Modern vehicles are increasingly connected and software-driven, making them more vulnerable to cybersecurity threats. The average connected vehicle now integrates dozens of electronic control units (ECUs), multiple connectivity protocols—from Bluetooth and WiFi to cellular 5G—and over-the-air (OTA) update capabilities that fundamentally expand the attack surface. This transformation positions cybersecurity as inseparable from vehicle safety. ISO/SAE 21434 provides the engineering framework necessary to manage these risks across the entire automotive product lifecycle. This article defines ISO/SAE 21434, examines its core components and practical use cases, and clarifies how compliance affects product development teams, original equipment manufacturers (OEMs), and enterprise customers across the automotive supply chain.
What is ISO/SAE 21434?
ISO 21434, "Road vehicles - cybersecurity engineering," is an automotive industry standard developed by the International Standard of Organization (ISO) alongside the Society of Automotive Engineers (SAE). Published in 2021, the standard establishes comprehensive requirements and processes for identifying, assessing, and mitigating cybersecurity risks in electrical and electronic (E/E) systems within road vehicles. The ISO/SAE 21434 standard defines the engineering requirements for cybersecurity risk management, helping to ensure that cyber risks are monitored, detected, and mitigated throughout the vehicle's lifecycle.
Unlike narrower standards that address isolated phases such as design or testing, ISO/SAE 21434 mandates a risk-based approach woven into organizational governance, development workflows, and post-deployment operations. The ISO/SAE 21434 is therefore a process-oriented standard and helps define a structured process to ensure cybersecurity along the lifecycle. This orientation means the standard does not prescribe specific technical solutions; instead, it defines processes, roles, responsibilities, and outcomes that organizations must achieve to build genuine security posture.
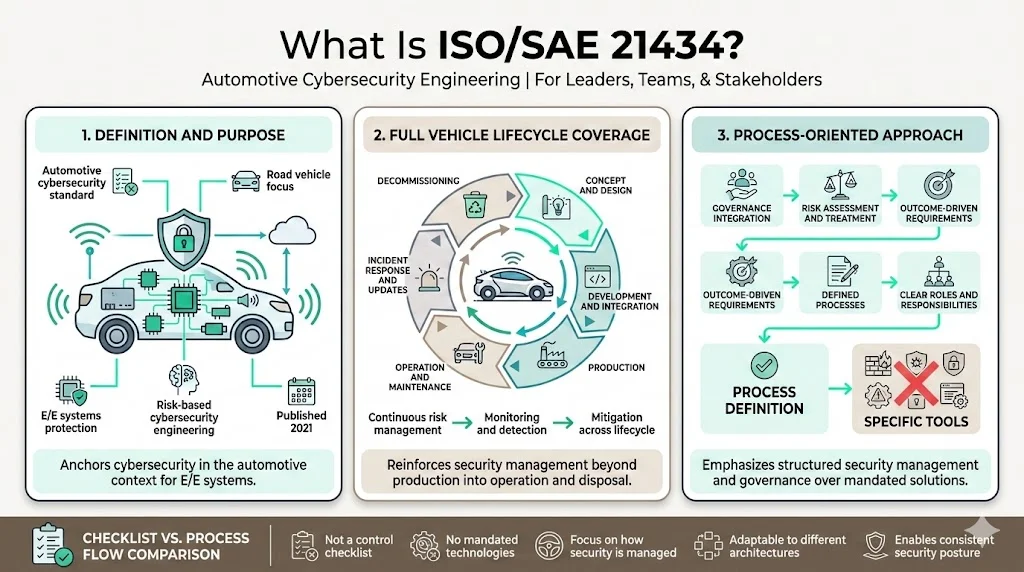
Lifecycle Coverage
ISO/SAE 21434 recommends that manufacturers (OEMs) and other members of the automotive supply chain consider security not only during a vehicle's conceptualization but also during its decommissioning. This spans concept development, risk assessment, product development, production, operation, maintenance, and eventual retirement. Each phase requires documented processes, defined security requirements, and evidence of control effectiveness—ensuring cybersecurity remains a continuous discipline rather than a project milestone.
This comprehensive coverage contrasts with standards focused solely on production or certification events. ISO/SAE 21434 explicitly requires feedback loops from field operations back into development, supporting continuous vulnerability assessment and iterative security improvements.
Who It Applies To
Automotive OEMs, Tier 1 and Tier 2 suppliers, and any organization involved in the design, development, or maintenance of vehicle E/E systems. This extends to automotive software providers, system integrators, semiconductor manufacturers, and middleware developers who contribute components to vehicle architectures. Because modern vehicles rely on deeply integrated supply chains, ISO/SAE 21434 impacts every participant—from the supplier providing a single ECU to the OEM orchestrating the final vehicle integration.
Enterprise clients across the automotive value chain must understand these obligations. A Tier-2 supplier manufacturing safety-critical components operates under cybersecurity requirements cascaded from the OEM. Failure to demonstrate ISO/SAE 21434 alignment jeopardizes supplier relationships and market access.
Why ISO/SAE 21434 Matters (Cybersecurity & Automotive Safety)
1) The Shift in Vehicle Safety
The automotive industry is undergoing significant change in all areas including new applications such as ADAS/Highly-Automated Driving (HAD), new EE architectures, new sensors such as Lidar, long distance imaging and 4D radar and extensive connectivity protocols for connected cars. The increasing number of connectivity protocols such as Bluetooth, WiFi, cellular including 5G, GPS, USB and in-car networks such as Controller Area Network (CAN), MIPI, and automotive Ethernet, and expanded adoption of Over-the-Air (OTA) software updates, dramatically accelerate cybersecurity risks.
Vehicles now function as mobile computing platforms. A successful cyberattack can disable braking systems, manipulate steering controls, exfiltrate personal data, or compromise fleet management systems. Cybersecurity failures translate directly into safety incidents—a reality that erases the traditional boundary between IT security and functional safety engineering.
2) Risks ISO/SAE 21434 Addresses
The standard confronts threats stemming from vehicle connectivity, third-party software integration, OTA update mechanisms, and supply chain dependencies. OTA updates and other connected applications, such as vehicle telematics and smartphone connectivity, can create security gaps that open systems to unauthorized access, tampering, and the injection of malware and viruses.
Real-world implications include unauthorized vehicle access, denial-of-service attacks that disable critical functions, theft of personally identifiable information (PII), and manipulation of vehicle behavior. Supply chain vulnerabilities—where a compromised component from a single supplier propagates risk across multiple vehicle platforms—represent particularly complex threats requiring systematic risk management.
3) How the Standard Frames Risk
ISO/SAE 21434 centers on Threat Analysis and Risk Assessment (TARA), a structured methodology for identifying assets, analyzing potential threats, assessing attack feasibility, and determining appropriate security controls. ISO/SAE 21434 describes Threat Analysis and Risk Assessment (TARA) to assess the cybersecurity risks in the product.
TARA maps identified threats to severity levels based on potential impact and likelihood. This risk-based prioritization directs engineering resources toward the most critical vulnerabilities, ensuring security controls align with actual threat landscapes rather than generic checklists. Organizations document TARA outcomes, trace them to system security requirements, and validate control effectiveness through verification and validation activities.
Core Components of ISO/SAE 21434
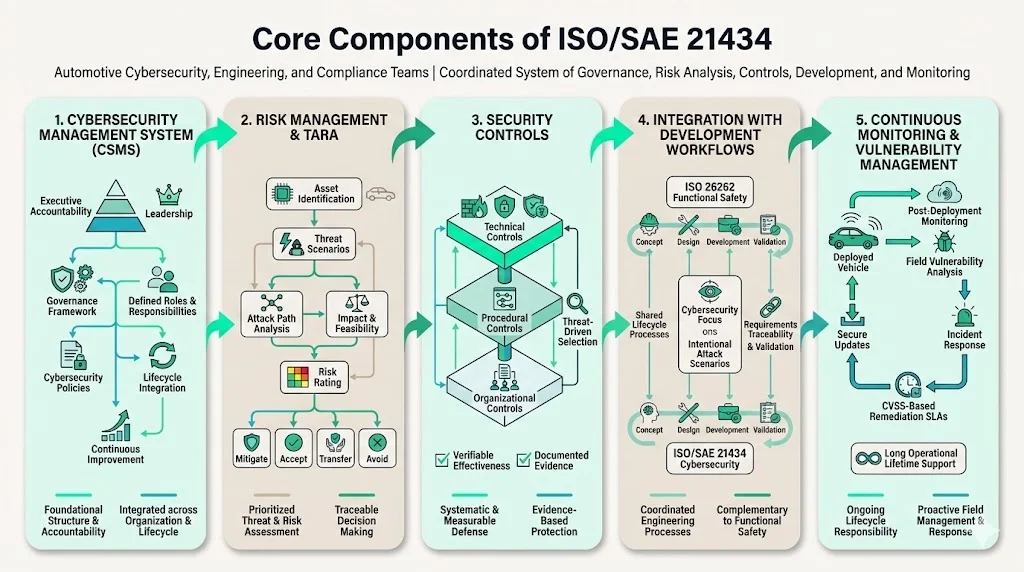
1) Cybersecurity Management System (CSMS)
The standard defines requirements for the establishment and maintenance of CSMS, covering organizational structure, risk management practices, and cybersecurity engineering processes. A CSMS establishes governance structures, assigns roles and responsibilities, defines policies, and integrates cybersecurity objectives into product lifecycle management.
The CSMS ties organizational risk management to product-level security requirements. It mandates executive management commitment, cross-functional collaboration between engineering and security teams, and continuous improvement mechanisms informed by vulnerability data and incident response. A mature CSMS ensures cybersecurity is embedded in corporate culture and operational workflows—not treated as an audit-driven formality.
2) Risk Management & TARA
TARA proceeds through systematic steps: asset identification, threat scenario development, attack path analysis, impact assessment, and feasibility evaluation. Each threat receives a risk rating based on severity and likelihood. Organizations then determine whether to mitigate, accept, transfer, or avoid each risk.
This methodology prioritizes security work. High-severity, high-feasibility threats demand immediate mitigation through technical controls, procedural safeguards, or architectural changes. Lower-priority risks may be accepted with documented rationale. TARA outputs feed directly into system security requirements, creating traceability from threat identification through control implementation and verification.
3) Security Controls
Security controls fall into three categories: technical (encryption, authentication, intrusion detection), procedural (secure coding standards, vulnerability disclosure processes), and organizational (security training, incident response teams). Provide a threat-informed approach to guide security controls.
Controls mitigate identified cyber threats as part of system security requirements. Each control must be verifiable through testing, analysis, or inspection. Organizations document control implementation, trace controls back to specific threats, and maintain evidence of effectiveness throughout the product lifecycle.
4) Integration with Development Workflows
ISO/SAE 21434 operates in parallel with functional safety standards while maintaining a distinct cybersecurity focus. ISO 26262 focuses on functional safety, while ISO/SAE 21434 addresses cybersecurity. Both standards are complementary and often implemented together.
Where ISO 26262 addresses random hardware failures and systematic faults, ISO/SAE 21434 confronts intentional attacks from adversaries. Organizations achieving ISO 26262 compliance for functional safety leverage existing processes—hazard analysis, requirements traceability, verification and validation—while adapting them to threat-centric cybersecurity engineering. This integration maximizes existing competencies and avoids duplicative processes.
5) Continuous Monitoring and Vulnerability Assessment
ISO/SAE 21434 mandates processes for ongoing security evaluation post-deployment. Organizations must monitor field vulnerabilities, analyze security incidents, and respond with timely updates. Vulnerability management includes establishing automated service-level agreements (SLAs) for remediation based on Common Vulnerability Scoring System (CVSS) ratings.
Feedback loops from production and operation phases inform product updates, enabling organizations to address newly discovered threats and incorporate lessons learned into subsequent development cycles. This continuous approach prevents security posture from degrading over a vehicle's operational lifetime—often 10 to 15 years.
Practical Use Cases (Vehicle Cybersecurity in Action)
Connected Vehicle Systems
Vehicle-to-everything (V2X) communications enable vehicles to exchange data with infrastructure, other vehicles, and cloud services. V2X systems support collision avoidance, traffic optimization, and cooperative driving. However, these connectivity pathways introduce attack vectors where adversaries can inject false data, disrupt communications, or compromise vehicle control systems.
ISO/SAE 21434 provides the framework for securing V2X architectures through cryptographic authentication, message integrity verification, and intrusion detection. OTA update mechanisms—essential for deploying security patches and feature enhancements—require rigorous security controls to prevent malware injection or unauthorized firmware modifications. Organizations applying TARA to V2X systems identify specific threats, assess feasibility, and implement layered defenses across communication protocols and backend infrastructure.
Enterprise Software & Services
Middleware and cloud-based services increasingly integrate with vehicle data platforms, supporting fleet management, predictive maintenance, and usage-based insurance. Enterprise software-as-a-service (SaaS) providers accessing vehicle telemetry, location data, or diagnostic information must demonstrate alignment with ISO/SAE 21434 to satisfy OEM security requirements.
Adherence to the standard reduces risk by ensuring third-party services implement appropriate access controls, data encryption, and secure API designs. OEMs evaluating enterprise vendors scrutinize CSMS maturity, TARA documentation, and evidence of continuous vulnerability management—treating cybersecurity posture as a contractual and technical prerequisite.
Suppliers & Tiered Dependencies
Consider a Tier-2 supplier manufacturing electronic brake control modules. The supplier's component integrates into a Tier-1 system, which the OEM then incorporates into the vehicle platform. A vulnerability in the Tier-2 component propagates risk throughout the supply chain.
ISO/SAE 21434 defines cybersecurity interfaces between supply chain participants. The OEM cascades security requirements to Tier-1 suppliers, who further cascade them to Tier-2 and Tier-3 providers. Each supplier documents their CSMS, conducts TARA for their components, implements required controls, and provides evidence to the next tier. This structured approach ensures upstream cybersecurity obligations align with downstream integration risks—essential for enterprise clients with complex supplier dependencies.
Electric Vehicles & Advanced Architectures
Electric vehicles (EVs) introduce expanded attack surfaces due to battery management systems, charging infrastructure connectivity, and energy grid integration. Advanced EV architectures consolidate compute resources into domain controllers and zonal architectures, reducing ECU count but concentrating risk.
Cybersecurity planning based on ISO/SAE 21434 addresses threats across edge-to-cloud environments. Battery management systems require protection against tampering that could trigger thermal runaway. Charging stations must authenticate vehicles and encrypt payment data. Cloud-based fleet management platforms demand secure data pipelines and access controls. Organizations apply TARA across these domains, implement defense-in-depth strategies, and maintain continuous monitoring to detect anomalies indicative of cyberattacks.
Compliance Relevance (Business & Regulatory)
Compliance vs. Regulation
ISO/SAE 21434 is a voluntary standard—organizations choose to adopt it. However, regulatory frameworks increasingly reference the standard as the recognized methodology for automotive cybersecurity engineering. Unlike UN Regulation No. 155 (UN R155), ISO/SAE 21434 is not mandatory. The two standards, however, are considerably aligned and complement each other.
This distinction matters: ISO/SAE 21434 provides the engineering processes, while regulations like UNECE R155 mandate outcomes. Organizations achieve regulatory compliance by implementing ISO/SAE 21434 processes and demonstrating conformance through documentation and third-party assessment.
Market Access and Regulatory Approval
To release new road vehicles, the United Nations Economic Commission mandates automotive OEMs for Europe's UN R155 regulation to adopt a cybersecurity management system like ISO/SAE 21434, making compliance a prerequisite for market success. UNECE R155 applies across Europe, Japan, South Korea, and other signatory nations. China and other markets have introduced parallel regulations with similar requirements.
Failure to adhere to these regulations can result in sales bans. Organizations unable to demonstrate CSMS certification and ongoing cybersecurity management face denial of type approval—effectively blocking market access. For enterprise clients targeting global markets, ISO/SAE 21434 alignment is non-negotiable.
Organizational Readiness
Achieving ISO/SAE 21434 compliance requires organizational commitment beyond documentation. Companies must establish governance structures, assign dedicated cybersecurity roles (e.g., cybersecurity managers, TARA specialists), implement tooling for threat modeling and vulnerability tracking, and train engineering teams on secure development practices.
Enterprise clients selling to OEMs or operating in regulated markets need to plan for multi-year implementation timelines. Organizations with mature ISO 26262 processes adapt existing competencies; those starting from baseline maturity face steeper learning curves and resource investments.
Risks of Non-Compliance
Organizations avoiding ISO/SAE 21434 implementation expose themselves to regulatory penalties, market exclusion, brand damage, and actual security breaches. A publicized vulnerability resulting from inadequate cybersecurity processes erodes customer trust and invites scrutiny from regulators. The reputational and financial costs of a major security incident—including recalls, litigation, and lost sales—far exceed the investment required for systematic cybersecurity engineering.
Steps to Achieve ISO/SAE 21434 Compliance
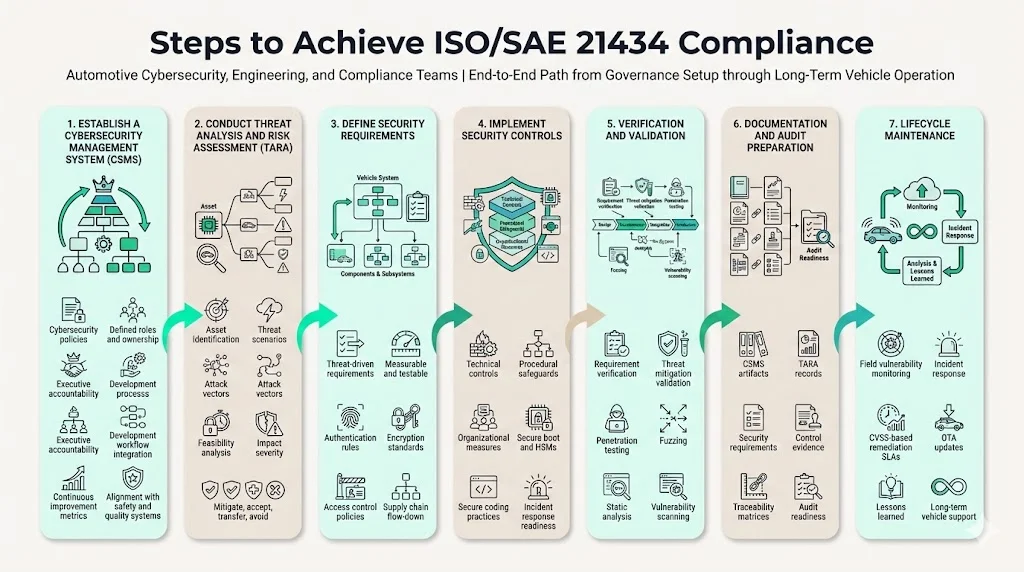
1) Establish a Cybersecurity Management System (CSMS)
Begin by defining cybersecurity policies, assigning organizational roles and responsibilities, and integrating cybersecurity objectives into product development workflows. Executive management must demonstrate commitment through resource allocation, governance oversight, and accountability structures. Document CSMS processes, establish metrics for continuous improvement, and define interfaces with functional safety and quality management systems.
2) Conduct Threat Analysis and Risk Assessment (TARA)
Identify critical assets within vehicle systems—ECUs, communication interfaces, data repositories. Develop threat scenarios considering attack vectors, adversary motivations, and potential impacts. Analyze attack feasibility based on attacker expertise, resources, and access. Assess risk severity using standardized criteria. Determine appropriate risk treatment strategies: mitigate through controls, accept with documented rationale, transfer via insurance or contractual mechanisms, or avoid by architectural redesign.
3) Define Security Requirements
Translate TARA insights into actionable system security requirements. Requirements must be specific, measurable, and traceable to identified threats. Specify authentication mechanisms, encryption standards, access control policies, secure communication protocols, and intrusion detection capabilities. Document requirements at system, subsystem, and component levels, cascading them through the supply chain.
4) Implement Security Controls
Execute control implementation using structured vulnerability assessment processes. Deploy technical controls (e.g., hardware security modules, secure boot mechanisms), establish procedural safeguards (e.g., secure coding guidelines, code review protocols), and implement organizational measures (e.g., security training programs, incident response teams). Maintain traceability from controls back to requirements and threats.
5) Verification & Validation
Test security features at each lifecycle stage. Verification confirms that implemented controls meet specified requirements through inspection, analysis, and testing. Validation demonstrates that controls effectively mitigate identified threats under realistic conditions. Use penetration testing, fuzzing, static code analysis, and vulnerability scanning to identify weaknesses before deployment.
6) Documentation & Audit Preparation
Maintain comprehensive artifacts demonstrating cybersecurity engineering activities. Document CSMS policies, TARA results, security requirements, control implementations, verification results, and post-deployment monitoring processes. Establish traceability matrices linking threats to requirements to controls to test cases. Prepare for internal audits and third-party assessments by organizing evidence according to ISO/SAE 21434 structure.
7) Lifecycle Maintenance
Establish continuous monitoring for field vulnerabilities, security incidents, and emerging threats. Implement automated SLAs for vulnerability remediation based on CVSS severity ratings. Maintain incident response capabilities to address active threats. Update products through OTA mechanisms or service campaigns as necessary. Feed lessons learned from operations back into development processes, improving cybersecurity posture across subsequent product generations.
Conclusion
ISO/SAE 21434 provides the engineering discipline necessary to address cybersecurity risks in an automotive landscape dominated by connectivity, software complexity, and sophisticated threat actors. The standard establishes lifecycle-wide processes for risk management, threat analysis, security control implementation, and continuous monitoring—transforming cybersecurity from an afterthought into a foundational engineering requirement. For enterprise clients across the automotive supply chain, ISO/SAE 21434 alignment is increasingly essential for regulatory compliance, market access, and competitive positioning. Organizations treating cybersecurity as performative compliance expose themselves to regulatory penalties, security breaches, and erosion of customer trust. Those implementing genuine risk-based cybersecurity engineering produce vehicles and components that meet regulatory obligations while protecting users from real threats. Assess current processes against ISO/SAE 21434 requirements, establish organizational readiness, and build cybersecurity capabilities that scale across product lifecycles and supply chain dependencies.
FAQs
1) What is ISO/SAE 21434?
ISO/SAE 21434 is an international standard for automotive cybersecurity engineering jointly published by the International Organization for Standardization (ISO) and the Society of Automotive Engineers (SAE). It defines processes, requirements, and guidelines for managing cybersecurity risks across the entire vehicle lifecycle—from concept through decommissioning.
2) Who must comply with ISO/SAE 21434?
Automotive OEMs, Tier-1 and Tier-2 suppliers, automotive software providers, system integrators, and any organization designing, developing, manufacturing, or maintaining electrical and electronic systems in road vehicles. Compliance obligations cascade through the supply chain based on contractual and regulatory requirements.
3) How does ISO/SAE 21434 differ from ISO 26262?
ISO 26262 addresses functional safety, focusing on preventing random hardware failures and systematic faults that could cause harm. ISO/SAE 21434 targets cybersecurity, addressing intentional attacks from adversaries seeking to exploit vulnerabilities. The two standards complement each other and are often implemented together to achieve comprehensive safety and security.
4) What are the main compliance steps?
Establish a Cybersecurity Management System (CSMS), conduct Threat Analysis and Risk Assessment (TARA), define security requirements based on identified threats, implement technical and procedural controls, verify and validate control effectiveness, document all activities for traceability and audit, and maintain lifecycle monitoring for vulnerabilities and incidents.
5) Is ISO/SAE 21434 mandatory in 2026?
While not legally mandatory, it is increasingly becoming a de facto requirement due to regulatory pressures and industry expectations. Regulations such as UNECE R155 mandate cybersecurity management systems for type approval—and ISO/SAE 21434 provides the recognized framework for achieving those regulatory requirements. Organizations targeting regulated markets effectively treat ISO/SAE 21434 compliance as mandatory for market access.



.svg)
.svg)
.svg)