Most organizations treat cloud platform adoption as a technology decision rather than a security architecture commitment. This creates a fundamental gap between operational flexibility and compliance readiness—a gap that becomes apparent when enterprise clients demand documented security controls or auditors scrutinize multi-tenant environments. With approximately 94% of organizations leveraging cloud services and 61% reporting at least one cloud-related security incident in 2025, the question is no longer whether to secure Platform as a Service (PaaS) deployments, but how to implement controls that satisfy both regulatory requirements and actual threat landscapes.
"ISO PaaS" represents the application of International Organization for Standardization (ISO) security standards—specifically ISO/IEC 27001 and ISO/IEC 27017—to cloud platform environments. These standards provide structured frameworks for managing information security in environments where infrastructure, middleware, development tools, and runtime components are provisioned as services. For enterprises building applications on PaaS or vendors offering PaaS solutions, ISO compliance establishes the documented, auditable security posture required for regulated industries, enterprise contracts, and long-term operational discipline.
This definition covers what PaaS entails, which ISO standards apply to cloud platforms, why ISO compliance matters for both PaaS providers and customers, real-world implementation considerations, and the actual security outcomes—along with limitations—that ISO frameworks deliver in cloud environments.
What is PaaS?
Platform as a Service (PaaS) is a cloud computing model providing complete development and deployment infrastructure—operating systems, middleware, runtime environments, databases, development tools, CI/CD pipelines—enabling development teams to build, deploy, and manage applications without provisioning underlying infrastructure. PaaS abstracts infrastructure complexity while delivering the full application stack supporting cloud-native development.
PaaS environments typically include infrastructure management, operating system maintenance, middleware services, runtime environments, managed databases, integrated development tools, automated scaling, monitoring capabilities, and deployment automation. This comprehensive stack allows developers to focus on application logic rather than infrastructure operations.
Organizations adopt PaaS for accelerated development cycles, elastic scalability aligned to demand, reduced infrastructure overhead, rapid experimentation capabilities, simplified deployment processes, and consistent environments across development, staging, and production. Common use cases include web application hosting, API development and management, microservices architectures, integration platforms, hybrid cloud deployments connecting on-premises and cloud resources, and backend services for mobile and IoT applications.
The multi-tenant nature of PaaS—where multiple customers share underlying infrastructure with logical separation—introduces specific security considerations. Virtualization boundaries, customer data isolation, shared responsibility models, configuration management across dynamic environments, and clear delineation of provider versus customer security obligations all require systematic controls beyond traditional on-premises security approaches.
What Does "ISO for PaaS" Mean?
There is no single "ISO PaaS" standard. Rather, security and compliance in PaaS environments are supported by specific standards from the International Organization for Standardization (ISO) and International Electrotechnical Commission (IEC) designed to address information security management and cloud-specific controls.
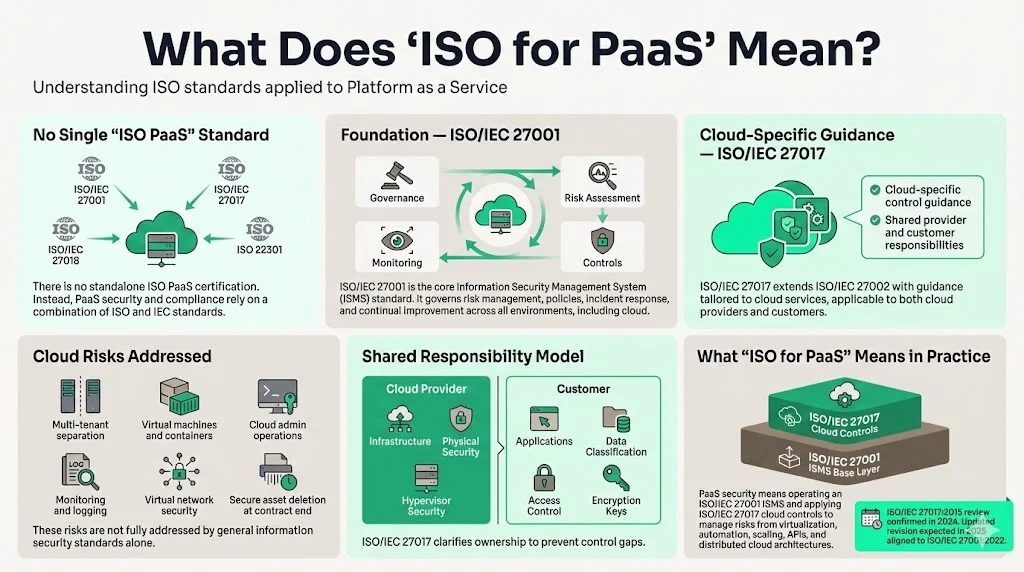
The foundational standard is ISO/IEC 27001, which establishes requirements for implementing, maintaining, and continuously improving an Information Security Management System (ISMS). ISO/IEC 27001 provides the overall framework for systematic risk assessment, control selection, policy documentation, incident response, and continuous monitoring applicable across technology environments including cloud platforms.
ISO/IEC 27017 is a cloud-specific security standard providing practical guidance for securing information in cloud environments, functioning as an extension of ISO/IEC 27002 (the code of practice for information security controls). ISO/IEC 27017:2015 provides additional implementation guidance for relevant controls specified in ISO/IEC 27002 plus additional controls with implementation guidance specifically relating to cloud services, offering guidance for both cloud service providers and cloud service customers.
The current ISO/IEC 27017:2015 standard was last reviewed and confirmed in 2024, with a revised version expected within coming months. The Draft International Standard (DIS) revision to ISO 27017 aligns with ISO 27001:2022, with the voting ballot closing by end of April 2025 and official publication expected between August and September 2025.
ISO/IEC 27017 addresses cloud-specific security considerations absent from general information security frameworks: separation of customer environments in multi-tenant architectures, secure virtual machine and container configuration, administrative operations security, activity monitoring and logging specific to cloud services, secure network configurations in virtualized environments, and handling of asset return or secure deletion at contract termination.
ISO/IEC 27017 focuses on clarifying roles of control implementation in cloud computing, addressing the shared responsibility model where cloud service providers manage certain security controls (infrastructure, physical security, hypervisor security) while customers remain responsible for others (application security, data classification, access management, encryption key management). This delineation prevents gaps where both parties assume the other handles specific controls.
In operational terms, "ISO for PaaS" means implementing ISO/IEC 27001 as the overarching ISMS framework, then applying ISO/IEC 27017's cloud-specific controls to address risks inherent in platform services—multi-tenancy, virtualization, dynamic provisioning, automated scaling, API-driven management, and the distributed nature of cloud architectures.
Why ISO Compliance Matters for PaaS—Purpose and Benefits
Applying ISO standards to PaaS environments addresses fundamental security and operational challenges that generic security approaches fail to systematically manage.
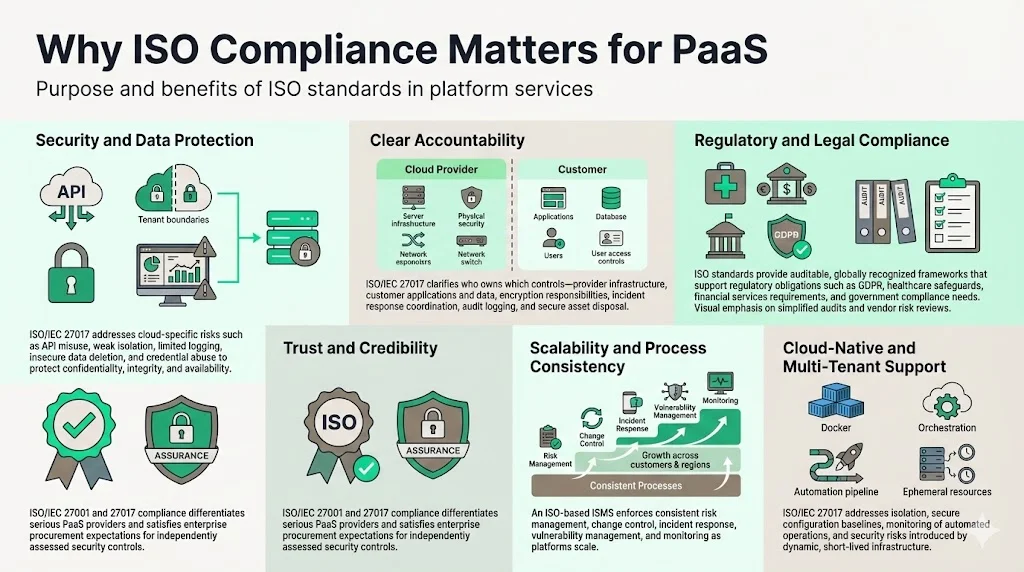
1) Security and Data Protection: Cloud platforms introduce attack vectors absent in traditional infrastructure—misconfigured APIs, inadequate tenant isolation, insufficient logging and monitoring, insecure data deletion, and unauthorized access through compromised credentials. ISO/IEC 27017's cloud-specific controls systematically address these risks, helping maintain confidentiality, integrity, and availability across virtualized, multi-tenant environments.
2) Clear Accountability: Cloud models involve third-party providers, shared responsibilities, virtual and ephemeral assets, and dynamic scaling, with ISO/IEC 27017 clarifying control implementation roles in cloud computing. Without documented responsibility matrices, organizations face confusion about who secures what—provider-managed infrastructure versus customer-managed applications, data encryption responsibilities, incident response coordination, audit log retention, and secure asset disposal at contract termination.
3) Regulatory and Legal Compliance: Enterprises in regulated industries—financial services, healthcare, legal, government—require documented, auditable security frameworks demonstrating systematic risk management. ISO standards provide globally recognized references satisfying regulatory obligations including GDPR data protection requirements, HIPAA safeguards for protected health information, financial services regulations, and industry-specific compliance mandates. Documented ISO compliance simplifies regulatory audits and vendor risk assessments.
4) Trust and Credibility: For PaaS providers selling to enterprise clients, ISO/IEC 27001 and 27017 compliance signals systematic commitment to security and compliance—differentiating serious providers from vendors relying on marketing claims. Enterprise procurement processes increasingly require evidence of third-party audited security controls before engaging cloud platforms handling sensitive data or supporting business-critical applications.
5) Scalability and Consistent Processes: As platform usage scales across multiple customers, geographies, and use cases, ad-hoc security approaches become unwieldy and error-prone. ISO-based ISMS ensures consistent processes for risk assessment, control implementation, change management, incident response, vulnerability management, and continuous monitoring—maintaining security discipline as complexity increases.
6) Support for Multi-Tenant and Cloud-Native Architectures: PaaS environments typically leverage containerization, orchestration platforms, virtualization layers, and automated deployment pipelines. ISO/IEC 27017's controls address isolation requirements for multi-tenant deployments, secure configuration baselines for containers and virtual machines, monitoring of automated operations, and security implications of ephemeral infrastructure where resources are created and destroyed dynamically.
Real-World Importance—For Enterprise Clients and PaaS Vendors
ISO compliance creates concrete operational advantages and reduces specific risks for both PaaS consumers and providers.
For Enterprises Consuming PaaS: ISO-compliant providers deliver assurance on systematic security controls, documented policies and procedures, consistent monitoring and incident response capabilities, and audit trails supporting regulatory compliance. This reduces internal compliance burden—enterprises can leverage provider ISO certifications during their own audits rather than building comprehensive cloud security programs from scratch. For organizations subject to regulatory oversight, using ISO-compliant PaaS simplifies demonstrating due diligence in vendor selection and ongoing risk management. Documented shared responsibility matrices clarify exactly which security controls the enterprise must implement versus those managed by the provider.
For PaaS Vendors and Cloud Providers: ISO compliance functions as competitive differentiation when selling to security-conscious or regulated enterprises. Many enterprise procurement processes require ISO/IEC 27001 certification as a minimum qualification—lack of certification eliminates vendors from consideration regardless of other capabilities. ISO frameworks help manage provider liabilities by establishing documented controls, clear responsibility boundaries, and evidence of systematic security management—reducing risk from misconfiguration, data breaches, or inadequate incident response. Operationally, ISMS implementation standardizes security protocols across multi-tenant architectures, global data centers, and diverse customer requirements.
Critical Scenarios for ISO PaaS Compliance: Financial services organizations using PaaS for transaction processing, customer portals, or data analytics face strict regulatory requirements where ISO compliance provides documented evidence of security controls. Healthcare providers deploying applications handling protected health information on PaaS need systematic safeguards addressing HIPAA requirements—ISO frameworks provide the structure. Multi-tenant SaaS vendors building on PaaS infrastructure require clear isolation controls and compliance documentation to satisfy their own enterprise customers. Hybrid cloud deployments mixing on-premises and cloud resources need consistent security governance across environments—ISO standards provide unified frameworks. Long-term enterprise contracts often mandate specific compliance certifications and audit rights—ISO compliance satisfies these contractual obligations while providing ongoing audit readiness.
How to Implement ISO Compliance for PaaS
Implementing ISO standards for PaaS requires systematic assessment, documentation, control implementation, and continuous monitoring—not one-time certification efforts.
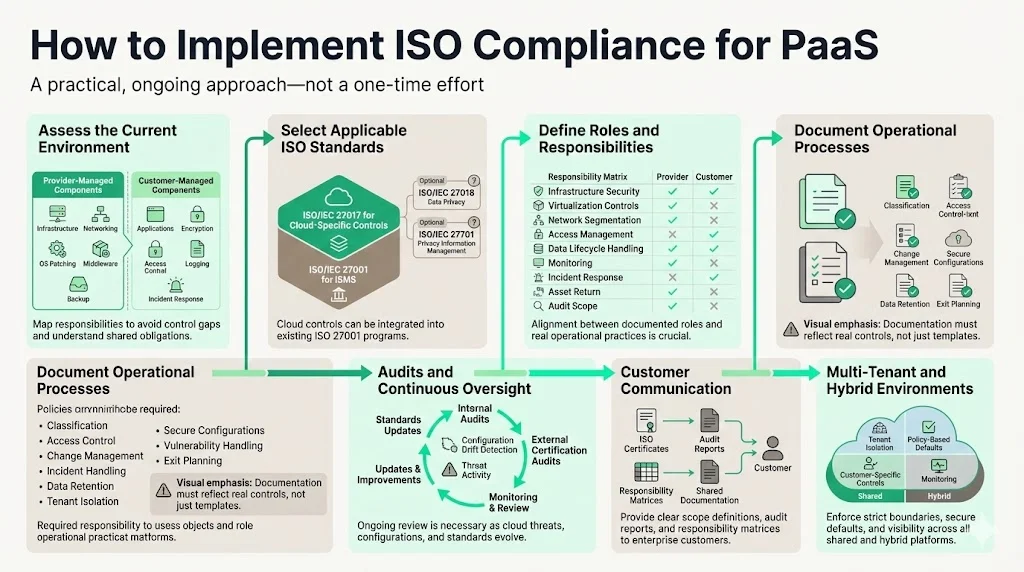
1) Assess Current Environment: Map which components are managed by provider versus customer—infrastructure provisioning, network configuration, operating system patching, middleware management, application security, data encryption, access control, logging and monitoring, backup and recovery, and incident response. This responsibility mapping prevents gaps where neither party implements required controls.
2) Choose Applicable Standards: At minimum, implement ISO/IEC 27001 for overall ISMS establishment and ISO/IEC 27017 for cloud-specific controls. Depending on industry and data types, consider additional standards—ISO/IEC 27018 for personally identifiable information protection in public clouds, ISO/IEC 27701 for privacy information management, or industry-specific frameworks. For organizations already holding ISO/IEC 27001 certification, ISO 27017's cloud-specific controls can be incorporated into existing ISO 27001 certification processes.
3) Define Roles and Responsibilities Clearly: Document exactly who handles infrastructure security, virtualization layer controls, network segmentation, access management, data lifecycle management including secure deletion, configuration management, activity monitoring, incident detection and response, asset return at contract termination, and audit compliance. These responsibility matrices must align with actual operational practices, not aspirational policies.
4) Document Processes: Establish security policies covering information classification, access control, change management, incident response procedures, data handling and retention, tenant isolation requirements, secure configuration baselines, vulnerability management, exit strategies and data portability. Documentation must reflect actual implemented controls, not generic templates—auditors verify operational reality matches documented policies.
5) Regular Audits and Continuous Monitoring: Conduct periodic internal audits assessing control effectiveness, external audits by accredited certification bodies for formal ISO certification, continuous monitoring for configuration drift and suspicious activity, and regular updates addressing new cloud-specific threats or changes in standards. Organizations must reevaluate existing cloud security policies to align with updated controls and assess shared responsibility models to ensure clear security ownership between customers and providers as standards evolve.
6) Communicate Compliance to Customers: Provide ISO certifications, SOC 2 reports, audit documentation, responsibility matrices, and compliance attestations to enterprise clients. Transparency regarding scope of certification—which services and components are covered—builds trust and facilitates customer compliance efforts.
7) For Multi-Tenant and Hybrid Environments: Implement virtualization isolation controls, tenant boundary enforcement, secure default configurations with policy-backed templates, customer-specific security policies where required, and monitoring ensuring no cross-tenant data access or configuration interference.
What ISO Compliance Does—and Does Not—Guarantee
ISO frameworks systematically manage risks but do not eliminate all security threats or operational challenges.
Not a Silver Bullet: ISO compliance addresses systematic security management—risk assessment, control implementation, continuous monitoring—but does not prevent all security incidents. Human error, zero-day vulnerabilities, sophisticated attacks, misconfigurations outside certification scope, social engineering targeting employees, and supply chain compromises can occur despite ISO compliance. The value lies in systematic detection, response, and continuous improvement rather than perfect prevention.
Resource Overhead: Implementing and maintaining ISMS and cloud-specific controls requires dedicated resources—security personnel, audit preparation, documentation maintenance, continuous monitoring infrastructure, and periodic reassessment. Organizations pursuing ISO compliance must commit to ongoing investment, not one-time certification efforts. For PaaS providers, this overhead must be factored into service economics while remaining competitive.
Shared Responsibility Complexity: In cloud contexts, security failures by either provider or customer create risk regardless of the other party's compliance. A provider with ISO certification cannot prevent customer misconfigurations—deploying applications with hardcoded credentials, inadequate access controls, or insecure APIs. Conversely, customers implementing strong security cannot compensate for provider infrastructure vulnerabilities or inadequate tenant isolation. Clear responsibility delineation helps but does not eliminate this inherent complexity.
Certification Scope Matters: Only portions of the environment covered under certification scope receive audit validation. Custom application code, third-party integrations, partner services, or components explicitly excluded from scope may lack the same rigor. Organizations must understand exactly what certification covers—which services, data centers, and operational processes—versus what remains outside formal scope.
Evolving Standards and Cloud Technology: Cloud platforms evolve rapidly—serverless computing, service mesh architectures, edge computing, multi-cloud orchestration. Standards may lag emerging technologies or require interpretation for newer deployment models. The current ISO/IEC 27017:2015 is expected to be replaced by ISO/IEC DIS 27017 within coming months, reflecting continuous standard updates addressing technology evolution. Organizations must adapt frameworks proactively rather than waiting for standard updates.
Conclusion
Combining PaaS operational flexibility with ISO security discipline provides enterprises with documented, auditable security frameworks addressing the specific risks of multi-tenant cloud platforms. ISO/IEC 27001 establishes systematic ISMS implementation while ISO/IEC 27017 addresses cloud-specific controls—tenant isolation, virtualization security, shared responsibility clarity, and secure asset lifecycle management.
For PaaS providers, ISO compliance differentiates serious security commitment from marketing claims, facilitates enterprise sales requiring third-party validated controls, and provides operational discipline managing complex multi-tenant environments. For enterprises consuming PaaS, using ISO-compliant providers reduces internal compliance burden, simplifies regulatory audits, and establishes clear accountability for security controls across shared responsibility boundaries.
Organizations offering or consuming PaaS in enterprise contexts should treat ISO compliance as fundamental infrastructure for trust, security, and audit readiness—not optional add-ons or checkbox exercises. The investment in systematic security management, documented controls, and continuous monitoring delivers long-term stability, reduced risk exposure, and competitive advantage in environments where security incidents, regulatory scrutiny, and enterprise procurement requirements make compliance a business imperative rather than a technical preference.
FAQs
1) What is ISO PaaS?
There is no standalone "ISO PaaS" product or certification. The term refers to implementing ISO/IEC standards—particularly ISO/IEC 27001 for Information Security Management Systems and ISO/IEC 27017 for cloud-specific security controls—within Platform as a Service environments. PaaS providers can implement these standards to demonstrate systematic security management, while enterprises consuming PaaS can require ISO compliance from vendors. The combination addresses both general information security requirements and cloud-specific risks including multi-tenancy, virtualization, shared responsibility, and dynamic provisioning.
2) What is PaaS certification?
ISO 27017 functions as a code of practice rather than a standalone certification framework—organizations cannot obtain separate ISO 27017 certificates through independent auditing, but can incorporate ISO 27017's cloud-specific controls into existing ISO 27001 certification processes. PaaS certification typically means ISO/IEC 27001 certification where the scope explicitly includes platform services and incorporates ISO/IEC 27017 controls addressing cloud-specific risks. Accredited certification bodies conduct formal audits verifying that documented controls match operational reality, resulting in ISO/IEC 27001 certificates covering PaaS offerings. These certifications require surveillance audits maintaining ongoing compliance rather than one-time assessments.
3) What is PaaS for insurance?
Insurance organizations use PaaS for policy administration systems, claims processing applications, customer portals, data analytics platforms, and integration services connecting core systems with partners and third parties. ISO 27017 is ideal for organizations involved in cloud computing including those offering SaaS, PaaS, or IaaS platforms, with insurance representing a sector where regulatory requirements, data sensitivity, and fiduciary obligations make ISO compliance particularly important. Insurance PaaS deployments must address data protection regulations, maintain audit trails for regulatory compliance, implement strong access controls protecting policyholder information, and ensure business continuity supporting claims operations. ISO frameworks provide the systematic security management, documented controls, and audit readiness required for regulated insurance operations on cloud platforms.
4) How to become a premium auditor?
Organizations seeking to pass ISO audits and achieve certification should build comprehensive ISMS based on ISO/IEC 27001, adopt applicable standards including ISO/IEC 27017 for cloud services, conduct internal audits validating control effectiveness before external assessment, engage accredited certification bodies for formal audits, and maintain continuous compliance through surveillance audits and ongoing risk management. For individuals pursuing auditor credentials, recognized certification paths include ISO/IEC 27001 Lead Auditor courses from accredited training providers, demonstrated experience conducting information security audits, and certifications from bodies including IRCA (International Register of Certificated Auditors) or equivalent national accreditation organizations. Premium auditor status requires deep technical knowledge of information security controls, practical experience across multiple industries and technology environments, understanding of both ISMS frameworks and operational implementation, and ability to assess whether documented controls match actual security posture rather than accepting paper compliance.



.svg)
.svg)
.svg)