Most organizations deploy perimeter defenses against external threats while overlooking a more insidious risk: keystroke capture from devices already inside the network. Keyloggers are malicious software or hardware tools that record keystrokes, potentially capturing sensitive information such as passwords, credit card numbers, and personal messages. When an attacker monitors every character entered on a keyboard, credentials for cloud infrastructure, financial systems, and proprietary databases become immediately compromised. This creates a fundamental security gap that bypasses authentication controls entirely—particularly problematic when infostealer malware logs and prior data breaches compile billions of credentials that enable credential stuffing attacks across multiple systems due to password reuse.
Understanding keylogging as both an attack vector and a compliance consideration requires examining how these tools operate, where they're deployed, and which controls effectively neutralize the threat.
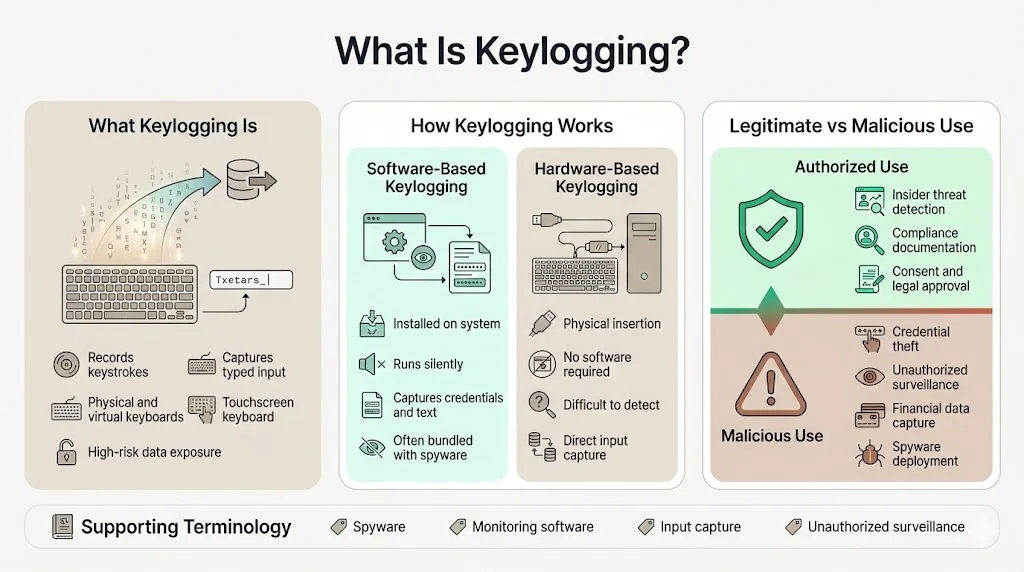
What is Keylogging?
Keylogging is the systematic recording of keystrokes to capture input data typed on physical or virtual keyboards. This technique operates through either software programs installed on target systems or hardware devices physically inserted between keyboards and computers. A keylogger is an insidious form of spyware. The captured data typically includes usernames, passwords, financial account numbers, confidential communications, and proprietary business information.
The distinction between legitimate and malicious use centers on authorization and intent. Organizations may deploy keylogging capabilities within authorized monitoring software for employee activity tracking, insider threat detection, or regulatory compliance documentation. It's also a legal and sometimes ethical tool to monitor the activity of employees when proper consent and legal frameworks exist. Malicious keylogging occurs when these capabilities are deployed without authorization—through spyware, remote access tools, or unauthorized surveillance—to intercept credentials and sensitive data for exploitation.
Related terminology includes spyware (malicious software that collects user data without consent), monitoring software (authorized tools for user activity tracking), input capture (technical method of intercepting keyboard events), and unauthorized surveillance (illegal monitoring without proper consent or legal authority).
How Keyloggers Work
Software-Based Keyloggers
Software keyloggers are programs or scripts installed on a computer system to monitor and record keystrokes, listening to events triggered within the computer and operating invisibly without visual indicators. These programs intercept keyboard input at various system levels—from application programming interfaces (APIs) that monitor keyboard events to kernel-level hooks that capture keystrokes before the operating system processes them. Once installed, software keyloggers continuously record typed characters, often logging timestamps, application contexts, and associated system activity.
The captured data allows attackers to access stolen information without having physical access to the compromised device. Most software keyloggers transmit captured data to remote servers via HTTP/HTTPS requests, email protocols (SMTP), or messaging platforms like Telegram. Campaigns distributing PowerShell and C# malware have been found active since early 2025, leveraging malvertising as a propagation vector, with infection chains executing modules in-memory to minimize forensic trail.
Distribution methods include phishing emails with malicious attachments, drive-by downloads from compromised websites, trojanized software bundled with legitimate applications, and exploitation of unpatched vulnerabilities. New versions of Snake Keylogger malware were behind over 280 million blocked infection attempts worldwide since the start of 2025, typically delivered through phishing emails containing malicious attachments or links to steal sensitive information from browsers by logging keystrokes and capturing credentials.
Hardware-Based Keyloggers
Hardware keyloggers are physical devices attached to target computers or keyboards, plugged into USB ports, placed between the computer and keyboard cable, or integrated into computer hardware itself. Unlike software variants, hardware keyloggers require physical access for installation but offer significant stealth advantages. They intercept electrical signals directly from keyboard connections before data reaches the operating system, making them invisible to software-based security tools.
Hardware keyloggers record keystrokes directly as they pass through the keyboard before they reach the computer's operating system, with some variations more challenging to detect as they do not rely on software-based methods. These devices store captured keystrokes in internal memory, which attackers later retrieve through physical access or, in advanced variants, wireless transmission. Detection requires physical inspection of ports, cables, and internal hardware—a control rarely implemented in standard security operations.
Hidden in Legitimate Software
Some commercially available monitoring tools and employee activity tracking platforms include keylogging features designed for authorized use. IT departments may deploy these applications for security monitoring, productivity tracking, or compliance documentation. When used within legal frameworks with proper employee notification, these tools serve legitimate business purposes. However, the same technical capabilities can be misused when deployed without authorization, consent, or legal justification—creating unauthorized surveillance that may violate employment laws, privacy regulations, and data protection requirements.
Types and Variants of Keylogging
Form-grabbing keyloggers specifically target web form inputs, capturing data as users submit information through browser forms rather than recording every keystroke. These variants intercept form submission events, capturing structured data like login credentials, payment information, and personal identifiers exactly as entered into web applications.
JavaScript keyloggers operate within web browsers through malicious scripts injected into compromised websites or served through malicious advertisements. Unidentified threat actors have been observed targeting publicly exposed Microsoft Exchange servers to inject malicious code into login pages that harvest credentials, with attacks targeting 65 victims in 26 countries worldwide. These scripts monitor keyboard events within the browser context, transmitting captured data to attacker-controlled servers without requiring installed software on the target system.
Kernel-level versus user-level keyloggers represent a technical distinction in implementation depth. User-level keyloggers operate within standard application permissions, hooking into operating system APIs that report keyboard events. The most difficult keyloggers to detect work at the very core of the operating system—at the kernel—requiring advanced software development skills and knowledge of writing kernel code, proving deeply challenging to detect and eradicate while remaining resistant to most standard security solutions. Kernel-level variants install as low-level system drivers with privileged access, intercepting keystrokes before the operating system processes input events—making detection significantly more difficult.
Remote access tools (RATs) frequently embed keylogging as one capability within broader surveillance frameworks. RATs (Remote Access Trojans) include keylogger functionality, allowing attackers to remotely monitor and control infected computers. These comprehensive malware platforms combine keystroke logging with screen capture, file exfiltration, webcam access, and persistent remote control—enabling sophisticated, long-term compromises.
Business Risks and Impact
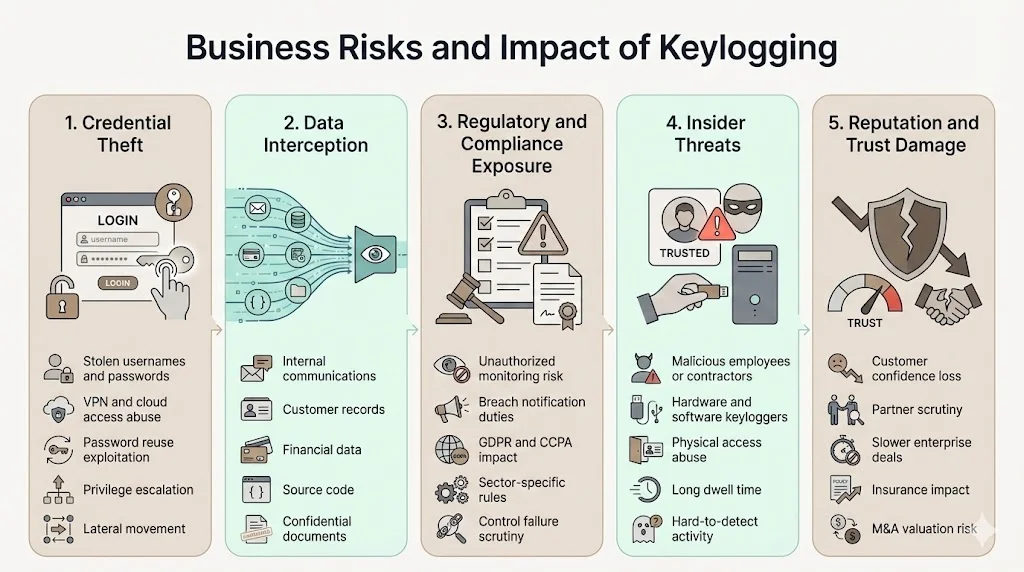
1) Credential Theft
Stolen credentials provide immediate unauthorized access to enterprise systems, cloud infrastructure, and administrative accounts. When keyloggers capture passwords as users authenticate to VPNs, email systems, or cloud services, attackers gain legitimate-appearing access that bypasses perimeter security controls. Password reuse creates systemic vulnerability—attackers with one valid credential can access dozens of services automatically, exploiting the fact that many users and employees reuse passwords across multiple systems. Compromised administrative credentials enable privilege escalation, lateral movement across networks, and access to sensitive data repositories that support broader attack objectives.
2) Data Interception
Beyond authentication credentials, keyloggers capture any data entered via keyboard: internal communications in email and messaging platforms, proprietary information typed into documents and spreadsheets, customer data entered into CRM systems, financial information including account numbers and transaction details, and source code or technical documentation. Multi-stage attack sequences targeting industries like finance, healthcare, technology, and media result in theft of passwords, browser data, and cryptocurrency wallets. This comprehensive data exposure extends far beyond initial credential theft, potentially compromising intellectual property, customer data, and confidential business information.
3) Regulatory and Compliance Concerns
Unauthorized monitoring through keyloggers may violate employment laws requiring employee notification of monitoring activities, depending on jurisdiction. Data breaches resulting from keylogger compromises trigger notification requirements under GDPR (affecting EU data subjects), CCPA (affecting California residents), and sector-specific regulations like HIPAA for healthcare information. Organizations face regulatory fines, mandatory breach notifications, and compliance violations when keyloggers enable unauthorized access to protected data categories. The regulatory exposure extends beyond the initial compromise to encompass inadequate security controls, insufficient monitoring, and failure to implement reasonable safeguards.
4) Insider Threats
Employees or contractors may deploy keyloggers for corporate espionage, competitive intelligence gathering, or personal financial gain. Malicious insiders with physical access can install hardware keyloggers on executive workstations, conference room computers, or shared terminals. Alternatively, insiders may deploy software keyloggers using existing system access, exploiting trusted positions to bypass security controls. These insider-initiated keylogging operations often persist longer than external attacks because authorized access patterns don't trigger anomaly detection systems.
5) Reputation and Trust
Public disclosure of keylogger-enabled breaches erodes customer confidence in organizational security practices. When customers learn that credentials or personal information were captured through keylogger compromises, they question whether the organization implements adequate security controls. Business partners and vendors may impose additional security requirements or terminate relationships following publicized incidents. The reputational damage extends beyond immediate customer relationships to affect enterprise sales cycles, insurance premiums, and valuation in M&A transactions.
Detection and Response for Businesses
Typical Signs Keylogging Might Be Present
If devices suddenly become slow, lag, or experience unusual resource usage even during basic tasks, it could indicate the presence of a keylogger or other malicious software. Unexpected outbound network connections, particularly to unfamiliar external IP addresses or domains, may indicate keystroke data transmission. Users may report unusual system behavior, including delayed keyboard response, unexpected process activity visible in task managers, or unfamiliar programs loading at system startup.
Physical inspection may reveal hardware keyloggers: USB devices inserted between keyboards and computers, inline connectors on PS/2 keyboard cables, or tampered keyboard housings. These physical indicators require deliberate inspection protocols rather than relying on software detection alone.
Tools and Techniques
Specialized anti-keylogger software detects keylogging behavior through behavioral analysis rather than signature-based detection. These tools monitor for processes attempting to hook keyboard input, unauthorized access to keyboard event streams, or suspicious inter-process communication patterns associated with keystroke capture. Endpoint detection and response (EDR) platforms provide comprehensive monitoring of system-level activity, flagging suspicious process behaviors including keyboard hooks, memory injection, and anomalous network communications.
Network monitoring tools identify unusual outbound data transmissions consistent with keystroke log exfiltration: small, frequent HTTPS POST requests to unfamiliar domains; SMTP traffic from non-email applications; or encrypted connections to suspicious IP addresses. Implementing egress filtering and monitoring outbound traffic patterns provides visibility into potential data exfiltration.
Forensic analysis of compromised systems requires examining running processes, loaded kernel modules, registry persistence mechanisms, and scheduled tasks. Memory forensics can identify keyloggers running entirely in RAM without persistent disk artifacts.
Incident Response
Upon detecting keylogger activity, immediately isolate affected machines from the network to prevent continued data exfiltration. Network segmentation controls should prevent lateral movement to additional systems. Conduct forensic analysis to determine the keylogger's installation method, persistence mechanisms, and data exfiltration destinations. This analysis informs containment scope and remediation priorities.
Rotate all credentials potentially exposed during the compromise period, prioritizing administrative accounts, privileged access credentials, and external service authentication. Enforce multi-factor authentication (MFA) across all systems to limit the utility of captured credentials. Review authentication logs for unauthorized access attempts or successful logins from unusual locations, devices, or time periods. Monitor for secondary compromises resulting from stolen credentials, including cloud infrastructure access, email account abuse, or financial system transactions.
Prevention Strategies
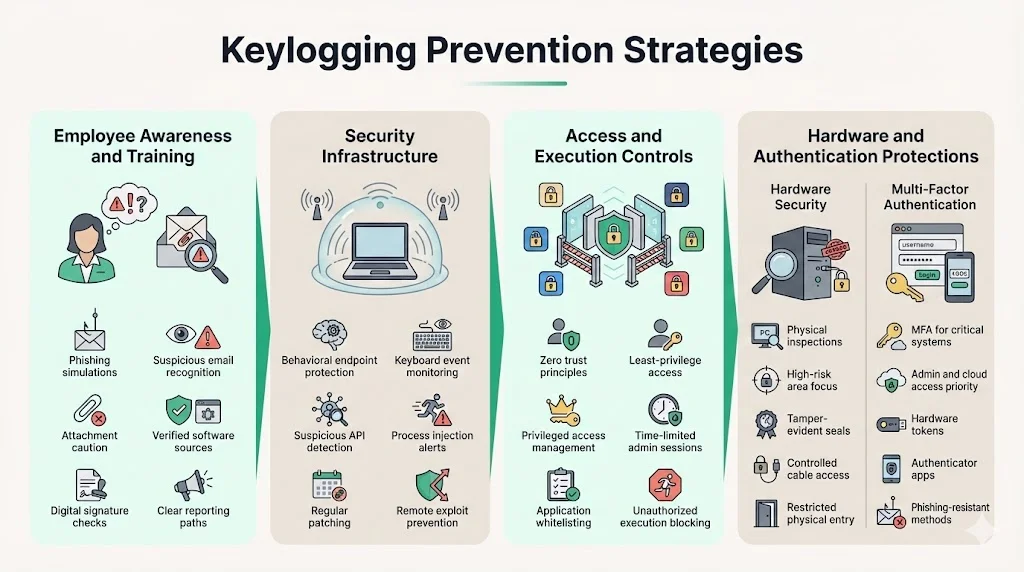
Employee Awareness and Training
Phishing simulations train employees to recognize malicious emails that deliver keylogger payloads. Regular training should emphasize verifying sender authenticity, scrutinizing unexpected attachments, and reporting suspicious communications. Educate users on secure download practices: obtaining software only from official vendor websites, verifying digital signatures on downloaded files, and avoiding third-party download sites that may bundle malware with legitimate applications.
Security Infrastructure
Endpoint protection platforms with behavioral monitoring detect keylogging activity based on process behavior rather than known malware signatures. Deploy solutions that monitor for keyboard event hooking, suspicious API calls, and unauthorized process injection. Regular vulnerability management through systematic patching eliminates exploitable weaknesses that attackers use to install keyloggers remotely. Prioritize patches addressing remote code execution vulnerabilities and privilege escalation flaws.
Implement zero trust architecture principles, eliminating implicit trust based on network location. Privileged access management (PAM) solutions enforce least-privilege access, time-limited credential elevation, and session monitoring for administrative accounts—limiting the impact of captured credentials. Application whitelisting prevents unauthorized software execution, blocking keylogger installation attempts that rely on user-mode processes.
Hardware Security
Establish physical inspection protocols for high-risk environments: executive offices, finance departments, and systems processing sensitive data. Train security personnel to identify hardware keyloggers during routine equipment inspections. Implement tamper-evident seals on critical systems, cable management that prevents inconspicuous device insertion, and locked-down physical access to prevent unauthorized hardware modifications.
Multi-Factor Authentication
MFA dramatically limits damage from captured credentials by requiring additional authentication factors beyond passwords. Even when keyloggers capture passwords, attackers cannot authenticate without possession of hardware tokens, mobile authenticator applications, or biometric factors. Prioritize MFA deployment for administrative accounts, cloud infrastructure access, email systems, and any application containing sensitive data. Implement phishing-resistant MFA methods such as FIDO2 hardware tokens or certificate-based authentication rather than SMS-based codes vulnerable to interception.
Legal and Ethical Considerations
The legal landscape surrounding keyloggers is strict—they must not be used to monitor devices without ownership, and those being monitored should be informed. Employer monitoring of employee devices requires clear policies disclosed during onboarding, explicit consent where legally required, and legitimate business justification. Jurisdictions vary significantly in permissible monitoring scope: some require active notification of monitoring activities, others permit monitoring with advance policy disclosure, and some impose strict limitations on monitoring personal communications even on company-owned devices.
When implementing authorized monitoring that includes keylogging capabilities, organizations must balance security objectives against privacy expectations and legal constraints. Document the business justification for monitoring, implement technical controls limiting monitoring scope to business-relevant activities, and establish clear policies governing data retention, access controls for monitoring data, and prohibited uses of captured information. Legal counsel should review monitoring practices against applicable employment law, data protection regulations, and industry-specific compliance requirements before implementation.
Conclusion
Keyloggers play a role in advanced persistent threats—sophisticated attacks involving several intrusion methods that extend over prolonged periods of months, quietly harvesting sensitive information with devastating effects on victim organizations. The threat operates across multiple vectors: software variants delivered through phishing and exploits, hardware devices requiring physical access, and JavaScript-based browser monitoring. Organizations face credential theft enabling unauthorized access, comprehensive data interception beyond initial password capture, regulatory compliance violations triggering mandatory notifications and fines, and reputational damage eroding customer trust.
Effective defense requires combining technical controls with organizational discipline. Endpoint detection and response platforms identify suspicious keyboard-monitoring behavior. Regular vulnerability patching eliminates remote installation vectors. Multi-factor authentication limits credential utility even when captured. Physical security protocols detect hardware implants. Employee awareness training reduces phishing success rates. Network monitoring identifies data exfiltration patterns. These layered controls create defense in depth, ensuring that failure of any single control doesn't enable complete compromise. Organizations treating security as continuous operational discipline rather than periodic compliance exercises maintain the vigilance required to detect and neutralize keylogging threats before significant damage occurs.
FAQs
Q1: What is keylogging?
Keylogging is the systematic recording of keyboard input to capture typed data including passwords, credentials, confidential communications, and sensitive information. It operates through software programs monitoring keyboard events within operating systems or hardware devices physically intercepting electrical signals from keyboards before they reach computers.
Q2: How does a keylogger work?
Software keyloggers hook into operating system keyboard event streams or install as kernel-level drivers intercepting keystrokes before applications process input. Hardware keyloggers physically insert between keyboards and computers, recording electrical signals directly. Both variants store captured keystrokes locally or transmit data to remote servers via HTTP, SMTP, or messaging protocols.
Q3: Is keylogging illegal for businesses?
Legality depends on authorization, consent, and jurisdiction. Employers may implement monitoring with proper disclosure, employee consent where required, and legitimate business justification. Unauthorized keylogging violates computer fraud statutes, wiretapping laws, and data protection regulations. Privacy laws vary significantly across jurisdictions regarding required notification, permissible monitoring scope, and employee consent requirements.
Q4: How do companies detect keyloggers?
Organizations deploy endpoint detection tools monitoring for keyboard-hooking behavior, unusual process activity accessing keyboard input streams, and suspicious inter-process communication patterns. Network monitoring identifies anomalous outbound data transmissions consistent with keystroke exfiltration. Physical inspection protocols detect hardware keyloggers on USB ports and keyboard connections. Performance degradation and unexpected system behavior may indicate software keylogger presence.
Q5: How can enterprises protect against keylogging?
Implement endpoint protection with behavioral monitoring detecting keyboard hooks and suspicious API calls. Deploy multi-factor authentication limiting credential utility when passwords are captured. Maintain regular vulnerability patching eliminating remote installation vectors. Conduct phishing awareness training reducing malicious email success rates. Establish physical security protocols for executive systems and high-risk areas. Monitor network traffic for unusual outbound connections indicating data exfiltration. Enforce privileged access management restricting administrative credential exposure.



.svg)
.svg)
.svg)