Most organizations implement security controls reactively—patching vulnerabilities as they surface, granting access as requests arrive, approving changes under deadline pressure. This approach creates a fundamental gap between operational security and genuine control effectiveness—a gap that becomes apparent when auditors question the reliability of your financial systems, or when a single unauthorized change compromises data integrity across multiple applications.
Information Technology General Controls (ITGC) are controls that apply to all systems, components, processes, and data for a given IT environment, designed to ensure the proper development and implementation of applications, as well as the integrity of programs, data files, and computer operations. Unlike application-specific controls that govern individual software functions, ITGC establishes the foundational framework that makes all other controls reliable. Without strong general controls, the reliability of application-level controls may be compromised.
For organizations selling to enterprise clients, ITGC compliance directly influences trust, procurement velocity, and long-term partnership viability. ITGCs are crucial for financial reporting, data protection, and meeting regulatory requirements—without proper ITGCs in place, businesses become vulnerable to operational failures, data breaches, fraud, and the risks of non-compliance with regulatory standards like the Sarbanes-Oxley Act (SOX) or the EU's General Data Protection Regulation (GDPR). Enterprise buyers evaluate ITGC maturity during vendor assessments because weak controls signal systemic risk—not just to security, but to operational reliability and audit readiness.
This article examines ITGC compliance as a discipline: its core components, relationship to IT governance and risk management, implementation across key control domains, role in regulatory compliance, and strategic value for organizations serving enterprise markets.
What is ITGC? Core Concepts & Scope
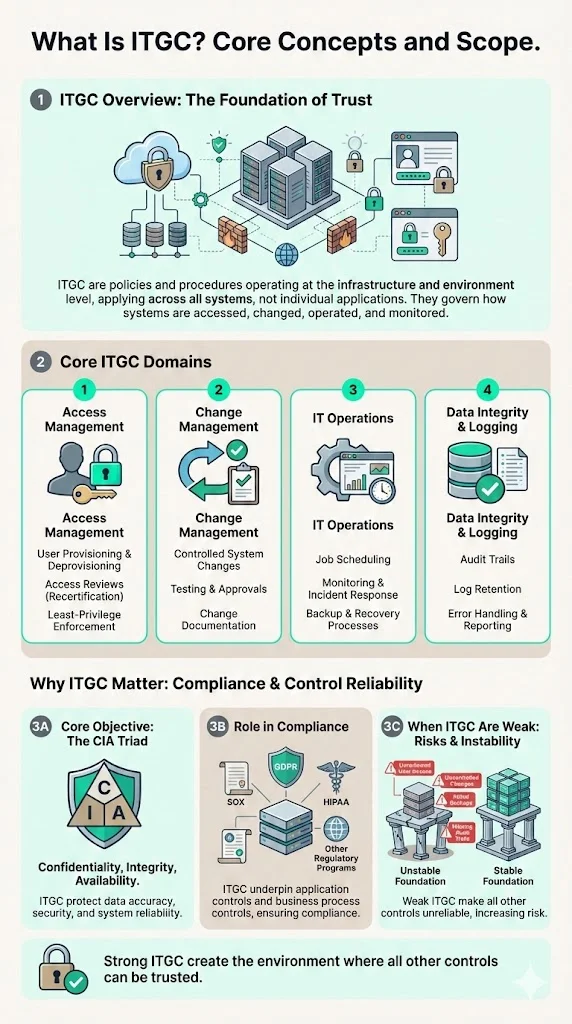
ITGC are a set of policies and procedures that help manage and protect an organization's IT systems, ensuring that systems function reliably, data remains secure and accurate, and any changes are properly controlled and documented. They operate at the infrastructure and environment level—governing access management, change procedures, operational processes, and data integrity mechanisms across all systems rather than within specific applications.
The fundamental objective: ensure the confidentiality, integrity, and availability of data and systems. These controls form the foundation for compliance with key regulatory frameworks like SOX, GDPR, HIPAA, and more. They underpin broader internal controls by creating a stable, secure IT environment where application-level controls and business process controls function as designed. When ITGC are weak or absent, even sophisticated application controls become unreliable because the underlying environment itself is unstable—user access may be unreviewed, changes may bypass testing, backups may fail, or audit trails may be incomplete.
Relation to IT Governance, Risk Management, and Compliance
ITGC serves as a key pillar of effective IT governance—the framework that ensures IT operations, change management, and system development follow defined, repeatable processes aligned with business objectives. As companies rely more on automation, cloud technologies, and cross-functional integrations, the role of ITGCs has become more central to an organization's overall governance and risk management framework.
From a risk management perspective, ITGC addresses fundamental threats: unauthorized access, data corruption, system failures, security breaches, configuration drift, and fraud. They provide structured mechanisms to identify, assess, and mitigate these risks through documented policies, technical controls, and continuous monitoring. These controls form the foundation for managing risk, protecting systems, and supporting compliance—they protect against data theft, unauthorized access, operational disruptions, and data breaches, influencing every layer of IT, from software deployment to user account management.
For compliance, ITGC supports both financial and data protection regulatory requirements. Organizations subject to SOX, HIPAA, GDPR, PCI DSS, or industry-specific regulations rely on ITGC to demonstrate that their IT environment produces reliable, trustworthy data. Auditors evaluate ITGC effectiveness before relying on automated application controls—if ITGC are deficient, the entire control environment may be deemed unreliable, regardless of how sophisticated individual application controls appear.
Key Domains / Types of ITGC Controls
ITGC are typically organized into domains that reflect different aspects of IT operations and security. Based on common audit frameworks and industry practice, these domains include:
1) Access Management / Logical Access Controls
Controls governing user authentication, authorization, account provisioning and deprovisioning, password policies, multi-factor authentication, privileged access management, segregation of duties, and periodic user access reviews. Logical Access Controls protect data and systems from unauthorized access. Effective access controls ensure that only authorized individuals can access systems and data appropriate to their role, and that access is promptly revoked when no longer required. Prioritizing controls like access management, change management, and segregation of duties (SoD) checks allows companies to automate the highest risk areas first to get the most benefit.
2) Change Management / Program Change Controls
Processes for authorizing, testing, approving, documenting, and implementing changes to applications, configurations, or infrastructure. Change Management Controls ensure changes to systems and applications are authorized and tested. Change management controls prevent unauthorized or inadequately tested modifications from introducing vulnerabilities, causing system instability, or compromising data integrity. They require documented change requests, impact assessments, testing evidence, approval workflows, and post-implementation reviews.
3) System Development & Implementation / Program Development Controls
Controls ensuring that new systems, major updates, or custom development follow a secure development lifecycle with appropriate requirements definition, design reviews, security testing, user acceptance testing, authorization gates, and comprehensive documentation. These controls ensure that systems are built with security and compliance requirements embedded from the outset, rather than retrofitted after deployment.
4) IT Operations / Computer & Infrastructure Operations Controls
Controls covering system monitoring, incident response, job scheduling, backup and recovery procedures, disaster recovery planning, business continuity processes, capacity management, physical security, and environmental controls (power, cooling, fire suppression). IT Operations Controls manage day-to-day IT operations efficiently and securely. Operational controls ensure systems remain available, performant, and resilient against disruptions.
5) Data Integrity Controls
Processes ensuring data remains accurate, complete, and unaltered throughout its lifecycle—whether at rest, in transit, or during processing. Data integrity controls include audit trails, transaction logs, data validation routines, reconciliation procedures, backup verification, and recovery testing. These controls provide assurance that financial reporting data, customer information, and operational data can be trusted.
About 39% of audits spot gaps or evidence issues in ITGC testing—a reminder that just having controls in place isn't enough; you need to check them often, make sure they actually work, and fix them when they don't.
Role of ITGC Compliance in Audit Standards and Regulatory Compliance
For companies subject to Sarbanes-Oxley Act (SOX) Section 404, ITGC compliance directly affects the reliability of financial reporting. SOX requires management to assess and attest to the effectiveness of internal controls over financial reporting. Since most financial data flows through IT systems—ERPs, general ledgers, transaction processing systems—auditors must evaluate the IT controls supporting those systems. Regulatory frameworks like SOX require businesses to maintain effective ITGCs—these controls help businesses meet compliance requirements, avoiding costly penalties, fines, and reputational damage.
Without effective ITGC, automated application controls become unreliable. If access controls are weak, unauthorized users could manipulate financial data. If change management is absent, unapproved code changes could alter transaction processing logic. If backup procedures are inadequate, data loss could compromise audit trails. Auditors will not rely on application-level controls when the underlying IT environment cannot be trusted—resulting in expanded audit scope, qualified opinions, or material weaknesses.
Beyond SOX, ITGC supports compliance with broader regulatory regimes. GDPR requires organizations to implement appropriate technical and organizational measures to ensure data security and integrity. HIPAA mandates administrative, physical, and technical safeguards for electronic protected health information (ePHI). PCI DSS requires specific access controls, change management, and monitoring for systems handling cardholder data. ITGC compliance frameworks like SOX, ISO 27001, and COBIT provide structured approaches to governance—regular audits and continuous monitoring are critical for maintaining ITGC effectiveness.
For organizations serving enterprise clients, demonstrating robust ITGC compliance differentiates security posture and operational maturity. Enterprise buyers—particularly in regulated industries such as financial services, healthcare, and government—require evidence of effective controls during vendor due diligence. Strong ITGC demonstrates that your organization manages IT risk systematically, produces reliable data, and maintains audit readiness year-round rather than scrambling before audit engagements.
Implementing ITGC Compliance: A Step-by-Step Process
Implementing ITGC compliance requires structured methodology, cross-functional collaboration, and sustained commitment. The following five-step framework provides a practical approach, commonly applied in SOX compliance contexts but applicable to any ITGC initiative:
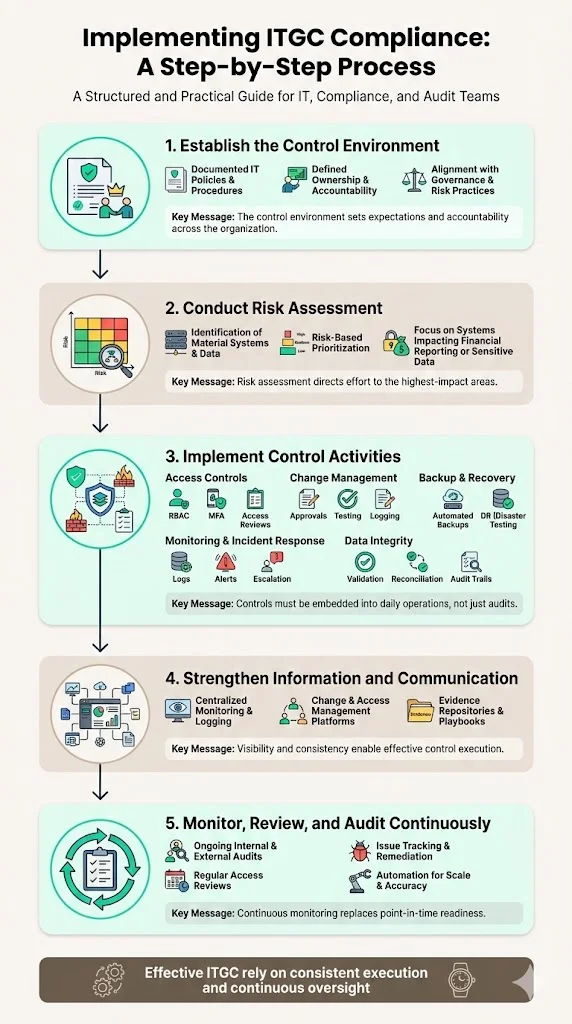
Step 1: Establish Control Environment
Define comprehensive policies, procedures, and process documentation governing IT operations, security, change management, access management, and incident response. Assign clear ownership and accountability across IT, finance, audit, and senior management. Ensure policies align with overall IT governance frameworks and risk management practices.
The control environment establishes the organizational foundation—defining expectations, responsibilities, and the tone from leadership regarding control discipline. Without documented policies and assigned ownership, control activities become inconsistent and difficult to audit.
Step 2: Conduct Risk Assessment
Identify which IT systems, infrastructure components, applications, and data repositories are material for financial reporting or other compliance objectives. Evaluate risks specific to each system: unauthorized access, privilege escalation, data corruption, uncontrolled changes, system failures, disaster scenarios, and regulatory impact.
A risk-based approach to ITGCs has become more important, given the number of applications and systems—IT and audit teams are increasingly prioritizing their efforts based on the risk profile of each system and application, focusing resources on those critical to the organization's business operations or that house sensitive data. Risk assessment focuses ITGC implementation efforts on high-impact areas, ensuring resources are allocated where they provide maximum risk reduction.
Step 3: Implement Control Activities
Deploy technical and procedural controls across all identified systems:
- Access controls: Implement user account management processes, role-based access control (RBAC), multi-factor authentication, privileged access management, segregation of duties matrices, and quarterly user access reviews.
- Change management: Establish change request workflows, require documented justifications and approvals, mandate testing in non-production environments, maintain change logs, and conduct post-implementation reviews.
- Data backup and recovery: Configure automated backup schedules, test recovery procedures quarterly, document disaster recovery plans, and maintain offsite or cloud-based backup storage.
- System monitoring and incident management: Deploy logging and monitoring tools, establish incident response procedures, define escalation paths, and maintain audit trails for security events and system changes.
- Data integrity measures: Implement transaction logging, data validation controls, reconciliation procedures, and audit trail protections to ensure data remains accurate and unaltered.
Control implementation must be documented, tested, and integrated into operational workflows. Ad hoc controls that exist only during audit periods do not constitute effective ITGC.
Step 4: Strengthen Information & Communication Systems
Deploy centralized platforms and tools to manage ITGC processes—system monitoring dashboards, log aggregation and analysis tools, change management ticketing systems, access review platforms, and compliance evidence repositories. Maintain comprehensive process documentation, security policies, operational procedures, and emergency response playbooks.
Effective information and communication systems ensure that control activities are visible, auditable, and consistently executed. They provide real-time insight into control effectiveness and enable rapid response to control failures or emerging risks.
Step 5: Monitor, Review & Audit Controls Continuously
Establish regular ITGC audit cadences—internal audits quarterly or semi-annually, external audits annually. Conduct periodic user access reviews (typically quarterly), system monitoring reviews, incident post-mortems, and control effectiveness assessments. Maintain comprehensive logs and evidence documentation for auditors. Track remediation of identified issues through formal corrective action processes. Document continuous compliance efforts to demonstrate sustained control effectiveness rather than point-in-time audit readiness.
Automation has become essential to improve accuracy, reduce human error, and enable organizations to apply controls at a broader scale—manual controls are now considered inefficient and error-prone, especially as IT environments become more complex. Advanced organizations implement automated compliance monitoring, alerting for control exceptions, and remediation workflow tracking to maintain continuous compliance visibility.
How ITGC Supports Security, Risk Management & Operational Resilience
ITGC directly strengthens security posture by enforcing access controls and logical access policies, reducing the risk of unauthorized access, privilege abuse, insider threats, and external breaches. Comprehensive user access reviews and segregation of duties controls prevent conflicts of interest and detect dormant or excessive privileges that create security exposure.
Change management and system monitoring controls help prevent insecure configurations, unapproved modifications, and configuration drift—common sources of vulnerabilities. By requiring testing, approval, and documentation before changes are deployed, change management reduces the likelihood of introducing security flaws or operational instability.
Data integrity controls, backup and disaster recovery procedures, and incident management processes safeguard against data loss, corruption, or ransomware attacks. Over 80% of data breaches in 2023 were linked to cloud storage, and 75% of organizations experienced at least one ransomware attack in the past year, with the average ransomware recovery cost reaching $2.73 million. Robust backup and recovery controls ensure business continuity and limit the impact of security incidents.
Operational controls and system operations safeguards ensure business continuity, uptime, and reliability—valuable for enterprise clients who expect stable, predictable service delivery. Documented disaster recovery plans, tested backup procedures, and incident response capabilities demonstrate operational maturity and resilience.
Proper IT governance and compliance frameworks also manage regulatory risks—financial reporting accuracy, data privacy obligations, and audit readiness—supporting trust with stakeholders, customers, and enterprise clients. ITGC provides the foundation for demonstrating that your organization operates responsibly, securely, and in compliance with applicable regulations.
Challenges & Common Pitfalls for Enterprises
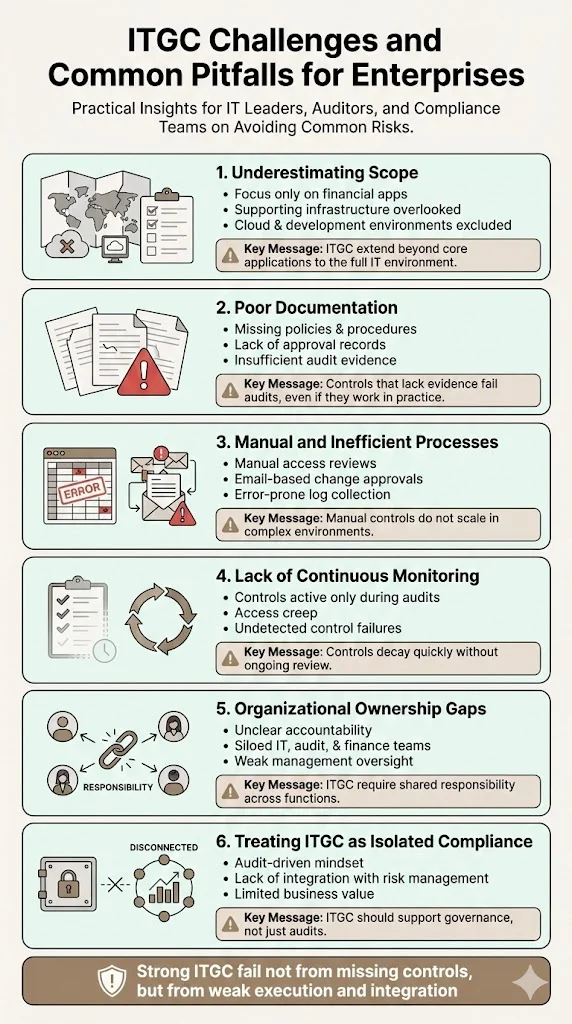
- Underestimating scope: Treating ITGC as a checklist exercise rather than a holistic governance framework leads to gaps in coverage. Organizations often focus on obvious systems (financial applications) while overlooking supporting infrastructure, cloud services, or development environments that also require controls.
- Poor documentation: Even when controls operate effectively in practice, inadequate documentation leads to audit findings. Auditors require evidence—policies, procedures, approval records, access reviews, change logs, testing results. Without comprehensive documentation, controls cannot be verified.
- Inefficient manual processes: Access reviews conducted via spreadsheets, change approvals tracked through email, or audit logs compiled manually are error-prone, inconsistent, and unsustainable as IT environments scale. Automated controls facilitate extensive coverage that is often impossible to achieve manually—organizations can now run automated checks on user access across multiple systems, identifying conflicts or anomalies within seconds instead of days.
- Failing to monitor continuously: Controls implemented during audit preparation but not maintained year-round become ineffective over time. Access permissions accumulate without review, changes bypass approval workflows, backups fail without detection, or incidents go unlogged. Continuous monitoring and periodic reviews ensure controls remain effective between formal audit cycles.
- Overlooking organizational factors: Without clear ownership across IT, audit, finance, and management, control activities drift or become inconsistent. ITGC requires cross-functional collaboration—IT teams implement technical controls, finance teams define materiality and financial reporting requirements, audit teams verify effectiveness, and management provides oversight and accountability.
- Isolated ITGC initiatives: ITGC should integrate with broader compliance and operational risk management strategies. When ITGC are treated as isolated audit requirements rather than foundational components of IT governance, they fail to deliver strategic value or support business objectives beyond compliance obligations.
For Companies Selling to Enterprise Clients: Why ITGC Compliance Matters
Enterprise clients—particularly in regulated industries such as financial services, healthcare, government, and payments—demand proof of robust internal controls, security, data integrity, and compliance before engaging vendors. During procurement and vendor risk assessments, buyers evaluate ITGC maturity as an indicator of operational reliability and security posture.
ITGC compliance demonstrates governance maturity—signaling that your organization manages IT systematically, maintains audit readiness, and operates with discipline. This builds trust, reduces buyer friction during due diligence, and supports long-term partnerships. Organizations with mature ITGC are perceived as lower-risk vendors, capable of meeting stringent security, operational, and regulatory expectations.
Robust ITGC ensures your internal operations—including financial reporting accuracy, audit effectiveness, and data security—remain solid, reducing the risk of breaches, audit failures, or compliance violations that could damage reputation or terminate customer relationships. For publicly traded companies or those pursuing IPO, ITGC compliance is non-negotiable for SOX attestation.
Strong ITGC can streamline due diligence during procurement or vendor evaluation processes. Enterprise buyers conducting security assessments, audit inquiries, or compliance validation benefit from well-documented controls, readily available evidence, and demonstrated continuous monitoring. This translates to fewer questions, faster contract negotiations, and reduced time-to-revenue.
Conclusion
ITGC compliance is more than a checkbox exercise or audit requirement. It represents a foundational framework connecting IT governance, security, risk management, and regulatory compliance. For enterprises—especially those selling to large, regulated clients—robust ITGC demonstrates operational maturity, builds stakeholder trust, and ensures that systems produce reliable, secure data.
Implementing ITGC requires thoughtful planning, comprehensive documentation, continuous monitoring, and cross-functional collaboration involving IT, audit, finance, and management teams. Organizations must move beyond reactive, checklist-driven approaches to establish systematic control disciplines embedded in operational processes.
The once familiar territory of manual control checks and standalone applications has grown into a complex landscape of interconnected cloud-based systems requiring nuanced attention and a strategic approach to designing ITGCs. In an environment of complex IT architectures, cloud adoption, and evolving regulatory demands, ITGC compliance helps organizations run securely, reliably, and responsibly—transforming compliance from burden to competitive advantage.
FAQs
1) What are the 4 domains of ITGC?
ITGC are typically grouped into four main domains: (1) Access to programs and data (logical access controls covering authentication, authorization, user provisioning, and access reviews); (2) Program change/change management controls (governing how software, configurations, and infrastructure changes are authorized, tested, approved, and documented); (3) Program development/system development lifecycle controls (ensuring secure development practices, testing, and authorization for new systems or major updates); and (4) Computer operations/IT operations (including backups, disaster recovery, system monitoring, incident management, physical security, and operational procedures).
2) What are the 5 steps of the ITGC process?
A common five-step approach for implementing ITGC compliance includes: (1) Establish control environment—define policies, assign ownership, document procedures; (2) Conduct risk assessment—identify material systems, processes, and risks; (3) Implement control activities—deploy access controls, change management, backups, monitoring, and data integrity controls; (4) Strengthen information and communication systems—implement centralized monitoring, logging, documentation, and evidence collection platforms; (5) Monitor, review, and audit controls continuously—conduct internal and external audits, periodic access reviews, incident reviews, remediation tracking, and maintain evidence for ongoing compliance verification.
3) What is the difference between SOC and ITGC?
SOC (Service and Organization Controls) refers to attestation reports—SOC 1, SOC 2, and SOC 3—that provide independent assurance about a service organization's internal controls to external stakeholders such as customers, auditors, or regulators. SOC reports document the design and operating effectiveness of controls related to financial reporting (SOC 1) or security, availability, confidentiality, processing integrity, and privacy (SOC 2). ITGC, by contrast, are the internal control practices covering the entire IT environment—infrastructure, operations, access management, change management, and data integrity. ITGC are foundational controls that support SOC compliance. In short: SOC is about external reporting and attestation for stakeholders; ITGC is about implementing and maintaining internal control practices to ensure system reliability, security, and compliance.
4) What does ITGC mean in audit?
In audit context, ITGC refers to the set of controls over IT systems and infrastructure that auditors evaluate to assess the reliability, security, and integrity of systems—especially those supporting financial reporting or compliance obligations. Auditors test ITGC to determine whether the IT environment is stable and secure enough to rely upon application-level controls. If ITGC are weak, missing, or poorly documented, auditors may not rely on automated application controls—resulting in expanded testing, additional manual verification, or audit findings such as control deficiencies, significant deficiencies, or material weaknesses. Effective ITGC enables auditors to gain comfort that systems produce accurate, complete, and trustworthy data throughout the audit period.



.svg)
.svg)
.svg)