduce risk to users of vendors' products and services.
The standard applies to organizations that develop or provide software applications, firmware, hardware systems, cloud services, and online platforms. Any organization whose products or services are exposed to external users—particularly those selling to enterprise customers—should implement ISO 29147-aligned processes. Vulnerability disclosure enables users to perform technical vulnerability management as specified in ISO/IEC 27002:2013, 12.6.1.
Key Concepts and Components of ISO 29147
ISO/IEC 29147 covers three primary areas: receiving vulnerability reports, publishing vulnerability advisories, and establishing a vulnerability disclosure policy.
Vulnerability Disclosure Process: The standard requires organizations to establish documented procedures for receiving external vulnerability reports. This includes designating a dedicated contact capable of monitoring, tracking, and acknowledging reports. Organizations must provide clear reporting channels—typically a security contact email address, web form, or dedicated portal—and commit to acknowledging reports within defined timeframes.
Guidelines for Reporting Security Vulnerabilities: ISO 29147 specifies what information reporters should provide (affected product versions, reproduction steps, technical details, potential impact) and what vendors must communicate in response (acknowledgment, assessment status, remediation timeline, disclosure coordination). The standard emphasizes ongoing communication between vendors and reporters throughout the vulnerability lifecycle.
Information Disclosure and Remediation Information: Once vulnerabilities are verified and remediated, the standard provides guidelines on disclosing vulnerability remediation information through security advisories. These advisories should include affected product versions, vulnerability descriptions, impact assessments, remediation steps, and credit to reporters (where appropriate).
Confidentiality and Safe-Harbour Considerations: The standard addresses the need for confidentiality during vulnerability assessment and remediation. Organizations should establish safe-harbour provisions that protect security researchers who report vulnerabilities in good faith from legal action. This reduces researcher hesitancy and encourages responsible disclosure rather than public disclosure or exploitation.
Coordination and Communication Channels: Coordinated vulnerability disclosure is especially important when multiple vendors are affected. The standard provides guidance on coordinating with other vendors when vulnerabilities exist in shared components, libraries, or dependencies. Organizations must establish internal communication workflows connecting security teams, engineering, legal, customer support, and executive leadership.
How ISO 29147 Fits Into Broader Security Practices
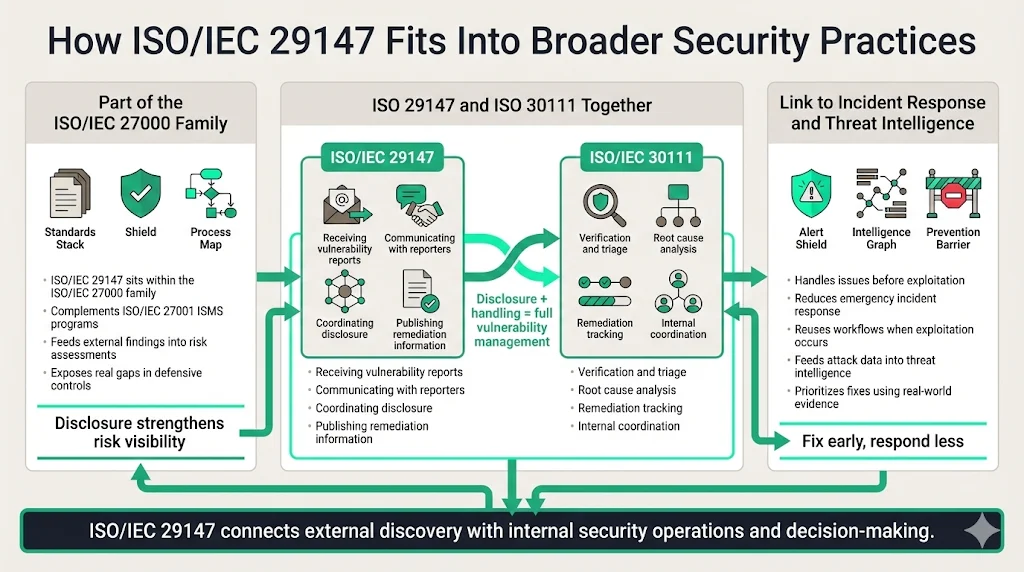
ISO/IEC 29147 operates within the broader ISO/IEC 27000 family of information security management standards. Organizations implementing ISO/IEC 27001—the certifiable standard for Information Security Management Systems (ISMS)—should integrate vulnerability disclosure processes into their overall security management framework. Vulnerability disclosure supports risk assessment procedures by providing external validation of security posture and identifying gaps in defensive controls.
Other related activities that take place between receiving and disclosing vulnerability reports are described in ISO/IEC 30111. While ISO 29147 focuses on disclosure—receiving reports and publishing remediation information—ISO 30111 addresses vulnerability handling processes: verification, triage, remediation tracking, and internal coordination. Organizations should implement both standards in tandem to create end-to-end vulnerability management capabilities.
Vulnerability disclosure integrates with incident response planning by establishing protocols for handling security issues before they become active incidents. When vulnerabilities are reported and remediated proactively, organizations avoid the resource-intensive emergency response required when vulnerabilities are exploited in production environments. The disclosure process feeds threat intelligence workflows by providing data on attack vectors, exploitation techniques, and affected system components—enabling security teams to prioritize defensive investments based on actual vulnerability reports rather than theoretical risk assessments.
Why Companies (Especially Those Selling to Enterprises) Should Care About ISO 29147
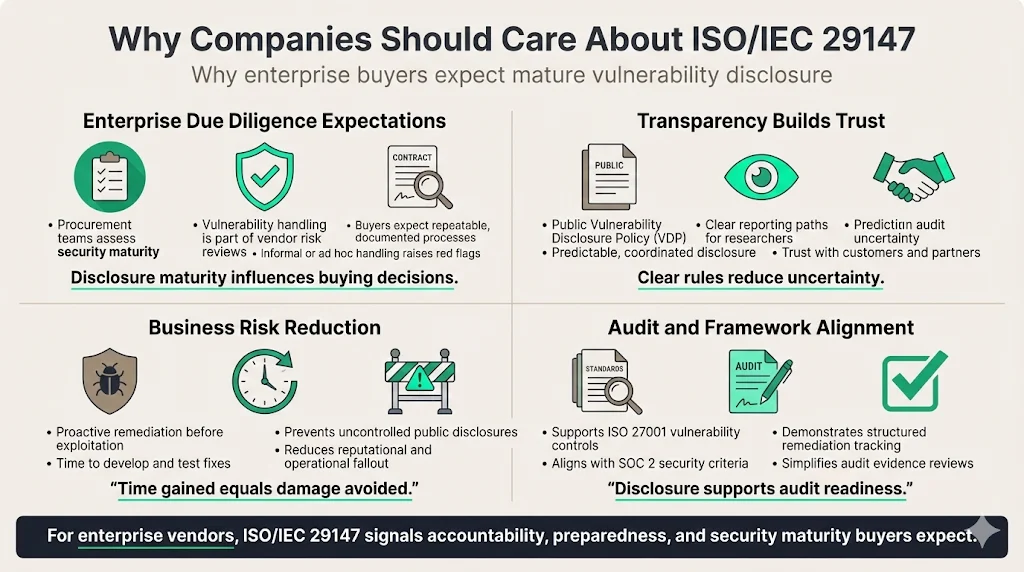
Enterprise procurement teams evaluate vendor security maturity during due diligence. Organizations that publish vulnerability disclosure policies and demonstrate ISO 29147-aligned processes signal operational maturity and accountability. Enterprises want assurance that when security researchers discover vulnerabilities in vendor products, those vulnerabilities will be handled systematically—not ignored, mishandled, or disclosed prematurely.
Publishing a public Vulnerability Disclosure Policy (VDP) demonstrates transparency and builds trust with customers, partners, and the security research community. Organizations without clear disclosure processes risk having vulnerabilities disclosed publicly without coordination, creating security exposure for all customers simultaneously. Vendors with established processes can coordinate disclosure timing, prepare patches, notify affected customers, and publish advisories—minimizing business impact and maintaining customer confidence.
Structured vulnerability disclosure reduces business risk by enabling proactive remediation before exploitation. When security researchers report vulnerabilities through established channels rather than selling them on underground markets or disclosing them publicly, vendors gain the time required to develop, test, and deploy fixes. This approach prevents the reputational damage, regulatory scrutiny, and customer churn that accompany public security incidents.
ISO 29147-aligned processes support compliance requirements within ISO 27001, SOC 2, and other frameworks that mandate vulnerability management controls. Auditors evaluate whether organizations have documented procedures for receiving vulnerability reports, tracking remediation, and communicating with stakeholders—all requirements addressed by ISO 29147.
Practical Steps for Implementing ISO 29147 in Your Organization
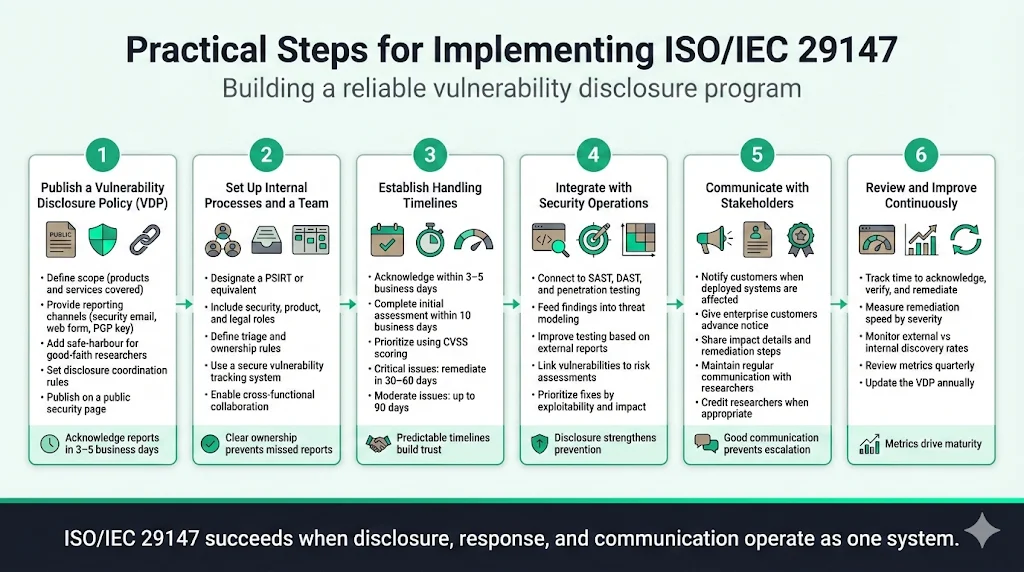
1) Creating a Public Vulnerability Disclosure Policy: Establish a VDP that defines scope (which products and services are covered), reporting channels (security email address, web form, PGP key for encrypted communication), safe-harbour provisions (commitment not to pursue legal action against good-faith reporters), and disclosure coordination commitments (acknowledgment within 3-5 business days, regular status updates, coordinated public disclosure timing). Publish this policy on a dedicated security page accessible from your website footer and product documentation.
2) Setting Up Internal Processes and a Team: Designate a Product Security Incident Response Team (PSIRT) or equivalent function responsible for receiving, triaging, and tracking vulnerability reports. This team should include security engineers with expertise in your technology stack, product managers who understand system architecture, and legal counsel familiar with responsible disclosure practices. Implement a vulnerability tracking system that maintains confidentiality while enabling cross-functional collaboration.
3) Establishing Timelines: Define service-level commitments for vulnerability handling: acknowledge reports within 3-5 business days, complete initial assessment within 10 business days, communicate remediation timelines based on severity scoring (CVSS), and coordinate disclosure timing with reporters. Critical vulnerabilities (CVSS 9.0-10.0) typically require remediation within 30-60 days; moderate vulnerabilities may extend to 90 days.
4) Integration with Existing Security Operations: Connect vulnerability disclosure processes with security testing standards (SAST, DAST, penetration testing), risk assessment procedures (threat modeling, attack surface analysis), and incident response planning. When external reports identify vulnerabilities missed by internal testing, use that data to improve testing coverage. Feed vulnerability data into risk assessments to prioritize remediation based on exploitability and business impact.
5) Communicating with Stakeholders: Establish communication protocols for notifying customers when vulnerabilities affect deployed systems. Enterprise customers expect advance notification before public disclosure, technical details about impact and exploitation requirements, and clear remediation guidance (patches, configuration changes, compensating controls). Maintain ongoing communication with security researchers throughout the handling process—researchers who receive acknowledgment, status updates, and credit are more likely to report future vulnerabilities responsibly.
6) Continuous Review and Improvement: Track metrics including time to acknowledge reports, time to verify vulnerabilities, time to remediate by severity level, and percentage of vulnerabilities reported externally versus discovered internally. Monitor these metrics quarterly to identify process bottlenecks and capacity constraints. Review disclosure policy effectiveness annually based on reporter feedback and industry best practices evolution.
Common Challenges and How to Address Them
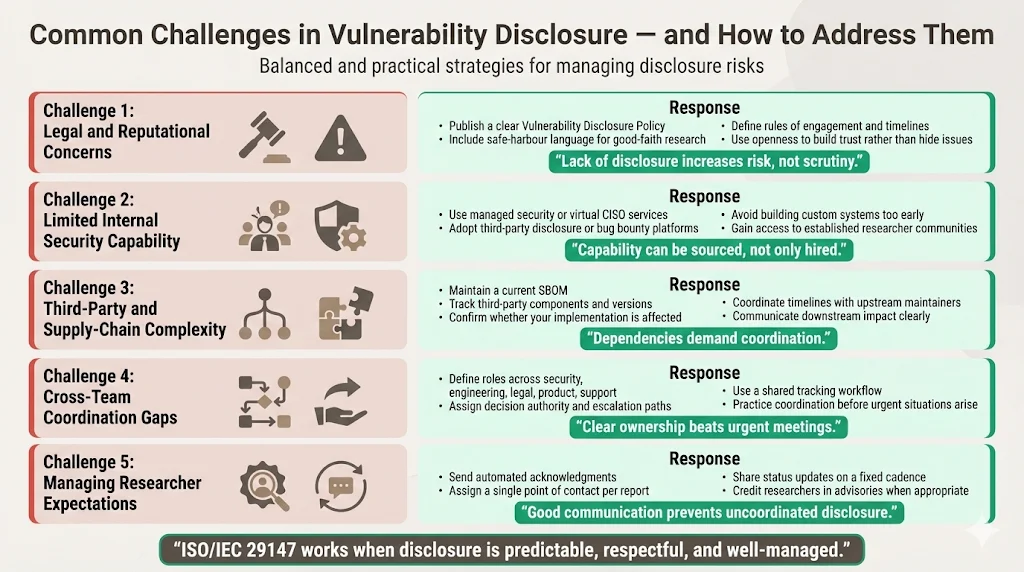
1) Legal and Reputational Concerns: Organizations often fear that publishing a vulnerability disclosure policy invites security scrutiny or creates legal liability. The opposite is true—organizations without disclosure policies still have vulnerabilities, but lack mechanisms for learning about them before exploitation. Safe-harbour provisions protect both researchers and organizations by establishing clear rules of engagement. Transparent disclosure builds customer confidence by demonstrating accountability rather than concealing security issues.
2) Lack of Internal Capability: Many organizations lack dedicated security expertise, particularly smaller vendors or those in industries where security has not historically been prioritized. Consider implementing managed security services that provide dedicated CISO expertise and security operations capability. Alternatively, engage third-party bug bounty platforms that provide ISO 29147-compliant vulnerability disclosure infrastructure, eliminating the need to build internal systems while providing access to security researcher communities.
3) Complexity in Third-Party and Supply-Chain Software: Most software incorporates third-party libraries, frameworks, and dependencies. When vulnerabilities exist in these components, vendors must coordinate disclosure with upstream maintainers while protecting downstream users. Maintain a software bill of materials (SBOM) documenting all third-party components. When vulnerabilities are reported in dependencies, verify whether your implementation is affected, coordinate with upstream vendors on remediation timing, and communicate impact to your customers.
4) Coordination Between Multiple Teams: Vulnerability handling requires collaboration between engineering (assessment and remediation), security (risk scoring and testing), legal (safe-harbour and disclosure timing), product management (prioritization and release planning), and customer support (communication and deployment assistance). Establish a documented workflow with clear role definitions and decision-making authority to prevent confusion during time-sensitive vulnerability handling.
5) Managing External Researcher Expectations: Security researchers expect acknowledgment, transparency about assessment progress, and credit for their contributions. Organizations that fail to communicate regularly or ignore reports risk having vulnerabilities disclosed publicly without coordination. Implement automated acknowledgment systems, assign a single point of contact for each report, provide status updates at defined intervals (weekly for critical issues, biweekly for moderate severity), and publish researcher credits in security advisories.
How ISO 29147 Complements Security Testing Standards, Threat Intelligence, and Incident Response
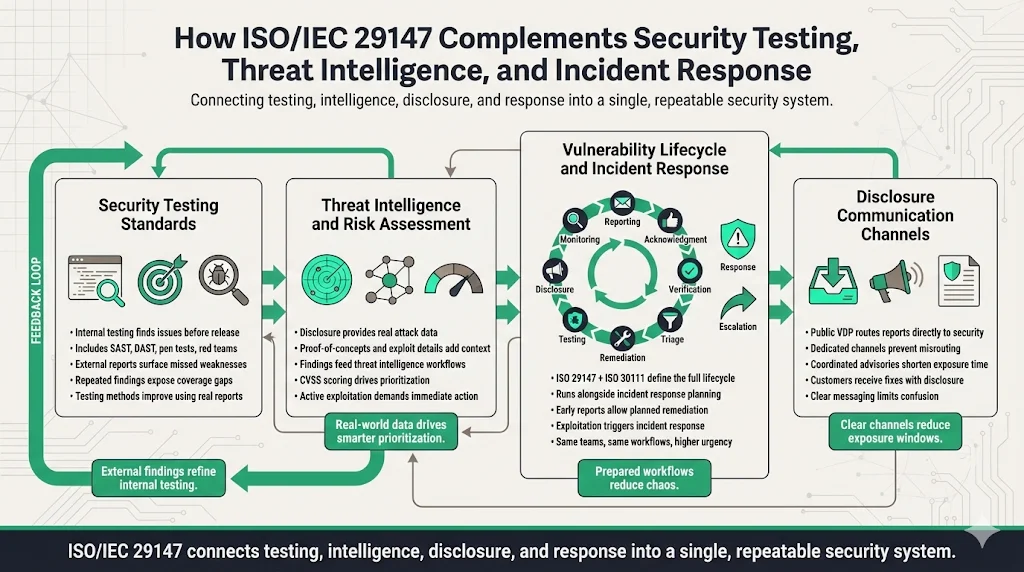
1) Security Testing Standards: Internal security testing—static code analysis, dynamic application security testing, penetration testing, red team exercises—identifies vulnerabilities before deployment. ISO 29147 addresses what happens when external parties discover vulnerabilities despite internal testing. Organizations should use external vulnerability reports as feedback on testing coverage gaps. When researchers report vulnerability classes consistently missed by internal testing (authentication bypass, business logic flaws, API security issues), adjust testing methodologies to improve coverage.
2) Threat Intelligence Protocols and Risk Assessment Procedures: Vulnerability disclosure feeds threat intelligence by providing real-world data about attack vectors targeting your products. When researchers report exploitation techniques, proof-of-concept code, or evidence of active exploitation attempts, integrate that intelligence into risk assessment procedures. Use CVSS-based risk scoring to prioritize remediation—critical vulnerabilities with known exploitation or public proof-of-concept require immediate action; theoretical vulnerabilities without exploitation evidence can follow standard release cycles.
3) Security Vulnerability Lifecycle and Incident Response Planning: ISO 29147 and ISO 30111 together define the complete vulnerability lifecycle: discovery → reporting → acknowledgment → verification → triage → remediation → testing → disclosure → monitoring. This lifecycle operates in parallel with incident response planning. When vulnerabilities are reported before exploitation, organizations can remediate proactively through standard change management processes. When vulnerabilities are actively exploited, the same teams and processes transition from vulnerability handling to incident response—but with the advantage of having established workflows, technical context, and remediation plans already developed.
4) Disclosure Communication Channels: Clear communication channels—both for receiving external reports and disseminating remediation information—reduce the time between discovery and remediation. Organizations with published VDPs and dedicated security contact addresses receive reports directly to security teams rather than having them routed through customer support or legal departments. Published security advisories and customer notification programs ensure that users learn about vulnerabilities and available remediations simultaneously with public disclosure, minimizing exposure windows.
Conclusion
ISO/IEC 29147 matters for organizations selling to enterprise clients because enterprise procurement teams evaluate vendor security maturity based on documented vulnerability management capabilities. Publishing a vulnerability disclosure policy and implementing ISO 29147-aligned processes demonstrates operational maturity, accountability, and commitment to protecting customer security—differentiators that influence enterprise purchasing decisions.
Organizations should view ISO 29147 not as a compliance checkbox but as foundational security infrastructure. External vulnerability reporting provides security validation that internal testing cannot replicate. Security researchers approach systems from attacker perspectives, identify business logic flaws that automated tools miss, and discover vulnerabilities in deployed configurations that differ from test environments. Vendors that establish structured disclosure processes gain access to this external security expertise—effectively expanding their security testing capability without proportional resource investment.
The alternative—operating without vulnerability disclosure processes—creates risk exposure that becomes apparent during security incidents, customer audits, or regulatory investigations. Organizations without clear reporting channels still have vulnerabilities, but discover them through exploitation, public disclosure, or breach rather than through coordinated private reporting. Implementing ISO 29147 transforms vulnerability discovery from crisis response into proactive security operations.
FAQ Section
1) What is ISO 29147?
ISO/IEC 29147:2018 provides requirements and recommendations to vendors on the disclosure of vulnerabilities in products and services. The standard establishes protocols for receiving external vulnerability reports, coordinating with reporters and other affected vendors, and publishing remediation information. ISO/IEC 29147:2018 is the second edition of the international standard for vulnerability disclosure. It applies to organizations that develop or provide software, hardware, online services, or any product exposed to external users.
2) What is the ISO 27001 standard?
ISO/IEC 27001 is the international standard for Information Security Management Systems (ISMS). It establishes requirements for systematically managing information security risk through documented policies, procedures, and controls. Organizations implement ISO 27001 to establish governance frameworks covering all aspects of information security: access control, cryptography, physical security, incident management, business continuity, supplier security, and compliance. ISO 27001 is certifiable—organizations can undergo third-party audits to achieve ISO 27001 certification, demonstrating to customers and regulators that they maintain mature information security management practices.
3) What is the ISO standard for vulnerability disclosure?
ISO/IEC 29147:2018 is the international standard specifically addressing vulnerability disclosure. Published in October 2018, it superseded the 2014 edition and was reviewed and confirmed as current in 2024. The standard provides requirements and recommendations for vendors to establish vulnerability disclosure policies, receive reports from external security researchers, coordinate remediation, and publish security advisories. Organizations implementing ISO 29147 create structured processes that reduce risk by enabling proactive vulnerability remediation before exploitation.
4) What is the difference between ISO 27001 and ISO 27000?
ISO/IEC 27000 is the foundational document in the ISO/IEC 27000 family of standards—it provides overview, vocabulary, and definitions used throughout the series. ISO/IEC 27000 defines terms like "information security," "risk," "control," and "ISMS" to ensure consistent understanding across all related standards. ISO/IEC 27001 is the certifiable standard that prescribes specific requirements for implementing, operating, monitoring, and improving an Information Security Management System. Organizations implement ISO 27001 to achieve certification; they reference ISO 27000 for terminology and conceptual framework. The ISO/IEC 27000 series includes dozens of standards covering specific security domains: ISO 27002 (security controls), ISO 27017 (cloud security), ISO 27035 (incident management), and ISO 29147 (vulnerability disclosure).



.svg)
.svg)
.svg)