Most organizations encounter "ISO" in vendor questionnaires, compliance requirements, and enterprise RFPs without fully understanding what the designation represents or why it matters. This creates a fundamental gap between checking a compliance box and implementing security infrastructure that enterprise buyers actually trust—a gap that becomes apparent when due diligence intensifies or when incidents expose the difference between documented controls and operational reality.
Understanding what ISO stands for and how standardization supports data protection is essential for companies selling to enterprise clients. The stakes around data security, regulatory scrutiny, and vendor risk management demand more than superficial compliance claims. Enterprise decision-makers evaluate vendors based on standardized frameworks that provide auditable evidence of consistent security practices rather than ad-hoc implementations.
This definition covers what ISO stands for, why standardization matters for enterprise data protection, which ISO standards directly impact vendor credibility, and practical steps for aligning your organization with ISO principles that enterprise buyers require.
What ISO Stands For?
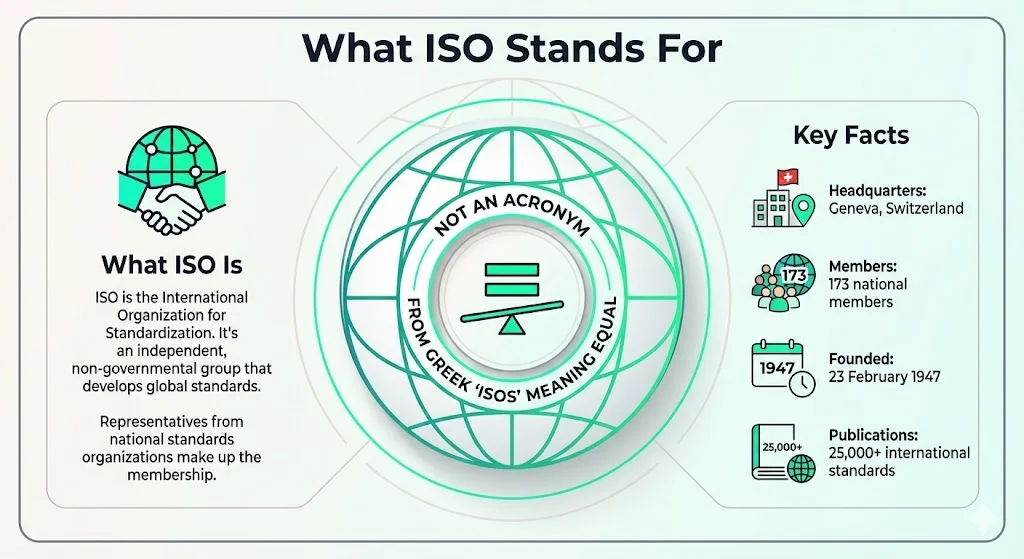
ISO is the International Organization for Standardization—an independent, non-governmental, international standard development organization composed of representatives from national standards organizations of member countries. The organization is headquartered in Geneva, Switzerland.
A common misconception is that ISO is an abbreviation for "International Standardization Organization" or similar—in fact, the letters do not officially represent an acronym, with the organization explaining that founders chose "ISO" to avoid different acronyms in different languages. The name derives from the Greek word "isos," meaning "equal"—reflecting the organization's mission to create equal, consistent standards across global markets.
As of 2025, there are 173 national members representing ISO in their country, with each country having only one member. ISO was founded on 23 February 1947, and has published over 25,000 international standards covering almost all aspects of technology and manufacturing.
Why Standardization Matters
Standardization creates common frameworks, definitions, and processes so that products, services, and security controls across industries and geographies operate reliably and predictably. For organizations selling to enterprise clients, standardization directly impacts vendor onboarding, audit efficiency, and integration complexity.
When your enterprise clients require vendors to meet standardized practices, they're simplifying their own risk management. Rather than evaluating each vendor's unique security approach, they assess alignment with established frameworks. This reduces friction in vendor management, accelerates procurement cycles, and provides enterprise security teams with consistent baselines for comparison.
ISO has over 800 technical committees (TCs) and subcommittees (SCs) to take care of standards development. These committees bring together subject matter experts from national standards bodies, industry representatives, and technical specialists to develop consensus-based standards that reflect current best practices and emerging threats.
How ISO Develops Standards
ISO standards are developed according to principles of industry-wide, voluntary consensus, meaning views of all interested parties are taken into account—including manufacturers, vendors, users, consumer groups, testing laboratories, governments, engineering professionals, and research organizations—with the process being market-driven and based on voluntary involvement.
The standards development process moves through defined stages: proposal (where industry sectors communicate needs through national member bodies), preparatory work (committee draft development), enquiry (stakeholder review), approval (formal voting by ISO members), and publication. This systematic approach ensures standards reflect practical implementation requirements rather than theoretical ideals.
Technical committees composed of national body representatives develop standards within specific domains. For example, ISO/IEC JTC 1/SC 27 handles information security, cybersecurity, and privacy protection standards—the committee responsible for ISO/IEC 27001 and related security management frameworks that enterprise buyers routinely require from vendors.
Why ISO-Recognized Standards Support Data Protection
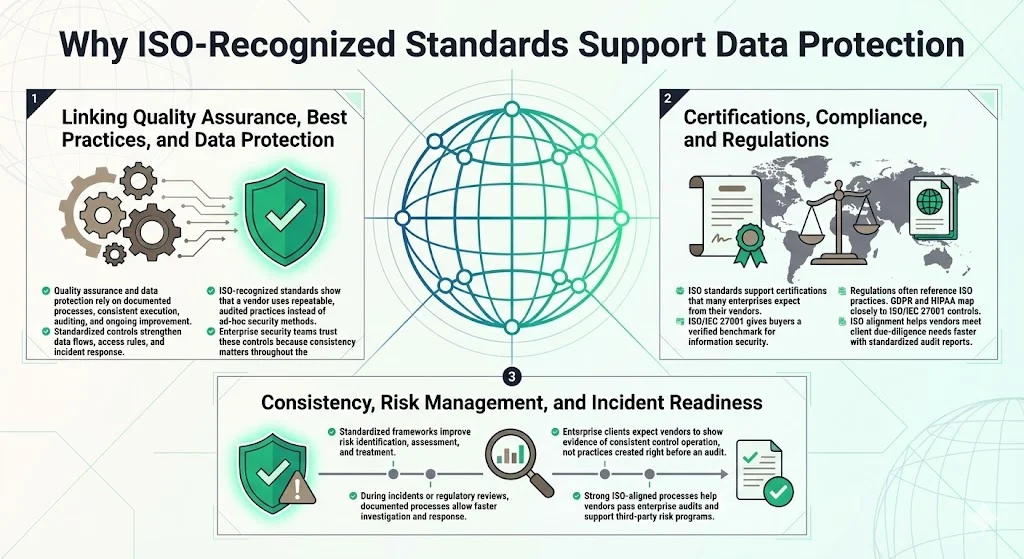
1) Linking Quality Assurance, Best Practices & Data Protection
Quality assurance and data protection share foundational requirements: documented processes, consistent implementation, regular auditing, and continuous improvement. When security controls follow standardized frameworks, data flows, access management, and incident response improve because practices are defined, measured, and refined rather than improvised.
For enterprise vendors, ISO-recognized standards demonstrate you've implemented audited, repeatable processes rather than ad-hoc security measures that vary by project or team. This matters during vendor assessments because enterprise security teams evaluate whether your controls will remain consistent across the engagement lifecycle—not just during the sales cycle.
2) Certifications, Compliance & Regulations
ISO standards often serve as the foundation for certifications that enterprise clients require during vendor qualification. ISO/IEC 27001 certification for information security management systems provides a credible, auditor-verified benchmark that reduces enterprise buyers' due diligence burden.
Many regulations reference or align with ISO standards because they represent globally-accepted baseline practices. GDPR's technical and organizational measures requirements align with ISO/IEC 27001 control objectives. HIPAA's administrative, physical, and technical safeguards map to ISO/IEC 27001's control framework. When vendors demonstrate ISO alignment, they're simultaneously addressing regulatory expectations that enterprise clients must satisfy through their vendor ecosystem.
Enterprise clients ask for compliance evidence during onboarding, annual reviews, and security incidents. ISO certifications provide standardized audit reports that speak the language enterprise security teams understand—reducing the need for custom assessments and accelerating vendor approval processes.
3) Consistency, Risk Management & Incident Readiness
Standardized approaches build consistency across operations, making risk identification, assessment, and treatment more systematic. When incidents occur—data breaches, regulatory inquiries, or audit findings—organizations with documented, standard processes can demonstrate control effectiveness, identify root causes, and implement remediation faster than those operating on informal practices.
This becomes critical when selling to enterprise clients with strict vendor management, audit, and supply chain requirements. Enterprise organizations increasingly face regulatory scrutiny over their vendor ecosystem. Third-party risk management programs evaluate whether vendors can demonstrate consistent security practices, respond effectively to incidents, and maintain audit trails that satisfy regulatory examination.
Organizations without standardized frameworks struggle during enterprise vendor audits because they cannot produce consistent evidence across different assessment periods or demonstrate how controls have operated continuously rather than being implemented just before audits.
Key ISO Standards That Matter for Data Protection
ISO/IEC 27001 – Information Security Management
ISO/IEC 27001 specifies requirements for establishing, implementing, maintaining, and continually improving an information security management system (ISMS). The standard requires organizations to conduct systematic risk assessments, implement controls based on identified risks, monitor control effectiveness, and demonstrate continual improvement through regular management review.
The current version, ISO/IEC 27001:2022, covers information security, cybersecurity and privacy protection—information security management systems requirements. This framework supports data protection by requiring documented policies for data classification, access control, encryption, incident response, business continuity, and vendor management.
ISO/IEC 27001 Type I certification demonstrates your controls were designed appropriately at a point in time. Type II certification—requiring a minimum observation period of three to twelve months—demonstrates controls operated effectively over time. Enterprise buyers increasingly require Type II certification because it provides evidence of sustained control effectiveness rather than point-in-time implementation.
ISO/IEC 27002 provides implementation guidance for the controls referenced in ISO/IEC 27001, offering detailed practices for implementing access controls, cryptography, physical security, and operations security that support data protection objectives.
ISO/IEC 20000-1, ISO 22301, ISO 8000 (as examples)
Beyond information security, several ISO standards directly impact enterprise data operations, service delivery, and business continuity:
ISO/IEC 20000-1 addresses IT service management, establishing requirements for planning, designing, transitioning, delivering, and improving services. For vendors managing customer data through service delivery, this standard demonstrates systematic service management practices that reduce operational risk.
ISO 22301 covers business continuity management systems, requiring organizations to identify threats, assess impacts, and implement controls ensuring critical operations continue during disruptions. Enterprise clients evaluate vendor business continuity capabilities because vendor failures can cascade into their own operations—particularly for SaaS providers or critical service vendors.
ISO 8000 addresses data quality and master data management, establishing principles for data accuracy, consistency, and completeness. While less widely adopted than ISO/IEC 27001, this standard becomes relevant for vendors handling enterprise master data or providing data integration services where data quality directly impacts business operations.
Why Choosing the Right Standard Matters for Vendors
Selecting appropriate ISO standards is not one-size-fits-all. Enterprise clients in financial services may require ISO/IEC 27001 plus sector-specific frameworks like PCI DSS. Healthcare organizations expect HIPAA compliance, which aligns with but extends beyond ISO/IEC 27001 requirements. Technology companies selling to European enterprises often need both ISO/IEC 27001 and GDPR compliance evidence.
Being certified to—or demonstrably aligned with—relevant ISO standards provides credibility during vendor onboarding, contract negotiations, and RFP responses. Organizations that can articulate their ISO alignment, provide audit reports, and map their controls to ISO frameworks reduce friction in enterprise sales cycles and differentiate themselves from competitors relying on unsubstantiated security claims.
Practical Steps for Companies Selling to Enterprise Clients
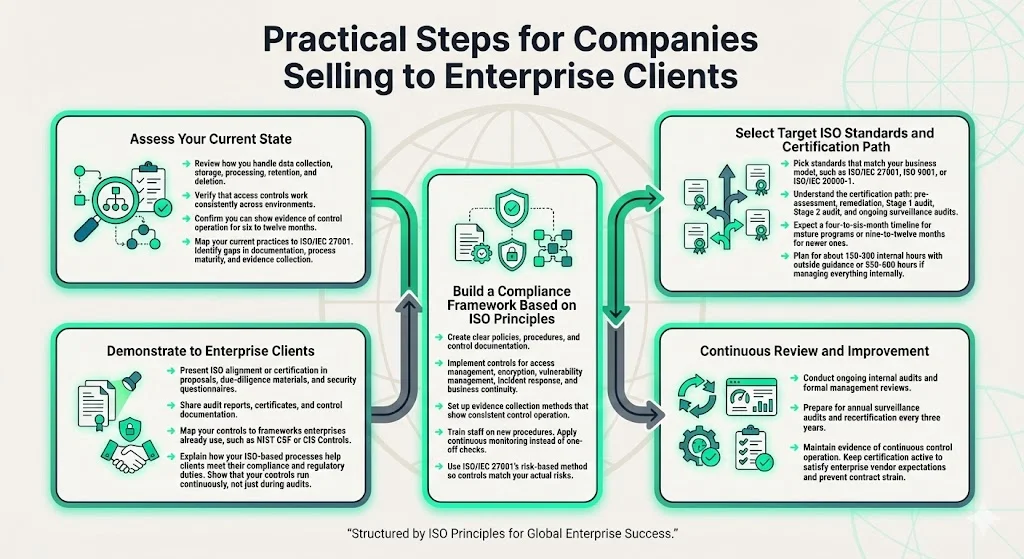
1) Assess Your Current State
Begin by reviewing your existing processes: Do you have documented standards for data collection, storage, processing, retention, and deletion? Are access controls consistently applied across environments? Can you produce evidence demonstrating how controls have operated over the past six to twelve months?
Map current practices to relevant ISO standard requirements. Identify gaps between your documented controls and ISO/IEC 27001 requirements. This gap assessment reveals which controls need development, which require better documentation, and which operate effectively but lack evidence collection mechanisms.
2) Select Target ISO Standard(s) & Certification Path
Based on your business model—SaaS provider, data processor, managed service provider—choose which ISO standards align with enterprise client expectations. ISO/IEC 27001 addresses information security management. ISO 9001 covers quality management systems. ISO/IEC 20000-1 focuses on IT service management.
Understand the certification process: selecting an accredited certification body, conducting pre-assessment audits, remediating identified gaps, undergoing Stage 1 audit (documentation review) and Stage 2 audit (implementation verification), and maintaining certification through annual surveillance audits and triennial recertification.
Certification timelines typically range from four to six months for organizations with mature security programs, extending to nine to twelve months for organizations building foundational controls. Budget 150-300 hours of internal effort for ISO/IEC 27001 implementation when working with experienced consultants or managed service providers, compared to 550-600 hours for self-managed approaches.
3) Develop a Compliance Framework Built on ISO Principles
Develop policies, procedures, and control documentation reflecting standardized practices. Implement controls addressing access management, encryption, vulnerability management, incident response, and business continuity. Establish evidence collection mechanisms demonstrating control operation over time—not just control existence.
Train personnel on new procedures and their role in maintaining controls. Implement continuous monitoring for critical controls so you can demonstrate ongoing effectiveness rather than periodic verification. Align your risk management approach with ISO/IEC 27001's risk-based methodology, ensuring controls are proportional to identified risks rather than implementing generic checklists.
4) Demonstrate to Enterprise Clients
Showcase your ISO alignment or certification in proposals, security questionnaires, and vendor assessment responses. Provide audit reports, certificate copies, and control documentation during due diligence. Map your implemented controls to frameworks enterprise clients use—NIST Cybersecurity Framework, CIS Controls, or industry-specific requirements.
Articulate how your ISO-aligned processes support enterprise clients' vendor compliance obligations, regulatory requirements, and risk management objectives. Position certification as evidence of operational discipline rather than a compliance checkbox—demonstrating that your security practices operate continuously, not just during audit periods.
5) Continuous Review & Improvement
ISO standards require continual improvement and periodic review. Surveillance audits occur annually. Recertification happens every three years. Internal audits must occur at planned intervals. Management review meetings must assess ISMS performance and improvement opportunities.
For enterprise clients, this ongoing commitment matters because they inspect vendor practices not just during onboarding but throughout the relationship. Vendors whose ISO certifications lapse or who cannot demonstrate sustained control operation face contract termination or additional audit requirements that strain the client relationship.
Common Misconceptions & Clarifications
"ISO" on Social Media & in Other Contexts
On social media platforms, "ISO" commonly means "in search of"—unrelated to standards or compliance. In photography, "ISO" refers to image sensor sensitivity settings. In computing, "ISO file" describes disc image formats. These colloquial uses create confusion when discussing ISO standards and certifications.
When enterprise buyers reference "ISO" in vendor requirements, they're specifically asking about the International Organization for Standardization frameworks—typically ISO/IEC 27001 for information security or ISO 9001 for quality management. Clarify which ISO standard applies to avoid misunderstanding scope and requirements.
"ISO Certification Means You're Perfect"
Certification demonstrates you met the standard's requirements at the audit point in time and maintained controls during the observation period—not that you're immune to security incidents or operational failures. ISO/IEC 27001 certification means you've implemented a systematic approach to managing information security risks, not that no vulnerabilities exist.
Emphasize ongoing controls, continuous monitoring, and improvement mechanisms rather than certification as an end state. Enterprise clients understand that certified vendors can still experience incidents—what matters is whether your ISO-aligned processes enable effective detection, response, and remediation when issues occur.
One Standard Fits All?
Different industries, geographies, and business models require different ISO standards or complementary frameworks. Financial services organizations may need ISO/IEC 27001 plus ISO 22301 for business continuity. Healthcare vendors require HIPAA compliance, which extends beyond ISO/IEC 27001's baseline. European operations may require ISO/IEC 27701 for privacy information management alongside GDPR compliance.
Align with enterprise client expectations rather than pursuing generic certification. Understand which standards your target market requires, which frameworks their security teams use for vendor assessment, and which certifications accelerate rather than merely satisfy their procurement requirements.
Why Enterprise Buyers Care (and What This Means for You)
Enterprise buyers evaluate vendor supply chains based on risk reduction, consistent practices, audit trail quality, and compliance evidence availability. Their vendor risk management programs assess whether vendors can demonstrate standardized security controls, maintain documentation supporting regulatory examination, and respond effectively when incidents occur.
ISO alignment helps vendors stand out during procurement by reducing friction in vendor onboarding, simplifying due diligence requirements, and answering security questions before they're asked. When RFPs require "ISO/IEC 27001 certification or equivalent controls," vendors with active certifications bypass lengthy security assessments that delay contract execution.
Speaking the language of standardization, certification, compliance frameworks, and best practices increases enterprise buyer trust. Security teams staffed with CISOs, security architects, and compliance professionals evaluate vendors based on whether security claims can be independently verified through recognized standards rather than relying on marketing assertions about "bank-level security" or "military-grade encryption."
Organizations demonstrating ISO alignment signal operational maturity that resonates with enterprise buyers managing hundreds of vendor relationships. Rather than conducting custom assessments for each vendor, enterprise security teams can evaluate ISO audit reports, map certified controls to their risk frameworks, and make faster procurement decisions based on standardized evidence.
Conclusion
ISO stands for the International Organization for Standardization—the independent body developing globally-recognized standards that support data protection, operational consistency, and enterprise vendor readiness. With over 25,000 published international standards and over 800 technical committees driving continuous development, ISO frameworks provide the foundation enterprise buyers use to evaluate vendor security practices and compliance posture.
For companies selling to enterprise clients, investing in ISO alignment or certification represents a strategic move beyond compliance checkboxes. It demonstrates operational discipline, provides independently-verified evidence of control effectiveness, and positions your organization as a credible vendor capable of meeting stringent security and regulatory requirements.
Start with a gap assessment identifying how current practices map to ISO/IEC 27001 or other relevant standards. Determine which ISO frameworks align with your target market's expectations. Prepare to demonstrate not just certification status but sustained control operation through documented evidence, continuous monitoring, and systematic improvement—the operational reality that ISO standards require and enterprise buyers increasingly demand.
Frequently Asked Questions
1) What does ISO mean on social media?
On social media, "ISO" typically means "In Search Of." In compliance and security contexts, "ISO" refers to the International Organization for Standardization and its frameworks for quality management, information security, and operational best practices.
2) What does ISO stand for?
ISO stands for the International Organization for Standardization—an independent, non-governmental organization that develops globally-recognized standards across industries, technologies, and business processes.
3) What does ISO mean in the workplace?
In workplace contexts, "ISO" typically refers to adherence to an ISO standard such as ISO/IEC 27001 for information security management or ISO 9001 for quality management. It signals that the organization follows defined, audited processes and controls rather than ad-hoc practices.
4) What is the main purpose of ISO?
ISO's mission is to promote the development of standardization and related activities in the world, facilitate international exchange of goods and services, and develop cooperation in intellectual, scientific, technological and economic activity. The organization develops consensus-based standards that promote consistency, quality, safety, interoperability, and best practices across industries and geographies.



.svg)
.svg)
.svg)