Most organizations allocate substantial resources to compliance management, yet remain vulnerable to the most sophisticated threat actors. This gap stems from a fundamental misunderstanding: baseline security requirements protect against routine threats, but advanced persistent threats (APTs) require defense-in-depth strategies designed to counter adversaries with significant capability and intent. Organizations handling Controlled Unclassified Information (CUI) associated with critical programs or high-value assets face adversaries actively seeking to exploit gaps in supply-chain security, system resilience, and monitoring capabilities.
NIST SP 800-172 provides recommended security requirements to protect the confidentiality, integrity, and availability of CUI when it is resident in a nonfederal system and organization and is associated with a high value asset or critical program. The standard addresses a documented reality: organizations entrusted with sensitive but unclassified data for federal agencies or defense programs become targets for nation-state actors and organized threat groups. For businesses positioning themselves to serve government contractors or enterprise clients with stringent security requirements, understanding and implementing NIST 800-172 represents the difference between baseline compliance and genuinely penetration-resistant architecture.
What is the National Institute of Standards and Technology (NIST) and its "800-series"?

The National Institute of Standards and Technology (NIST) functions as the federal government's authoritative source for cybersecurity and information security standards. Operating within the U.S. Department of Commerce, NIST develops frameworks, publications, and technical guidance that federal agencies—and increasingly, private-sector organizations—rely upon to establish defensible security postures.
The 800-series publications constitute NIST's computer security guidance library. These Special Publications (SPs) range from foundational risk management frameworks to specific technical implementation standards. The series includes SP 800-53, which catalogs security and privacy controls for information systems; SP 800-171, which defines baseline security requirements for protecting CUI in nonfederal systems; and SP 800-172, which establishes enhanced requirements for high-risk environments.
The enhanced security requirements in SP 800-172r3 supplement the security requirements in SP 800-171r3 and are intended for use by federal agencies in contractual vehicles or other agreements between those agencies and nonfederal organizations. This layered approach reflects the reality that not all CUI warrants the same protection intensity. NIST 800-171 establishes the baseline; NIST 800-172 addresses scenarios where baseline controls prove insufficient against adversaries with advanced capabilities.
What is NIST 800-172 — Purpose and Scope

NIST SP 800-172 contains recommendations for enhanced security requirements to provide additional protection for Controlled Unclassified Information (CUI) in nonfederal systems and organizations when such information is associated with critical programs or high value assets. The enhanced security requirements are designed to respond to the advanced persistent threat (APT) and supplement the basic and derived security requirements in SP 800-171.
The distinction matters. CUI encompasses sensitive but unclassified information that federal law, regulation, or government-wide policy requires safeguarding. This includes export-controlled technical data, law enforcement sensitive information, procurement-sensitive data, and dozens of other categories documented in the CUI Registry. When that CUI relates to critical defense programs, intelligence operations, or infrastructure assets that adversaries actively target, baseline protections become inadequate.
The enhanced security requirements give organizations the capability to achieve a multidimensional, defense-in-depth protection strategy against advanced persistent threats (APTs) and help to ensure the resiliency of systems and organizations. APTs represent nation-state actors or sophisticated criminal organizations conducting sustained, targeted campaigns to compromise specific systems or exfiltrate particular data sets. These adversaries possess technical expertise, funding, and patience that routine cybercriminals lack. Defense requires proactive monitoring, penetration-resistant architecture, and damage-limiting operations—capabilities that NIST 800-172 systematically addresses.
NIST 800-172 is not a standalone standard. The enhanced requirements apply only to components of nonfederal systems that process, store, or transmit CUI or that provide security protection for such components when the designated CUI is associated with a critical program or high value asset. The enhanced requirements supplement the basic and derived security requirements in NIST Special Publication 800-171. Organizations must first achieve NIST 800-171 compliance before layering on 800-172 enhanced controls. Federal agencies specify 800-172 requirements contractually when risk assessments indicate that baseline protections inadequately address threat profiles.
Structure of NIST 800-172: Controls and Control Families
NIST 800-172 organizes enhanced requirements using the same 14 control families established in NIST 800-171: Access Control; Awareness and Training; Audit and Accountability; Configuration Management; Identification and Authentication; Incident Response; Maintenance; Media Protection; Personnel Security; Physical Protection; Risk Assessment; Security Assessment; System and Communications Protection; and System and Information Integrity.
The Audit and Accountability, Maintenance, Media Protection, and Physical Protection families do not contain enhanced requirements because the baseline controls in those areas provide adequate protection for most scenarios involving CUI. The remaining ten families contain enhanced requirements addressing specific gaps that APTs exploit.
The current version, NIST SP 800-172 Revision 2 (published February 2021), contains 35 enhanced security requirements beyond the 110 baseline requirements in NIST 800-171 Revision 2. These requirements address advanced threat scenarios through multiple protection strategies:
Access Control enhanced requirements focus on restricting information system access based on demonstrable need-to-know and establishing dual authorization for high-risk operations—mechanisms that limit insider threats and credential compromise.
Configuration Management requirements emphasize control of system components throughout their lifecycle, including supply-chain risk management for hardware, software, and services that could introduce vulnerabilities.
Identification and Authentication enhanced controls address cryptographic protections for authentication credentials, multi-factor authentication resilience, and session management designed to resist sophisticated replay or hijacking attacks.
Incident Response requirements mandate capability to detect, analyze, and respond to indicators of advanced threats, including integration of threat intelligence and coordination with law enforcement or intelligence agencies when APT activity is identified.
Risk Assessment enhanced controls require continuous monitoring, vulnerability scanning integrated with threat intelligence, and assessment of supply-chain risks—recognizing that adversaries increasingly compromise trusted vendors to gain access to target systems.
Security Assessment requirements mandate regular penetration testing, red-team exercises simulating APT tactics, and assessment of organizational security posture against evolving threat landscapes.
System and Communications Protection enhanced controls address network segmentation, encrypted communications resilient to cryptanalysis, and protection mechanisms designed to limit lateral movement within compromised environments.
System and Information Integrity requirements emphasize integrity verification, real-time monitoring for anomalous behavior, and automated response capabilities that contain threats before significant damage occurs.
What Changed vs. NIST 800-171 — Why 800-172 Matters
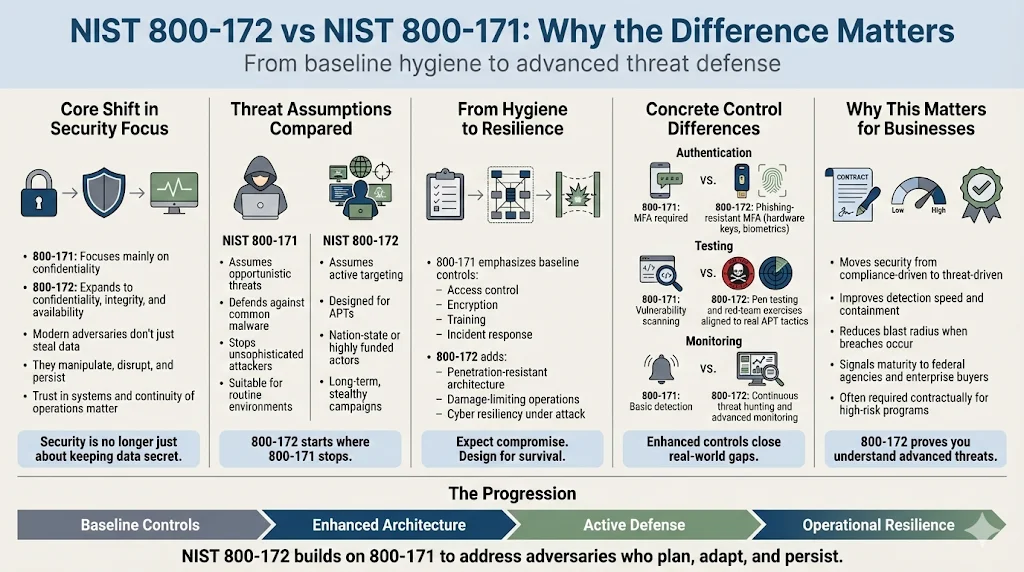
While the security requirements in SP 800-171 focus primarily on confidentiality protection, the enhanced security requirements in this publication address confidentiality, integrity, and availability protection. This expansion reflects operational reality: APTs do not merely exfiltrate data. Sophisticated adversaries manipulate data to undermine trust in information, disrupt operations by destroying system integrity, or establish persistent access that enables long-term intelligence collection.
NIST 800-171 establishes "routine" cybersecurity hygiene—access controls, encryption, security awareness training, incident response procedures. These controls defend against opportunistic threats, common malware, and unsophisticated adversaries. Organizations achieving 800-171 compliance demonstrate responsible data stewardship adequate for most commercial purposes.
NIST 800-172 presumes adversaries actively targeting the organization with significant resources. Enhanced requirements address penetration-resistant architecture (system designs that resist compromise even when adversaries possess sophisticated tools), damage-limiting operations (containment strategies that minimize impact when breaches occur), and cyber resiliency (capability to maintain essential functions despite active attacks).
Concrete examples illustrate the distinction. NIST 800-171 requires multi-factor authentication for network access; NIST 800-172 requires phishing-resistant multi-factor authentication using hardware tokens or biometrics that adversaries cannot remotely compromise. NIST 800-171 requires vulnerability scanning; NIST 800-172 requires penetration testing and red-team exercises simulating actual APT tactics, techniques, and procedures documented in frameworks like MITRE ATT&CK.
For businesses, adopting NIST 800-172 transforms security posture from compliance-focused to threat-focused. The standard requires active security testing, continuous threat hunting, supply-chain risk evaluation across vendor relationships, and damage-limitation strategies that assume breach will occur. Organizations implementing these enhanced controls reduce their attack surface, increase detection speed when incidents occur, and demonstrate to federal agencies or enterprise clients that they understand and address advanced threat scenarios.
Who Needs to Care: Which Businesses Should Pay Attention to NIST 800-172

Organizations handling CUI for federal agencies in contexts involving critical programs or high-value assets face potential contractual requirements to implement NIST 800-172. This includes defense contractors developing classified or sensitive military systems, aerospace firms working on critical infrastructure projects, research institutions conducting sensitive federally-funded studies, and technology companies providing cloud services or software to federal agencies with stringent security requirements.
The scope extends beyond direct federal contractors. Subcontractors throughout defense and federal supply chains encounter CUI. A software vendor providing tools to a prime defense contractor may process technical specifications, procurement schedules, or system architecture details that qualify as CUI associated with critical programs. Cloud service providers hosting data for federal agencies or defense contractors must implement controls commensurate with the sensitivity of hosted information.
Managed security service providers (MSSPs) and managed service providers (MSPs) supporting organizations with NIST 800-172 obligations inherit those requirements for any systems processing, storing, or transmitting CUI. Service providers cannot exempt themselves from enhanced controls simply because they operate infrastructure on behalf of clients—the CUI security requirements flow to any entity handling the information.
Businesses positioning themselves to serve enterprise clients with mature security programs increasingly encounter NIST 800-172 as a competitive differentiator. Large enterprises evaluating vendors for sensitive projects assess whether potential partners demonstrate security postures aligned with federal standards. Organizations that proactively achieve 800-172 compliance signal commitment to robust data protection that resonates with security-conscious clients, even outside government contracting contexts.
Impacts on Businesses Selling to Enterprise Clients / Government Contractors
When federal contracts specify NIST 800-172 compliance, businesses must implement all 110 baseline requirements from NIST 800-171 plus the 35 enhanced requirements from NIST 800-172. Failure to achieve and maintain compliance creates contract performance issues, potential False Claims Act liability if organizations misrepresent their security posture, and loss of eligibility to bid on future contracts requiring enhanced protections.
The operational impact extends across technology infrastructure, personnel, and processes. Enhanced controls often require investment in security information and event management (SIEM) platforms providing continuous monitoring capabilities, endpoint detection and response (EDR) tools that identify sophisticated malware, network segmentation architectures that contain lateral movement, and cryptographic protections for authentication credentials and sensitive data. Organizations need security personnel with expertise in threat hunting, penetration testing, and incident response—capabilities beyond standard IT administration.
Process requirements prove equally demanding. NIST 800-172 mandates regular penetration testing and red-team exercises, requiring engagement of specialized security firms or development of internal red-team capabilities. Supply-chain risk management requires documented evaluation of vendors providing hardware, software, or services, including assessment of their security postures and potential exposure to foreign adversaries. Incident response procedures must include integration with federal agency security operations centers and, in some cases, coordination with law enforcement or intelligence agencies when APT indicators appear.
The competitive advantage for compliant organizations is substantial. Defense and federal markets represent billions in annual contract value. Organizations achieving NIST 800-172 compliance differentiate themselves in procurement evaluations, demonstrate security maturity that reduces client risk, and position themselves to bid on high-value programs that competitors cannot access. Enterprise clients increasingly reference NIST standards when evaluating vendor security, making 800-172 compliance valuable beyond federal contracting.
Risk reduction represents perhaps the most significant business impact. APT compromises result in intellectual property theft, operational disruptions lasting weeks or months, regulatory investigations, and reputational damage that destroys client relationships. Organizations implementing NIST 800-172 controls substantially reduce breach probability and, when incidents occur, contain damage through resilience mechanisms and damage-limiting operations built into their architecture.
Long-term regulatory and compliance readiness improves. As cybersecurity threats evolve and regulations tighten—trends evident in recent federal rulemaking and state privacy laws—organizations with mature security programs adapt more readily to new requirements. NIST 800-172 compliance establishes security infrastructure, documented processes, and organizational capabilities that future audits or certifications build upon rather than requiring ground-up development.
Step-by-Step: How a Business Can Approach NIST 800-172 Compliance
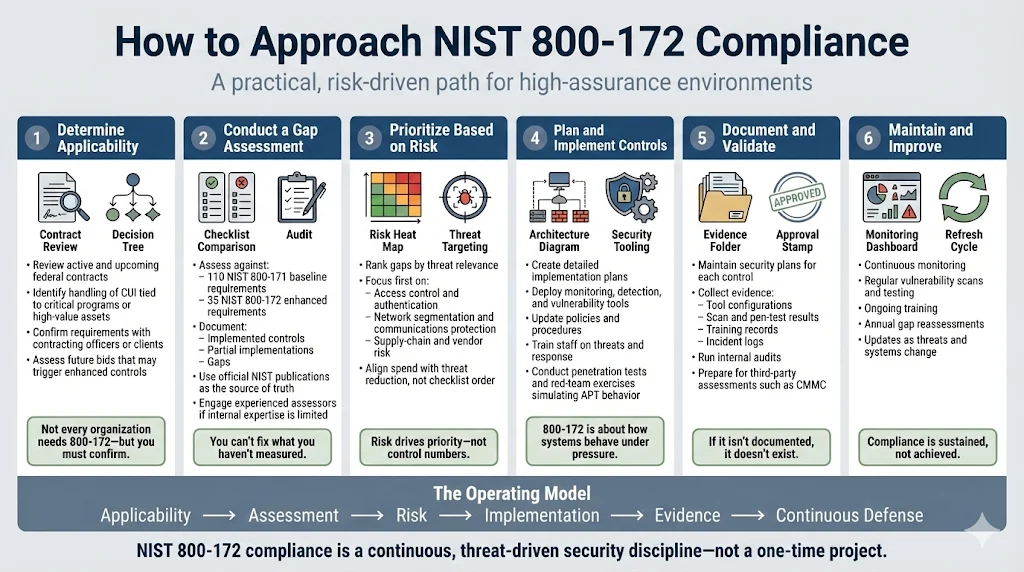
Step 1: Determine applicability. Review existing federal contracts, pending proposals, and client security requirements to identify whether your organization handles CUI associated with critical programs or high-value assets. Engage contract officers or client procurement teams to clarify whether NIST 800-172 applies. If pursuing federal contracts, assess whether target opportunities involve critical programs that will mandate enhanced controls.
Step 2: Conduct gap assessment. Systematically evaluate your current security posture against all 110 NIST 800-171 baseline requirements and 35 NIST 800-172 enhanced requirements. Document implemented controls, partially implemented controls, and missing controls for each requirement. Use the official NIST publications as authoritative sources—SP 800-171 Revision 3 and SP 800-172 Revision 2 (with Revision 3 under development as of late 2025). Gap assessments require security expertise; organizations lacking internal capabilities should engage qualified assessors familiar with federal compliance standards.
Step 3: Prioritize controls based on risk. Not all gaps present equal risk. Prioritize controls addressing your highest-risk threat scenarios: access controls and authentication mechanisms if credential compromise represents primary risk; network segmentation and communications protection if lateral movement concerns dominate; supply-chain risk management if vendor relationships introduce vulnerabilities. Risk-based prioritization aligns investment with actual threat reduction rather than arbitrary implementation sequences.
Step 4: Plan and implement required controls. Develop implementation plans specifying technology deployments, policy development, process changes, and personnel training required for each control. Deploy security tools providing continuous monitoring, vulnerability management, and incident detection capabilities. Define and document security policies covering access control, configuration management, incident response, and personnel security. Train staff on security procedures, threat awareness, and incident reporting. Conduct penetration testing and red-team exercises using qualified security firms or internal teams with APT simulation expertise.
Step 5: Document comprehensively. Federal assessments require documented evidence that controls exist and operate effectively. Maintain security plans describing how your organization implements each NIST 800-172 requirement. Collect evidence artifacts including security tool configurations, vulnerability scan results, penetration test reports, training completion records, incident response logs, and configuration management documentation. Conduct internal audits verifying controls operate as documented. Organizations pursuing Cybersecurity Maturity Model Certification (CMMC)—the Department of Defense assessment framework—will undergo third-party audits requiring extensive documentation.
Step 6: Maintain over time. NIST 800-172 compliance is not a one-time achievement. Continuous monitoring, periodic vulnerability assessments, regular penetration testing, and ongoing security awareness training maintain control effectiveness. Review and update controls as threat landscapes evolve, new vulnerabilities emerge, or system architectures change. Conduct periodic gap assessments—annually at minimum—to verify continued compliance and identify areas requiring improvement.
Challenges & Common Pitfalls for Businesses Adopting NIST 800-172
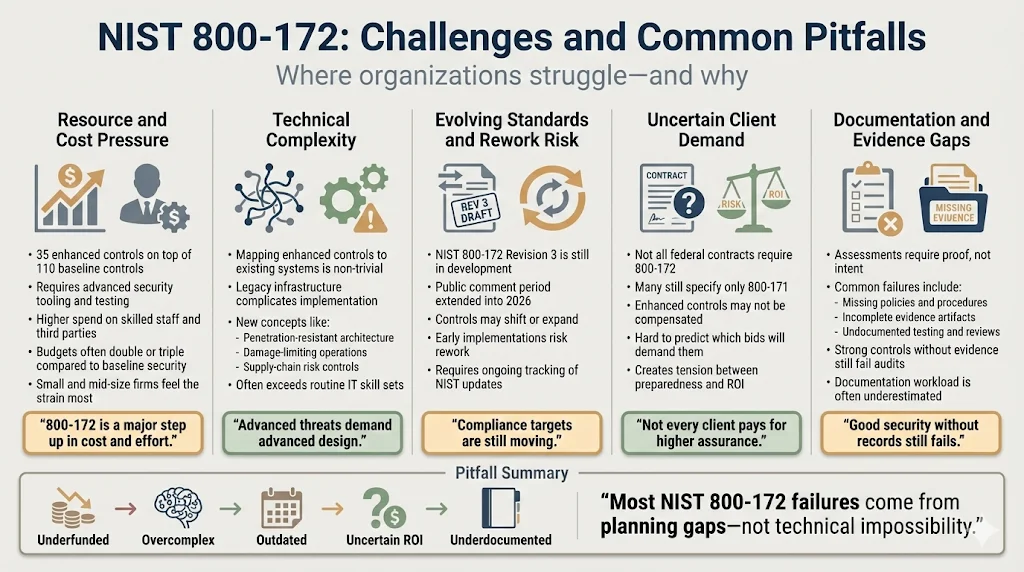
Resource requirements represent the primary challenge. Implementing 35 enhanced controls beyond the baseline 110 demands investment in security tools, skilled personnel, and third-party services (penetration testing, assessments, audits). Organizations accustomed to baseline IT security must often double or triple security budgets to achieve 800-172 compliance. Small and mid-size businesses particularly struggle with the cost burden when pursuing their first federal contracts requiring enhanced protections.
Technical complexity compounds resource challenges. Mapping 800-172 controls to existing systems, determining appropriate implementation approaches, and integrating enhanced controls with legacy architecture requires security expertise many organizations lack. Controls addressing supply-chain risk management, penetration-resistant architecture, and damage-limiting operations involve concepts beyond routine IT administration. Organizations must either develop internal expertise through hiring and training or engage consultants and managed security service providers with demonstrated NIST compliance experience.
The public comment period has been extended through January 16, 2026 for NIST SP 800-172 Revision 3, indicating the standard continues evolving. Organizations implementing controls based on Revision 2 face potential rework when Revision 3 finalizes. Staying current with standard revisions, understanding how changes affect compliance obligations, and planning for transitions between versions requires ongoing attention to NIST publications and federal contract requirements.
Client demand uncertainty creates business planning challenges. Not all federal contracts mandate NIST 800-172; many specify only 800-171 baseline requirements. Organizations investing significant resources in enhanced controls may discover that prospective contracts do not require—or financially compensate for—the additional security maturity. Businesses must balance proactive investment in differentiated security capabilities against the risk that clients will not value or require those capabilities.
Documentation burden consistently emerges as an implementation obstacle. Federal assessors require evidence that controls exist, operate effectively, and receive continuous oversight. Organizations often implement technical controls adequately but fail to document policies, procedures, testing results, and evidence artifacts that assessments require. The gap between actual security posture and documented security posture creates assessment failures despite adequate technical implementations.
How 800-172 Fits into Broader Cybersecurity / Compliance Strategies
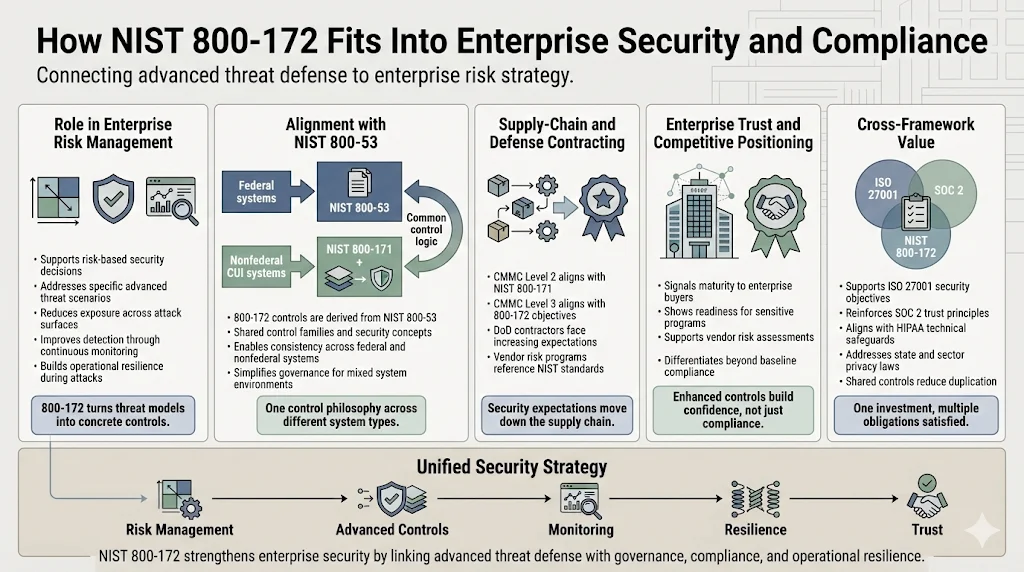
NIST 800-172 supports comprehensive risk management strategies by providing structured controls addressing specific threat scenarios. Organizations implementing enhanced requirements reduce vulnerabilities across attack surfaces, improve detection capabilities through continuous monitoring and threat intelligence integration, and establish resilience mechanisms that maintain operations despite active attacks. The standard integrates naturally with enterprise risk management frameworks, information security management systems (ISMS), and compliance programs addressing multiple regulatory obligations.
The relationship between NIST 800-172 and NIST SP 800-53 (Security and Privacy Controls for Information Systems and Organizations) proves particularly important. The enhanced security requirements are derived from the security controls in SP 800-53. Organizations operating both federal information systems (governed by 800-53) and nonfederal systems handling federal CUI (governed by 800-171/800-172) benefit from the alignment between these frameworks. Control families, protection strategies, and implementation guidance share conceptual foundations, allowing organizations to harmonize security approaches across diverse system portfolios.
Supply-chain security standards increasingly reference NIST frameworks. The Cybersecurity Maturity Model Certification (CMMC) program—mandatory for Department of Defense contractors—directly incorporates NIST 800-171 requirements at Level 2 and expects enhanced protections at Level 3 that align with 800-172 objectives. Vendor risk management programs at large enterprises frequently evaluate suppliers against NIST standards, creating market pressure for compliance even outside federal contracting contexts.
For businesses offering services to enterprise clients, positioning security maturity becomes a trust proposition. Communicating that your organization implements not just baseline NIST 800-171 controls but enhanced 800-172 requirements signals sophisticated understanding of advanced threats and commitment to defense-in-depth strategies. This differentiation proves valuable in competitive procurement evaluations, due diligence processes for strategic partnerships, and client security assessments that inform vendor selection.
Organizations pursuing multiple compliance frameworks (ISO 27001, SOC 2, HIPAA, state privacy laws) benefit from NIST 800-172 implementation because enhanced controls address security domains spanning regulatory requirements. Continuous monitoring, incident response capabilities, access controls, and encryption requirements in NIST 800-172 satisfy overlapping obligations in other frameworks. Mapping controls across frameworks and implementing shared security infrastructure reduces redundant investment while improving overall security posture.
Conclusion: What This Means for Business Leaders and Decision-Makers
Advanced persistent threats represent the most significant cybersecurity risk organizations handling sensitive information face. Nation-state actors, sophisticated criminal organizations, and well-resourced adversaries conduct targeted campaigns against defense contractors, federal suppliers, and enterprises managing high-value assets. Baseline security controls—while necessary—prove insufficient against adversaries with advanced capabilities and sustained intent.
The protection of Controlled Unclassified Information (CUI) resident in nonfederal systems and organizations is of paramount importance to federal agencies and can directly impact the ability of the Federal Government to successfully conduct its essential missions and functions. For businesses serving federal agencies, defense programs, or security-conscious enterprise clients, implementing NIST 800-172 enhanced controls addresses documented threat scenarios while demonstrating security maturity that opens market opportunities.
Organizations must treat NIST 800-172 compliance not as optional but as foundational for business development in federal and defense markets. Waiting until contract requirements arrive creates rushed implementations, incomplete control deployments, and documentation gaps that fail assessments. Proactive adoption—gap assessment, prioritized implementation planning, systematic control deployment—positions organizations to bid on high-value contracts, reduces risk exposure to advanced threats, and establishes security infrastructure that adapts as threat landscapes evolve.
The investment proves substantial: technology deployments, skilled personnel, third-party services, and ongoing maintenance. The return—reduced breach risk, competitive differentiation, access to federal and defense markets, and long-term compliance readiness—justifies that investment for organizations committed to serving clients with stringent security requirements. Security is not a checkbox exercise. It is the operational discipline that protects your organization, your clients, and the critical programs you support.
FAQs
1) What is the difference between NIST 800-171 and 800-172?
NIST 800-171 establishes baseline security requirements for protecting Controlled Unclassified Information (CUI) in nonfederal systems—110 controls addressing fundamental cybersecurity hygiene including access control, encryption, security awareness, and incident response. NIST 800-172 provides 35 enhanced security requirements supplementing the 800-171 baseline, specifically designed to defend against advanced persistent threats (APTs) when CUI is associated with critical programs or high-value assets. Organizations must implement all 800-171 baseline requirements before layering on 800-172 enhanced controls. While 800-171 focuses primarily on confidentiality protection, 800-172 addresses confidentiality, integrity, and availability through penetration-resistant architecture, damage-limiting operations, and cyber-resiliency mechanisms.
2) What is the purpose of NIST SP 800-172?
NIST SP 800-172 provides recommended security requirements to protect the confidentiality, integrity, and availability of CUI when it is resident in a nonfederal system and organization and is associated with a high value asset or critical program. The standard addresses threat scenarios where adversaries with sophisticated capabilities and significant resources actively target organizations to exfiltrate sensitive data, disrupt operations, or establish persistent access for long-term intelligence collection. Enhanced requirements give organizations capabilities to achieve defense-in-depth protection strategies, ensure system and organizational resiliency against APTs, and demonstrate to federal agencies that contractors implement security controls commensurate with the sensitivity and criticality of information they handle.
3) How many controls are in NIST 800-172?
NIST SP 800-172 Revision 2 (current version published February 2021) contains 35 enhanced security requirements that supplement the 110 baseline requirements in NIST 800-171. These enhanced controls span 10 of the 14 security requirement families established in NIST 800-171. Organizations implementing NIST 800-172 must satisfy all 145 total requirements (110 baseline plus 35 enhanced). NIST SP 800-172 Revision 3 is under development with a final public draft released September 2025 and comment period extended through January 2026; the finalized revision may adjust the number and structure of enhanced requirements to align with updates in NIST SP 800-171 Revision 3 and SP 800-53 Revision 5.
4) What is NIST 800-171 in a nutshell?
NIST SP 800-171 defines security requirements federal agencies specify in contracts, grants, or other agreements with nonfederal organizations to protect the confidentiality of Controlled Unclassified Information (CUI) when that information resides in nonfederal systems. The standard contains 110 security requirements organized into 14 control families addressing access control, awareness and training, audit and accountability, configuration management, identification and authentication, incident response, maintenance, media protection, personnel security, physical protection, risk assessment, security assessment, system and communications protection, and system and information integrity. NIST 800-171 establishes baseline cybersecurity requirements adequate for routine threat scenarios; federal agencies mandate enhanced NIST 800-172 requirements when CUI is associated with critical programs or high-value assets facing advanced persistent threats.



.svg)
.svg)
.svg)