Most organizations treat digital forensics as an afterthought—building security infrastructure without considering how evidence would be collected if an incident occurred. This approach creates a critical gap between incident response capabilities and legal defensibility, a gap that becomes painfully apparent when breaches require investigation, regulatory inquiries demand documentation, or litigation necessitates admissible evidence. For enterprises selling to enterprise clients, this forensic readiness gap represents both a security vulnerability and a competitive liability.
What is ISO/IEC 27037?
ISO/IEC 27037 provides guidelines for specific activities in handling digital evidence, which are identification, collection, acquisition and preservation of digital evidence that may be of evidential value. Published in 2012 by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC), the standard establishes systematic procedures for managing potential digital evidence from initial recognition through preservation.
The purpose of ISO/IEC 27037 is to establish principles and general requirements for the process of ensuring the integrity, authenticity, and reliability of potential digital evidence. The standard addresses four core processes: identification of devices and data sources containing potential evidence, collection of physical devices or data, acquisition through copying or imaging procedures, and preservation to maintain evidentiary integrity throughout the chain of custody.
The standard applies across organizational functions—IT departments managing infrastructure, security teams responding to incidents, legal teams handling investigations, and compliance teams preparing for audits. ISO/IEC 27037 provides guidance to individuals with respect to common situations encountered throughout the digital evidence handling process and assists organizations in their disciplinary procedures and in facilitating the exchange of potential digital evidence between jurisdictions.
Why ISO/IEC 27037 Matters for Enterprises
1) Ensuring Evidence Preservation and Integrity
Digital evidence degrades rapidly when handled improperly. A single improper modification—accessing a powered-on device without proper precautions, failing to create forensic copies, breaking chain of custody documentation—can render evidence inadmissible in legal proceedings or regulatory investigations. ISO/IEC 27037 provides guidelines for specific activities in handling potential digital evidence; these processes are identification, collection, acquisition and preservation of potential digital evidence. These processes are required in an investigation that is designed to maintain the integrity of the digital evidence – an acceptable methodology in obtaining digital evidence that will contribute to its admissibility in legal and disciplinary actions as well as other required instances.
For enterprises facing audits, litigation, or regulatory scrutiny, evidence admissibility determines outcomes. Structured evidence handling processes support forensic defensibility when investigators must demonstrate that collected evidence accurately reflects original data states, unchanged except through documented procedures.
2) Strengthening Cybersecurity Standards and Forensic Readiness
ISO/IEC 27037 embeds forensic investigation capabilities directly into security posture. Rather than scrambling to establish evidence collection procedures after an incident occurs, organizations implementing the standard maintain continuous forensic readiness—documented procedures, trained personnel, established chain of custody protocols, and validated collection tools.
For B2B enterprises, forensic readiness functions as a trust signal. Clients conducting vendor risk assessments increasingly evaluate incident response capabilities, asking: Can you investigate breaches systematically? Will evidence withstand regulatory scrutiny? Do you maintain documented procedures for evidence preservation? ISO/IEC 27037 alignment demonstrates that your organization treats security incidents as opportunities for rigorous investigation rather than rushed containment followed by incomplete analysis.
3) Facilitating Risk Management and Incident Preparedness
Digital incidents—data breaches, insider threats, intellectual property theft, compliance violations—demand investigation capabilities. Organizations without forensic readiness face binary choices: preserve evidence and extend downtime, or restore operations and lose investigative opportunities. Neither choice satisfies stakeholders expecting both rapid recovery and thorough investigation.
ISO/IEC 27037 implementation enables organizations to respond systematically to incidents requiring evidence collection. While the standard addresses only the initial forensic lifecycle—identification through preservation, not analysis or interpretation—it establishes the foundation for legally defensible investigations. This capability directly supports risk management frameworks requiring documented incident response procedures and evidence-based root cause analysis.
How ISO/IEC 27037 Fits Within Broader IT Security Frameworks
ISO/IEC 27037 belongs to the ISO/IEC 27000 family of information security standards. ISO/IEC 27037 complements ISO/IEC 27001 and ISO/IEC 27002, and in particular the control requirements concerning potential digital evidence acquisition by providing additional implementation guidance. While ISO/IEC 27001 establishes requirements for Information Security Management Systems (ISMS) and ISO/IEC 27002 provides control implementation guidance, ISO/IEC 27037 addresses the specialized domain of digital evidence handling.
The standard integrates with incident response frameworks, particularly ISO/IEC 27035, which guides security incident management from detection through recovery. In the context of incident handling where an ISIRT exists, the roles of a DEFR and/or DES as a member of an ISIRT team are discussed in ISO/IEC 27035:2011. ISO/IEC 27037 handles evidence collection and preservation; ISO/IEC 27035 addresses the broader incident lifecycle including detection, reporting, assessment, response, and lessons learned.
Organizations implementing comprehensive security and compliance programs typically combine ISO/IEC 27037 with ISO/IEC 27001 for ISMS establishment, ISO/IEC 27002 for control implementation, ISO/IEC 27035 for incident management, and ISO/IEC 27005 for risk management. This integrated approach creates end-to-end security posture addressing risk assessment, control implementation, incident response, and forensic readiness.
Key Concepts and Best Practices Under ISO/IEC 27037
1) Identification establishes which devices and data sources contain potential digital evidence. Organizations must document decision criteria: which systems warrant evidence collection, what threshold triggers forensic procedures, who authorizes collection activities. Identification prevents over-collection (wasting resources on irrelevant systems) and under-collection (missing critical evidence sources).
2) Collection and Acquisition procedures vary based on device state and evidence type. Powered-off devices typically undergo physical collection and imaging in controlled environments. Powered-on systems require volatile data capture—active network connections, running processes, memory contents—before powering down for traditional acquisition. The standard recognizes that different approaches and tools apply depending on circumstances, requiring documented procedures for each scenario.
3) Preservation maintains evidence integrity through documented chain of custody and controlled storage conditions. Every evidence transfer, every access, every analysis activity requires documentation. The standard emphasizes that some evidence changes are unavoidable—accessing a live system modifies timestamps, collecting volatile memory requires executing commands that alter system state—but all changes must be documented and justified as necessary for evidence preservation.
4) Device and Jurisdictional Adaptability extends the standard's applicability. ISO/IEC 27037 gives guidance for the following devices and/or functions that are used in various circumstances: - Digital storage media used in standard computers like hard drives, floppy disks, optical and magneto optical disks, data devices with similar functions, - Mobile phones, Personal Digital Assistants (PDAs), Personal Electronic Devices (PEDs), memory cards, - Mobile navigation systems,- Digital still and video cameras (including CCTV),- Standard computer with network connections,- Networks based on TCP/IP and other digital protocols, and - Devices with similar functions as above. The standard's device-agnostic approach supports evidence collection across evolving technology landscapes.
5) Process-Based Rather Than Tool-Prescriptive implementation gives organizations flexibility while maintaining rigor. ISO/IEC 27037 doesn't mandate specific forensic tools or software; instead, it requires documented procedures executed by qualified personnel. Organizations select tools appropriate to their infrastructure, budget, and investigative requirements, then document tool validation, calibration, and limitations.
Benefits for Enterprises Selling to Enterprise Clients
- Trust and Credibility: Demonstrating ISO/IEC 27037 alignment differentiates vendors in competitive evaluations. Enterprise clients conducting vendor risk assessments examine incident response capabilities, forensic readiness, and evidence handling procedures. Organizations implementing standardized digital evidence processes signal operational maturity beyond baseline security compliance.
- Compliance Readiness: Regulatory frameworks increasingly require documented incident investigation capabilities. GDPR mandates breach notification with detailed incident analysis. HIPAA requires documented security incident procedures. SOC 2 auditors evaluate incident detection and response controls. ISO/IEC 27037 implementation supports these requirements by establishing systematic evidence handling procedures that withstand regulatory scrutiny.
- Incident Response Capability: Evidence-based incident investigation enables organizations to answer critical questions following security events: What systems were compromised? What data was accessed? When did the breach occur? How did attackers gain access? Organizations without forensic capabilities provide incomplete answers; those with ISO/IEC 27037-aligned procedures deliver documented, defensible analysis.
- Competitive Differentiation: Most vendors implement reactive security measures—firewalls, encryption, access controls—without systematic forensic readiness. ISO/IEC 27037 implementation positions organizations as operationally sophisticated, prepared not just to prevent incidents but to investigate them rigorously when prevention fails. This differentiation matters in bid evaluations, vendor assessments, and contract negotiations where clients demand demonstrated security maturity.
Limitations and What ISO/IEC 27037 Doesn't Cover
ISO/IEC 27037 addresses only the initial forensic lifecycle: identification, collection, acquisition, and preservation. The standard explicitly excludes analysis, examination, and interpretation of evidence—the processes that extract investigative conclusions from collected data. Organizations implementing ISO/IEC 27037 gain evidence handling capabilities but require additional expertise or frameworks for forensic analysis.
The standard provides guidelines, not prescriptive requirements. Unlike ISO/IEC 27001, which establishes certifiable requirements for ISMS implementation, ISO/IEC 27037 offers best practices requiring organizational adaptation. Compliance depends on documented procedures aligned with jurisdictional legal requirements, which vary significantly across regulatory environments.
ISO/IEC 27037 implementation doesn't replace comprehensive information security management. Evidence handling capabilities function as one component within broader security frameworks addressing risk assessment, control implementation, vulnerability management, and continuous monitoring. Organizations treating ISO/IEC 27037 as standalone compliance miss integration opportunities with ISO/IEC 27001, ISO/IEC 27002, ISO/IEC 27035, and ISO/IEC 27005.
Practical Steps for Implementation
Organizations implementing ISO/IEC 27037-aligned procedures should begin by inventorying digital assets and data sources containing potential evidence: production systems, backup infrastructure, network devices, endpoint systems, mobile devices, cloud environments, and third-party integrations. Document system criticality, data sensitivity, and jurisdictional location.
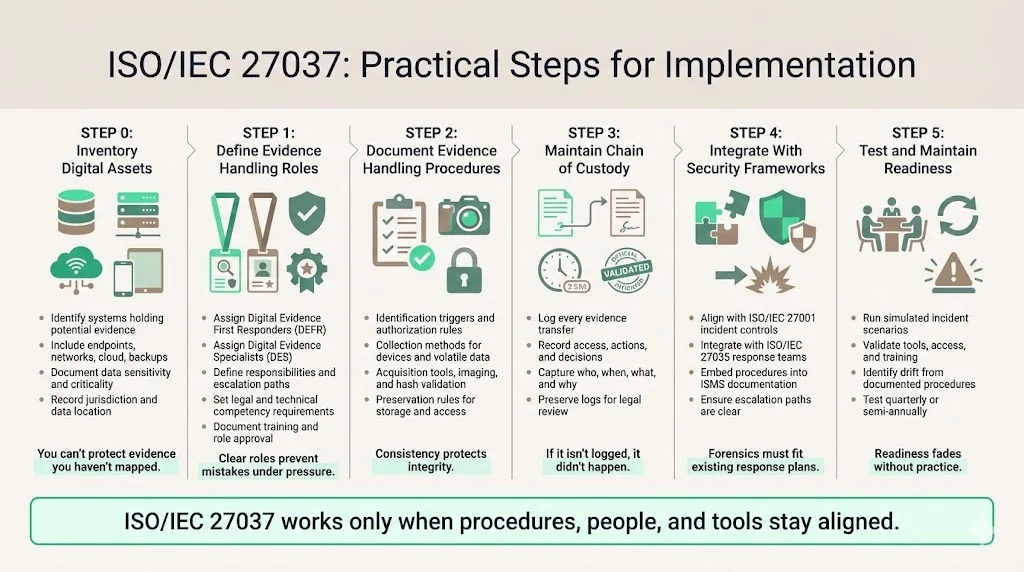
1) Define organizational roles for evidence handling. The DES provides specialized expertise to the DEFR. Digital Evidence First Responders (DEFR) conduct initial identification and collection activities; Digital Evidence Specialists (DES) provide technical expertise for complex acquisition scenarios. The DEFR and/or DES should have the relevant technical and legal competencies (e.g. those in Annex A) and should be able to demonstrate that they are properly trained and have sufficient technical and legal understanding to handle potential digital evidence appropriately. Document role definitions, training requirements, and competency assessments.
2) Establish documented procedures for each evidence handling phase. Identification procedures specify triggers requiring forensic collection, authorization workflows, and decision criteria for device prioritization. Collection procedures address physical device handling, volatile data capture, network isolation, and initial documentation requirements. Acquisition procedures define imaging tools, hash validation methods, and storage protocols. Preservation procedures establish chain of custody documentation, evidence storage conditions, access controls, and retention policies.
3) Maintain a chain of custody logs documenting every evidence transfer, every analysis access, and every procedural decision. These logs become critical when evidence admissibility is challenged in legal proceedings or regulatory investigations. Documentation should capture who handled evidence, when handling occurred, what actions were performed, and why specific procedures were selected.
4) Integrate ISO/IEC 27037 procedures with existing ISMS and incident response frameworks. If implementing ISO/IEC 27001, incorporate evidence handling as documented procedures supporting incident management controls. If implementing ISO/IEC 27035, align DEFR and DES roles with incident response team structures.
5) Test forensic readiness periodically through tabletop exercises and simulated incident scenarios. Identify gaps in procedures, tool availability, personnel training, and documentation practices. Forensic capabilities degrade without regular validation—tools become outdated, procedures drift from documentation, trained personnel leave organizations. Quarterly or semi-annual testing maintains operational readiness.
Why ISO/IEC 27037 Is Important for Enterprise Compliance and Security
The emphasis on digital evidence collection and evidence preservation ensures that when cyber-incidents occur, organizations respond with documented, defensible procedures maintaining data integrity throughout the forensic lifecycle. This capability directly supports information assurance objectives—demonstrating that security controls function as documented and that incident investigations produce reliable findings.
Legal compliance increasingly demands systematic evidence handling. Regulatory frameworks require documented incident response capabilities with evidence supporting root cause analysis, impact assessment, and remediation verification. Organizations without forensic readiness face compliance gaps when regulators demand: How do you know what happened? How can you prove your analysis? What evidence supports your breach notification timeline?
ISO/IEC 27037 functions as a building block within comprehensive IT security frameworks. Combined with risk management practices, ISMS implementation, and incident response capabilities, evidence handling procedures complete the security lifecycle—preventing incidents where possible, detecting them when prevention fails, investigating them systematically when detection succeeds, and remediating them based on evidence-driven analysis.
For enterprises selling to enterprise clients, ISO/IEC 27037 alignment demonstrates operational maturity. Clients don't just want vendors with strong perimeter defenses; they want partners prepared to investigate incidents rigorously, maintain evidence integrity, and support joint forensic analysis when shared infrastructure is compromised. This forensic readiness distinguishes security-mature organizations from those performing security theater—implementing controls that look impressive on paper but lack operational depth when tested by actual incidents.
Frequently Asked Questions
1) What is ISO/IEC 27037?
ISO/IEC 27037 is an international standard providing guidelines for identifying, collecting, acquiring and preserving digital evidence. The standard ensures integrity, authenticity and reliability of electronic evidence through documented procedures applicable to investigations, audits, and legal proceedings.
2) What is the difference between ISO 27001 and ISO 27035?
ISO/IEC 27001 defines requirements for establishing, implementing, maintaining, and continuously improving an Information Security Management System (ISMS). Organizations achieve ISO/IEC 27001 certification through audits demonstrating ISMS implementation against specified control objectives. ISO/IEC 27035 provides guidance for security incident management—detection, reporting, assessment, response, and recovery—without establishing certifiable requirements. ISO/IEC 27001 addresses systematic security governance; ISO/IEC 27035 addresses operational incident handling.
3) What is the ISO 3700 standard?
No recognized ISO 3700 standard exists within information security frameworks. This likely represents confusion with ISO/IEC 27000-series standards addressing information security management, including ISO/IEC 27000 (vocabulary and definitions), ISO/IEC 27001 (ISMS requirements), ISO/IEC 27002 (security controls), ISO/IEC 27035 (incident management), and ISO/IEC 27037 (digital evidence handling).
4) What is the ISO/IEC 27001 standard?
ISO/IEC 27001 establishes requirements for Information Security Management Systems (ISMS). The standard requires organizations to conduct risk assessments, implement security controls addressing identified risks, maintain documented procedures for security operations, monitor control effectiveness, and continuously improve security posture. Organizations achieve ISO/IEC 27001 certification through third-party audits conducted over minimum observation periods—typically 6-12 months for initial certification—demonstrating sustained ISMS operation. Certification requires surveillance audits every 6-12 months and recertification audits every three years, ensuring continuous compliance with ISMS requirements.



.svg)
.svg)
.svg)