Most enterprises treat cybersecurity regulation as a compliance checkbox rather than an operational imperative. This approach creates significant exposure when incidents occur—particularly under the NIS2 Directive, where regulatory scrutiny now extends to thousands of organizations previously outside formal oversight. The NIS2 Directive represents the European Union's most comprehensive cybersecurity legislation to date, establishing binding security requirements across essential and important entities in critical sectors. Organizations serving EU markets must understand how NIS2 affects their operations, their clients, and their obligations for incident reporting, risk management, and continuous monitoring. This definition covers the directive's scope, core requirements, implementation challenges, and practical steps for achieving compliance ahead of the October 2024 transposition deadline now being enforced across member states.
What is NIS2? Understanding the Basics
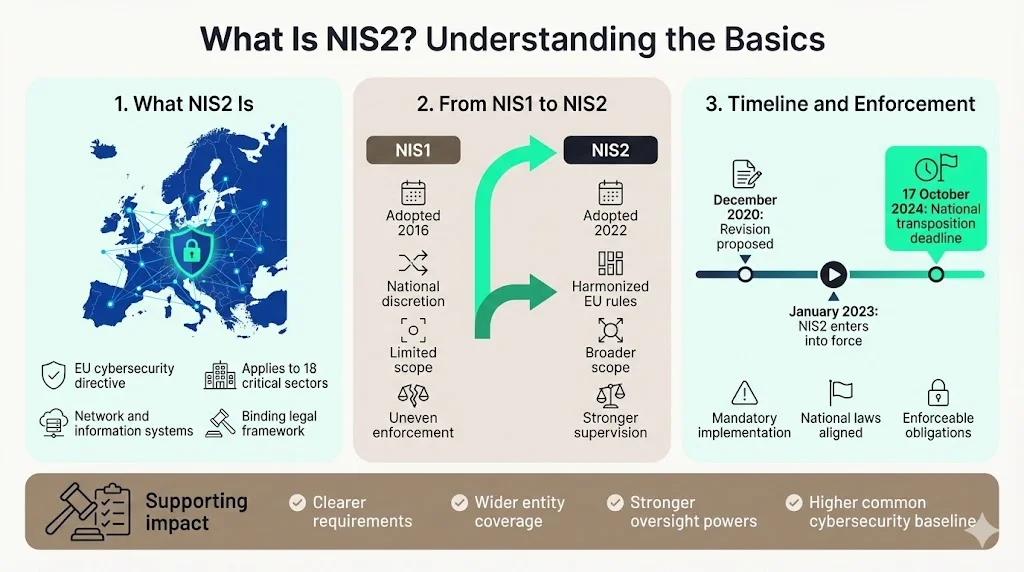
The NIS2 Directive establishes a unified legal framework to uphold cybersecurity in 18 critical sectors across the EU. Formally known as Directive 2022/2555, NIS2 replaced its predecessor, Directive 2016/1148 or NIS1, which represented the EU's first comprehensive cybersecurity legislation. NIS1 was aimed at boosting cybersecurity of network and information systems to safeguard vital services for the EU's economy and society, but member states retained considerable discretion in determining which entities fell within scope.
The Commission proposed revising NIS1 in December 2020, resulting in the adoption of NIS2, which came into force in January 2023, with member states required to transpose the directive into national law by 17 October 2024. The directive represents a fundamental shift in how the European Union approaches cybersecurity risk management, moving from discretionary national implementation to harmonized, binding requirements across all member states. NIS2 raises the EU common level of ambition on cybersecurity, through a wider scope, clearer rules and stronger supervision tools.
The Purpose Behind NIS2
NIS2 addresses critical gaps exposed by the evolving threat landscape and increased digitization across European economies. It requires member states to enhance their cybersecurity capabilities, while introducing risk management measures and reporting requirements to entities from more sectors and setting up rules for cooperation, information sharing, supervision, and enforcement of cybersecurity measures. The directive's primary objectives include strengthening network and information system resilience across critical infrastructure, establishing consistent cybersecurity practices that reduce regulatory divergence between member states, and improving incident detection and response capabilities.
The directive introduces accountability of the top management for non-compliance with cybersecurity risk management measures, bringing cybersecurity to the attention of the boardroom. This executive accountability provision fundamentally changes how organizations must approach cybersecurity—no longer a purely technical function, but a board-level governance matter subject to regulatory enforcement. The directive sets up a network of Computer Security Incident Response Teams (CSIRTs) to exchange information on cyber threats and respond to incidents, and creates the European cyber crisis liaison organisation network (EU-CyCLONe) to manage large-scale cybersecurity incidents or crises.
Key Concepts and Requirements of NIS2
Expanded Scope and Who it Applies To
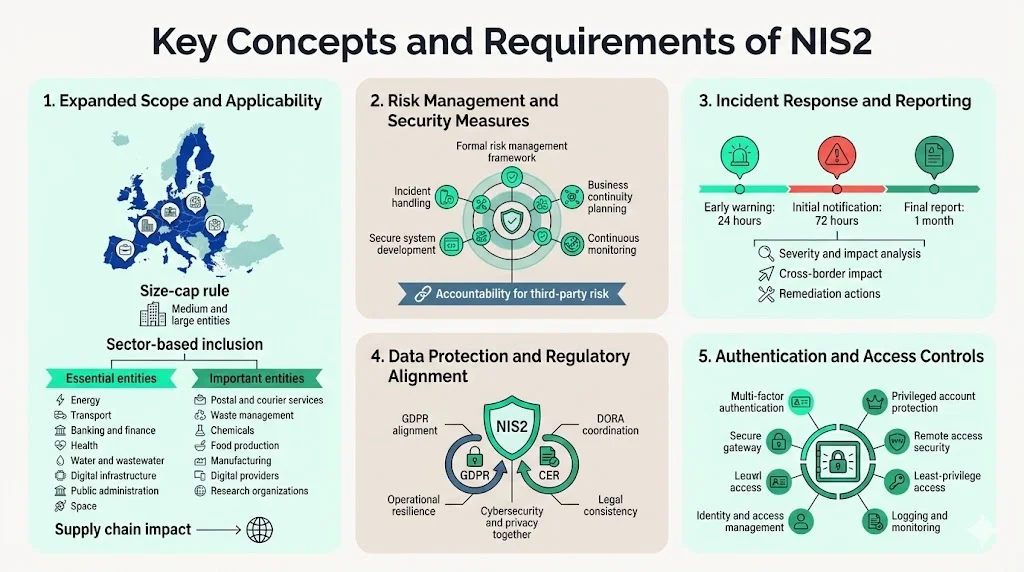
NIS2 dramatically expands the number of organizations subject to EU cybersecurity requirements. While under the old NIS directive member states were responsible for determining which entities would meet the criteria to qualify as operators of essential services, the new NIS2 directive introduces a size-cap rule meaning that all medium-sized and large entities operating within the sectors or providing services covered by the directive will fall within its scope. The directive categorizes covered organizations as either "essential entities" operating in highly critical sectors or "important entities" in sectors with significant economic or societal impact.
Essential entities include organizations in energy, transport, banking, financial market infrastructure, health, drinking water, wastewater, digital infrastructure, public administration, and space sectors. Important entities encompass postal and courier services, waste management, chemical production and distribution, food production and distribution, manufacturing of critical products, digital providers, and research organizations. Enterprises serving EU clients must assess whether they or their supply chain partners fall within scope based on organizational size, sector classification, and criticality of services provided.
Risk Management and Security Measures
NIS2 sets the baseline for cybersecurity risk management measures and reporting obligations across all sectors covered by the directive, such as energy, transport, health and digital infrastructure. Organizations must implement comprehensive risk management frameworks addressing incident handling, business continuity and crisis management, supply chain security, security in network and information system acquisition and development, and policies on assessing the effectiveness of risk management measures.
Covered entities must conduct regular vulnerability assessments, implement security controls proportionate to identified risks, and maintain continuous monitoring capabilities. Risk management obligations extend to supply chains—organizations remain accountable for cybersecurity risks introduced through third-party vendors, managed service providers, and technology partners. This supply chain accountability creates cascading compliance requirements for enterprises even when they fall outside NIS2's direct scope, as clients subject to the directive will impose contractual security obligations on their vendors.
Incident Response and Reporting
NIS2 establishes strict incident notification timelines designed to accelerate threat detection and coordinated response. Organizations must provide early warning notification within 24 hours of becoming aware of a significant incident, followed by an incident notification within 72 hours containing initial assessment of the incident including severity and impact, and a final report within one month providing detailed description, incident type, cross-border impact if relevant, and measures taken. These deadlines represent a substantial acceleration compared to previous regulatory expectations and require organizations to maintain robust incident detection and classification capabilities.
Data Protection and Privacy Compliance
NIS2 operates within a broader European regulatory landscape that includes GDPR, the Digital Operational Resilience Act (DORA) for financial services, and the Critical Entities Resilience (CER) Directive. The directive has been aligned with sector-specific legislation, in particular DORA and CER, to provide legal clarity and ensure coherence. Organizations must implement security measures that protect both operational continuity and personal data, requiring integrated compliance strategies that address cybersecurity and data protection requirements simultaneously.
Authentication Protocols and Access Controls
NIS2 mandates implementation of strong authentication mechanisms and access control procedures as fundamental security measures. Organizations must deploy multi-factor authentication for privileged accounts and remote access, implement least-privilege access principles limiting user permissions to necessary functions, establish identity and access management systems with regular access reviews, and maintain logging and monitoring of authentication events. These technical controls form the foundation of defensive cybersecurity architecture required under the directive.
NIS2 vs NIS1: What's Changed
The transition from NIS1 to NIS2 represents a substantial expansion in scope, enforcement, and harmonization. NIS2 expands coverage to a wider range of sectors than the previous NIS Directive, including postal and courier services, as well as the chemical and food sectors. Where NIS1 covered approximately 2,000 entities across member states, estimates suggest NIS2 will apply to 160,000+ organizations EU-wide.
NIS1 allowed member states significant discretion in identifying covered entities and implementing requirements, leading to substantial regulatory divergence. NIS2 eliminates much of this discretion through the size-cap rule and harmonized sector definitions, creating more consistent obligations across borders. Unlike the original NIS Directive, NIS2 introduces stronger enforcement powers for national authorities, including regular audits, security inspections, binding instructions, and administrative fines of up to €10 million or 2% of global annual turnover, whichever is higher. Management bodies are personally accountable for compliance, and governance failures may result in temporary bans or disqualification of individuals from leadership roles.
The directive also strengthens incident reporting requirements with faster timelines, expands supply chain security obligations, and establishes more robust cooperation mechanisms including EU-CyCLONe for coordinated crisis response. These changes reflect a fundamental shift in regulatory philosophy—from encouraging voluntary cybersecurity improvement to mandating baseline security capabilities backed by meaningful enforcement consequences.
Real-World Importance for Enterprises
Better Network Security Posture
NIS2 compels organizations to implement documented, auditable security controls across their technology infrastructure. This regulatory pressure drives genuine security improvements beyond compliance theater—risk-based vulnerability management programs, defense-in-depth architectures with layered security controls, continuous monitoring and threat detection capabilities, and formal change management and configuration control processes. Enterprises that help clients achieve NIS2 compliance while building actual security resilience differentiate themselves from vendors offering superficial compliance artifacts.
More Predictable Risk Management
The directive establishes structured frameworks for identifying, assessing, and mitigating cybersecurity risks. Organizations must document threat models specific to their operating environment, assess likelihood and impact of identified risks, implement controls proportionate to risk levels, and regularly reassess risk posture as threats evolve. This systematic approach integrates cybersecurity risk into broader enterprise risk management strategies, enabling more informed decision-making about security investments and risk acceptance.
Improved Business Continuity
Organizations with strong incident response capabilities and resilient system architectures experience fewer operational disruptions when security incidents occur. NIS2's emphasis on business continuity planning, backup and recovery procedures, and crisis management protocols creates infrastructure designed to withstand attacks and recover rapidly. For enterprise clients, reduced downtime translates directly to revenue protection, customer trust preservation, and competitive advantage maintenance.
Competitive Advantage
Enterprises demonstrating NIS2 compliance capability gain access to markets and clients that would otherwise remain closed. Organizations selling into critical sectors increasingly require vendors to document security controls, undergo security assessments, and accept contractual liability for security failures. Service providers with established compliance frameworks, experienced security personnel, and documented track records win competitive evaluations against technically capable competitors lacking compliance infrastructure.
Implementation and Compliance Challenges
Organizations face substantial challenges achieving NIS2 compliance within required timeframes. Common obstacles include determining precise scope—ambiguity remains around which organizational units and subsidiaries fall within coverage, how to classify entities operating across multiple sectors, and whether service relationships create direct obligations. Resource constraints affect most organizations, particularly mid-sized companies unprepared for formal cybersecurity requirements now facing demands for dedicated security personnel, compliance documentation, technical security implementations, and ongoing monitoring capabilities.
Technical debt accumulated over years of organic IT growth creates significant remediation challenges. Legacy systems lacking modern security controls, network architectures designed without security segmentation, inadequate logging and monitoring infrastructure, and incomplete asset inventories all require substantial investment to address. Supply chain complexity compounds these challenges—organizations must identify all critical vendors and service providers, assess third-party security postures, implement contractual security requirements, and monitor ongoing vendor compliance.
Coordination between legal, IT, security, and business units proves difficult for organizations lacking established governance structures. NIS2 requires executive engagement, cross-functional cooperation, and sustained investment—capabilities many organizations must develop while simultaneously implementing technical controls and meeting regulatory deadlines.
Best Practices for Enterprises Preparing for NIS2
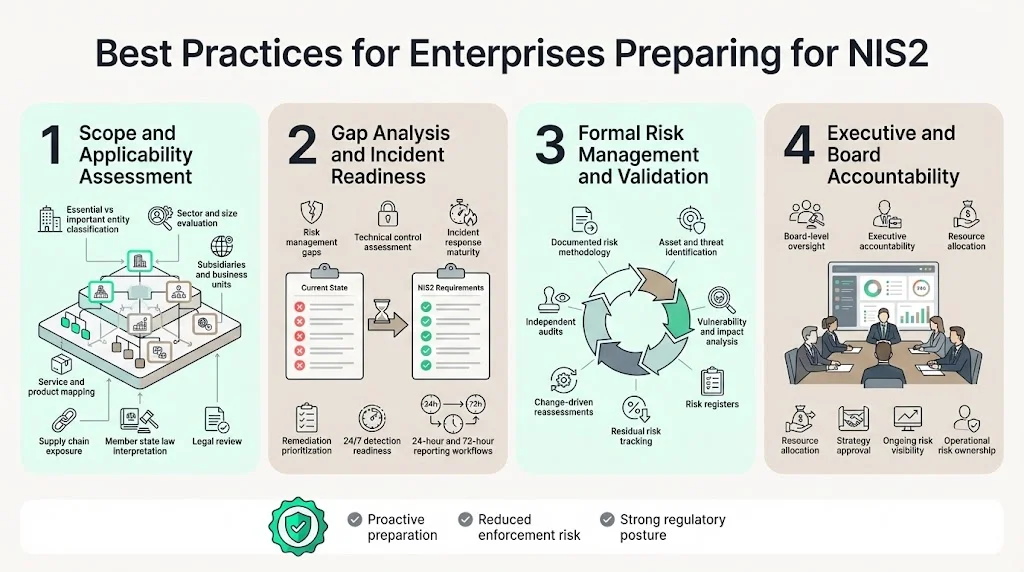
Organizations should begin with comprehensive scope assessment determining whether the organization qualifies as an essential or important entity based on sector, size, and criticality of services. Document all subsidiaries, business units, and service offerings that may trigger coverage. Engage legal counsel with NIS2 expertise to interpret member state transposition laws, as national implementations contain jurisdiction-specific requirements.
Conduct gap assessments comparing current security posture against NIS2 requirements across risk management frameworks, technical security controls, incident response capabilities, supply chain security measures, and governance structures. Prioritize remediation based on risk levels and regulatory deadlines. Establish incident response programs including 24/7 monitoring and detection capabilities, documented incident classification procedures meeting regulatory definitions, notification workflows meeting 24-hour and 72-hour deadlines, and cross-border incident coordination procedures.
Implement formal risk management programs with documented methodologies for identifying assets, threats, vulnerabilities, and potential impacts. Maintain risk registers tracking identified risks, implemented controls, and residual risk levels. Conduct regular risk assessments, particularly following significant changes to systems or threat landscape. Engage third-party security audits to validate control implementation and identify gaps before regulatory inspections occur. Independent assessors provide credibility with auditors and boards while identifying deficiencies internal teams may overlook.
Train management and boards on their personal accountability under NIS2. Cybersecurity is no longer a back-office technical issue—it is a board-level accountability matter and a core element of operational risk management. Executives must approve security strategies, allocate adequate resources, and demonstrate active oversight of cybersecurity risk management.
Case Example: Member States Implementing NIS2
The status of NIS2 implementation varies across EU member states, with Germany's final law potentially taking effect before the end of 2025, Italy having incorporated NIS2 into national legislation, and France still in the process of enacting necessary laws. The European Commission has launched infringement proceedings against EU member states who failed to meet the implementation deadline.
Germany expects NIS2 to affect approximately 30,000 companies nationwide, representing a massive expansion from previous cybersecurity regulations. Belgium, Denmark, Greece, Hungary, Italy, Malta, and Slovakia have enacted implementing legislation with enforcement now active. Other member states including Ireland, Austria, and Luxembourg continue drafting transposition laws while facing Commission pressure to complete implementation.
This fragmented transposition timeline creates complexity for multinational enterprises operating across multiple jurisdictions. Organizations cannot wait for complete harmonization—they must monitor implementation progress in each member state where they operate, assess jurisdiction-specific requirements as national laws emerge, and implement controls meeting the strictest requirements across their operating footprint. National implementations contain variations in scope definitions, reporting procedures, supervisory authority structures, and penalty frameworks that require jurisdiction-by-jurisdiction compliance analysis.
Conclusion
NIS2 represents the most significant expansion of cybersecurity regulation in European history, extending binding security requirements to tens of thousands of organizations previously outside formal oversight. The directive establishes baseline expectations for risk management, incident response, supply chain security, and executive accountability that fundamentally change how organizations approach cybersecurity operations. Organizations treating NIS2 as a compliance project rather than an operational transformation will find themselves unprepared for regulatory inspections, exposed to substantial penalties, and vulnerable to the incidents the directive aims to prevent.
Enterprises must begin compliance preparation immediately regardless of national transposition status in their jurisdictions. The obligations are clear, enforcement mechanisms are substantial, and regulatory scrutiny is inevitable. Organizations that implement genuine security controls meeting NIS2 requirements—not superficial compliance artifacts—build resilient infrastructure that protects operations, satisfies regulators, and creates competitive advantage in markets demanding demonstrated security capability.
Frequently Asked Questions (FAQ)
1) What is the NIS2 Directive?
The NIS2 Directive is EU-wide cybersecurity legislation establishing binding security requirements for essential and important entities across 18 critical sectors. It replaces the original NIS Directive with expanded scope, stricter requirements, and stronger enforcement mechanisms including administrative fines up to €10 million or 2% of global annual turnover.
2) Who does NIS2 apply to?
NIS2 applies to medium-sized and large organizations operating in covered sectors including energy, transport, health, digital infrastructure, banking, postal services, waste management, chemical production, food production, manufacturing of critical products, public administration, and space. Organizations meeting size thresholds in these sectors automatically fall within scope, with member states retaining limited discretion to include smaller entities providing critical services.
3) How is NIS2 different from NIS1?
NIS2 expands coverage from approximately 2,000 entities under NIS1 to an estimated 160,000+ organizations across the EU. It introduces harmonized sector definitions reducing member state discretion, establishes faster incident reporting timelines, implements personal liability for management bodies, and creates substantially higher financial penalties. The directive also strengthens supply chain security requirements and establishes coordinated crisis response mechanisms through EU-CyCLONe.
4) What are the penalties for non-compliance?
Administrative fines reach €10 million or 2% of global annual turnover, whichever is higher, for organizations failing to implement required security measures or meet reporting obligations. Management bodies face personal accountability including potential temporary bans or disqualification from leadership roles for governance failures. National competent authorities possess enforcement powers including regular audits, security inspections, and binding remediation orders.
5) How should enterprises prepare for NIS2 in 2026?
Organizations should conduct immediate scope assessments to determine applicability, perform gap analyses comparing current security posture against NIS2 requirements, implement risk management frameworks with documented methodologies, establish 24/7 incident detection and reporting capabilities, assess and secure supply chain relationships, and engage executive leadership in compliance oversight. Third-party security audits validate readiness before regulatory inspections occur. Preparation requires sustained investment in technical controls, governance structures, and security personnel—not last-minute documentation exercises.



.svg)
.svg)
.svg)