Most organizations conduct security testing as an annual ritual rather than a structured discipline backed by documented methodology. This approach creates a fundamental gap between claimed security posture and actual control effectiveness—a gap that becomes apparent when regulators demand evidence, enterprise clients require proof of vulnerability management, or incidents expose weaknesses that testing should have identified months earlier.
NIST SP 800-115, titled "Technical Guide to Information Security Testing and Assessment," provides organizations with practical guidance for planning and conducting technical security tests and examinations, analyzing findings, and developing mitigation strategies. The National Institute of Standards and Technology (NIST), the U.S. federal agency responsible for developing cybersecurity standards and guidelines, published this document as part of its 800 series of computer security publications—a collection of technical guides addressing everything from control frameworks to incident response to encryption standards.
For companies selling to enterprise clients—particularly those in regulated industries or handling sensitive data—NIST SP 800-115 represents more than guidance. It establishes a recognized benchmark for security testing methodologies that sophisticated buyers expect vendors to reference when discussing vulnerability assessment, penetration testing, and control validation practices. When enterprise procurement teams evaluate security programs, they distinguish between vendors who conduct ad hoc testing and those who demonstrate systematic, evidence-based assessment aligned to established standards.
This article explains how NIST SP 800-115 supports data protection objectives, what the publication contains, how it complements other compliance frameworks, and how organizations—whether conducting assessments internally or providing security services—can leverage its methodology to strengthen security infrastructure and build client trust.
What is NIST SP 800-115?

Published September 30, 2008, NIST SP 800-115 provides the foundational methodology for technical security testing across federal information systems and has been widely adopted by private sector organizations seeking structured assessment approaches. The guide addresses finding vulnerabilities in systems or networks and verifying compliance with policies or requirements, though it is not intended as a comprehensive testing program but rather an overview of key technical testing elements with emphasis on specific techniques, benefits, limitations, and recommendations.
The intended audience includes system and network administrators and other technical staff responsible for preparing, operating, and securing systems and network infrastructures, while managers can use the information to facilitate technical decision-making processes; the material is technically oriented and assumes readers possess at least a basic understanding of system and network security.
The publication serves as the technical implementation guide for organizations already familiar with control frameworks like NIST SP 800-53 (security and privacy controls catalog) but needing specific guidance on how to test those controls rather than merely what controls to implement.
Why it matters for data protection and enterprise clients
The cybersecurity threat landscape has intensified pressure on enterprises to demonstrate not just the presence of technical security controls but documented evidence of their effectiveness over time. Enterprise clients—particularly those in healthcare, finance, government contracting, and regulated sectors—increasingly require vendors to show systematic vulnerability management, regular penetration testing, and audit-ready evidence of security assessment activities.
NIST SP 800-115 addresses this requirement by providing enterprises with a recognized standard for security testing efforts. When vendors reference 800-115 methodology in security documentation, enterprise buyers recognize the framework and understand the rigor it represents. This alignment becomes a competitive differentiator: organizations demonstrating structured, repeatable assessment processes based on established standards stand apart from competitors conducting informal or inconsistent testing.
For companies selling security products or managed services to enterprise clients, the standard offers a common language for discussing assessment methodologies, test planning requirements, evidence collection approaches, and reporting expectations. Rather than explaining proprietary testing processes that require client education and trust-building, vendors can reference 800-115 phases and techniques—terminology enterprise security teams already understand and value.
How NIST SP 800-115 works—Key Components & Methodologies
Phases of the assessment/testing process
NIST SP 800-115 structures security testing into distinct phases that ensure systematic coverage, appropriate authorization, and actionable outcomes:
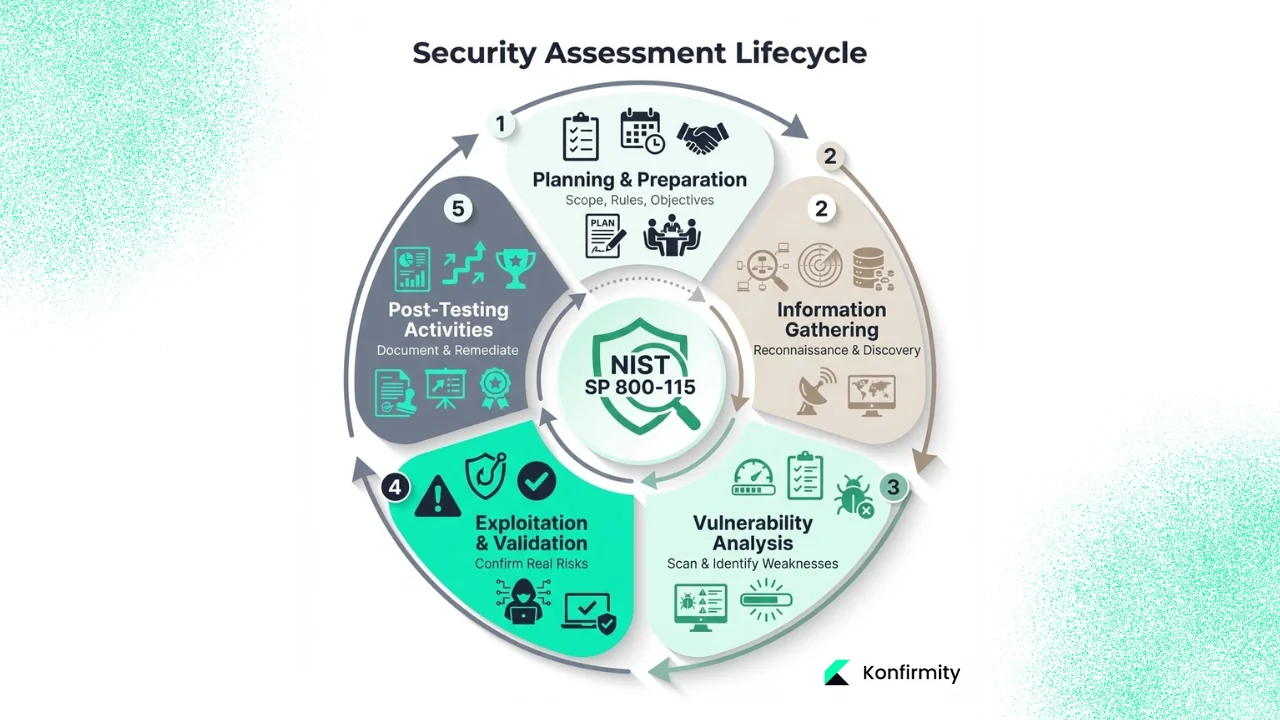
- Test planning & preparation: Organizations define assessment scope (specific systems, network segments, applications), establish rules of engagement detailing what testers may and may not do, identify objectives (compliance verification, pre-deployment validation, incident investigation), and document roles and responsibilities across security teams, system owners, and assessment personnel. This phase prevents scope creep, ensures stakeholder buy-in, and establishes legal and operational boundaries before any technical activity begins.
- Information gathering / target identification: Teams conduct reconnaissance to discover assets within scope, identify network topology and architecture, enumerate open ports and running services, map trust relationships and data flows, and collect publicly available information that attackers might leverage. This phase builds the foundation for understanding the attack surface without yet attempting exploitation.
- Vulnerability analysis: Assessors scan systems for known weaknesses, review system and application configurations against hardening standards, analyze patch levels and software versions, examine authentication mechanisms and access controls, and review security logs for indicators of existing compromise or misconfigurations. This phase identifies potential vulnerabilities requiring deeper validation.
- Exploitation / validation: Penetration testers attempt controlled exploitation of identified vulnerabilities to confirm they are genuine risks rather than false positives, demonstrate the potential impact of successful attacks, validate whether compensating controls effectively mitigate vulnerabilities, and determine the extent to which attackers could pivot to additional systems following initial compromise. This phase distinguishes theoretical weaknesses from exploitable security gaps.
- Post-testing activities: Organizations document findings in comprehensive reports containing executive summaries for leadership, technical appendices detailing vulnerability specifics and evidence, conduct root cause analysis to identify why controls failed rather than merely cataloging symptoms, develop prioritized remediation recommendations based on risk and business impact, and establish tracking mechanisms to verify fixes and prevent recurrence.
Techniques and technical security controls addressed
Within these phases, NIST SP 800-115 details specific techniques for validating security posture:
- Review techniques include documentation review (examining security policies, system security plans, architecture diagrams), log review (analyzing authentication logs, system logs, application logs for anomalies or security events), ruleset review (evaluating firewall rules, IDS/IPS signatures, router ACLs), system configuration review (comparing actual configurations against hardening baselines), and file integrity checking (verifying system files haven't been modified by attackers or misconfigurations).
- Target identification and analysis techniques encompass network discovery (identifying live hosts and network topology), port and service identification (determining what services are exposed), vulnerability scanning (automated identification of known vulnerabilities), wireless scanning (discovering wireless networks and assessing wireless security controls), and identifying software versions and patch levels across the environment.
- Validation techniques include password cracking (testing password strength and policy enforcement), penetration testing (simulated attacks following reconnaissance and vulnerability identification), social engineering assessments (testing human security controls), and physical security testing (when appropriate to scope).
The guide emphasizes evaluating how well technical security controls function in practice—not simply whether they exist on paper. This focus on control effectiveness rather than control presence distinguishes 800-115 from compliance checklists that verify documentation without validating operational security.
Relationship to vulnerability assessment and penetration testing
The publication explicitly addresses penetration testing, risk assessment, security assessment, security examination, security testing, and vulnerability scanning as interconnected elements of comprehensive security validation. Organizations frequently conflate these terms, but 800-115 clarifies their distinct purposes:
Vulnerability scanning represents automated or semi-automated identification of known vulnerabilities using tools that compare system configurations and software versions against vulnerability databases. These scans provide breadth—covering many systems quickly—but limited depth in validating whether vulnerabilities are genuinely exploitable given the specific environment and compensating controls.
Penetration testing involves manual, skilled assessment where testers attempt to exploit vulnerabilities, chain multiple weaknesses together, simulate attacker techniques, and demonstrate actual security impact. Penetration testing provides depth—thoroughly validating high-risk areas—but necessarily covers less breadth given the time and expertise required.
Organizations selling security assessment services or tools to enterprise clients benefit from mapping their offerings to these distinct phases and techniques. Rather than generic "security testing," vendors can specify they provide vulnerability scanning aligned with 800-115 target identification techniques, penetration testing following the exploitation/validation phase methodology, or comprehensive assessments encompassing all phases from planning through post-testing analysis and remediation tracking.
How NIST SP 800-115 supports data protection and compliance posture
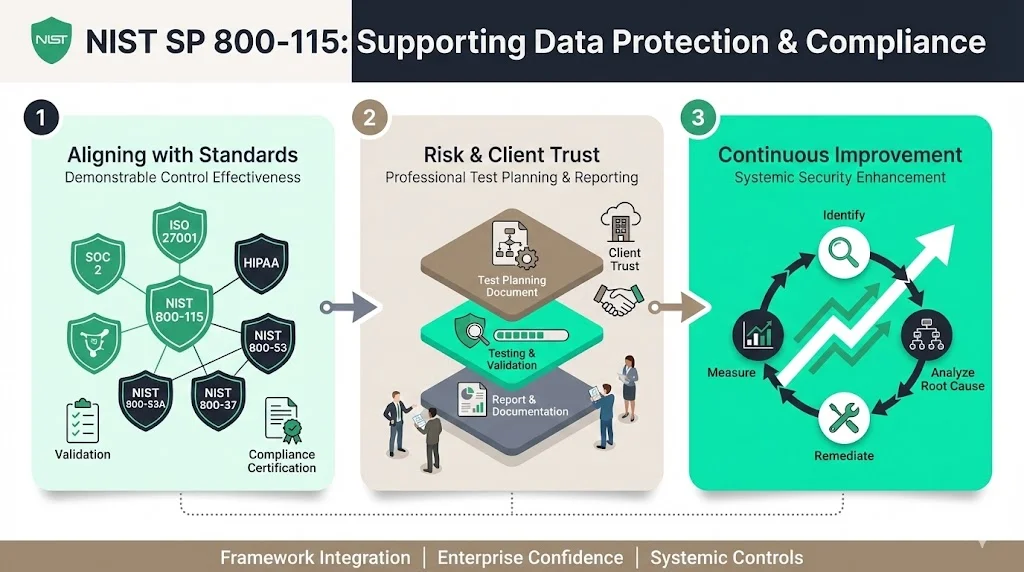
1) Aligning with information security standards and enterprise requirements
Enterprise data protection requirements extend beyond implementing technical security controls to demonstrating those controls function as intended under operational conditions. NIST created the SP 800-53A methodology for assessing security control effectiveness in federal information systems, and SP 800-115 offers recommendations for technical testing and examination techniques that can be used for many assessment methodologies and leveraged for many assessment purposes.
This relationship matters for organizations pursuing SOC 2, ISO 27001, HIPAA compliance, or other frameworks: controls must not only exist but demonstrably protect systems and data. NIST SP 800-115 provides the structured methodology to validate control effectiveness—moving from "we implemented encryption" to "we tested encryption implementation, verified key management procedures, confirmed data at rest and in transit remain protected, identified configuration weaknesses, and remediated gaps."
SP 800-53A was developed for use in conjunction with NIST SP 800-37, Guide for the Security Certification and Accreditation of Federal Information Systems, illustrating how 800-115 fits within a broader ecosystem of standards addressing what controls to implement (800-53), how to assess those controls (800-53A), and how to technically test systems (800-115). Organizations demonstrating familiarity with these interconnections signal sophisticated security programs to enterprise clients.
2) Linking test-planning and report-documentation to business risk and client trust
The test planning phase ensures assessment scope, objectives, rules of engagement, and stakeholder roles are documented before technical work begins. This planning prevents disruptions to production systems, establishes clear authorization boundaries preventing legal or operational complications, defines success criteria enabling objective evaluation of results, and secures stakeholder buy-in from system owners who might otherwise resist security testing.
For companies selling to enterprise clients, demonstrating structured test planning aligned with 800-115 methodology differentiates professional security programs from informal approaches. Enterprise procurement teams understand that vendors who define scope, document rules of engagement, and establish clear objectives before testing produce more reliable results and pose less risk to business operations.
Post-testing report documentation—a core requirement in 800-115—addresses the needs of multiple stakeholders: executive summaries communicate business risk and resource requirements to leadership, technical appendices provide engineers with specific vulnerability details and remediation guidance, and evidence documentation supports audit requirements when compliance frameworks demand proof of regular security assessments.
Organizations that produce audit-ready reports following 800-115 structure simplify enterprise clients' vendor risk management processes. When clients request evidence of security testing, vendors providing comprehensive reports with executive summaries, technical findings, evidence artifacts, and remediation tracking demonstrate security maturity that informal testing cannot match.
3) Supporting continual improvement of technical security controls
NIST SP 800-115 emphasizes root cause analysis: identifying not just individual vulnerabilities but the underlying process failures, configuration management gaps, or control weaknesses that allowed vulnerabilities to exist. This focus drives systemic improvement rather than point-in-time fixes.
For example, discovering a SQL injection vulnerability might lead to patching that specific flaw. Root cause analysis asks: Why wasn't secure coding training provided? Why didn't code review catch this issue? Why doesn't the web application firewall block SQL injection attempts? Why aren't vulnerability scans configured to detect injection flaws? Addressing root causes prevents entire classes of vulnerabilities rather than playing whack-a-mole with individual findings.
Organizations selling managed security services or assessment tools to enterprise clients can position offerings around this continuous improvement cycle. Rather than annual penetration tests that identify vulnerabilities but don't address why they occurred, services aligned with 800-115 methodology include root cause analysis, process recommendations, control effectiveness measurement over time, and integration with vulnerability management programs to track remediation and measure recurrence rates.
How companies can use NIST SP 800-115 when selling to enterprise clients
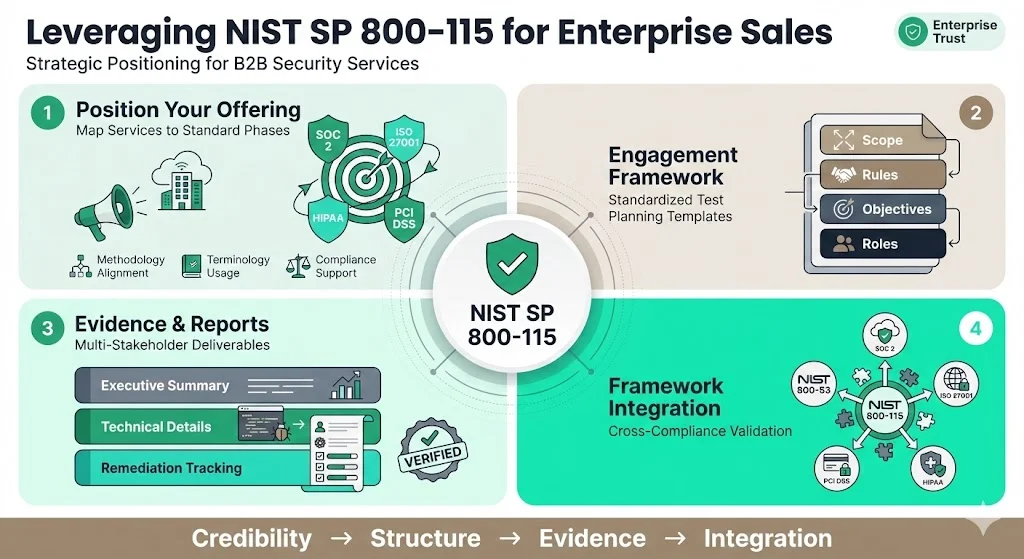
1) Positioning your offering around the standard
Map your security assessment services, vulnerability management platforms, or penetration testing capabilities directly to NIST SP 800-115 phases and techniques. When enterprise clients request information about your testing methodology, reference the 800-115 framework: your planning process follows the test planning & preparation phase, your reconnaissance activities align with information gathering techniques documented in the standard, your vulnerability identification incorporates both automated scanning and manual analysis consistent with 800-115 guidance, and your reporting structure mirrors the post-testing documentation requirements.
Use the terminology enterprise security teams recognize: technical security controls, vulnerability assessment, penetration testing, assessment methodologies, rules of engagement, target identification, exploitation, report documentation. This language signals you understand enterprise security requirements rather than speaking in marketing generalities.
Position your offering as helping enterprises meet both internal security objectives and external obligations: vendor risk management programs requiring evidence of supplier security testing, compliance frameworks demanding regular vulnerability assessments and penetration testing, cyber insurance policies requiring documented security validation, and regulatory requirements for technical security controls verification.
2) Creating a framework for engagement and test planning
Develop standardized test planning templates that reference NIST SP 800-115 methodology and include:
- Scope definition: Specific IP ranges, applications, systems, network segments, and user populations included in testing; explicit exclusions (production databases, third-party systems, out-of-scope networks); time windows when testing may occur; and restrictions on testing techniques (no DoS attacks, no social engineering, no physical security testing).
- Rules of engagement: Authorization documentation from system owners; emergency contact procedures if testing causes issues; data handling requirements (how vulnerability data and test evidence will be secured); and notification requirements (real-time alerts for critical findings versus consolidated reporting).
- Objectives and success criteria: What questions testing should answer (are credentials adequately protected? Can attackers pivot from the DMZ to internal networks? are security patches applied consistently?); what compliance requirements testing addresses (SOC 2 control validation, PCI DSS penetration testing requirements, GDPR technical controls verification); and how results will be measured and reported.
- Roles and responsibilities: Who conducts testing; who receives real-time notifications of critical findings; who authorizes scope changes; who validates remediation; and who maintains evidence for audit purposes.
By demonstrating structured test planning aligned with 800-115, your organization shows enterprise clients you approach security assessment as a discipline rather than an informal exercise, reducing their perceived risk of engagement.
3) Evidence and reporting for enterprise compliance and trust
Enterprise clients require security testing reports that serve multiple purposes: demonstrating vendor due diligence for their vendor risk management programs, providing evidence for their compliance frameworks (SOC 2, ISO 27001, HIPAA), supporting budget justification when remediation requires resources, and enabling their technical teams to efficiently remediate findings.
NIST SP 800-115 emphasizes producing reports with both executive summaries and technical appendices. Structure your deliverables accordingly:
Executive summary: Overall security posture assessment; count and severity distribution of findings; business risk context (what could attackers accomplish? what data could be compromised?); comparison to previous assessments showing improvement or degradation; and high-level remediation recommendations with estimated effort and priority.
Technical appendix: Detailed vulnerability descriptions; specific affected systems and software versions; proof-of-concept demonstrating exploitability; remediation guidance with configuration examples or patches; references to CVE identifiers, CWE categories, or OWASP guidance; and evidence artifacts (sanitized screenshots, log excerpts, scan output).
Remediation tracking: Vulnerability identifiers enabling tracking in issue management systems; severity ratings based on CVSS or similar frameworks; target remediation timeframes based on risk; and validation procedures to confirm fixes are effective.
When enterprise clients see reports structured this way, they recognize alignment with established standards and can efficiently integrate findings into their vulnerability management and compliance programs. Your testing becomes part of their security infrastructure rather than a standalone vendor deliverable requiring translation and interpretation.
4) Integrating with other standards/controls frameworks
Enterprise organizations rarely operate in a single-framework environment. They may pursue SOC 2 for SaaS clients, maintain ISO 27001 certification for international customers, comply with HIPAA for healthcare data, follow PCI DSS for payment processing, and map controls to NIST SP 800-53 for government contracts.
Position NIST SP 800-115 as the testing methodology that validates controls across all these frameworks. While 800-53 defines what controls to implement, 800-115 defines how to test them. ISO 27001 requires risk assessments and security testing; 800-115 provides the technical methodology. SOC 2 trust services criteria demand control effectiveness evidence; 800-115-aligned testing produces that evidence. HIPAA requires regular technical security control testing; 800-115 offers the structured approach.
When selling to enterprise clients, frame your offering as supporting their entire compliance portfolio: your assessment methodology aligns with NIST 800-115, your vulnerability findings map to relevant controls in 800-53 or ISO 27001 Annex A, your reports provide evidence for SOC 2 auditors or HIPAA assessments, and your remediation tracking integrates with their risk management processes regardless of framework.
This positioning helps clients understand your service provides leverage across multiple compliance objectives rather than addressing only a single requirement—increasing perceived value and justifying investment.
Challenges and practical considerations
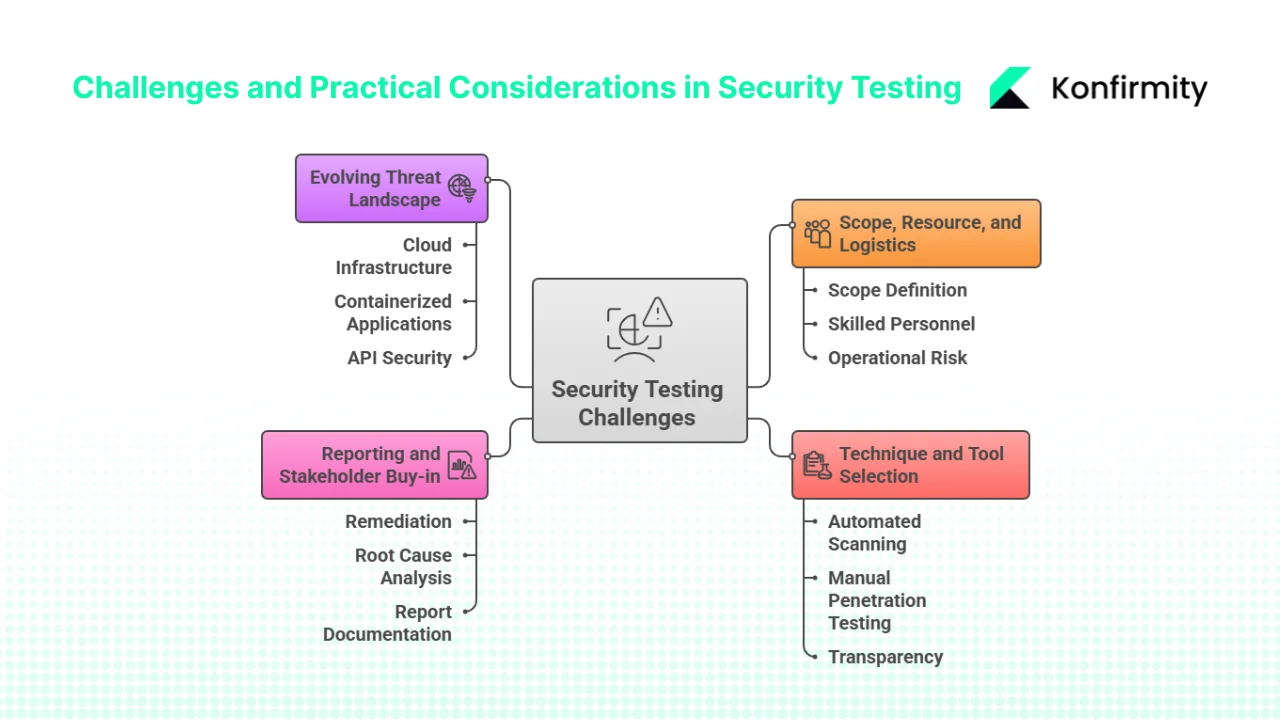
1) Scope, resource and logistics issues
Organizations frequently struggle with defining appropriate assessment scope. Testing everything is prohibitively expensive and time-consuming; testing too little leaves critical systems unexamined. NIST SP 800-115's emphasis on planning addresses this challenge by requiring scope definition based on risk, business criticality, and assessment objectives before testing begins.
Availability of skilled assessment personnel remains a persistent challenge. Vulnerability scanning requires less specialized expertise, but penetration testing—particularly the exploitation/validation phase—demands technical skills in multiple domains: networking, operating systems, web applications, cloud infrastructure, and attacker techniques. Organizations must decide whether to build internal capabilities, engage consulting firms, or adopt managed services based on available resources and assessment frequency requirements.
Testing production systems introduces operational risk. Vulnerability scans can cause system instability if not properly configured; penetration testing might inadvertently disrupt services or expose systems to additional risk if testing credentials are compromised. The test planning phase must address change control requirements, rollback procedures, communication plans, and monitoring during testing to minimize business impact.
2) Choosing the right techniques and tools
Dozens of technical security testing and examination techniques exist that can be used to assess security posture of systems and networks. Organizations must select appropriate techniques based on assessment objectives, system criticality, compliance requirements, available budget and expertise, and acceptable risk levels.
Automated vulnerability scanning tools provide efficient coverage of known vulnerabilities but generate false positives requiring validation, may miss complex logic flaws or business logic vulnerabilities, and cannot assess whether compensating controls effectively mitigate identified risks. Manual penetration testing validates findings and assesses complex attack chains but covers limited scope given time constraints and cannot scale to test entire environments comprehensively.
For companies providing security assessment services or tools to enterprise clients, clearly define what methodologies you employ, what tools you use and how they're configured, what types of vulnerabilities your approach detects versus misses, and how findings are validated before reporting. Enterprise clients appreciate transparency about methodology limitations rather than claims of comprehensive coverage that prove unrealistic.
3) Reporting, stakeholder buy-in and follow-through
Producing impressive vulnerability reports is meaningless without effective remediation, root cause analysis, and process improvement. Organizations frequently conduct assessments, receive reports, and then struggle to prioritize findings, secure remediation resources, track fixes to completion, and validate that remediation was effective.
NIST SP 800-115's emphasis on post-testing activities addresses this challenge: reports should include prioritization based on risk and business impact, remediation guidance specific enough for technical teams to act upon, root cause analysis identifying process or control failures rather than just symptoms, and validation procedures confirming fixes address underlying issues.
Enterprise clients expect security assessment vendors to support the remediation cycle: answering questions about findings, validating proposed fixes, conducting retesting to confirm vulnerabilities are resolved, and tracking metrics like mean time to remediation and vulnerability recurrence rates. Vendors who provide assessment reports and then disengage leave clients struggling with remediation; those who support the complete cycle deliver greater value.
Report documentation must meet enterprise expectations: executive summaries translating technical findings into business risk for leadership, technical details enabling engineers to understand and fix issues, traceability to original test objectives and scope demonstrating thoroughness, evidence artifacts supporting audit requirements, and integration with existing vulnerability management or GRC platforms minimizing manual work.
4) Keeping up with evolving threat, context and technology
NIST SP 800-115 was published September 30, 2008—over 16 years ago. While the fundamental methodology remains sound, the technology landscape, threat environment, and attack techniques have evolved significantly: cloud infrastructure, containerized applications, serverless computing, IoT devices, mobile applications, and API-driven architectures introduce security considerations the original publication didn't extensively address.
Organizations applying 800-115 must adapt the methodology to modern contexts: testing cloud infrastructure requires understanding shared responsibility models and cloud provider security controls; assessing containerized environments demands expertise in container security, orchestration platforms, and image vulnerability scanning; validating API security requires techniques specific to REST, GraphQL, or gRPC rather than traditional web application testing.
For security service providers and tool vendors, this evolution represents both challenge and opportunity: demonstrate how your offering applies 800-115's sound foundational methodology to contemporary environments, show expertise in modern attack techniques and technology stacks, incorporate emerging standards and guidance (NIST continues publishing additional special publications addressing cloud security, supply chain risk, zero trust architecture), and position your approach as principle-based rather than checklist-driven—enabling adaptation as technology continues evolving.
Case Study / Example Application
A SaaS vendor serving enterprise healthcare clients needed to demonstrate robust security testing aligned with both HIPAA technical safeguards and SOC 2 requirements. Enterprise clients increasingly requested evidence of regular penetration testing and vulnerability management before signing contracts or during vendor risk assessments.
The vendor engaged a managed security service provider whose assessment methodology explicitly referenced NIST SP 800-115 phases and techniques. The engagement began with structured test planning: scope included the production application, API infrastructure, and administrative interfaces; rules of engagement prohibited testing during business hours and established escalation procedures for critical findings; objectives focused on validating authentication controls, testing for common OWASP vulnerabilities, and assessing encryption implementation.
Information gathering identified exposed services, mapped API endpoints, and enumerated software versions. Vulnerability analysis using both automated scanning and manual review discovered authentication weaknesses in administrative interfaces, improper access controls allowing privilege escalation, and configuration issues exposing sensitive data in API responses. The exploitation phase validated these findings through controlled testing, demonstrating an attacker could access patient health information without proper authorization.
Post-testing activities produced comprehensive documentation: an executive summary communicated business risk and regulatory implications to the vendor's leadership; technical appendices provided development teams with specific remediation guidance including code examples; root cause analysis identified gaps in secure development practices and code review processes; and remediation recommendations included both immediate fixes and process improvements to prevent similar issues in future releases.
The vendor's security team tracked remediation through their vulnerability management platform, implemented fixes within 30 days for critical findings, and engaged the assessment provider for retesting validating vulnerabilities that were resolved. The vendor incorporated the assessment report and remediation evidence into their security documentation package for enterprise clients.
During subsequent sales cycles, the vendor referenced their NIST SP 800-115-aligned security testing program when enterprise clients requested security information. Procurement teams recognized the methodology, audit teams accepted the reports as evidence for SOC 2 and HIPAA assessments, and the structured approach differentiated the vendor from competitors conducting informal or undocumented testing. The vendor closed two enterprise contracts specifically citing security program maturity as a decisive factor.
This example illustrates how NIST SP 800-115 methodology transforms security testing from a compliance checkbox into a competitive advantage: structured test planning, comprehensive vulnerability analysis, exploitation validation, and audit-ready report documentation build enterprise client confidence and support both security objectives and business development goals.
Conclusion
NIST SP 800-115 assists organizations in planning and conducting technical information security tests and examinations, analyzing findings, and developing mitigation strategies. The standard provides structure to security testing, supports data protection by verifying controls function as intended rather than merely exist on paper, and offers enterprises a recognized methodology for demonstrating security program maturity.
For companies selling security services, assessment tools, or technology products to enterprise clients, aligning offerings to NIST SP 800-115 builds credibility and trust. Enterprise buyers recognize the standard, understand the rigor it represents, and value vendors who speak the language of assessment methodologies, technical security controls, rules of engagement, and audit-ready report documentation. This alignment supports compliance discussions across SOC 2, ISO 27001, HIPAA, and other frameworks requiring security testing evidence.
Organizations should review the complete NIST SP 800-115 publication, map their security programs or service offerings to the standard's phases and techniques, develop test planning templates and reporting structures consistent with 800-115 guidance, and engage enterprise clients using the terminology and methodology they expect. Security testing conducted as a structured discipline following recognized standards delivers greater business value than informal approaches—strengthening both security posture and client relationships.
FAQs
1) What is the NIST SP 800-115 standard?
NIST Special Publication 800-115, "Technical Guide to Information Security Testing and Assessment," provides guidelines for organizations on how to conduct security testing and assessments of their information systems, covering various methodologies, techniques, and processes related to security assessments. The guide addresses vulnerability assessments, penetration testing, security testing techniques, and post-test reporting to help organizations validate control effectiveness.
2) What is the difference between NIST 800-53 and 800-115?
NIST SP 800-53 is a comprehensive catalog of security and privacy controls defining what technical, administrative, and physical safeguards organizations should implement to protect information systems. NIST SP 800-115 focuses on how to test and assess those controls through vulnerability assessment, penetration testing, and other technical examination techniques. While 800-53 tells you what controls to have, 800-115 tells you how to validate they work as intended.
3) What is 800-115?
800-115 is shorthand for NIST Special Publication 800-115, the technical guide for information security testing and assessment providing structured methodology for planning, conducting, analyzing, and reporting on security tests and examinations.
4) What is the main purpose of NIST 800-115?
NIST 800-115 provides organizations with comprehensive guidance on performing security testing and assessments, offering a structured approach to identify vulnerabilities and weaknesses in information systems, validate the effectiveness of security measures, and ensure compliance with security policies and regulations. The guide helps organizations move beyond checking whether controls exist to proving they function effectively under operational conditions.



.svg)
.svg)
.svg)